1. Introduction
In mobile agent research, there are two types of problems: coverage and exploration. Coverage is concerned with patrolling an area, i.e., how to organize the agents so they can maximize the area they can view while still being able to be in contact range of the other agents in a chain [
1,
2,
3,
4]. This assumes that the agents already have full understanding of the area to be able to determine the best course of action to achieve these goals. On the other hand, exploration works with a previously unknown area, and attempts to map all the area. Applications of area exploration include to find survivors quickly, setup a network, or to rendezvous distributed agents. Hence, exploration is a more fundamental problem which may also be used to solve coverage problems.
To explore an unknown area, previous papers have used sensor networks [
5,
6,
7,
8,
9]. This style of exploration has the agents placing static sensors at intervals of the area to create a network and cover the explored area. The sensors then can be used by the agent to find the area boundaries and store information from previous scans of the robots that can help to explore new parts of the area. The agent itself has little memory and relies heavily on the sensors. The sensors must be carried by the agents adding weight that inhibits the mobility.
In this paper, we present a set of algorithms to solve area exploration without using auxiliary static sensor nodes, but rather, with just self-reliant mobile agents. The area is an orthogonal closed region that is made up of horizontal and vertical walls. This area is then discretized into
N traversable points that are connected to their neighboring points in the cardinal directions. An agent moves north, east, south, or west, on the neighbor points from its current position, whenever these points are available. The number
N is not known to the agents. The agents discover the area and the number of points during exploration. The area contains holes, non-traversable locations, which are randomly distributed in the area; for example,
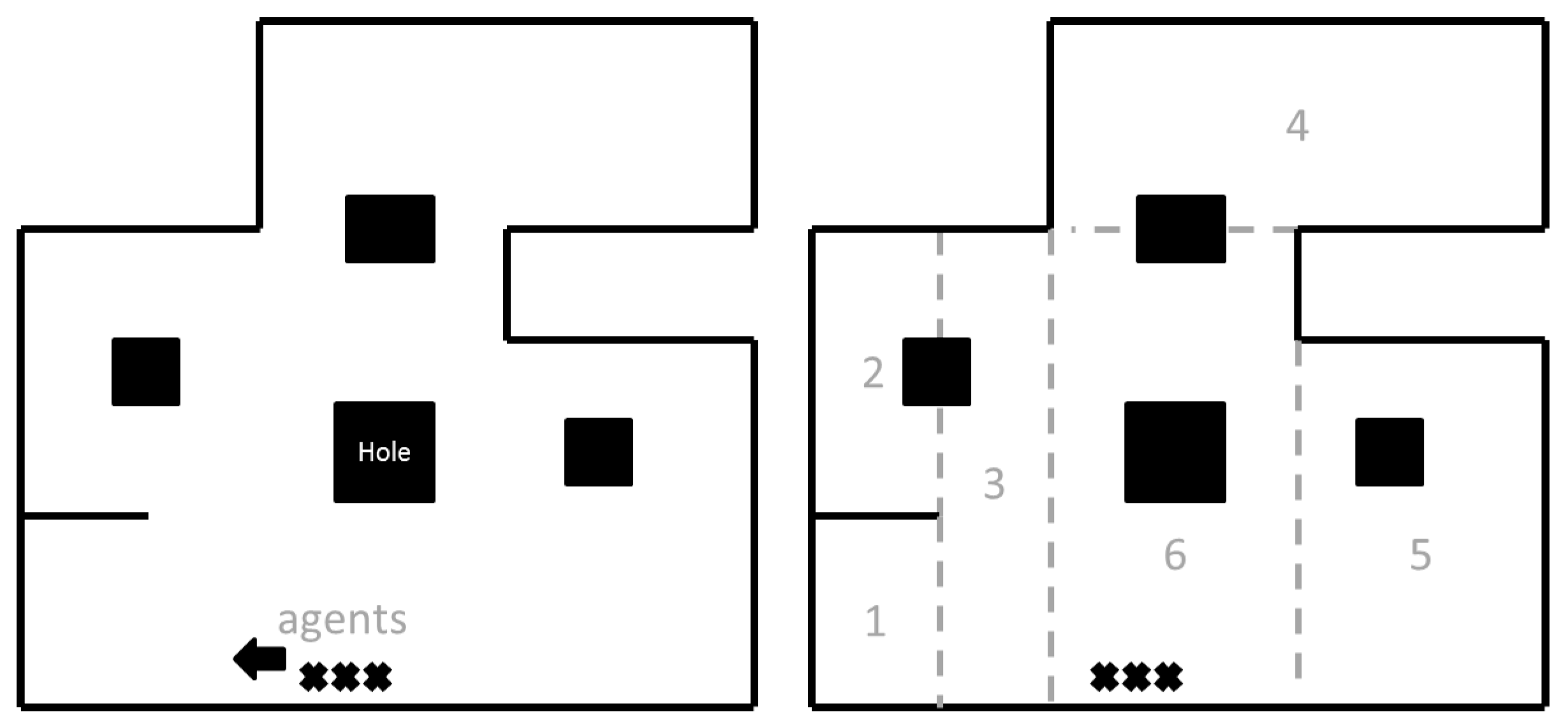
Figure 1 depicts black holes in the area. These holes are rectangular and have a length and width within an aspect ratio
a. The agents begin in a chain along the perimeter of the area,
Figure 1 black
xs. To close area 1,
Figure 1, at the time of reaching the first and second corner a room cannot be closed, it is only after reaching the third corner in this scenario to close a room. This is due to the agents not knowing the composition of the room causing them to have a previously visited
x coordinate with the third corner.
All agents are assumed to be the same with equal traversal ability, communication range, and total memory. An agent occupies a single point at a time and can move one point in the cardinal directions in which the point has connection. We assume that it takes one time step to move point to point. The agents have enough memory to map the entire area (i.e., find coordinates of explored points) which can be shared between agents. To share area information, the agents must be within adjacent points, or in a connected chain in which there is a sequence of adjacent pairs of agents. Agents share information on their total area traversed as well as the orientation of the area. Through this process, agents can make decisions, such as room scan roles, and which one will be the front agent for perimeter scan. These constraints on the agents enables them to not rely on sensors to have knowledge of the unexplored area. The work of an agent is the total number of points it traverses. Each agent keeps track of the work it has performed, and the goal is to maintain balanced work among the agents.
The main goal is to explore an unknown orthogonal region of N points with k mobile agents in parallel in order to reduce the work, which is the total number of points visited, of each agent to explore the area to , namely balancing the work and total exploration time . The difficulty with this is the introduction of holes in the area. If the holes were not there, we could simply traverse the entire perimeter, divide the area into k equal partitions, and send the agents to their respective area. This is not possible with holes, as one or more of these partitions could consist mainly of holes, so the agents associated with those partitions would not perform leading to an imbalance of work between all agents. Thus, we developed an algorithm that handles the unknown holes in the area to maintain balanced work.
