Enhancing Cyber-Physical Resiliency of Microgrid Control under Denial-of-Service Attack with Digital Twins
Abstract
1. Introduction
2. Cyber-Physical Power System and Cyber-Attacks
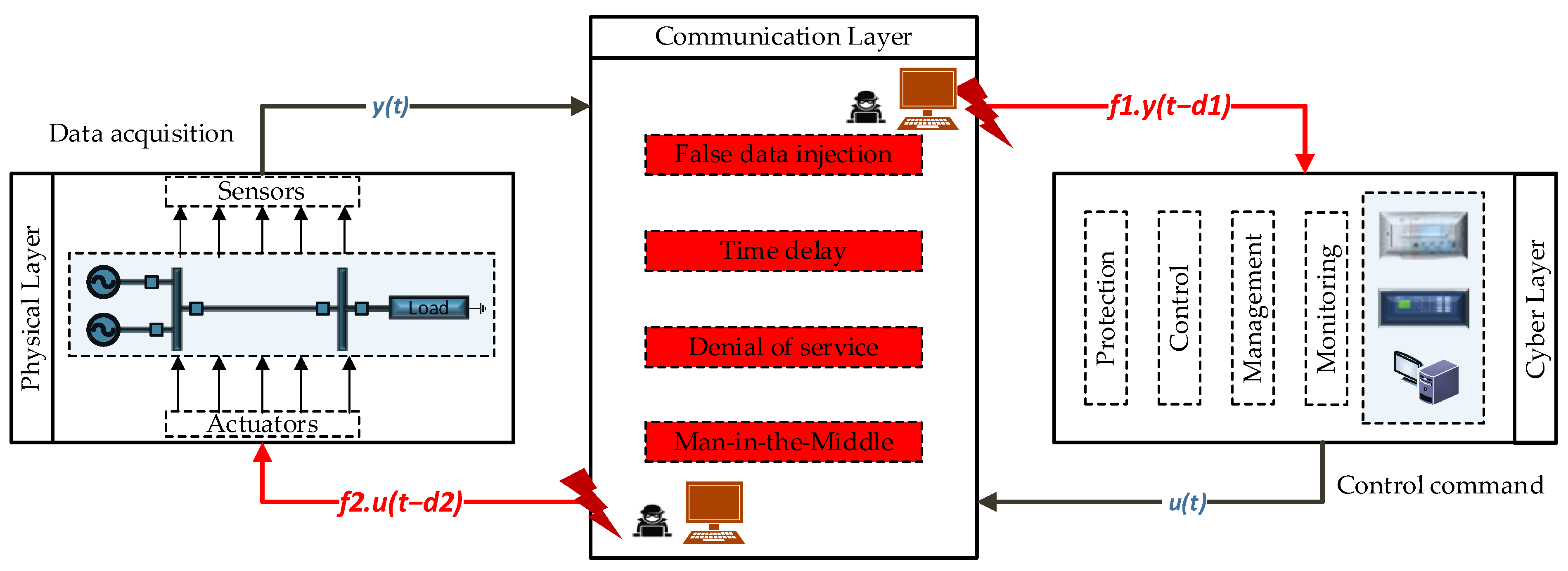
2.1. Cyber-Physical System (CPS) Layers and Attack Modeling
2.2. Denial-of-Service Attack in Microgrids
3. Background of Digital Twin Technology and Applications in Smart Grid
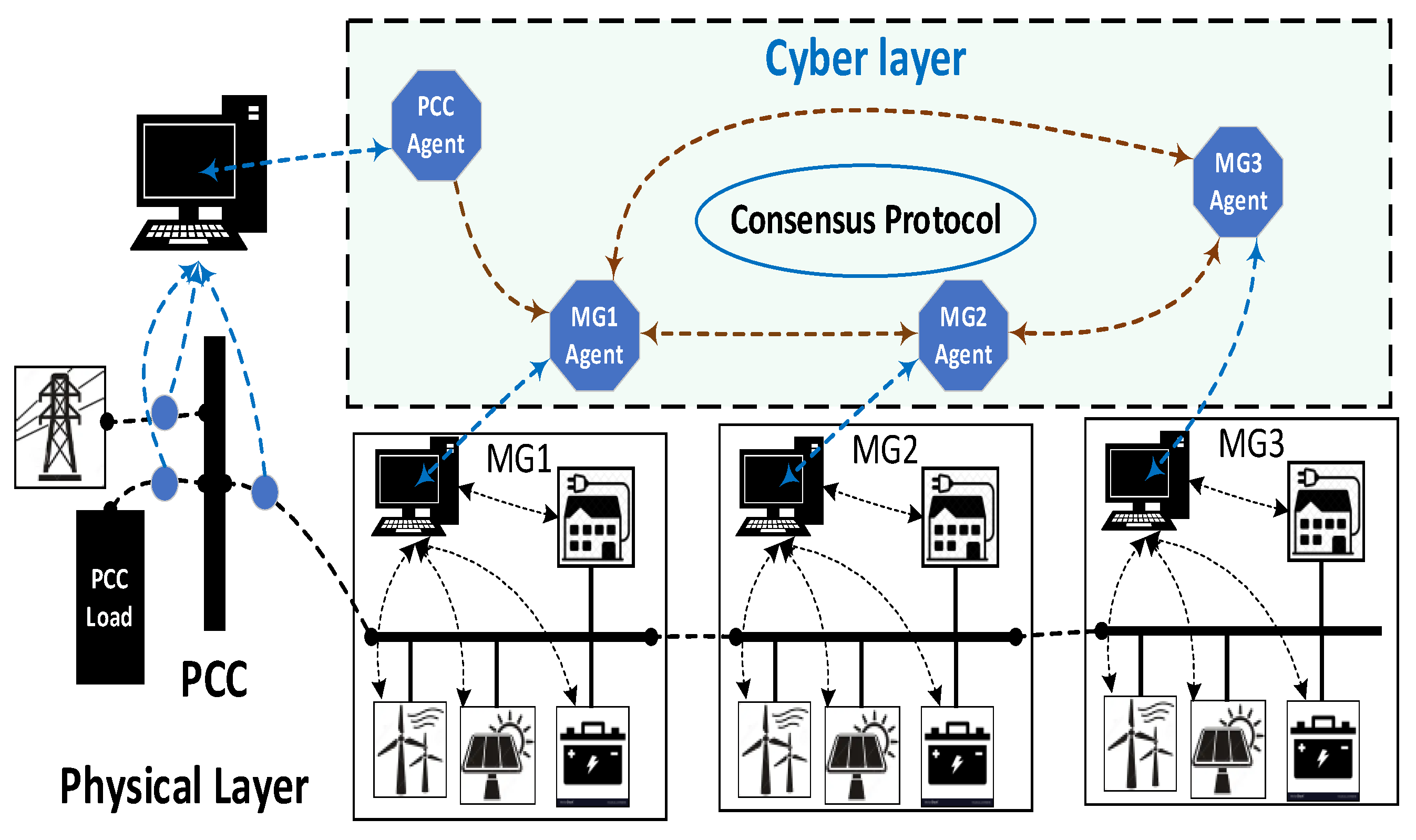
4. Proposed Multi-MGs with Multi-Agents Based Control Architecture
4.1. Physical Layer Modeling
4.2. Communication Layer
4.3. Cyber Layer
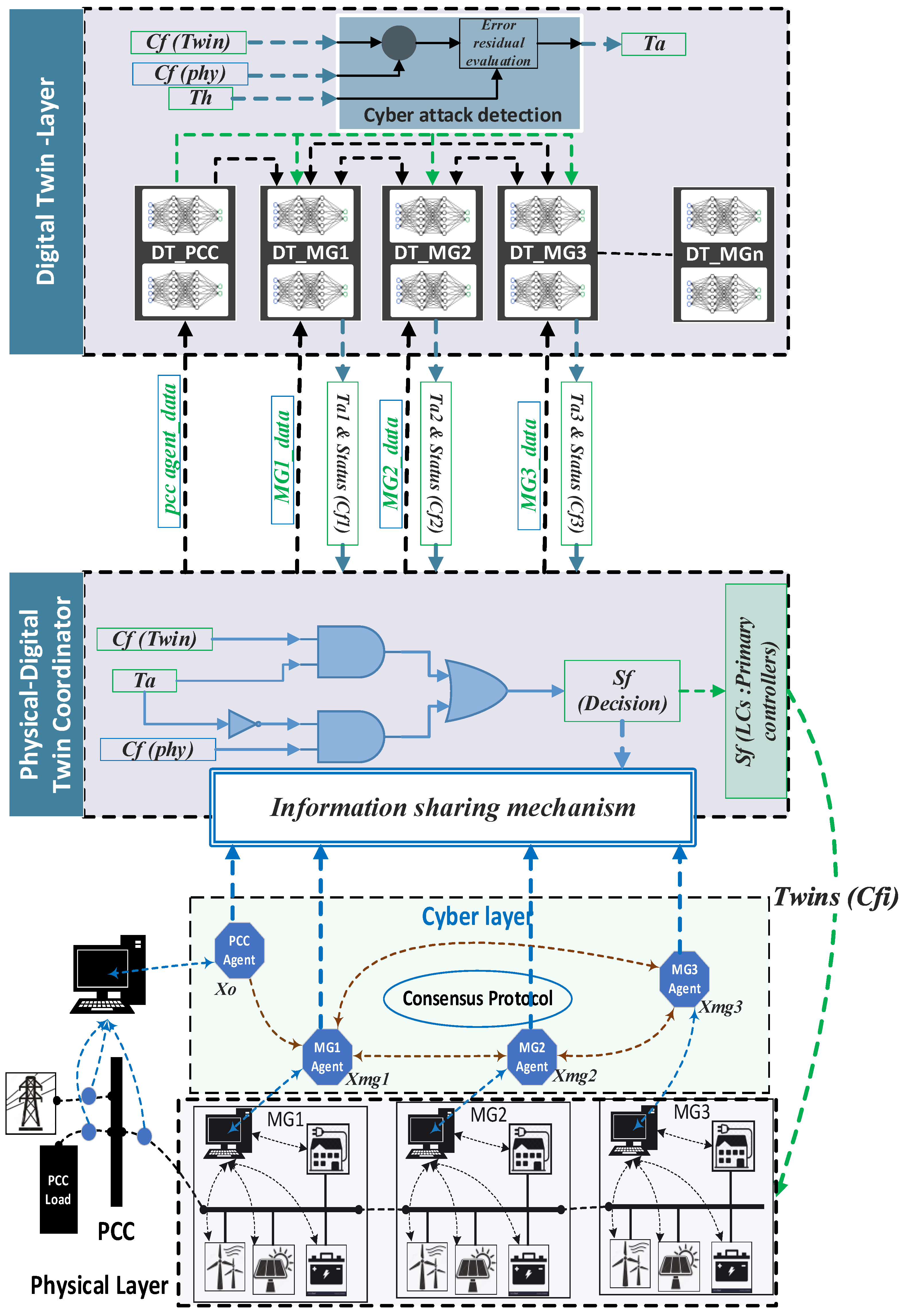
5. Digital Twin-Based Attack Detection and Mitigation
5.1. Black-Box Model of Microgrids Based on LSTM
5.2. Data-Driven Digital Twin Model of Microgrids
5.3. Training and Learning
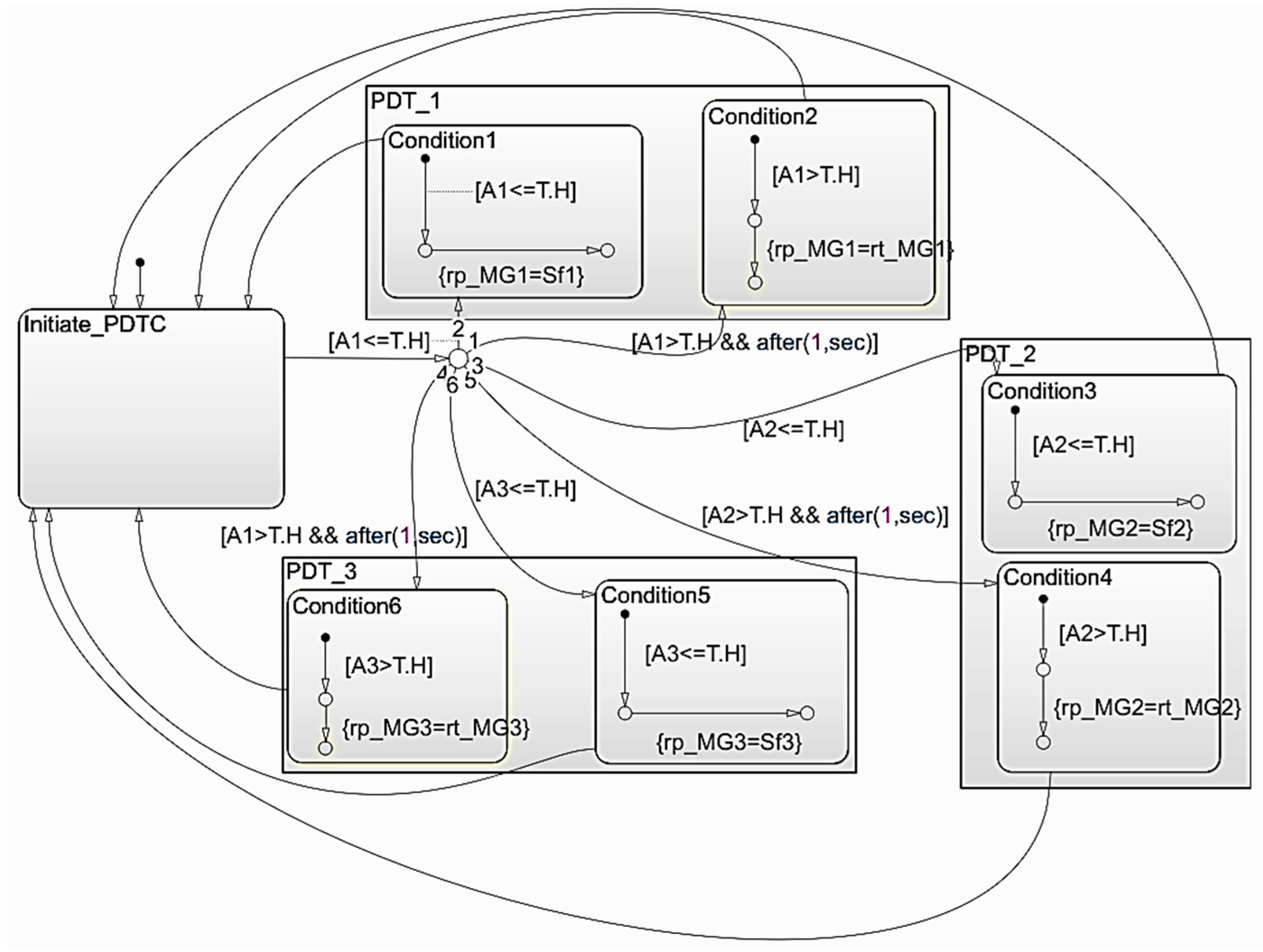
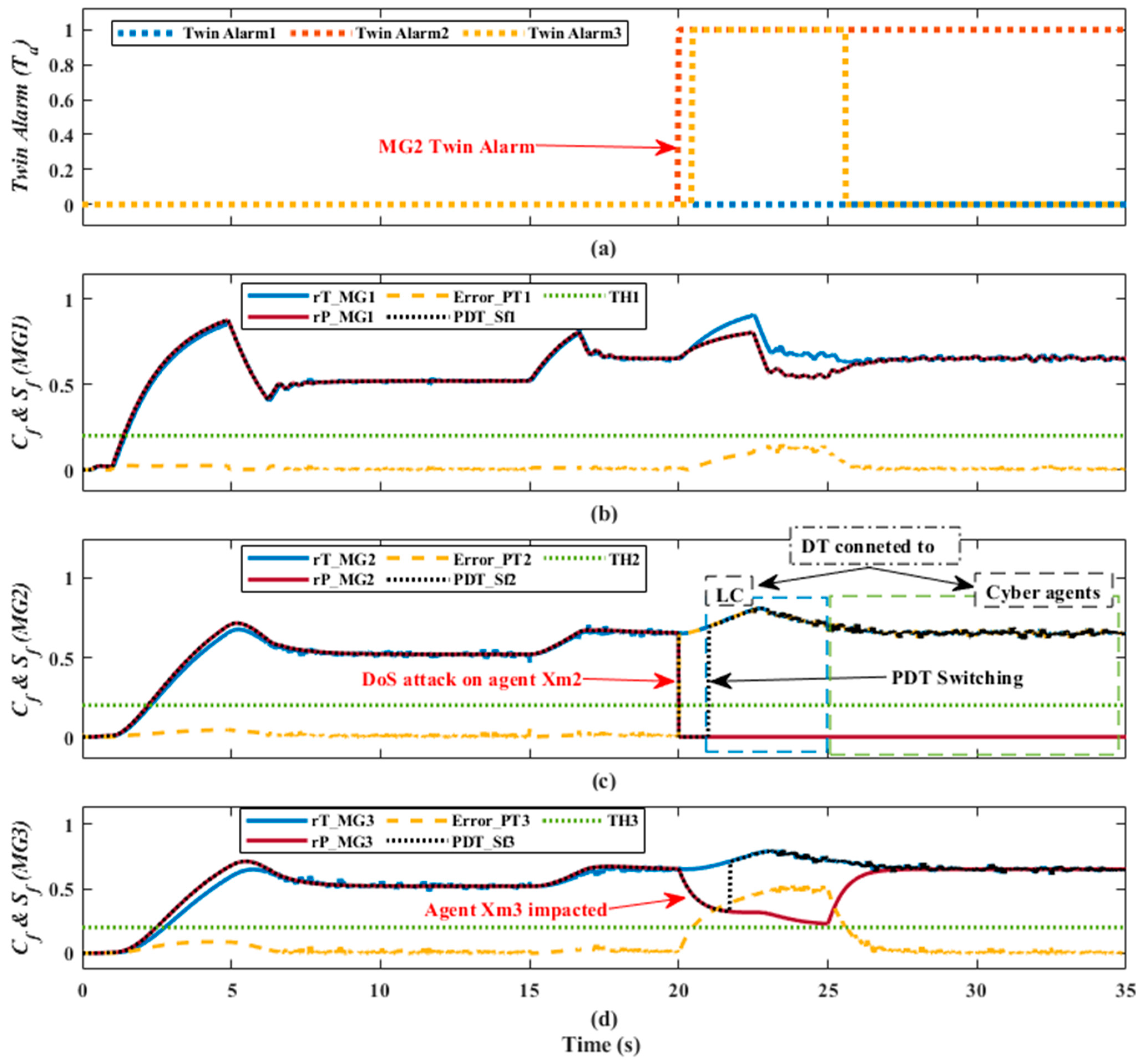
5.4. Physical–Digital Twin Coordinator for Attack Mitigation
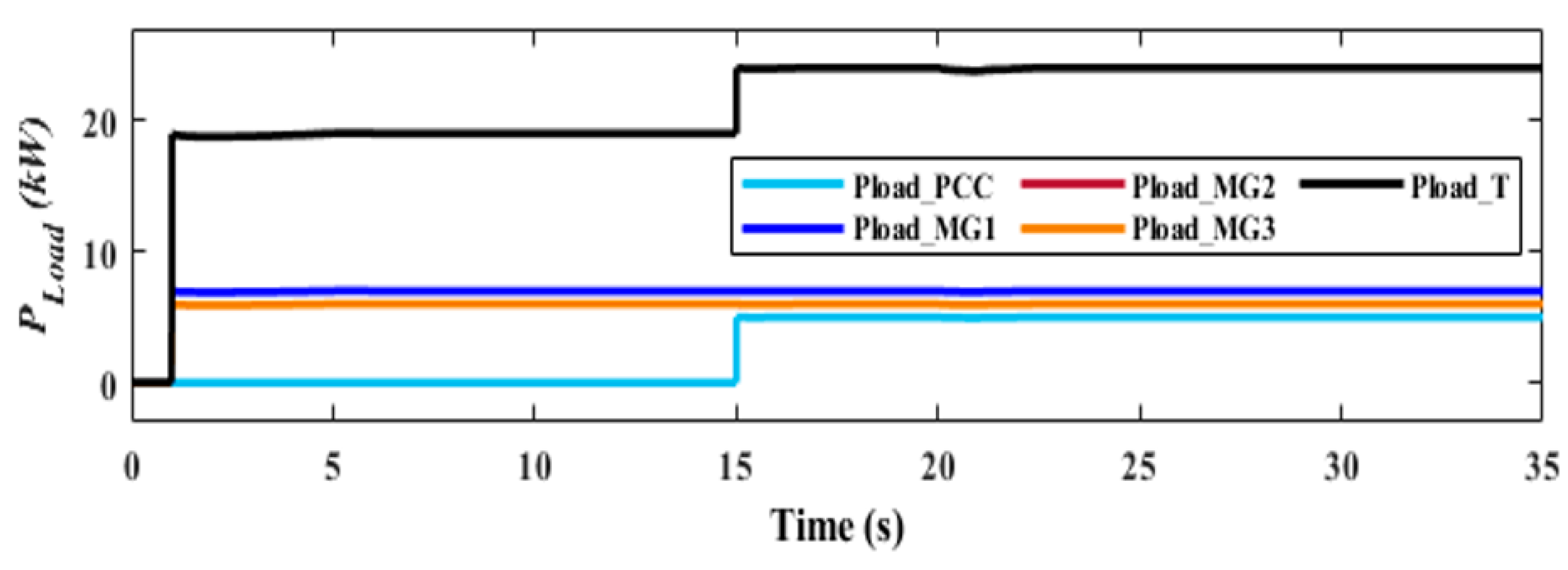
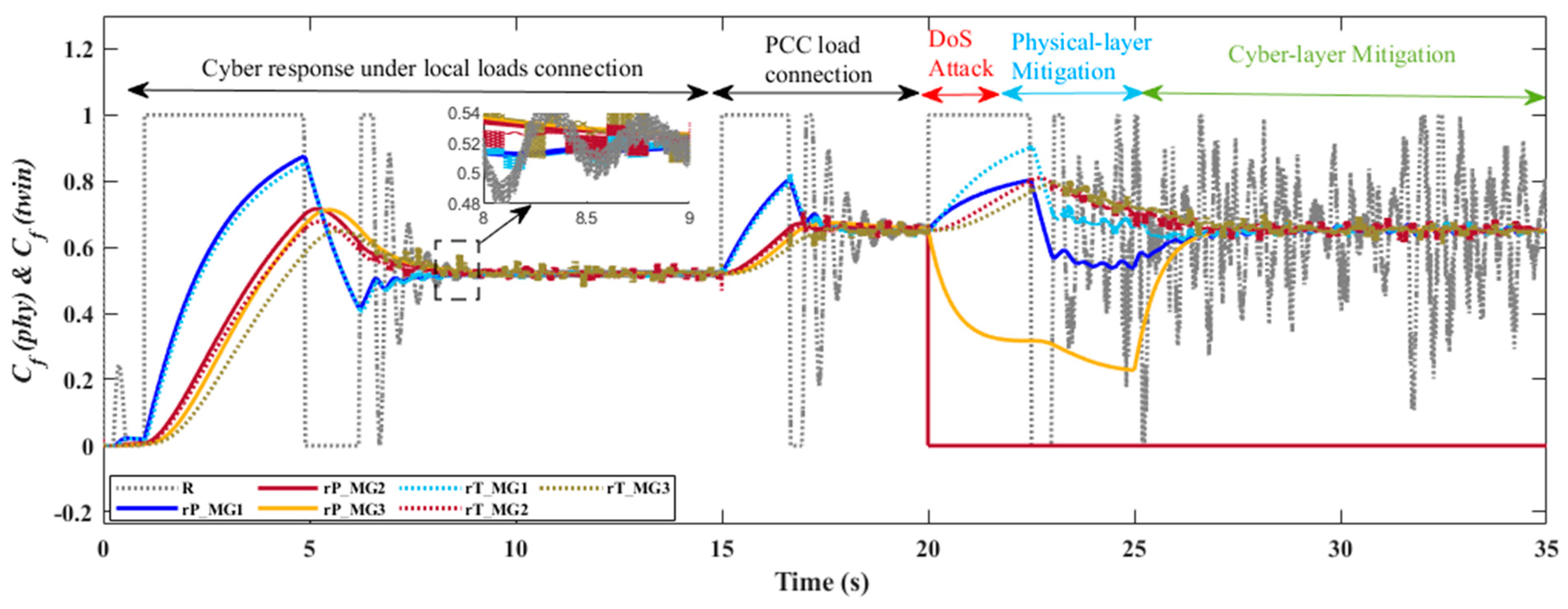
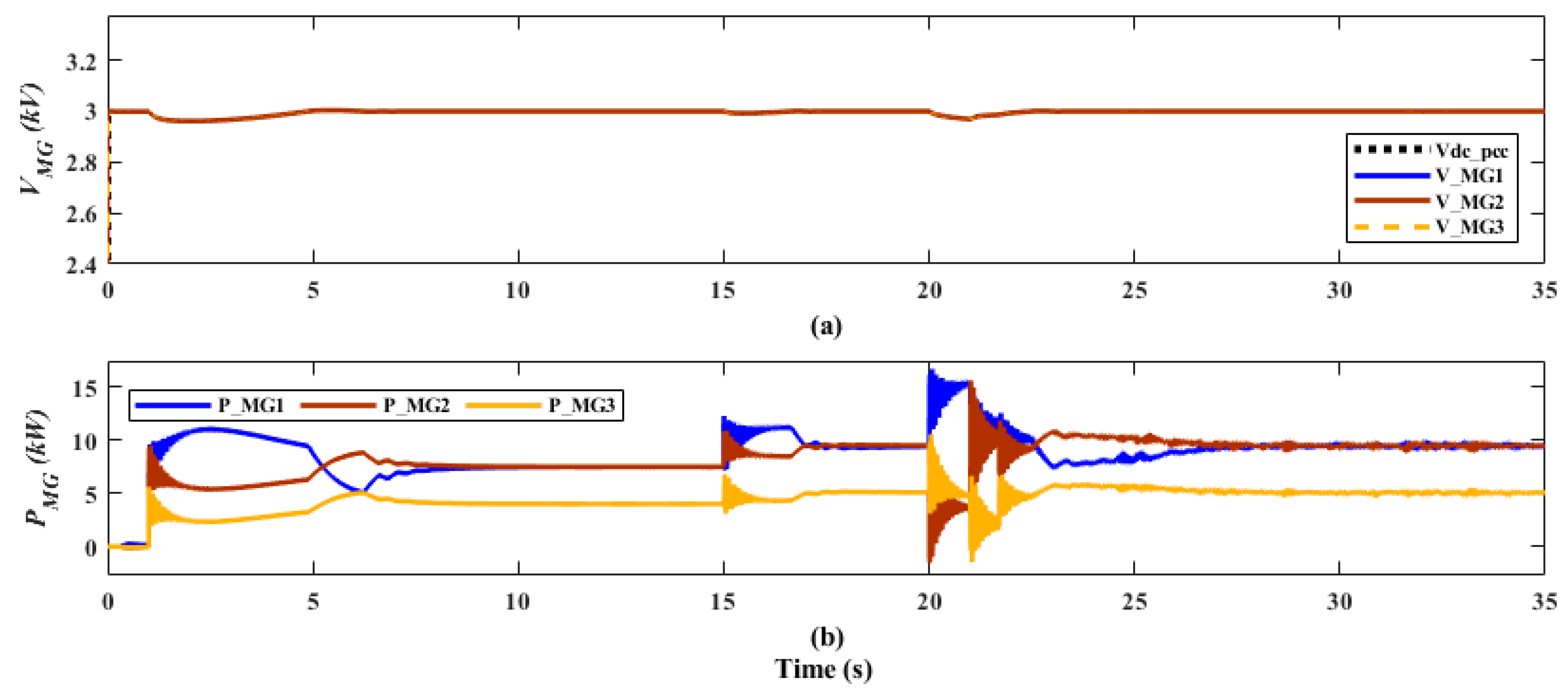
6. Simulation of the Proposed System Under Normal Operation and DoS Attack
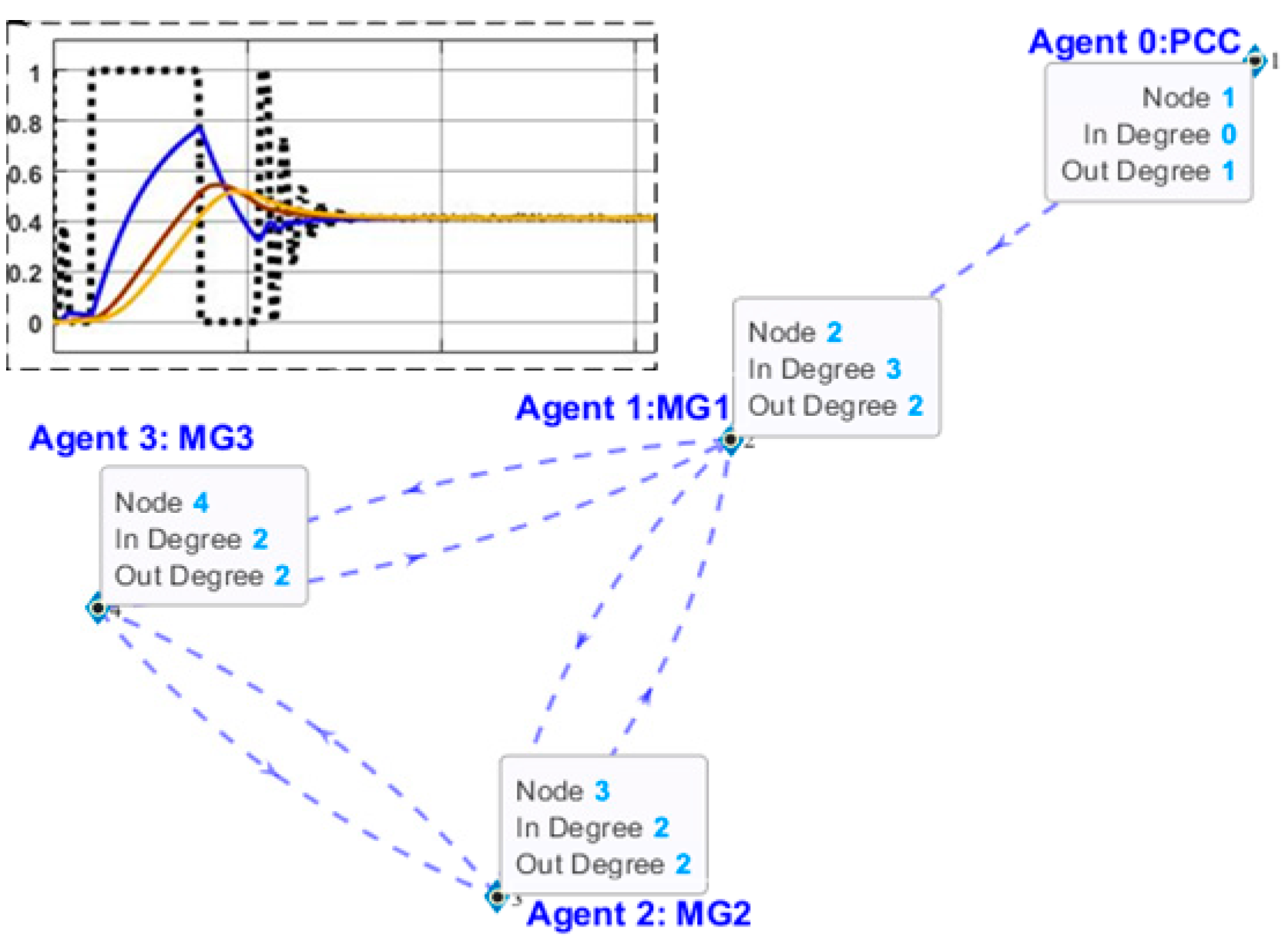
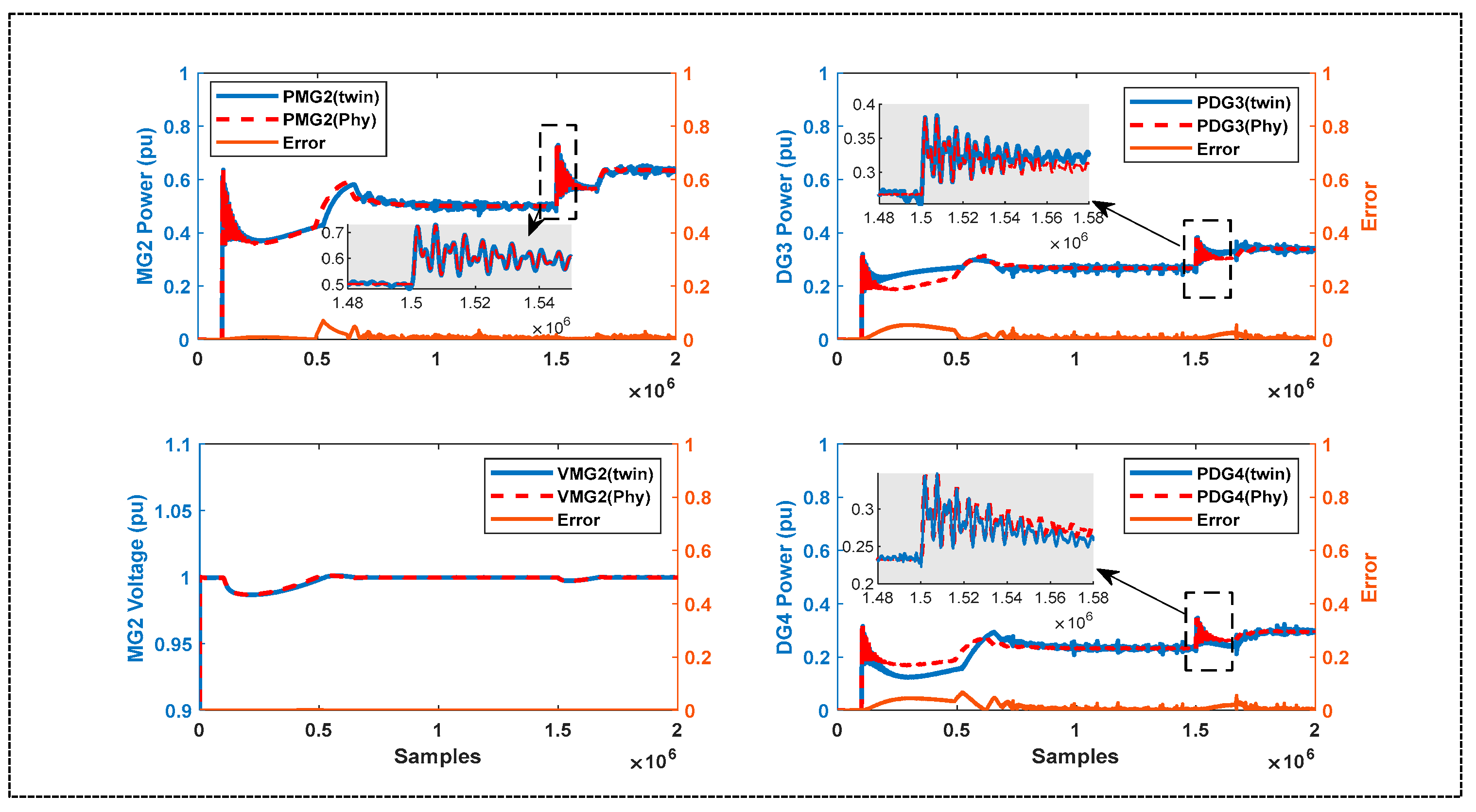
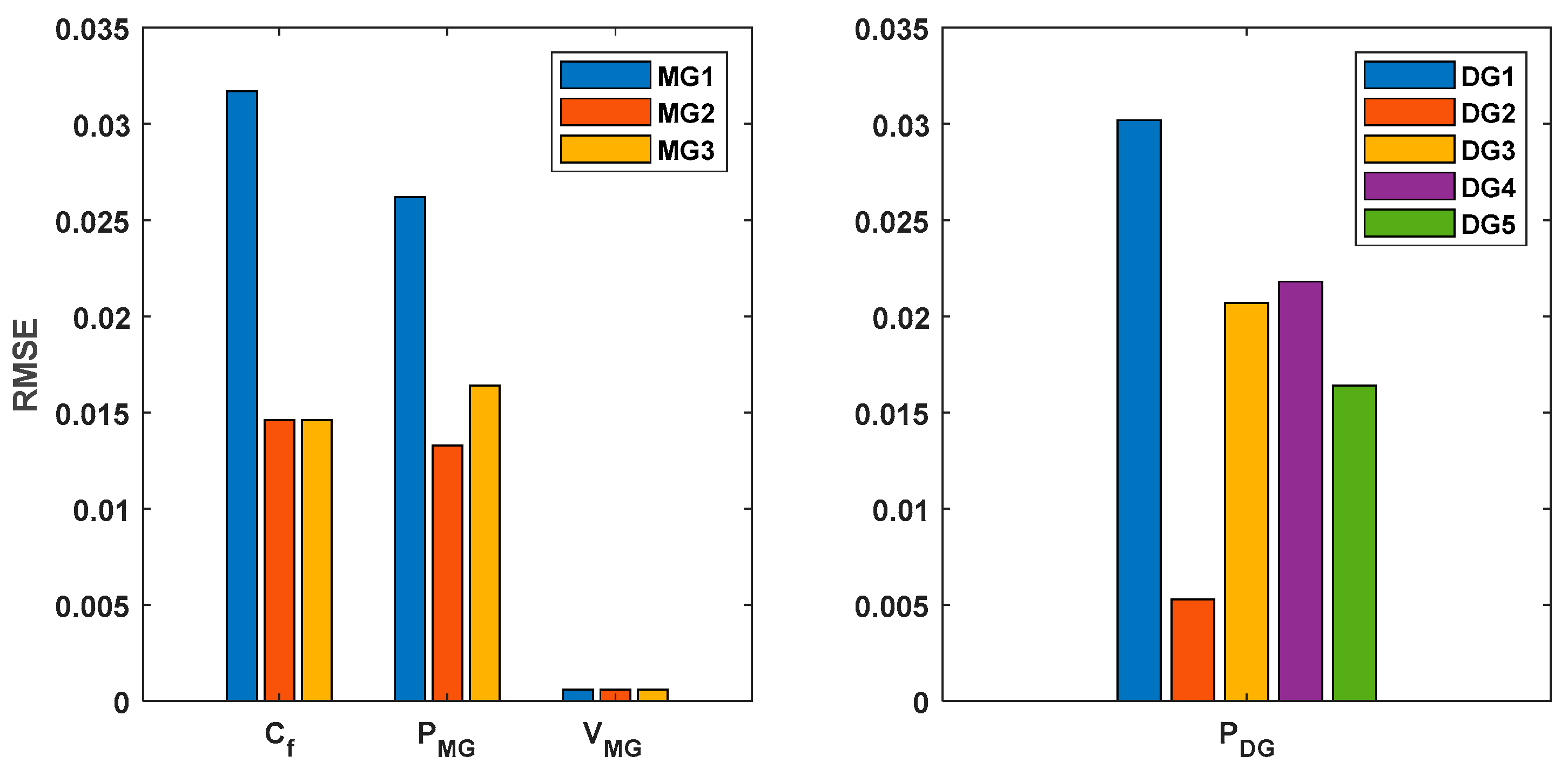
6.1. Twin Models Performance Results
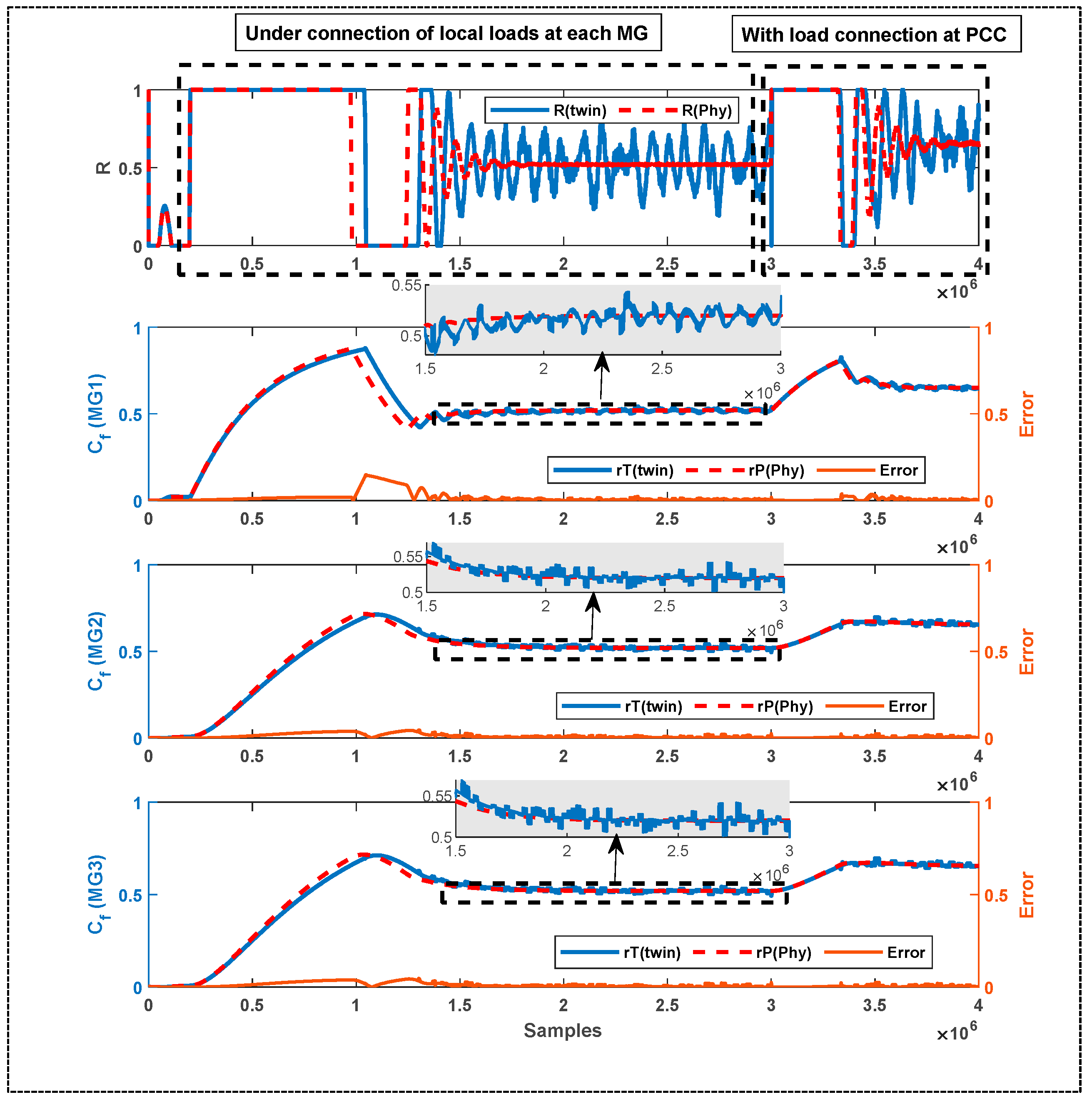
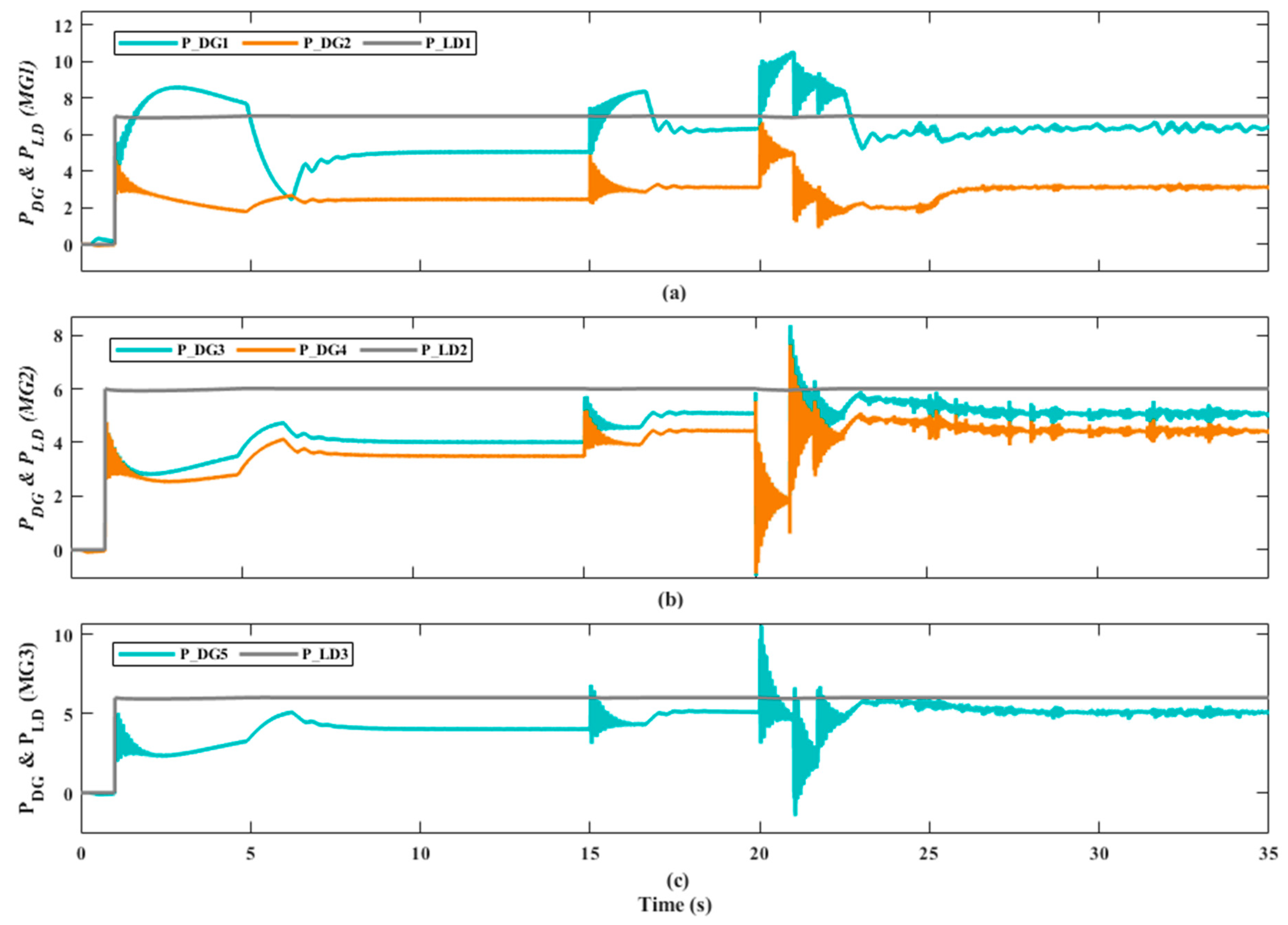
6.2. Results and Evaluation of the Proposed DT Response under DoS Attack
