1. Introduction
With the continuous development of modern information technology, all walks of life show the trend of intelligence and informatization [
1]. The generality and heterogeneity characteristics of network security borders are becoming increasingly obvious, the pressure of network security defense has been increasing, and network security work has risen to the national strategic height [
2]. In 2019, the promulgation of the basic requirements [
3] for the protection of the information security technology network security level in “(GB/T 22239-2019)” [
4] and other standards put forward more detailed information in new areas such as cloud computing, the Internet of Things, mobile internet, industrial control, big data, and other new areas. As an important part of the power grid, network security is of great significance for the network security and reliable operation of the power grid [
5].
At present, the deep integration of advanced information and communication technology such as artificial intelligence, big data, and the Internet of Things is often compared with the traditional power grid, and the new power system is more multisource, open, and general. Due to this great expansion, the difficulty of security protection increased sharply [
6,
7], and improvements in the safety construction of the power system are urgently needed. Compliance inspections and security assessments are important ways to guide the security construction of the power information system. To this end, this article seeks to understand the current status of the network security of the power system, combined with the network security classified protection 2.0 (hereinafter referred to as the “classified protection 2.0”), and proposes a safety assessment system of the power information system based on classified protection 2.0 [
8]. In addition, this paper also integrates Trusted Computing into the power system, proposes a power system security protection model, improves the traditional TOPSIS evaluation algorithm, proposes a comprehensive evaluation method combining subjective and objective methods, uses this algorithm to analyze the proposed scheme, and proves the feasibility of the algorithm and the rationality of the scheme. It provides an important theoretical basis for the safe, reliable, and standardized development of the power system.
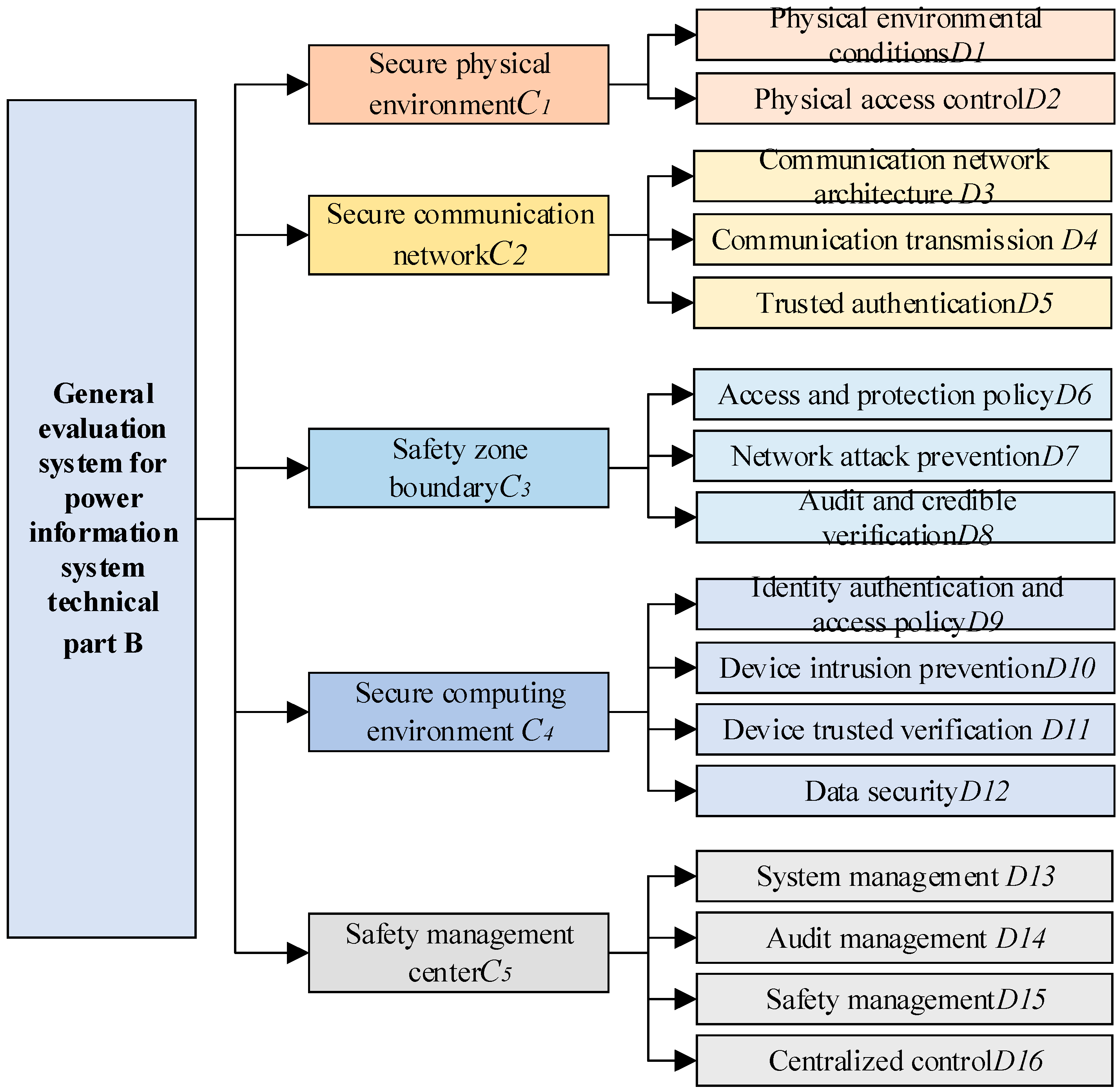
3. Establishment of Power Information System Index System Considering Classified Protection 2.0
The main research object of this paper is the power information system, and the power information system security evaluation index system is constructed in combination with the classified protection 2.0 standard, the power information security level evaluation index (GB/T 32351-2015) [
28], and the power information system security inspection specification (GB/T 36047-2018) [
29]. The index system is divided into three levels: target level (B), primary index (C), and secondary index (D).
This paper mainly evaluates the security of the technical part of the power information system, which is constructed according to classified protection 2.0. The technical part includes five types of first-class indexes: secure physical environment (
), secure communication network (
), secure area boundary (
), secure computing environment (
), and security management center (
). Under various primary indexes, several secondary indexes are subdivided. The secondary indexes are extracted and established according to grade protection 2.0 and the relevant standards of the power industry. The specific index system is shown in
Figure 2.
