MHSEER: A Meta-Heuristic Secure and Energy-Efficient Routing Protocol for Wireless Sensor Network-Based Industrial IoT
Abstract
:1. Introduction
1.1. Objective
1.2. Contributions
- An architecture of WSN-IIoT has been developed for the MHSEER protocol that helps minimize the delay and energy consumption of the network with maximum stability [14].
- To solve the above-mentioned issues, an MHSEER approach has been proposed, which enhances the choice for reliable data routing using a heuristic function and uses the encoding and decoding of data package based on counter encryption mode (CEM) [9].
- The proposed protocol compares the different parameters of a routing protocol such as throughput, network delay, packet drop rate, faulty pathways, and energy usage with the above-mentioned existing approaches. MHSEER increases the throughput and decreases metrics such as the packet drop rate and energy usage.
1.3. Structure
2. Related Work
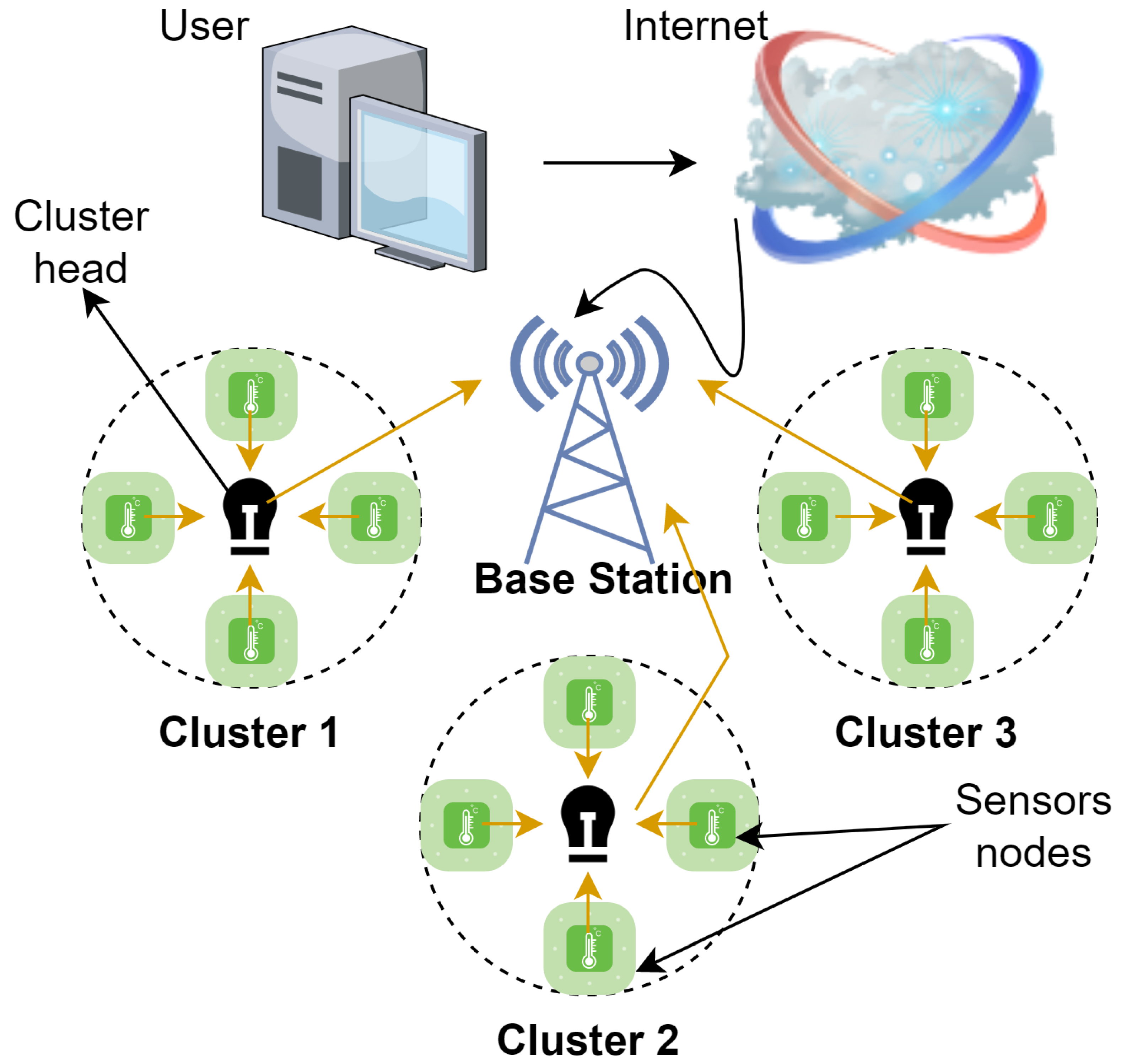
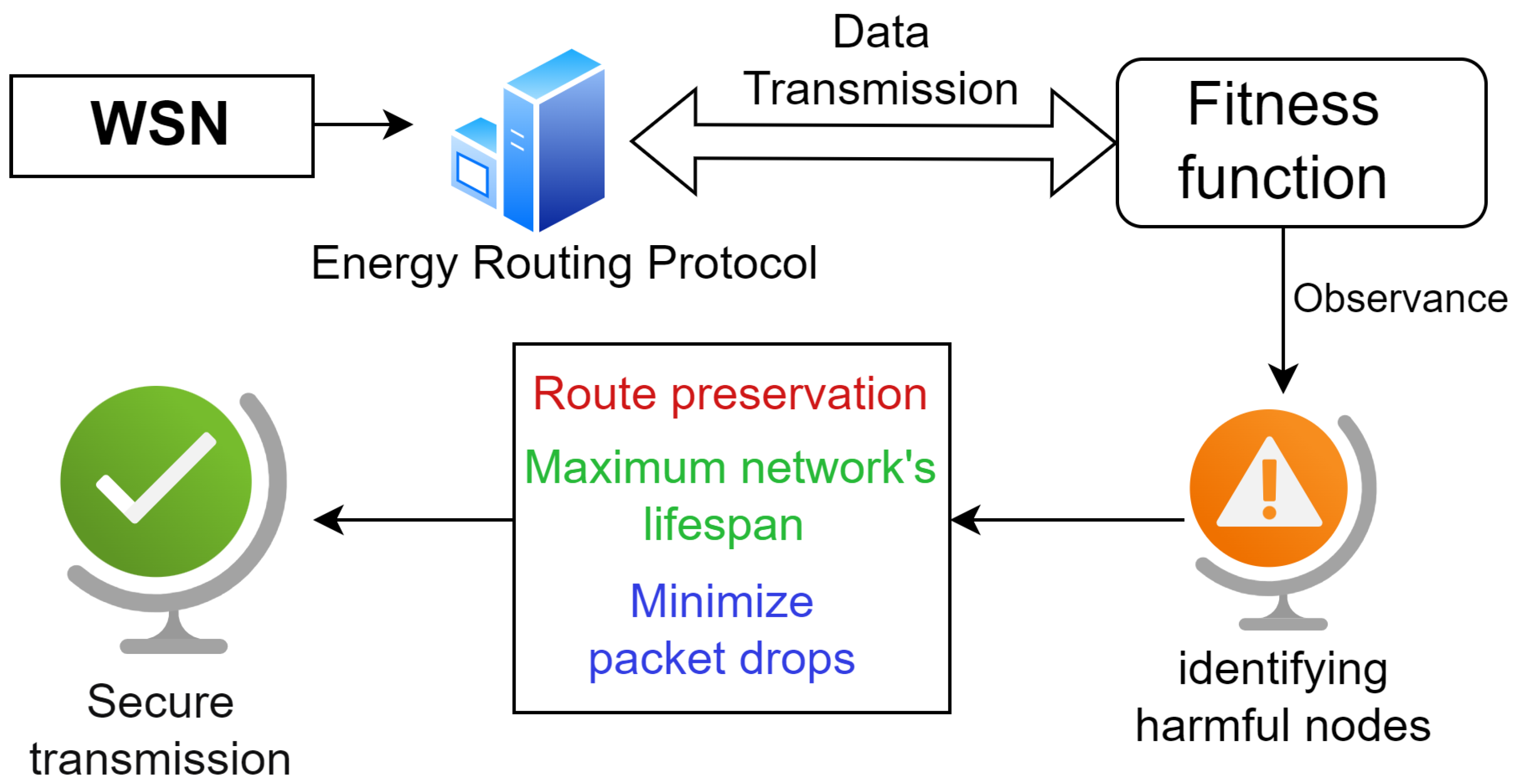
3. Proposed Architecture of WSN-IIoT for Energy Routing Protocol
4. Methodology
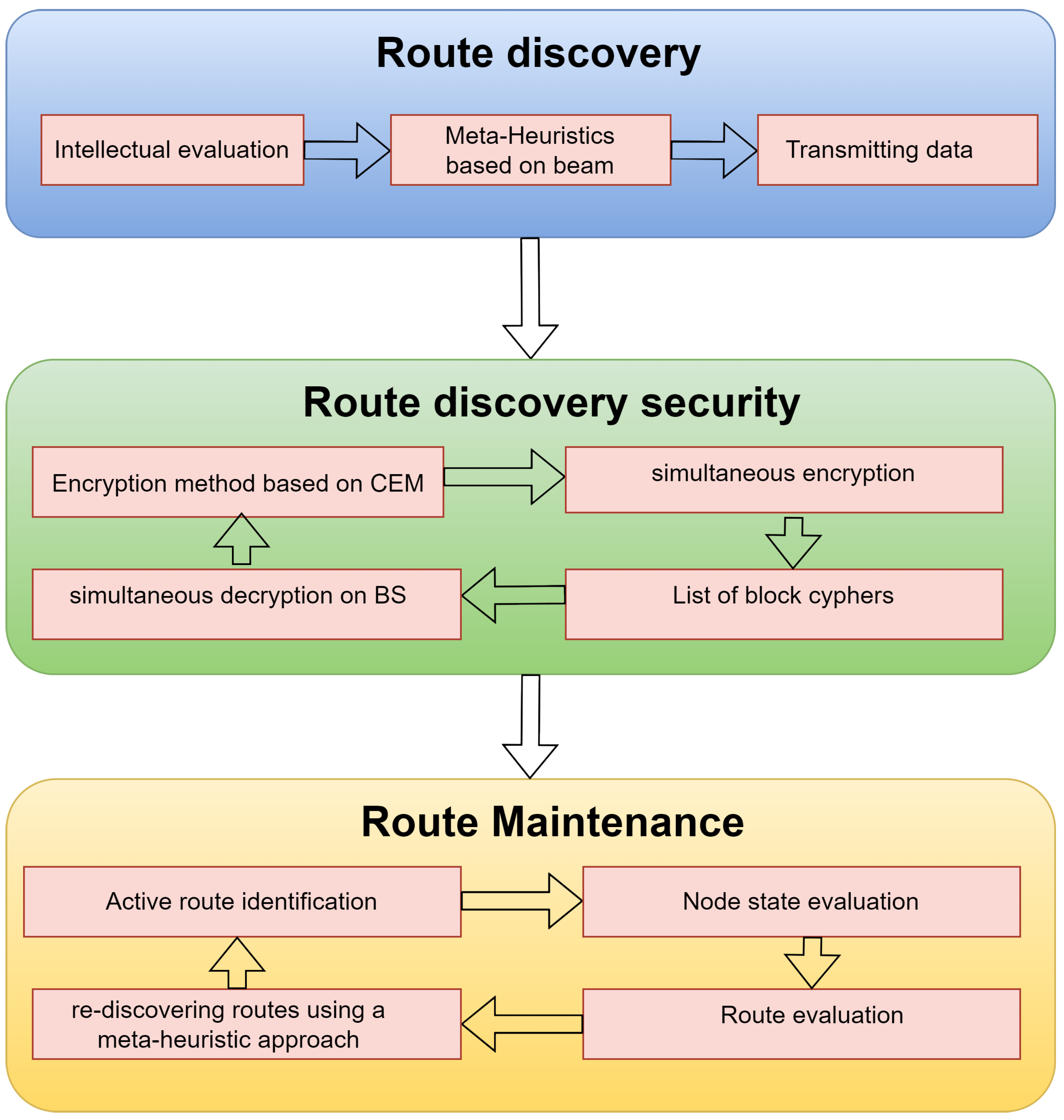
4.1. Route Discovery
4.2. Route Discovery Security
4.3. Route Maintenance
5. Results and Discussion
5.1. Throughput Analysis
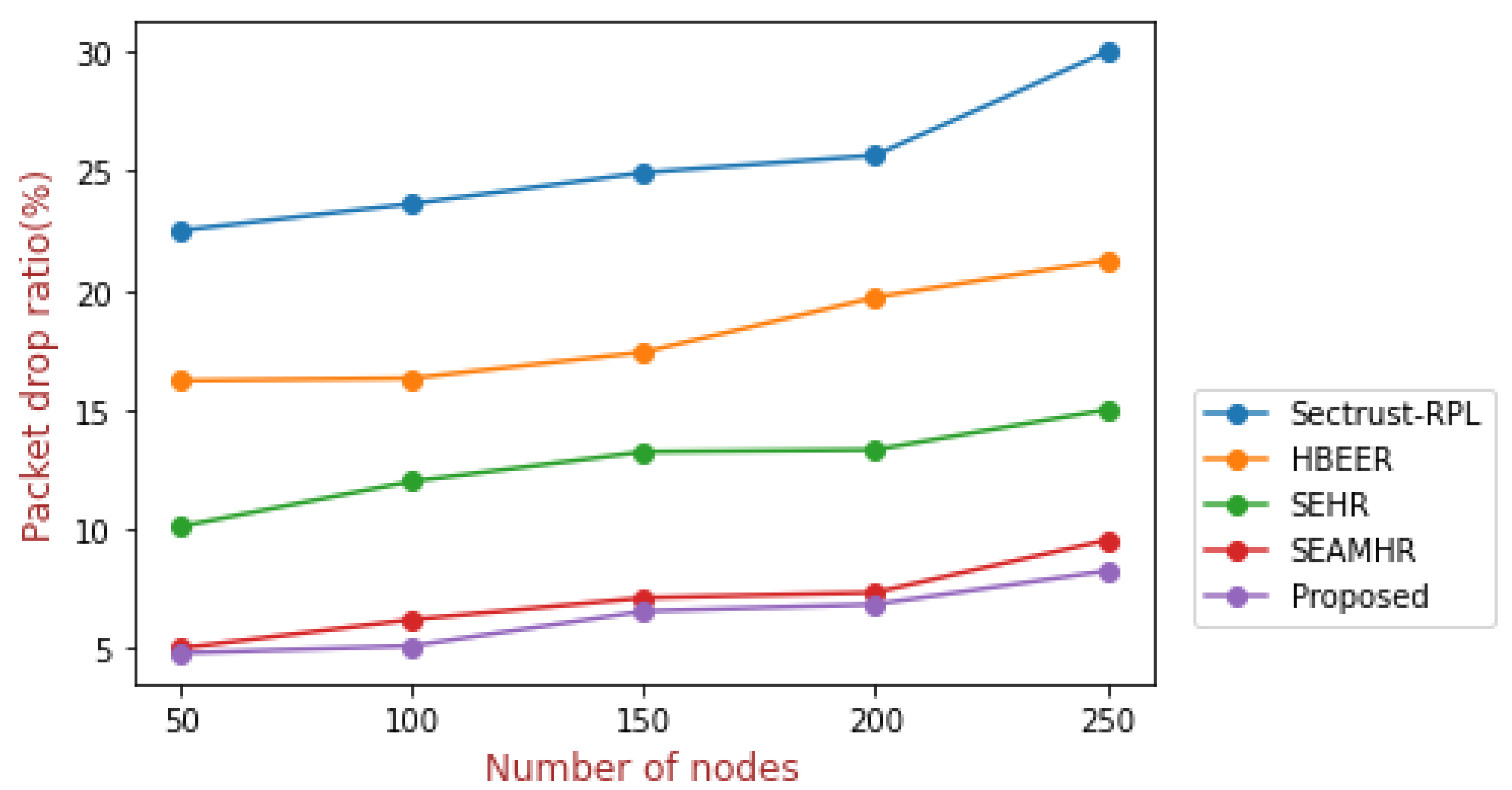
5.2. Packet Drop Ratio Analysis
5.3. End-to-End Delay Analysis
5.4. Energy Consumption Analysis
5.5. Faulty Routes Analysis
5.6. Findings and Implications for the Research
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Airehrour, D.; Gutierrez, J.A.; Ray, S.K. SecTrust-RPL: A secure trust-aware RPL routing protocol for Internet of Things. Future Gener. Comput. Syst. 2019, 93, 860–876. [Google Scholar] [CrossRef]
- Hamzah, A.; Shurman, M.; Al-Jarrah, O.; Taqieddin, E. Energy-efficient fuzzy-logic-based clustering technique for hierarchical routing protocols in wireless sensor networks. Sensors 2019, 19, 561. [Google Scholar] [CrossRef]
- Sharma, S.; Kaur, A. Survey on wireless sensor network, Its Applications and Issues. In Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2021; Volume 1969, p. 012042. [Google Scholar]