The difficulty with these holes is that they are arbitrarily placed in the area. As a sub area was closed, if we simply divided the area into k partitions, then we cannot guarantee that all the agents perform near equal work as they can only communicate within a single grid point. For example, let’s assume that the hole in a room of n points takes up all space except a single path around the area, then if partitioned, each agent encounters the same hole resulting in repeated work, which involves traversing around the hole and performing total work in the area instead of n total work. Moreover, as another example one agent may have to explore smaller number of holes (or total points) than other agents again resulting in imbalanced work.
To get the near equal work for each agent, we have introduced the concept of Leader, Active, and Inactive agent roles when an area is being closed (room created) and explored. These roles are determined based on the amount of work that was previously performed in other closed areas, the most, Leader, the least, Active, and all the rest, Inactive. Leader organizes the other agents to maintain their overall work when Active return to the Leader. Active performs traversal and when enough work has been completed, Active returns to the Leader to maintain equal work. Inactive remain with the Leader until an Active returns sharing its work making them Active. When the closed area is completed the agents return to being against the perimeter to traverse to the next closed area. When a room is discovered then all the agents move to explore the room. Inside the room, the exploration is performed in parallel by the agents while balancing their work. The reason of this approach, of exploring the rooms one after the other in sequence, is to have an online exploration of the whole area in one pass of the perimeter. Otherwise, we would first explore the whole perimeter, and then split the area into rooms, but this would have required to revisit the perimeter. Such a process would also not give us balanced work as large chunks of the area that most of the agents are sent might be made up of holes, unbalancing the agents’ work.
In our algorithm, the agents start along all adjacent to each other next to the perimeter. Then they traverse the perimeter maintaining a convoy. During the traversal, the agents create rooms to explore and map. The whole area is divided on the fly into a sequence of rooms, which are explored one after the other.
In our approach, each room is a rectangular closed area which is identified on the fly at corners of the perimeter. When a room is identified the agents move immediately into the room together and explore all the points of the room by dividing the work among each other. A room may contain obstacles which are not immediately detected, and hence, the area of the room may not be able to be divided equally among the robots, which may cause imbalance of the work. To alleviate this problem, the agents start the room exploration slowly, and use exponential delay and meeting times when exploring the room to handle the unknown holes in the room. Agents that exceed their allocated work quota give future work to other agents to maintain parallelism and load balancing.
Paper Outline
The paper will continue as the following:
Section 2 has the related work,
Section 3 introduces the problem and agent description,
Section 4 our algorithms,
Section 5 the analysis with respective results, and
Section 6 gives conclusion and future work.
2. Related Work
The most related previous work is solving a similar problem, using “oriented disjoint rectangular obstacles” in an
grid [
10]. In this, the agents also use only local information, but with the oriented obstacles, all obstacles follow an oriented pattern that allow the area to be divided into similarly shaped partitions. Our problem has arbitrarily located rectangular obstacles of ratio
a. With this, our problem or theirs cannot be reduced to the same problem. For this reason, a new algorithm had to be developed not only to traverse the entire area, as it does not follow their
grid rules with disjointed obstacles, and another algorithm for the room, as the obstacles do not follow the same constraints. Finally, our focus is on balanced work as well as parallel while theirs is only on parallel work.
The most closely related topics in the literature are “map merging”, concerned with multiple-robot simultaneous localization and mapping (SLAM) [
11], and “map synchronization” [
12], where the agents share the map information of the area explored. Agents are not assumed to be together and use probabilistic generalized Voronoi diagram to, “achieve fast and accurate map fusion for large maps”[
11]. In map synchronization, agents can form into subgroups that are close enough to have the same map, while other agents that are not will synchronize maps when they approach [
12]. This is also similar to Frontier based, which is concerned with exploring all points of a grid area in a minimum amount of time [
13,
14]. However, these do not consider load balancing the work of the agents as we do here.
One topic of focus on this area is agents that can fail. This can be through “black hole” or “black link” in an edge or link in a sensor network [
15], or the agent itself can fail [
16]. To be able to explore the entire area, the number of sensors must be more than the number of edges plus two times the number of links [
15]. With using “pheromones”, Levy Walk was determined to outperform random walk when exploring, especially when failure prone agents are introduced [
16].
Exploration is also a topic of interest in communication networks. Ad-Hoc networks are constantly changing, mobile agent routing leaves information at nodes it visits and reads the information that is left at a node [
17,
18]. In this way, the agents can cooperate much like ants leaving information to share with others when looking for food. When speed of network changes increases the delay decreases but roughly only 68% of packets are received and this amount drops greatly as speed increases [
17]. MAR [
18] can perform at greater speeds with the same percentage of packets received but less delay.
Machine learning algorithms have also been used for mobile agent exploration. Q-Learning has been used as a “Human-like” learning algorithm to manage energy, avoid obstacles, working towards goals, and following a line [
8]. Another implementation used online-learning Bayesian network to predict terrain range and magnetic field intensity [
19]. A second online-learning method used Gaussian Processes [
20]. In this learning, decentralized agents, flying quadcopters, are used to explore an area by mapping the distance of an unknown environment [
20].
Agents have also been given roles or working with a stationary agent to explore an area. For search and rescue, agents are given a larger environment than what they can explore while staying in range so they must go out of communication range with agents being declared explorers or relays [
21]. Area is shared from the explorer to the relay and then back to the command center [
21]. Another case is when the agent must communicate with a computer when an obstacle is located so that the computer can determine the path to take [
22]. The agents can also make a decision given multiple criteria to locate and rescue victims within a limited amount of time [
23]. This MCDM model, used in search and rescue does not attempt to explore the whole map, but to use the knowledge of the agents exploration to move quickly to locations that the victims are believed to be, in this manner it finds the majority in the least amount of time [
23].
Similar to search and rescue, research has also been conducted for agents to rendezvous before exploration of the area [
24]. In this research, agents look for “landmarks” to attempt to see if any other agents are within range of their sight or if they can find any other “landmarks” to search from there [
24]. This research does not focus on the exploration itself, but attempts to minimize the time for agents to rendezvous.
Constraints have been set on the power of agents, they are assumed to have limited power and must work together to find “targets” distributed in an unexplored area. The first strategy is to use a similar technique as ants, drop pheromones, to tell other agents this area has been explored, or there is a target in this direction [
25]. This strategy does not require communication, so it is able to save more energy for exploration. Next, the technique is to use communication between agents similar to how fireflies communicate [
25]. The downside to this strategy is that it consumes energy to communicate. The more complex the task the better firefly approach performs compared to the ant approach.
3. Model
The problem we are exploring consider an orthogonal area on the plane. Through this, the perimeter edges all meet at right angles. There can also be interior lines within the interior which are extension of the edges from the perimeter. It is assumed that the whole orthogonal area can be discretized into grid points that make up the entire orthogonal area. We assume that grid points are spaced one unit distance apart. Each point is adjacent to those (up to four) neighbor grid points that are one unit distance in the cardinal directions (north, east, south, west).
We assume that all agents have the same sense of common cardinal directions, where they all know where is north, east, south, and west. This helps them to agree on a common clockwise direction for traversing the perimeter. An agent is dimensionless and resides in exactly one grid point at a time. Two agents directly communicate (they are in communication range with each other) if they reside in adjacent grid points (one unit distance away). However, they can also indirectly communicate with each other through a chain of agents such that each pair along the chain reside in adjacent grid points. The agent visibility range includes the four adjacent points in the cardinal direction. Agents can maneuver on the grid points moving from the current grid point to an adjacent grid point.
