Cybersecurity in Cyber–Physical Power Systems
Abstract
1. Introduction
- A robust review of the literature that is capable of guiding decision-making on a possible operational scenario in which the cyber–physical power system suffers cyberattacks, indicating a possible solution to this problem.
- A theoretical framework capable of assisting in the planning and developing of cybersecurity systems for cyber–physical systems.
- A tool to prevent and mitigate these types of attacks.
- A review of the layers, basic components, and key vulnerabilities of the devices that comprise the control and management system for cyber–physical systems.
- A robust history and the main types of cyberattacks against industrial systems, as well as the main standards and regulations developed for cybersecurity in microgrids.
2. Background
2.1. History of Cyberattacks
| Year | Involved Countries | Type of Cyberattack | Cyber Incident |
|---|---|---|---|
| 1982 | URSS | Code manipulation | Pipeline destruction in Siberia due to manipulation of control software code causes valves to malfunction [38]. |
| 1999 | Bellingham, USA | Code manipulation | Code manipulation that led to a slowdown of a pipeline SCADA system [38]. |
| 2000 | Queensland, Australia | Attack | Cyberattack on Maroochy Water Services. This wireless attack remotely controlled 150 pumping stations and released millions of gallons of untreated sewage [33]. |
| 2003 | Ohio, USA | Malware | The Ohio nuclear power plant suffers the injection of a Malware (Slammer Worm) into its control system [34,38]. |
| 2007 | Idaho National Laboratory, USA | Attack | A hacker injected false data and controlled a generator breaker. This cyberattack became known as the Aurora Attack [34,38]. |
| 2008 | Turkey | Attack | Explosion of oil and barrels in Turkish pipelines caused by false data injection attacks that manipulated the control system [34,38]. |
| 2010 | Iran | Malware | Iran’s nuclear power plant control facilities were attacked by a malware called Stuxnet [33]. |
| 2010 | China, USA, and Netherlands | Malware | Night Dragon malware: This cyberattack was targeted at large companies in the energy and oil sector [33]. |
| 2011 | Global | Malware | Duqu/Flame/Gauss malware: This malware was discovered by Hungarian researchers in 2011 and aims to steal information from the control system of companies and their suppliers [33]. |
| 2012 | Global | Campaign (series of attacks) | In 2012, a set of cyberattacks targeting the oil and natural gas industry was discovered. This series of attacks is called the Gas Pipeline Cyber Invasion Campaign [33]. |
| 2012 | Saudi Arabia and Qatar | Malware | Power generation and supply has been affected due to this malware attack on the computer system of large energy companies in the Middle East. This attack is known as Shamoon Malware [33,34,38]. |
| 2013 | USA and Russia | Attack | In 2013, the attackers carried out a cyberattack on a company that provides maintenance services on a store’s air-conditioning, heating, and ventilation system. From this attack, the hacker was able to extract financial data from the target stores. This cyber event became known as Target Stores Attacks [33]. |
| 2013 | USA and Iran | Attack | The Bowman Dam that controls the water level after abnormal storms was accessed by Iranian invaders through a cyberattack, according to the US. This cyber event became known as the New York Dam Attack [33]. |
| 2013 | USA and Russia | Malware | The Havex malware is a trojan horse that has the ability to remotely access and collect unauthorized information from industrial control systems [33]. |
| 2014 | Germany | Attack | A steel mill in Germany suffered a cyberattack based on spear-phishing and social engineering. The attackers gained access to the industrial control system and caused several failures in the control, operation, and triggering of equipment [33]. |
| 2014 | Global | Malware | BlackEnergy malware is a cyberattack that aims to extract information from the various Human–Machine Interface providers [33]. |
| 2014 | USA, Turkey, Switzerland, and Russia | Campaign (series of attacks) | The energy sector in the USA, Turkey, and Switzerland suffered a campaign of cyberattacks aimed at spying and accessing confidential information from the control process. This cyber incident became known as Dragonfly/Energetic Bear Campaign No. 1 [33]. |
| 2015 | Ukraine | Attack | In 2015, the blackout in Ukraine was caused by the injection of false data into the power grid. This cyber event affected thousands of users for a few hours and was considered the first successful attack on a country’s power system [33,34,38,42]. |
| 2016 | Syria and USA | Attack | A water treatment company suffered a cyberattack on its control system that modified the dosage of chemicals used in its processing. This cyberattack became known as the Kemuri Water Company Attack [33]. |
| 2016 | Saudi Arabia and other Middle Eastern countries | Malware | After four years, the Shamoon malware was used again for a cyberattack on the computer system of the civil aviation sector in Saudi Arabia and other Middle Eastern countries. This attack aimed to erase data from the system [33]. |
| 2016 | Ukraine | Attack | The Ukrainian power grid once again suffered a cyberattack that led to power outages. This time, this attack was more robust, and a denial-of-service attack hit the telephone system. The new malware used in this attack is known as Crashoverride [33,42]. |
| 2017 | USA and Ukraine | Malware | CRASHOVERRIDE is malware responsible for generating power interruptions in countries’ power systems. The cyberattack in the Ukraine in 2019 used this mechanism [33]. |
| 2017 | Iran, USA, Saudi Arabia, and South Korea | Group (set of malwares) | APT33 is a set of malwares that aims to spy on the aviation, energy, and petrochemical industries. In addition, this cyberattack has the destructive ability to erase process data and share confidential information with attackers [33]. |
| 2017 | Ukraine, Russia, USA, UK, and Australia | Attack | NotPetya is malware that was initially used against the Ukraine and has the ability to target a nation’s critical infrastructure. It is a destructive cyberattack of Russian origin [33]. |
| 2017 | USA | Campaign (series of attacks) | Dragonfly/Energetic Bear No. 2 is a set of cyberattacks that target a country’s strategic infrastructure sectors, such as the electric and nuclear power grids and the water supply [33]. |
| 2017 | Middle Eastern countries | Malware | TRITON/Trisis/HatMan consists of new malware that has the ability to access and modify confidential information and execute algorithms that destabilize the industrial security system [33]. |
| 2019 | USA | Attack | A cyberattack interfered with power grid operations in the US on 5 March 2019. The type of attack used was denial of service. This was the first cyberattack in the wind and solar energy sector [34]. |
| 2019 | India | Malware | The Kudankulam nuclear power plant in India suffered a cyberattack in 2019 [34]. |
| 2019 | Venezuela | Attack | In 2019, the power grid in Venezuela was attacked, causing a power outage for more than five days in several states, including the capital [42,43]. |
| 2020 | Portugal | Ransomware (malware) | The giant Portuguese energy company, Energies of Portugal, was attacked in 2020 by Ragnar Locker. The attackers reportedly stole 10 TB of confidential data [43]. |
| 2020 | Brazil | Attack | On 16 June 2020, a Brazilian power generation and distribution company, Light S.A., was attacked by a Sodinokibi malware and had its operation temporarily halted [43]. |
| 2020 | Venezuela | Attack | In 2020, the power grid in Venezuela was attacked, causing a power outage in several states, except the capital [44]. |
| 2021 | USA | Ransomware (malware) | A set of hackers used the ransomware attack and broke into Colonial Pipeline’s network and digital systems, leading to an outage of the pipeline for several days [45]. |
2.2. Classification of Cyberattacks
- (i).
- Availability;
- (ii).
- Integrity;
- (iii).
- Confidentiality.
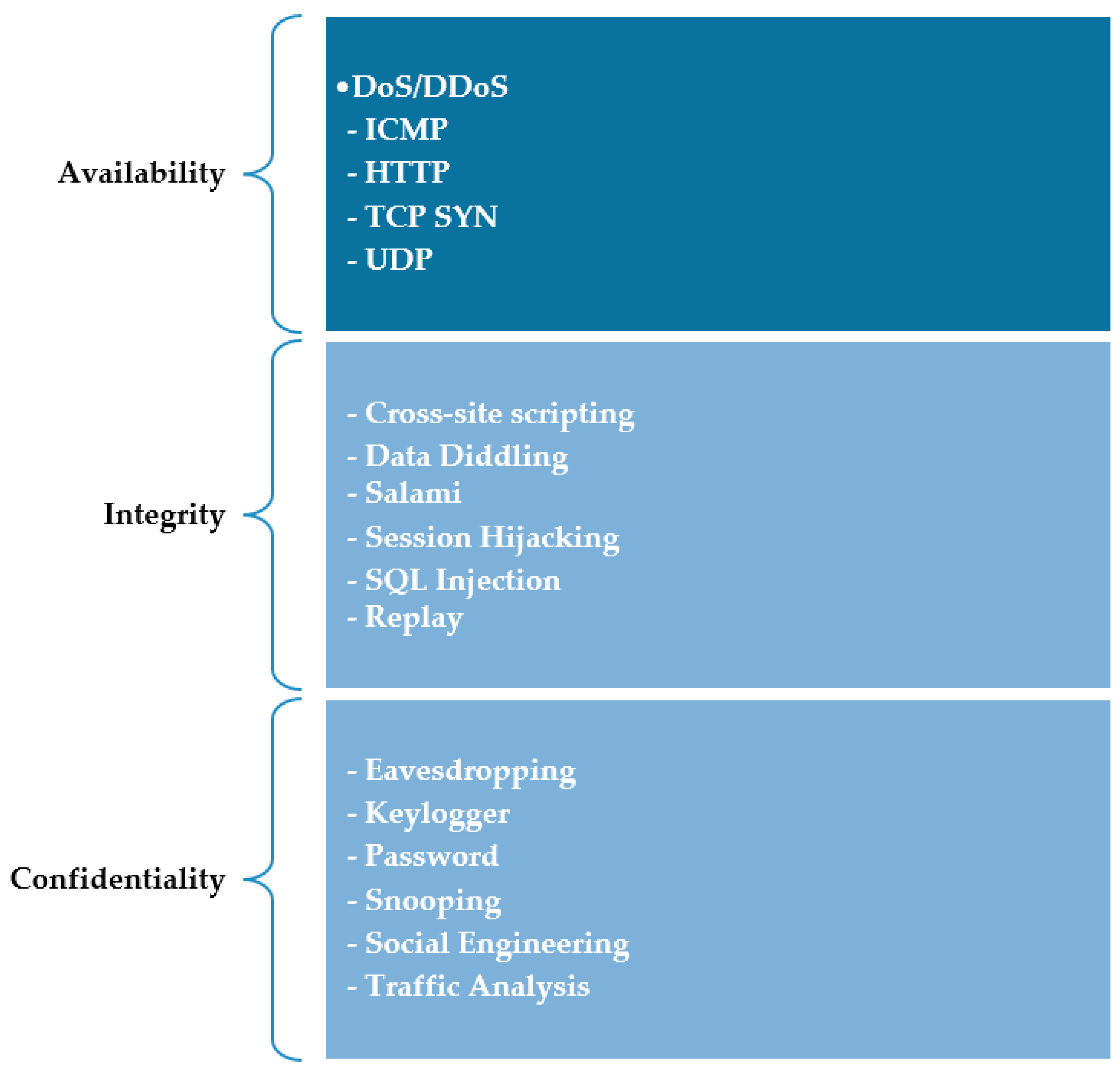
2.2.1. Availability
- DoS/DDoS
- It studies the system information to find possible vulnerabilities in the network and then sends an attack;
- The attacker creates bots that install malicious programs on the invaded computers so that they can be controlled. The hacked computers are called zombies;
- The attacker encourages the invaded computers to send various attack messages to target the victim;
- The attacker extracts the information of interest and erases the data from memory.