- Behera, T.M.; Samal, U.C.; Mohapatra, S.K.; Khan, M.S.; Appasani, B.; Bizon, N.; Thounthong, P. Energy-Efficient Routing Protocols for Wireless Sensor Networks: Architectures, Strategies, and Performance. Electronics 2022, 11, 2282. [Google Scholar] [CrossRef]
- Hayajneh, A.A.; Bhuiyan, M.Z.A.; McAndrew, I. A novel security protocol for wireless sensor networks with cooperative communication. Computers 2020, 9, 4. [Google Scholar] [CrossRef]
- Haseeb, K.; Almustafa, K.M.; Jan, Z.; Saba, T.; Tariq, U. Secure and energy-aware heuristic routing protocol for wireless sensor network. IEEE Access 2020, 8, 163962–163974. [Google Scholar] [CrossRef]
- Kumar, A.; Sharma, I. Enhancing Cybersecurity Policies with Blockchain Technology: A Survey. In Proceedings of the 2022 5th International Conference on Contemporary Computing and Informatics (IC3I), Greater Noida, India, 14–16 December 2022; pp. 1050–1054. [Google Scholar] [CrossRef]
- Kuhlani, H.; Wang, X.; Hawbani, A.; Busaileh, O. Heuristic data dissemination for mobile sink networks. Wirel. Netw. 2020, 26, 479–493. [Google Scholar] [CrossRef]
- Gurram, G.V.; Shariff, N.C.; Biradar, R.L. A Secure Energy Aware Meta-Heuristic Routing Protocol (SEAMHR) for sustainable IoT-Wireless Sensor Network (WSN). Theor. Comput. Sci. 2022, 930, 63–76. [Google Scholar] [CrossRef]
- Liu, Y.; Wu, Q.; Zhao, T.; Tie, Y.; Bai, F.; Jin, M. An improved energy-efficient routing protocol for wireless sensor networks. Sensors 2019, 19, 4579. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Bashir, M.U.; Lloret, J.; Leon, A. Optimized cluster-based dynamic energy-aware routing protocol for wireless sensor networks in agriculture precision. J. Sens. 2020, 2020, 9040395. [Google Scholar] [CrossRef]
- Sharma, S.; Guleria, K. Pneumonia Detection from Chest X-ray Images using Transfer Learning. In Proceedings of the 2022 10th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 13–14 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Akin, E.; Korkmaz, T. Comparison of routing algorithms with static and dynamic link cost in software defined networking (SDN). IEEE Access 2019, 7, 148629–148644. [Google Scholar] [CrossRef]
