1. Introduction
Digital assets that combine cash and cryptography are known as cryptocurrencies. Peer-to-peer networks and public blockchains are frequently the foundations of cryptocurrencies, allowing network participants to validate financial transactions [
1]. The majority of cryptocurrencies are decentralized, which has several benefits over conventional centralized financial systems, including quick transactions and minimal transaction fees [
2]. Since Bitcoin was the first cryptocurrency to be established back in 2008, the terms, cryptocurrency (decentralized digital assets that use cryptographic functions) and digital coin (centralized digital assets), are frequently used interchangeably [
3]. The cryptocurrency market has grown since the introduction of Bitcoin, and as of now, there are over 17,000 distinct cryptocurrency projects, of which, over 9000 are active [
4]. There were more than 1800 full-time workers and a market value of over
$1.7 trillion for cryptocurrencies in February 2022 [
4]. Controversy remains regarding whether cryptocurrencies should be considered a method of payment or a high-risk investment. The interest in cryptocurrencies has largely risen in recent years, despite some criticism of their volatility [
5]. Cryptocurrencies are both lauded as decentralized transaction mediums and debated due to barriers like limited everyday use and regulatory challenges. While they promise a decentralized payment alternative, their role as a primary payment method remains contested. Additionally, cryptocurrencies, especially Bitcoin, have gained attention as speculative investments, promising high rewards. However, their marked price volatility raises concerns about their stability and value, leading some to question their reliability as a store of wealth. Despite skepticism, the increasing appeal of cryptocurrencies is fueled by factors like institutional acceptance, blockchain advancements, distrust in traditional banking, and global digitization. This positions them prominently in financial discourse [
6].
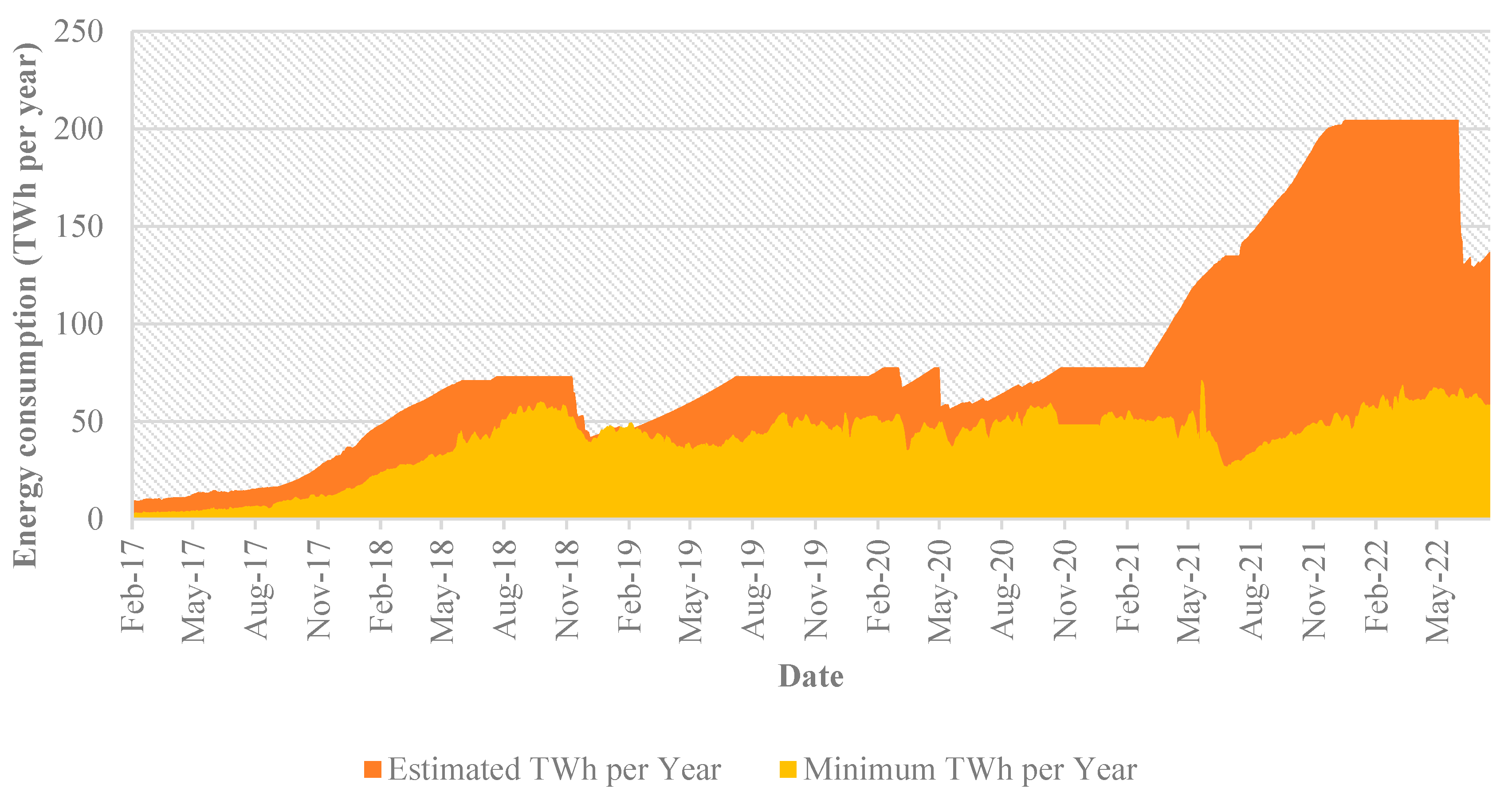
Concerns about cryptocurrencies’ excessive power usage have been raised by their expanding marketplaces [
7]. Because of the notoriously energy-intensive roof of Work consensus method used by Bitcoin, some studies have calculated that the network’s electricity consumption is comparable to that of whole countries like Ireland and Austria [
8]. Since Bitcoin dominates the crypto markets and accounts for 41.9% of market value, several research have concentrated on it (20 February 2022) [
4]. To place the energy use and CO
2 emissions of cryptocurrencies in the present and the future, however, a correct perspective on the crypto markets beyond Bitcoin and Proof of Work is required as the market share for new projects increases [
9].
Recent decades have seen an increase in both worldwide energy consumption and CO
2 emissions [
10], and according to the International Energy Agency (IEA), CO
2 emissions from the generation of electricity in 2021 grew globally by 7% [
11]. The energy use and carbon impact of the Bitcoin marketplace are also expanding. However, new projects using novel consensus algorithms, such as Ethereum 2.0, Cardano, Algorand, Chia Network, may be employed to grow markets without endangering the environment [
12].
In recent years, alongside the meteoric rise and adoption of cryptocurrencies, there has been growing discourse concerning their ecological implications. The decentralized nature of these digital assets, while groundbreaking in many respects, has also been a source of concern from an environmental standpoint [
13]. Cryptocurrency operations, especially those utilizing energy-intensive consensus algorithms like Proof of Work, have been linked to significant energy consumption, often sourced from non-renewable power plants, resulting in substantial carbon footprints. As digital assets become more integrated into our global financial systems, it is crucial to holistically understand and address their environmental impacts. This study seeks to shed light on this pertinent issue by exploring various cryptocurrency projects and their ecological ramifications.
Because various cryptocurrencies have varying consensus procedures and technology requirements, it has proven challenging to quantify the energy usage of cryptocurrencies. While it is true that the decentralized nature of blockchain networks makes it inherently difficult to determine the precise location and energy sources of all nodes and miners, advancements in surveillance and regulations have allowed certain states to identify and monitor major mining operations. Nevertheless, given the global and dispersed nature of the network, obtaining a comprehensive and exact calculation of the resource and energy mix powering every node remains a challenge. Localized data may be available in regions with concentrated mining activities, but a complete global overview remains elusive.
1.1. Research Question
The following research question is used to study and analyze the current cryptocurrency marketplaces outside of Bitcoin as well as the energy use and carbon footprint of cryptocurrency projects: how do the energy consumption and CO2 emissions of diverse cryptocurrency projects, driven by their underlying consensus algorithms, compare to traditional payment methods, and what influence do financial determinants, especially in the context of Bitcoin, have on these environmental metrics?
More in-depth analysis of the technology used in various projects would have been outside the purview of this study. This study explores cryptocurrency from an ecological standpoint. Nine distinct projects were chosen due to the vast number of cryptocurrencies, on the basis of their market size, consensus method, and data accessibility. The secondary energy used in producing and cooling hardware is not considered because of a lack of information.
There are six sections in this paper.
Section 2 introduces blockchain technology and cryptocurrencies, while
Section 3 does the same for consensus algorithms and a few specific crypto projects. The energy consumption of the projects is reviewed in the fourth section, and in the fifth section, energy consumption and CO
2 emissions of cryptocurrency projects are discussed. The results of this investigation are summarized in
Section 6.
1.2. Methodology
Our study employed a mixed-methods approach, combining quantitative analysis of data gathered from blockchain networks and qualitative analysis of academic literature, industry reports, and expert opinions on the environmental impact of cryptocurrencies. Data were collected from prominent blockchain explorers, while peer-reviewed articles and industry publications provided insights into consensus algorithms, energy consumption patterns, and CO2 emissions ratings.
