Current Status and Perspective of Vulnerability Assessment of Cyber-Physical Power Systems Based on Complex Network Theory
Abstract
:1. Introduction
1.1. Motivation
1.2. Necessity
1.3. Organization
2. The Connotation of CPPS Vulnerability Assessment Research
2.1. The Definition of CPPS Vulnerability Assessment
- Its triggers are high threat, such as deliberate attacks and extreme weather.
- The consequences of events with low probability and high risk include system destabilization, major power outages, and severe structural damage.
- Its assessment is negative, which is a relative measure of the degree of damage to the system.
2.2. The Difference between Vulnerability and Risk, Reliability, and Resilience
2.2.1. The Difference between Vulnerability and Risk
- Regarding predisposing factors, all uncertainties are considered in risk assessment, whereas vulnerability assessment focuses solely on high-threat factors.
- Event consequences are the subject of risk assessment studies, encompassing events that can have a negative impact on the system. In contrast, vulnerability assessments concentrate on events characterized by severe negative impacts.
2.2.2. The Difference between Vulnerability and Reliability
- Regarding the predisposing factors, reliability necessitates attention to both the duration (occurrence) and the probability of occurrence of these factors. These factors can be diverse, considering not only uncertainties but also certainties, such as planned outages of components and reasonably expected unplanned outages [44]. In contrast, vulnerability does not concern itself with the duration and probability of the predisposing events, as these factors are inherently uncertain. Additionally, reliability, in general, places more emphasis on high-probability and low-impact events [47].
- The assessment results differ for reliability and vulnerability. Reliability solely concentrates on the system’s continuous-time metric of continuously supplying power, whereas vulnerability encompasses all time-independent metrics related to negative structural and functional aspects.
- In relation to operating states, both normal and fault operating states are considered in reliability assessment, with the fault operating state commonly regarded as an criterion [48]. Conversely, vulnerability assessment focuses on evaluating the system specifically in the fault operating state.
2.2.3. The Difference between Vulnerability and Resilience
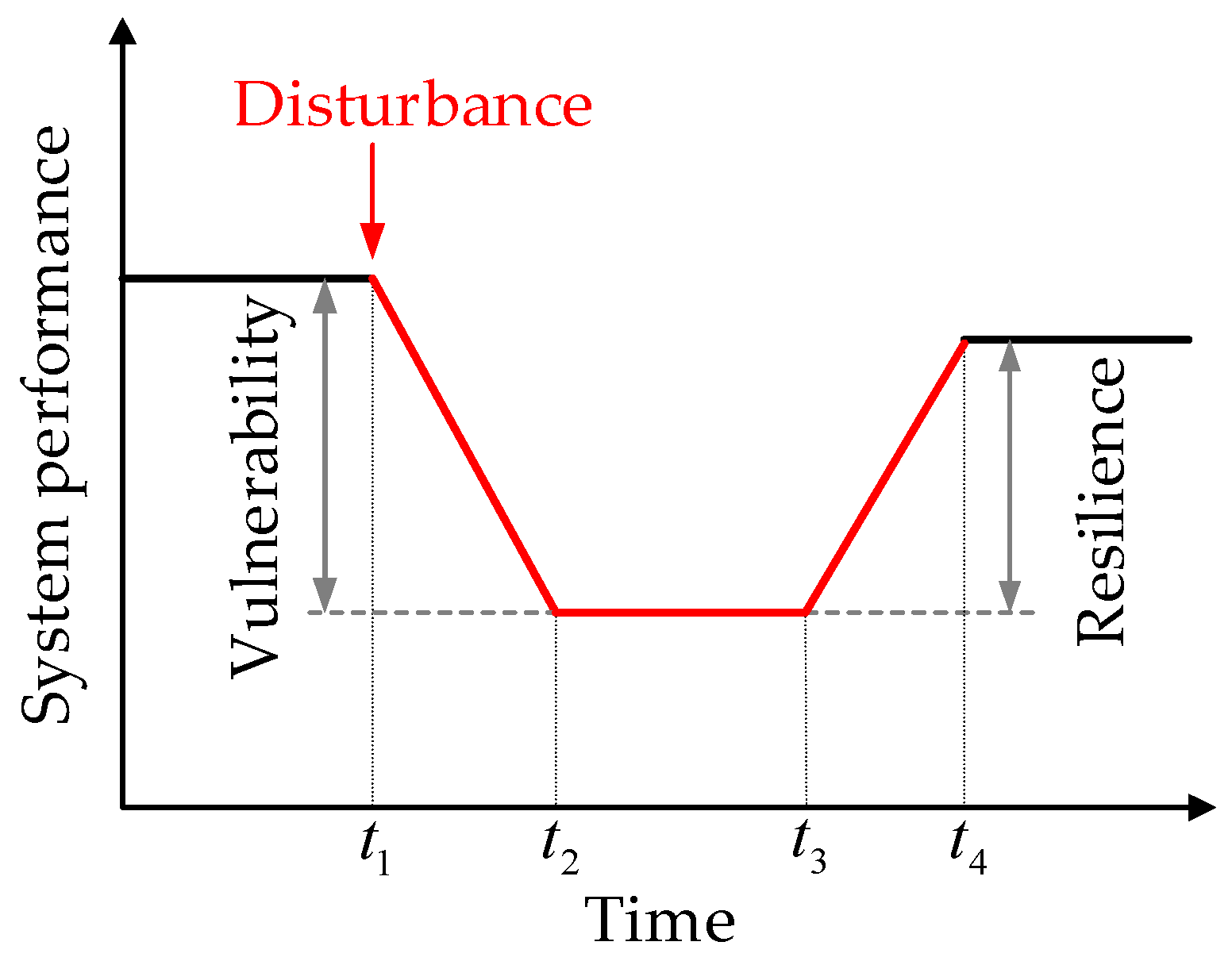