- Binu, G.; Shajimohan, B. A novel heuristic based energy efficient routing strategy in wireless sensor network. Peer- Netw. Appl. 2020, 13, 1853–1871. [Google Scholar] [CrossRef]
- Gowri, S.; Pappa, C.K.; Tamilvizhi, T.; Nelson, L.; Surendran, R. Intelligent Analysis on Frameworks for Mobile App Development. In Proceedings of the 2023 5th International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 23–25 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1506–1512. [Google Scholar]
- Seyfollahi, A.; Taami, T.; Ghaffari, A. Towards developing a machine learning-metaheuristic-enhanced energy-sensitive routing framework for the internet of things. Microprocess. Microsyst. 2023, 96, 104747. [Google Scholar] [CrossRef]
- Yun, W.K.; Yoo, S.J. Q-learning-based data-aggregation-aware energy-efficient routing protocol for wireless sensor networks. IEEE Access 2021, 9, 10737–10750. [Google Scholar] [CrossRef]
- Daanoune, I.; Baghdad, A.; Ballouk, A. An enhanced energy-efficient routing protocol for wireless sensor network. Int. J. Electr. Comput. Eng. (2088–8708) 2020, 10, 5462–5469. [Google Scholar] [CrossRef]
- Liao, R.F.; Wen, H.; Wu, J.; Pan, F.; Xu, A.; Jiang, Y.; Xie, F.; Cao, M. Deep-learning-based physical layer authentication for industrial wireless sensor networks. Sensors 2019, 19, 2440. [Google Scholar] [CrossRef]
- Narayan, V.; Daniel, A.; Chaturvedi, P. E-FEERP: Enhanced Fuzzy-based Energy Efficient Routing Protocol for Wireless Sensor Network. Wirel. Pers. Commun. 2023, 1–28. [Google Scholar] [CrossRef]
- Gemeda, K.A.; Gianini, G.; Libsie, M. The effect of node selfishness on the performance of WSN cluster-based routing algorithms. In Proceedings of the AFRICON 2015, Addis Ababa, Ethiopia, 14–17 September 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–5. [Google Scholar]
- Gemeda, K.A.; Gianini, G.; Libsie, M. Collaborative packets forwarding to extend lifetime of multi-authority wireless sensor networks. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC), Palladam, India, 10–11 February 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 513–519. [Google Scholar]