1.3. Disclaimer
This review paper delves into specific environmental implications of blockchain technology, particularly focusing on energy consumption and carbon emissions associated with cryptocurrency projects. While there are various environmental facets to consider with blockchain and cryptocurrencies, our primary lens for this research is on their energy consumption patterns and resultant carbon footprints. It is essential to clarify that this study neither provides financial nor investment advice. Consequently, while our research emphasizes environmental impacts, it does not delve into the economic performance, volatility, security, or reliability of cryptocurrencies. Readers should not interpret the information presented herein as guidance for financial or investment decisions.
2. Blockchain Technology
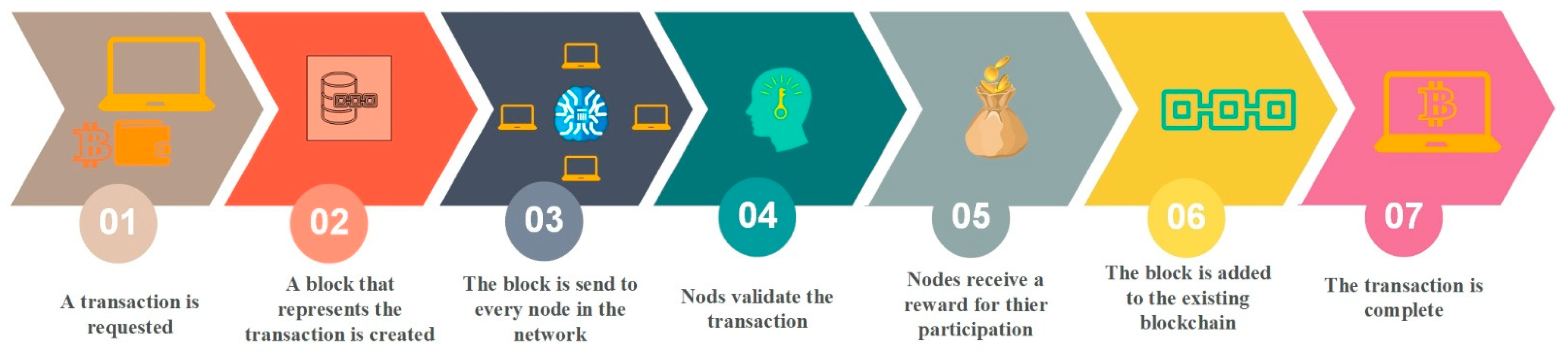
Despite the fact that the technology may be applied in various contexts, the majority of cryptocurrencies are based on blockchain technology, and blockchains are frequently linked to cryptocurrencies. A ledger or chain of blocks used to store data might be referred to as a blockchain [
14]. Transactions, data records, and executables may all be included in the data kept on the blockchain. A blockchain is made up of transactions that are combined into blocks using encryption in the case of conventional cryptocurrencies like bitcoin. The chain is created by cryptographically connecting each block to the one before it. A so-called ‘peer-to-peer’ (P2P) network is then created, with the chain being maintained by nodes and distributed to all network users. If the block’s data are changed later, the chain will ‘break’, since the block’s encryption has changed.
Figure 1 depicts the operation of a blockchain [
15].
Blockchain technology is used by cryptocurrencies to keep track of network transactions and to establish consensus among users. Blockchains may be grouped according to their many characteristics. Blockchains can be public, private, or somewhere in between, with or without permissions. Anyone can publish blocks without a third party’s approval in a permissionless blockchain network [
16]. The majority of these blockchains are constructed on top of them and are open-source and freely accessible to everyone. The permissionless blockchain network allows all users to read from and write to the ledger, and the blockchain is open to all network participants. Permissionless blockchain networks frequently utilize a multiparty agreement or consensus method with certain restrictions for users who seek to publish blocks in order to avoid abuse and efforts to publish fraudulent blocks [
17]. Later in this work, several of these consensus algorithms are covered.
On the other hand, before releasing blocks, centralized or decentralized authors must provide their approval in permissioned blockchain networks [
17]. Given that the creator controls who has access to and control over the network, read access and submitting transactions may or may not be prohibited in a network like this. The majority of these networks employ consensus techniques for publishing blocks; thus, permissioned networks can nonetheless have the same openness and traceability as permissionless networks. Due to the administrators’ preexisting degree of confidence inside the network, consensus techniques utilized in permissioned networks frequently have less requirements than in permissionless networks. Due to the lack of complex consensus mechanisms, permissioned blockchain networks are frequently quicker and less computationally costly.
The majority of cryptocurrencies, including the two biggest, Bitcoin and Ethereum, are public blockchain instances. Everyone on the blockchain network may read transaction information on a public blockchain, making it accessible to all users. Public blockchains are intended to be completely transparent and decentralized, which means that no one and nothing is in charge of them. The system is maintained via the peer-to-peer network, which also verifies new blocks added to the chain. Due to the widespread distribution of users and the blockchain, public blockchain networks are resilient to single points of failure. The blockchain network can continue to function even if one of its servers is offline since the others are still running [
18]. Without a single point of authority, the network must use consensus techniques to reach agreement on verifying transactions and new blocks [
14]. Permissioned and permissionless public blockchain are both possible.
Private blockchains are more centralized than public blockchains since they are used to transfer data between corporations, for instance. Private blockchains are permissioned networks because the data they store are not publicly accessible. The blockchain economy is only accessible to authorized parties. Not all private blockchains have a token [
18]. Although some cryptocurrencies have features a the public blockchain and some, of a private blockchain, they are not entirely decentralized.
2.1. Smart Contract and Decentralized Apps
Within the expanding realm of blockchain technology, the introduction of ‘smart contracts’ and ‘decentralized apps (dApps)’ stands out as a transformative innovation. At its core, a smart contract is a self-executing contract embedded with the terms of the agreement between buyer and seller. These terms are written into lines of code, which reside on the blockchain network. What sets smart contracts apart is their ability to automatically execute or enforce themselves when specific, pre-defined conditions or criteria are met, without the need for intermediaries [
19]. Decentralized apps, commonly known as dApps, leverage the principles of smart contracts and are applications that run on a blockchain or P2P network of computers [
20]. Unlike traditional applications that run on centralized servers, dApps are inherently resistant to tampering and censorship due to their decentralized nature. These applications function without a central authority, thus enhancing their security and potentially reducing risks of censorship or control by a single entity. In the contemporary digital landscape, dApps have found diverse applications ranging from decentralized social media platforms to gaming ecosystems, and their operation is underpinned by the automatic execution feature of smart contracts.
2.2. Hash Functions
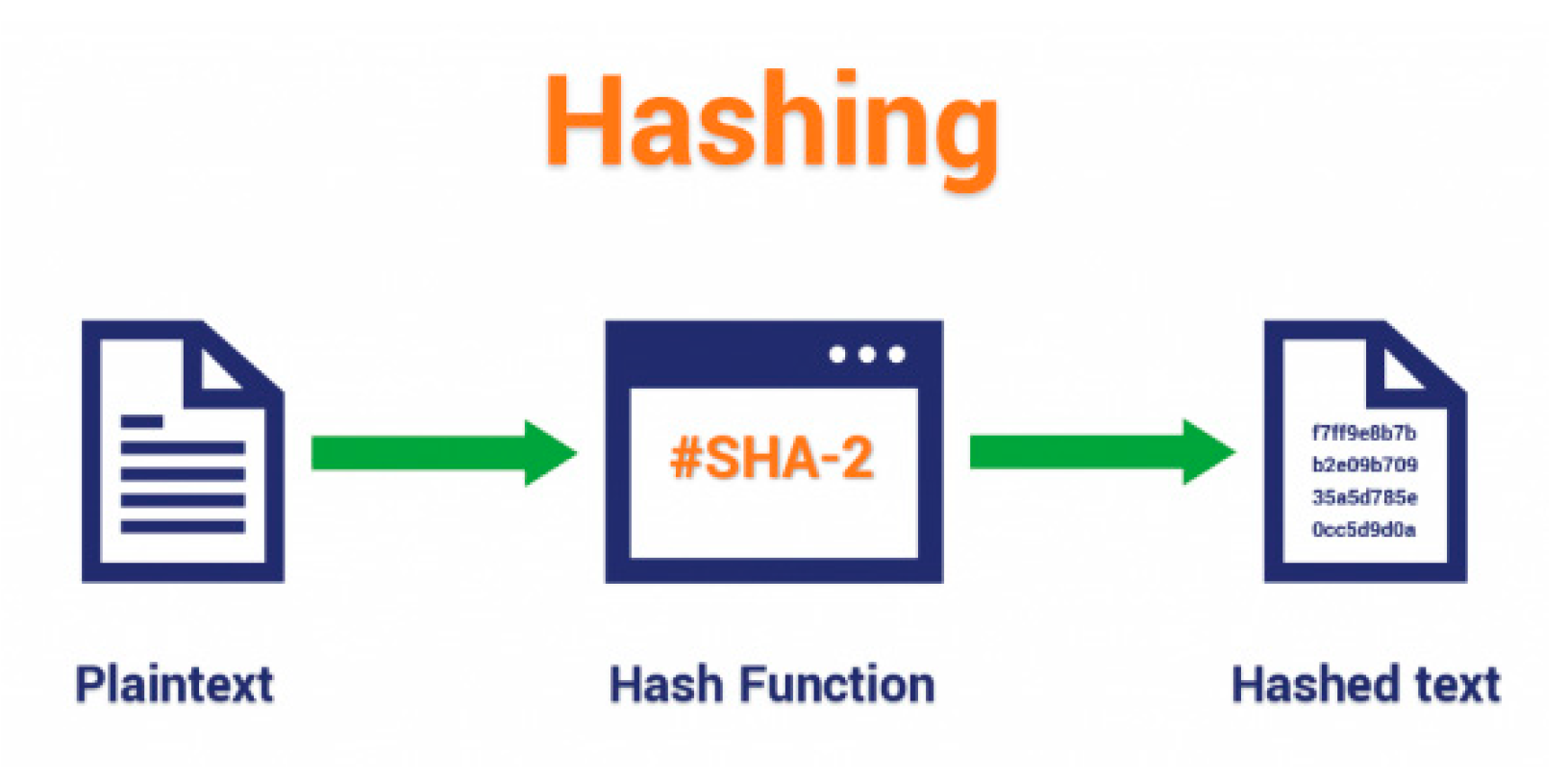
The underlying idea behind hash functions, which have been around for a while in computer science, is to compress any type of string into an output string with a fixed length [
21]. To protect and compress data, a block uses hash algorithms. Given only the output value and a cryptographic hash function, it is computationally impossible to determine the input value [
17]. Additionally, finding two distinct inputs that would result in the same output is either impossible or extremely rare. There is an infinite number of inputs, but a finite number of outputs; hence, there is a probability of collision. When anything is processed through a hash function, the same input value always results in the same output, yet even a minor change in the input value causes the entire output to change (one example of SHA-256 hashing function, input: Hello, Output: 185f8db32271fe25f561a6fc938b2e264306ec304eda518007d1764826381969).