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in power grids: Challenges and opportunities. Sensors 2021, 21, 6225. [Google Scholar] [CrossRef] [PubMed]
- Zhou, B.; Zou, J.; Chung, C.Y.; Wang, H.; Liu, N.; Voropai, N.; Xu, D. Multi-microgrid energy management systems: Architecture, communication, and scheduling strategies. J. Mod. Power Syst. Clean Energy 2021, 9, 463–476. [Google Scholar] [CrossRef]
- Jafari, M.; Rahman, M.A.; Paudyal, S. Optimal false data injection attacks against power system frequency stability. IEEE Trans. Smart Grid 2023, 14, 1276–1288. [Google Scholar] [CrossRef]
- Choi, I.-S.; Hong, J.; Kim, T.-W. Multi-agent based cyber attack detection and mitigation for distribution automation system. IEEE Access 2020, 8, 183495–183504. [Google Scholar] [CrossRef]
- Ashok, A.; Govindarasu, M.; Wang, J. Cyber-physical attack-resilient wide-area monitoring, protection, and control for the power grid. Proc. IEEE 2017, 105, 1389–1407. [Google Scholar] [CrossRef]
- Fuller, A.; Fan, Z.; Day, C.; Barlow, C. Digital twin: Enabling technologies, challenges and open research. IEEE Access 2020, 8, 108952–108971. [Google Scholar] [CrossRef]
- Tao, F.; Qi, Q.; Wang, L.; Nee, A. Digital twins and cyber-physical systems toward smart manufacturing and industry 4.0: Correlation and comparison. Engineering 2019, 5, 653–661. [Google Scholar] [CrossRef]