- Manshaei, M.H.; Zhu, Q.; Alpcan, T.; Bacşar, T.; Hubaux, J.P. Game theory meets network security and privacy. ACM Comput. Surv. (CSUR) 2013, 45, 25. [Google Scholar] [CrossRef]
- Gianini, G.; Damiani, E.; Mayer, T.R.; Coquil, D.; Kosch, H.; Brunie, L. Many-player inspection games in networked environments. In Proceedings of the 2013 7th IEEE International Conference on Digital Ecosystems and Technologies (DEST), Menlo Park, CA, USA, 24–26 July 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–6. [Google Scholar]
- Lena Cota, G.; Mokhtar, S.B.; Lawall, J.; Muller, G.; Gianini, G.; Damiani, E.; Brunie, L. A framework for the design configuration of accountable selfish-resilient Peer-to-Peer systems. In Proceedings of the 2015 IEEE 34th Symposium on Reliable Distributed Systems (SRDS), Montreal, QC, Canada, 28 September–1 October 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 276–285. [Google Scholar]
- Lena Cota, G.; Mokhtar, S.B.; Gianini, G.; Damiani, E.; Lawall, J.; Muller, G.; Brunie, L. Analysing Selfishness Flooding with SEINE. In Proceedings of the 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Denver, CO, USA, 26–29 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 603–614. [Google Scholar]
- Lena Cota, G.; Mokhtar, S.B.; Gianini, G.; Damiani, E.; Lawall, J.; Muller, G.; Brunie, L. RACOON++: A semi-automatic framework for the selfishness-aware design of cooperative systems. IEEE Trans. Dependable Secur. Comput. 2017, 16, 635–650. [Google Scholar] [CrossRef]
- Gianini, G.; Mio, C.; Fossi, L.G.; Egyed-Zsigmon, E. A Watermark Inspection Game for IoT Settings. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 2642, pp. 29–34. [Google Scholar]
- Gianini, G.; Viola, F.; Lena-Cota, G.; Lin, J. Hybrid Inspector-Inspectee-Agent Games in Mobile Cloud Computing. In Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks, Alicante, Spain, 16–20 November 2020; pp. 95–100. [Google Scholar]