Figure 2 presents an example of how the hashing process works.
Several hash functions are employed by different blockchain implementations and cryptocurrency projects. The Secure Hash Algorithm (SHA), particularly the SHA-256 variant, is widely used in many applications due to its speed and compatibility with most computers. Bitcoin, the pioneer cryptocurrency, is a well-known project that employs the SHA-256 hash function. Solana, on the other hand, is a more recent and innovative blockchain platform designed for high throughput and scalability. While it also uses SHA-256 as its hash mechanism, what differentiates Solana is its unique ‘Proof of History’ consensus mechanism. This allows the Solana network to achieve higher transaction speeds without compromising security. Another standout feature is Solana’s capability to process 65,000 transactions per second, significantly higher than many existing blockchains, making it an attractive platform for various decentralized applications and projects [
23]. The function name’s inclusion of the number 256 denotes that the output will always be 256 bits, or 32 bytes. Usually, 64-character strings are shown like these outputs [
17].
Cryptocurrencies often rely on cryptographic hash functions to maintain security and data integrity within their networks. While many cryptocurrencies use popular hash functions like SHA-256, some projects, in their pursuit of unique features or enhanced security, create their own hashing algorithms. IOTA was one such project that initially used its proprietary hash function, Curl-P-27. However, in 2017, a team of researchers identified vulnerabilities within the Curl-P-27 hash function, making it susceptible to potential attacks. The primary defect was that it did not guarantee ‘collision resistance’, a fundamental property where two different inputs should not produce the same output. Recognizing the security implications, IOTA transitioned from Curl-P-27 to Kerl, a variant of the widely acknowledged Keccak-384 algorithm [
24]. Yet, this transition was not without its own set of controversies. An online user later reported discovering a collision in Kerl, which sparked significant criticism and concerns over the security and reliability of the hashing method chosen by IOTA. It underlines the complexities and challenges projects face in either opting for proprietary algorithms or modifying established ones [
25].
Ethereum, the second-largest cryptocurrency project, also employs the original Keccak-384 hash mechanism [
26]. Hashing is the process of entering input values into a hash function and retrieving output values. A hash value, or just a hash, is the name given to the hash function’s result [
27]. The phrase, ‘hash rate’, refers to how much hashing occurs in the Bitcoin network per second. It varies greatly depending on the hardware and methods employed.
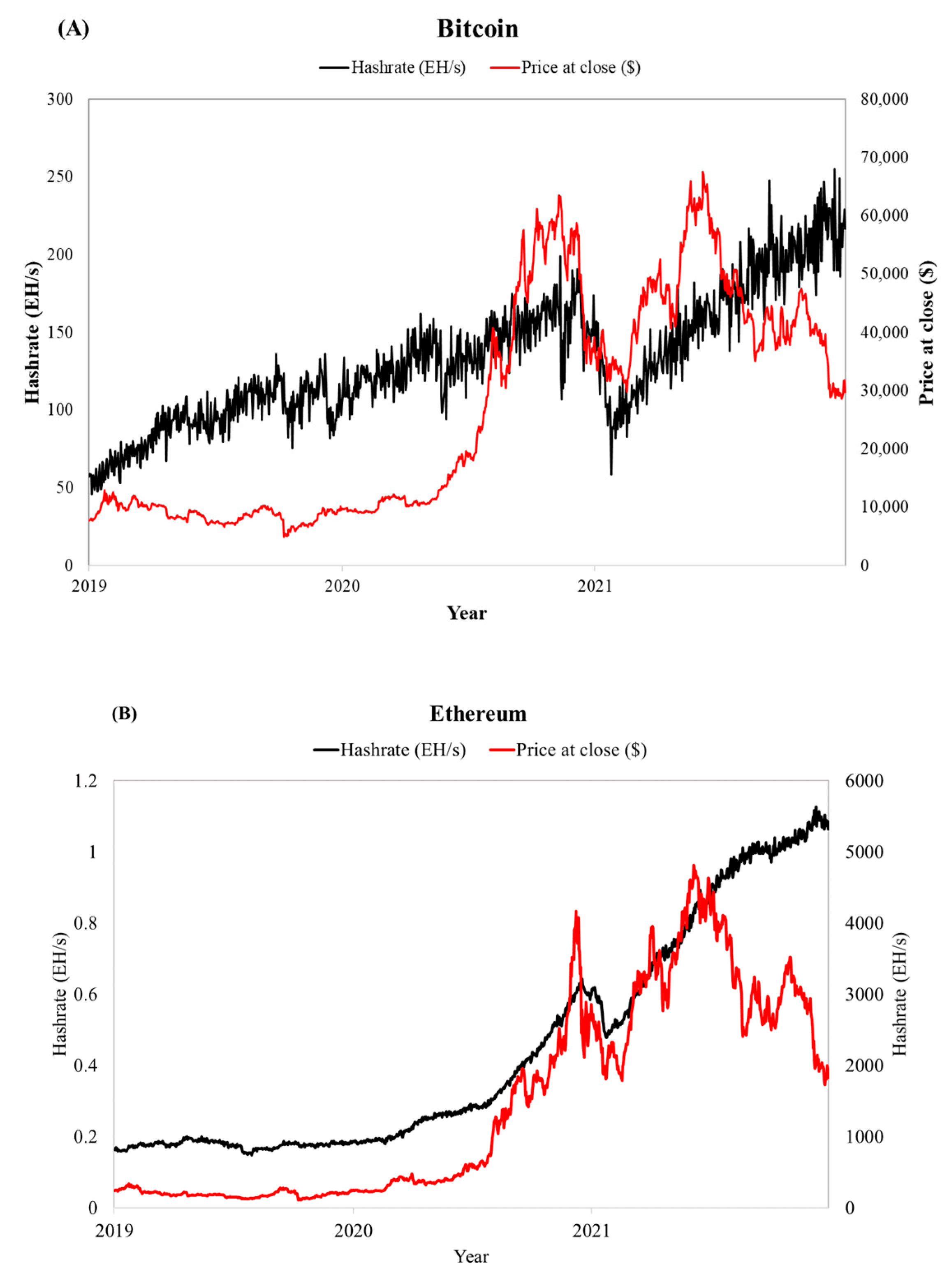
Figure 3 shows network hashrates and coin exchange prices in USD for Bitcoin
Figure 3A and Ethereum
Figure 3B (BTC hashrate: [
28]; ETH hashrate: [
29], Ref. for price: [
4]). While this paper delves into the intricacies of cryptocurrencies, blockchain technology, and their consequential environmental impacts, it is crucial to recognize the vastness of this domain. The subsequent section provides a focused overview of roles and methods that influence the energy consumption of cryptocurrency. However, it is worth noting that the environmental implications of cryptocurrencies and blockchain technology extend beyond just energy consumption. There are multiple layers of complexity and myriad factors that could further affect the environment. Due to the scope of this review, not all of these factors are exhaustively discussed. It is always recommended for readers and researchers to explore further, taking a holistic view of the potential environmental ramifications.