- Qi, Q.; Tao, F.; Hu, T.; Anwer, N.; Liu, A.; Wei, Y.; Wang, L.; Nee, A. Enabling technologies and tools for digital twin. J. Manuf. Syst. 2021, 58, 3–21. [Google Scholar] [CrossRef]
- Guo, J.; Lv, Z. Application of digital twins in multiple fields. Multimed. Tools Appl. 2022, 81, 26941–26967. [Google Scholar] [CrossRef]
- Abdelrahman, M.S.; Kharchouf, I.; Nguyen, T.L.; Mohammed, O.A. A Hybrid physical co-simulation smart grid testbed for testing and impact analysis of cyber-attacks on power systems: Framework and attack scenarios. Energies 2023, 16, 7771. [Google Scholar] [CrossRef]
- Cheng, Z.; Yue, D.; Hu, S.; Huang, C.; Dou, C.; Chen, L. Resilient load frequency control design: Dos attacks against additional control loop. Int. J. Electr. Power Energy Syst. 2020, 115, 105496. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, P.; Ma, L. Denial of service attack and defense method on load frequency control system. J. Frankl. Inst. 2019, 356, 8625–8645. [Google Scholar] [CrossRef]
- Liu, Y.; Peng, Y.; Wang, B.; Yao, S.; Liu, Z. Review on cyber-physical systems. IEEE/CAA J. Autom. Sin. 2017, 4, 27–40. [Google Scholar] [CrossRef]
- Kim, K.-D.; Kumar, P.R. Cyber–physical systems: A perspective at the centennial. Proc. IEEE 2012, 100, 1287–1308. [Google Scholar] [CrossRef]
- Glaessgen, E.; Stargel, D. The digital twin paradigm for future NASA and us air force vehicles. In Proceedings of the 53rd AI-AA/ASME/ASCE/AHS/ASC Structures, Structural Dynamics and Materials Conference 20th AIAA/ASME/AHS Adaptive Structures Conference 14th AIAA, Honolulu, HI, USA, 23–26 April 2012; p. 1818. [Google Scholar]