- In relation to the assessment results, resilience and vulnerability differ. Resilience, unlike vulnerability, not only focuses on the system’s ability to continuously power itself but also takes into account the time it takes for the system to recover from a failure to its prefailure operational state [52]. This measurement involves continuous time. Additionally, vulnerability can, to some extent, indicate the system’s resilience ability [56]. As shown in Figure 1, when the power grid encounters a disturbance event, vulnerability affects the severity of the system damage, and when the losses reach a certain level, it becomes challenging for the system to return to a normal state. In other words, if the system exhibits greater vulnerability, disturbances can propagate rapidly and extensively within the system (as discussed in Section 5), resulting in difficulties in recovery. This implies that the system possesses lower resilience.
- Regarding the operating state, resilience takes into consideration the system operating state before, during, and after the failure, whereas vulnerability solely measures the system’s performance during the failed operating state.
2.3. Classification of Vulnerability Assessment
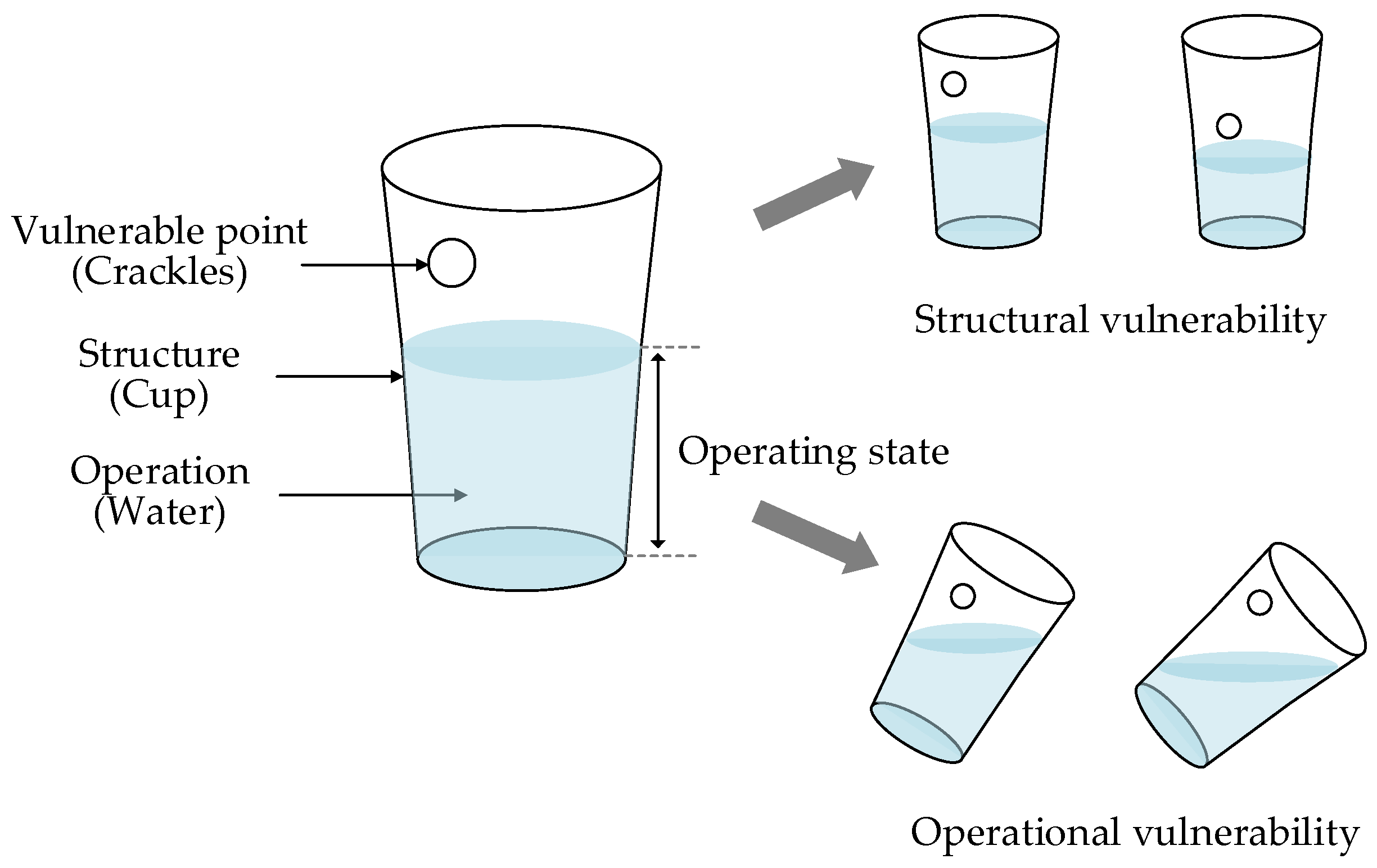
2.3.1. Structural Vulnerability and Operational Vulnerability
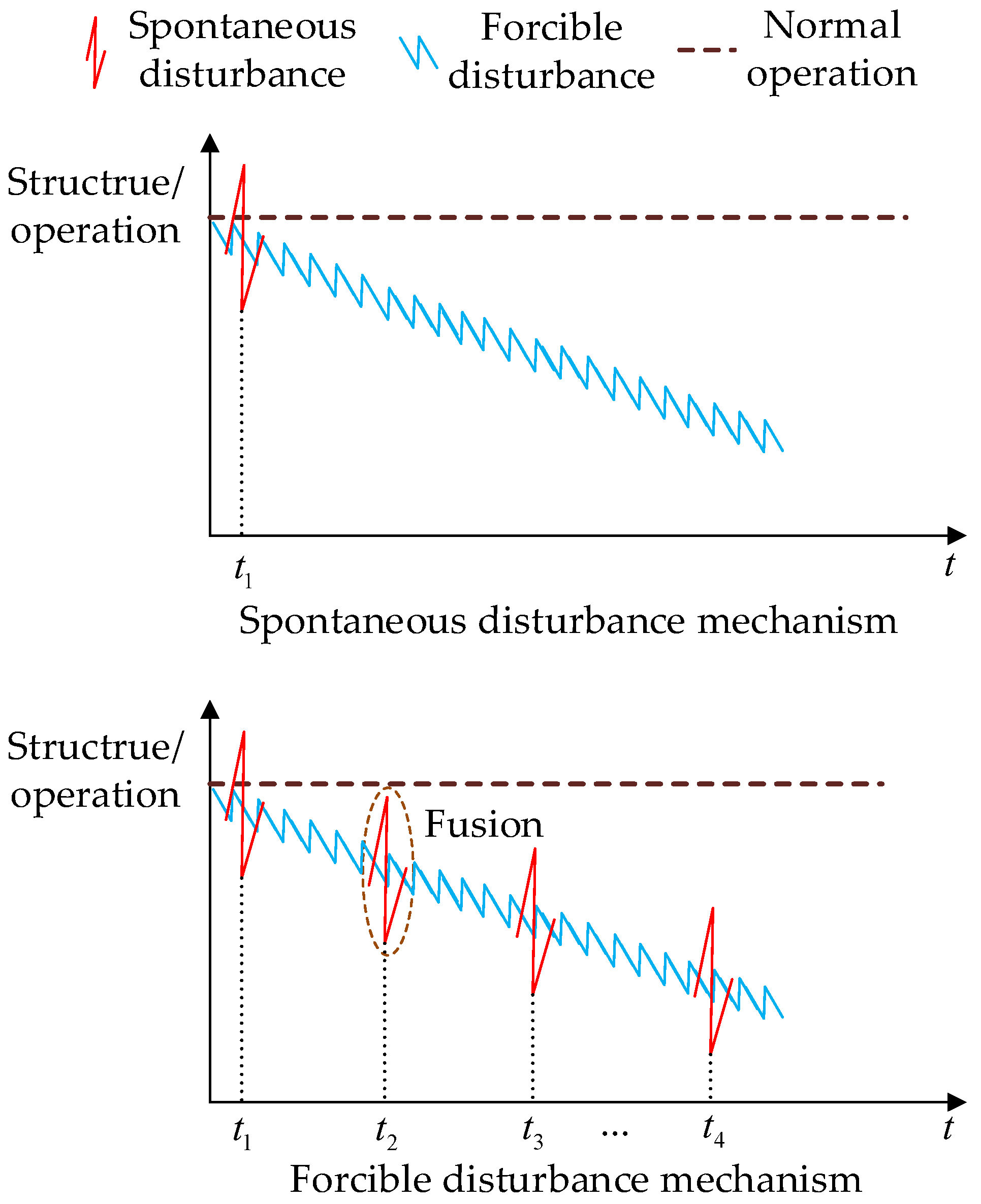
2.3.2. Spontaneous and Forcible Disturbance Vulnerability
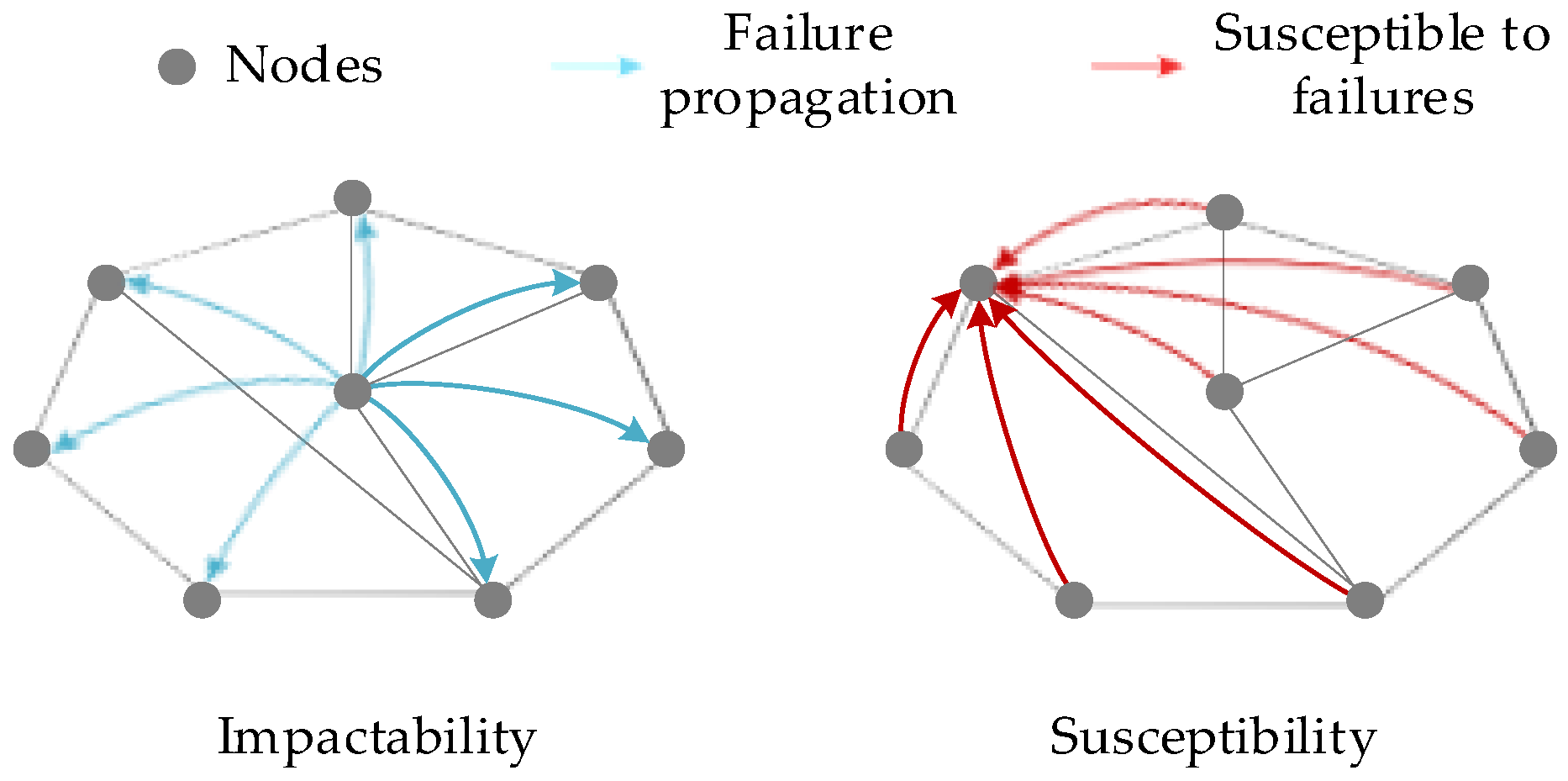
2.3.3. Impactability Vulnerability and Susceptibility Vulnerability
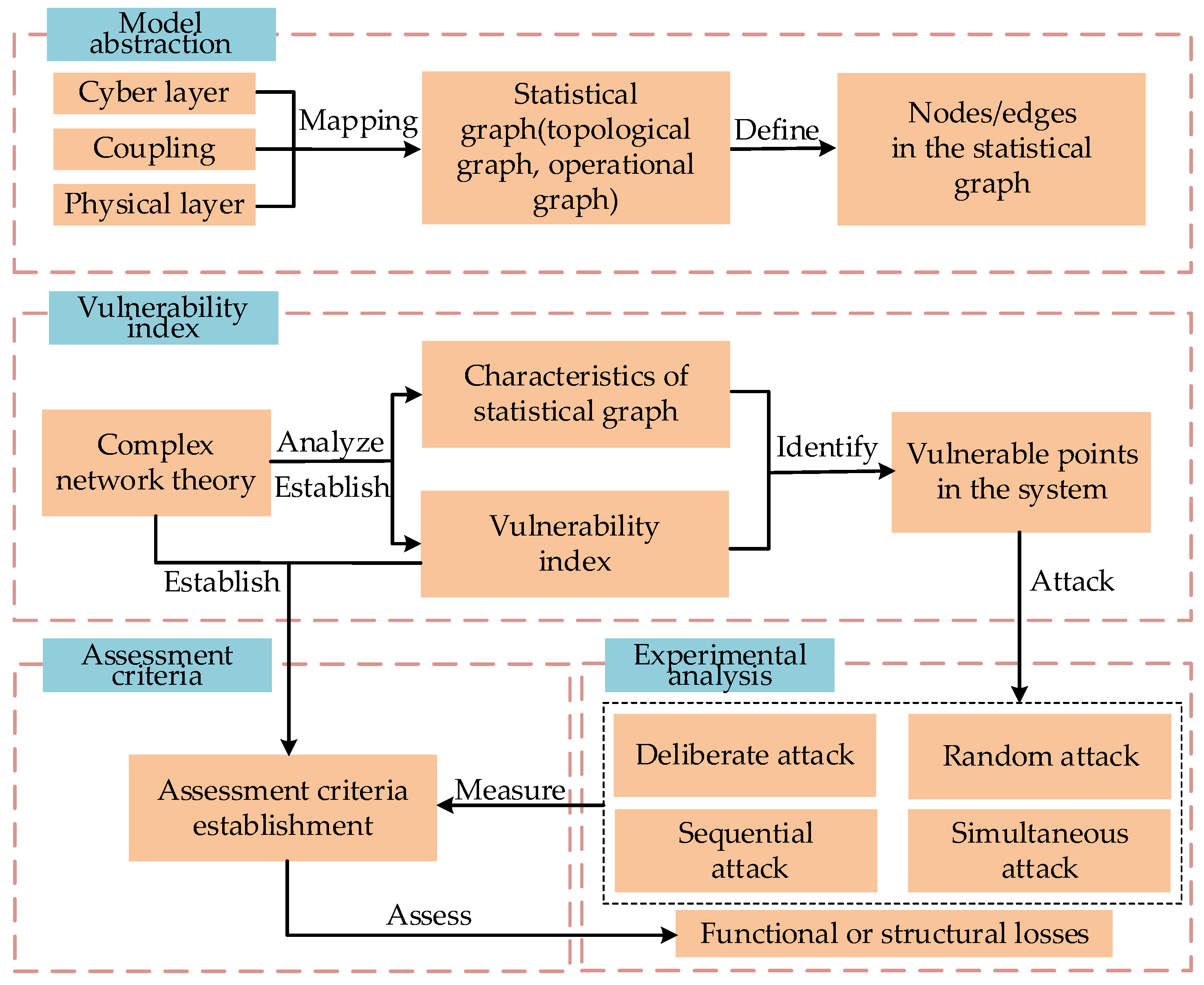
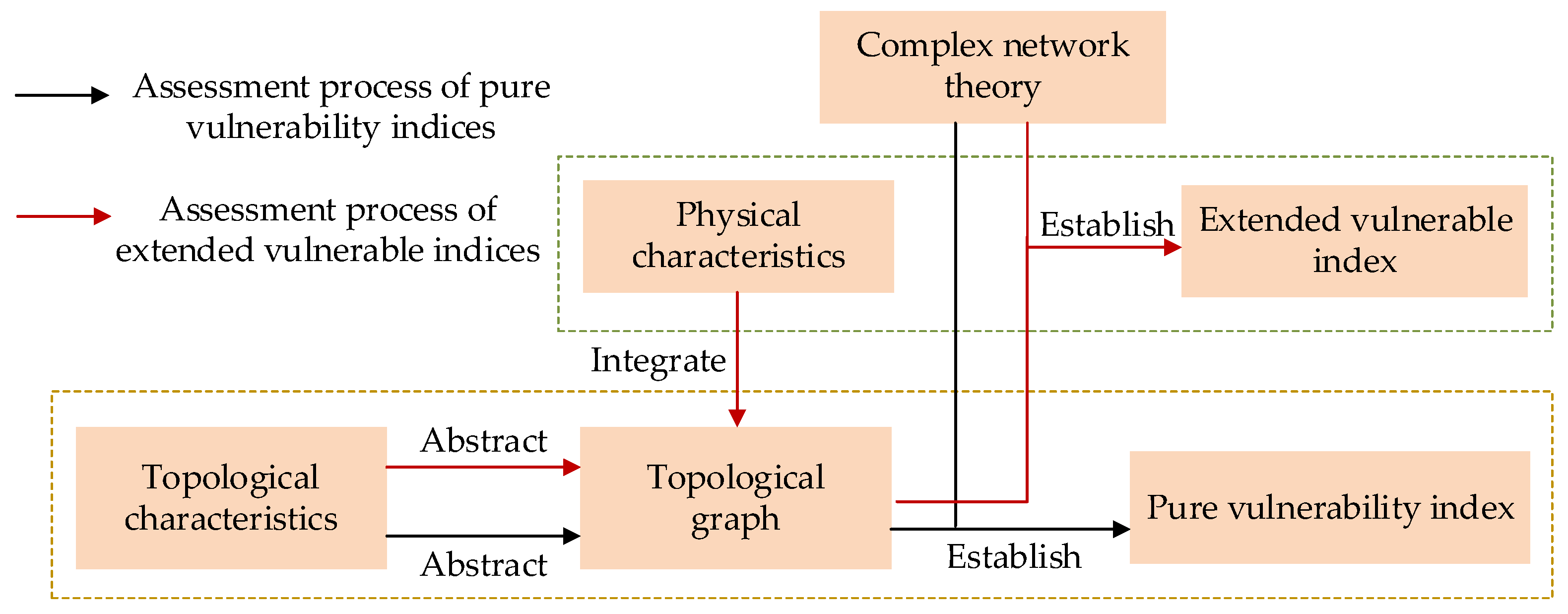
3. The Foundation Framework for CPPS Vulnerability Assessment Based on Complex Network Theory
3.1. Feasibility of Complex Network Theory in CPPS Vulnerability Assessment Research
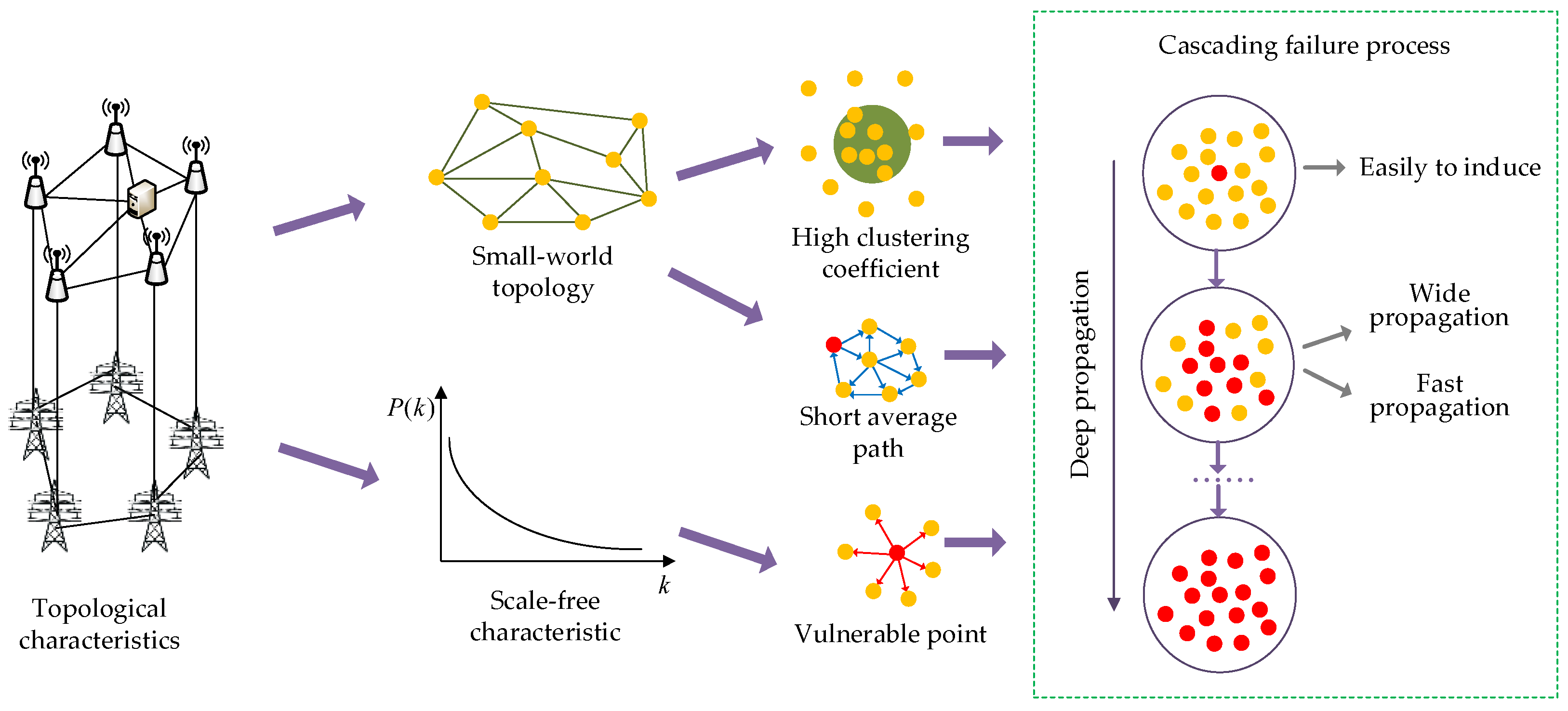
- Complexity: The power grid has transformed into a high-dimensional, nonlinear, and complex artificial network [71], with a wide spatial distribution and a large range of disturbance propagation, as a result of power grid interconnection and continuous expansion in scale [72]. Simultaneously, the power grid’s evolution into a complex cyber-physical system characterized by multidimensional heterogeneity and intricate interaction mechanisms further adds to its complexity [73]. On the one hand, the CPPS is subject to various complex and variable internal and external threat factors, with contingencies and correlations among these factors. On the other hand, the interrelationships between components and systems, as well as the inter-component relationships, are closely tied to the system’s topology and operation. The convergence and interplay of these aspects contribute to the highly complex failure mechanism of the system, challenging conventional analysis methods and imposing limitations on vulnerability assessment. To address this challenge, complex network theory emerges as a promising analytical approach from the field of complexity studies. By employing complex network theory, one can effectively explore and elucidate the uncertainty and intricate characteristics inherent in vulnerability assessment, thus offering a novel perspective to tackle the complexity of the system.