2.3. Problems and Limitations
There are several issues and restrictions when analyzing cryptocurrencies and their effects on the environment. One is that it is impossible to determine the precise number of Bitcoin users [
27]. User numbers are challenging to estimate since a single user may have many wallets for various tokens. According to the Global Cryptocurrency Benchmarking Study, there were between 2.9 million and 5.8 million unique wallet users in 2017, yet there were up to 35 million active wallets [
27]. Furthermore, as nodes might be single devices or groups of devices, it is challenging to monitor their energy usage [
8].
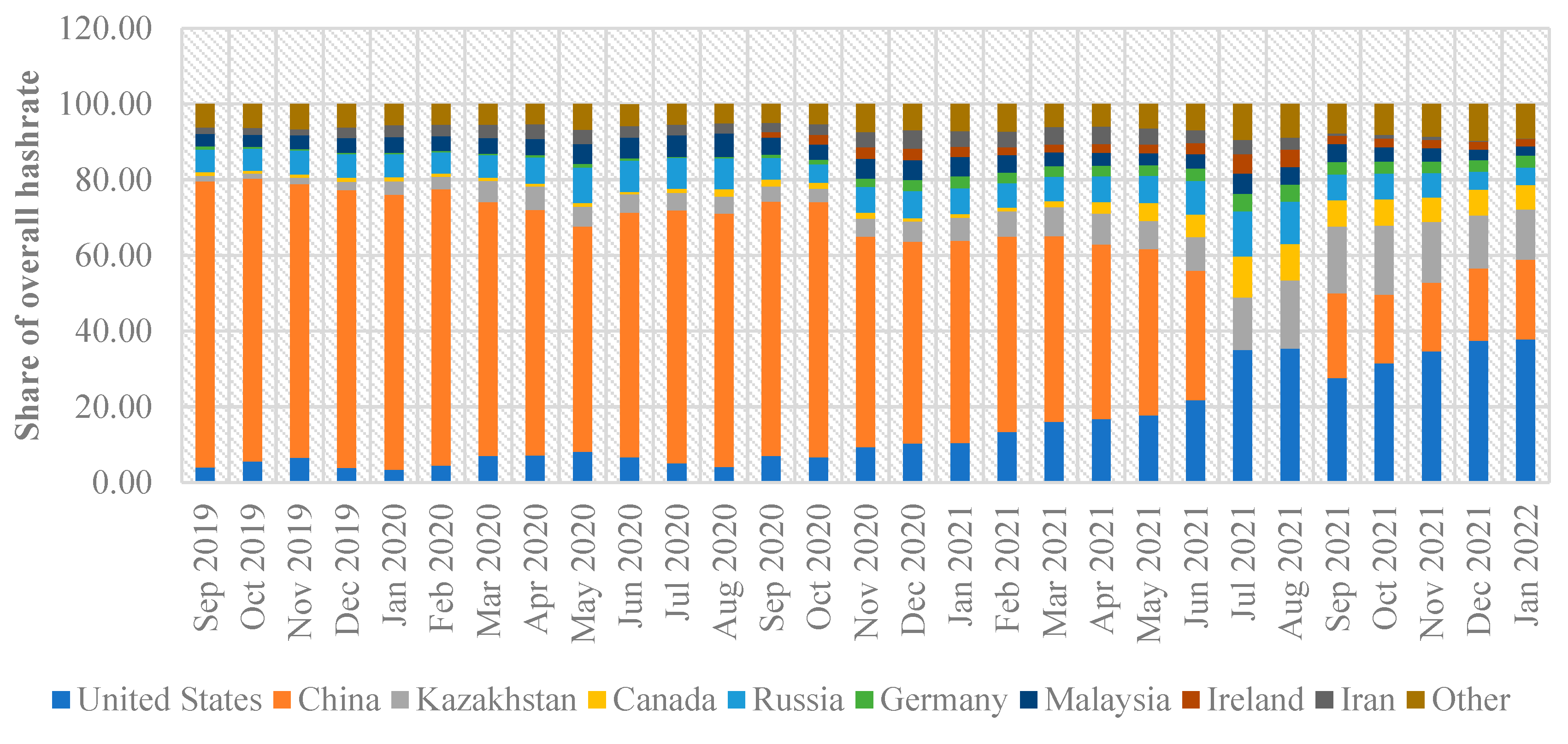
The location of Bitcoin miners and consumers is another issue. Users and miners can be located anywhere in the world, since cryptocurrencies are decentralized. Additionally, the geographical location and actual number of miners are anonymous because of the encryption [
30]. Even while some mining pools make their location known, mining is not necessarily required to take place in the pool that is nearby. A miner from China or Europe may join a pool there. The carbon footprint varies by location due to the consumption of power from various sources. Several mining pools in China were found in 2017 by the Global Cryptocurrency Benchmarking Study, despite the fact that the bulk of miners’ whereabouts remain undisclosed [
27].
The third issue is the market dramatically shifting. While some projects are terminated, others are being replaced. Additionally, market capitalization is subject to rapid change. It is challenging to analyze important currencies in rapidly shifting markets since both market share and market capitalization are subject to change at any time.
The overall consumption is the fourth issue. Although several studies have estimated the amount of power consumed for transactions and mining, it is impossible to ascertain the total network usage due to various hardware regulations. Due to a lack of knowledge, many estimates do not take into account the efficiency of the power usage by the mining equipment or the energy consumption by the cooling systems [
8]. The Global Cryptocurrency Benchmarking Study was able to identify certain pools that were in climates where cooling would not be necessary; however, as was noted before, owing to the anonymity of miner locations, it is nearly difficult to track the energy use of the cooling systems [
27].
Given that the carbon intensity of the relevant grid varies globally, proper assessment of carbon footprint would require location information [
27]. From a few grams to over 800 g per kWh, the carbon intensity might vary [
31]. ElectricityMap’s figures from more than 50 countries show that because coal accounts for the vast majority of power generation, using 1 kWh there would emit 725 g of CO
2 [
31]. On the other hand, because Norway’s power is generated from renewable sources, 1 kWh spent there would only result in 25 g of CO
2 (25 April 2022). Based on the figures the IEA supplied in 2018, calculations by the Crypto Carbon Ratings Institute (CCRI) utilized a carbon intensity of 475 g/kWh CO
2.
3. Consensus Algorithm
Peers from across the world can validate or verify transactions on a decentralized public blockchain. The status of the ledger must be agreed upon by all participants in a peer-to-peer network, and transactions must be processed securely. Different consensus methods are used by cryptocurrencies to guarantee peer agreement and protect the network from fraudulent users.
Environmental Relevance: The choice of consensus algorithm plays a pivotal role in the environmental footprint of a cryptocurrency. Some algorithms, like Proof of Work, demand significant computational power and, consequently, substantial energy. Others, like Proof of Stake or Delegated Proof of Stake, aim to reduce this energy burden. As we delve into specific consensus methods in the subsequent sections, we will explore their respective environmental implications.
3.1. Proof of Work
Bitcoin was first released in 2008 by a person or group going by the alias, Satoshi Nakamoto [
32]. Nakamoto was the first to use the Proof of Work consensus mechanism to resolve the double spending issue with cryptocurrencies. Miners have to invest their time and computing power in order to mine blocks and obtain new Bitcoins in order to maintain security and prevent double spending [
33].
