RETRACTED: A Kalman Filter-Based Distributed Cyber-Attack Mitigation Strategy for Distributed Generator Units in Meshed DC Microgrids
Abstract
:1. Introduction
- (1)
- This might be the first paper to present a holistic control algorithm to mitigate both the voltage and current FDIAs of DGUs in meshed DC microgrids.
- (2)
- This might be the first paper to use KF as the state estimator to authenticate the voltage and current measurements being used for the hierarchical control loops. This heavily reduces the computational burden as compared to the conventional counterparts with ANN.
- (3)
- A mitigation layer is proposed with FAPI controllers that update their gains automatically with the variations in system parameters.
- (4)
- Both simulation and experimental verificatications are presented of the superior dynamic responses of the proposed distributed control compared to conventional control schemes.
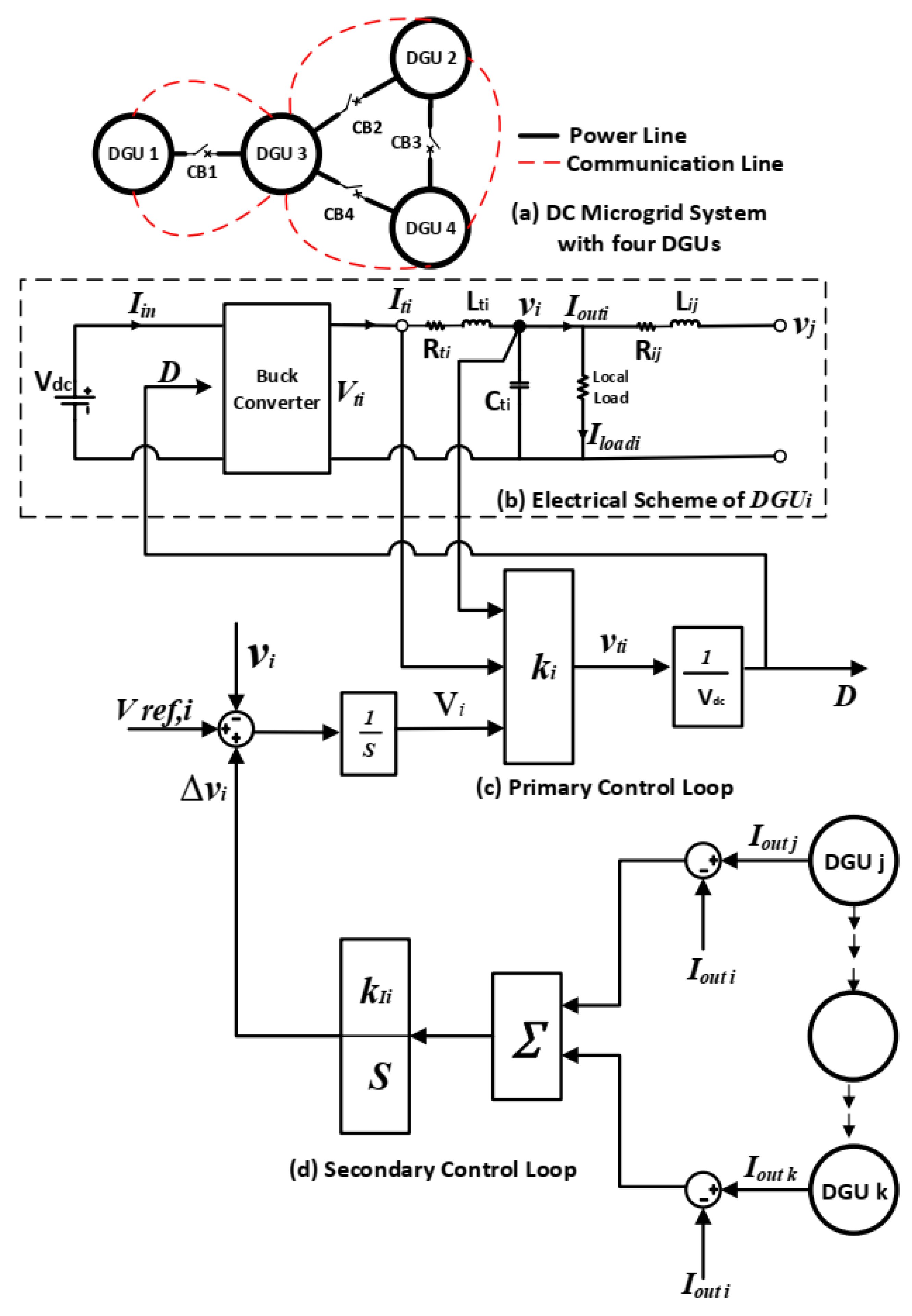
2. System Model and Distributed Control Strategy
2.1. The Primary Controller
2.2. The Secondary Controller
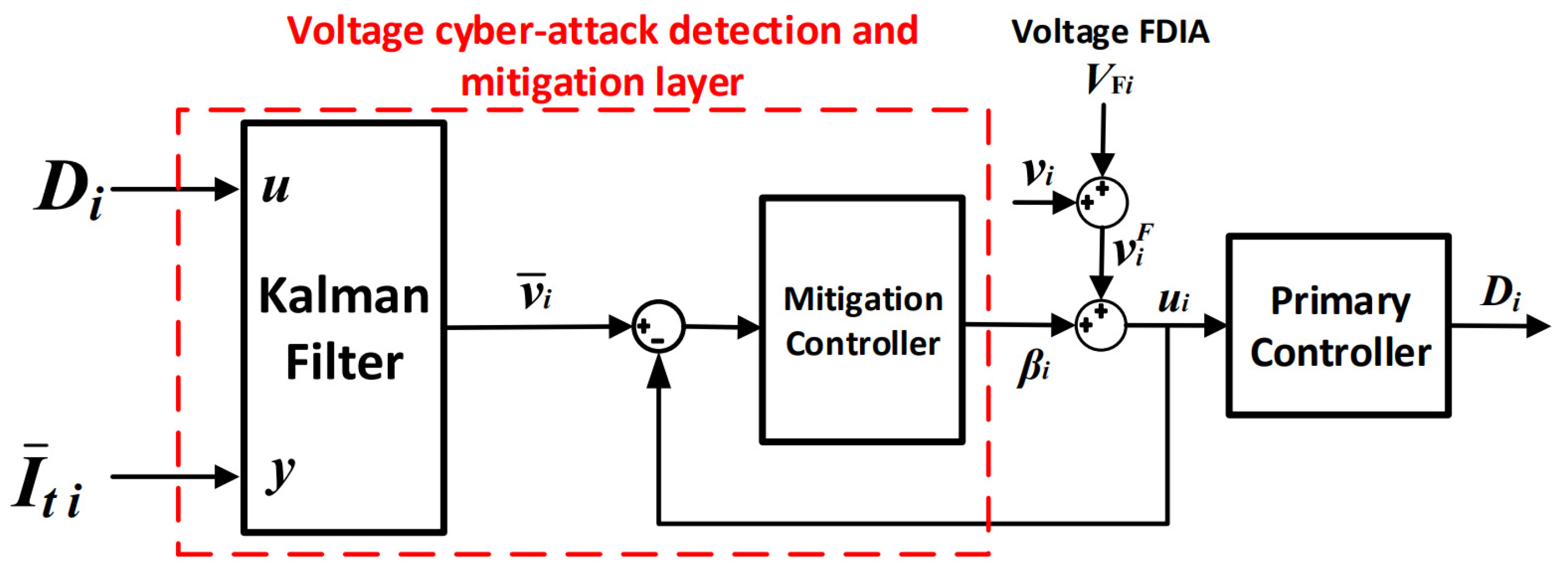
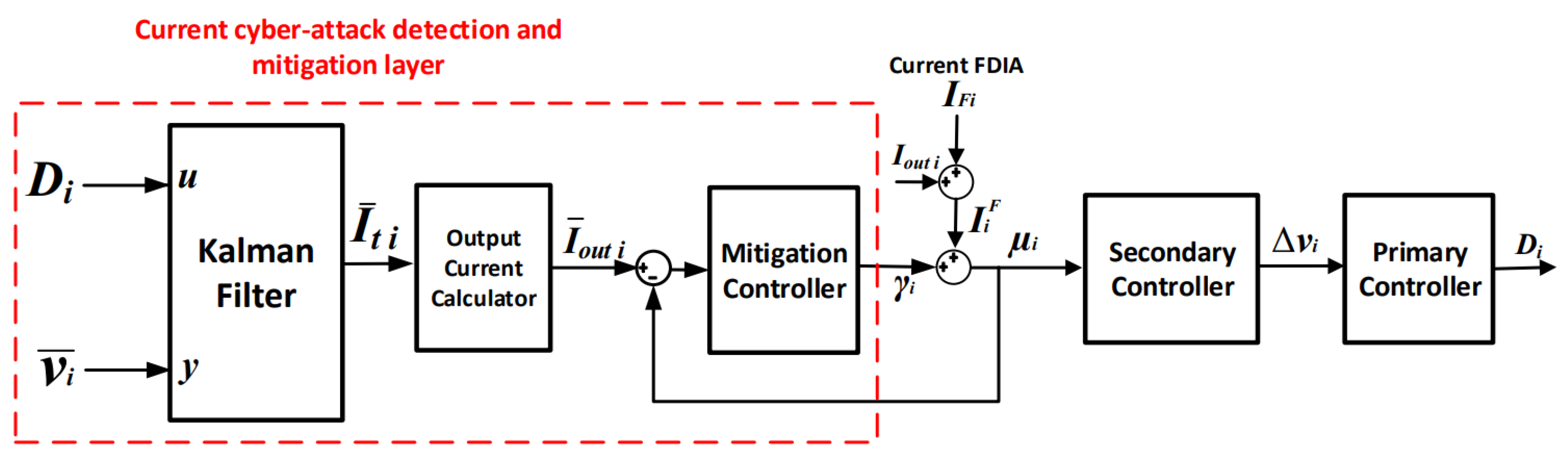
3. Proposed Cyber-Attack-Mitigation Layers
3.1. Kalman Filter
- (1)
- Initialization Step
- (2)
- Prediction Step
- (3)
- Update Step
3.2. Stability of Kalman Filter
3.3. Voltage Cyber-Attack-Mitigation Layer
3.4. Current Cyber-Attack-Mitigation Layer
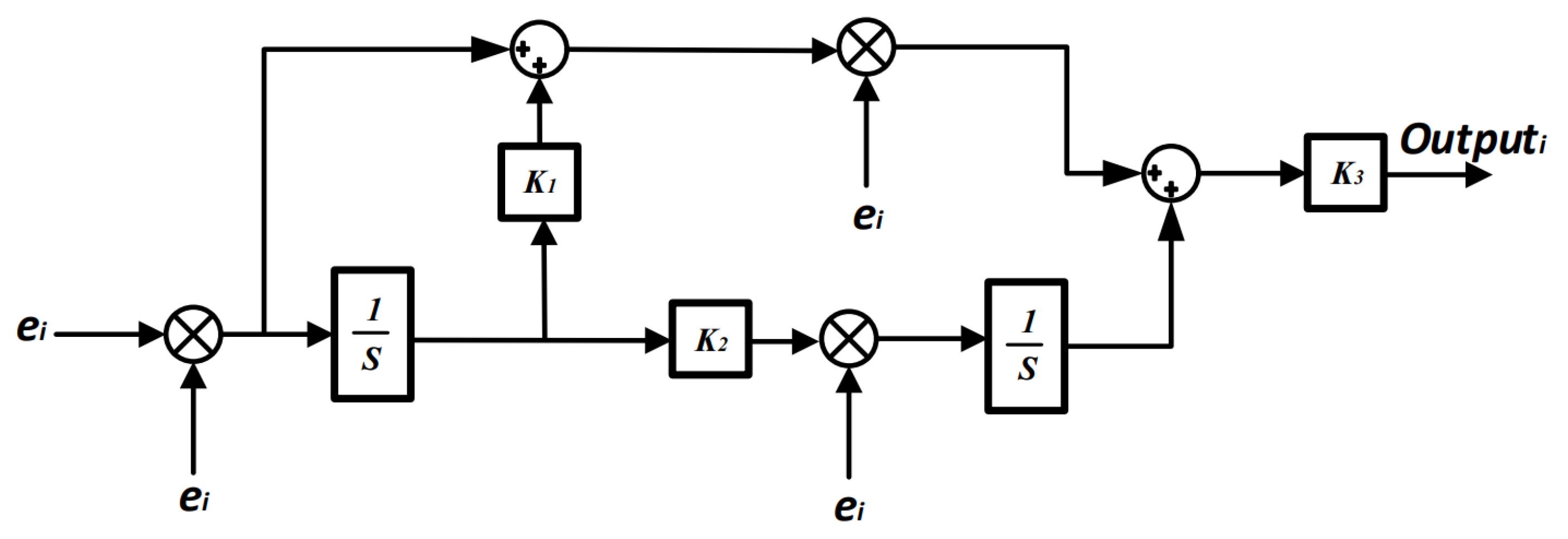
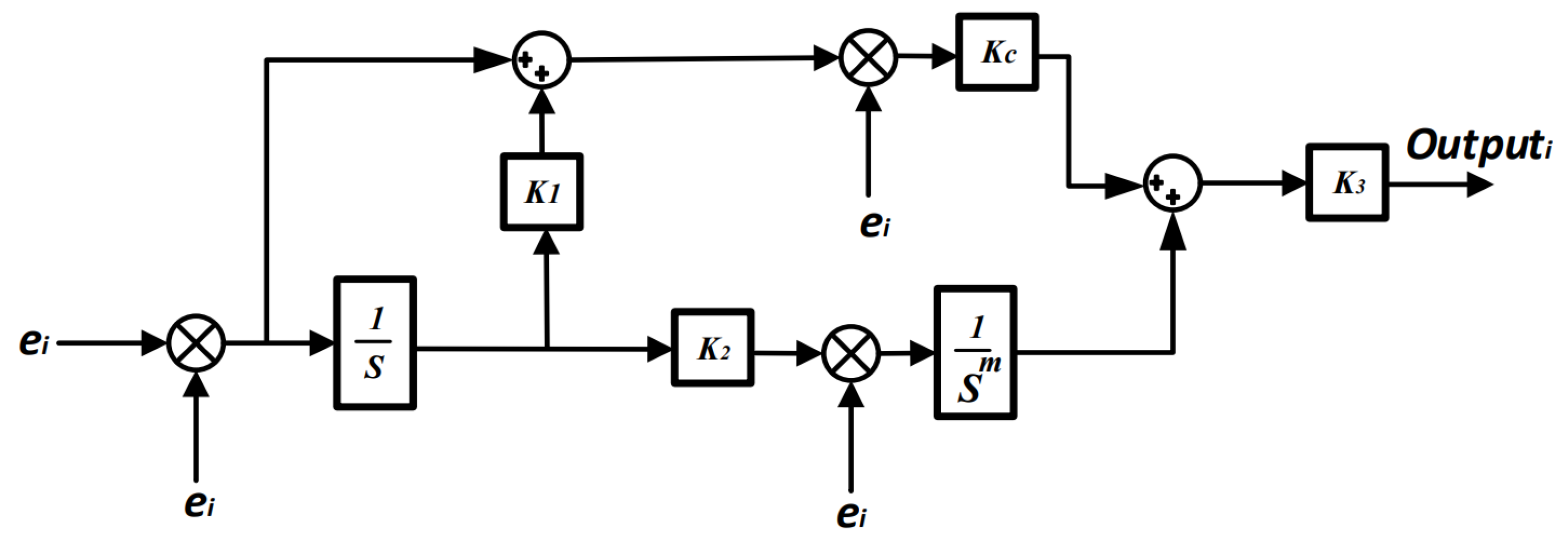