In the area there are rectangular holes such that no grid point exists in the hole making them non-traversable. These holes are unknown until discovered by an agent. Each hole in the area has an aspect ratio a such that a hole can be of any size as long as the width and length are bounded by the aspect ratio; that is, the width over length ratio is bounded by a, and length over width ratio is also bounded by a. Each hole must have at least two unit distance separating it from another hole or from any edge of the perimeter (or internal edge). In this way, at least one grid point fits between the holes or between a hole and an edge. To completely discover a hole, an agent must traverse around the hole, which is the only way to detect whether it is a hole or part of the perimeter.
A unit of work corresponds to visiting a grid point. To completely explore the area, all the grid points that make up the area must be visited, and the information is shared by each agent. The agents have enough memory to map the entire area as well as recording the amount of work performed by all agents, both perimeter and room work. A worst case bound for the total amount of memory that an agent would need to have to map the entire area would be storing N coordinates, corresponding to the total number of grid points in the area. In addition, an agent may store information to track the amount of work performed by the other agents. Agents share the information of what they have encountered, including holes and grid points, when they return to communication range. All agents are assumed to be identical; able to traverse a single grid point at each time step, communication range of one grid point, vision of one grid point to map the area surrounding the agent. Each grid point that an agent moves counts as one unit of work. Multiple agents can all communicate with one another through a chain of agents.
During the perimeter work, agents move together maintaining a chain along the perimeter. Agents move together to find a room and then perform the room scan algorithm in parallel. As this area is unknown the agents must follow in this convoy as communication is limited. In an attempt to close a room, the front agent will attempt to leave the perimeter to reach a previously explored grid point. If able to close, then the front agent returns to the other agents and perform the room work, otherwise, the front agent returns, and they continue traversing the perimeter. After completing room work, the agents determine, through their chain of communication, which agent has the least total perimeter work and that agent is moved to the front of the agents to lead the perimeter traversal.
When a room is encountered, then the agents must determine their role, Leader, Active, or Inactive. The one that is Leader is the one that has the most work, Active is the one that has the least work, and Inactive are all those in between. As agents communicate their total work, if two agents have most total work then we assume they have unique identifiers and the one with the lower identifier is made Leader. Leader communicates with the Active as they return to share or give their work to an Inactive to maintain equal room work. In keeping balanced work agents must return to the Leader for communication range to determine what to do with their work. Please note that even through the Leader is stationary, it already performed most of the work and the other nodes can perform the work, and in any case the Leader will be swapped by one the remaining agents that returns with more work. Active traverse the area, after a set amount of work if there remains work in the room, then the Active returns to Leader to determine what is to be done next. Finally, Inactive wait with the Leader to be given work that remains from the Active. Active agents know the location of the Leader and Inactive agents to return to communicate with the Leader. When the Active gains more work than the Leader, the Active and Leader will change roles. Once the work is completed all agents will return to the Leader to organize into a line along the perimeter.
This process of performing perimeter work until a room is discovered and then performing room work is repeated until all points are traversed.
4. Algorithms
As mentioned in the introduction, the exploration algorithms can be separated into two parts, perimeter exploration and room exploration. In perimeter exploration the area is divided into rooms. Agents maintain a track of the work they perform during perimeter and the work they perform during room exploration separately. During perimeter work, agents will rotate the agent with the lowest perimeter work after a room is attempted to be closed to maintain balanced perimeter work. With room work, the agent with the most work will be in charge of coordinating the room work between other agents and transferring the responsibility to a new agent with more work whenever necessary.
4.1. Perimeter Exploration
The first algorithm performs the exploration of perimeter
P (Algorithm 1) . When the exploration begins, the agents all traverse clockwise along the perimeter, depicted in
Figure 1 by the black arrow. The agents follow the front agent in that direction maintaining a connected convoy (chain of agents), as discussed in
Section 3, along the perimeter of the area, adding explored points to
P. If the front agent is no longer against the perimeter or they have reached a perimeter wall along the path they notify the other agents that a corner has been reached at point
. At this point, before continuing along the perimeter moving along the path, if a corner is encountered then the front agent looks at its mapping of the area to determine if they have already visited a perimeter point across, namely
such that
where
or
and
is in the visited
P. The agent can find possibly up to three candidate
depending on exploration history of
P, as shown for example in
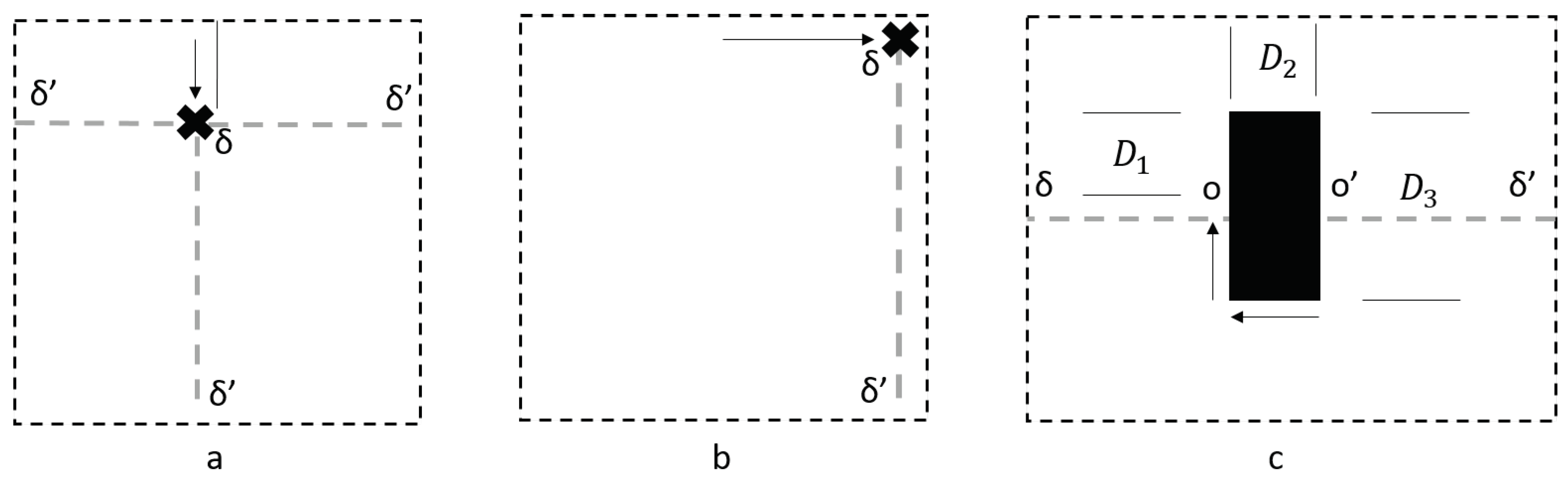
Figure 2a,b.
