Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters
Abstract
1. Introduction
1.1. Literature Review
1.2. Paper Approach
- Securing meshed DC microgrids control system by exploiting artificial neural networks for estimating authenticated measurements.
- Introducing distributed detection and mitigation layers for FDIAs on both voltage and current measurements.
- Keeping proper current sharing and decent reference voltage tracking, regardless of the presence of FDIA.
- Experimentally evaluating the dynamic performance of the proposed mitigation layers under different FDIA attack values.
2. System Model and Control Scheme
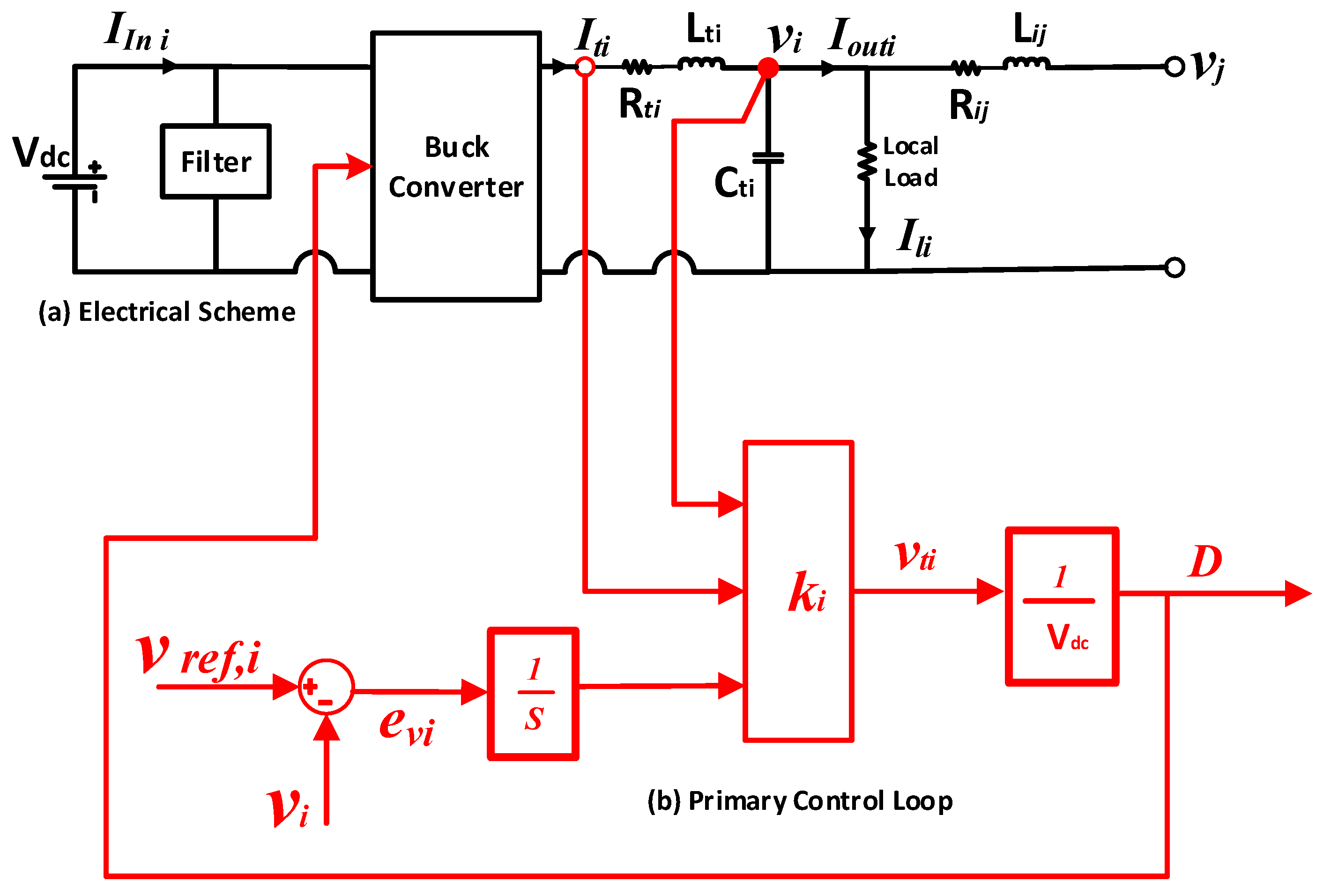
2.1. System Model
System Model after Adding the Integral Action
2.2. System Control Strategy
2.2.1. State Feedback Primary Controller