Since the security evaluation of classified protection 2.0 is conducted by subjective judgment, it is not conducive to academic research. Therefore, this paper integrates and optimizes the secondary indexes with reference to classified protection 2.0 and the relevant standards of the power industry and makes an objective quantitative analysis on some indexes to ensure the comprehensiveness of the security assessment.
3.1. Safe Physical Environment Index
Referring to the basic requirements of level 3 in classified protection 2.0, the secure physical environment index can be optimized and integrated into two level 2 indexes: physical environment conditions () and physical access control ().
The physical environment requirements (
) include the physical location selection, anti-theft devices and damage prevention, lightning protection, fire prevention, waterproof and moisture-proof features, anti-static features, temperature and humidity control, power supply protection, and electromagnetic protection. Each item is subdivided into several judgment points, as shown in
Table 1.
The physical environmental condition
is a qualitative indicator that is composed of multiple classified protection 2.0 judgment points. Their scores can be expressed by the compliance ratio value, as shown in Equations (1) and (2).
indicates the total number of judgment points of the physical environmental conditions; indicates the number of judgment points that are not applicable; and indicates the score of each judgment point, which is usually obtained through a field evaluation by grade protection evaluation experts. Subsequent qualitative indexes are scored in this way.
- 2.
Physical access control
Physical access control (
) is an index used to evaluate whether the power information system implements the access control of the computer room in accordance with the requirements of classified protection 2.0. It requires that the entrances and exits of the computer room are guarded by special personnel or equipped with an electronic access control system to control, identify, and record the personnel entering. Physical access control
can be expressed by the percentage of machine rooms meeting the requirements of classified protection 2.0, as shown in (3).
indicates the total number of physical machine rooms of the power information system; indicates the number of machine rooms meeting the requirements of classified protection 2.0.
3.2. Safe Communication Network Index
The index of the secure communication network includes three secondary indexes: communication network architecture , communication transmission , and trusted verification .
- (1)
Communication network architecture
The core requirements of the communication network architecture () are as follows: 1. The system network bandwidth is appropriate, and the processing capacity of the core equipment should match the bandwidth. 2. The system network architecture shall be divided into security areas, and corresponding protective measures shall be taken between each area. 3. The whole network design shall ensure the redundancy of communication lines and equipment.
The network communication architecture is composed of measurement indexes and qualitative indexes. The calculation formula of this paper is as follows:
where
represents the weight value of each judgment point of item
i. In this paper, the weight value is taken as 1/
n, which can be adjusted according to the actual importance during the specific implementation. represents the qualitative index judgment point of the communication network architecture
, and its score formula is shown in Formula (1).
In addition, indicates the score of the system network bandwidth, indicates the actual network bandwidth, and indicates the maximum bandwidth required by the service. The unit is Gbps.
- (2)
Communication transmission
Communication transmission is the core index used to ensure the communication transmission quality of the power information system. Its security requirements can be summarized as follows: ensure the integrity and confidentiality of data transmission.
A quantitative analysis of the available packet loss rate must be undertaken for transmission integrity. The smaller the packet loss rate, the better the communication transmission integrity. This equation for this rate is expressed as follows:
is the packet loss rate, is the size of the input message in the measurement time period, and is the size of the output message in the time period.
Transmission confidentiality is a qualitative index that mainly ensures the confidentiality of data in the communication process by checking that cryptographic technology should be used, which can be quantified by Formula (1).
Therefore, considering both data integrity and confidentiality, this paper establishes the communication transmission quantization formula as follows:
where
,
are the weight values of integrity and confidentiality, which are taken as 1/2 in this paper, and can be adjusted according to the actual importance during implementation.
is the quantized value of each judgment point of transmission confidentiality, which is quantized by Formula (1);
is the judgment value of the packet loss rate. Referring to the overload packet loss rate of the China Southern Power Grid, which is required to be lower than 0.1 ‰, the judgment value of the packet loss rate is defined as follows:
- (3)
Trusted authentication
The trusted verification is a technical index used to evaluate whether the communication equipment of the power information system is reliable and credible. The trusted verification is carried out through the system boot program, system program, important configuration parameters, and communication application program of the equipment. Trusted verification is a qualitative index, and it is difficult to obtain accurate values of it through measurement and calculation. In this paper, Equations (1) and (2) are used to quantify it.
3.3. Safety Zone Boundary Index
According to the requirements of classified protection 2.0, the security area boundary puts forward security control requirements for the network boundary of the power information system. The main objects are the system boundary and area boundary, including network gates, firewalls, switches, routers, etc. The security control points involved include boundary protection, access control, intrusion prevention, malicious code and spam prevention, security audit, and trusted verification. In order to ensure the efficiency of index evaluation, this paper refines and integrates three secondary indexes: access and protection strategy , network attack prevention , and network attack prevention .
In the classified protection 2.0 system, the evaluation indexes for the boundary of the security area are qualitative indexes. The three level 2 indexes integrated in this paper are composed of multiple classified protection 2.0 judgment points. The scores of judgment points are shown in Formula (1), and the comprehensive scores of all secondary indexes are shown in Formula (2).
3.4. Safety Calculation of Environment Indexes
The security computing environment puts forward security control requirements for the interior of the boundary. The main objects are all objects of the power information system, including network devices, security devices, server devices, terminal devices, application systems, data objects, and other devices. The security control points involved include identity authentication, access control, security audit, intrusion prevention, malicious code prevention, trusted verification, data integrity, data confidentiality, data backup and recovery, residual information protection, and personal information protection. Combined with the relevant standards of the power industry, this paper refines and integrates four secondary indexes: identity authentication and access strategy , equipment intrusion prevention , equipment trusted verification , and data security .
This index includes identity authentication and access control. In this approach, the components are sorted and analyzed according to the level 3 general requirements of classified protection 2.0, and the identity authentication requirements include the following:
Identity uniqueness, with automatic de-duplication inspection;
Mandatory application function for password complexity;
Have login failure function;
Encrypted transmission is adopted for remote access;
Have more than two identification methods.
The access control requirements include the following:
Account authority allocation;
Access rules for authorized subjects to objects;
Granularity requirements for access control;
Set safety signs for important subjects and objects.