Figure 2a,b depicts zooming in on a corner point such that in
Figure 2a, the agent encounters the corner from traversing from the top, while in
Figure 2b, the agent encounters the corner traversing from the left. Each of these candidate closures can be placed in a queue, without loss of generality, we can assume they are placed in the queue from cardinal direction north then clockwise around the front agent.
The front agent then takes the first direction in the queue and begins moving towards the picked
to determine if a room closure is possible. The front agent continues along a straight path until reaching the previously explored position
, as for example depicted in room 1 generated in
Figure 1 where no obstacle is encountered. Otherwise, as depicted in
Figure 1 in the generation of room 3, if the agent detects an obstacle along its path then it must determine if the obstacle is a hole or a wall, which is determined by calling the obstacle subroutine Algorithm 2.
The front agent returns to if an unexplored wall was hit or the agent successfully reached . After returning, if was reached a room has been found, and then room scan is called, and the corner is marked as used. After performing room scan, or hitting a wall and returning, the front agent of the convoy switching with the agent that has the least amount of perimeter work completed, to balance the work in the perimeter. After all the have been explored for that , the agents perform the turn and continue scanning the remainder of the perimeter.
| Algorithm 1: PerimeterScan |
![Algorithms 12 00104 i001 Algorithms 12 00104 i001]() |
The obstacle subroutine Algorithm 2 determines if the obstacle encountered is a hole or a wall. Let the point that the obstacle is encountered be
o. The agent checks that the first length of the obstacle
(see
Figure 2c), perpendicular to the line
l between
and
, is shorter than the aspect ratio
a multiplied by the length of
l which is
. If this value is exceeded, then the obstacle cannot be a hole that fits between
and
. Continuing from this point, the agent checks each dimension to make sure that the obstacle is a hole. It checks if both of the lengths
and
,
Figure 2c, are within the
a aspect ratio, first between
and
and finally between
and
. During the exploration to
the agent will pass
such that
is on the line from
to
. After this point, it is known that the obstacle adheres the aspect ratio restrictions of a hole, but the agent must make sure that it is rectangular by returning to
o around the points that are between
and
that have not been explored. If it is indeed a hole, the agent adds in its memory as a known hole, a hole that is detected in the area, and returns to
.
| Algorithm 2: ObstacleCheck () |
![Algorithms 12 00104 i002 Algorithms 12 00104 i002]() |
4.2. Room Exploration
After front agent in perimeter scan successfully reaches and returning to the other agents, a room is found, the room scan is invoked. Now that the dimension of the room is known, the agents could have divided the room into k equal areas and begin to search. However, given that the holes are arbitrarily placed, it can be such that the assignments of some agents may contain no work. The other agents cannot detect this until being within communication range. With this, it can also be such that the agents repeat the same work when traversing around a hole in the area. Therefore, to maintain balanced work, we introduce agent roles and a slow start to increase parallelism.
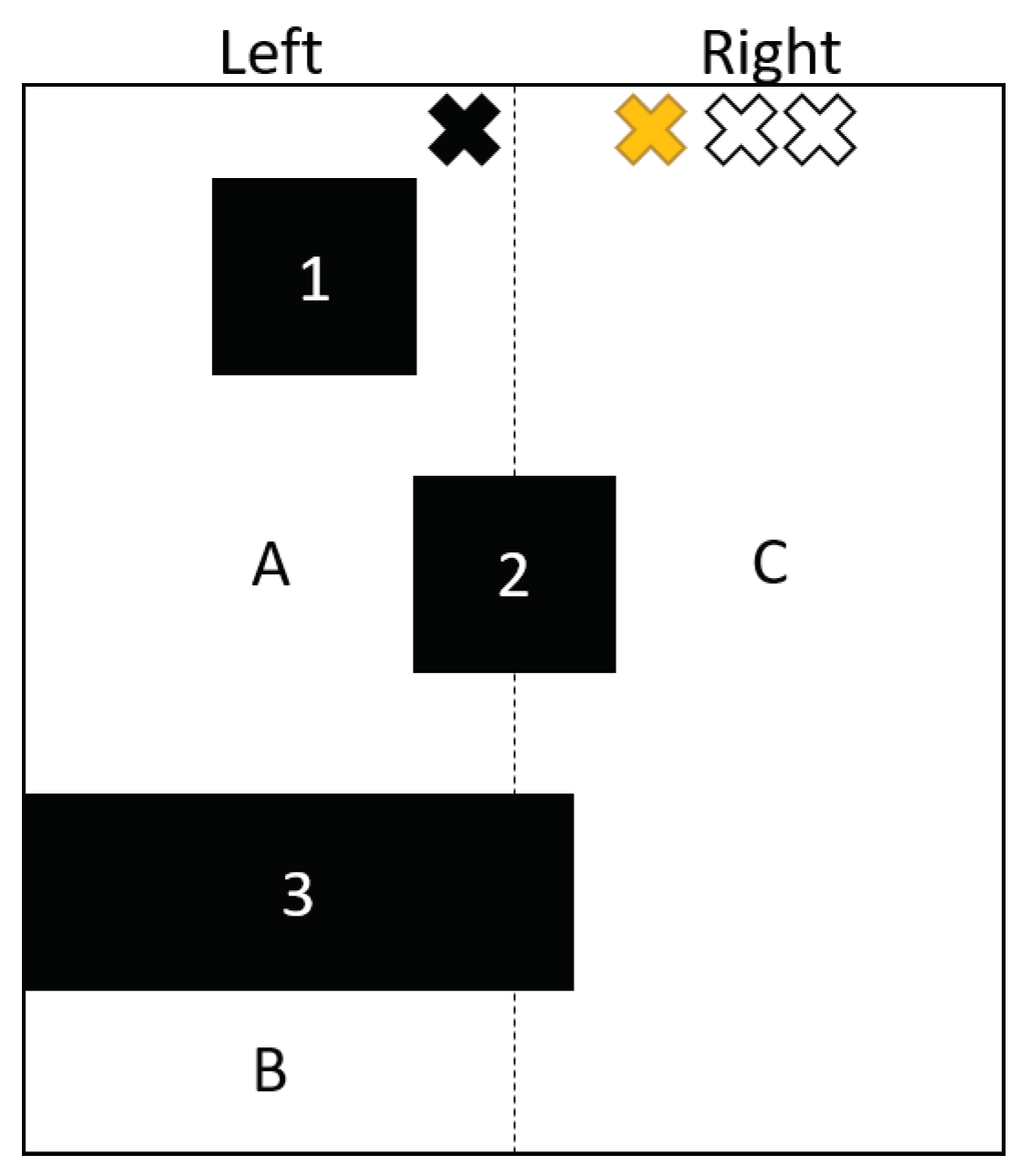
The agents are set to the roles of Leader, Active, or Inactive. All agents are within communication range at this point and communicate their work with the other agents to determine who has the most work, Leader, and the one with least work, Active, and the remaining, Inactive. If two share work then that agent with the lower ID will be Leader. The purpose of the Leader is to maintain a ratio of work between all agents to balance the work performed by each agent. The Active agent is given a task in the form of a stack of areas to explore, and performs the exploration until a work threshold is reached. This stack is initially a single task consisting of the entire room. As the Active agent performs the traversal it will split the current task and push it back on the stack. A task is two corner points of the perimeter of the area they are required to explore. In giving the Active agent these two points, the agent can discern the rectangle of exploration.