- Communication network slowness;
- Blocking authorized users’ access to system resources.
- A1. ICMP
- A2. HTTP
- A3. TCP SYN
- A4.UDP
2.2.2. Integrity
- A.
- Cross-Site Scripting
- B.
- Data Diddling
- C.
- Salami
- D.
- Session Hijacking
- E.
- SQL Injection
- F.
- Replay
2.2.3. Confidentiality
- A.
- Eavesdropping
- B.
- Keylogger
- C.
- Password Attacks
- Attack based on the combination of all characters contained in the dictionary;
- Attack using hacking software that tries numerous possible password combinations,
- Guessing attack, the attacker uses the victim’s personal data to discover the password.
- Sentence substitution: Choose a sentence and substitute each word or digit with other characters;
- Keyboard change: Choose a basic password and then add characters according to the random movement chosen by the user. You must save this movement;
- Use the formula: Put the password in the format of an equation or function with numbers and characters,
- Special character insertion: Replace conventional characters in the basic password with special characters.
- D.
- Snooping
- E.
- Social Engineering
- F.
- Traffic Analysis
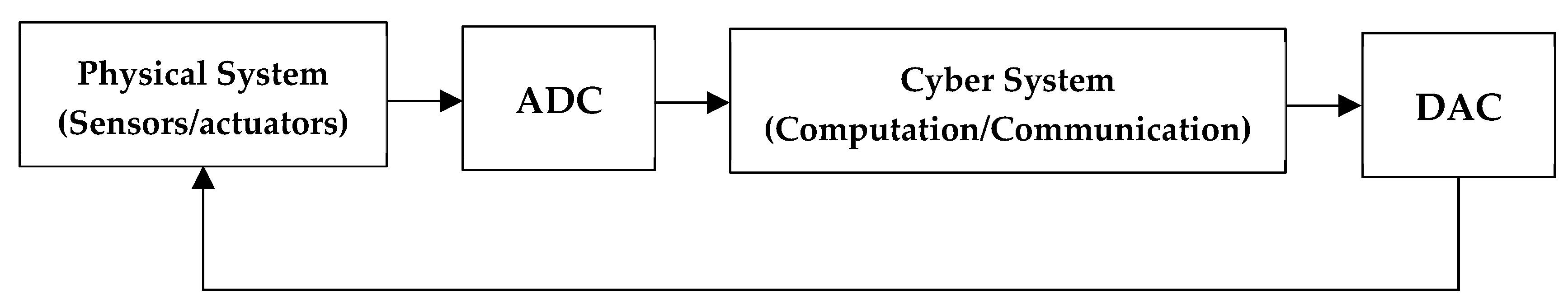
3. Cyber–Physical System
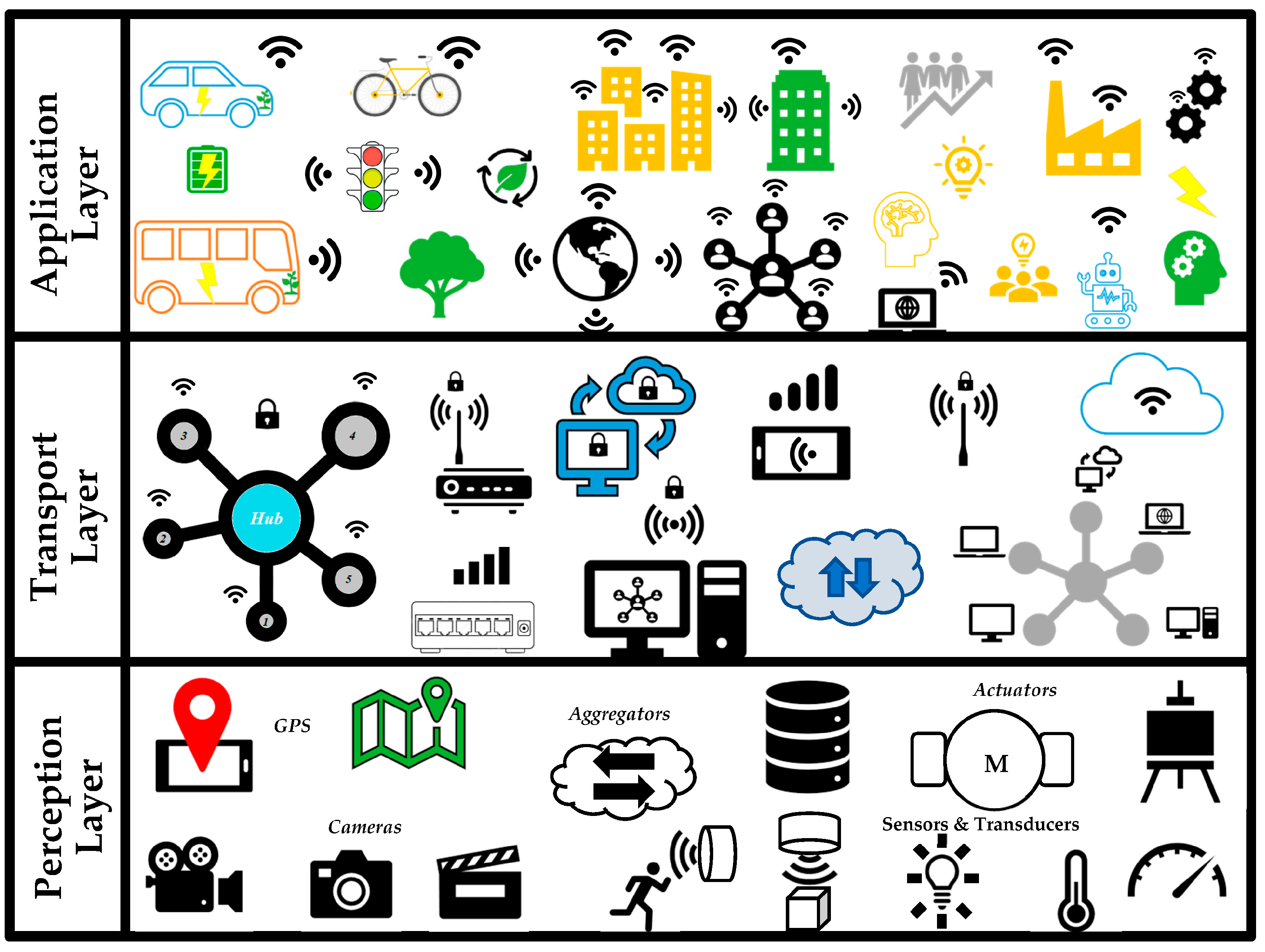
3.1. Cyber–Physical System Layers
3.1.1. Perception Layer
3.1.2. Transport Layer
3.1.3. Application Layer
3.2. Cyber–Physical System Components
- (i).
- Physical components;
- (ii).
- Detection components,
- (iii).
- Control and communication components.