- 2.
Intrusion prevention
Intrusion prevention can be divided into two parts: intrusion prevention and malicious code prevention. The system is required to detect intrusion on important nodes. It is required to adopt technical measures against malicious code attacks or active immune trusted verification mechanisms to identify intrusion and virus behaviors and effectively block them in a timely manner.
- 3.
Device trusted verification
The main objects of equipment trusted verification are the network equipment, security equipment, server equipment, terminal equipment, application system, data objects, and other equipment of the power information system. It is required that the trusted root can be used to verify the system boot program, system program, important configuration parameters, and the application program of the computing equipment, and the dynamic trusted verification can be carried out in the key execution links of the application program. After detecting that its credibility is damaged, it will give an alarm, and the verification results will be formed into audit records and sent to the security management center.
Data security indexes include data integrity, data confidentiality, data backup and recovery, residual information protection, and personal information protection. The specific requirements can be summarized as follows:
Data shall not be tampered with or accessed without authorization;
Ensure data confidentiality through encryption algorithm;
Real-time backup of important data;
Only collect and save personal information necessary for business.
Identity authentication and access strategy , equipment intrusion prevention , equipment trusted verification , and data security are qualitative indexes. The scores of judgment points are shown in Formula (1), and the comprehensive scores of various secondary indexes are shown in Formula (2).
3.5. Indexes of Safety Management Center
The security management center is a new technical requirement in the classified protection 2.0 version compared with the 1.0 version. It strengthens the concept of the security management center and highlights the importance of the security management center in the construction of information security classified protection. Referring to classified protection 2.0, this index item is divided into four level 2 indexes: system management , audit management , security management, and centralized control .
System management , audit management , and security management put forward clear requirements for the management subject, authority control, and control process of system administrators, audit administrators, and security administrators, respectively, and require the management system in the security management center to comply with the “separation of powers” authority management model. Centralized control specifies the centralized control functions that the management system needs to comply with. The four secondary indexes are qualitative indexes. The scores of judgment points are shown in Formula (1), and the comprehensive scores of all secondary indexes are shown in Formula (2).
4. Security Protection Model for Power Information System
4.1. Power Information System Architecture
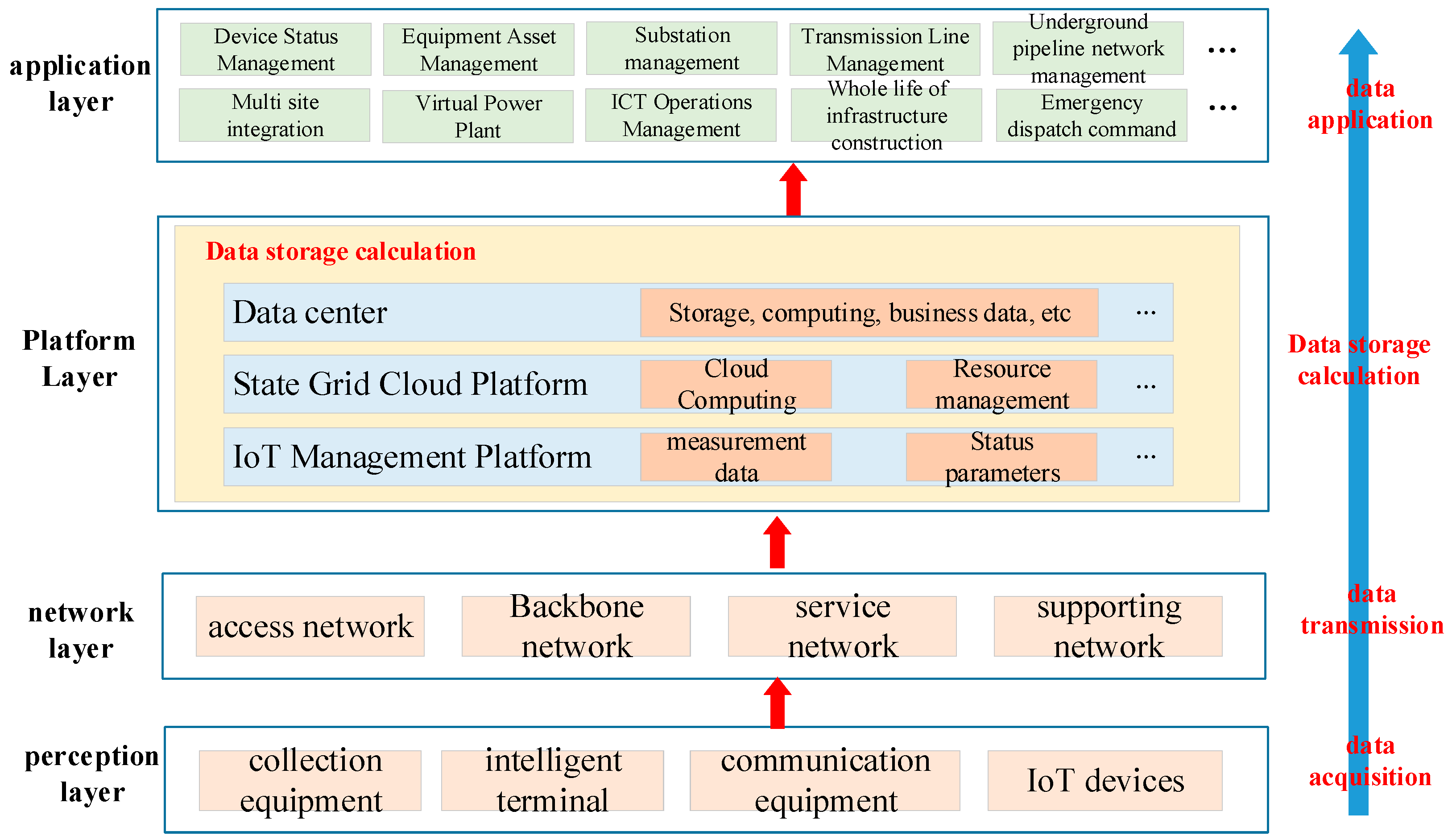
The architecture of the new power system, like other forms of IoT systems, is divided into four layers: perception layer, network layer, platform layer, and application layer. Since the platform layer is the core of the entire IoT system, generally speaking, the direction from the platform layer to the application layer is called north, the direction from the perception layer is the south, and the platform layer is called the middle platform. The architecture of the power information system is shown in
Figure 3.