The Inactive agents are in a convoy by the Leader waiting for the Leader to give them a task and become Active. The allocation of the work to the agents is performed in a balanced way, such that those agents with lower work are given work and those that exceed the work of lower working agents are made Inactive. If this is the first room attempted to close then no agent has any room work so it is arbitrary which agent is set to Leader, Active, or Inactive. Otherwise, the agent with the most room work is set to the Leader, yellow ‘x’ in
Figure 3, the one with the least room work is set to Active, black ‘x’ in
Figure 3, and the rest begin as Inactive, white ‘x’ in
Figure 3.
The work threshold of an Active agent is initially set to a value
that is determined by the longest length of the room and the cost of traversing around holes on a straight path, discussed in more detail in
Section 5 where we analyze the algorithm. As the room exploration progresses, the work threshold exponentially increases to accommodate the expected work in the newly discovered areas. The amount of work threshold only increases when work is not shared or given to another agent. This is due to the fact that if no other agent was there, then doubling the amount of work to return will maintain equal work among the agents. Gradually, Inactive agents are becoming Active as more area is discovered in the room.
The Leader subroutine (Algorithm 3) describes the Leader’s role as Active agents return to the Leader. The Leader’s job is to maintain the remaining work between itself and the Active and Inactive agents. When an agent i has performed work that exceeds its threshold or it ran out of tasks to perform, it returns to communication range of the Leader. In performing this the agents repeats the same amount of work as the threshold to return, but with exponentially increasing work threshold the agent will perform more new work than the cost to return to the Leader. This way, load balancing can be achieved at a faster pace. It is necessary to return to communication with the Leader to enable the Leader to balance the work between the Inactive agents. If the agent i has a stack remaining, or the Leader has a stack, then the Leader takes agent is stack and merges it with its own. The Leader must first make sure that the total work performed by agent i has not exceeded a ratio 3 between the Leader and agent i, if agent i did exceed this ratio, then the Leader and agent swap roles and the Leader begins the Active part of RoomScan. If at least one other Inactive agent j is waiting with agent i then the Leader must check the ratio of work between agent i and all Inactive agents j to decide what to do with the stack. If agent is work is within a ratio 4 of all other agents j then the Leader splits the stack in half, giving one part back to agent i and the other to the agent with lowest total work. After this, the Leader resets the threshold back to the minimum for agent i and signals agents i and j to become Active. Otherwise, if Inactive agent(s) j are waiting and i has exceeded the ratio, then the entire stack is given to the agent with lowest total work. Finally, if no other agent is Inactive and agent i is within a ratio of 4 between all the Active agents, then the stack is returned to agent i and agent i is signaled to remain Active.
The Active subroutine (Algorithm 4) describes the Active agents’ role as they are given a task by the Leader. The agent
i tracks their current work, and their current threshold of work to determine when to return to the Leader. While the agent has task(s) to accomplish and the new work they have completed has not exceeded the current work threshold, the agent will take a task to accomplish. Agent
i then takes the current task area and determines what are the smaller and larger dimensions of this task area. Then, agent
i moves to the middle of the larger dimension and determines how many sub areas will be generated by traversing across the line that splits the task area. The sub areas are determined by the holes encountered through this line, such that holes touching the line and the boundaries of the original area determine new sub areas. We give an example of this step in
Figure 3, as explained below. The reason for the room split is to parallelize the exploration task of the room, as the different agents will move to the various identified sub areas and explore them in parallel. The created sub areas are pushed to the stack, and each of them has the potential to be subdivided further.
| Algorithm 3: Leader part of RoomScan |
![Algorithms 12 00104 i003 Algorithms 12 00104 i003]() |
For example,
Figure 3 shows the vertical traversal line that goes through the room and splits it across the hole boundaries (holes labeled 1, 2, 3) into three subareas
A,
B, and
C. As shown in
Figure 3, agent
i does not have to change its traversal due to hole 1 as this hole is at least one point away from the traversal line. Agent
i will have to change its traversal, due to hole 2 as this is along the traversal path and unknown to agent
i. As
Figure 3 has the Leader in the top right and the split is vertical, the agent pushes areas onto the stack from the right to the left so that the area furthest from the Leader is the next task to be explored. For each room on the right of the split the agent
i pushes the furthest from the Leader on the stack, from
Figure 3 only
C is on the right. Then, agent
i begins pushing the rooms on the left from the closest to the furthest from the Leader,
Figure 3 first
A then
B. This process is similar for other locations of the Leader and split type, to maintain a stack of connected areas with the top being the furthest from the Leader on the opposite half of the area.
When the work threshold was reached and agent i still has a stack of task(s), it doubles the work threshold and goes back to the Leader. The purpose of doubling the work threshold is such that if no other agent was there to share work, then the other agents j are all Active and the agent i should perform more exploration before going to the Leader again. As all other agents j are Active, agent i can perform double the work and maintain the ratio 4 between all other Active agents j. If at any point agent i has no more tasks to do then agent i returns to the Leader.
| Algorithm 4: Active agent i in RoomScan |
![Algorithms 12 00104 i004 Algorithms 12 00104 i004]() |
5. Analysis
We continue now with the analysis of the algorithms. We have separated the two types of agents’ actions, perimeter and room scan, to clearly discuss the work performed during each algorithm.
Section 5.1 goes though the proof for perimeter scan and obstacle check.
Section 5.2 will deal with room scan and the actions of the Leader and other agents (Active/Inactive). Finally, in
Section 5.3, we combine the analysis for the works completed during all algorithms to prove the total work performed by each agent is
and total time is
where N is the total number of grid points in the orthogonal region.
5.1. Perimeter Scan
To analyze these algorithms, we begin by proving the completeness of perimeter scan. We show that the algorithm performs a post-order traversal of all the rooms through converting the sequence of steps as rooms are generated into a tree structure. From here, we analyze the total amount of work that has been completed by each agent during the perimeter scan and obstacle check algorithms.
5.1.1. Sequence of Steps
Perimeter scan can be broken down into a sequence of steps , such that each is a grid point , and any two consecutive points in the sequence differ in only one dimension, namely either and , or and , for . From this sequence, three types of subsequences occur: Wall, Corner, and Cross.
Wall: subsequence of steps , where , such that either the x-coordinate is the same (), or the y-coordinate is the same (), i.e., the subsequence of steps follows along the same x or y coordinate.
Corner: Is a single point , that changes from the dimension of the subsequence path, either , and , or , and , .
Cross: a subsequence of closing a room from corner or a wall to another wall or corner. Namely, it is a subsequence after a corner or wall, such that is a recently visited grid point and and share either x or y value ( and or and ). The other points will differ by one point in the x or y direction such that and or and as the agents could have encountered holes along the Cross. Algorithm 1, when closing a room ends in (Lines 11–25).