3.5. Fractional Adaptive Controllers for Mitigation Layers
4. Simulation Results
4.1. Case Study 1: Mixed Attacks
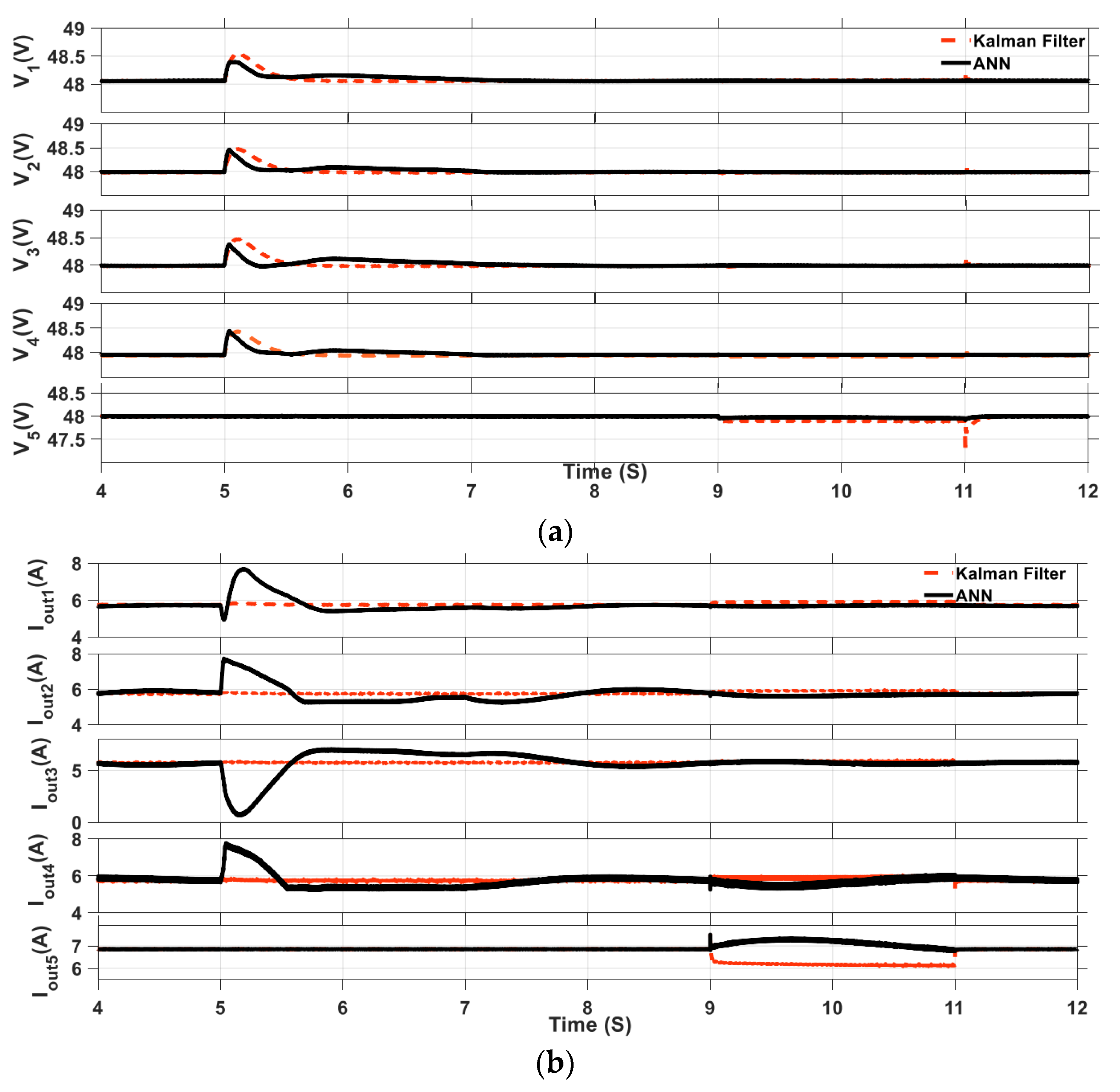
4.2. Case Study 2: Comparison between KF and ANNs
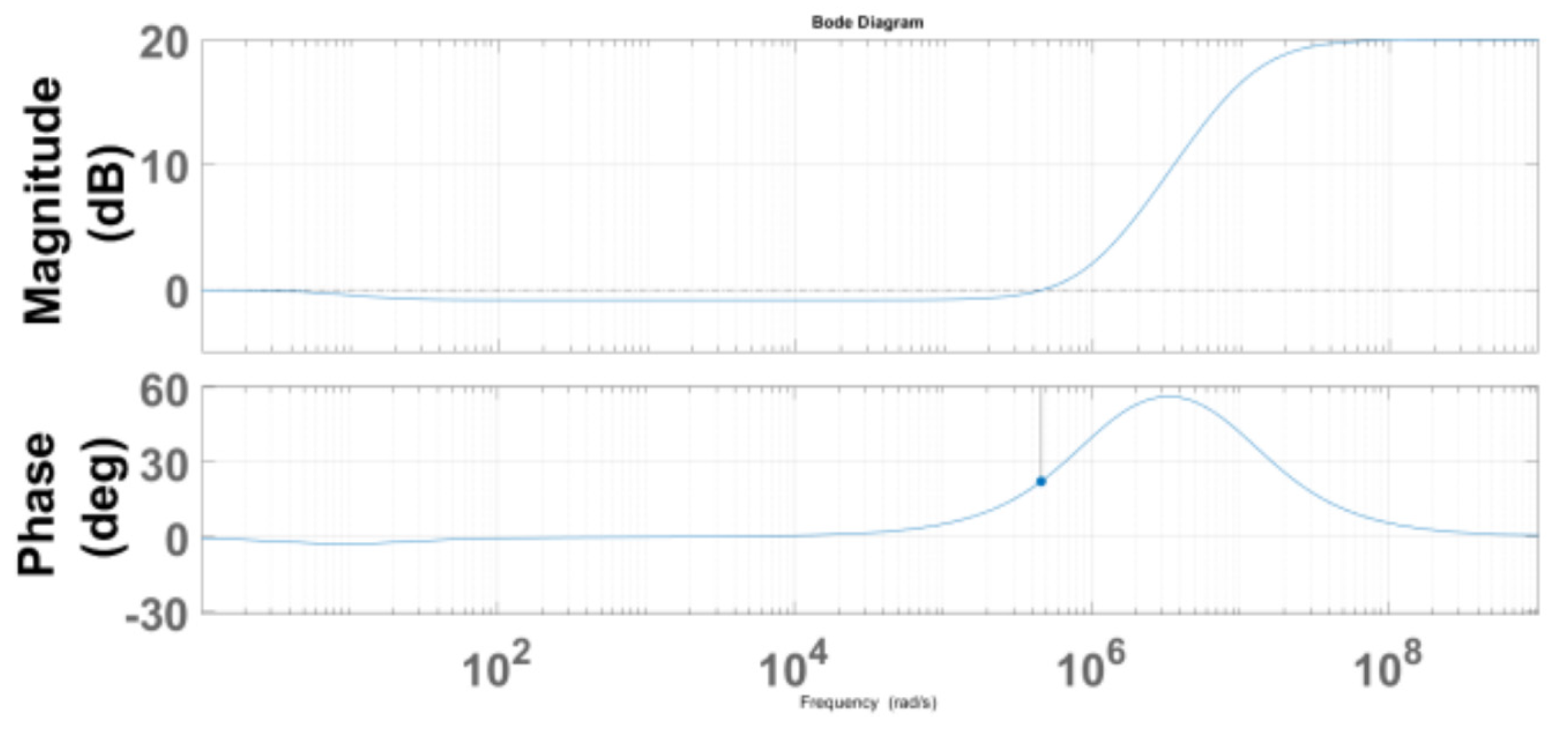
4.3. Case Study 3: Mitigation Layer Stability
5. Experimental Results
5.1. API Controller
5.2. Tuned PI Controller
5.3. FAPI Controller
5.4. Time-Varying Cyber-Attack Using FAPI Controller
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Connected DGUs (i,j) | Resistance Rij (Ω) | Inductance Lij (µH) |
|---|---|---|
| Line 1–3 | 0.07 | 2.1 |
| Line 2–3 | 0.04 | 2.3 |
| Line 2–4 | 0.08 | 1.8 |
| Line 3–4 | 0.07 | 1 |
| Line 4–5 | 0.05 | 2 |
| DGUi [1–4] | Resistance Rn (Ω) | Inductance Ln (mH) | Capacitance Cti (mF) | Local Load (Ω) |
|---|---|---|---|---|
| DGU 1 | 0.2 | 1.8 | 2.2 | 10 |
| DGU 2 | 0.3 | 2.0 | 1.9 | 9 |
| DGU 3 | 0.1 | 2.2 | 1.7 | 8 |
| DGU 4 | 0.5 | 3.0 | 2.5 | 7 |
| DGU 5 | 0.4 | 1.3 | 2 | 7 |
| DGU 1 | k1 = [−2.13, −0.16, 13.55] |
| DGU 2 | k2 = [−0.87, −0.05, 48.28] |
| DGU 3 | k3 = [−0.48, −0.108, 30.67] |
| DGU 4 | k4 = [−7, −0.175, 102.96] |
| DGU 5 | k5 = [−0.10, −0.01, 16.4] |
| Controller Parameters | FAPI | API |
|---|---|---|
| K1 | 1 | 100 |
| K2 | 1 | 2400 |
| K3 | −1 | 0.88 |
| KC | 2 | - |
| m | 0.1 | 1 |
References
- Guerrero, J.M.; Vasquez, J.C.; Matas, J.; de Vicuna, L.G.; Castilla, M. Hierarchical control of droop-controlled AC and DC microgrids—A general approach toward standardization. IEEE Trans. Ind. Electron. 2011, 58, 158–172. [Google Scholar] [CrossRef]