Perception Layer: Previously, various business departments of the State Grid of China have built some typical applications using terminals, networks, and business systems based on actual needs. The power Internet of Things has begun to take shape, and we believe that the construction of the new power system perception layer is mainly based on the unified communication technology standards of the previous construction of the power grid power system, expanding the perception range in various aspects of the power system.
Network layer: The new power system aims to establish ubiquitous connections between power-related equipment, with a larger number of terminals and information volume compared to the core power system and lower requirements for information security. Due to the high security requirements of data in the power system, it exists in the industrial intranet and has low network scalability. Due to the differences in data volume and data security, the construction of the ubiquitous power IoT requires the construction of another network. A power wireless private network has become the preferred solution due to its high security and low cost.
Platform layer: The construction content of the platform layer mainly includes the data center, State Grid cloud platform, IoT management platform, and other parts. The focus is to achieve IoT management of massive power-related terminals, achieve various types of data collection, collect data at once and use these data everywhere, explore the value of massive data collection, improve platform support ability, achieve refined management of networked devices, improve data processing efficiency, and achieve open and shared platform capabilities.
Application layer: The construction of the application layer is divided into two parts: internal business and external business. The main construction direction of internal business is to improve customer service level, improve enterprise business performance, ensure safe and economic operation of the power grid, and promote clean energy consumption. The main construction direction of external business is to create an intelligent energy storage service platform, cultivate and develop emerging businesses, and build an energy ecosystem. We believe that internal business aims to improve the internal management efficiency of the State Grid by improving the level of intelligence, while external business aims to achieve the transformation of State Grid business through content provision.
4.2. Power System Security Protection Model Based on Trusted Computing
With the in-depth development of the power system, the types and quantities of terminal devices are complex, and their performance and working properties are also very different. There is also a significant gap in their security requirements. Therefore, it is necessary to propose a unified security architecture model to ensure the security of the power system.
The power system is simplified into a three-layer model of a terminal layer, network layer, and master station layer. In order to achieve secure and reliable information exchange in the power system, a security management and control architecture of the power system based on Trusted Computing is proposed to achieve trusted authentication between layers and the integrity measurement of each device. The specific architecture is shown in the
Figure 4.
The Trusted Computing technology is integrated into the power system architecture, which is divided into the master station layer, network layer, and terminal layer according to the system hierarchy. The main station layer is composed of the distribution network main station, database server, application server, etc. Its main function is to achieve the overall control of the main station over the power grid. At the same level as the main station, there is also the security management center CA, which mainly participates in grid security management and control as a third party for security certification. The network layer includes the distribution network communication network and substations, which act as relay stations to control and exchange information with the perception layer terminals. The perception layer includes intelligent terminals, intelligent sensors, and other control and perception devices, as well as lightweight perception devices such as fault detectors and smart meters, responsible for the control and information collection of power grid terminals.
With the development of Trusted Computing, Trusted Computing technology has developed from a single hardware chip to a variety of software and hardware forms, especially in mobile devices and embedded devices with limited computing and storage resources. For example, the ARM-based TrustZone achieves device trustworthiness through processor partitioning; Physical Unclonable Functions (PUFs), which achieve trusted authentication, key management, and other functions through the uniqueness of their physical security features, are commonly used in scenarios such as the Internet of Things, mobile networks, and wearable devices due to their lightweight and easy implementation characteristics. As a technology to ensure the predictability of information systems, Trusted Computing can be used in the research of secure communication of power system terminals, which can not only verify the integrity of equipment itself, but also achieve trusted access between equipment. In order to introduce Trusted Computing into the power system security protection model, it is necessary to trust the root TCM (Trusted Cryptography Modul) on each equipment platform. There are three ways that this can be achieved:
For embedded platforms with weak computing performance, soft TCM design can be adopted, and only basic TCM function commands can be implemented, including integrity measurement and cryptography calculation;
For platforms with ARM equipped with Trustzone and low requirements for TCM performance, Trustzone can be used to build a more complete TCM functional area, and then build the trusted root of the platform;
Like a host platform, a TCM security chip is built in/out of the system motherboard bus interface to build a complete TCM trusted root function.
Considering the large number, variety, and complex access mode of power system equipment, this paper conceives to use multiple platform trusted root design, flexibly use Trusted Computing, and achieve the security and reliability of the terminal.
In this architecture, the second and third trusted root TCM construction methods are adopted for Trusted Computing applications of the awareness layer devices. The Trustzone structure is introduced based on the ARM system to build a fully functional TCM area in the substation equipment, or, like the host platform, build a TCM security chip through the system motherboard bus interface, and then build a complete TCM trusted root function to achieve the integrity measurement of the substation layer equipment itself and secure and trusted communication between the equipment and the substation.
Due to the low computing power and weak performance of some sensing layer terminals, in this architecture, such terminals mainly implement soft TCM design through physical non-cloning technology (PUF), and only implement basic TCM function commands (including integrity measurement and cryptography calculation). This can also achieve integrity measurement of the terminal device itself and secure and trustworthy communication between the terminal and the substation.
Terminal:
The trusted logic on the terminal side is shown in the
Figure 5 above. The chip is trusted security hardware, the operating system is Linux, and the whitelist is the application program.
Master station:
The Trusted Computing support platform on the master station side is shown in the
Figure 6 above. The application software of the computer system and the trusted password support platform are two-way interconnected. The Trusted Computing password support platform consists of the TCM service module and the trusted password module. The cryptographic algorithm engine includes SM2, SM3, SM4, and a random number generator.
5. Comprehensive Weight Analysis Based on AHP and Entropy Weight Method
The analytic hierarchy process (AHP) regards a multi-objective decision-making problem as a system. By analyzing each small objective of the objective, it is divided into multiple secondary indexes, and then the AHP is carried out.
The AHP mainly starts from the evaluator’s understanding of the essence and elements of the evaluation problem, takes the research object as a system, and makes decisions according to the thinking mode of decomposition, comparative judgment, and synthesis.