- Grieves, M. Digital Twin: Manufacturing Excellence through Virtual Factory Replication; A White Paper; Michael Grieves, LLC: Melbourne, FL, USA, 2014. [Google Scholar]
- Moutis, P.; Alizadeh-Mousavi, O. Digital Twin of Distribution Power Transformer for Real-Time Monitoring of Medium Volt-age From Low Voltage Measurements. IEEE Trans. Power Deliv. 2021, 36, 1952–1963. [Google Scholar] [CrossRef]
- Mukherjee, V.; Martinovski, T.; Szucs, A.; Westerlund, J.; Belahcen, A. Improved Analytical Model of Induction Machine for Digital Twin Application. In Proceedings of the 2020 International Conference on Electrical Machines (ICEM), Gothenburg, Sweden, 23–26 August 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Nguyen-Huu, T.A.; Tran, T.T.; Tran, M.Q.; Nguyen, P.H.; Slootweg, J. Operation Orchestration of Local Energy Communi-ties through Digital Twin: A Review on suitable Modeling and Simulation Approaches. In Proceedings of the 2022 IEEE 7th International Energy Conference (ENERGYCON), Riga, Latvia, 9–12 May 2022; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar]
- Yuan, J.; Sun, M.; Xie, J.; Su, D.; Guo, J.; Guo, Y.; Wang, S. A Multi-agent System Construction Method for Substation Digital Twin. In Proceedings of the 2022 2nd International Conference on Electrical Engineering and Mechatronics Technology (ICEEMT), Hangzhou, China, 1–3 July 2022; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar]