- Yang, Y.; Tan, S.-C.; Hui, S.Y.R. Mitigating Distribution Power Loss of DC Microgrids With DC Electric Springs. IEEE Trans. Smart Grid 2018, 9, 5897–5906. [Google Scholar] [CrossRef]
- Mokhtar, M.; Marei, M.I.; El-Sattar, A.A. A control scheme for islanded and grid-connected DC microgrids. In Proceedings of the 19th International IEEE Middle East Power Systems Conference (MEP-CON), Cairo, Egypt, 19–21 December 2017; pp. 176–180. [Google Scholar]
- Habibi, M.R.; Baghaee, H.R.; Dragicevic, T.; Blaabjerg, F. False Data Injection Cyber-Attacks Mitigation in Parallel DC/DC Converters Based on Artificial Neural Networks. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 717–721. [Google Scholar] [CrossRef]
- Deng, C.; Guo, F.; Wen, C.; Yue, D.; Wang, Y. Distributed Resilient Secondary Control for DC Microgrids against Hetero-geneous Communication Delays and DoS Attacks. IEEE Trans. Ind. Electron. 2022, 69, 11560–11568. [Google Scholar] [CrossRef]
- Yang, Y.; Qin, Y.; Tan, S.-C.; Hui, S.Y.R. Reducing Distribution Power Loss of Islanded AC Microgrids Using Distributed Electric Springs With Predictive Control. IEEE Trans. Ind. Electron. 2020, 67, 9001–9011. [Google Scholar] [CrossRef]
- Zhou, J.; Chen, B.; Yu, L. Intermediate-Variable-Based Estimation for FDI Attacks in Cyber-Physical Systems. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 2762–2766. [Google Scholar] [CrossRef]