- Gemeda, K.A.; Gianini, G.; Libsie, M. An evolutionary cluster-game approach for Wireless Sensor Networks in non-collaborative settings. Pervasive Mob. Comput. 2017, 42, 209–225. [Google Scholar] [CrossRef]
- El Alami, H.; Najid, A. ECH: An enhanced clustering hierarchy approach to maximize lifetime of wireless sensor networks. IEEE Access 2019, 7, 107142–107153. [Google Scholar] [CrossRef]
- Yin, Y.; Li, Y.; Gao, H.; Liang, T.; Pan, Q. FGC: GCN based federated learning approach for trust industrial service recommendation. IEEE Trans. Ind. Inform. 2022, 19, 3240–3250. [Google Scholar] [CrossRef]
- Gao, H.; Huang, W.; Liu, T.; Yin, Y.; Li, Y. Ppo2: Location privacy-oriented task offloading to edge computing using reinforcement learning for intelligent autonomous transport systems. IEEE Trans. Intell. Transp. Syst. 2022. [Google Scholar] [CrossRef]
- Babbar, H.; Rani, S. Software-defined networking framework securing internet of things. In Integration of WSN and IoT for Smart Cities; Springer: Cham, Switzerland, 2020; pp. 1–14. [Google Scholar]
- Babbar, H.; Rani, S.; Islam, S.M.; Iyer, S. QoS based Security Architecture for Software-Defined Wireless Sensor Networking. In Proceedings of the 2021 6th International Conference on Innovative Technology in Intelligent System and Industrial Applications (CITISIA), Sydney, Australia, 24–26 November 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–5. [Google Scholar]
- Khalaf, O.I.; Abdulsahib, G.M. Energy efficient routing and reliable data transmission protocol in WSN. Int. J. Adv. Soft Comput. Appl. 2020, 12, 45–53. [Google Scholar]
- Lilhore, U.K.; Khalaf, O.I.; Simaiya, S.; Tavera Romero, C.A.; Abdulsahib, G.M.; Kumar, D. A depth-controlled and energy-efficient routing protocol for underwater wireless sensor networks. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221117118. [Google Scholar] [CrossRef]
- Elsmany, E.F.A.; Omar, M.A.; Wan, T.C.; Altahir, A.A. EESRA: Energy efficient scalable routing algorithm for wireless sensor networks. IEEE Access 2019, 7, 96974–96983. [Google Scholar] [CrossRef]