- Similarity: From the perspective of basic functions, both the cyber network and the physical network within the CPPS share similarities with other infrastructure, as they facilitate the transportation or exchange of material, whether tangible or intangible [74,75]. Considering the structural characteristics, the CPPS topology exhibits some correlation with the system performance and operational characteristics [70]. Regarding operational attributes, CPPSs demonstrate self-organized critical properties and kinetic characteristics in fault propagation [76]. As these properties are typical of complex systems and tightly linked to the system’s vulnerability points, they offer substantial guidance for the implementation of complex network theory in CPPS vulnerability assessment.
- Holistic: The classical electrical theory has its foundation in a reductionist approach to analysis [70], leading traditional vulnerability assessment methods for steady-state and transient states to focus more on qualitative analysis of the local electrical–physical characteristics of the system or individual components, as well as the operational attributes the system [77,78]. However, assessing the vulnerability of a CPPS requires the impact of interactions between the cyber network and the physical network to be considered. The conventional approach of studying vulnerability in the CPPS solely from a single network perspective (either a cyber or a physical network) has proven quite limited [73,79]. In contrast, complex network theory represents an analytical approach rooted in systems theory, encompassing statistical analysis of the overall expression of the power system [80]. Consequently, it places greater emphasis on studying the statistical characteristics of faults among components and systems from a holistic standpoint, thereby revealing the system’s vulnerability. Thus, complex network theory introduces a novel analytical perspective for vulnerability assessment.
3.2. Research Topics of Complex Network Theory in CPPS Vulnerability Assessment
4. Current Status of Research on CPPS Vulnerability Assessment Based on Complex Network Theory
4.1. Structural Vulnerability Assessment Based on Complex Network Theory
| Nodes/Edges | Weights | Dynamic/Static | Meaning | Related Literature |
|---|---|---|---|---|
| Edges | Branch reactance (impedance) | Static | Characterize the power capacity of the transmission (the smaller the branch reactance, the greater the power transmitted under the same conditions) | [90,109,110,111,112,113,114] |
| Edges | Branch capacity | Static | Characterize the power capacity of the transmission (the larger the capacity, the greater the power capacity transmitted) | [115,116] |
| Edges | Branch voltage level | Static | Characterize the power capacity transmitted (the higher the voltage level, the higher the corresponding transmission capacity [117]) | [117] |