3.2.1. Physical Components
3.2.2. Detection Components
- Sensors
- Aggregators
- Actuators
3.2.3. Control and Communication Components
- Programmable Logic Controllers (PLCs)
- Distributed Control Systems (DCSs)
- Remote Terminal Units (RTUs)
- Supervisory Control and Data Acquisition (SCADA)
- Phasor Measurement Unit (PMU)
3.3. Cyber–Physical System Vulnerabilities
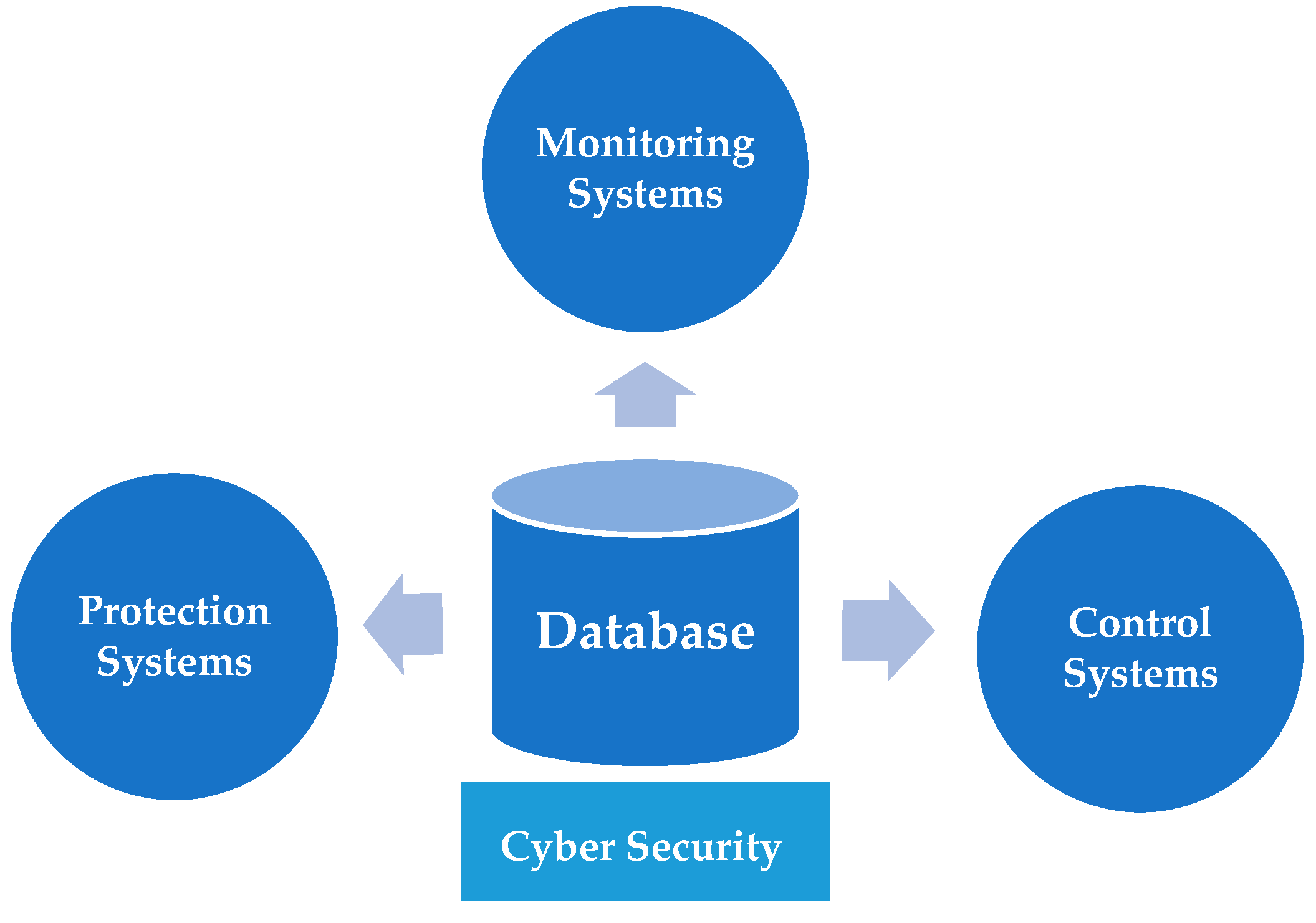
4. Cybersecurity Applications and Methodology
4.1. Cybersecurity on Monitoring Systems
4.2. Cybersecurity on Control Systems
4.3. Cybersecurity in Protection Systems
4.4. Defense Strategies and Future Trends for Cybersecurity
- Strategies based on protection against cyberattacks are related to meters, sensors, aggregators, actuators, defense devices, and all other components that make up the physical part of a MG and a CPS.
- Identification-based strategies aim to mitigate or eliminate the unwanted effects of cyberattacks. Detection can happen in a static manner, in which it seeks to achieve stationary stability, and in a dynamic manner, in which dynamic information is used in the detection process [47].
- Modernization of the electricity system: The gradual replacement of conventional power generation by clean energy increases the penetration of renewables, modifies the behavior, and adds the characteristic of intermittent generation to the system. Moreover, the use of new IoT technologies and the integration between devices and sectors provide the emergence of smart grids, which, due to the dependence on the Internet for operation and communication, present cyber vulnerabilities. Thus, the MG needs reliable and resilient cybersecurity in order not to harm its communication, state estimation, frequency control, voltage regulation, and the performance of its applications, such as the possibility of operation in the islanded mode and the connection of other islanded grids.
- Transportation and electrification: The process of electrification of transportation is a strategy that encourages the development, production, and use of electrically powered buses, vehicles, trains, and subways, as well as being an important factor in decreasing the emission of polluting gases into the atmosphere. These technological vehicles connected to charging stations modify and are part of the MG. Thus, this new means of transportation becomes a target of cyberattacks, and the security of charging stations is considered a point of vulnerability and of research interest [146]. From this perspective, the author of [147] designed simulation software to evaluate the cyber vulnerability of electric vehicle charging structures and devices. Therefore, cybersecurity in transportation electrification is a current problem that is under research and development.
5. Regulations and Standards
- i.
- AMI-SER
- ii.
- IEC 62351
- iii.
- NERC-CIP
- iv.
- NIST Standard
- v.
- NIST SP 800-82
- vi.
- NISTIR 7628
- vii.
- IEEE 2030 Std.2
- viii.
- IEEE C37.240
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACK | acknowledgment |
| ADS | Anomaly Detection System |
| ADP | Adaptive Dynamic Programming |
| AEs | autoencoders |
| AHP | Analytic Hierarchy Process |
| AI | artificial intelligence |
| AMI | advanced metering infrastructure |
| AMI-SER | Advanced Metering Infrastructure System Security Requirements |
| CI | computational intelligence |
| CIA | code injection attacks |
| COVID-19 | coronavirus disease pandemic |
| CPS | cyber–physical systems |
| CP-SAM | Cyber–Physical Security Assessment Metric |
| CPPS | cyber–physical power system |
| CPU | central processing unit |
| DCS | Distributed Control System |
| DDoS | distributed denial of service |
| DOM | document object model |
| DoS | denial of service |
| EV | electric vehicle |
| FDI | false data injection |
| GPS | Global Position System |
| HMI | Human–Machine Interface |
| HTM | Hybrid Trigger Mechanism |
| HTTP | Hypertext Transfer Protocol |
| ICMP | Internet Control Message Protocol |
| ICPSs | industrial cyber–physical systems |
| IEC | International Electrotechnical Commission |
| IEEE | Institute of Electrical and Electronics Engineers |
| IIoT | Industrial Internet of Things |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IR | infrared |
| LCDRs | line current differential relays |
| LOF | Local Outlier Factor |
| LSTM | Long Short-Term Memory |
| MADDL | Multi-Agent Distributed Deep Learning |
| MCDM | multicriteria decision-making |
| MLP | Multilayer Perceptron |
| ML-RSM | Multilayer Run-Time Security Monitor |
| MG | microgrids |
| MPC | Model Predictive Control |
| NERC-CIP | North American Electric Reliability Corporation Critical Infrastructure Protection |
| NIST | National Institute of Standards and Technology |
| NIST SP | National Institute of Standards and Technology Special Publication |
| NISTIR | National Institute of Standards and Technology Interagency Report |
| NPPs | nuclear power plants |
| OCSVMs | one-class support vector machines |
| PCHD | Port Controlled Hamiltonian with dissipation |
| PLC | Programmable Logic Controller |
| PMU | Phasor Measurement Unit |
| RA | replay attack |
| RFID | Radio-Frequency Identification |
| RPS | Reactor Protection System |
| RSDBN | regularized sparse deep belief network |
| RTU | Remote Terminal Unit |
| SCADA | Supervisory Control and Data Acquisition |
| SG | smart grid |
| SMC | sliding mode controller |
| SP | Special Publication |
| SYN | synchronization |
| TCN | Temporal Convolutional Neural Network |
| TCP | Transmission Control Protocol |
| TOPSIS | Technique for Order of Preference by Similarity to Ideal Solution |
| TTSCPSs | two-timescale CPSs |
| UCAIug | UCA International users’ group |
| UDP | user datagram protocol |
References
- De Vries, J. The Industrial Revolution and the Industrious Revolution. J. Econ. Hist. 1994, 54, 249–270. [Google Scholar] [CrossRef]
- Hudson, P. The Industrial Revolution, 1st ed.; Bloomsbury Publishing: London, UK, 2014; p. 256. ISBN 9781474225489. [Google Scholar]
- Xu, M.; David, J.M.; Kim, S.H. The Fourth Industrial Revolution: Opportunities and Challenges. Int. J. Financ. Res. 2018, 9, 90–95. [Google Scholar] [CrossRef]
- Rohde, R.; Muller, R.M.; Jacobsen, R.; Muller, E.; Perlmutter, S.; Rosenfeld, A.; Wurtele, J.; Groom, D.; Wickham, C. A new estimate of the average Earth surface land temperature spanning 1753 to 2011. Geoinfor. Geostat. Overv. 2013, 1, 1. [Google Scholar] [CrossRef]
- Hansen, J.; Sato, M. Global temperature change. Proc. Natl. Acad. Sci. USA 2006, 103, 14288–14293. [Google Scholar] [CrossRef] [PubMed]
- Nita, I.A.; Sfîcă, L.; Voiculescu, M.; Birsan, M.V.; Micheu, M.M. Changes in the global mean air temperature over land since 1980. Atmos. Res. 2022, 279, 106392. [Google Scholar] [CrossRef]
- Pileggi, S.F.; Lamia, S.A. Climate Change TimeLine: An Ontology to Tell the Story so Far. IEEE Access 2020, 8, 65294–65312. [Google Scholar] [CrossRef]
- Anderson, T.R.; Hawkins, E.D.; Jones, P.J. CO2, the greenhouse effect and global warming: From the pioneering work of Arrhenius and Callendar to today’s Earth System Models. Endeavour 2016, 50, 178–187. [Google Scholar] [CrossRef]