- Halladay, J.; Cullen, D.; Briner, N.; Warren, J.; Fye, K.; Basnet, R.; Bergen, J.; Doleck, T. Detection and Characterization of DDoS Attacks Using Time-Based Features. IEEE Access 2022, 10, 49794–49807. [Google Scholar] [CrossRef]
- Amin, M.; El-Sousy, F.F.M.; Aziz, G.A.A.; Gaber, K.; Mohammed, O.A. CPS Attacks Mitigation Approaches on Power Electronic Systems with Security Challenges for Smart Grid Applications: A Review. IEEE Access 2021, 9, 38571–38601. [Google Scholar] [CrossRef]
- Zhong, X.; Yu, L.; Brooks, R.; Venayagamoorthy, G.K. Cyber security in smart DC microgrid operations. In Proceedings of the IEEE First International Conference on DC Microgrids (ICDCM), Atlanta, GA, USA, 7–10 June 2015; pp. 86–91. [Google Scholar]
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False Data Injection Cyber-Attacks Detection for Multiple DC Microgrid Clusters. Appl. Energy 2022, 310, 118425. [Google Scholar] [CrossRef]
- Beg, O.A.; Johnson, T.T.; Davoudi, A. Detection of False-Data Injection Attacks in Cyber-Physical DC Microgrids. IEEE Trans. Ind. Inform. 2017, 13, 2693–2703. [Google Scholar] [CrossRef]
- Dehghani, M.; Niknam, T.; Ghiasi, M.; Bayati, N.; Savaghebi, M. Cyber-attack detection in dc microgrids based on deep machine learning and wavelet singular values approach. Electronics 2021, 10, 1914. [Google Scholar] [CrossRef]
- Qian, X.; Yang, Y.; Li, C.; Tan, S.-C. Operating Cost Reduction of DC Microgrids Under Real-Time Pricing Using Adaptive Differential Evolution Algorithm. IEEE Access 2020, 8, 169247–169258. [Google Scholar] [CrossRef]