Considering that the index evaluation of the classified protection 2.0 system is mostly qualitative and conforms to the core idea of the analytic hierarchy process, this paper takes the analytic hierarchy process as the basic weight analysis method. However, the AHP has some shortcomings, such as small quantitative data and many qualitative components, and it is not convincing. This paper aims to use the entropy weight method to correct the basic weight with the goal of minimizing the deviation. The specific evaluation model used in this paper is shown in
Figure 7. The AHP method is based on expert experience, and the entropy weight method is based on historical evaluation data of similar systems. The combination of subjective and objective methods can effectively ensure the rationality of index weight distribution.
5.1. Subjective Weighting of Evaluation Indexes Based on Analytic Hierarchy Process
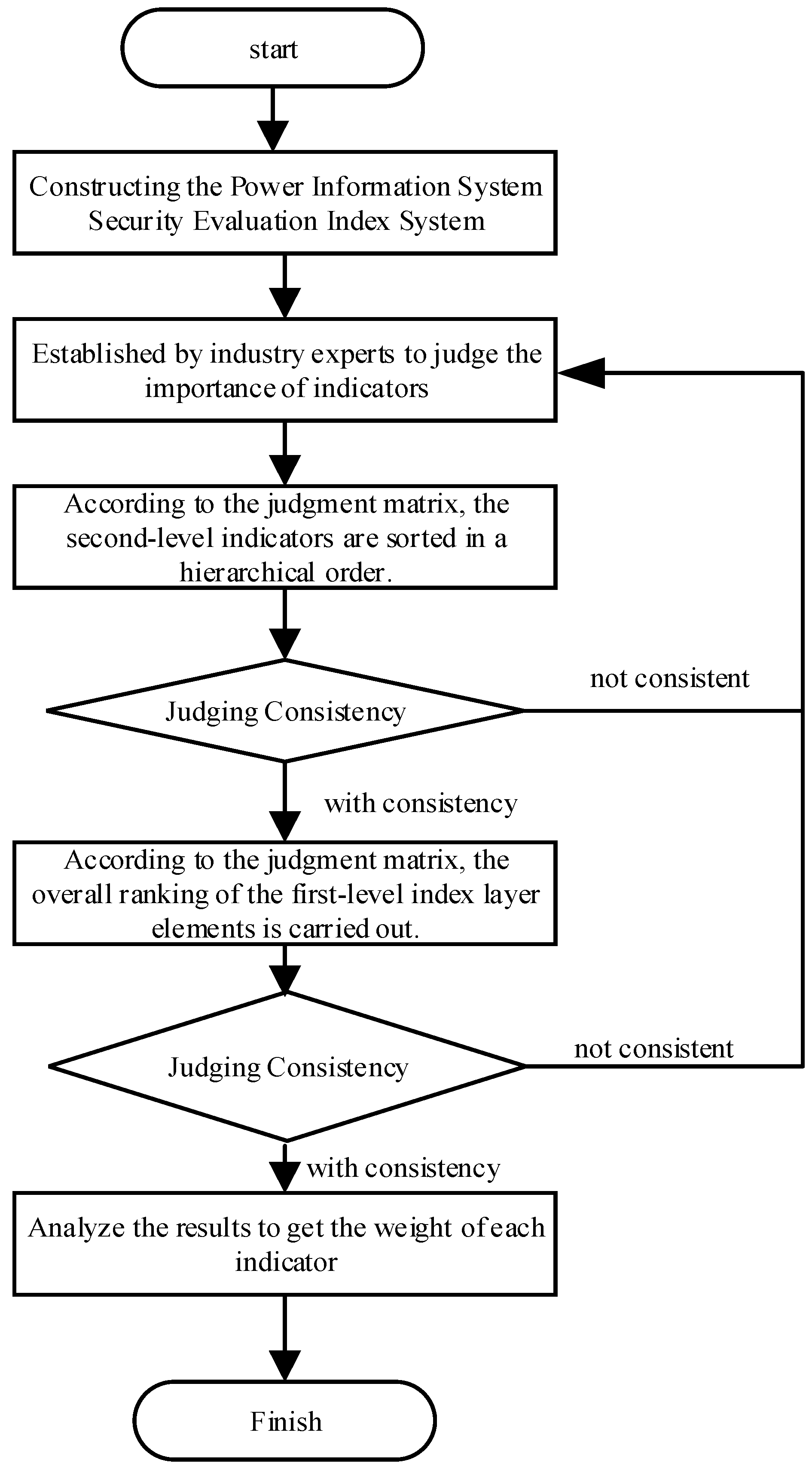
The specific steps of obtaining the index weight by the analytic hierarchy process can be roughly divided into the following: (1) establishing the hierarchical structure of the analytic hierarchy process, quantifying the qualitative results, and obtaining the judgment matrix; (2) carrying out hierarchical single sorting and consistency judgment; (3) carrying out hierarchical total sorting and consistency judgment. The specific process is shown in
Figure 8.
First, according to expert opinions, the indexes of each layer are judged by two, the relative importance
is obtained, and the judgment matrix is constructed. The judgment matrix
N is established as follows:
Secondly, the eigenvector of the maximum eigenvalue
of the judgment matrix is found,
ω,
ω is obtained after normalization, and
ω′,
ω′ is the basic weight value of the indicator at this level. The relationship can be expressed by Formula (10):
Then, a consistency check is performed on the weight values of a single sort. The consistency check formula is as follows:
where
CI (consistency index),
RI (average random consistency index),
CR (consistency ratio), and
n are the order of judgment matrix.
RI is a constant, which is related to the order of the judgment matrix. When
CI = 0, the judgment matrix n has complete consistency; when
CI tends to zero, it has relatively reliable consistency; and when the consistency ratio < 0.10, it can be considered that the judgment matrix
n has consistency and meets the requirements of design.
Finally, the total weight value of the three-level indexes is calculated by a single sorting weight value, and the consistency is tested. The total weight is calculated as shown in the following formula:
where
c is the upper secondary indicator weight of the tertiary indicator
i and
is the weight value of the tertiary indicator I at the secondary indicator level.