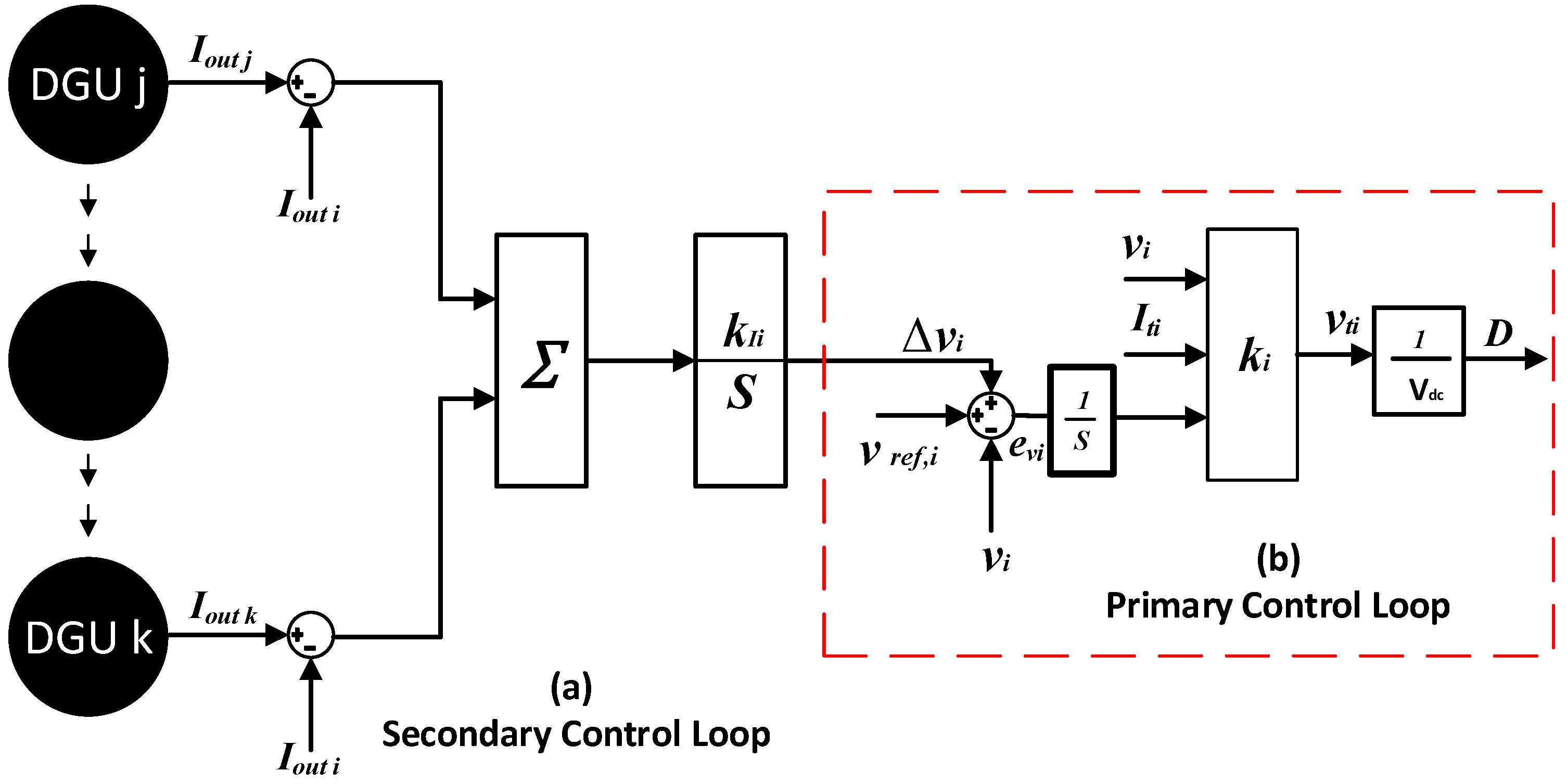
2.2.2. Consensus Based Secondary Controller
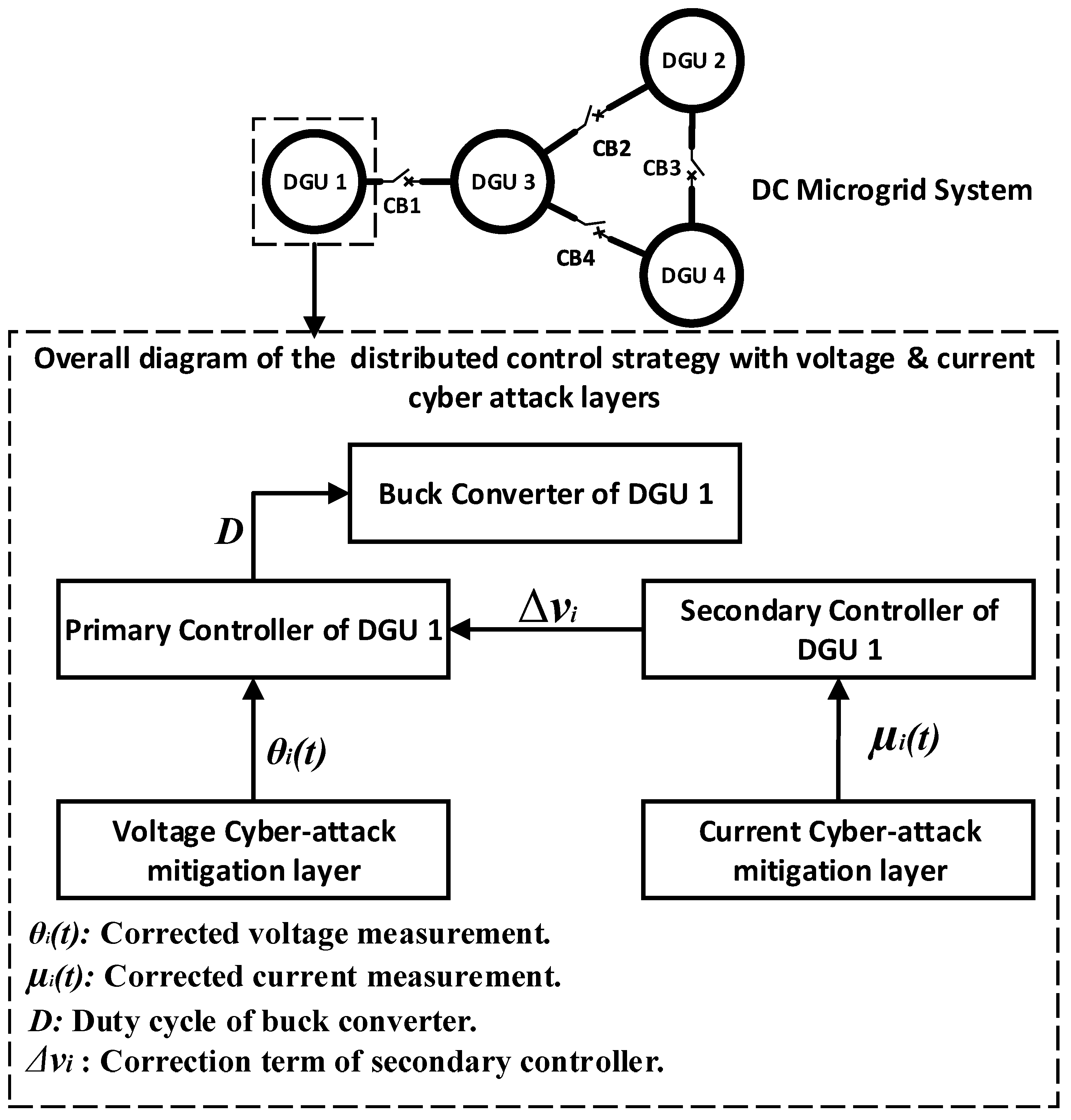
3. Proposed Modified Control Scheme
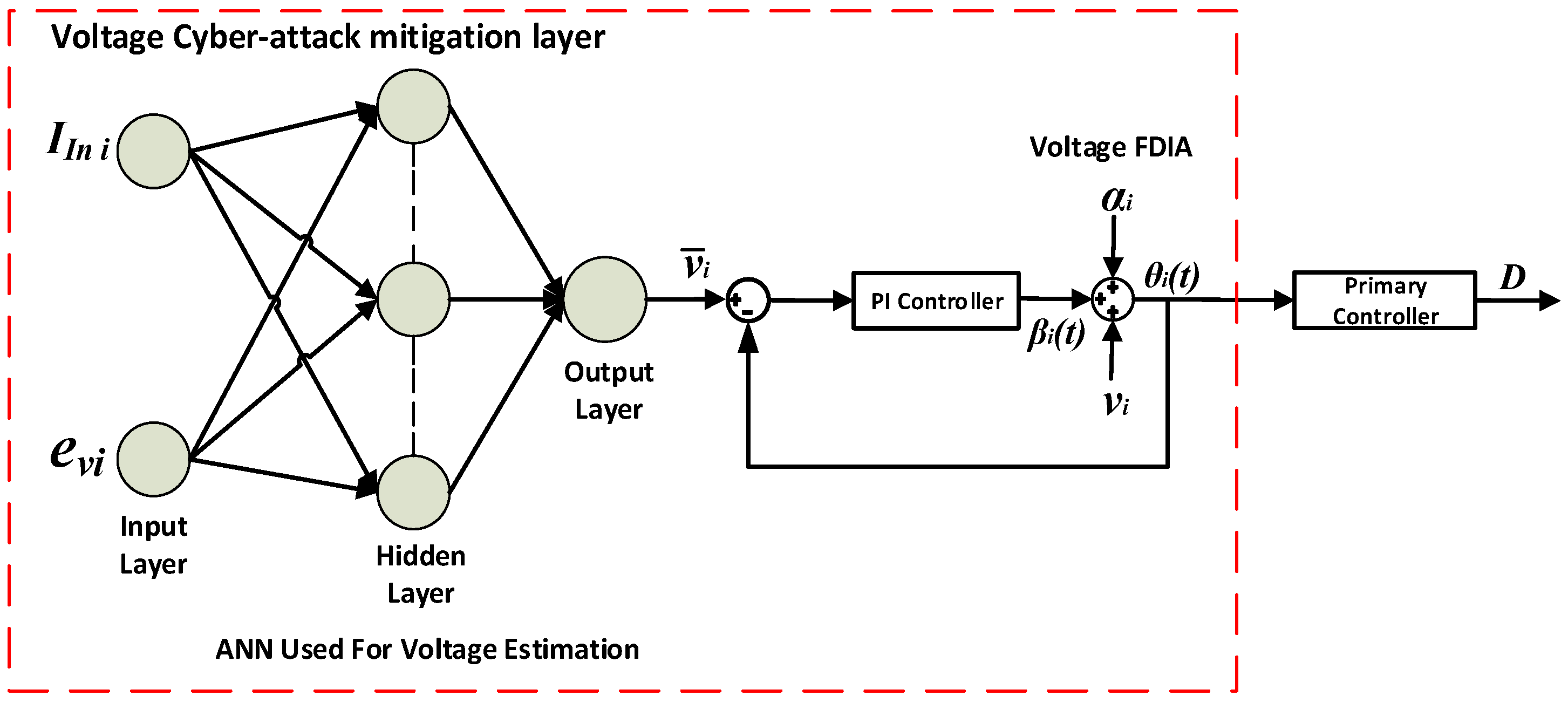
3.1. Modified Primary Controller