- Sahoo, S.; Peng, J.C.-H.; Devakumar, A.; Mishra, S.; Dragicevic, T. On Detection of False Data in Cooperative DC Microgrids—A Discordant Element Approach. IEEE Trans. Ind. Electron. 2020, 67, 6562–6571. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of False Data Injection Cyber-Attacks in DC Microgrids Based on Recurrent Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 5294–5310. [Google Scholar] [CrossRef]
- Habibi, M.R.; Sahoo, S.; Rivera, S.; Dragicevic, T.; Blaabjerg, F. Decentralized Coordinated Cyberattack Detection and Mitigation Strategy in DC Microgrids Based on Artificial Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4629–4638. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragičević, T. Secure Control of DC Microgrids for Instant Detection and Mitigation of Cyber-Attacks Based on Artificial Intelligence. IEEE Syst. J. 2022, 16, 2580–2591. [Google Scholar] [CrossRef]
- El-Ebiary, A.H.; Mokhtar, M.; Mansour, A.M.; Awad, F.H.; Marei, M.I.; Attia, M.A. Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters. Energies 2022, 15, 9426. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragicevic, T. Secure MPC/ANN-Based False Data Injection Cyber-Attack Detection and Mitigation in DC Microgrids. IEEE Syst. J. 2022, 16, 1487–1498. [Google Scholar] [CrossRef]
- Yang, Y.; Ho, S.-S.; Tan, S.-C.; Hui, S.-Y.R. Small-Signal Model and Stability of Electric Springs in Power Grids. IEEE Trans. Smart Grid 2018, 9, 857–865. [Google Scholar] [CrossRef]