5.2. Objective Weighting of Evaluation Indexes Based on Entropy Weight Method
In multi-index decision-making problems, the smaller the entropy of an index, the greater the amount of information, the greater the role it plays in the comprehensive evaluation of models, and the greater the weight of the index. The entropy weight method gives appropriate weights to the indexes according to the entropy value of the indexes in the original data. Its practical significance is to enhance the weights of those indexes that are more easily ignored. The entropy weight method can avoid the influence of subjective factors and make the calculated weight more objective.
In order to calculate the entropy weight of power information system indexes, it is necessary to calculate the entropy weight of secondary indexes according to the original data and then accumulate from bottom to top to obtain the entropy weight of primary indexes. The specific steps are as follows:
According to the historical evaluation data and the evaluation data of similar systems, the original data matrix can be constructed. It is assumed that there are m groups of original data, and each group of data is composed of
n evaluation index data. The form is as follows:
where
represents the
j-th index value of the
i-th group of original data.
- 2.
Standardization of raw data
The index values in the original matrix
X are standardized as follows:
- 3.
Calculate the entropy of the j-th index
where
represents the proportion of the
j-th index of evaluation object
i.
- 4.
Calculate the difference coefficient of the j-th index
where
represents the entropy value of the
j-th indicator.
- 5.
Calculate the entropy weight of the j-th index
5.3. Comprehensive Index Weighting Based on the Principle of Minimum Discriminant Information
The subjective weight and objective weight are calculated by the analytic hierarchy process, , and the entropy method, . In this paper, the influence of subjective and objective factors on the weight is fully considered, and the subjective weight and objective weight are combined to obtain the comprehensive weight, . The commonly used combination methods are linear combination and multiplication combination. Among them, the linear combination obtains the comprehensive weight by adding the subjective and objective weights according to a certain proportion coefficient. The proportion coefficient of this method is determined by human experience, which has a great impact on the subjectivity of the comprehensive weight. The multiplicative combination obtains the comprehensive weight by multiplying the subjective and objective weights and then normalizing them, in which is easy to produce a “multiplication effect” on the weight value, which deviates from the actual situation. Therefore, this paper uses the method based on the principle of minimum discriminant information to calculate the comprehensive weight to ensure that the calculated weight is closest to the subjective weight and objective weight. The specific calculation process is as follows:
Step 1: the objective function is set as follows:
represents the objective function.
Step 2: the objective function is solved based on the Lagrange function:
Step 3: the formula for calculating the comprehensive weight is as follows:
5.4. Comprehensive Evaluation of Indexes Based on TOPSIS Algorithm
The TOPSIS algorithm is an algorithm that can sort the relative advantages and disadvantages of a limited number of evaluation objects. It reflects the advantages and disadvantages of the scheme through the closeness to the optimal target and the worst target. Based on the comprehensive weight calculated in
Section 3.3, this paper uses the TOPSIS algorithm to comprehensively evaluate the security of the power information system. The specific steps are as follows:
Step 1: Establish the specification matrix. Based on the original data matrix of grade protection evaluation, this paper carries out normalization processing and a row weighting calculation to obtain the normalized matrix.
where
V represents the normalization matrix,
represents the
j-th index value of the
i-th group of original data, and
represents the comprehensive weight value of the
j-th index.
Step 2: Generate the best scheme and the worst scheme. The calculation process involves two ideal schemes, the optimal scheme and the worst-case scenario . The maximum and minimum values of the original data of each index i are taken as the optimal scheme and the worst scheme of the system, respectively. That is, the best scheme is and the worst scheme is .
Step 3: Calculate the Euclidean
distance between the target scheme and the optimal scheme and the Euclidean distance between the target scheme
and the worst scheme
. The calculation method is as follows:
Step 4: Calculate the closeness. The closeness degree can be calculated according to the distance from the best and worst scheme. The greater the closeness degree is, the better the scheme is. The calculation method is as follows:
represents the closeness.
According to the closeness of the system, we can judge whether the safety protection of the system is reliable. The greater the pasting progress, the closer the system is to the optimal scheme and the farther it is from the worst scheme, indicating that the better the system security protection, the better its security.
6. Case Analysis
6.1. Analytic Hierarchy Process Weight Calculation
In this paper, experts are invited to compare and scale indexes at each level to construct a judgment matrix. Taking the first-level index layer as an example, an example analysis was carried out, and the results are shown in
Table 1.
It can be seen from the analysis results that the secure computing environment occupies the largest weight, which is 0.4073 after normalization. The weight of the safe physical environment index is the smallest, which is 0.0541 after normalization, and both the CR and CI are less than 0.1, which is consistent.
The weights were calculated by the AHP method for other secondary indexes, and the results are summarized as shown in
Table 2. Among the related standards of classified protection 2.0, the secure computing environment contains the most general security requirements and is the most important index item to ensure the safe operation of the power information system. Therefore, the weight of its secure computing environment is the highest using the AHP, which is 0.4073.
Taking the weight analysis of the secondary indicator data security in a secure computing environment as an example, data security has the highest weight among all secondary indexes, at 0.1916. Data security includes key contents such as data integrity, confidentiality, personal information protection, and residual information protection, and is closely related to the basic services of the power information system, electricity security, and user information protection. Therefore, it is reasonable to have the highest total weight of data security.
6.2. Entropy Weight Method Weight Calculation
The weight of the entropy weight method is calculated based on the similar and historical data of the power information system classified protection evaluation. In this paper, based on the network security level evaluation reports of six information systems, according to the quantitative rules shown in the preceding text and the attached table, the following raw data table (
Table 3) was formed by summarizing and sorting out the indexes.
The smaller the information entropy of an index, the smaller the dispersion of the original data of the evaluation object, and the smaller the security gap of this index in various systems, so the weight occupied by this index is also small. Formulas (15)–(18) were used to calculate the information entropy and weight of the evaluation indexes, and the specific results can be summarized in
Table 4.
As shown in
Table 4, among all the indexes obtained by the entropy weight method, the trusted verification
occupies the highest weight, which is 0.1527. It is easy to see from the analysis of the original data that the compliance of the
index of the trusted verification is the lowest, indicating that most systems tend to ignore this index during their security construction. Therefore, it is reasonable for trusted verification
to occupy the highest weight. In the evaluation of the graded protection of the six sample systems, the four indexes of physical access control
, communication network architecture
, communication transmission
, and audit management
almost all meet the evaluation requirements, indicating that most systems can effectively guarantee their reliability. Therefore, the weights of such indexes calculated by the entropy weight method are relatively small.