- Rachel, W. Chapter 11: Impacts of global climate change at different annual mean global temperature increases. In Avoiding Dangerous Climate Change, 1st ed.; Schellnhuber, H.M., Cramer, W., Nakicenovic, N., Wigley, T., Yohe, G., Eds.; Cambridge University Press: Cambridge, UK, 2006; pp. 93–94. ISBN 9780521864718. [Google Scholar]
- Arnell, N.W. The implications of climate change for emergency planning. Int. J. Disaster Risk Reduct. 2022, 83, 103425. [Google Scholar] [CrossRef]
- Hallegatte, S.; Rozenberg, J. Climate change through a poverty lens. Nat. Clim Chang. 2017, 7, 250–256. [Google Scholar] [CrossRef]
- Diffenbaugh, N.S.; Burke, M. Global warming has increased global economic inequality. Proc. Natl. Acad. Sci. USA 2019, 116, 9808–9813. [Google Scholar] [CrossRef]
- Raymakers, A.J.N.; Sue-Chue-Lam, C.; Haldane, V.; Cooper-Reed, A.; Toccalino, D. Climate change, sustainability, and health services research. Health Policy Technol. 2022, 12, 100694. [Google Scholar] [CrossRef]
- Ahmadian, E.; Sodagar, B.; Bingham, C.; Elnokaly, A.; Mills, G. Effect of urban built form and density on building energy performance in temperate climates. Energy Build. 2021, 236, 110762. [Google Scholar] [CrossRef]
- Ahmadian, E.; Bingham, C.; Elnokaly, A.; Sodagar, B.; Verhaert, I. Impact of Climate Change and Technological Innovation on the Energy Performance and Built form of Future Cities. Energies 2022, 15, 8592. [Google Scholar] [CrossRef]
- Ahmadian, E.; Byrd, H.; Sodagar, B.; Matthewman, S.; Kenney, C.; Mills, G. Energy and the form of cities: The counterintuitive impact of disruptive technologies. Archit. Sci. Rev. 2019, 62, 145–151. [Google Scholar] [CrossRef]
- Arnold, G.W. Challenges and opportunities in smart grid: A position article. Proc. IEEE 2011, 99, 922–927. [Google Scholar] [CrossRef]
- Davies, S. Grid gets the smarts [power smart grid]. Eng. Technol. 2013, 7, 42–45. [Google Scholar] [CrossRef]
- Gómez-Expósito, A.; Arcos-Vargas, A.; Maza-Ortega, J.M.; Rosendo-Macias, J.A.; Alvarez-Cordero, G.; Carillo-Aparicio, S.; Gonzalez-Lara, J.; Morales-Wagner, D.; Gonzalez-Garcia, T. City-Friendly Smart Network Technologies and Infrastructures: The Spanish Experience. Proc. IEEE 2018, 106, 626–660. [Google Scholar] [CrossRef]
- Pustokhin, D.A.; Pustokhina, I.V.; Rani, P.; Kansal, V.; Elhoseny, M.; Joshi, G.P.; Shankar, K. Optimal deep learning approaches and healthcare big data analytics for mobile networks toward 5G. Comput. Electr. Eng. 2021, 95, 107376. [Google Scholar] [CrossRef]
- Longo, F.; Padovano, A.; Aiello, G.; Fusto, C.; Certa, A. How 5G-based industrial IoT is transforming human-centered smart factories: A Quality of Experience model for Operator 4.0 applications. IFAC-PapersOnLine 2021, 54, 255–262. [Google Scholar] [CrossRef]
- Lezzi, M.; Lazoi, M.; Corallo, A. Cybersecurity for Industry 4.0 in the current literature: A reference framework. Comput. Ind. 2018, 103, 97–110. [Google Scholar] [CrossRef]
- Navarro, E.M.; Alvarez, A.N.R.; Anguiano, F.I. S A new telesurgery generation supported by 5G technology: Benefits and future trends. Procedia Comput. Sci. 2022, 200, 31–38. [Google Scholar] [CrossRef]
- Meshram, D.A.; Patil, D.D. 5G Enabled Tactile Internet for Tele-Robotic Surgery. Procedia Comput. Sci. 2020, 171, 2618–2625. [Google Scholar] [CrossRef]
- Hakak, S.; Gadekallu, T.R.; Maddikunta, P.K.R.; Ramu, S.P.; M, P.; De Alwis, C.; Liyanage, M. Autonomous vehicles in 5G and beyond: A survey. Veh. Commun. 2023, 39, 100551. [Google Scholar] [CrossRef]
- Energy.gov. National Cyber-Informed Engineering Strategy from the U.S. Department of Energy. Available online: https://www.energy.gov/sites/default/files/2022-06/FINAL%20DOE%20National%20CIE%20Strategy%20-%20June%202022_0.pdf (accessed on 10 December 2022).
- gov.uk. Government Cyber Security Strategy: Building a Cyber Resilient Public Sector. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1049825/government-cyber-security-strategy.pdf (accessed on 10 December 2022).
- Institute for Security Technology Studies. Law Enforcement Tools and Technologies for Investigating Cyber Attacks: Gap Analysis Report. 2004. Available online: https://priv.gg/e/ISTSLawEnforcementResearchandDevelopmentAgendaJune2004.pdf (accessed on 10 December 2022).
- Smith, E.; Corzine, S.; Racey, D.; Dunne, P.; Hassett, C.; Weiss, J. Going beyond cybersecurity compliance: What power and utility companies really need to consider. IEEE Power Energy Mag. 2016, 14, 48–56. [Google Scholar] [CrossRef]
- Liu, C.C.; Bedoya, J.C.; Sahani, N.; Stefanov, A.; Appiah-Kubi, J.; Sun, C.C.; Lee, J.Y.; Zhu, R. Cyber–Physical System Security of Distribution Systems. Found. Trends® Electr. Energy Syst. 2021, 4, 346–410. [Google Scholar] [CrossRef]
- Li, Z.; Shahidehpour, M.; Aminifar, F. Cybersecurity in Distributed Power Systems. Proc. IEEE 2017, 105, 1367–1388. [Google Scholar] [CrossRef]
- Vaidya, T. 2001–2013: Survey and Analysis of Major Cyberattacks. arXiv 2015, arXiv:1507.06673. [Google Scholar] [CrossRef]
- Hemsley, K.; Fisher, R. A History of Cyber Incidents and Threats Involving Industrial Control Systems. In Critical Infrastructure Protection XII, Proceedings of the 12th IFIP WG 11.10 International Conference, ICCIP 2018, Arlington, VA, USA, 12–14 March 2018; Springer: Berlin/Heidelberg, Germany, 2018; Volume 542. [Google Scholar] [CrossRef]
- Yohanandhan, R.V.; Elavarasan, R.M.; Manoharan, P.; Mihet-Popa, L. Cyber-Physical Power System (CPPS): A Review on Modeling, Simulation, and Analysis with Cyber Security Applications. IEEE Access 2020, 8, 151019–151064. [Google Scholar] [CrossRef]
- Baezner, M.; Robin, P. Stuxnet; Center for Security Studies (CSS), ETH Zürich: Zürich, Switzerland, 2017; pp. 1–14. [Google Scholar] [CrossRef]
- Saxena, S.; Bhatia, S.; Gupta, R. Cybersecurity Analysis of Load Frequency Control in Power Systems: A Survey. Designs 2021, 5, 52. [Google Scholar] [CrossRef]
- Case. Defense Use. Analysis of the Cyber Attack on the Ukrainian Power Grid. Electr. Inf. Shar. Anal. Cent. (E-ISAC) 2016, 388, 1–29. Available online: https://africautc.org/wp-content/uploads/2018/05/E-ISAC_SANS_Ukraine_DUC_5.pdf (accessed on 10 December 2022).
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A Survey on the Detection Algorithms for False Data Injection Attacks in Smart Grids. IEEE Trans. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Muthuppalaniappan, M.; Stevenson, K. Healthcare cyber-attacks and the COVID-19 pandemic: An urgent threat to global health. Int. J. Qual. Health Care 2021, 33, mzaa117. [Google Scholar] [CrossRef] [PubMed]
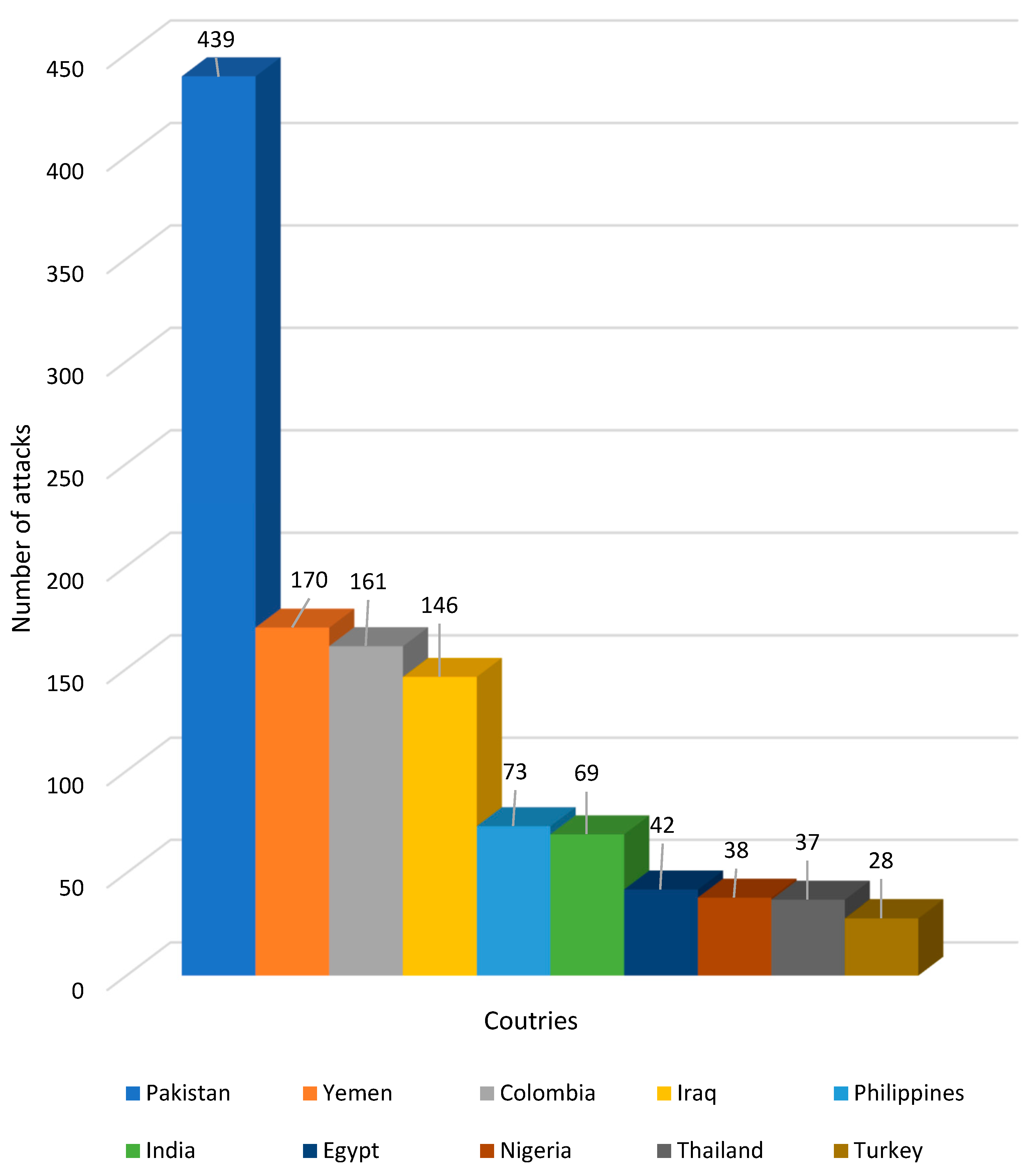
- Venkatachary, S.K.; Prasad, J.; Samikannu, R. Cybersecurity and cyber terrorism-in energy sector–a review. J. Cyber Secur. Technol. 2018, 2, 111–130. [Google Scholar] [CrossRef]
- Pate, A. Terrorism Trends with a Focus on Energy and Mining. START Res. Brief 2015, 1–2. Available online: https://www.start.umd.edu/pubs/START_TerrorismEnergyAttacks_ResearchBrief_June2015.pdf (accessed on 10 December 2022).