| Edges | Branch circuit impedance multiplied by the inverse of the voltage rating factor | Static | Characterize the power capacity of the transmission | [68] |
| Edges | Branch power transmission distribution factor | Dynamic (changes in generator load node pairs) | Characterize the sensitivity of each branch to the tidal transmission contribution | [57,93,102,118,119,120,121] |
| Edges | The probability that a branch circuit will be in normal operation for a certain period of time | Dynamic (branch operation time related) | Cumulative running time of the characterization branch | [122] |
| Edges | Branch current sharing factor | Dynamic (injection current and branch voltage variation) | Characterize the effect of unit injected power on the branch current | [95,123] |
| Edges | Current (power) flowing in the branch circuit after the generator load node pair and injection of current (power) | Dynamic (changes in generator load node pairs) | Characterize the degree of contribution of branch flows to the whole network | [92,97,124,125,126] |
| Nodes | Rated capacity or output of the generator node, actual or peak value of the load node | Static/dynamic (changes with flow distribution) | Characterize the importance of node transmission and distribution power | [97,116,117,124] |
| Basic Characteristic Quantity | Research Object | Operating State | Electrical Quantity | Meaning | Related Literature |
|---|---|---|---|---|---|
| Betweenness | Branch/node | Normal | Branch reactance, branch capacity | Characterize the importance of branch transmission and distribution power from a system perspective | [57,90,93,114,115,120,128] |
| Betweenness | Branch | Normal | Branch circuit current (power), generator rated (issued) power, load | Reflects the power transfer of the branch in the generation load node from a system perspective | [95,97,124,125,126] |
| Betweenness | Branch | N-1 standard | Branch power, generator capacity, peak load, branch impedance, branch capacity | Characterize the importance of branch transmission and distribution power and the coupling between the branches from a system perspective | [92] |
| Betweenness | Branch/node | Normal | The probability of normal operation time in a certain period of time for a branch | Characterize the continuous operation time of system components from a reliability perspective | [122] |
| Betweenness | Branch | Normal | Branch circuit voltage level, branch circuit impedance | Characterize the importance of branch transmission and distribution power from a system perspective | [68] |
| Betweenness | Branch | Normal | Node injection current, branch conductance | Characterize the importance of branch transmission and distribution power from a system perspective | [123] |
| Betweenness | Branch | N-1 standard | Kinetic energy of generator rotor | The degree of transient impulse to the branch circuit after the system is disturbed | [127] |