- Bazmohammadi, N.; Madary, A.; Vasquez, J.C.; Mohammadi, H.B.; Khan, B.; Wu, Y.; Guerrero, J.M. Microgrid digital twins: Concepts, applications, and future trends. IEEE Access 2022, 10, 2284–2302. [Google Scholar] [CrossRef]
- Madni, A.M.; Madni, C.C.; Lucero, S.D. Leveraging Digital Twin Technology in Model-Based Systems Engineering. Systems 2019, 7, 7. [Google Scholar] [CrossRef]
- Jiang, H.; Tjandra, R.; Soh, C.B.; Cao, S.; Soh, D.C.L.; Tan, K.T.; Tseng, K.J.; Krishnan, S.B. Digital Twin of Microgrid for Pre-dictive Power Control to Buildings. Sustainability 2024, 16, 482. [Google Scholar] [CrossRef]
- Milton, M.; De La, C.O.; Ginn, H.L.; Benigni, A. Controller-Embeddable Probabilistic Real-Time DTs for Power Electronic Converter Diagnostics. IEEE Trans. Power Electron. 2020, 35, 9850–9864. [Google Scholar] [CrossRef]
- Saad, A.; Faddel, S.; Youssef, T.; Mohammed, O.A. On the implementation of IoT-based digital twin for networked mi-crogrids resiliency against cyber attacks. IEEE Trans. Smart Grid. 2020, 11, 5138–5150. [Google Scholar] [CrossRef]
- Liu, X.-K.; Wang, S.-Q.; Chi, M.; Liu, Z.-W.; Wang, Y.-W. Resilient secondary control and stability analysis for dc microgrids under mixed cyber attacks. IEEE Trans. Ind. Electron. 2024, 71, 1938–1947. [Google Scholar] [CrossRef]