- Karamdel, S.; Liang, X.; Faried, S.O.; Mitolo, M. Optimization Models in Cyber-Physical Power Systems: A Review. IEEE Access 2022, 10, 130469–130486. [Google Scholar] [CrossRef]
- He, S.; Zhou, Y.; Lv, X.; Chen, W. Detection Method for Tolerable False Data Injection Attack Based on Deep Learning Framework. In Proceedings of the Chinese Automation Congress (CAC), Shanghai, China, 6–8 November 2020; pp. 6717–6721. [Google Scholar] [CrossRef]
- Du, D.; Zhu, M.; Li, X.; Fei, M.; Bu, S.; Wu, L.; Li, K. A Review on Cybersecurity Analysis, Attack Detection, and Attack Defense Methods in Cyber-Physical Power Systems. J. Mod. Power Syst. Clean Energy 2023, 11, 727–743. [Google Scholar] [CrossRef]
- Duo, W.; Zhou, M.; Abusorrah, A. A Survey of Cyber Attacks on Cyber Physical Systems: Recent Advances and Challenges. IEEE/CAA J. Autom. Sin. 2022, 9, 784–800. [Google Scholar] [CrossRef]
- Surya, S.; Srinivasan, M.K.; Williamson, S. Technological Perspective of Cyber Secure Smart Inverters Used in Power Distribution System: State of the Art Review. Appl. Sci. 2021, 11, 8780. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27. [Google Scholar] [CrossRef]
- Deng, R.; Xiao, G.; Lu, R.; Liang, H.; Vasilakos, A.V. False Data Injection on State Estimation in Power Systems—Attacks, Impacts, and Defense: A Survey. IEEE Trans. Ind. Inf. 2017, 13, 411–423. [Google Scholar] [CrossRef]
- Wang, Q.; Tai, W.; Tang, Y.; Ni, M. Review of the false data injection attack against the cyber-physical power system. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 101–107. [Google Scholar] [CrossRef]
- Brar, H.S.; Kumar, G. Cybercrimes: A Proposed Taxonomy and Challenges. J. Comput. Netw. Commun. 2018, 2018, 1798659. [Google Scholar] [CrossRef]
- Alsuwian, T.; Shahid Butt, A.; Amin, A.A. Smart Grid Cyber Security Enhancement: Challenges and Solutions—A Review. Sustainability 2022, 14, 14226. [Google Scholar] [CrossRef]
- Mejri, M.N.; Ben-Othman, J.; Hamdi, M. Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Biju, J.M.; Gopal, N.; Prakash, A.J. Cyber attacks and its different types. Int. Res. J. Eng. Technol. 2019, 6, 4849–4852. [Google Scholar]
- Neira, A.B.; Kantarci, B.; Nogueira, M. Distributed denial of service attack prediction: Challenges, open issues and opportunities. Comput. Netw. 2023, 222, 109553. [Google Scholar] [CrossRef]
- Osanaiye, O.; Choo, K.K.R.; Dlodlo, M. Distributed denial of service (DDoS) resilience in cloud: Review and conceptual cloud DDoS mitigation framework. J. Netw. Comput. Appl. 2016, 67, 147–165. [Google Scholar] [CrossRef]
- Kishore, P.K.; Ramamoorthy, S.; Rajavarman, V.N. ARTP: Anomaly based real time prevention of Distributed Denial of Service attacks on the web using machine learning approach. Int. J. Intell. Netw. 2023, 4, 38–45. [Google Scholar] [CrossRef]
- Hoque, N.; Bhattacharyya, D.K.; Kalita, J.K. Botnet in DDoS Attacks: Trends and Challenges. IEEE Commun. Surv. Tutor. 2015, 17, 2242–2270. [Google Scholar] [CrossRef]
- Kaushik, A.K.; Joshi, R.C. Network forensic system for ICMP attacks. Int. J. Comput. Appl. 2010, 2, 14–21. [Google Scholar] [CrossRef]
- Jaafar, G.A.; Abdullah, S.M.; Ismail, S. Review of Recent Detection Methods for HTTP DDoS Attack. J. Comput. Netw. Commun. 2019, 2019, 1283472. [Google Scholar] [CrossRef]
- Comer, D. Computer Networks and Internets with Internet Applications, 4th ed.; Pearson Education: Noida, India, 2004; pp. 1–719. ISBN 817758927X. [Google Scholar]
- Mahjabin, T.; Xiao, Y.; Sun, G.; Jiang, W. A survey of distributed denial-of-service attack, prevention, and mitigation techniques. Int. J. Distrib. Sens. Netw. 2017, 13, 1–33. [Google Scholar] [CrossRef]
- Salim, M.M.; Rathore, S.; Park, J.H. Distributed denial of service attacks and its defenses in IoT: A survey. J. Supercomput. 2020, 76, 5320–5363. [Google Scholar] [CrossRef]
- Alnabulsi, H.; Islam, R.; Talukder, M. GMSA: Gathering Multiple Signatures Approach to Defend Against Code Injection Attacks. IEEE Access 2018, 6, 77829–77840. [Google Scholar] [CrossRef]
- Shar, L.K.; Tan, H.B.K. Defending against Cross-Site Scripting Attacks. Computer 2012, 45, 55–62. [Google Scholar] [CrossRef]
- Yusof, I.; Pathan, A.S.K. Mitigating Cross-Site Scripting Attacks with a Content Security Policy. Computer 2016, 49, 56–63. [Google Scholar] [CrossRef]
- Cohen, F. Information system attacks: A preliminary classification scheme. Comput. Secur. 1997, 16, 29–46. [Google Scholar] [CrossRef]
- Ahmad, D.R.M.; Dubrawsky, I.; Flynn, H.; Grand, J.K.; Graham, R.; Johnson, N.L.; Kaminsky, D.E.; Lynch, F.W.; Manzuik, S.W.; Permeh, R.; et al. (Eds.) Chapter 11—Session Hijacking. Hack Proofing Your Network, 2nd ed.; Syngress: Rockland, MA, USA, 2002; pp. 407–441. [Google Scholar] [CrossRef]
- Li, Q.; Wang, F.; Wang, J.; Li, W. LSTM-Based SQL Injection Detection Method for Intelligent Transportation System. IEEE Trans. Veh. Technol. 2019, 68, 4182–4191. [Google Scholar] [CrossRef]
- Ghiasi, M.; Niknam, T.; Wang, Z.; Mehrandezh, M.; Dehghani, M.; Ghadimi, N. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: Past, present and future. Electr. Power Syst. Res. 2023, 215, 108975. [Google Scholar] [CrossRef]
- Mokhtar, B.; Azab, M. Survey on Security Issues in Vehicular Ad Hoc Networks. Alex. Eng. J. 2015, 54, 1115–1126. [Google Scholar] [CrossRef]
- Ortolani, S.; Giuffrida, C.; Crispo, B. Unprivileged Black-Box Detection of User-Space Keyloggers. IEEE Trans. Dependable Secur. Comput. 2013, 10, 40–52. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Goundar, S. Keyloggers: Silent cyber security weapons. Netw. Secur. 2020, 2020, 14–19. [Google Scholar] [CrossRef]
- Sreenivas, R.S.; Anitha, R. Detecting keyloggers based on traffic analysis with periodic behaviour. Netw. Secur. 2011, 2011, 14–19. [Google Scholar] [CrossRef]
- Sun, H.M.; Chen, Y.H.; Lin, Y.H. oPass: A User Authentication Protocol Resistant to Password Stealing and Password Reuse Attacks. IEEE Trans. Inf. Forensics Secur. 2011, 7, 651–663. [Google Scholar] [CrossRef]
- Song, J.; Wang, D.; Yun, Z.; Han, X. Alphapwd: A Password Generation Strategy Based on Mnemonic Shape. IEEE Access 2019, 7, 119052–119059. [Google Scholar] [CrossRef]
- Yu, X.; Wang, Z.; Li, Y.; Li, L.; Zhu, W.T.; Song, L. EvoPass: Evolvable graphical password against shoulder-surfing attacks. Comput. Secur. 2017, 70, 179–198. [Google Scholar] [CrossRef]
- Ye, B.; Guo, Y.; Zhang, L.; Guo, X. An empirical study of mnemonic password creation tips. Comput. Secur. 2019, 85, 41–50. [Google Scholar] [CrossRef]
- Abrishamchi, M.A.N.; Zainal, A.; Ghaleb, F.A.; Qasem, S.N.; Albarrak, A.M. Smart Home Privacy Protection Methods against a Passive Wireless Snooping Side-Channel Attack. Sensors 2022, 22, 8564. [Google Scholar] [CrossRef] [PubMed]
- Edwards, M.; Larson, R.; Green, B.; Rashid, A.; Baron, A. Panning for gold: Automatically analysing online social engineering attack surfaces. Comput. Secur. 2017, 69, 18–34. [Google Scholar] [CrossRef]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Syafitri, W.; Shukur, Z.; Mokhtar, U.A.; Sulaiman, R.; Ibrahim, M.A. Social Engineering Attacks Prevention: A Systematic Literature Review. IEEE Access 2022, 10, 39325–39343. [Google Scholar] [CrossRef]
- Lee, J.; Bagheri, B.; Kao, H.A. A Cyber-Physical Systems architecture for Industry 4.0-based manufacturing systems. Manuf. Lett. 2015, 3, 18–23. [Google Scholar] [CrossRef]