| Average path | Node | Normal | Branch reactance | Characterize the connectivity of nodes in the system | [110] |
| Degree | Node | Normal | Node injection power, branch voltage level | Integrated characterization of the topological and power characteristics of the system | [117] |
| Degree | Node | Normal | Branch reactance | Characterize the power transmission capability of the node | [128] |
| Degree | Node | Normal | The probability of normal operation time in a certain period of time for a branch | Characterize the node’s duration of operation from a reliability perspective | [122] |
| Maximum flow | Branch/node | Normal | Branch reactance, branch capacity | Characterize the carrying capacity of the branch/node for system flow | [112,116,118] |
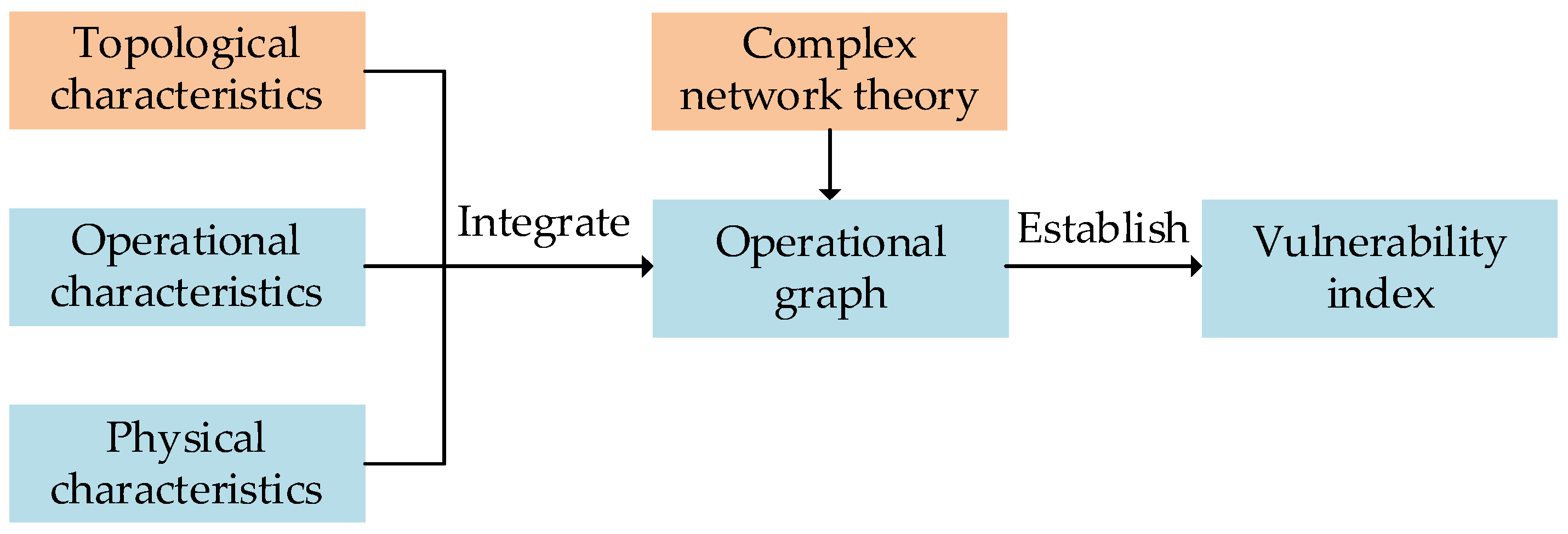
4.2. Operational Vulnerability Assessment Based on Complex Network Theory
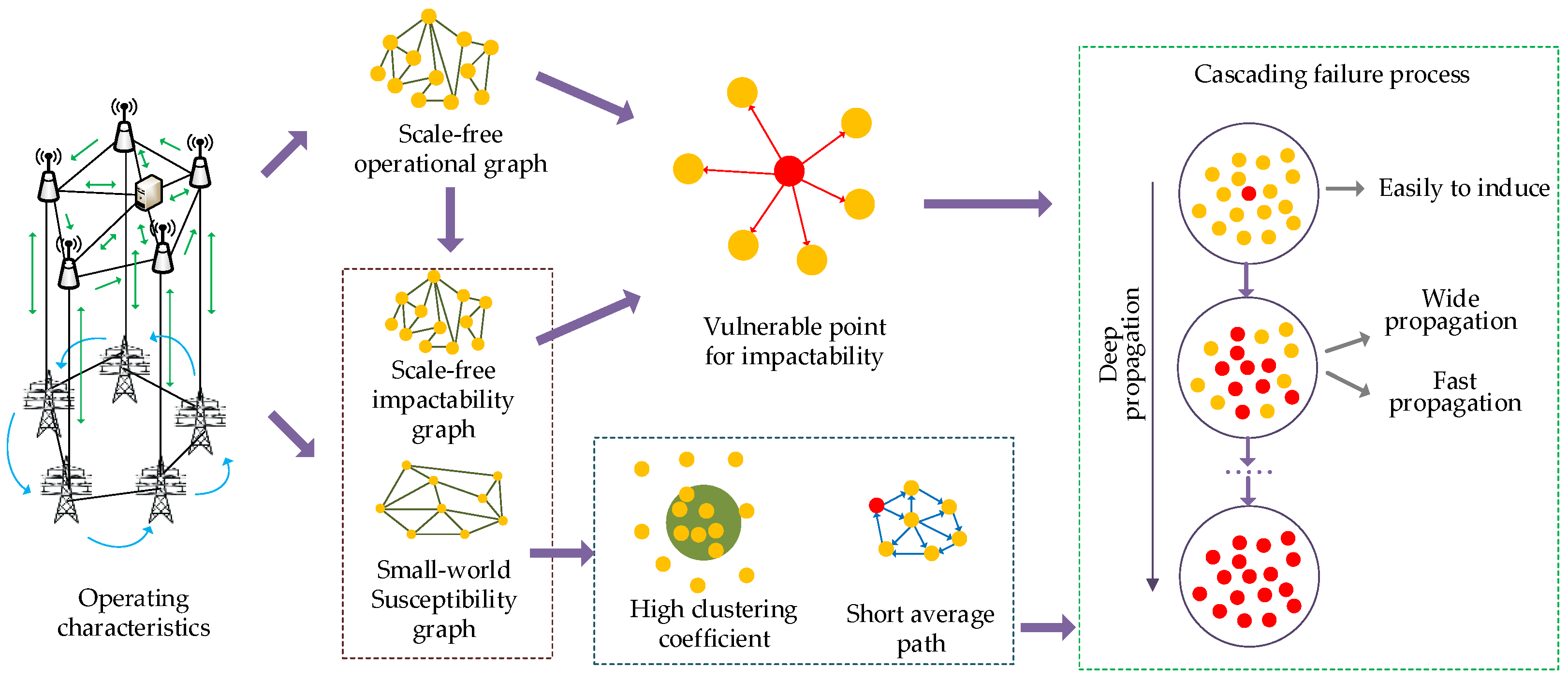
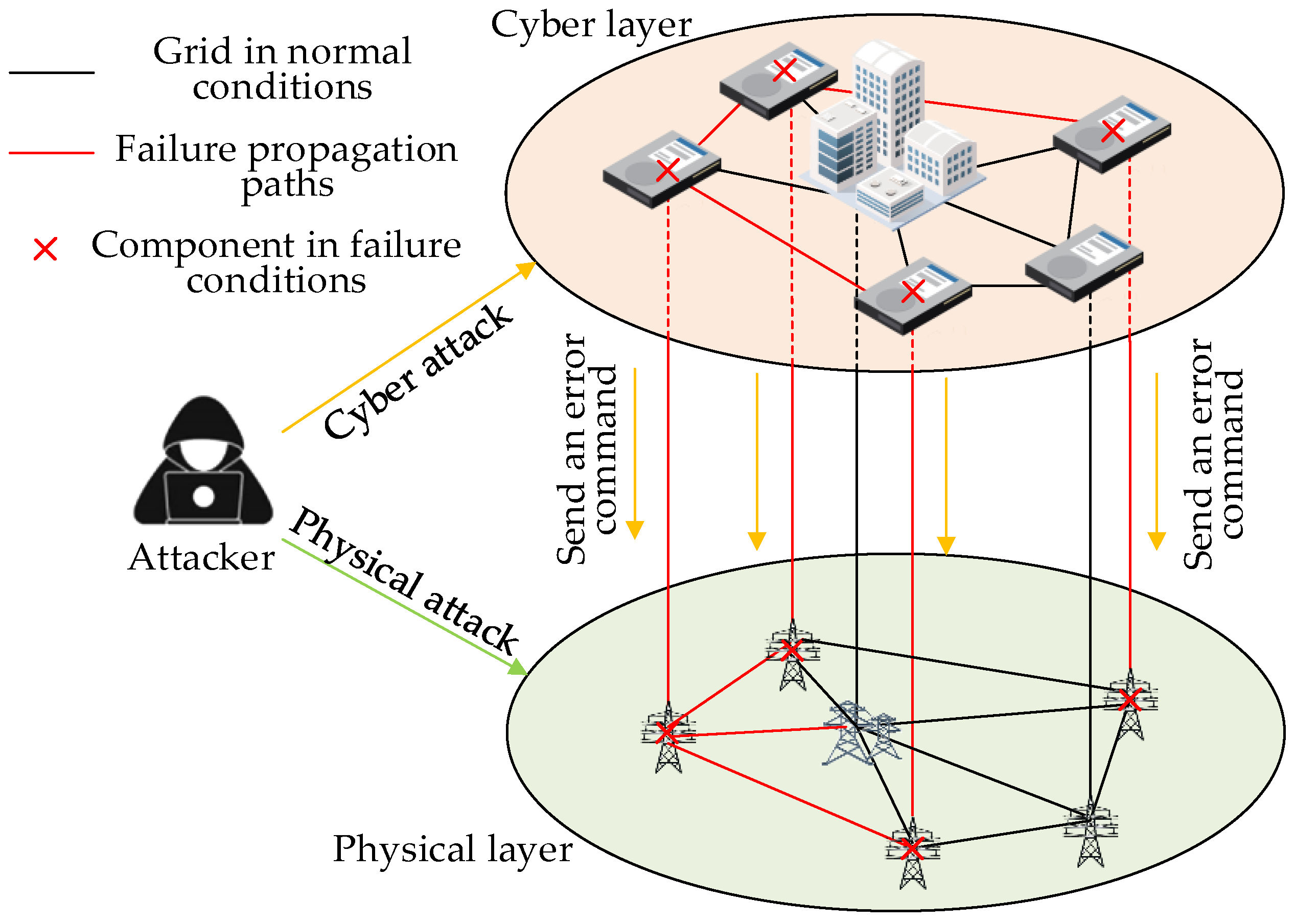
5. Interrelationship between System Vulnerability and Cascading Failures
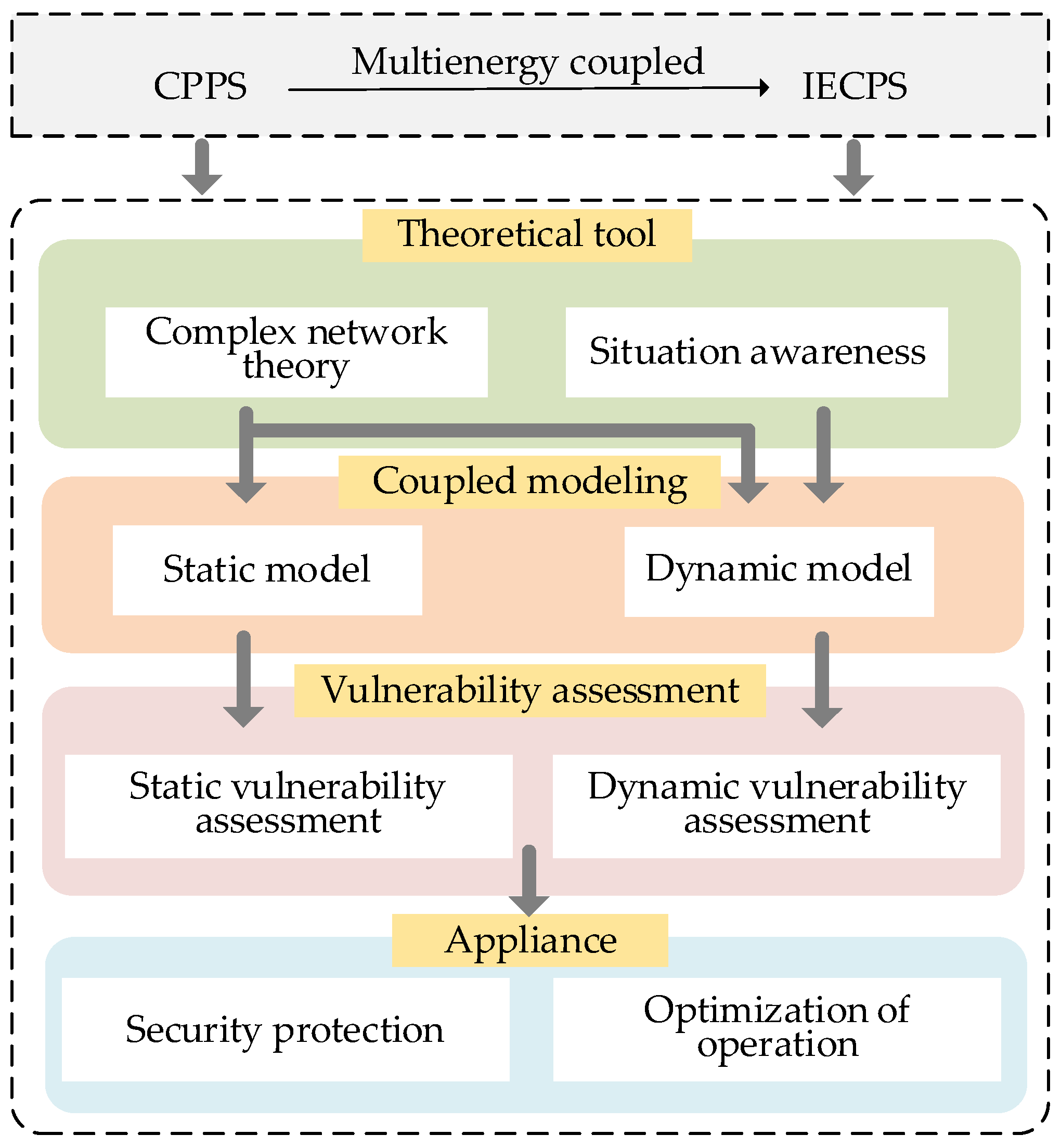
6. Applications and Prospects of Vulnerability Assessment Based on Complex Network Theory
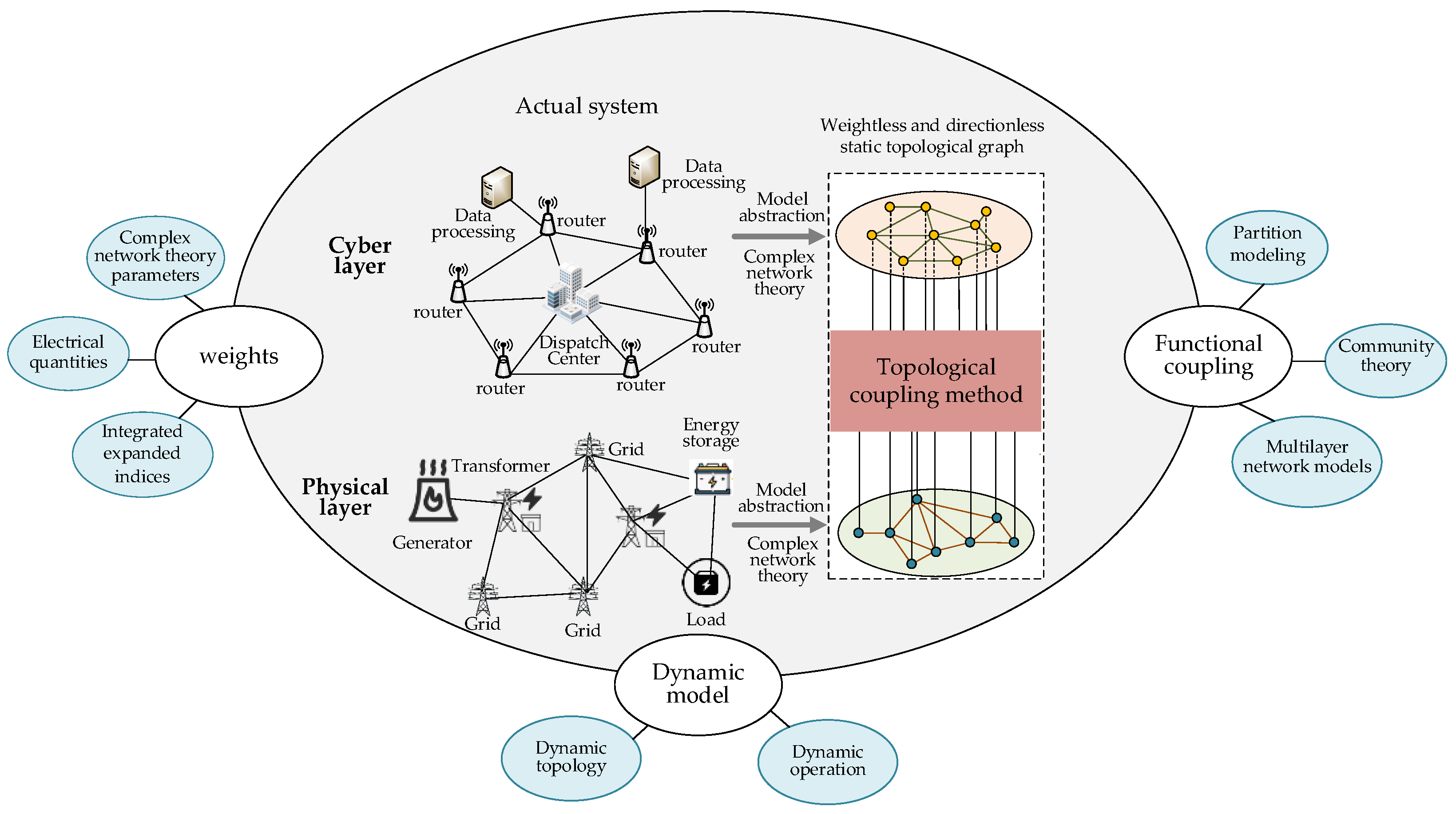
6.1. CPPS Coupling Modeling and Analysis
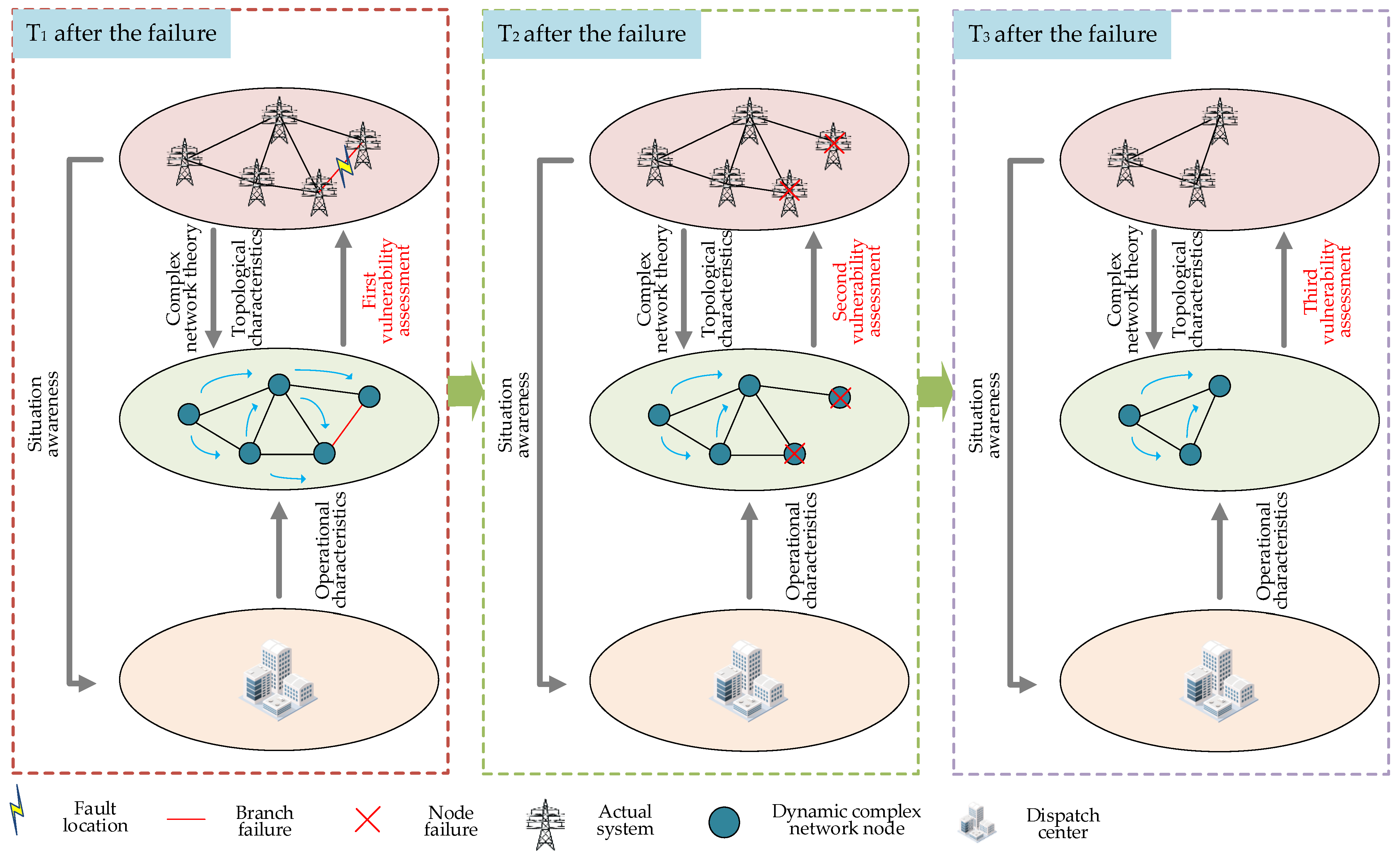
6.2. Dynamic Vulnerability Assessment Based on Situation Awareness
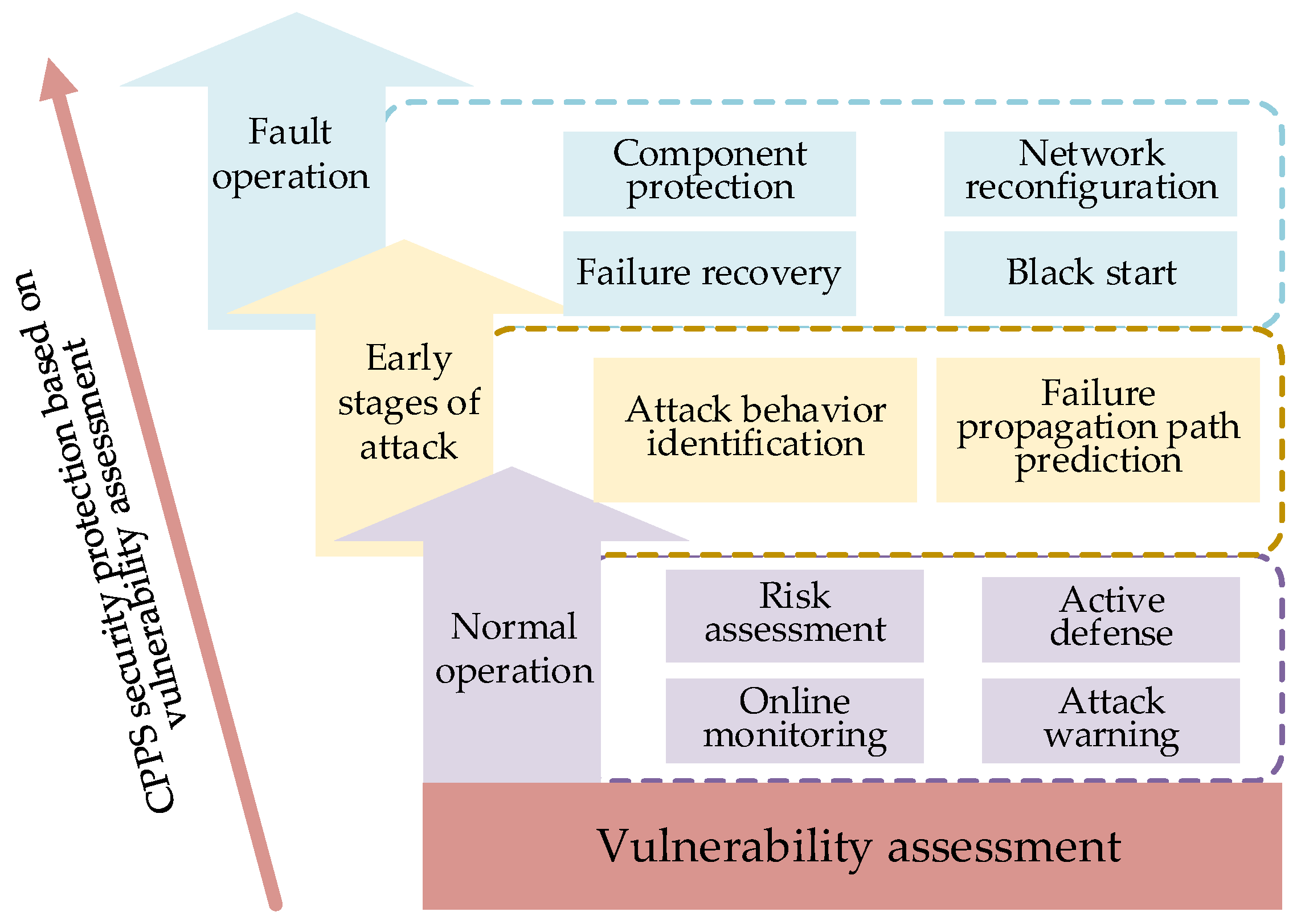
6.3. Security Protection of CPPS Based on Vulnerability Assessment
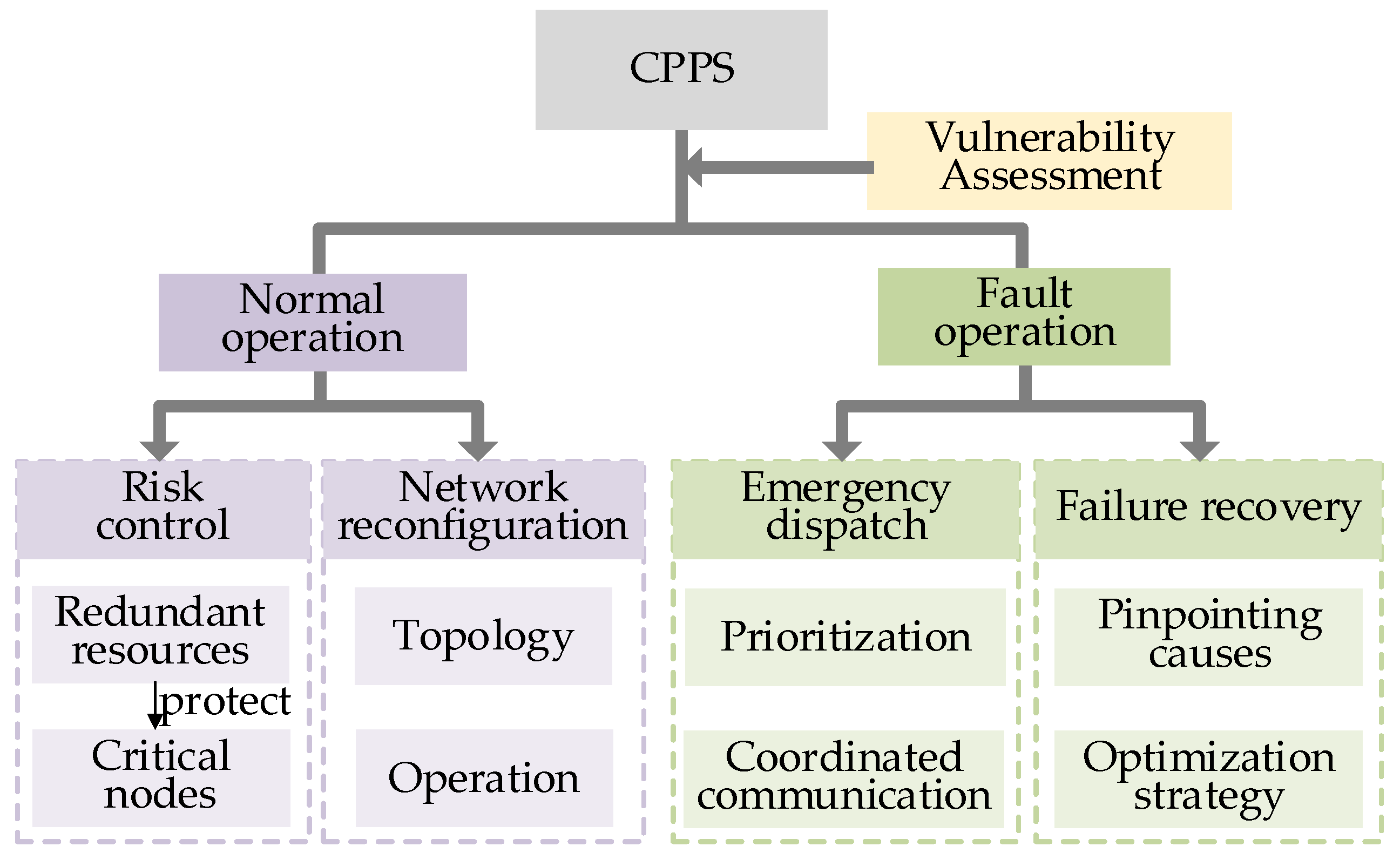
6.4. Optimization Operation of CPPS Based on Vulnerability Assessment
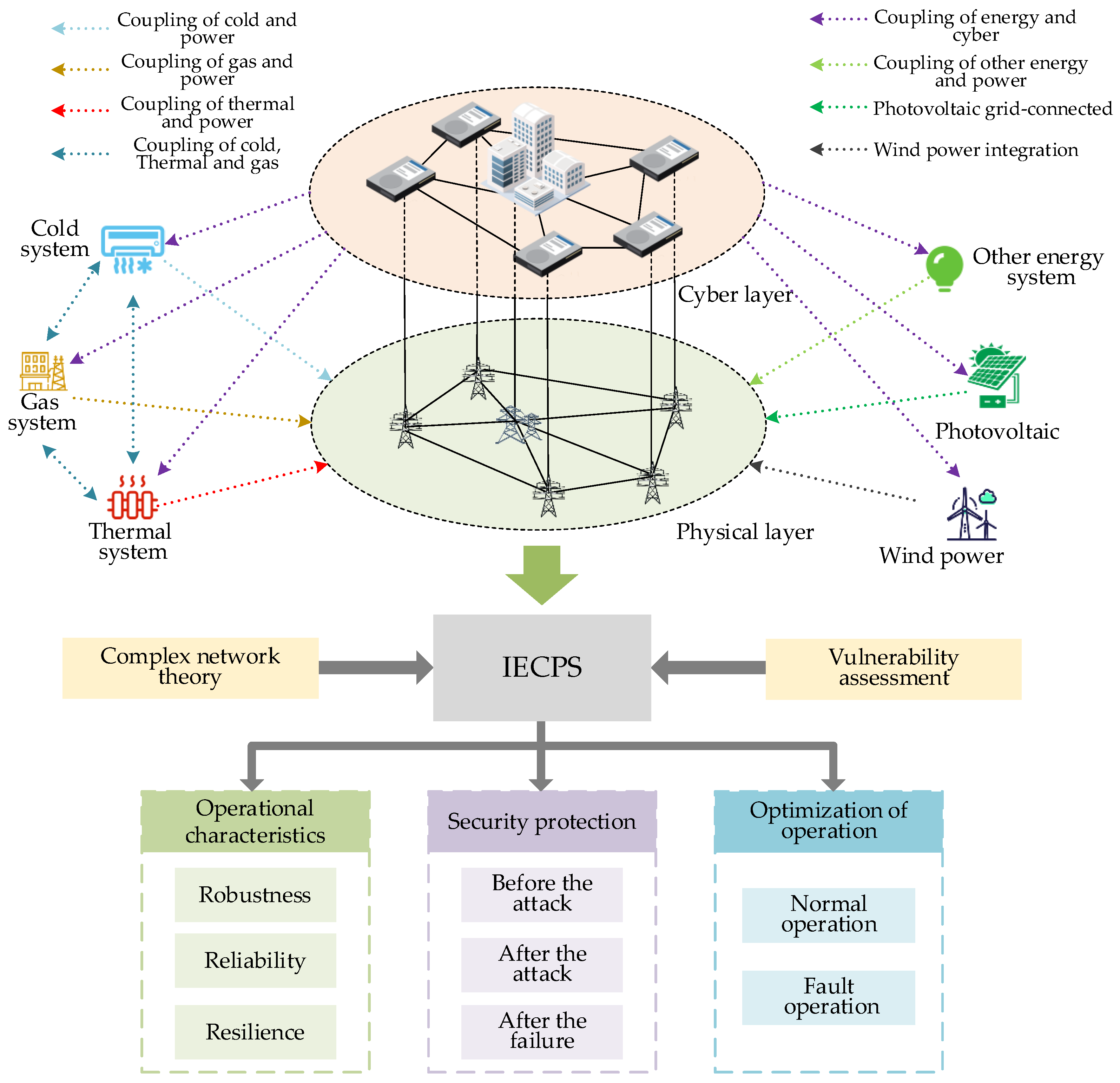
6.5. Vulnerability Assessment of the Integrated Energy Cyber–Physical System
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cai, Y.; Huang, T.; Ettore, B.; Cao, Y.; Li, Y. Self-Sustainable Community of Electricity Prosumers in the Emerging Distribution System. IEEE Trans. Smart Grid 2017, 8, 2207–2216. [Google Scholar] [CrossRef]
- Wei, X.; Gao, S.; Zang, T.; Huang, T.; Wang, T.; Li, D. Social Energy Internet: Concept, Architecture and Outlook. Proc. CSEE 2018, 38, 4969–4986+5295. [Google Scholar]
- Gao, S.; Gao, F.; Liu, Y.; Zang, T.; Huang, T.; Chen, K. Prospect of Research on Self-Aware Energy Internet. Autom. Electr. Power Syst. 2021, 45, 1–17. [Google Scholar]
- Chen, Q.; Liu, D.; Lin, J.; He, J.; Wang, Y. Business Models and Market Mechanisms of Energy Internet(1). Power Syst. Technol. 2015, 39, 3050–3056. [Google Scholar]
- Liu, D.; Zeng, M.; Huang, R.; Ji, L.; Chen, Q.; Duan, J.; Li, Y. Business Models and Market Mechanisms of E-Net(2). Power Syst. Technol. 2015, 39, 3057–3063. [Google Scholar]
- He, R.; Long, L.; Zhang, B.; Wang, Y.; Xiao, Z. Cyber System Physicalizing Modeling and Analysis Method in Cyber-Physical Power Systems. Proc. CSEE 2022, 1–14. Available online: http://kns.cnki.net/kcms/detail/11.2107.TM.20220909.1500.002.html (accessed on 21 August 2023).