5.1.2. Special Subsequences and Rooms
Define a new sequence , where each element is a subsequence of S, representing either walls, corners, crosses, i.e., . First three type have an attribute: for , , where the start point is , and the end point is ; for , , where is the corner coordinate, and denotes the direction of the turn which is either left or right; and for , , where start point is and the end point is .
In closing a room, a room starts with a
or
, and ends with a
. A
is followed by a
or a
if they all had exterior walls along the path, or a
if there was a successful room closure direction. In
Figure 4, part a begins with a
,
, and repeats until the
is reached that reached that has the previously explored point in
that was successfully reached by the front agent, whereas in part b, the room begins with a
,
.
5.1.3. Replacing Rooms and Sequence Transformation
We can define a sequence of subsequences . Each pth subsequence is generated by the item in the sequence, so that subsequence is generated after room discovered in . Subsequence replaces the subsequence of : that made up room with a new subsequence that transforms the into (s) and (s) depend on how the room was entered and the holes along the . When a room is closed we want to treat the of that room as a for future room generation. To do this we create a new subsequence and treat that as a in the subsequence.
This new subsequence is
such that
j is the maximum number of subsequence elements. In
Figure 5a the sequence in
,
is replaced in
to
, the attributes developed from the attributes of
,
, and
, see for example
Table 1. Similarly,
Figure 5b transforms from
,
, and
to
. In performing this transformation,
Table 1 depicts how each basic
q is mapped to
. Similarly, more complex
are generated in the same manner. As these are only two basic room types, without any holes, other closures will have multiple
created for
, the
, as with the introduction of holes the
will transform into multiple
and
as it is no longer a traversal along a single dimension.
For , the last room in the region, as will be all elements of , replaces the subsequence of , that made up room with signifying that the region is explored in its entirety.
5.1.4. Conversion to Tree
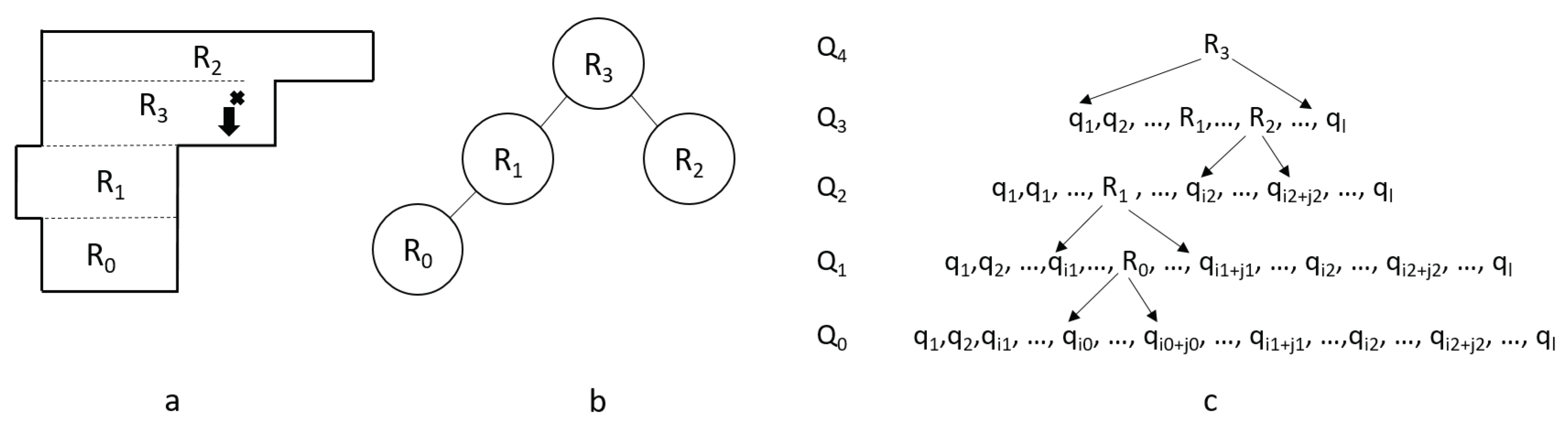
Given
is a sequence of steps
that discovers a room
, traversing the discovery of rooms in reverse,
, a tree
T of rooms can be generated (see
Figure 6b). The root of
T is room
(room
in
Figure 6) which is the last room to be discovered and corresponds to the room where the agents started the whole discovery process. Suppose that
corresponds to sequence
in
. Room
was generated from
and is included in
.
The children of
are the rooms
such that
is in the sequence of
in
between the points
and
that generated
(see
Figure 6c). Given multiple children of
they are added to the tree from left to right following their ordering in the sequence. If a room
does not have any room sequence between its respective
and
, then it is considered to be a leaf of the tree. Following these rules we generate a tree structure, with
as the root, as we work backwards from the room discovery,
Figure 6c, adding the respective children of each room as it is expanded from
to
until we return to
.
For the discussion below assume that two points and are ordered as if , and if . Consider two rooms and that in have the corresponding subsequences and respectively. The sequences of and in are either disjoined, when or , or contained, when and or and , or connected, when or .
Lemma 1. Any pair of connected rooms, with neither being the root, have the same parent.
Proof. Let us assume that and are two connected rooms. Let be the parent . Since is the parent of we have that is the first room that contains , we have and . Also, from connected we know that either or . Thus, or . Therefore, from our projections and are not disjoined or connected, namely one contains the other.
Suppose that . Therefore, contains . Since contains , we have that contains , which is a contradiction, since and are connected. Therefore, . Consequently, must also contain .
Suppose that there is another room that is the parent of . Therefore as rooms and are connected then contains , As is the parent of , must be contained in . This results in a contradiction because contains and is a descendant of . From this, is the parent of and . □
If the room discovered in was not the room the agents began the exploration in, then there are two connected rooms that are the roots of two trees.
Lemma 2. For disjoint rooms and where , the subsequence that generates must appear earlier than in .
Proof. Let’s assume that it is possible for subsequence, , to appear earlier than subsequence, , in ; . As traversal is from left to right, at some such that the subsequence, would be traversed and then at the subsequence would be traversed. Thus, it is not possible for an earlier subsequence that makes up a disjoined room to be explored after a later disjoined room. □
All points will be covered by agents after the entire perimeter is traversed. Given Lemmas 1 and Lemma 2 the whole area is divided into room which are explored in a post-order traversal of
T. As we see from
Figure 6a, from the agent’s start position and traversal direction, the agents discover room
and 3 which after generating the tree structure,
Figure 6b, traverses the left subtree, then the right subtree, and finally the root, a post-order traversal.
Corollary 1. The area is divided into rooms through the traversal of the perimeter. Following in reverse order create a tree T of rooms which are explored following post-order traversal of the tree.
5.1.5. Perimeter Traversal
During perimeter scan, all agents will perform the traversal along the perimeter of the outer wall. When agents reach a corner that is along a previously explored point, the front agent will attempt to close the room and return. If an obstacle is detected then that agent will try to determine if it is a hole, given the aspect ratio, if it is then that agent continues to attempt to close the room. The agent returns to other agents if it is a room or runs into a wall. From there, if it is a room, room scan will begin, otherwise the agents will continue perimeter scan. Before continuing perimeter scan the agent that has the least amount of perimeter work completed, such that it has not attempted to close a room or has had the smallest attempt of all agents to close a room, switches places with the front agent.