- Baheti, R.; Gill, H. Cyber-physical systems. Impact Control Technol. 2011, 12, 161–166. [Google Scholar]
- Lee, E.A. The Past, Present and Future of Cyber-Physical Systems: A Focus on Models. Sensors 2015, 15, 4837–4869. [Google Scholar] [CrossRef] [PubMed]
- Abdelmalak, M.; Venkataramanan, V.; Macwan, R. A Survey of Cyber-Physical Power System Modeling Methods for Future Energy Systems. IEEE Access 2022, 10, 99875–99896. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocess. Microsyst. 2020, 77, 103201. [Google Scholar] [CrossRef]
- Lee, J.; Lapira, E.; Bagheri, B.; Kao, H. Recent advances and trends in predictive manufacturing systems in big data environment. Manuf. Lett. 2013, 1, 38–41. [Google Scholar] [CrossRef]
- Amin, M.; El-Sousy, F.F.M.; Aziz, G.A.A.; Gaber, K.; Mohammed, O.A. CPS Attacks Mitigation Approaches on Power Electronic Systems With Security Challenges for Smart Grid Applications: A Review. IEEE Access 2021, 9, 38571–38601. [Google Scholar] [CrossRef]
- Chen, H. Applications of cyber-physical system: A literature review. J. Ind. Integr. Manag. 2017, 2, 1–28. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. Cyber physical systems security: Analysis, challenges and solutions. Comput. Secur. 2017, 68, 81–97. [Google Scholar] [CrossRef]
- Ali, S.; Balushi, T.A.; Nadir, Z.; Hussain, O.K. Cyber Security for Cyber Physical Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–174. [Google Scholar] [CrossRef]
- Hasan, M.K.; Habib, A.K.M.A.; Shukur, Z.; Ibrahim, F.; Islam, S.; Razzaque, M.A. Review on cyber-physical and cyber-security system in smart grid: Standards, protocols, constraints, and recommendations. J. Netw. Comput. Appl. 2023, 209, 103540. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Mao, X.; Li, X.; Huang, Y.; Shi, J.; Zhang, Y. Programmable Logic Controllers Past Linear Temporal Logic for Monitoring Applications in Industrial Control Systems. IEEE Trans. Ind. Informat. 2022, 18, 4393–4405. [Google Scholar] [CrossRef]
- Alphonsus, E.R.; Abdullah, M.O. A review on the applications of programmable logic controllers (PLCs). Renew. Sust. Energy Rev. 2016, 60, 1185–1205. [Google Scholar] [CrossRef]
- Tang, W.; Daoutidis, P. Distributed control and optimization of process system networks: A review and perspective. Chin. J. Chem. Eng. 2019, 27, 1461–1473. [Google Scholar] [CrossRef]
- Chen, L.; Tang, J.; Bian, X.; Zhan, S.; Lu, X.; Chang, Y. Condition assessment of distribution automation remote terminal units based on double-layer improved cloud model. Energy Rep. 2022, 8, 408–425. [Google Scholar] [CrossRef]
- Kazemi, A.A.R.; Dehghanian, P. A practical approach on optimal RTU placement in power distribution systems incorporating fuzzy sets theory. Int. J. Electr. Power Energy Syst. 2012, 37, 31–42. [Google Scholar] [CrossRef]
- Shammah, A.A.E.; El-Ela, A.A.; Azmy, A.M. Optimal location of remote terminal units in distribution systems using genetic algorithm. Electr. Power Syst. Res. 2012, 89, 165–170. [Google Scholar] [CrossRef]
- Yadav, G.; Paul, K. Architecture and security of SCADA systems: A review. Int. J. Crit. Infrastruct. Prot. 2021, 34, 100433. [Google Scholar] [CrossRef]
- Sheng, C.; Yao, Y.; Fu, Q.; Yang, W. A cyber-physical model for SCADA system and its intrusion detection. Comput. Netw. 2021, 185, 107677. [Google Scholar] [CrossRef]
- Sajid, A.; Abbas, H.; Saleem, K. Cloud-Assisted IoT-Based SCADA Systems Security: A Review of the State of the Art and Future Challenges. IEEE Access 2016, 4, 1375–1384. [Google Scholar] [CrossRef]
- Gumaei, A.; Hassan, M.M.; Huda, S.; Hassan, M.R.; Camacho, D.; Ser, J.D.; Fortino, G. A robust cyberattack detection approach using optimal features of SCADA power systems in smart grids. Appl. Soft Comput. 2020, 96, 106658. [Google Scholar] [CrossRef]
- Vanfretti, L.; Baudette, M.; White, A.D. Chapter 31—Monitoring and Control of Renewable Energy Sources Using Synchronized Phasor Measurements. Renewable Energy Integration; Academic Press: Cambridge, MA, USA, 2017; pp. 419–434. [Google Scholar] [CrossRef]
- IEEE Std C37.118.1-2011 (Revision of IEEE Std C37.118-2005); IEEE Standard for Synchrophasor Measurements for Power Systems. IEEE: Piscataway, NJ, USA, 2011; pp. 1–61. [CrossRef]
- Kiio, M.N.; Wekesa, C.W.; Kamau, S.I. Evaluating Performance of a Linear Hybrid State Estimator Utilizing Measurements From RTUs and Optimally Placed PMUs. IEEE Access 2022, 10, 63113–63131. [Google Scholar] [CrossRef]
- Azizi, S.; Gharehpetian, G.B.; Dobakhshari, A.S. Optimal Integration of Phasor Measurement Units in Power Systems Considering Conventional Measurements. IEEE Trans. Smart Grid 2013, 4, 1113–1121. [Google Scholar] [CrossRef]
- Gabbar, H.A. Chapter 2—Smart energy grid infrastructures and interconnected micro energy grids. In Smart Energy Grid Engineering; Academic Press: Cambridge, MA, USA, 2017; pp. 23–45. [Google Scholar] [CrossRef]
- Paul, S.; Ding, F.; Utkarsh, K.; Liu, W.; O’Malley, M.J.; Barnett, J. On Vulnerability and Resilience of Cyber-Physical Power Systems: A Review. IEEE Syst. J. 2022, 16, 2367–2378. [Google Scholar] [CrossRef]
- Davidson, C.; Andel, T.; Yampolskiy, M.; McDonald, T.; Glisson, B.; Thomas, T. On SCADA PLC and fieldbus cyber-security. In Proceedings of the 13th International Conference on Cyber Warfare and Security, ICCWS 2018, Washington, DC, USA, 8–9 March 2018; pp. 140–148. [Google Scholar]
- Ghaleb, A.; Zhioua, S.; Almulhem, A. On PLC network security. Int. J. Crit. Infrastruct. Prot. 2018, 22, 62–69. [Google Scholar] [CrossRef]
- Alsabbagh, W.; Langendörfer, P. A Flashback on Control Logic Injection Attacks against Programmable Logic Controllers. Automation 2022, 3, 596–621. [Google Scholar] [CrossRef]
- Han, S.; Lee, K.; Cho, S.; Park, M. Anomaly Detection Based on Temporal Behavior Monitoring in Programmable Logic Controllers. Electronics 2021, 10, 1218. [Google Scholar] [CrossRef]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security Challenges in Industry 4.0 PLC Systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- Khan, M.T.; Tomić, I. Securing Industrial Cyber–Physical Systems: A Run-Time Multilayer Monitoring. IEEE Trans. Ind. Inform. 2021, 17, 6251–6259. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, W.; Ma, T.; Tang, Z.; Xie, Y.; Gui, W.; Niyoyita, J.P. Toward security monitoring of industrial Cyber-Physical systems via hierarchically distributed intrusion detection. Expert Syst. Appl. 2020, 158, 113578. [Google Scholar] [CrossRef]
- Marino, D.L.; Wickramasinghe, C.S.; Tsouvalas, B.; Rieger, C and M. Manic. Data-Driven Correlation of Cyber and Physical Anomalies for Holistic System Health Monitoring. IEEE Access 2021, 9, 163138–163150. [Google Scholar] [CrossRef]
- Fausto, A.; Gaggero, G.B.; Patrone, F.; Girdinio, P.; Marchese, M. Toward the Integration of Cyber and Physical Security Monitoring Systems for Critical Infrastructures. Sensors 2021, 21, 6970. [Google Scholar] [CrossRef] [PubMed]
- Venkataramanan, V.; Hahn, A.; Srivastava, A. CP-SAM: Cyber-Physical Security Assessment Metric for Monitoring Microgrid Resiliency. IEEE Trans. Smart Grid 2020, 11, 1055–1065. [Google Scholar] [CrossRef]
- Li, Q.; Meng, S.; Zhang, S.; Wu, M.; Zhang, J.; Ahvanooey, M.T.; Aslam, M.S. Safety Risk Monitoring of Cyber-Physical Power Systems Based on Ensemble Learning Algorithm. IEEE Access 2019, 7, 24788–24805. [Google Scholar] [CrossRef]