- Meng, L.; Dragicevic, T.; Roldán-Pérez, J.; Vasquez, J.C.; Guerrero, J.M. Modeling and Sensitivity Study of Consensus Al-gorithm Based Distributed Hierarchical Control for DC Microgrids. IEEE Trans. Smart Grid 2016, 7, 1504–1515. [Google Scholar] [CrossRef]
- Olfati-Saber, R.; Murray, R.M. Consensus problems in networks of agents with switching topology and time-delays. IEEE Trans. Autom. Control 2004, 49, 1520–1533. [Google Scholar] [CrossRef]
- Rana, M.M.; Li, L.; Su, S.W. State Estimation of the DC Microgrids with Constant Power Loads under DoS Attacks. IEEE/CAA J. Autom. Sin. 2018, 5, 602–609. [Google Scholar] [CrossRef]
- Munsi, S.; Siddique, A.B.; Das, S.K.; Paul, S.K.; Islam, R.; Moni, M.A. A Novel Blended State Estimated Adaptive Controller for Voltage and Current Control of Microgrid Against Unknown Noise. IEEE Access 2019, 7, 161975–161995. [Google Scholar] [CrossRef]
- Liu, H.; Hu, F.; Su, J.; Wei, X.; Qin, R. Comparisons on Kalman-Filter-Based Dynamic State Estimation Algorithms of Power Systems. IEEE Access 2020, 8, 51035–51043. [Google Scholar] [CrossRef]
- Zhang, Q. On stability of the Kalman filter for discrete time output error systems. Syst. Control. Lett. 2017, 107, 84–91. [Google Scholar] [CrossRef]
- Boyi, N.; Zhang, Q. Stability of the kalman filter for output error systems. IFAC-PapersOnLine 2015, 48, 1106–1111. [Google Scholar]
- Yang, Y.; Qin, Y.; Tan, S.-C.; Hui, S.Y.R. Efficient Improvement of Photovoltaic-Battery Systems in Standalone DC Microgrids Using a Local Hierarchical Control for the Battery System. IEEE Trans. Power Electron. 2019, 34, 10796–10807. [Google Scholar] [CrossRef]