Lemma 3. A shortest path of adjacent points in the orthogonal region between any two points on a single dimension with Euclidean distance C from each other, has a maximum length of .
Proof. Without loss of generality, let us assume that the start and end points are on the same horizontal line. Then we can form a path which traverses from the start to end consisting of several path segments:
Each are the lengths of horizontal path segments on same line as start and end, are the lengths of horizontal path segments along encountered holes parallel to the line between start and end, are the lengths of vertical path segments of encountered holes that are perpendicular to the line between start and end. There are two for every as there is a connecting to and connecting to . Due to holes being rectangular, the sum of .
We will continue to show . As a is the aspect ratio of the hole dimensions, then for each hole length we can assume the longer length is the associated and , meaning that at most these can be larger. Thus, since each has two associated , . As stated above, then, since , , thus, . □
Suppose that the perimeter, not including attempted, up to discovery of room has traversable points. Each of these points is traversed by all k agents. The total traversable points is , then orthogonal region up to room i has a total interior traversable points such that where we remove the perimeter points from the total points in the area.
Lemma 4. Total perimeter work from all agents performed is .
Proof. As the perimeter is traversed by all agents, k agents perform movements to traverse all points along the perimeter. During a only the agent with the least perimeter total work will gather work. Holes and walls discovered by an agent during a are known by all other agents when the crossing agent returns. Agents do not attempt to close a room if a previously discovered hole or wall is located along that path. For this reason, there are two opportunities to traverse a position in the room, horizontal and vertical crosses, and as such, 4 traversals over any position in both directions of the Cross. Thus, the total amount of work performed during is for perimeter movements and for the attempted crosses. □
From Lemma 3, there is a with maximum Euclidean distance corresponds to a maximum path distance , when moving around holes. is the largest distance that any agent traverses during the traversal of its assigned Cross.
Lemma 5. Difference in perimeter work between any two agents is .
Proof. All agents perform the perimeter traversals, so the difference in work appears when crosses are performed, as these are done by a single agent. Agents swap after completing a Cross if another agent has less work to allow them to perform the next Cross. Let us assume that an agent could exceed work compared to other agents. For two agents i and j with respective works and , if then before the Cross was taken, as agent i could gain at most new work. This contradicts the algorithm as the agent with the lower work would perform a Cross. Hence, all agents are bounded by a difference in work of . □
Lemma 6 (Perimeter Work)
If , the perimeter work of each individual agent is .
Proof. From Lemma 4, we have that the total work is and Lemma 5 proves the max difference between any two agents is . As agents are within work of one another, each agent must have work at most . With the assumption that , this can be simplified to which is . □
Lemma 7 (Perimeter Time)
With total number of Γ the total perimeter time is at most .
Proof. Each agent follows along the perimeter moving one position each time step, given P perimeter points, takes P time to visit each perimeter position. At every we have at most 3 directions that a room can be generated with a maximum of distance to traverse. An agent must traverse the closure in both directions, thus to traverse possible room closures for all . This creates an upper bound on the total time to finish the perimeter scan portion . □
5.2. Room Scan
We continue with the work analysis of the agents during room scan. In our algorithm, as the perimeter scan progresses, new rooms are being discovered, and each room is explored separately in room scan by the work performed by the Active agents and controlled by the Leader. For balancing the work, the robots keep a separate count of the total work performed during room scan. The first room discovered is a special case, as there are no previous rooms or room work. Hence, we start with analyzing the work completed by each agent in the first room. From this point, we can now describe the relationship between all agents work throughout each subsequent room exploration to explain total work of all agents together and work performed by each agent individually after the completion of each separate room. Finally, after the last room we can analyze the total work and work completed by each agent at the end of the whole area exploration.
5.2.1. First Room Exploration
Consider the first closed room and suppose that it is of size , where the length of is at least as large as . Suppose also that there is a total of n traversable points in the room. The aspect ratio of the holes in the room is a. Without loss of generality, we will assume that is horizontal, and is vertical. All agents currently have 0 initial work. Before, we proceed with the work analysis, we need bound the longest shortest path in the room, which will be later used to bound the difference on the works of different agents.
Lemma 8. The maximum shortest path between any two points in a room has length .
Proof. A shortest path between any arbitrary pair of points in the room can be formed by connecting two subpaths h and v, the first is horizontal of length H, and the second is vertical of length V, to reach the other point.
There can be a hole along the two subpaths. This creates key positions in the path and . is the starting point, and is the ending point. Assuming horizontal subpath taken first, and are the start and end positions, respectively, of h and and are the start and end positions of v. If then there is a path around a hole that goes from to and to . This hole is only traversed along two dimensions, one horizontal and one vertical, with lengths and , respectively. Therefore, .
From Lemma 3, and . Thus, the total length of the path at most . □
Lemma 9. In a room with n points the total work by all agents is .
Proof. Let us take the case that there is a single agent with no specific work threshold to returning to the meeting point in the room. From Algorithm 4, the agent takes the original area, moves to the middle of the long dimension and performs a split traversing unexplored positions along this traversal. After exploration , the total room, generates a stack of connected areas such that there is a path of previously explored points on the split that connects each pair of and . When is popped off it can either make sub areas that are connected through the split of and connect to through the previous split or the agent moves to along the split of . Through this recursive process, the agent traverses split positions at most 4 times (down and up both halves). Every point with will be part a split in one of the recursive steps. Therefore, the whole recursive process is generating total traversals of the total .
Now let us add multiple agents that balance their work, but without acting concurrently, i.e., when the work threshold is reached an agent swaps its stack of work with another agent to balance its work. With a threshold, agents are now able to leave and return to an if they have completed enough work to return to the Leader and another agent returns in their place. From Lemma 8, the threshold newly explored points. In this, newly explored points pays for already explored points when going to the origin and swap the stacks. Since in the worst case an agent may return at most times to the origin, the total work with the threshold is at most .
Finally, we view the complete algorithm with multiple agents that can also share the work when the threshold is reached, i.e., the agents perform parallel exploration. With agents splitting their work with another agent, according to Algorithm 4 one agent had work and reached the threshold. Upon returning, it shares half the work, some area , such that the first agent contains and the second agent contains . With this addition, agents can perform work in parallel, gaining the ability to share work but requiring another D each time sharing happens to account for the new agent to traverse to its given area. Therefore, total work becomes at most . □
Lemma 10. At the end of the room scan of a room with n points, given the initial work of all agents is 0, one of the two holds:
- i.
If , the difference in work between any two agents is , or otherwise,
- ii.
the ratio of the work between any two agents is bounded by 8.
Proof. For case i, as agents return to meet after work, where , then there are not enough traversable points for all agents to get work. This will lead to some out of k agents completing work and other agents not completing any work.
For case ii, , such that all agents were given a chance to be Active. The Leader maintains a ratio 4 of work between all agents and a ratio 3 between all other agents and the Leader. As two agents may approach the ratio 4 and the lower one could complete work just after the one with greater work has completed, then the agent with greater work will double their current work before returning being at most ratio 8 more work than this agent. After returning this agent will be set to Inactive and swapped with the lower total work agent. As the Leader has global knowledge of the work of all agents, after they share information, the Leader can maintain the ratio 8 of work between all agents. □
Theorem 1. At the end of the room scan with n points, each agent performs work when .