- Alghassab, M. Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector. Energies 2022, 15, 218. [Google Scholar] [CrossRef]
- Choi, M.K.; Yeun, C.Y.; Seong, P.H. A Novel Monitoring System for the Data Integrity of Reactor Protection System Using Blockchain Technology. IEEE Access 2020, 8, 118732–118740. [Google Scholar] [CrossRef]
- Bin Mofidul, R.; Alam, M.M.; Rahman, M.H.; Jang, Y.M. Real-Time Energy Data Acquisition, Anomaly Detection, and Monitoring System: Implementation of a Secured, Robust, and Integrated Global IIoT Infrastructure with Edge and Cloud AI. Sensors 2022, 22, 8980. [Google Scholar] [CrossRef]
- Poltavtseva, M.; Shelupanov, A.; Bragin, D.; Zegzhda, D.; Alexandrova, E. Key Concepts of Systemological Approach to CPS Adaptive Information Security Monitoring. Symmetry 2021, 13, 2425. [Google Scholar] [CrossRef]
- Chen, C.; Zhang, K.; Ni, M.; Wang, Y. Cyber-attack-tolerant Frequency Control of Power Systems. J. Mod. Power Syst. Clean Energy 2021, 9, 307–315. [Google Scholar] [CrossRef]
- Poudel, S.; Ni, Z.; Malla, N. Real-time cyber physical system testbed for power system security and control. Int. J. Electr. Power Energy Syst. 2017, 90, 124–133. [Google Scholar] [CrossRef]
- Zhao, Y.; Chen, Z.; Zhou, C.; Tian, Y.C.; Qin, Y. Passivity-Based Robust Control Against Quantified False Data Injection Attacks in Cyber-Physical Systems. IEEE/CAA J. Autom. Sin. 2021, 8, 1440–1450. [Google Scholar] [CrossRef]
- Hegazy, H.I.; Tag Eldien, A.S.; Tantawy, M.M.; Fouda, M.M.; TagElDien, H.A. Real-Time Locational Detection of Stealthy False Data Injection Attack in Smart Grid: Using Multivariate-Based Multi-Label Classification Approach. Energies 2022, 15, 5312. [Google Scholar] [CrossRef]
- Song, J.; Huang, L.Y.; Karimi, H.R.; Niu, Y.; Zhou, J. ADP-Based Security Decentralized Sliding Mode Control for Partially Unknown Large-Scale Systems Under Injection Attacks. IEEE Trans. Circuits Syst. I. Regul. Pap. 2020, 67, 5290–5301. [Google Scholar] [CrossRef]
- Cao, Z.; Niu, Y.; Song, J. Finite-Time Sliding-Mode Control of Markovian Jump Cyber-Physical Systems Against Randomly Occurring Injection Attacks. IEEE Trans. Automat. Contr. 2020, 65, 1264–1271. [Google Scholar] [CrossRef]
- Zhang, Y.; Ma, L.; Wang, G.; Yang, C.; Zhou, L.; Dai, W. Observer-Based Control for the Two-Time-Scale Cyber-Physical Systems: The Dual-Scale DoS Attacks Case. IEEE Trans. Netw. Sci. Eng. 2021, 8, 3369–3379. [Google Scholar] [CrossRef]
- Wang, M.; Geng, Y.; Wang, J.; Liu, K.; Che, X.; Wei, Q. H∞ Control for ICPS with Hybrid-Triggered Mechanism Encountering Stealthy DoS Jamming Attacks. Actuators 2022, 11, 193. [Google Scholar] [CrossRef]
- Joo, Y.; Qu, Z.; Namerikawa, T. Resilient Control of Cyber-Physical System Using Nonlinear Encoding Signal Against System Integrity Attacks. IEEE Trans. Automat. Contr. 2021, 66, 4334–4341. [Google Scholar] [CrossRef]
- Alsokhiry, F.; Annuk, A.; Kabanen, T.; Mohamed, M.A. A Malware Attack Enabled an Online Energy Strategy for Dynamic Wireless EVs within Transportation Systems. Mathematics 2022, 10, 4691. [Google Scholar] [CrossRef]
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F. Development of a Cyber-Resilient Line Current Differential Relay. IEEE Trans. Ind. Informat. 2019, 15, 305–318. [Google Scholar] [CrossRef]
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F.; Youssef, A.M. An Intrusion Detection Method for Line Current Differential Relays. IEEE Trans. Inf. Forensics Secur. 2019, 15, 329–344. [Google Scholar] [CrossRef]
- Ameli, A.; Saleh, K.A.; Kirakosyan, A.; El-Saadany, E.F.; Salama, M.M.A. An Intrusion Detection Method for Line Current Differential Relays in Medium-Voltage DC Microgrids. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3580–3594. [Google Scholar] [CrossRef]
- Ameli, A.; Ayad, A.; El-Saadany, E.F.; Salama, M.M.A.; Youssef, A.M. A Learning-Based Framework for Detecting Cyber-Attacks Against Line Current Differential Relays. IEEE Trans. Power Deliv. 2021, 36, 2274–2286. [Google Scholar] [CrossRef]
- Saber, A.M.; Youssef, A.; Svetinovic, D.; Zeineldin, H.H.; El-Saadany, E.F. Anomaly-Based Detection of Cyberattacks on Line Current Differential Relays. IEEE Trans. Smart Grid 2022, 13, 4787–4800. [Google Scholar] [CrossRef]
- Ganjkhani, M.; Hosseini, M.M.; Parvania, M. Optimal Defensive Strategy for Power Distribution Systems Against Relay Setting Attacks. IEEE Trans. Power Deliv. 2022, 38, 1499–1509. [Google Scholar] [CrossRef]
- Rajaee, M.; Mazlumi, K. Multi-Agent Distributed Deep Learning Algorithm to Detect Cyber-Attacks in Distance Relays. IEEE Access 2023, 11, 10842–10849. [Google Scholar] [CrossRef]
- Gutierrez-Rojas, D.; Demidov, I.; Kontou, A.; Lagos, D.; Sahoo, S.; Nardelli, P.J. Operational Issues on Adaptive Protection of Microgrids due to Cyber Attacks. IEEE Trans. Circuits Syst. II Express Briefs 2023. [Google Scholar] [CrossRef]
- Nuqui, R.; Hong, J.; Kondabathini, A.; Ishchenko, D.; Coats, D. A Collaborative Defense for Securing Protective Relay Settings in Electrical Cyber Physical Systems. In Proceedings of the Resilience Week (RWS), Denver, CO, USA, 20–23 August 2018; pp. 49–54. [Google Scholar] [CrossRef]
- Ahmed, A.; Krishnan, V.V.G.; Foroutan, S.A.; Touhiduzzaman, M.; Rublein, C.; Srivastava, A.; Wu, Y.; Hahn, A.; Suresh, S. Cyber Physical Security Analytics for Anomalies in Transmission Protection Systems. IEEE Trans. Ind. Appl. 2019, 55, 6313–6323. [Google Scholar] [CrossRef]
- Kaur, J.; Ramkumar, K.R. The recent trends in cyber security: A review. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 5766–5781. [Google Scholar] [CrossRef]
- Feng, H.; Tavakoli, R.; Onar, O.C.; Pantic, Z. Advances in High-Power Wireless Charging Systems: Overview and Design Considerations. IEEE Trans. Transp. Electrif. 2020, 6, 886–919. [Google Scholar] [CrossRef]
- Sanghvi, A.; Markel, T. Cybersecurity for Electric Vehicle Fast-Charging Infrastructure. In Proceedings of the 2021 IEEE Transportation Electrification Conference & Expo (ITEC), Chicago, IL, USA, 21–25 June 2021. [Google Scholar] [CrossRef]
- Leszczyna, R. Standards on cyber security assessment of smart grid. Int. J. Crit. Infrastruct. Prot. 2018, 22, 70–89. [Google Scholar] [CrossRef]
- Brown, B.; Singletary, B.; Willke, B.; Bennett, C.; Highfill, D.; Houseman, D.; Cleveland, F.; Lipson, H.; Ivers, J.; Gooding, J.; et al. AMI System Security Requirements; v1.01; Technical Report; 2008. Available online: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/14-AMI_System_Security_Requirements_updated.pdf (accessed on 25 February 2023).
- Schlegel, R.; Obermeier, S.; Schneider, J. A security evaluation of IEC 62351. J. Inf. Secur. Appl. 2017, 34, 197–204. [Google Scholar] [CrossRef]
- Christensen, D.; Martin, M.; Gantumur, E.; Mendrick, B. Risk Assessment at the Edge: Applying NERC CIP to Aggregated Grid-Edge Resources. Electr. J. 2019, 32, 50–57. [Google Scholar] [CrossRef]
- Parks, R.C.; Rogers, E. Vulnerability Assessment for Critical Infrastructure Control Systems. IEEE Secur. Priv. 2008, 6, 37–43. [Google Scholar] [CrossRef]
- NISTIR 7628: Guidelines for Smart Grid Cyber Security: Smart Grid Cyber Security Strategy, Architecture, and High-Level Requirements; The Smart Grid Interoperability Panel–Cyber Security Working Group: Washington, DC, USA, 2010. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2010/NIST.IR.7628.pdf (accessed on 25 February 2023).