- Zhang, Y.; Liu, W.; Liu, G.; Huang, S. Modeling and Vulnerability Analysis of Electric Cyber Physical System Considering Topological Correlation and Double Coupling. Proc. CSEE 2021, 41, 5486–5500. [Google Scholar]
- Yuan, H.; Niu, F.; Gao, X. Establishment and Application of an Urban Economic Vulnerability Evaluation System. Acta Geogr. Sin. 2015, 70, 271–282. [Google Scholar]
- Wang, Y.; Lan, H. Fresh Agricultural Products Supply Chain in the E-Commerce Environment Vulnerability Model. In Proceedings of the 2015 International Conference on Logistics, Informatics and Service Sciences (LISS), Barcelona, Spain, 27–29 July 2015; pp. 1–4. [Google Scholar]
- Aretano, R.; Semeraro, T.; Petrosillo, I.; Marco, A.D.; Pasimeni, M.R.; Zurlini, G. Mapping Ecological Vulnerability to Fire for Effective Conservation Management of Natural Protected Areas. Ecol. Model. 2015, 295, 163–175. [Google Scholar] [CrossRef]
- He, L.; Shen, J.; Zhang, Y. Ecological Vulnerability Assessment for Ecological Conservation and Environmental Management. J. Environ. Manag. 2018, 206, 1115–1125. [Google Scholar] [CrossRef] [PubMed]
- Du, W.; Mathur, A.P. Testing for Software Vulnerability Using Environment Perturbation. Qual. Reliab. Eng. Int. 2002, 18, 261–272. [Google Scholar] [CrossRef]
- Rahimi, S.; Zargham, M.R. Vulnerability Scrying Method for Software Vulnerability Discovery Prediction Without a Vulnerability Database. IEEE Trans. Reliab. 2013, 62, 395–407. [Google Scholar] [CrossRef]
- Rodríguez-Núñez, E.; García-Palomares, J.C. Measuring the Vulnerability of Public Transport Networks. J. Transp. Geogr. 2014, 35, 50–63. [Google Scholar] [CrossRef]
- Cats, O.; Jenelius, E. Dynamic Vulnerability Analysis of Public Transport Networks: Mitigation Effects of Real-Time Information. Netw. Spat. Econ. 2014, 14, 435–463. [Google Scholar] [CrossRef]
- Panteli, M.; Trakas, D.N.; Mancarella, P.; Hatziargyriou, N.D. Boosting the Power Grid Resilience to Extreme Weather Events Using Defensive Islanding. IEEE Trans. Smart Grid 2016, 7, 2913–2922. [Google Scholar] [CrossRef]
- Mathaios, P.; Cassandra, P.; Sean, W.; Richard, D.; Pierluigi, M. Power System Resilience to Extreme Weather: Fragility Modeling, Probabilistic Impact Assessment, and Adaptation Measures. IEEE Trans. Power Syst. 2017, 32, 3747–3757. [Google Scholar]
- Bompard, E.; Huang, T.; Wu, Y.; Cremenescu, M. Classification and Trend Analysis of Threats Origins to the Security of Power Systems. Int. J. Electr. Power Energy Syst. 2013, 50, 50–64. [Google Scholar] [CrossRef]
- Anderson, C.W.; Santos, J.R.; Haimes, Y.Y. A Risk-Based Input-Output Methodology for Measuring the Effects of the August 2003 Northeast Blackout. Econ. Syst. Res. 2007, 19, 183–204. [Google Scholar] [CrossRef]
- Ralph, L. Stuxnet: Dissecting a Cyberwarfare Weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar]
- Mao, A.; Zhang, G.; Lü, Y.; Gao, J. Analysis on Large-Scale Blackout Occurred in South America and North Mexico Interconnected Power Grid on Sept. 8, 2011 and Lessons for Electric Power Dispatching in China. Power Syst. Technol. 2012, 36, 74–78. [Google Scholar]
- Tang, Y.; Bu, G.; Yi, J. Analysis and Lessons of the Blackout in Indian Power Grid on July 30 and 31. Proc. CSEE 2012, 32, 167–174. [Google Scholar]
- Guo, Q.; Xin, S.; Wang, J.; Sun, H. Comprehensive Security Assessment for a Cyber Physical Energy System a Lesson from Ukraine’s Blackout. Autom. Electr. Power Syst. 2016, 40, 145–147. [Google Scholar]
- Zeng, H.; Sun, F.; Li, T.; Zhang, Q.; Tang, J.; Zhang, T. Analysis of “9.28” Blackout in South Australia and Its Enlightenment to China. Autom. Electr. Power Syst. 2017, 41, 1–6. [Google Scholar]
- Bai, J.; Liu, T.; Cao, G.; Chen, C. A Survey Vulnerability Assessment Method for Power System. Power Syst. Technol. 2008, 32, 26–30. [Google Scholar]
- Liu, C.C.; Jung, J.; Heydt, G.T.; Vittal, V.; Phadke, A.G. The Strategic Power Infrastructure Defense (SPID) System. A Conceptual Design. IEEE Control Syst. Mag. 2000, 20, 40–52. [Google Scholar]
- Li, Q.; Cao, Z.; Tanveer, M.; Pandey, H.M.; Wang, C. An Effective Reliability Evaluation Method for Power Communication Network Based on Community Structure. IEEE Trans. Ind. Appl. 2019, 56, 4489–4500. [Google Scholar] [CrossRef]
- Huang, T.; Voronca, S.L.; Purcarea, A.A.; Estebsari, A.; Bompard, E. Analysis of Chain of Events in Major Historic Power Outages. Adv. Electr. Comput. Eng. 2014, 14, 63–70. [Google Scholar] [CrossRef]
- Fouad, A.A.; Zhou, Q.; Vittal, V. System Vulnerability as a Concept to Assess Power System Dynamic Security. IEEE Trans. Power Syst. A Publ. Power Eng. Soc. 1994, 9, 1009–1015. [Google Scholar] [CrossRef]
- Zhou, Q.; Davidson, J.; Fouad, A.A. Application of Artificial Neural Networks in Power System Security and Vulnerability Assessment. IEEE Trans. Power Syst. A Publ. Power Eng. Soc. 1994, 9, 525–532. [Google Scholar] [CrossRef]
- Tamronglak, S.; Horowitz, S.H.; Phadke, A.G.; Thorp, J.S. Anatomy of Power System Blackouts: Preventive Relaying Strategies. IEEE Trans. Power Deliv. 1996, 11, 708–715. [Google Scholar] [CrossRef]
- Phadke, A.G.; Thorp, J.S. Expose Hidden Failures to Prevent Cascading Outages [in Power Systems]. IEEE Comput. Appl. Power 1996, 9, 20–23. [Google Scholar] [CrossRef]
- Liang, J.; Sankar, L.; Kosut, O. Vulnerability Analysis and Consequences of False Data Injection Attack on Power System State Estimation. IEEE Trans. Power Syst. A Publ. Power Eng. Soc. 2016, 31, 3864–3872. [Google Scholar] [CrossRef]
- Bompard, E.; Napoli, R.; Xue, F. Vulnerability of Interconnected Power Systems to Malicious Attacks under Limited Information. Int. Trans. Electr. Energy Syst. 2013, 18, 820–834. [Google Scholar] [CrossRef]
- Mohagheghi, S.; Javanbakht, P. Power Grid and Natural Disasters: A Framework for Vulnerability Assessment. In Proceedings of the 2015 Seventh Annual IEEE Green Technologies Conference, New Orleans, LA, USA, 15–17 April 2015; pp. 199–205. [Google Scholar]
- Kwasinski, A. Analysis of Vulnerabilities of Telecommunication Systems to Natural Disasters. In Proceedings of the 2010 IEEE International Systems Conference, San Diego, CA, USA, 5–8 April 2010; pp. 359–364. [Google Scholar]
- Rodriguez, C.M.F. Vulnerability and Robustness Indices against Blackouts in Power Grids; Alma Mater Studiorum—Università di Bologna: Bologna, Italy, 2013. [Google Scholar]
- Johansson, J.; Hassel, H.; Zio, E. Reliability and Vulnerability Analyses of Critical Infrastructures: Comparing Two Approaches in the Context of Power Systems. Reliab. Eng. Syst. Saf. 2013, 120, 27–38. [Google Scholar] [CrossRef]
- Office of Energy Assurance. Vulnerability Assessment Methodology—Electric Power Infrastructure; Department of Energy: Washington, DC, USA, 2002. [Google Scholar]
- Terje, A. On Some Recent Definitions and Analysis Frameworks for Risk, Vulnerability, and Resilience. Risk Anal. 2011, 31, 515–522. [Google Scholar]
- McCalley, J.D.; Vittal, V.; Abi-Samra, N. An Overview of Risk Based Security Assessment. In Proceedings of the 1999 IEEE Power Engineering Society Summer Meeting. Conference Proceedings (Cat. No. 99CH36364), Edmonton, AB, Canada, 18–22 July 1999; Volume 1, pp. 173–178. [Google Scholar]
- Feng, Y.; Wu, W.; Zhang, B.; Li, W. Power System Operation Risk Assessment Using Credibility Theory. IEEE Trans. Power Syst. 2008, 23, 1309–1318. [Google Scholar] [CrossRef]
- Blockley, D.I.; Agarwal, J.; Pinto, J.T.; Woodman, N.J. Structural Vulnerability, Reliability and Risk. Prog. Struct. Eng. Mater. 2002, 4, 203–212. [Google Scholar] [CrossRef]
- Guo, Y. Power System Reliability Analysis; Tsinghua University Press: Beijing, China, 2003. [Google Scholar]
- Allan, R. Power System Reliability Assessment—A Conceptual and Historical Review. Reliab. Eng. Syst. Saf. 1994, 46, 3–13. [Google Scholar] [CrossRef]
- Chen, L.; Guo, Y. Transient Energy Function Algorithm for Reliability Security Evaluation. J. Tsinghua Univ. (Sci. Technol.) 2001, 41, 5–8. [Google Scholar]
- Panteli, M.; Mancarella, P. The Grid: Stronger, Bigger, Smarter?: Presenting a Conceptual Framework of Power System Resilience. IEEE Power Energy Mag. 2015, 13, 58–66. [Google Scholar] [CrossRef]
- Gu, C.; Tang, Q.; Shen, Y. N-1 Reliability of 220kV Power Grid under Maintenance. East China Electr. Power 2014, 42, 2369–2372. [Google Scholar]
- Bie, Z.; Lin, Y.; Qiu, A. Concept and Research Prospects of Power System Resilience. Autom. Electr. Power Syst. 2015, 39, 1–9. [Google Scholar]
- Chaudry, M.; Ekins, P.; Ramachandran, K.; Shakoor, A.; Skea, J.; Strbac, G.; Wang, X.; Whitaker, J. Building a Resilient UK Energy System; UK Energy Research Center(UKERC): London, UK, 2011. [Google Scholar]
- National Infrastructure Advisory Council. A Framework for Establishing Critical Infrastructure Resilience Goals; National Infrastructure Advisory Council: Washington, DC, USA, 2010.