- Maheshwari, P.; Sharma, A.K.; Verma, K. Energy efficient cluster based routing protocol for WSN using butterfly optimization algorithm and ant colony optimization. Ad. Hoc. Netw. 2021, 110, 102317. [Google Scholar] [CrossRef]
- Xu, C.; Xiong, Z.; Zhao, G.; Yu, S. An energy-efficient region source routing protocol for lifetime maximization in WSN. IEEE Access 2019, 7, 135277–135289. [Google Scholar] [CrossRef]




| Ref. No. | Year/ Author Name | Objective | Software Used | Parameter | Future Scope |
|---|---|---|---|---|---|
| [1] | 2019/ Airehrour et al. | By integrating the SecTrust system into the RPL protocol, a simulated exercise was conducted to demonstrate the SecTrust system’s effectiveness at fending off Rank and Sybil assaults. | PhD Research Lab of Auckland University of Technology. | Throughput, packet drop rate. | To increase the network’s integration of trustworthy nodes that have repaid their battery life by extending the SecTrust-RPL. |
| [2] | 2019/ Hamzah et al. | Utilize the gain ratio to assess how effectively the clustering methods can balance the energy distribution among WSN sensor nodes. A fuzzy logic-based CH election method, a k-means-based clustering method, and LEACH are contrasted with the suggested technique FL-EEC/D. | .NET | SN’s residual power, the distance to the BS, the density of the SN, the compacting of the SN, and location appropriateness. | The Gini index is a reasonable assessment tool for assessing the routing protocols’ energy effectiveness in WSNs for the metric of energy distribution balance. |
| [6] | 2020/ Haseeb et al. | The method provided reliable and insightful learning through the use of heuristic evaluation, which was taken from AI. This technique uses a heuristic approach to spot and guard against data breaches | MATLAB | Throughput, the ratio of packet drops, significant delay, consumed energy, erroneous routes, overhead on networks, and computational cost. | To make the system smarter and fault-tolerant by employing certain lightweight machine learning-based approaches to enhance the SEHR technique. |