- IEEE Std 2030.2-2015; IEEE Guide for the Interoperability of Energy Storage Systems Integrated with the Electric Power Infrastructure. IEEE: Piscataway, NJ, USA, 2015; pp. 1–138. [CrossRef]
- IEEE Std C37.240-2014; IEEE Standard Cybersecurity Requirements for Substation Automation, Protection, and Control Systems. IEEE: Piscataway, NJ, USA, 2015; pp. 1–38. [CrossRef]
| Method | Attack Point | Purpose | Field of Application | Simulation | Reference |
|---|---|---|---|---|---|
| Multilayer Run-Time Security Monitor | Application and communication layer attacks. | Identify divergences caused by communications and application layer attacks and prevent propagation to other control layers. | ICPSs | Water distribution system. | [115] |
| Regularized sparse deep belief network (RSDBN) model is adopted; noise-adaptive Kalman filter | Hierarchically distributed attack in ICPS layers, perception, and application layer. | Identify potential cyberattacks through hierarchically distributed intrusion detection. | ICPSs | Numerical simulation on an ICPS platform with OPNET and benchmark simplified Tennessee Eastman process | [116] |
| Three unsupervised machine-learning algorithms: OCSVMs, LOF, and AEs | Network scanning, denial of service, and malicious command data injection. | Detection of cyber and physical anomalies. | Critical infrastructure of the CPS | IEEE-33 bus model | [117] |
| Machine-learning algorithms | Critical Infrastructure Attack | Cyber and physical anomaly detection | Critical infrastructure of the CPS | Power plant | [118] |
| Multicriteria decision-making (MCDM), Choquet Integral in compute CP-SAM | Malicious and accidental microgrid failures | Increase the resiliency, reliability, and security of a microgrid by creating a robust cybersecurity assessment metric. | Cyber–power system | The test was performed using a real microgrid model | [119] |
| Big data platform architecture for log analysis for CPS and prediction algorithm based on time series | Log anomalies | Propose and implement a log analysis architecture capable of identifying and detecting anomalies in the power system. | Hydropower generation control networks | The tests were run with a real dataset from a CPS recorded over 3 months | [120] |
| Fuzzy hesitant methodology of the Analytic Hierarchy Process (AHP) and the Technique for Order of Preference by Similarity to Ideal Solution (TOPSIS) | On data availability, integrity, and confidentiality. | Analyze and estimate assessments through an operational procedure for the cybersecurity of the industrial system. | Industrial control system in the energy sector | Computational simulation of six different alternatives | [121] |
| Blockchain Technology | Malicious attack of false data injection into PLC. | Accurately monitor data and protect the PLC against cyberattacks. In addition, a system is proposed to ensure the operation of the Reactor Protection System. | Isolated networks of nuclear power plants | The proposed approach is tested through an experiment that injects dummy data into PLCs | [122] |
| AI algorithms | Real-time detection of anomalies in electrical appliances. | Data acquisition, fault identification, management, and real-time monitoring of energy data based on AI algorithms. | Industrial Internet of Things | Hardware design, server, and database creation in open source and computer simulation | [123] |
| Adaptive method and multicriteria optimization | Cyberattacks and network traffic anomaly detection. | Creating an adaptive system to manage and monitor information security. | CPS | Experimental study of intelligent home intrusion detection | [124] |
| Method | Attack Point | Purpose | Field of Application | Simulation | Reference |
|---|---|---|---|---|---|
| Model Predictive Control | Cyberattacks of denial of service and fake data injection types | Develop a frequency control approach tolerant to cyberattacks. | Frequency Control of power systems. | The controller was tested on an IEEE benchmark system. | [125] |
| Adaptive control based on real-time CI (Computational intelligence). | Cyberattacks on the power system. | It presents a real-time testing methodology for analyzing and controlling power system stability and cybersecurity. | Power System | The test methodology was designed based on OPAL-RT and the SEL351S protection system. | [126] |
| Robust controller based on Port Controlled Hamiltonian with dissipation (PCHD) | False data injection attacks | A defense approach based on the energy conversion perspective. | Control system for a permanent-magnet synchronous motor. | The proposed approach is tested on an industrial CPS that controls a synchronous machine. | [127] |
| Long Short-Term Memory (LSTM) with Temporal Convolutional Neural Network (TCN) | False data injection attacks | A multivariate approach capable of accurately detecting the injection of false data into the CPS in real-time. | Smart Grid Control System | The performance of the designed framework is verified using an IEEE system and trained with Tensorflow libraries using Keras. | [128] |
| Sliding mode controller (SMC) methodology based on Adaptive Dynamic Programming (ADP) | False data injection attacks | A decentralized control approach to large-scale system security was developed to mitigate the effects of unknown injection attacks. | Decentralized Optimal Control Problem | The test was performed on a two-machine Energy system subjected to 3 separate attacks. | [129] |
| Designs a finite time interval sliding mode controller for Markovian hopping systems | Random injection attacks | A control approach that supports probabilistic injection of false data. | Markovian jump cyber–physical systems | The test was performed with single-link robot arm model. | [130] |
| Observer-based controller | DoS attacks | Proposes a control algorithm approach that is not vulnerable to DoS attacks. | A class of two-timescale cyber–physical systems | The effectiveness of the proposed approach was tested in two types: Comparison Simulation and through the inverted pendulum system controlled by a DC motor. | [131] |
| H∞ controller | DoS attacks | Performs a design study of the H∞ controller to mitigate the effects of the DoS attack. | ICPSs | To demonstrate the effectiveness of the proposed approach, numerical simulations are performed. | [132] |
| Resilient control by dynamic nonlinear encoding/decoding and chaotic oscillators. | Malicious attacks, stealthy system integrity attacks, and eavesdropping | It develops a control framework with devices for encoding and decoding disordered signals that can identify stealthy attacks on the cyber–physical system. | ICPSs | For testing and validation of the proposed approach, simulations are performed for the quadruple-tank process. | [133] |
| Offense–defense game model | Malware attacks | Presents an online technique based on the offense-defense game model capable of identifying these malware attacks. | Electrical vehicles | Numerical and dynamic simulation in GAMS and MATLAB software. | [134] |
| Method | Attack Point | Purpose | Field of Application | Simulation | Reference |
|---|---|---|---|---|---|
| Based on the differences between the calculated and measured overlapping voltages for LCDRs | Injection of false data into LCDRs | The proposed methodology aims to detect the types of injections of false data against LCDRs. | LCDRs | The developed methodology is validated using the IEEE-39 bus model and the OPAL simulator. | [135] |
| A state observer with unknown input | Injection of false data into LCDRs | Detect injection of false data and distinguish it from internal LCDRs operational failures. | LCDRs | The developed methodology is validated using the IEEE-39 bus model. | [136] |
| The developed method consists of passive oscillator circuits | Injection of false data into LCDRs | Presents a study on the impacts of attacks on time synchronization and false data in microgrids and acts to solve the problem from the physical perspective. | LCDRs | The proposed method is analyzed in simulation and validated through numerical analysis. | [137] |
| Model-based on intelligent learning with Multilayer Perceptron | Injection of false data into LCDRs | The detection of cyberattacks against LCDRs is performed using a learning-based framework. | LCDRs | The developed methodology is confirmed using the IEEE-39 bus model. | [138] |
| The anomaly-based framework that employs the Isolation Forest algorithm | Injection of false data into LCDRs | Detect cyberattacks and differentiate from a fake attack on systems that use LCDRs as protection. | LCDRs | The developed methodology is validated in benchmark IEEE 9-bus in PSCAD/EMTDC environment. | [139] |
| Methodology based on game theory | Cyberattack on relay configuration in power distribution systems | Ability to detect the best defense plan and mitigate the damage to the protection relays. | Power distribution system | The developed methodology is tested on the IEEE 123-node test feeder. | [140] |
| Multi-Agent Distributed Deep Learning | Injection of false data to the relays | This technique can detect the injection of false data to the relays before it simulates a false fault. | The protection system of a power grid. | The proposed cyberattack detection method is tested on the electrical networks: IEEE 6-bus, IEEE 14-bus, and IEEE 118-bus. | [141] |
| Adaptive technique | Injection of false data to the relays | This methodology has the objective of mitigating false attacks on the protection relays and avoiding power interruptions in the grid. | Protection relays | A real-time digital simulator was used to validate the proposed approach. | [142] |
| Rule-based algorithm and the principle of relay coordination | Malicious attacks on the protection relays | It presents a defense strategy against malicious attacks and unwanted modifications to the protection relays. | Protection relays | The proposed technique is tested and validated on a framework with relays and a real-time digital simulator for cyber–physical systems. | [143] |
| Recurrent neural network with LSTM cells | Cyberattacks and protection system anomalies | Intelligent algorithm with the ability to monitor and detect in real time the anomalies of the protection system caused by malicious attacks. | Transmission protection systems | The proposal is validated on the IEEE test system with relays. | [144] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ribas Monteiro, L.F.; Rodrigues, Y.R.; Zambroni de Souza, A.C. Cybersecurity in Cyber–Physical Power Systems. Energies 2023, 16, 4556. https://doi.org/10.3390/en16124556
Ribas Monteiro LF, Rodrigues YR, Zambroni de Souza AC. Cybersecurity in Cyber–Physical Power Systems. Energies. 2023; 16(12):4556. https://doi.org/10.3390/en16124556
Chicago/Turabian StyleRibas Monteiro, Luiz Fernando, Yuri R. Rodrigues, and A. C. Zambroni de Souza. 2023. "Cybersecurity in Cyber–Physical Power Systems" Energies 16, no. 12: 4556. https://doi.org/10.3390/en16124556
APA StyleRibas Monteiro, L. F., Rodrigues, Y. R., & Zambroni de Souza, A. C. (2023). Cybersecurity in Cyber–Physical Power Systems. Energies, 16(12), 4556. https://doi.org/10.3390/en16124556