Proof. From Lemma 9, let the total work be , for some constant . From case (ii) of Lemma 10, the ratio of the work between any two agents is at most 8. Therefore, since there is an agent that has work at most , each agent’s work does not exceed . □
5.2.2. Room Exploration
Let be the sequence of rooms that are visited in the algorithm. For each room , let be the maximum shortest path distance between any pair of points in , and let be the total number of traversable points in the room. For each room, the total number of previously explored points in the previously explored rooms are taken into account when determining the difference in work between agents. As with perimeter scan, we will use . We will show that when the sum of work in all rooms explored exceeds , a ratio 8 between the works of the agents is maintained. We define as the sum of all the traversable points in all the rooms up to , i.e., . After the completion of the room , each agent k has an associated work .
We extend Lemma 10, to the more general case where agents have prior work.
Lemma 11. If before the scan of room , , the work of any two agents g and h differ in work , then at the end of the room scan of then the difference is maintained or a ratio 8 is achieved.
Proof. Initially, only one agent gets Active in , suppose g. It must be that the work of g before , , is at most the work of every other agent h. In its traversal, g gains at most additional work. Therefore, . Thus, since our algorithm always picks an agent with the lowest work, as long as a single agent is scanning the room , the maximum work difference of is preserved.
Now, that the algorithm sends two or more agents for scanning. The agents that are selected by the Leader to scan the room must start with a ratio of work 4 within each other. These selected agents have also the lowest work at the time of their activation, with respect to all agents k, and each agent must have minimum total work of . At any time during their scan, the Active agents accumulate new work, but each agent at most doubles its work (according to our algorithm). Therefore, the ratio of work among those Active agents does not exceed 8.
Between Active and Inactive agents, the difference of work is decreasing until the time when Inactive agents get less work than the Active, and the Inactive become Active themselves. Until that happens the difference of work between Active and Inactive is . After that, the ratio 8 is also maintained between Active and Inactive agents. Even if all agents get Active, then they have a ratio 4 among them when they start scanning and will maintain a ratio 8 upon returning if one becomes Inactive due to the completion of their area. Therefore, in all cases, if multiple agents start scanning either the work difference is bounded by or a ratio 8 between the works of the agents is maintained. □
Lemma 12. If before the scan of room , , the work of any two agents g and h have a difference in their ratio of work , then at the end of the room scan of then ratio 8 is maintained or regress to difference of .
Proof. Similar to the proof of Lemma 11, at the beginning only one agent scans , say agent g, which gains at most work. Any other agent h must have work . If , then, the ratio 8 between these two agents is not preserved, but there is a maximum difference of in their works.
If more than one agent becomes Active for scanning, then similar to the proof of Lemma 11, the work ratio of 8 is maintained or the difference of works is bounded by . □
Lemma 13. At the end of scanning room for any two agents it holds that either or .
Proof. We will use induction. For the base case, , the claim holds immediately as initially no agent has any work so all are within and ratio 8. Suppose the claim holds up to the scanning of room . By induction hypothesis, for any two agents g and h, or .
If , then from Lemma 11, at the end of the scanning of the difference of the works between two agents is either bounded or the ratio of their works is at most 8. Similarly, if , then from Lemma 12, the work difference is bounded by or the ratio of their works is at most 8.
Therefore, in all cases it holds or , as needed. □
Lemma 14 (Room Work).
Upon the completion of each room the total work done up to that point is .
Proof. From above, , and from Lemma 9, the work done in a room is , more specifically at most . The sum of work for all rooms becomes at most which is . □
Lemma 15. Each agent performs work when .
Proof. From Lemma 14 the total work from all the agents combined is , say for some constant . Therefore, some agent has performed work at most . From Lemma 13, for any two agents g and h we have, or . Suppose that g has the maximum total work, and h has the minimum total work, among all k agents.
If , then agent has g has no more work than . If , then agent g has no more work than . Hence, in any case each agent’s work is . □
To perform analysis of the time complexity of room scan, we examine the total time given the orthogonal area contains no holes. (Logarithms are base 2.)
Lemma 16 (Room Time).
Assuming no holes, upon the completion of each room the maximum total time up to that point is .
Proof. At the start of room scan, we have an initial swapping of work until every agent reach work, creating a total time of at most for each agent to swap to be Active. After this point, at the beginning of each room, as we perform slow start, the agents share work doubling the number of Active agents each time steps taking a total of time for all agents to become Active. As there are no holes, the algorithm generates rectangular areas initially and all agents get an equal portion of the area. Now that all agents are Active, and given that the work performed in a room is (Lemma 9) we subtract the amount of work that has been performed during the sharing process and divide by the number of Active agents, as one agent is Leader, achieving the maximum total time for room completion . □
5.3. Combination of Work
In this section, we will combine Lemmas 4 and 14 to get the total work for all movements in the algorithm. We will also combine the total amount of work completed by an agent to get the total work done by each agent using Lemmas 6 and 15.
For the combination of these Lemmas and to use Lemma 15 for work of agents in room scan we assume . As is along a single dimension and is along two dimensions, . From Lemma 4, we get that the total work during the perimeter is , and from Lemma 14 we get that the total work during all room scans combined is . Therefore,
Corollary 2. The total work done by all agents at the end of scanning room is .
From Lemma 6 agents perform work and from Lemma 15 each agent performs work . Therefore,
Corollary 3. At the end of scanning room , each agent performs work .
Theorem 2 (Work Balancing).
If , then at the end of scanning room , the total work of all agents is and the work of each agent is .
Proof. Since from Corollary 2 the total work is , if for some constant , then . From Corollary 3, the total work performed by each individual agent is , with the above value of this is . □
5.4. Combination of Time
Given the Lemmas 7 and 16 we will show the total time to complete the exploration.
Corollary 4. The total time to complete exploration at the end of room scan is .
Given this total time to complete the exploration we have certain areas in which the total time is . Any exploration cannot do better than as this is all agent would be actively exploring during the entire exploration. For our exploration, we define a large room i is such that is of order . □
Corollary 5 (Parallel Exploration)
When in an orthogonal area is made up of a majority of large rooms, and the terms P, , and are , then time complexity is of , which is asymptotically optimal.
6. Conclusions
This paper proposes multiple algorithms, to perform exploration and a slow start, for multiple agent to perform parallel exploration with a limited communication range. Through the introduction of unknown holes in the area the room exploration algorithm of Leader with slow start was developed to minimize the cost of returning to the Leader while maintaining near equal work. Through exponential back-off with a reset to communicate with the Leader, communication costs are decreased as well as the cost of returning to communicate. With our algorithms, we achieve an overall performance of agent work in asymptotically optimal time .
Our future work is to implement the algorithms on several agents. We also plan to explore the algorithm with agent failure. Lastly, it is our goal to remove the orthogonal region and rectangular hole constraints to develop algorithms that enable the agents to explore concave polygons.