- Bie, Z.; Lin, Y.; Li, G.; Li, F. Battling the Extreme: A Study on the Power System Resilience. Proc. IEEE 2017, 105, 1253–1266. [Google Scholar] [CrossRef]
- Huang, G.; Wang, J.; Chen, C.; Qi, J.; Chuangxin, G. Integration of Preventive and Emergency Responses for Power Grid Resilience Enhancement. IEEE Trans. Power Syst. 2017, 32, 4451–4463. [Google Scholar] [CrossRef]
- Zhou, X.; Ge, S.; Li, T.; Liu, H. Assessing and Boosting Resilience of Distribution System under Extreme Weather. Proc. CSEE 2018, 38, 505–513+681. [Google Scholar]
- Wang, C.; Hou, Y.; Qiu, F.; Lei, S.; Liu, K. Resilience Enhancement With Sequentially Proactive Operation Strategies. IEEE Trans. Power Syst. 2017, 32, 2847–2857. [Google Scholar] [CrossRef]
- Zio, E. Challenges in the Vulnerability and Risk Analysis of Critical Infrastructures. Reliab. Eng. Syst. Saf. 2016, 152, 137–150. [Google Scholar] [CrossRef]
- Bompard, E.; Wu, D.; Xue, F. Structural Vulnerability of Power Systems: A Topological Approach. Electr. Power Syst. Res. 2011, 81, 1334–1340. [Google Scholar] [CrossRef]
- Wang, A.; Luo, Y.; Tu, G.; Liu, P. Vulnerability Assessment Scheme for Power System Transmission Networks Based on the Fault Chain Theory. IEEE Trans. Power Syst. A Publ. Power Eng. Soc. 2011, 26, 442–450. [Google Scholar] [CrossRef]
- Liu, Y.; Hu, B.; Liu, J.; Ding, L.; Xu, W.; Song, Z.; Li, Y. Power System Cascading Failure Analysis Theories and Application I—Related Theories and Application. Power Syst. Prot. Control 2013, 41, 148–155. [Google Scholar]
- Liu, Y.; Xu, W.; Ding, L.; Liu, J.; Hu, B.; Song, Z.; Xu, L. Power System Cascading Failure Analysis Theories and Application II—Key Features of Real Cascading Failures and Revelation Aspects. Power Syst. Prot. Control 2013, 41, 146–155. [Google Scholar]
- Ding, M.; Han, P. Small-World Topological Model Based Vulnerability Assessment Algorithm for Large-Scale World Power Grid. Autom. Electr. Power Syst. 2006, 8, 7–10+40. [Google Scholar]
- Juan, T.; Diego, C.; Manuel, J. An Electrical Power System Reconfiguration Model Based on Optimal Transmission Switching under Scenarios of Intentional Attacks. Energies 2023, 16, 2879. [Google Scholar]
- Fang, Y.; Sansavini, G. Optimizing Power System Investments and Resilience against Attacks. Reliab. Eng. Syst. Saf. 2017, 159, 161–173. [Google Scholar] [CrossRef]
- Sang, M.; Bao, M.; Ding, Y.; Xue, Y.; Yang, Y. Identification of Vulnerable Lines in Power Grid Considering Impact of Natural Gas Network. Autom. Electr. Power Syst. 2019, 43, 34–43. [Google Scholar]
- Wei, X.; Gao, S.; Huang, T.; Wang, T.; Fan, W. Identification of Two Vulnerability Features: A New Framework for Electrical Networks Based on the Load Redistribution Mechanism of Complex Networks. Complexity 2019, 2019, 3531209. [Google Scholar] [CrossRef]
- Wei, X.; Gao, S.; Huang, T.; Wang, T.; Zang, T. Electrical Network Operational Vulnerability Evaluation Based on Small-World and Scale-Free Properties. IEEE Access 2019, 7, 181072–181082. [Google Scholar] [CrossRef]
- Sergiou, C.; Lestas, M.; Antoniou, P.; Liaskos, C.; Pitsillides, A. Complex Systems: A Communication Networks Perspective Towards 6G. IEEE Access 2020, 8, 89007–89030. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, J.; Li, J.; Han, W.; Pan, R. Vulnerability Analysis of Electric Power Network under a Directed-Weighted Topological Model Based on the P-Q Networks Decomposition. Power Syst. Prot. Control 2010, 38, 19–22. [Google Scholar]
- Song, X. Complexity, Complex System, and the Science of Complexity. Bull. Natl. Nat. Sci. Found. China 2003, 17, 262–268. [Google Scholar]
- Wei, Z.; Gou, J. An Overview on Application of Complex Network Theory in Power System Analysis. Power Syst. Technol. 2015, 39, 279–287. [Google Scholar]
- Li, J.; Wang, H. Analysis on Power Grids and Blackouts with Complex Network Theory. Comput. Technol. Dev. 2008, 18, 247–249+253. [Google Scholar]
- Chen, W.; Jiang, Q.; Cao, Y.; Han, Z. Risk Based Vulnerability Assessment in Complex Power Systems. Power Syst. Technol. 2005, 29, 12–17. [Google Scholar]
- Wang, X.; Zhu, G.; He, R.; Tian, M.; Dong, Z.; Dai, D.; Long, J.; Zhao, L.; Zhang, Q. Survey of Cascading Failures in Cyber Physical Power System Based on Complex Network Theory. Power Syst. Technol. 2017, 41, 2947–2956. [Google Scholar]
- Parisa, R.; Abbas, J. Toward the Evolution of Wireless Powered Communication Networks for the Future Internet of Things. IEEE Netw. 2017, 31, 62–69. [Google Scholar]
- Gupta, A.; Bokde, N.; Kulat, K.D. Hybrid Leakage Management for Water Network Using PSF Algorithm and Soft Computing Techniques. Water Resour. Manag. 2018, 32, 1133–1151. [Google Scholar] [CrossRef]
- Dobson, J.; Carreras, B.A.; Lynch, V.E. Complex Systems Analysis of Series of Blackouts: Cascading Failure, Criticality, and Self-Organization. Chaos Interdiscip. J. Nonlinear Sci. 2007, 17, 026103. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y.; Liu, J.; Yang, J.; Wang, M. Stage Vulnerability of Power Grid and Its Alert Vulnerability Based on Faults Evolution. Power Syst. Technol. 2011, 35, 46–52. [Google Scholar]
- Huang, Z.; Li, H.; Du, T.; Lin, M. Vulnerable branch assessment based on branch energy function. Power Syst. Prot. Control 2012, 40, 7–11+115. [Google Scholar]
- Guo, H.; Yu, S.S.; Iu, H.H.; Fernando, T.; Zheng, C. A Complex Network Theory Analytical Approach to Power System Cascading Failure-From a Cyber-Physical Perspective. Chaos 2019, 29, 053111. [Google Scholar] [CrossRef]
- Bai, W.; Wang, B.; Zhou, T. Brief Review of Blackouts on Electric Power Grids in Viewpoint of Complex Networks. Complex Syst. Complex. Sci. 2005, 2, 29–37. [Google Scholar]
- Hu, D.; Wo, J. Virtual Circuit System of Smart Substations Based on IEC61850. Autom. Electr. Power Syst. 2010, 34, 78–82. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic Cascade of Failures in Interdependent Networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Jiang, J.; Xia, Y.; Xu, S.; Shen, H.-L.; Wu, J. An Asymmetric Interdependent Networks Model for Cyber-Physical Systems. Chaos 2020, 30, 053135. [Google Scholar] [CrossRef]
- Ji, X.; Wang, B.; Liu, D.; Zhao, T. Review on Interdependent Networks Theory and Its Applications in the Structural Vulnerability Analysis of Electrical Cyber-Physical System. Proc. CSEE 2016, 36, 4521–4533. [Google Scholar]
- Wang, Y.; Liu, D.; Lu, Y. Research on Hybrid System Modeling Method of Cyber Physical System for Power Grid. Proc. CSEE 2016, 36, 1464–1470. [Google Scholar]
- Bu, L.; Wang, Q.; Chen, X.; Wang, L.; Zhang, T.; Zhao, J.; Li, X. Toward Online Hybrid Systems Model Checking of Cyber-Physical Systems’ Time-Bounded Short-Run Behavior. ACM SIGBED Rev. 2011, 8, 7–10. [Google Scholar] [CrossRef]
- Amir, B.; Roni, P.; Shlomo, H. Percolation in Networks Composed of Connectivity and Dependency Links. Phys. Rev. E 2011, 83, 051127. [Google Scholar]
- Wang, T.; Sun, C.; Gu, X.; Qin, X. Modeling and Vulnerability Analysis of Electric Power Communication Coupled Network. Proc. CSEE 2018, 38, 3556–3567. [Google Scholar] [CrossRef]
- Zeng, Z.; Liu, D. Study on Cyber-Physical System Modeling on Coordinated Control of Photovoltaic Generation and Battery Energy Storage System. Power Syst. Technol. 2013, 37, 1506–1513. [Google Scholar]
- Cao, Y.; Chen, X.; Sun, K. Identification of Vulnerable Lines in Power Grid Based on Complex Network Theory. Electr. Power Autom. Equip. 2006, 26, 1–5. [Google Scholar]
- Yan, J.; He, H.; Sun, Y. Integrated Security Analysis on Cascading Failure in Complex Networks. IEEE Trans. Inf. Forensics Secur. 2014, 9, 451–463. [Google Scholar] [CrossRef]
- Bai, H.; Miao, S. Hybrid Flow Betweenness Approach for Identification of Vulnerable Line in Power System. IET Gener. Transm. Distrib. 2015, 9, 1324–1331. [Google Scholar] [CrossRef]
- Bompard, E.; Pons, E.; Wu, D. Extended Topological Metrics for the Analysis of Power Grid Vulnerability. IEEE Syst. J. 2012, 6, 481–487. [Google Scholar] [CrossRef]
- Zhou, B.; Cai, Y.; Zang, T.; Wu, J.; Sun, B.; Chen, S. Reliability Assessment of Cyber–Physical Distribution Systems Considering Cyber Disturbances. Appl. Sci. 2023, 13, 3452. [Google Scholar] [CrossRef]
- Wang, K.; Zhang, B.; Zhang, Z.; Yin, X.; Wang, B. An Electrical Betweenness Approach for Vulnerability Assessment of Power Grids Considering the Capacity of Generators and Load. Phys. A Stat. Mech. Its Appl. 2011, 390, 4692–4701. [Google Scholar] [CrossRef]
- Zhu, Y.; Yan, J.; Tang, Y.; Sun, Y.L.; He, H. Resilience Analysis of Power Grids Under the Sequential Attack. IEEE Trans. Inf. Forensics Secur. 2014, 9, 2340–2354. [Google Scholar] [CrossRef]
- Xu, L.; Wang, X.; Wang, X. Electric Betweenness and Its Application in Vulnerable Line Identification in Power System. Proc. CSEE 2010, 30, 33–39. [Google Scholar]
- Wei, X.; Gao, S.; Li, D.; Huang, T.; Pi, R.; Wang, T. Cascading Fault Graph for the Analysis of Transmission Network Vulnerability under Different Attacks. Proc. CSEE 2018, 38, 465–474. [Google Scholar]
- Crucitti, P.; Latora, V.; Marchiori, M. A Topological Analysis of the Italian Electric Power Grid. Phys. A Stat. Mech. Its Appl. 2004, 338, 92–97. [Google Scholar] [CrossRef]
- Albert, R.; Albert, I.; Nakarado, G.L. Structural Vulnerability of the North American Power Grid. Phys. Rev. E Stat. Nonlinear Soft Matter Phys. 2004, 69, 025103. [Google Scholar] [CrossRef]
- Bilis, E.I.; Kröger, W.; Nan, C. Performance of Electric Power Systems Under Physical Malicious Attacks. IEEE Syst. J. 2013, 7, 854–865. [Google Scholar] [CrossRef]
- Sanchez, E.C.; Hines, P.D.H.; Barrows, C.; Blumsack, S. Comparing the Topological and Electrical Structure of the North American Electric Power Infrastructure. IEEE Syst. J. 2012, 6, 616–626. [Google Scholar] [CrossRef]
- Barthélemy, M. Betweenness Centrality in Large Complex Networks. Eur. Phys. J. B 2004, 38, 163–168. [Google Scholar] [CrossRef]
- Meghanathan, N. Spectral Radius as a Measure of Variation in Node Degree for Complex Network Graphs. In Proceedings of the 2015 7th International Conference on u-and e-Service, Science and Technology, Haikou, China, 25–28 November 2015. [Google Scholar]
- Lagonotte, P.; Sabonnadiere, J.C.; Leost, J.Y.; Paul, J.P. Structural Analysis of the Electrical System: Application to Secondary Voltage Control in France. IEEE Trans. Power Syst. A Publ. Power Eng. Soc. 1989, 4, 479–486. [Google Scholar] [CrossRef]
- Zhu, B.; Guo, Y.; Li, C.; Jiang, Z.; Zhang, X.; Yuan, X. A Suvey of the Security Assessment and Securtity Defense of a Cyber Physical Power System Under Cyber Failure Threat. Power Syst. Prot. Control 2021, 49, 178–187. [Google Scholar]
- Shannon, C.E. A Mathematical Theory of Communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Zhang, G.; Zhong, H. Review and Prospect of Information Entropy and Its Applications in Power Systems. Proc. CSEE 2023, 43, 6155–6181. [Google Scholar] [CrossRef]
- Ding, M.; Han, P. Vulnerability Assessment to Small-World Power Grid Based on Weighted Topological Model. Proc. CSEE 2008, 28, 20–25. [Google Scholar]
- Xie, Q.; Deng, C.; Zhao, H.; Weng, Y. Evaluation Method for Node Importance of Power Grid Based on the Weighted Network Model. Autom. Electr. Power Syst. 2009, 33, 21–24. [Google Scholar]
- Cai, Y.; Cao, Y.; Li, Y.; Huang, X.; Tan, Y. Identification of Vulnerable Lines in Urban Power Grid Based on Voltage Grad and Running State. Proc. CSEE 2014, 34, 2124–2131. [Google Scholar]
- Dwivedi, A.; Yu, X. A Maximum-Flow-Based Complex Network Approach for Power System Vulnerability Analysis. IEEE Trans. Ind. Inform. 2013, 9, 81–88. [Google Scholar] [CrossRef]
- Nasiruzzaman, A.B.M.; Pota, H.R.; Akter, M.N. Vulnerability of the Large-Scale Future Smart Electric Power Grid. Phys. A Stat. Mech. Its Appl. 2014, 413, 11–24. [Google Scholar] [CrossRef]