6.3. Comprehensive Weight Calculation
The comprehensive weight calculation method is shown in Formula (21). The comprehensive weight was calculated by combining the two-level index weight of the AHP and the entropy weight method, and the results are shown in
Table 5.
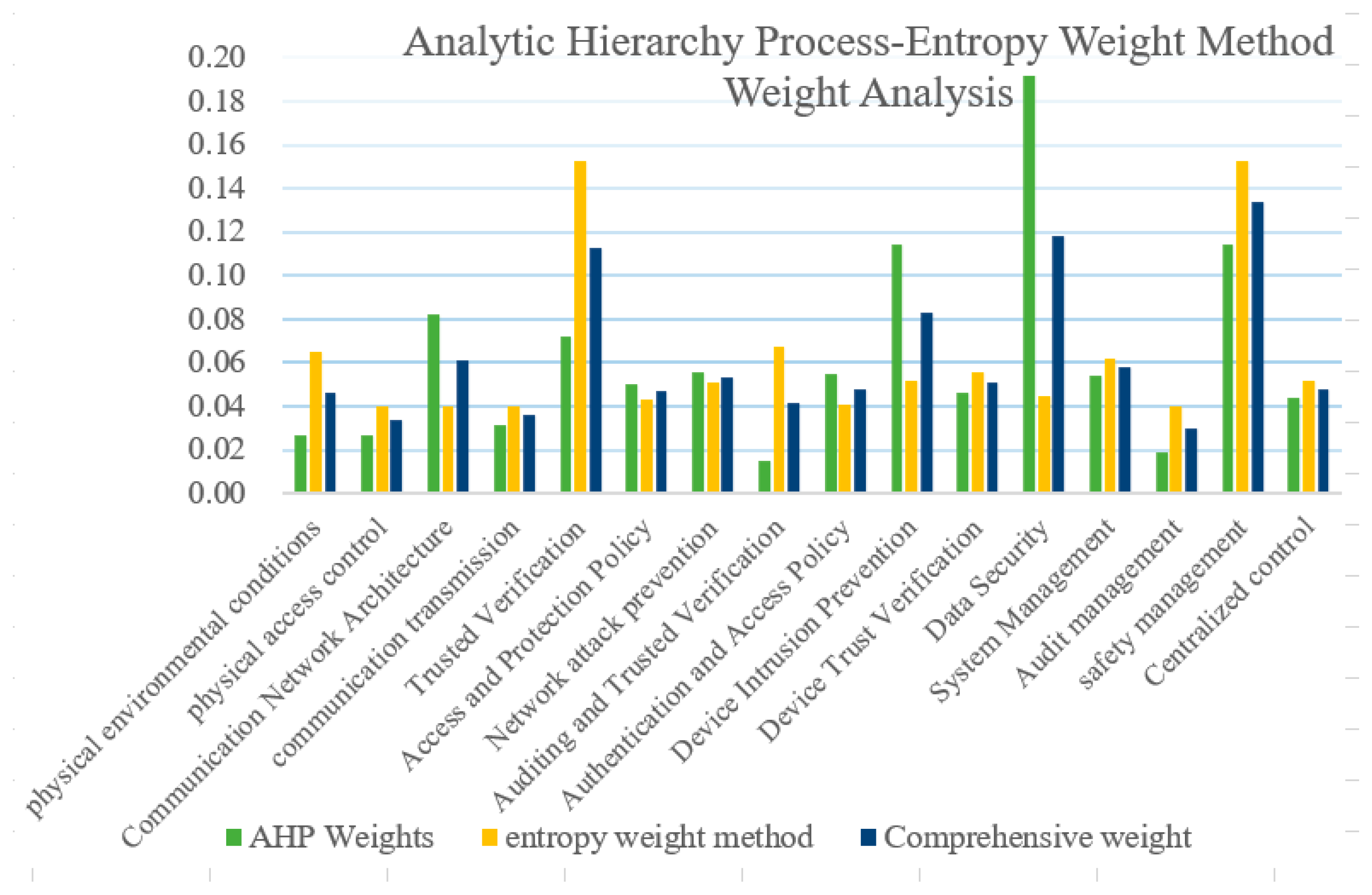
From the perspective of the first-level indexes, the weight of the AHP is not much different from the final comprehensive weight. The weight proportion of the secure computing environment is slightly reduced, but it still occupies the highest weight, which is consistent with the weight ranking obtained by expert evaluation.
From the point of view of the secondary indexes, the larger changes in weight are in credible verification , auditing and trusted verification , and device trust verification . Relative to the AHP weights, regarding , the comprehensive weight ranking has risen by 2 places, by 3 places, and by 2 places. This is the result of correcting the base weight using the entropy weight method. From the original data of the entropy weight method, it can be seen that the , , and indexes show that most systems do not meet the requirements of the indexes, indicating that the requirements of such indexes are easily ignored in the construction and maintenance of information systems, so it is reasonable to increase their comprehensive weights.
The weight changes can also be intuitively seen in
Figure 9. The comprehensive weight is between the weight of the AHP method and the entropy weight method, which reduces the subjective influence of the AHP method and avoids the problem that the AHP method relies on the subjective tendencies of decision makers. At the same time, it also weakens the degree of deviation between some conclusions of the entropy weight method and the actual situation, avoiding the problem of the entropy weight method relying on objective data, and the evaluation results are more accurate and objective.
6.4. Comprehensive Evaluation Analysis and Verification
Based on
Table 3 as the original data table, the optimal solution and the worst solution were constructed, as shown in
Table 6.
Based on the original data table and the comprehensive weight of each indicator calculated in the previous section, the Euclidean distance and Euclidean distance for the worst case between each system and the optimal solution was calculated using Formulas (23) and (24). The closeness was calculated using Formula (25). The specific calculation results are shown in the following table.