| [8] | 2019/ Kuhlani et al. | Developed an accessible virtual structure that serves as an intermediary architecture between the sink and the nodes while sharing metadata and query messages in order to lessen the mobile sink’s frequently current location to all nodes. | MATLAB | Average rate of delivery, average energy utilization, the lifespan of a network, and absolute delay. | The suggested approach can be further explained to understand the flow better. |
| [31] | 2019/ Alami et al. | To reduce the energy consumption of WSNs, hierarchical techniques that utilize clustering hierarchy are proposed. Data collection and transmission to a base station could be carried out using the nodes with the highest residual energy. | MATLAB | Stable timeframe, HNA, the lifespan of a network, network traffic, and throughput. | The suggested technique can be expanded to manage a system of mobile sinks and will analyze the network lifespan optimization. |
| Parameter | Value |
|---|---|
| Area of simulation | 300 ∗ 300 m |
| SNs | 250 |
| Infected nodes | 50 |
| Size of packets | 64 bits |
| Level of energy | 4 Joules |
| Position of BS | 200, 600 |
| Beamwidth | 4 |
| Control messages | 40 bits |
| Range of transmission | 40 m |
| Type of traffic | CBR |
| Parameters | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| Throughput (%) | 74.94 | 79.75 | 86.16 | 94.64 | 95.81 |
| Packet drop ratio (%) | 25.66 | 19.71 | 13.32 | 7.34 | 5.12 |
| End-to-end delay (ms) | 0.178 | 0.162 | 0.136 | 0.114 | 0.10 |
| Energy consumption (mJ) | 0.0326 | 0.0252 | 0.0190 | 0.0154 | 0.0102 |
| Faulty routes (%) | 17.07 | 13.31 | 10.46 | 7.83 | 6.51 |
| No. of Nodes | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| 50 | 78.8 | 85 | 89.8 | 95.2 | 95.8 |
| 100 | 77.4 | 84.4 | 89.2 | 94.9 | 96.2 |
| 150 | 76.2 | 82.3 | 86.3 | 94.76 | 95.9 |
| 200 | 74.94 | 79.75 | 86.16 | 94.64 | 95.12 |
| 250 | 70 | 76.2 | 85 | 92.8 | 93.25 |
| No. of Nodes | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| 50 | 22.51 | 16.22 | 10.11 | 5 | 4.8 |
| 100 | 23.63 | 16.32 | 12 | 6.21 | 5.10 |
| 150 | 24.94 | 17.41 | 13.24 | 7.12 | 6.56 |
| 200 | 25.66 | 19.71 | 13.32 | 7.34 | 6.85 |
| 250 | 30 | 21.27 | 15 | 9.54 | 8.24 |