- Han, C.; Lin, Z.; Yang, L.; Lin, J.; Liu, Y.; Zhu, J. Multi-Dimensional Critical Line Identification for Regional Power Systems under Typhoon. Autom. Electr. Power Syst. 2018, 42, 118–125. [Google Scholar]
- He, J.; Pang, S.; Yu, B.; Zhang, W.; Linq, H.; Liu, Y. Vulnerable Line Identification of Power Grid Based on Capacity Betweenness Index. Power Syst. Prot. Control 2013, 41, 30–35. [Google Scholar]
- Fang, J.; Su, C.; Chen, Z.; Sun, H.; Per, L. Power System Structural Vulnerability Assessment Based on an Improved Maximum Flow Approach. IEEE Trans. Smart Grid 2018, 9, 777–785. [Google Scholar] [CrossRef]
- Zhang, G.; Zhang, J.; Yang, J.; Wang, C.; Zhang, Y.; Duan, M. Vulnerability Assessment of Bulk Power Grid Based on Weighted Directional Graph and Complex Network Theory. Electr. Power Autom. Equip. 2009, 29, 21–26. [Google Scholar]
- Ju, W.; Li, Y. Identification of Critical Lines and Nodes in Power Grid Based Maximum Flow Transmission Contribution Degree. Autom. Electr. Power Syst. 2012, 36, 6–12. [Google Scholar]
- Xu, L.; Liu, J.; Liu, Y.; Liu, Y.; Gou, J.; Masoud, B. Node Importance Classified Comprehensive Assessment. Proc. CSEE 2014, 34, 1609–1617. [Google Scholar]
- Liu, L.; Liu, J.; Wei, Z.; Gong, H. Transmission Line Vulnerability Assessment Based on Synergetic Effect Analysis. Electr. Power Autom. Equip. 2016, 36, 30–37. [Google Scholar]
- Bompard, E.; Napoli, R.; Xue, F. Extended Topological Approach for the Assessment of Structural Vulnerability in Transmission Networks. IET Gener. Transm. Distrib. 2010, 4, 716–724. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, J.; Zhu, G.; Zhu, K.; Liu, Y.; Wang, M. Vulnerability Evaluation Model to Power Grid Based on Reliability-Parameter-Weighted Topological Model. Trans. China Electrotech. Soc. 2010, 25, 131–137. [Google Scholar]
- Ma, J.; Wang, X.; Wang, Z. Operation Betweenness Based Assessment on Overload Vulnerability. Power Syst. Technol. 2012, 36, 47–50. [Google Scholar]
- Xu, Q.; Wang, W.; Liu, J.; Liu, Z.; Xin, J.; Xu, Q. Application of Weighted Electric Betweenness Considering Sensitivity Factor in Identification of Vulnerable Grid Lines. Electr. Power Autom. Equip. 2013, 33, 53–58. [Google Scholar]
- Liu, W.; Liang, C.; Xu, P.; Dan, Y.; Wang, J.; Wang, W. Indetification of Critical Line in Power Systems Based on Flow Betweenness. Proc. CSEE 2013, 33, 90–98. [Google Scholar]
- Huang, Y.; Li, H.; Huang, T.; Li, Q.; Zheng, G. Branch Transient Vulnerability Assessment Based on the Complex Network and Transient Energy Function. Power Syst. Prot. Control 2014, 42, 69–74. [Google Scholar]
- Liu, Y.; Liu, J.; Wang, M.; Yang, J. Fast Assessment Method for Transient Vulnerability of Transmission Lines Based on Kinetic Energy Injection Betweenness. Proc. CSEE 2011, 31, 40–47. [Google Scholar]
- Xu, J.; Chen, C.; Luo, C.; Chen, X.; Xiong, W.; Lin, X. Identification of Power Grid Key Parts Based on Improved Complex Network Model. Autom. Electr. Power Syst. 2016, 40, 53–61. [Google Scholar]
- Wei, X.; Zhao, J.; Huang, T.; Ettore, B. A Novel Cascading Faults Graph Based Transmission Network Vulnerability Assessment Method. IEEE Trans. Power Syst. 2018, 33, 2995–3000. [Google Scholar] [CrossRef]
- Wei, X.; Gao, S.; Huang, T.; Bompard, E.; Pi, R.; Wang, T. Complex Network-Based Cascading Faults Graph for the Analysis of Transmission Network Vulnerability. IEEE Trans. Ind. Inform. 2019, 15, 1265–1276. [Google Scholar] [CrossRef]
- Zhu, Y.; Yan, J.; Sun, Y.; He, H. Revealing Cascading Failure Vulnerability in Power Grids Using Risk-Graph. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 3274–3284. [Google Scholar] [CrossRef]
- Hines, P.D.H.; Dobson, L.; Rezaei, P. Cascading Power Outages Propagate Locally in an Influence Graph That Is Not the Actual Grid Topology. IEEE Trans. Power Syst. 2016, 32, 958–967. [Google Scholar] [CrossRef]
- Qi, J.; Sun, K.; Mei, S. An Interaction Model for Simulation and Mitigation of Cascading Failures. IEEE Trans. Power Syst. 2015, 30, 804–819. [Google Scholar] [CrossRef]
- Ju, W.; Sun, K.; Qi, J. Multi-Layer Interaction Graph for Analysis and Mitigation of Cascading Outages. IEEE J. Emerg. Sel. Top. Circuits Syst. 2017, 7, 239–249. [Google Scholar] [CrossRef]
- Wang, T.; Wei, X.; Huang, T.; Wang, J.; Peng, H.; Pérez-Jiménez, M.J.; Valencia-Cabrera, L. Modeling Fault Propagation Paths in Power Systems: A New Framework Based on Event SNP Systems With Neurotransmitter Concentration. IEEE Access 2019, 7, 12798–12808. [Google Scholar] [CrossRef]
- Zhao, L.; Kwangho, P.; Lai, Y. Attack Vulnerability of Scale-Free Networks Due to Cascading Breakdown. Phys. Rev. E Stat. Nonlinear Soft Matter Phys. 2004, 70, 035101. [Google Scholar] [CrossRef]
- Dong-Hee, K.; Jun, K.B.; Hawoong, J. Universality Class of the Fiber Bundle Model on Complex Networks. Phys. Rev. Lett. 2005, 94, 025501. [Google Scholar]
- Watts, D.J.; Strogatz, S.H. Collective Dynamics of “small-World” Networks. Nature 1998, 393, 440–442. [Google Scholar] [CrossRef]
- Surdutovich, G.; Cortez, C.; Vitilina, R. Dynamics of ‘Small-World’ Networks and Vulnerability of the Electric Power Gird. In Proceedings of the VIII Symposium of Specialists in Electric Operational and Expansion Planning, Brsilia, Brazil, 17 May 2002. [Google Scholar]
- Monfared, M.A.S.; Jalili, M.; Alipour, Z. Topology and Vulnerability of the Iranian Power Grid. Phys. A Stat. Mech. Its Appl. 2014, 406, 24–33. [Google Scholar] [CrossRef]
- Meng, Z.; Lu, Z.; Song, J. Comparison Analysis of the Small-Word Topological Model of Chinese and American Power Grids. Autom. Electr. Power Syst. 2004, 28, 21–24. [Google Scholar]
- Zhou, B.; Sun, B.; Zang, T.; Cai, Y.; Wu, J.; Luo, H. Security Risk Assessment Approach for Distribution Network Cyber Physical Systems Considering Cyber Attack Vulnerabilities. Entropy 2022, 25, 47. [Google Scholar] [CrossRef]
- Wang, Q.; Li, M.; Tang, Y.; Ni, M. A Review on Research of Cyber-Attack and Defense in Cyber Physical Power System Part One Modelling and Evaluation. Autom. Electr. Power Syst. 2019, 43, 9–21. [Google Scholar]
- Hosseinzadeh, M.; Sinopoli, B.; Garone, E. Feasibility and Detection of Replay Attack in Networked Constrained Cyber-Physical Systems. In Proceedings of the 2019 57th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, VA, USA, 24–27 September 2019; pp. 712–717. [Google Scholar]
- Tran, T.-T.; Shin, O.-S.; Lee, J.-H. Detection of Replay Attacks in Smart Grid Systems. In Proceedings of the 2013 International Conference on Computing, Management and Telecommunications (ComManTel), Ho Chi Minh, Vietnam, 21–24 January 2013; pp. 298–302. [Google Scholar]
- Zhou, B.; Min, X.; Zang, T.; Zhang, Y.; Chen, Y.; Zhao, W. Loss Assessment and Vulnerability Analysis of an Intergrated Electricity Natural Gas System Under Load Redistribution Attack. Adv. Eng. Sci. 2023, 55, 3–13. [Google Scholar]
- He, Z.; Gao, S.; Wei, X.; Zang, T.; Lei, J. Research on Offensive and Defensive Game Model of False Topology Attack Based on Collaborative Tampering With Branch and Protection. Power Syst. Technol. 2022, 46, 4346–4355. [Google Scholar]
- Ruan, Z.; Lü, L.; Liu, Y.; Liu, J.; Wang, D.; Huang, L. Coordinated Attack Model of Cyber-Physical Power System Considering False Load Data Injection. Electr. Power Autom. Equip. 2019, 39, 181–187. [Google Scholar]
- Cao, M.; Wang, L.; Hu, B.; Xie, K.; Fu, J.; Wen, L.; Zhou, P.; Fan, X.; Li, B.; Zeng, Y. Coordinated Cyber-Physical Multi-Stage Attack Strategy Considering Cascading Failure of Intergrated Electricity-Natural Gas System. Electr. Power Autom. Equip. 2019, 39, 128–136. [Google Scholar]
- Ge, L.; Li, Y.; Li, Y.; Yan, J.; Sun, Y. Smart Distribution Network Situation Awareness for High-Quality Operation and Maintenance: A Brief Review. Energies 2022, 15, 828. [Google Scholar] [CrossRef]
- Hu, F.; Chen, L.; Chen, J. Cascading Failure Modeling and Robustness Evaluation Evaluation Based on Power Flow. Power Syst. Prot. Control 2021, 49, 35–43. [Google Scholar]
- Zou, Y.; Li, H. Study on Power Grid Partition and Attack Strategies Based on Complex Networks. Front. Phys. 2022, 9, 790218. [Google Scholar] [CrossRef]
- Pan, H.; Lian, H.; Na, C.; Li, X. Modeling and Vulnerability Analysis of Cyber-Physical Power Systems Based on Community Theory. IEEE Syst. J. 2020, 14, 3938–3948. [Google Scholar] [CrossRef]
- Jia, C.; Li, M.; Liu, R. Percolation and Cascading Dynamics on Multilayer Complex Networks. J. Univ. Electron. Sci. Technol. China 2022, 51, 148–160. [Google Scholar]
- Sun, K.; Wang, D.; Ge, X.; Wang, W.; Sun, W. Topological Evolution Model of Power System Based on Positioning Probability and Attenuation Mechanism. Proc. CSU-EPSA 2021, 33, 22–28. [Google Scholar]
- Beng, L.Y.; Abdulrazzaq, K.A.; Selvakumar, M.; Samer, A.S. An Adaptive Assessment and Prediction Mechanism in Network Security Situation Awareness. J. Comput. Sci. 2017, 13, 114–129. [Google Scholar]
- Chen, H.; Hu, Z.; Chen, S.; Yang, Y.; Fan, S. Research on Security Situation Awareness Method of Power Network Monitoring System Based on Data Mining. J. Phys. Conf. Ser. 2022, 2351, 012043. [Google Scholar] [CrossRef]
- Tian, S.; Li, K.; Wei, S.; Fu, Y.; Li, Z.; Liu, S. Security Situation Awareness Approach for Distribution Network Based on Synchronous Phasor Measurement Unit. Proc. CSEE 2021, 41, 617–632. [Google Scholar]
- Xiao, B.; Xiao, Z.; Jiang, Z.; Zhao, X.; Kan, Z.; Qi, X.; Bai, Y. Spatial Load Situation Awareness Based on Denoising Autoencoder, Singular Spectrum Analysis and Long Short-Term Memory Neural Networks. Proc. CSEE 2021, 41, 4858–4867. [Google Scholar]
- Shi, Z.; Wang, Z.; Wu, W.; Wang, X.; Hu, Z. Evaluation Renewable Energy Intergration Capability and Network Expansion Planning Based on Situation Awareness Theory. Power Syst. Technol. 2017, 41, 2180–2186. [Google Scholar]
- Yang, J.; Guo, Y.; Guo, C.; Chen, Z.; Wang, S.; Jiang, B. A Robust Active Distribution Network Defensive Strategy against Cyber-attack Considering Multi-uncertainties. IET Gener. Transm. Distrib. 2022, 16, 1476–1488. [Google Scholar] [CrossRef]
- Zhou, B.; Wu, J.; Zang, T.; Cai, Y.; Sun, B.; Qiu, Y. Emergency Dispatch Approach for Power Systems with Hybrid Energy Considering Thermal Power Unit Ramping. Energies 2023, 16, 4213. [Google Scholar] [CrossRef]
- Song, J.; Wang, Y.; Hu, R.; Xu, G.; Ma, S. Identification of Critical Nodes for the Integrated Energy Systems Based on Complex Networks and Unified Energy Flows. J. Phys. Conf. Ser. 2022, 2301, 012013. [Google Scholar] [CrossRef]
- Dong, S.; Zhou, B.; Zang, T.; Xiao, X. Vulnerability Assessment of Electrical and Thermal Cyber Physical System Considering Dual Coupling Characteristics. IET Gener. Transm. Distrib. 2022, 16, 4215–4229. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zang, T.; Wang, Z.; Wei, X.; Zhou, Y.; Wu, J.; Zhou, B. Current Status and Perspective of Vulnerability Assessment of Cyber-Physical Power Systems Based on Complex Network Theory. Energies 2023, 16, 6509. https://doi.org/10.3390/en16186509
Zang T, Wang Z, Wei X, Zhou Y, Wu J, Zhou B. Current Status and Perspective of Vulnerability Assessment of Cyber-Physical Power Systems Based on Complex Network Theory. Energies. 2023; 16(18):6509. https://doi.org/10.3390/en16186509
Chicago/Turabian StyleZang, Tianlei, Zian Wang, Xiaoguang Wei, Yi Zhou, Jiale Wu, and Buxiang Zhou. 2023. "Current Status and Perspective of Vulnerability Assessment of Cyber-Physical Power Systems Based on Complex Network Theory" Energies 16, no. 18: 6509. https://doi.org/10.3390/en16186509
APA StyleZang, T., Wang, Z., Wei, X., Zhou, Y., Wu, J., & Zhou, B. (2023). Current Status and Perspective of Vulnerability Assessment of Cyber-Physical Power Systems Based on Complex Network Theory. Energies, 16(18), 6509. https://doi.org/10.3390/en16186509