- Fan, B.; Guo, S.; Peng, J.; Yang, Q.; Liu, W.; Liu, L. A Consensus-based algorithm for power sharing and voltage regulation in DC microgrids. IEEE Trans. Ind. Inform. 2020, 16, 3987–3996. [Google Scholar] [CrossRef]
- Yohanandhan, R.V.; Elavarasan, R.M.; Manoharan, P.; Mihet-Popa, L. Cyber-physical power system (CPPS): A review on modeling, simulation, and analysis with cyber security applications. IEEE Access 2020, 8, 151019–151064. [Google Scholar] [CrossRef]
- Mohiuddin, S.M.; Qi, J. Attack resilient distributed control for ac microgrids with distributed robust state estimation. In Proceedings of the 2021 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 2–5 February 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Shafiee-Rad, M.; Sadabadi, M.S.; Shafiee, Q.; Jahed-Motlagh, M.R. Robust decentralized voltage control for uncertain DC microgrids. Int. J. Electr. Power Energy Syst. 2021, 125, 106468. [Google Scholar] [CrossRef]
- Wang, C.; Duan, J.; Fan, B.; Yang, Q.; Liu, W. Decentralized high-performance control of dc microgrids. IEEE Trans. Smart Grid 2019, 10, 3355–3363. [Google Scholar] [CrossRef]
- Meng, L.; Dragicevic, T.; Roldan-Perez, J.; Vasquez, J.C.; Guerrero, J.M. Modeling and sensitivity study of consensus algorithm-based distributed hierarchical control for dc microgrids. IEEE Trans. Smart Grid 2016, 7, 1504–1515. [Google Scholar] [CrossRef]
- Kharchouf, I.; Mohammed, O.A. Controller hardware-in-the-loop testbed of a distributed consensus multi-agent system control under deception and disruption cyber-attacks. Energies 2024, 17, 1669. [Google Scholar] [CrossRef]