- Yang, Y.; Tan, S.-C.; Hui, S.Y.R. Adaptive Reference Model Predictive Control With Improved Performance for Voltage-Source Inverters. IEEE Trans. Control. Syst. Technol. 2018, 26, 724–731. [Google Scholar] [CrossRef]
- Mohamed, S.; Mokhtar, M.; Marei, M.I. An Adaptive Control of Remote Hybrid Microgrid based on the CMPN Algorithm. Electr. Power Syst. Res. 2022, 213, 108793. [Google Scholar] [CrossRef]
- Yang, Y.; Mok, K.-T.; Tan, S.-C.; Hui, S.Y. Nonlinear dynamic power tracking of low-power wind energy conversion system. IEEE Trans. Power Electron. 2015, 30, 5223–5236. [Google Scholar] [CrossRef]
- Doostinia, M.; Beheshti, M.T.H.; Alavi, S.A.; Guerrero, J.M. Distributed control strategy for DC microgrids based on average consensus and fractional-order local controllers. IET Smart Grid 2021, 4, 549–560. [Google Scholar] [CrossRef]
- Computer Software; Version 2020a; MATLAB; The Math Works, Inc.: Portola Valley, CA, USA, 2020.
- Moldovan, T.; Inţe, R.; Nemeş, R.-O.; Ruba, M.; Marţiş, C. Typhoon HIL Real-Time Validation of Permanent Magnet Synchronous Motor’s Control. In Proceedings of the 9th International Conference on Modern Power Systems, Cluj-Napoca, Romania, 16–17 June 2021; pp. 1–6. [Google Scholar]
- Kumar, Y.P.; Bhimasingu, R. Alternative hardware-in-the-loop (HIL) setups for real-time simulation and testing of microgrids. In Proceedings of the 2016 IEEE 1st International Conference on Power Electronics, Intelligent Control and Energy Systems (ICPEICES), Delhi, India, 4–6 July 2016; pp. 1–6. [Google Scholar]