3.2. Modified Secondary Controller
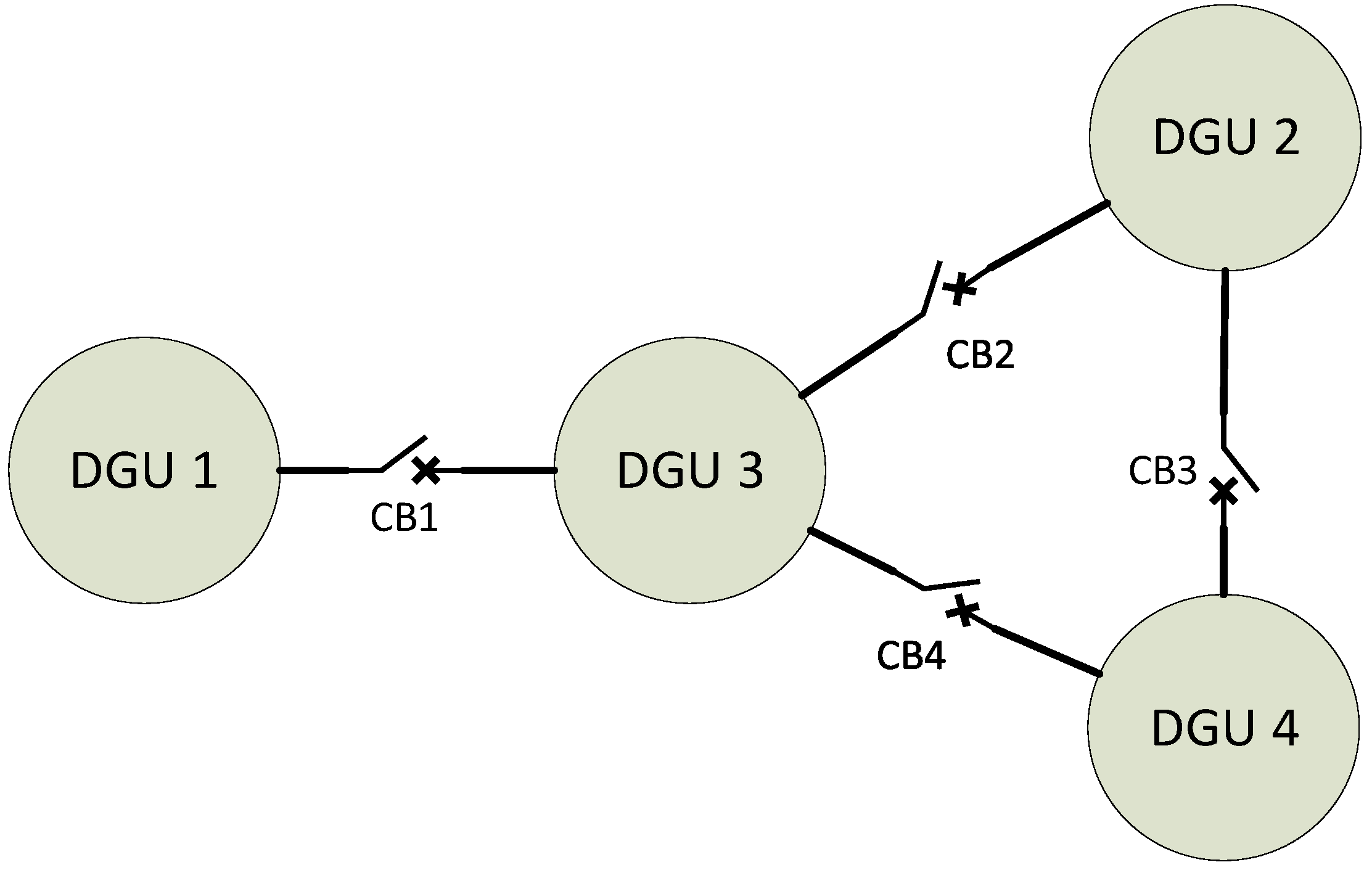
- DC microgrid system, including four meshed DGUs.
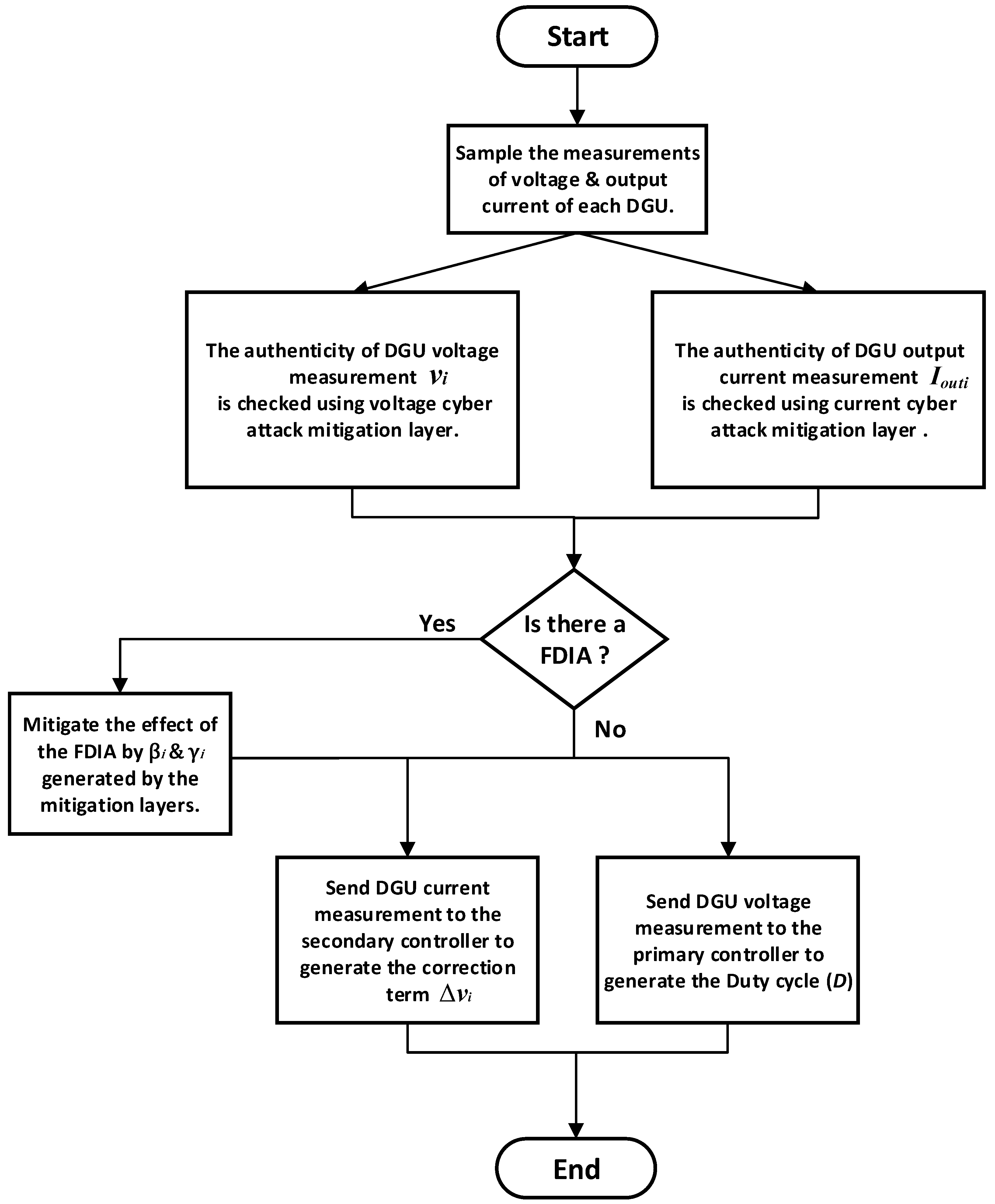
- Modified primary controller, which is based on a state feedback controller, Equation (14), integrated with a