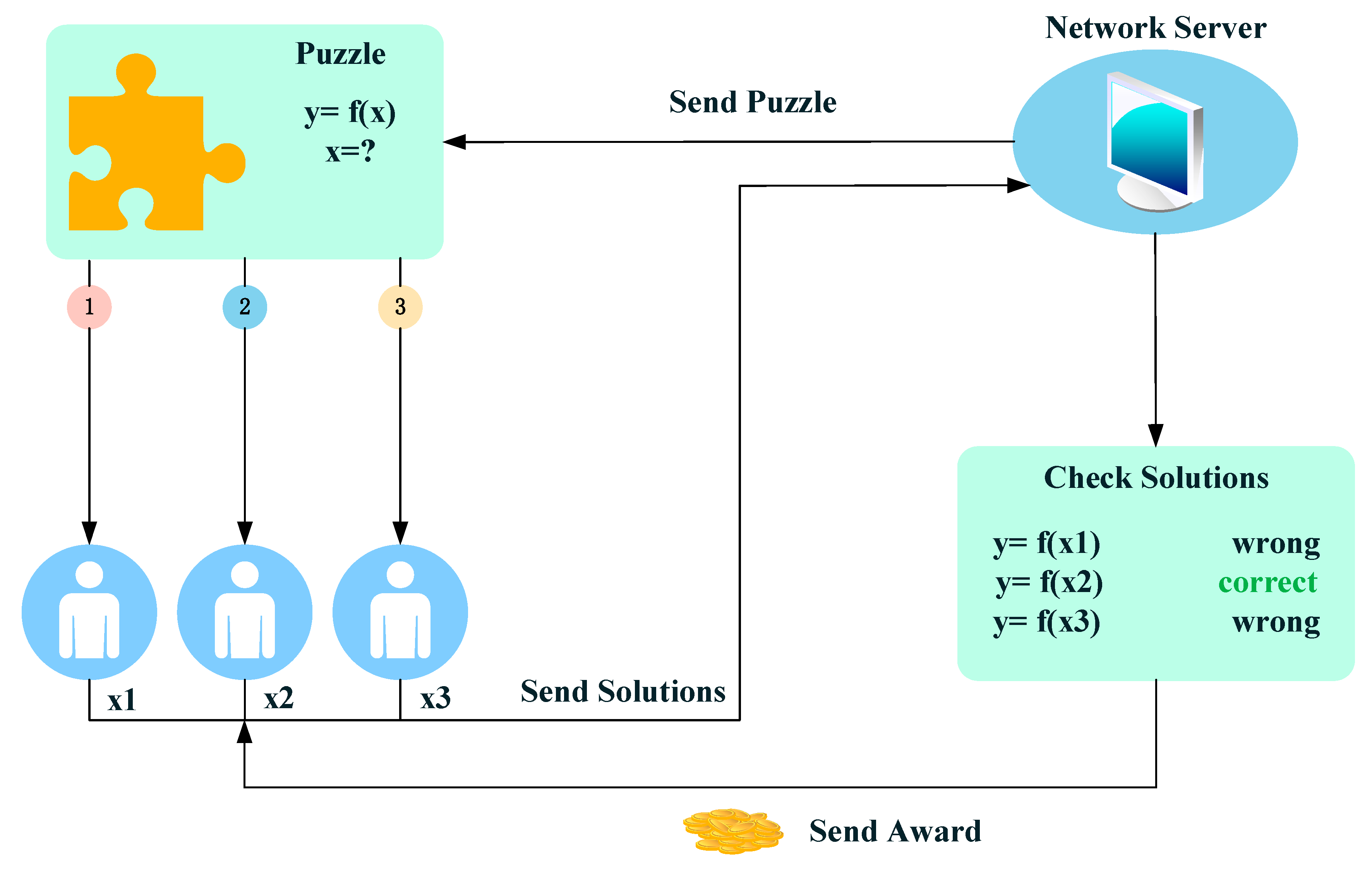
Network users known as miners verify transactions by constructing blocks in the Proof of Work mechanism. Miners must hash and compress network transactions in order to verify a block. The block hash is then created by hashing the transaction’s root hash, the block’s timestamp, the preceding block header, and the random value, ‘nonce’. Prior to the blockchain adding a new block, the block hash must satisfy some specifications established by the network. Since the supplied piece of data will always produce the same hash, miners must attempt to guess numerous nonce values in order to obtain this value. Miners receive new coins as soon as the block is mined and put to the chain.
Figure 4 shows a schematic diagram of the Proof of Work mechanism [
34].
The Bitcoin network controls how long it takes to mine a block. Finding the desired hash becomes more difficult as there are more miners and competitors. We refer to this as network difficulty. Finding a target hash and mining a block in Bitcoin takes a miner roughly 10 min. In more technical terms, the difficulty is a measurement of how challenging it is to discover a hash below a certain goal when mining a Bitcoin block. A high level of difficulty will require more processing power to mine the same amount of blocks, strengthening the network’s defenses against intrusions. The overall estimated mining power estimated in the Total Hash Rate (TH/s) chart is closely correlated with the difficulty adjustment [
28]. Today, specialized mining devices called ASIC miners are used to mine Bitcoins because of their high computer power and quick hash generation. Mining pools, which are collections of miners that pool their computer power and divide the rewards when a block is made, are currently used to mine a significant number of Bitcoins.
Since miners compete with one another for the reward, the Proof of Work technique uses a lot of energy. The fact that only the quickest miner receives a reward causes other miners who attempted to mine the same block to squander a lot of computer power. The PoW method is also used by other cryptocurrencies, although their hardware requirements and levels of difficulty differ from those of Bitcoin.
Ethereum is a different cryptocurrency that uses the Proof of Work consensus process. In 2015, Vitalik Buterin unveiled the Ethereum framework for decentralized applications [
35]. Ether is the name of Ethereum’s token (ETH) [
27]. Ethereum, in contrast to Bitcoin, is much more than merely a platform for blockchain transactions. Ethereum’s built-in smart contracts and Turing-complete programming language make it possible for anybody to construct decentralized applications (dApps). Because of worries about excessive power use, Ethereum switched to the Proof of Stake consensus mechanism, or ‘The Merge’, in 2022 [
27]. Equipment specifically made for mining Ethereum is required. Currently, Ethereum holds the second-place position in terms of market value and makes up 19.4% of the total market capitalization of all cryptocurrencies [
4].
Monero is the third Proof of Work currency our study has looked at. The XMR project is an open-source cryptocurrency that offers private and anonymous transactions by utilizing the ring signature method [
36]. In 2014, CryptoNote released Monero [
37] and according to market value, it is now the 33rd-biggest cryptocurrency [
4]. Because Monero features an ASIC-resistant RandomX algorithm and employs Proof of Work as its consensus mechanism, it is impossible to create specialized hardware to mine the cryptocurrency [
38]. Monero block mining typically takes two minutes [
39].
3.2. Proof-of-Stake
The Proof of Stake (PoS) consensus approach uses a small amount of computing power to validate transactions and create blocks without any mining competition. The user must stake part of their cash in order to validate transactions and suggest new blocks. Then, validators are randomly selected for the validation of new blocks. Because there is no rivalry between validators and less computational power is utilized, the PoS approach uses less energy than the PoW consensus technique. However, there are some issues with its decentralization, because affluent validators are more likely to be elected, because they have more money at stake [
40]. The PoS currencies, Cardano, Avalanche, and Polkadot, as well as their consensus mechanisms, were thoroughly explored in this study.
Figure 5 demonstrates a schematic design of the PoS mechanism [
41].
A third-generation cryptocurrency called Cardano has its own token called ADA [
42]. Charles Hokinson, the Co-founder of Ethereum, began working on Cardano’s development in 2015, and it was released in 2017 [
43]. Cardano secures the networks using the Proof of Stake mechanism called Ouroboros [
44]. This protocol breaks chains into epochs, which are subsequently split into time slots, to process transaction blocks. There is a leader in each slot who is in charge of validating transactions, building transaction blocks, and linking blocks to the chain [
44]. A ‘lottery’ is used to select the slot leaders, and the leader with the greatest stake has a stronger chance of winning [
43]. Cardano has ambiguous hardware requirements, but according to research by the CCRI, users should feel comfortable operating the program on any PC [
45].
Several blockchain applications employing smart contracts are supported by the Avalanche blockchain platform. The native currency of Avalanche is known as AVAX [
46]. Avalanche is an open-source project that was released in 2020 [
46]. The network intends to be quick, secure, scalable, versatile, and sustainable. It can handle up to 4500 transactions per second [
47]. AVAX users decide how rapidly new currencies are produced, and Proof of Stake consensus is often used to run the network. AVAX has a 720 million token supply limit [
47]. According to the CCRI analysis, Avalanche requires similar hardware to Cardano [
9].