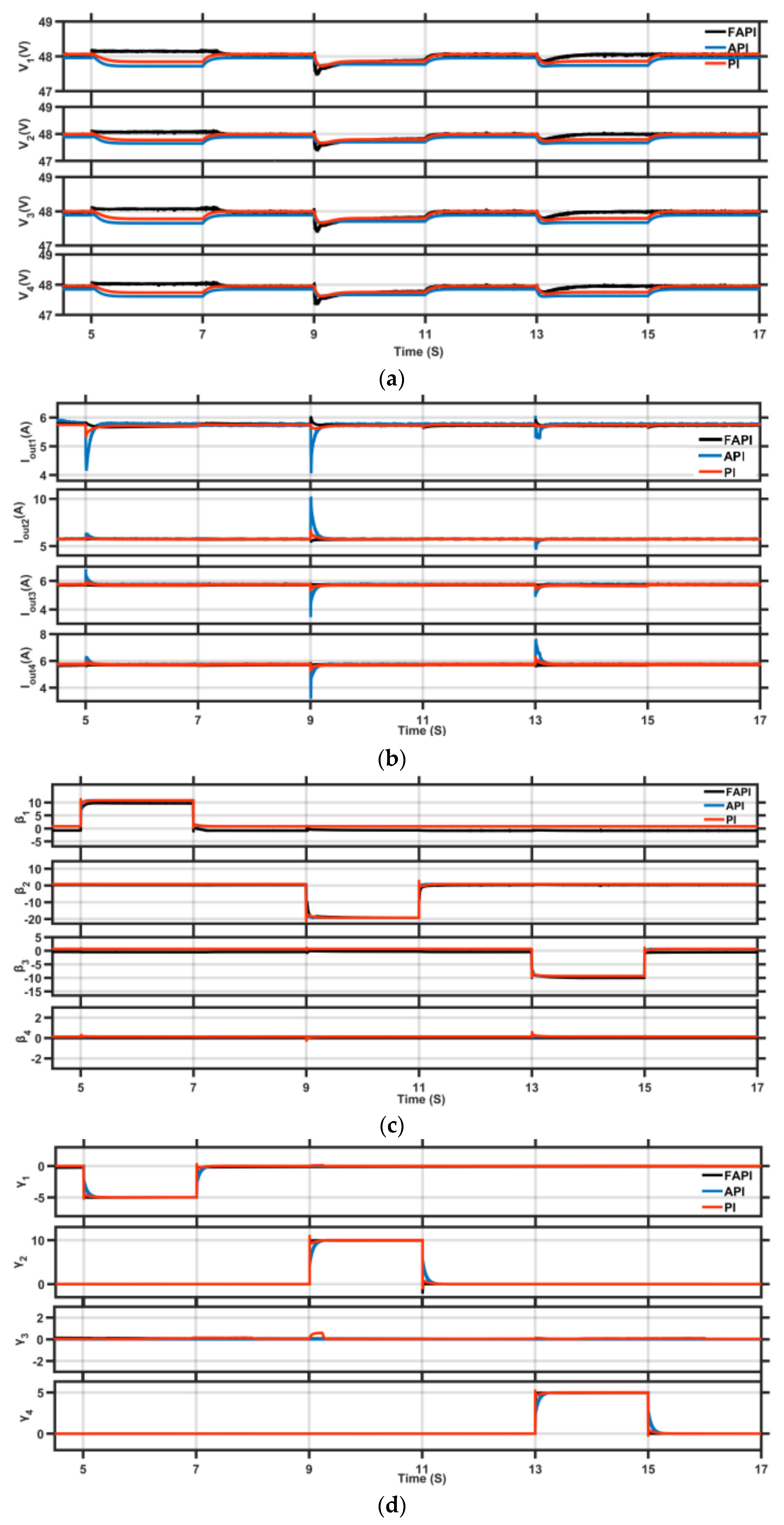


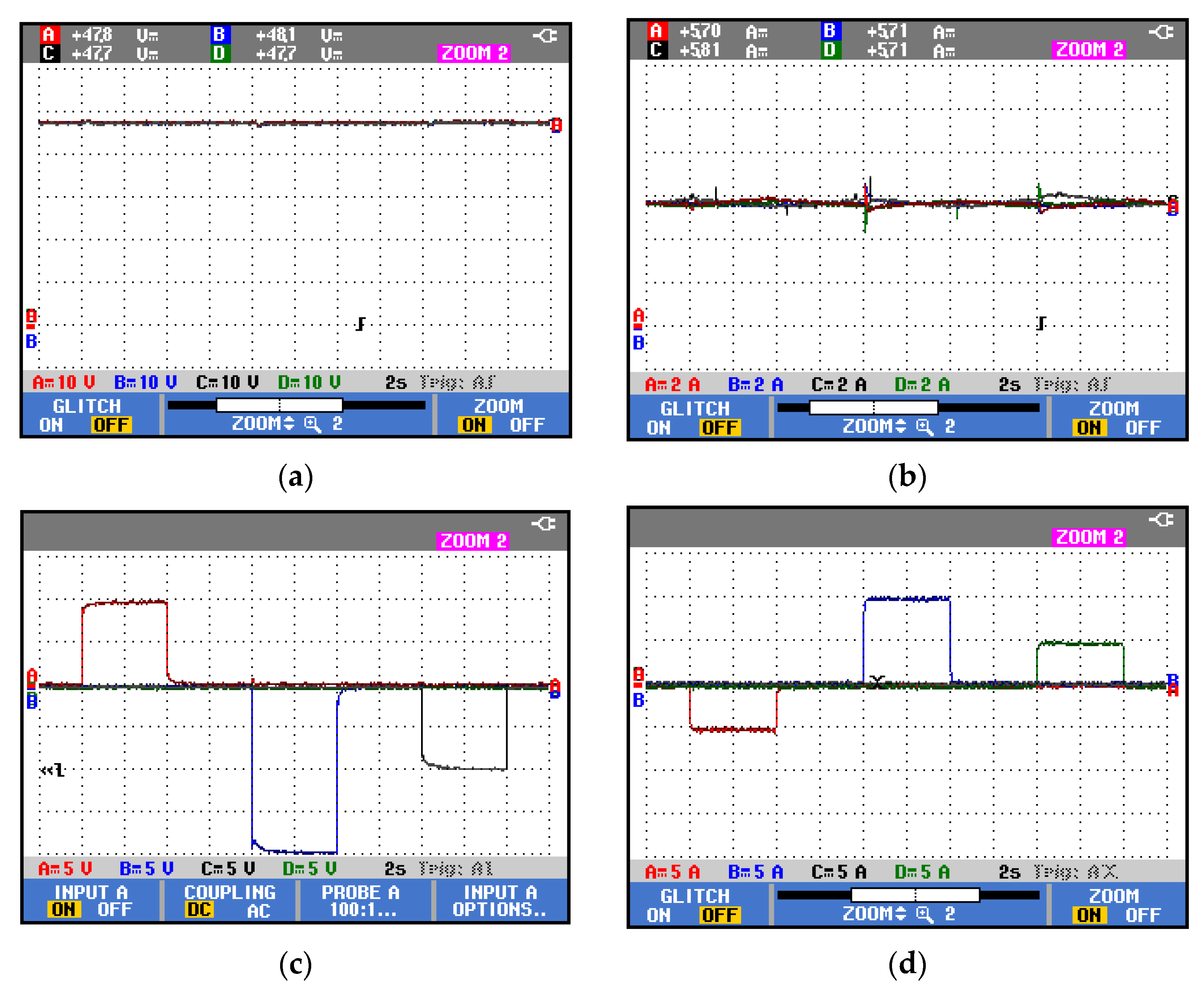
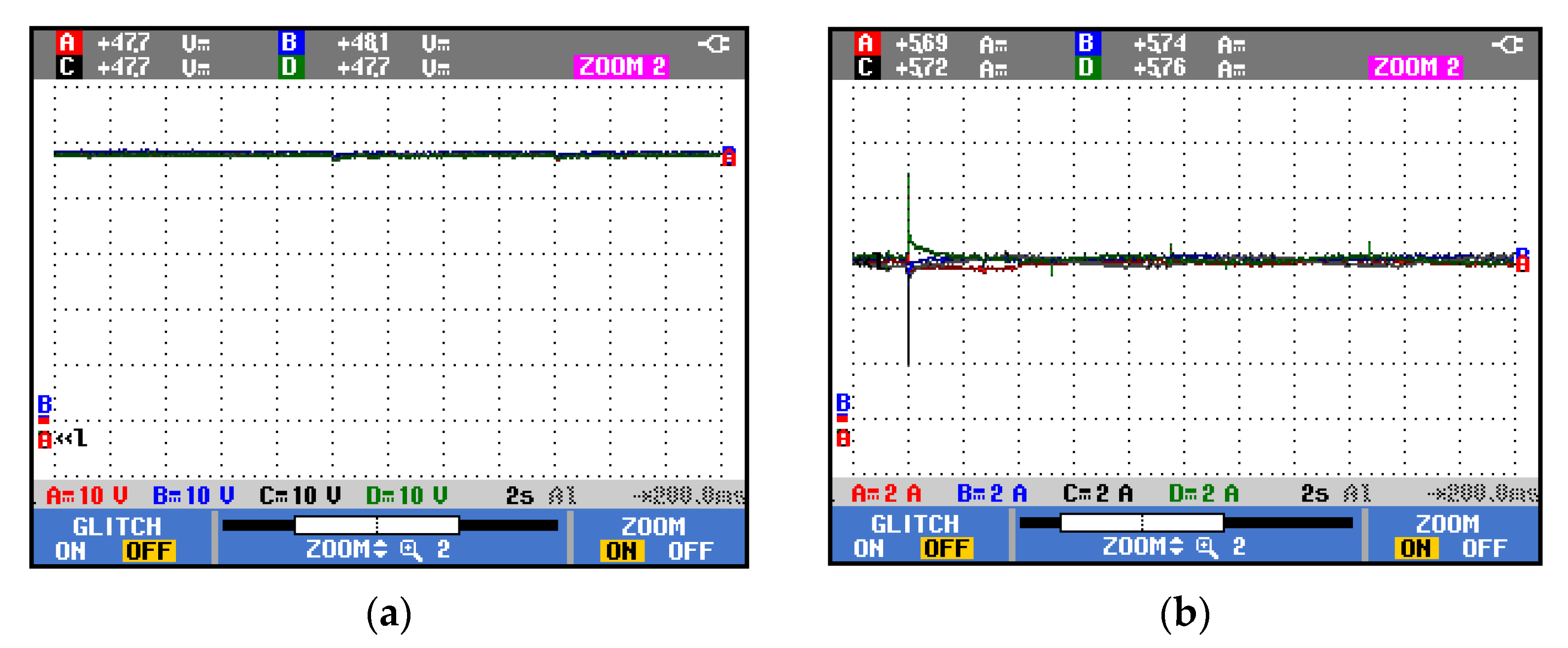

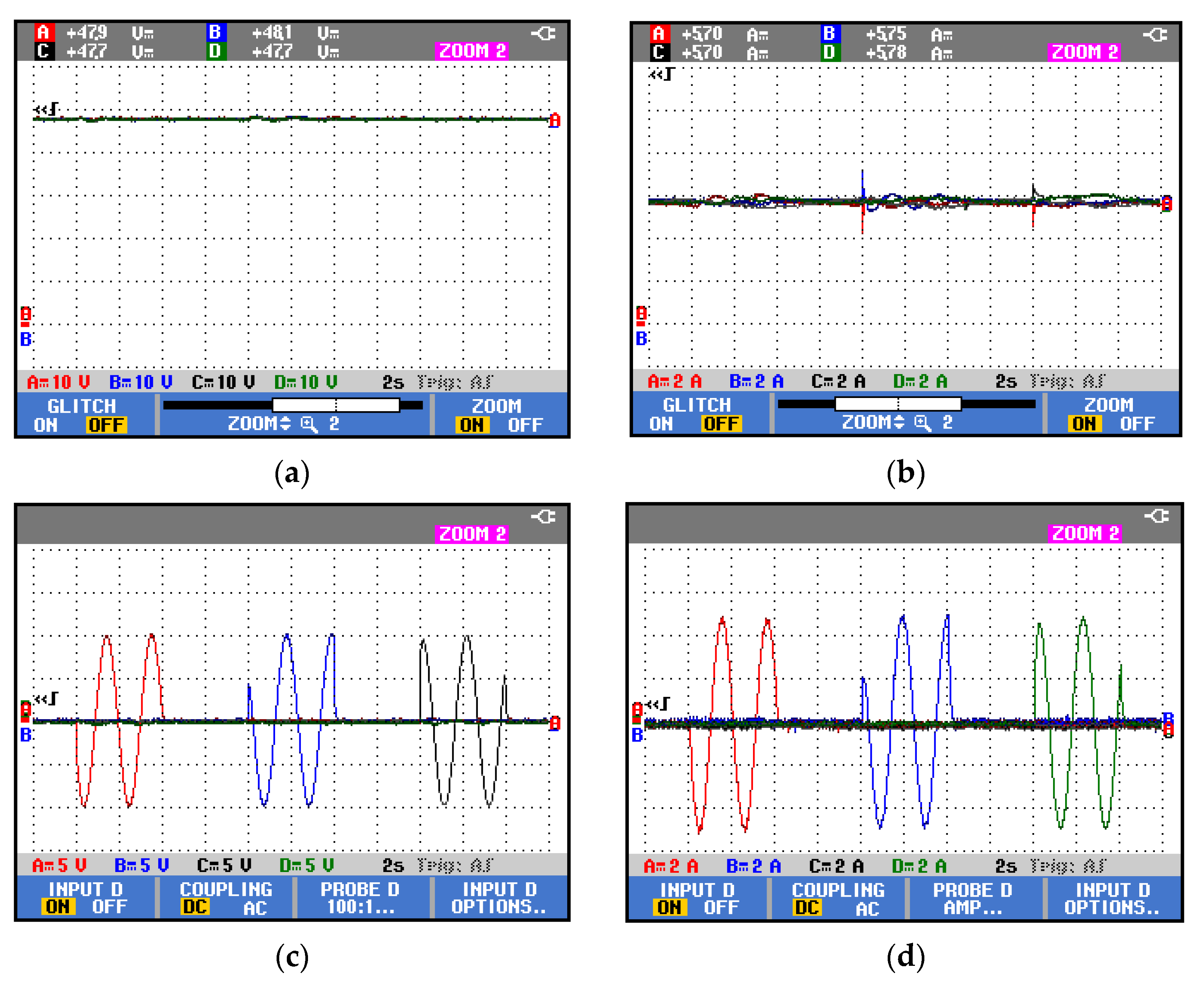
| Controller | Settling Time (s) | Current MPOS% |
|---|---|---|
| API | 2 | +145% |
| Tuned PI | 1 | +22.8% |
| FAPI | 0.25 | −65% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, W.; Fu, H.; Wu, S.; Yang, B.; Liu, Z. RETRACTED: A Kalman Filter-Based Distributed Cyber-Attack Mitigation Strategy for Distributed Generator Units in Meshed DC Microgrids. Energies 2023, 16, 7959. https://doi.org/10.3390/en16247959
Li W, Fu H, Wu S, Yang B, Liu Z. RETRACTED: A Kalman Filter-Based Distributed Cyber-Attack Mitigation Strategy for Distributed Generator Units in Meshed DC Microgrids. Energies. 2023; 16(24):7959. https://doi.org/10.3390/en16247959
Chicago/Turabian StyleLi, Wenpei, Han Fu, Shun Wu, Bin Yang, and Zhixiong Liu. 2023. "RETRACTED: A Kalman Filter-Based Distributed Cyber-Attack Mitigation Strategy for Distributed Generator Units in Meshed DC Microgrids" Energies 16, no. 24: 7959. https://doi.org/10.3390/en16247959
APA StyleLi, W., Fu, H., Wu, S., Yang, B., & Liu, Z. (2023). RETRACTED: A Kalman Filter-Based Distributed Cyber-Attack Mitigation Strategy for Distributed Generator Units in Meshed DC Microgrids. Energies, 16(24), 7959. https://doi.org/10.3390/en16247959