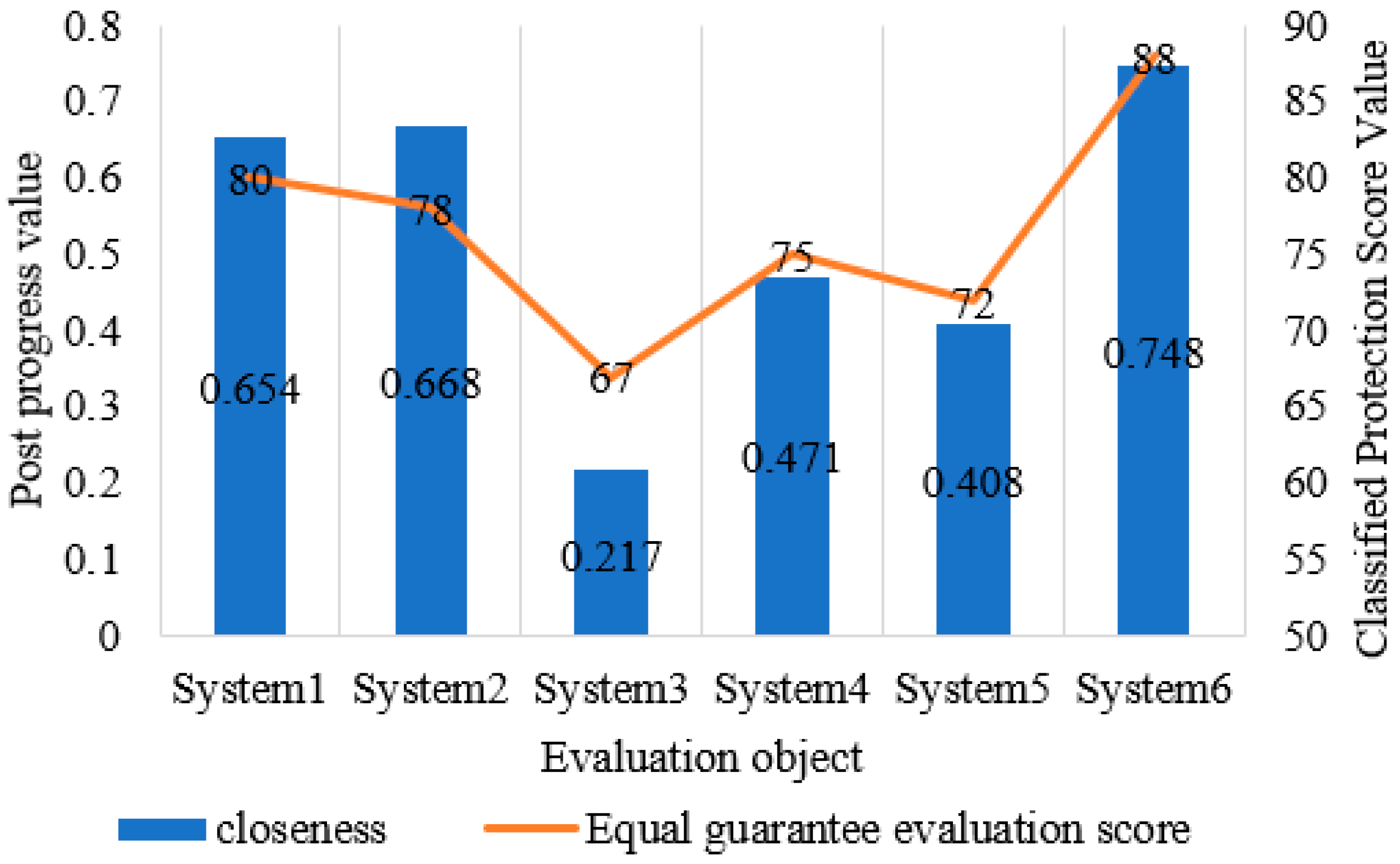
The comprehensive evaluation results based on the TOPSIS algorithm are shown in
Table 7. It can be seen that the Euclidean distance
of the optimal solution of system 6 is the smallest, which is 0.151, indicating that it is the closest to the optimal solution
. The Euclidean distance
of the worst scheme of system 6 is the largest, which is 0.449, indicating that it is the farthest from the worst scheme. System 6 has the highest degree of closeness C, which is 0.748, indicating that system 6 is the closest to the optimal solution.
Combined with the analysis from a practical point of view, several secondary indexes with a large proportion of comprehensive weight were analyzed: safety management
, trusted verification
, and network attack prevention
. The index evaluation of system 6 is the optimal solution or close to the optimal solution, and the comprehensive evaluation result has certain rationality. The graded protection test scores of the six power information systems selected in this paper were compared and analyzed with the TOPSIS post-progress calculation results, as shown in
Figure 10. The results show that the TOPSIS-based comprehensive evaluation results are basically consistent with the grade protection evaluation results, which confirms the scientificity and practicability of the evaluation model.
7. Conclusions
This paper takes classified protection 2.0 as the starting point and combines relevant standards for power information system evaluation. It evaluates the security of the power information system from five aspects: secure physical environment, secure communication network, secure area boundary, secure computing environment, and security management center. It constructs an evaluation index system that takes into account classified protection 2.0 and combines the analytic hierarchy process and entropy weight method to construct reasonable index weights from both subjective and objective aspects. In addition, this paper integrates Trusted Computing into the power system and constructs a power system security protection model, which has a certain positive guiding significance for improving the overall security of the power information system, helps to build a complete power information system network security protection system, and comprehensively improves the defense capability.
In this paper, the expert scores and the rating protection evaluation reports of the six systems are summarized and sorted into the original data, the comprehensive weight is calculated, and the comprehensive weight changes are compared and analyzed. The analytic hierarchy process (AHP) shows that in the relevant standards of classified protection 2.0, the secure computing environment contains the most common security requirements and is the most important index to ensure the safe operation of the power information system. Among all indexes obtained by the entropy weight method, credible verification accounts for the highest weight. It is easy to see from the analysis of the original data that the conformance of the credible verification index is the lowest, so it is reasonable that the credible verification accounts for the highest weight. Finally, by calculating the comprehensive weight, it can be concluded that the entropy weight method is used to correct the basic weight, resulting in a change in the weight ranking of relevant secondary indexes. This indicates that it is easy to overlook the requirements of such indexes in the construction and maintenance of information systems, so it is necessary to improve their comprehensive weight. The comparison and analysis of the TOPSIS closeness of the proposed evaluation model with the equivalency evaluation score confirmed the scientificity of the evaluation model.