Another Proof of Stake blockchain project is Polkadot, which uses DOT as its native currency on its Polkadot network [
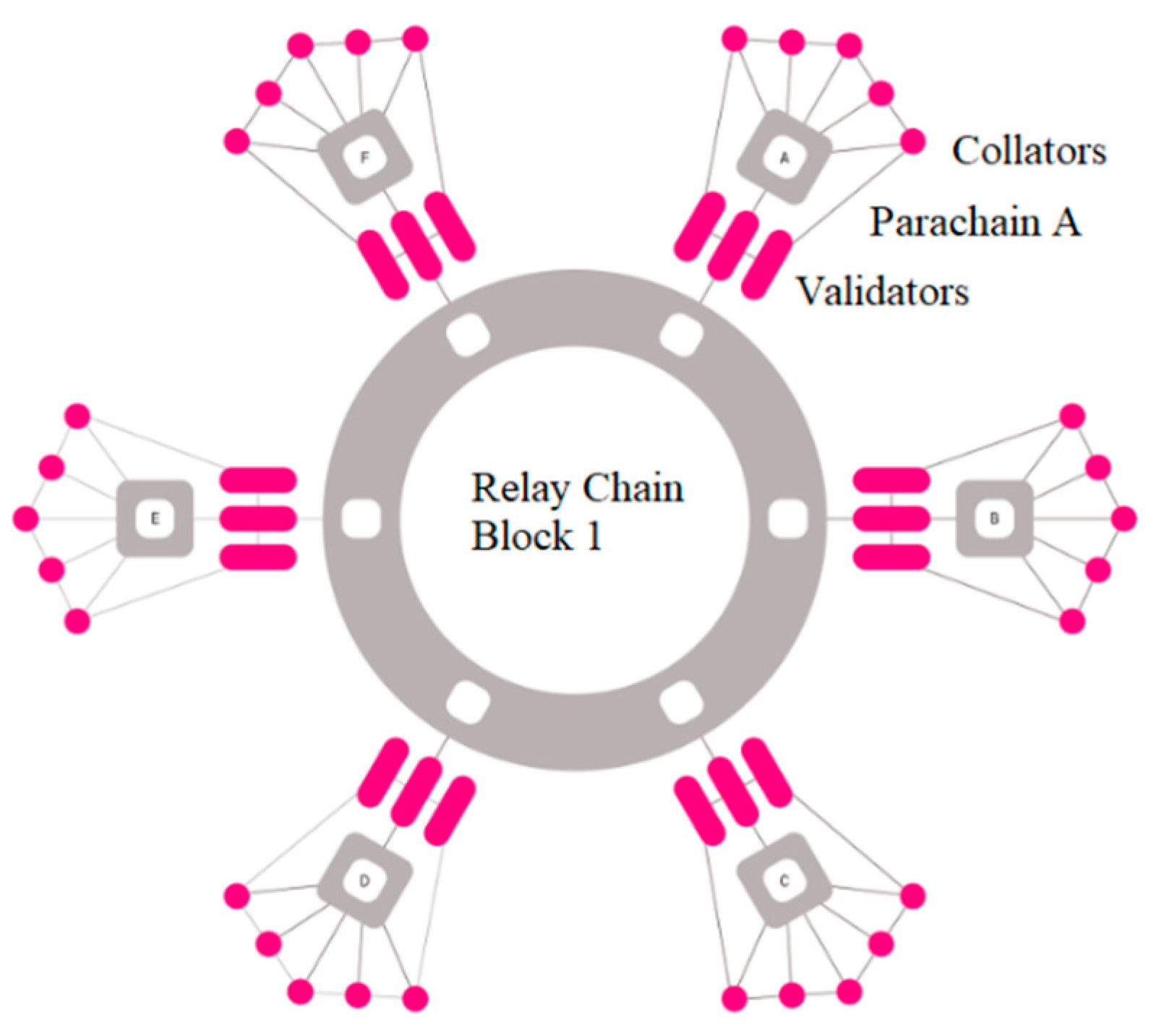
48]. The Polkadot network employs the sharder paradigm, in which transactions are handled concurrently in ‘parachains’ rather than in sequences [
48]. With the use of this sharded topology, the Polkadot network may be expanded to include several chains and even various blockchain projects, as shown in
Figure 6. Various chains and initiatives can process transactions and share data in the network. The Polkadot network is able to execute numerous transactions more quickly than typical blockchains by connecting many chains together in a parallel paradigm. Polkadot’s ‘Relay Chain’ main chain serves as the network’s consensus mechanism and security core. Polkadot’s hardware specifications were categorized by CCRI as ‘special’, as the network requires a certain kind of CPU, RAM, and storage [
9]. However, CCRI discovered through their investigation that they could also use other devices to run the network.
3.3. Other Consensus Algorithms
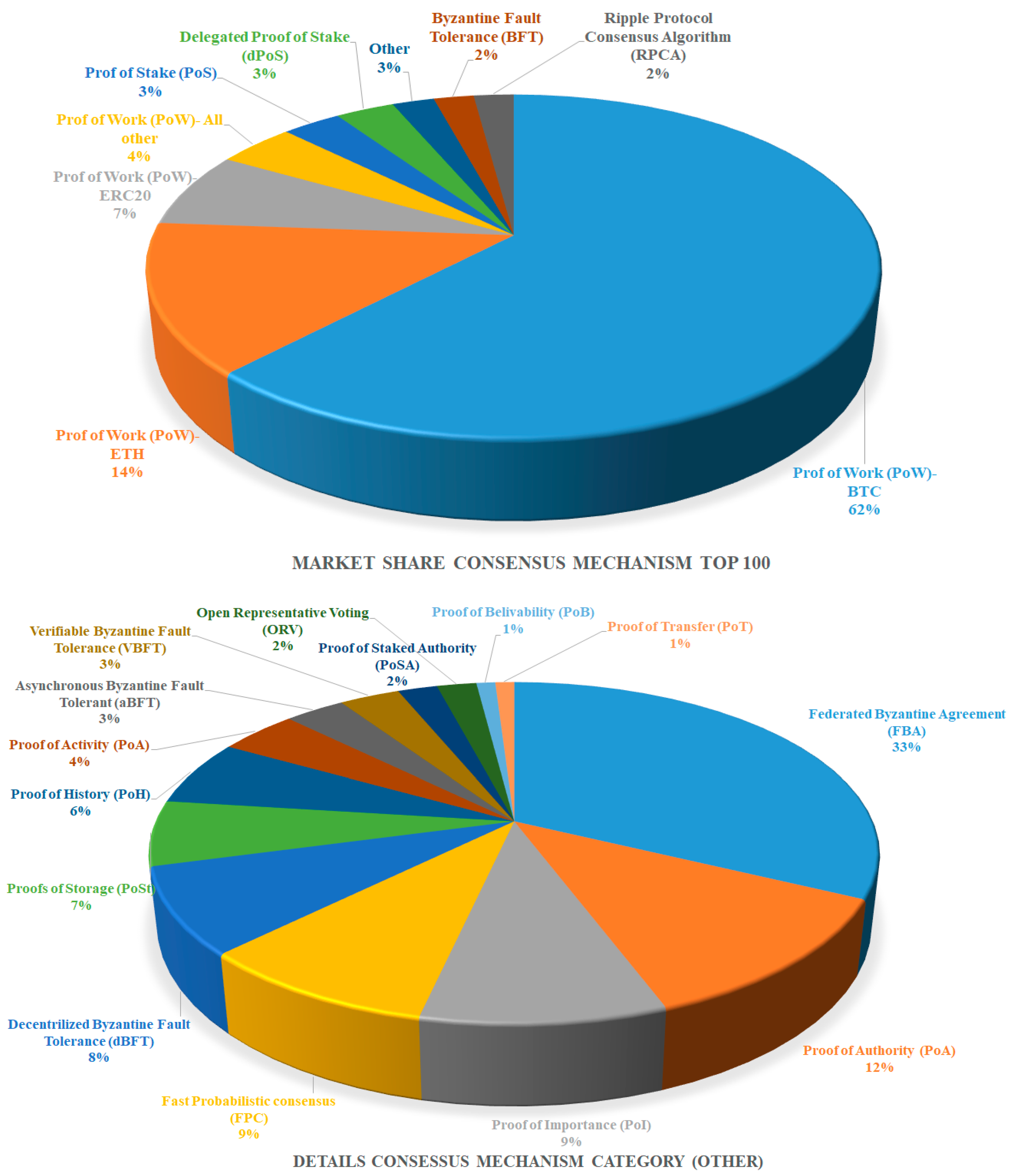
Numerous cryptocurrencies either use their own proprietary consensus algorithms or variants of existing consensus algorithms. (Refer to
Figure 7 for a detailed breakdown of the market share of consensus mechanisms among the top 100 crypto projects, and also the category labeled ‘Other’). We covered the Solana, XRPL, and IOTA consensus algorithms in this subsection. An open-source, high-performance blockchain serves as the foundation for the cryptocurrency project, Solana [
50]. The network employs Proof of History as its consensus algorithm to surpass more mature blockchain ecosystems, and SOL is the token that Solana uses [
51]. The Solana network theoretically has a capacity of over 710,000 transactions per second [
50]. PoH and horizontal scalability enable Solana to execute transactions quickly. The Proof of History mechanism, according to Solana’s creator Anatoly Yakovenko, is ‘a series of calculations that can give a technique to cryptographically validate the passage of time between two users’ [
23]. Solana employs a series of hashing operations so that the output from one is used as the input for the next. The sequence index indicates the number of calls made to the function. This data format makes it clear that actual time has passed between the first and last hash. Predicting the input of hash functions is fundamentally unfeasible due to their one-way nature. The only method to derive the desired hash is to execute the hash function the requisite number of times.
Transaction processing on the Solana network is quicker than in conventional blockchain setups. Leaders and validators are the two categories of nodes in the Solana network. The system’s leaders are its generators, and they rotate at set intervals [
51]. Validators verify the transactions uploaded to the ledger as full network members [
50]. With a series of computations, the leader prearranges the transactions and creates a digital record of each event that takes place on the network. This might also be referred to as the transaction’s timestamp (PoH). The transactions can potentially be split up into smaller batches by the leader, who will then distribute each batch to other nodes. Nodes exchange the transactions with other peers after verifying them and recreate the original batch collection [
51]. Since none of the validators must go over every transaction, the network is made more effective and functional. Solana has stringent specifications for the hardware needed to power the network; a certain CPU type is advised, and it is also noted that nodes may benefit from employing a graphics-processing unit (GPU) [
9].