| No. of Nodes | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| 50 | 0.152 | 0.141 | 0.120 | 0.0912 | 0.015 |
| 100 | 0.163 | 0.149 | 0.122 | 0.101 | 0.018 |
| 150 | 0.171 | 0.154 | 0.132 | 0.110 | 0.100 |
| 200 | 0.178 | 0.162 | 0.136 | 0.114 | 0.100 |
| 250 | 0.192 | 0.173 | 0.141 | 0.121 | 0.104 |
| No. of Nodes | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| 50 | 0.0276 | 0.0211 | 0.013 | 0.0131 | 0.0122 |
| 100 | 0.0301 | 0.0212 | 0.0156 | 0.0143 | 0.0130 |
| 150 | 0.0313 | 0.0223 | 0.0179 | 0.0150 | 0.0141 |
| 200 | 0.0326 | 0.0252 | 0.0190 | 0.0154 | 0.0142 |
| 250 | 0.0355 | 0.0271 | 0.0223 | 0.0162 | 0.0155 |
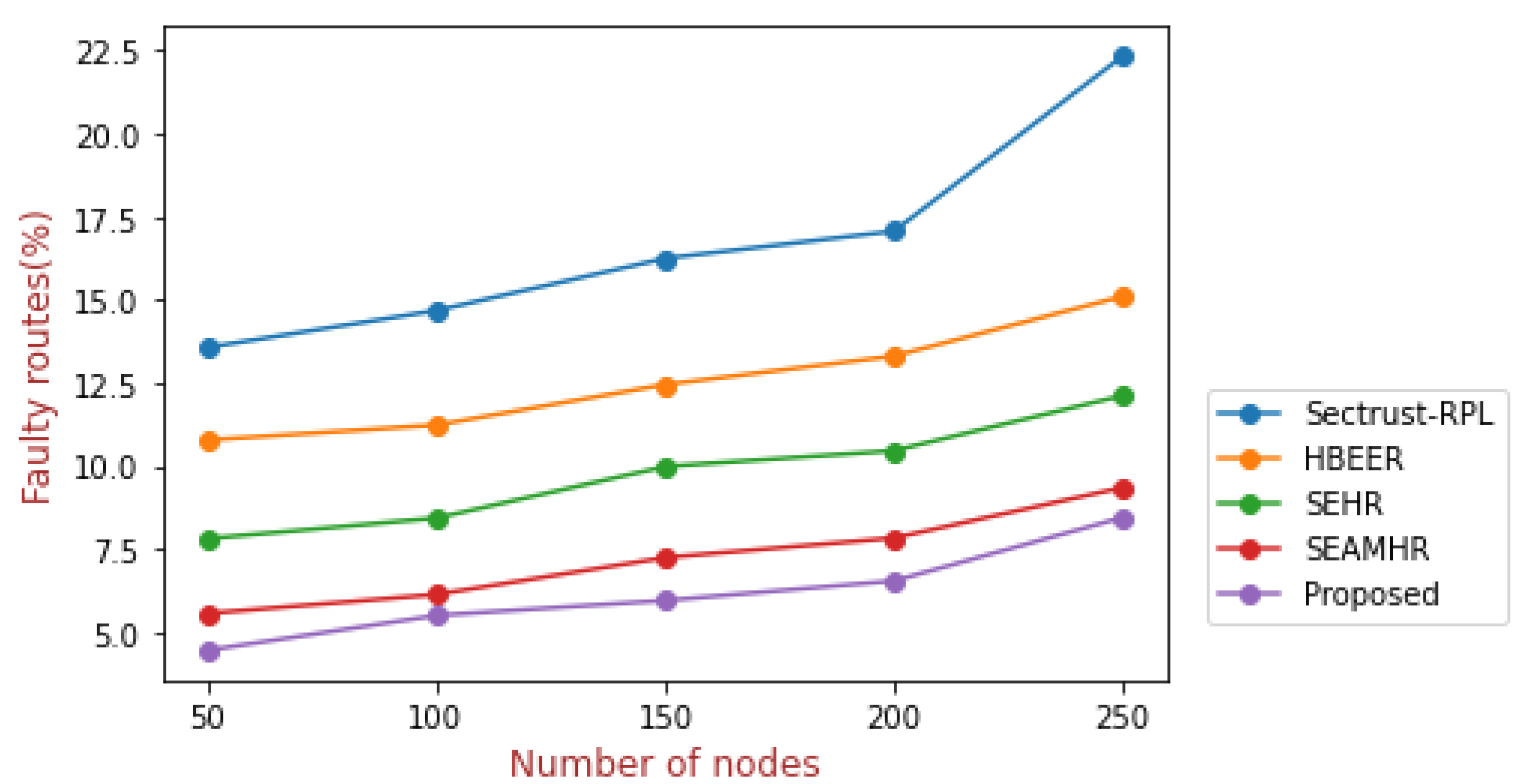
| No. of Nodes | Sectrust-RPL | HBEER | SEHR | SEAMHR | Proposed |
|---|---|---|---|---|---|
| 50 | 13.57 | 10.78 | 7.81 | 5.56 | 4.45 |
| 100 | 14.68 | 11.23 | 8.43 | 6.13 | 5.50 |
| 150 | 16.25 | 12.45 | 9.98 | 7.24 | 5.95 |
| 200 | 17.07 | 13.31 | 10.46 | 7.83 | 6.54 |
| 250 | 22.34 | 15.11 | 12.12 | 9.35 | 8.45 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sharma, A.; Babbar, H.; Rani, S.; Sah, D.K.; Sehar, S.; Gianini, G. MHSEER: A Meta-Heuristic Secure and Energy-Efficient Routing Protocol for Wireless Sensor Network-Based Industrial IoT. Energies 2023, 16, 4198. https://doi.org/10.3390/en16104198
Sharma A, Babbar H, Rani S, Sah DK, Sehar S, Gianini G. MHSEER: A Meta-Heuristic Secure and Energy-Efficient Routing Protocol for Wireless Sensor Network-Based Industrial IoT. Energies. 2023; 16(10):4198. https://doi.org/10.3390/en16104198
Chicago/Turabian StyleSharma, Anshika, Himanshi Babbar, Shalli Rani, Dipak Kumar Sah, Sountharrajan Sehar, and Gabriele Gianini. 2023. "MHSEER: A Meta-Heuristic Secure and Energy-Efficient Routing Protocol for Wireless Sensor Network-Based Industrial IoT" Energies 16, no. 10: 4198. https://doi.org/10.3390/en16104198
APA StyleSharma, A., Babbar, H., Rani, S., Sah, D. K., Sehar, S., & Gianini, G. (2023). MHSEER: A Meta-Heuristic Secure and Energy-Efficient Routing Protocol for Wireless Sensor Network-Based Industrial IoT. Energies, 16(10), 4198. https://doi.org/10.3390/en16104198