voltage cyber-attack detection, and mitigation layer.
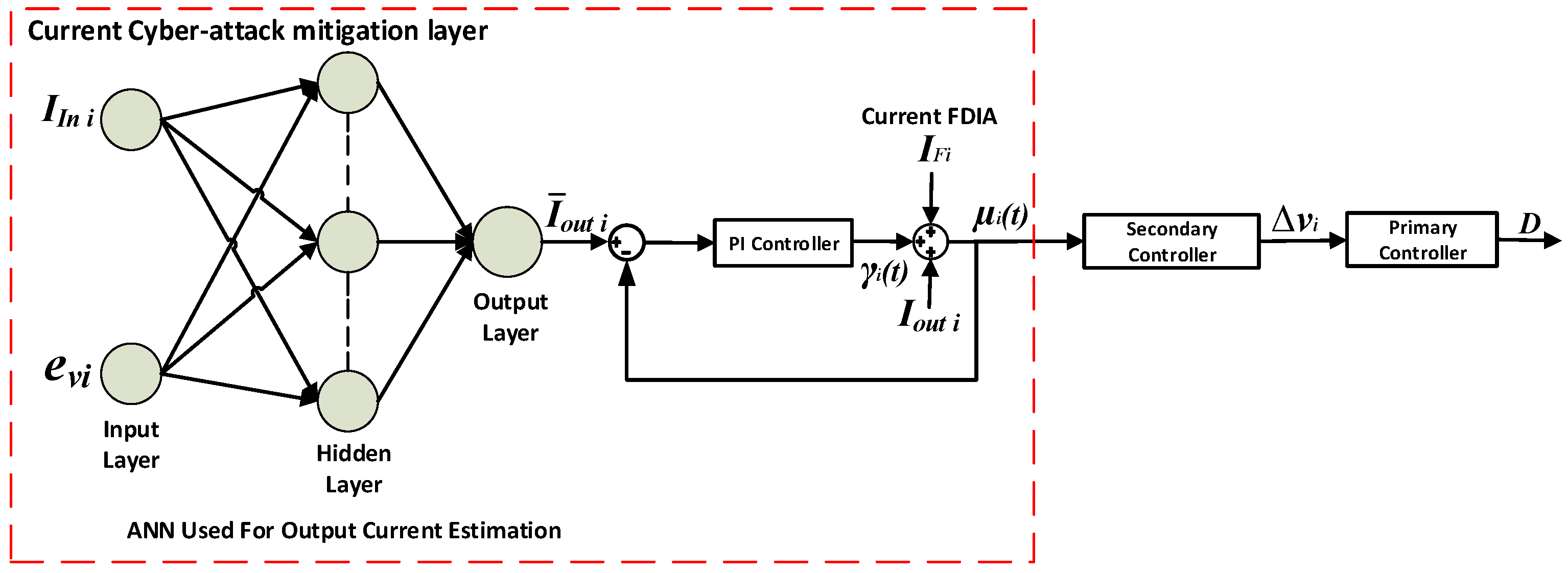
- Modified secondary controller, which is based on a consensus based controller, Equation (15), where a current cyber-attack detection and mitigation layer is incorporated.