Another project with a unique consensus process is XRP Ledger. Three former Bitcoin engineers, Jed McCaleb, Arthur Britto, and David Schwartz, created XRP Ledger, or XRPL, in 2011 [
52]. Making a cryptocurrency that is effective, scalable, and sustainable was the concept behind XRPL. Jed McCaleb, Arthur Britto, and Chris Larsen, two XRPL developers, formed the technology company, Ripple, in 2012. XRP Ledger Consensus Protocol, or simply XRP LCP, is the name of the consensus algorithm employed by XRP Ledger [
53]. The three stages of the consensus algorithm are collection, deliberation, and validation. Validators gather new transactions during the collection phase, adding properly formatted transactions to their open ledger. The decision to shut the ledger rests with each validator. The open ledger period frequently ends when specific criteria are satisfied. Validators trade suggestions with other validators they see as trustworthy throughout the discussion process. Each participant in the XRP LCP independently chooses which validators will hear about the decisions of the next ledger. Each trusted validator locally maintains a list of these trusted validators known as the Unique Node List (UNL). Validators add or remove transactions from the proposal throughout the discussion in order to iteratively update their transaction set. The proportion of concurring trustworthy validators is examined following each update. The validator applies the most recently closed ledger to the most recently verified ledger once there is agreement and consensus over transactions. Participants check the validity of the most recent closed ledger in the validation phase by comparing the hashes they obtained from reliable peers [
54].
Due to the Byzantine Fault Tolerant foundation of the XRP LCP, the XRP Ledger will continue to operate even in the event of a malicious actor or incomplete participant agreement [
55]. With no mining and no need for many confirmations to establish immutability, XRPL processes transactions quickly and effectively. Although there are certain special requirements and recommended CPU types for XRPL, it may be run on common hardware for testing or occasional use [
56]. XRPL discloses the approximate locations of its nodes, and it is seen as a more ‘green’ cryptocurrency because the majority of its users are in Europe and the USA, where power has a lower carbon footprint than in China [
57].
The final cryptocurrency under consideration is IOTA, which differs from the prior proposals evaluated because it lacks a blockchain and instead relies on a network of transactions that are processed in parallel [
58]. This network is called Tangle. A new transaction may be added to the Tangle by any user or network node. The message of a transaction is connected to two to eight preceding ones in the directed acyclic graph (DAG) that makes up the Tangle’s data structure. Numerous locations at the Tangle’s front allow for the attachment of messages [
58]. Tangle can process several transactions more quickly than a normal blockchain in which a new block is added to the previous one. No miners or transaction fees exist since anybody may contribute messages. All users of the network validate new messages without the need of validators or miners. Messages that make reference to a milestone are regarded as legitimate. The Coordinator, a unique node, defines the milestones. The Coordinator is a node that sends signed messages, or ‘milestones’, which other nodes rely on and employ as proof that the messages are genuine. When IOTA launches its IOTA 2.0 network, this Coordinator mechanism will be discontinued [
58].
On 24 February 2021, the Top 100 stocks held 96% of the overall market capitalization, which is calculated by multiplying the price by the circulating supply. A total of 93% of the market share of the top 100 cryptocurrencies is made up of cryptocurrencies based on Proof of Work, Proof of Stake, and Delegated Proof of Stake. We divided the 87 percent of rated cryptos by Proof of Work into three smaller categories in order to account for Bitcoin’s market dominance: exclusively Bitcoin is rated first, followed by Ethereum only in second place, all ERC20 Ethereum-based tokens in third place, and all other PoW-based cryptocurrencies in fourth place [
59]. The market’s cyclical nature frequently causes the ranking of procedures in the ‘Others’category to vary.
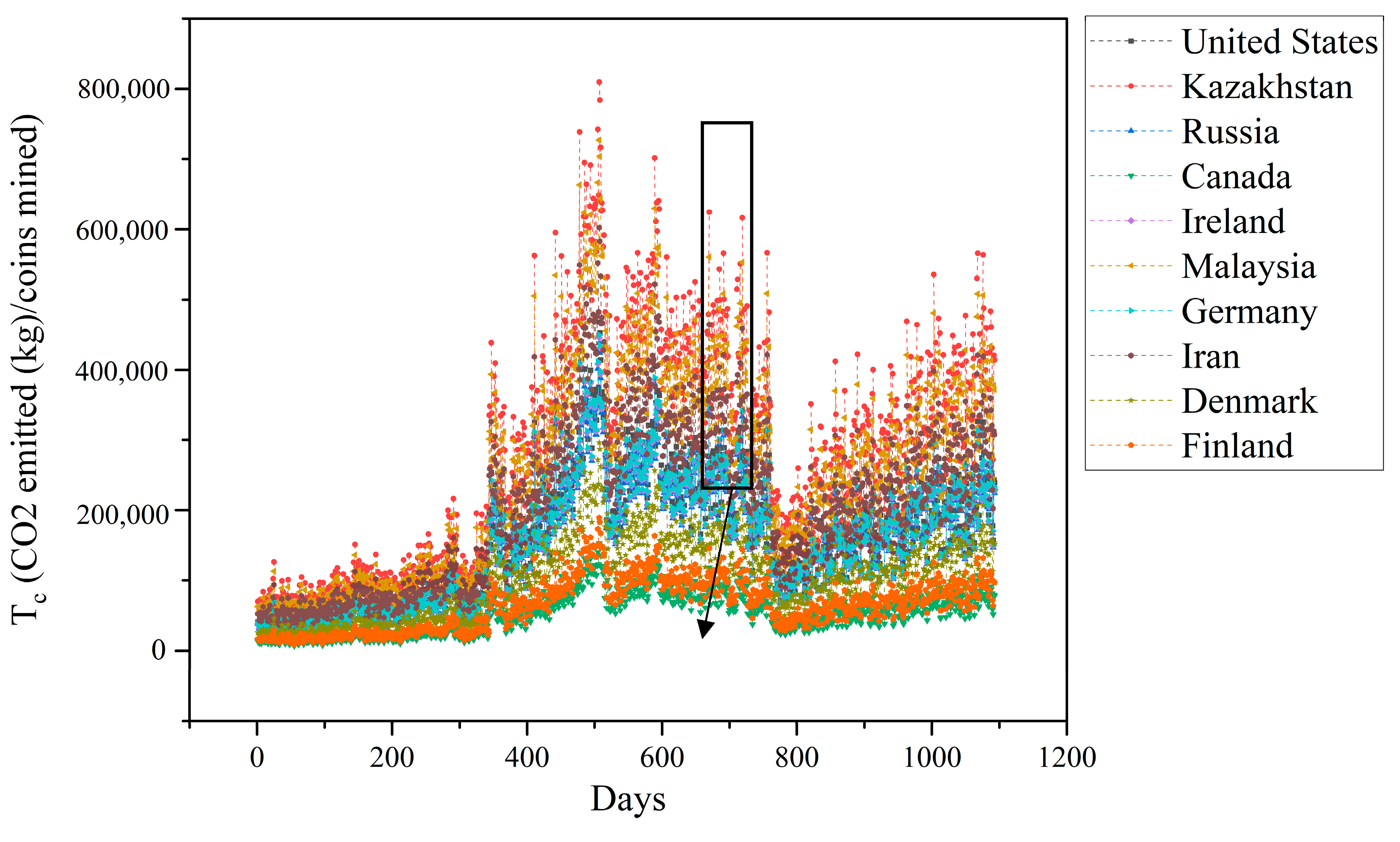
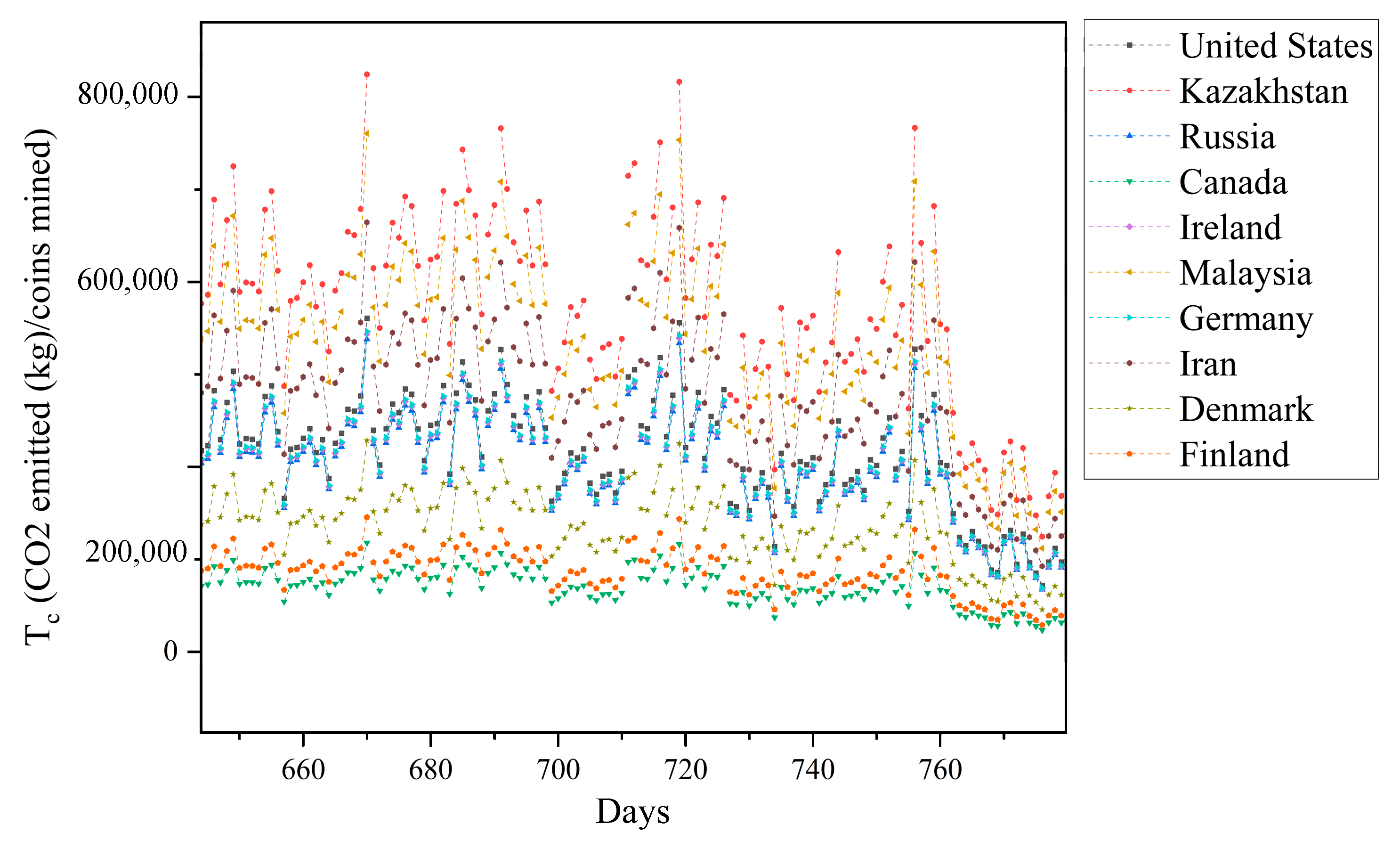
4. Energy Consumption and CO2 Emission
The daily network hashrate for each cryptocurrency was multiplied by the power efficiency (PE) of the mining rig, or computer, as shown in Equation (1), to determine how much power the entire network needed [
60].