- Saad, A.A.; Faddel, S.; Mohammed, O. A secured distributed control system for future interconnected smart grids. Appl. Energy 2019, 243, 57–70. [Google Scholar] [CrossRef]
- Saad, A.; Faddel, S.; Mohammed, O. IoT-based digital twin for energy cyber-physical systems: Design and implementation. Energies 2020, 13, 4762. [Google Scholar] [CrossRef]
- Wu, Z.; Li, J. A framework of dynamic data driven digital twin for complex engineering products: The example of air-craft engine health management. Procedia Manuf. 2021, 55, 139–146. [Google Scholar] [CrossRef]
- He, J.; Xiang, T.; Wang, Y.; Ruan, H.; Zhang, X. A Reinforcement learning handover parameter adaptation method based on LSTM-aided digital twin for UDN. Sensors 2023, 23, 2191. [Google Scholar] [CrossRef] [PubMed]
- Hussein, H.M.; Esoofally, M.; Donekal, A.; Rafin, S.M.S.H.; Mohammed, O. Comparative study-based data-driven models for lithium-ion battery state-of-charge estimation. Batteries 2024, 10, 89. [Google Scholar] [CrossRef]
- Jafari, M.; Kavousi-Fard, A.; Chen, T.; Karimi, M. A Review on digital twin technology in smart grid, transportation system and smart city: Challenges and future. IEEE Access 2023, 11, 17471–17484. [Google Scholar] [CrossRef]






| Parameter | Description | Value |
|---|---|---|
| MG1 Parameters | ||
| Prated (DG1) | DG1 rating | 10 kW |