where P is the cryptocurrency network’s power demand, HR is the network hashrate, and PE is the mining equipment’s power efficiency.
The number of blocks generated every hour, the coin reward for completing a block, and the conversion of coins to US dollars were then multiplied, as stated in Equation (2), to obtain a ‘network velocity’ (USD created per hour):
where v denotes network speed, t
B is the daily average block completion time (in minutes), R denotes the coin reward for completing a block, and EX denotes the exchange rate from cryptocurrency to US dollars.
In order to calculate the amount of energy required to produce one US dollar, the network power (P) was divided by the velocity and multiplied by the unit conversion factor from megawatt hours to megajoules, as shown in Equation (3).
where P and v are previously known, and EC is the energy cost, which is the amount of energy needed each day to earn one US dollar.
The daily computed energy required to create one coin was divided by peer-reviewed data on country-specific emission factors (kg CO
2 per kWh
−1), as shown in Equation (4), to give a final assessment of each network’s potential environmental impact.
The total daily energy required to produce a coin on a given day is NC, and the other parameters have previously been established. On the other hand, ECs fluctuate in terms of energy, and the only time NC values change is when the network’s energy needs change. In order to calculate the CO
2 emissions per coin, country-specific emission factors (Y) were employed, as specified in Equation (5):
where Y is the mass of CO
2 emitted per kilowatt-hour of energy generated for a country or region, TC is the carbon cost, which is defined as the mass of CO
2 emitted per coin mined, and median (NC) is the median NC value.
7. Conclusions
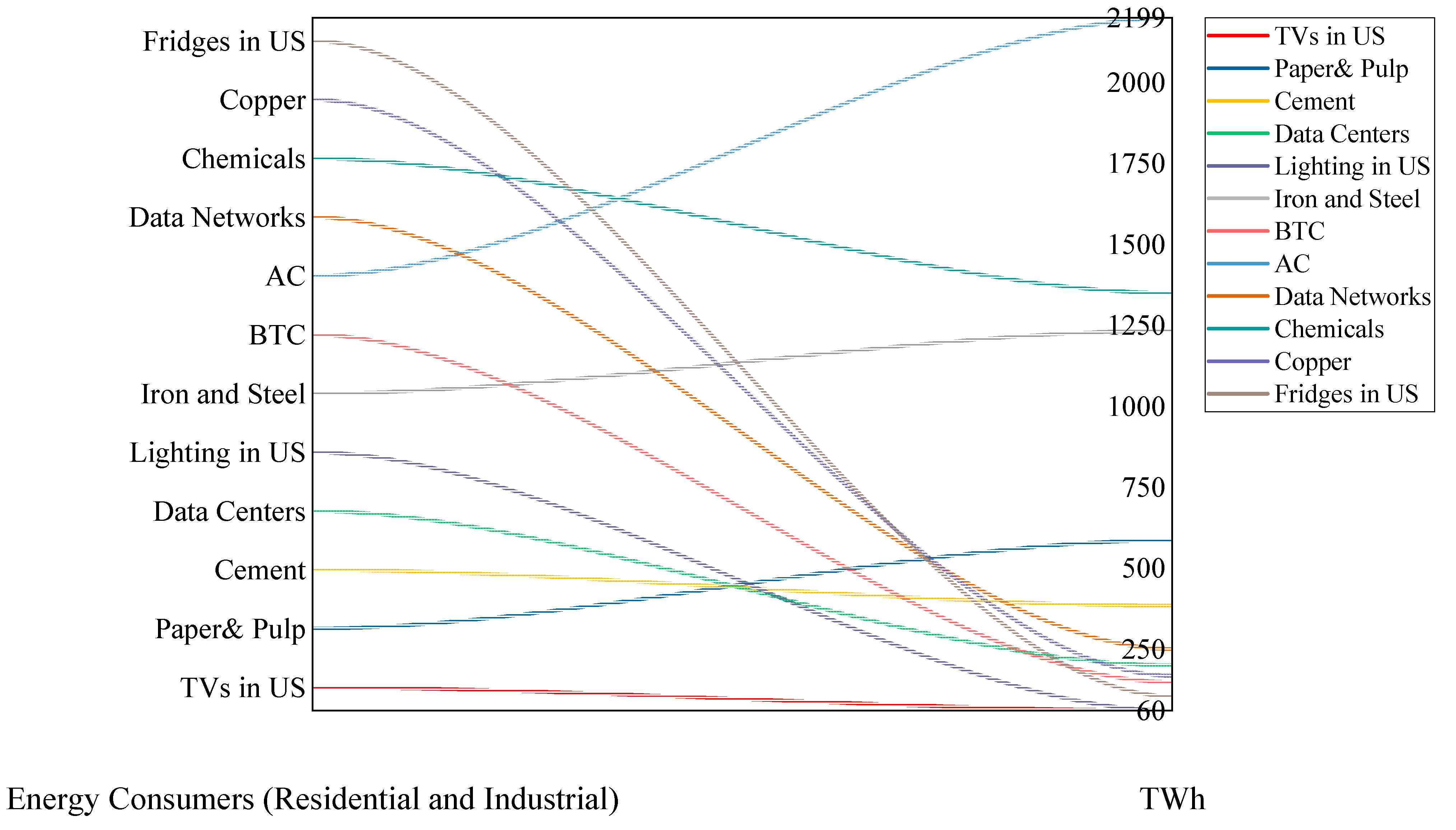
In this review paper, we undertook a comprehensive exploration of several cryptocurrencies, focusing on their environmental impact. Our findings reveal substantial discrepancies in the energy consumption across various cryptocurrency projects. These discrepancies largely stem from the type of consensus algorithm used, with the Proof of Work algorithm exhibiting a considerably high energy footprint. Comparisons with traditional payment systems, such as Visa and Mastercard transactions, reveal that cryptocurrencies utilizing more energy-efficient consensus mechanisms can attain comparable levels of energy usage.
Further complicating the assessment is the challenge in accurately calculating CO2 emissions attributable to cryptocurrencies. The environmental footprint significantly varies based on the geographical distribution of miners and users, due to the differing carbon intensity of energy sources across regions. Though our calculations employed global averages, it is crucial to note that if the majority of users are concentrated in regions with a high carbon output like China, the actual emissions could potentially be higher.
However, our study recognizes that cryptocurrencies represent a pioneering technology with immense potential. Instead of dismissing this technology due to its environmental challenges, we believe it is crucial to address these issues and guide it towards a more sustainable future. Our research highlights that many cryptocurrency projects already demonstrate significantly lower CO2 emissions than the Bitcoin network. Therefore, continuous improvements in consensus algorithms and increasing utilization of renewable energy sources for mining operations can substantially reduce the environmental impact of cryptocurrencies.
In conclusion, as we navigate the digital era, this paper underscores the need for a nuanced understanding and sustainable approach to the evolution of cryptocurrencies, so we can harness their potential while minimizing their environmental impact.