| Prated (DG2) | DG2 rating | 5 kW |
| P_LD1 | Load power | 7 kW |
| MG2 Parameters | ||
| Prated (DG3) | DG3 rating | 8 kW |
| Prated (DG4) | DG4 rating | 7 kW |
| P_LD2 | Load power | 6 kW |
| MG3 Parameters | ||
| Prated (DG5) | DG5 rating | 8 kW |
| P_LD3 | Load power | 6 kW |
| V | MG voltage | 3 kV |
| Pload (PCC) | PCC load power | 5 kW |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdelrahman, M.S.; Kharchouf, I.; Hussein, H.M.; Esoofally, M.; Mohammed, O.A. Enhancing Cyber-Physical Resiliency of Microgrid Control under Denial-of-Service Attack with Digital Twins. Energies 2024, 17, 3927. https://doi.org/10.3390/en17163927
Abdelrahman MS, Kharchouf I, Hussein HM, Esoofally M, Mohammed OA. Enhancing Cyber-Physical Resiliency of Microgrid Control under Denial-of-Service Attack with Digital Twins. Energies. 2024; 17(16):3927. https://doi.org/10.3390/en17163927
Chicago/Turabian StyleAbdelrahman, Mahmoud S., Ibtissam Kharchouf, Hossam M. Hussein, Mustafa Esoofally, and Osama A. Mohammed. 2024. "Enhancing Cyber-Physical Resiliency of Microgrid Control under Denial-of-Service Attack with Digital Twins" Energies 17, no. 16: 3927. https://doi.org/10.3390/en17163927
APA StyleAbdelrahman, M. S., Kharchouf, I., Hussein, H. M., Esoofally, M., & Mohammed, O. A. (2024). Enhancing Cyber-Physical Resiliency of Microgrid Control under Denial-of-Service Attack with Digital Twins. Energies, 17(16), 3927. https://doi.org/10.3390/en17163927