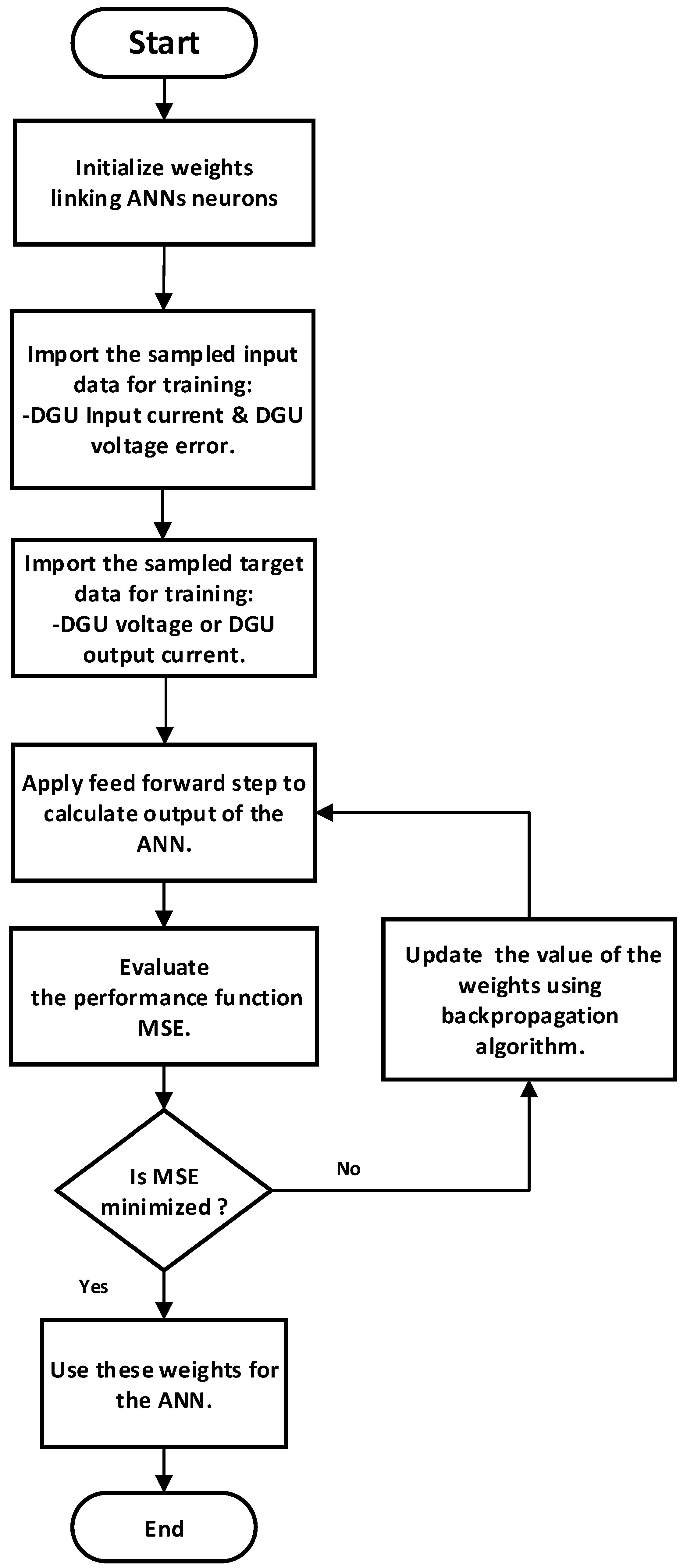
3.3. Cyber-Attack Detection and Mitigation Layers Training
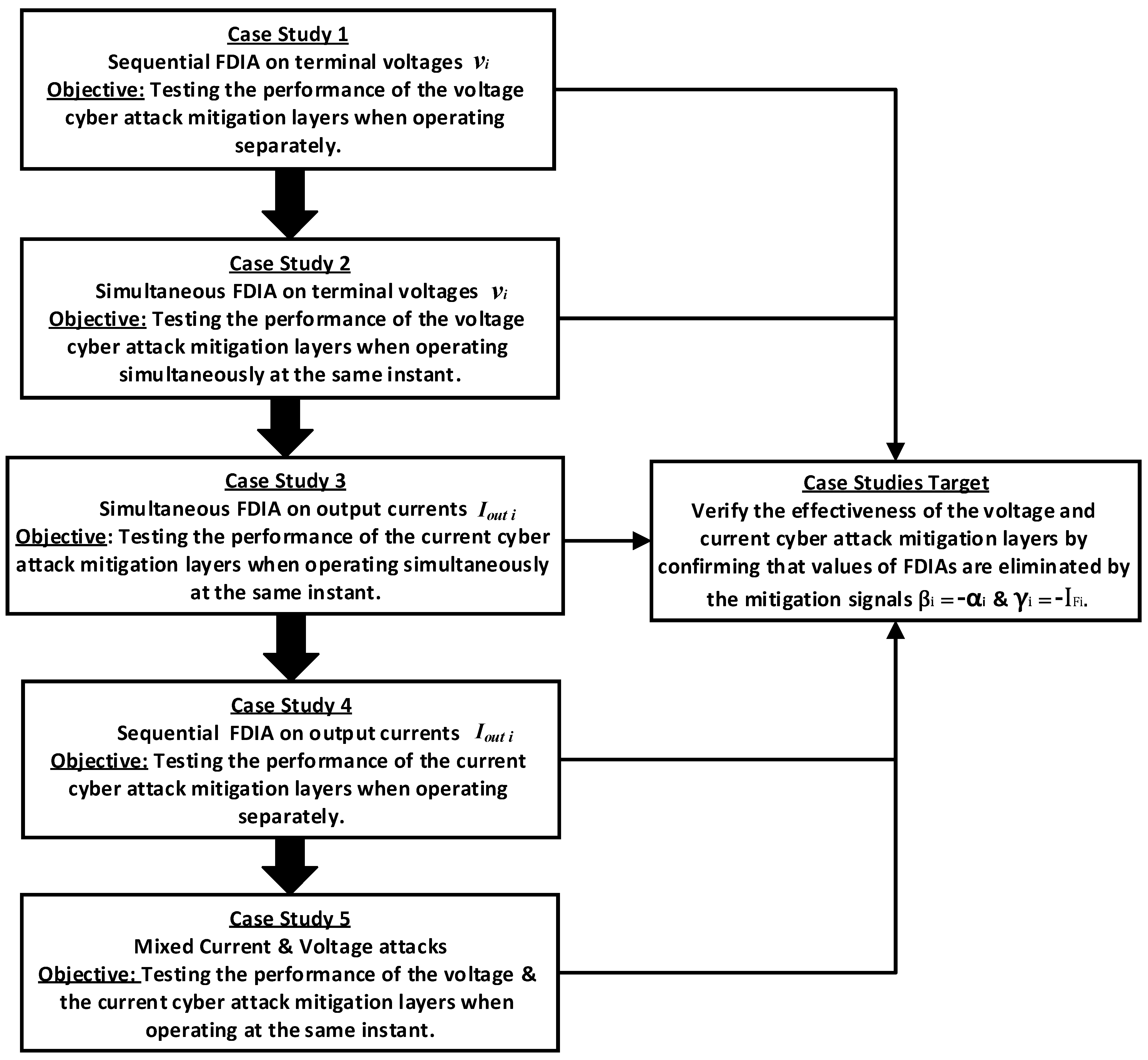
4. Simulation Results
4.1. Sequential FDIA on Terminal Voltages of DGUs
4.2. Simultaneous FDIA on Terminal Voltages of DGUs
4.3. Simultaneous FDIA on Output Currents of DGUs
4.4. Sequential FDIA on Output Currents of DGUs
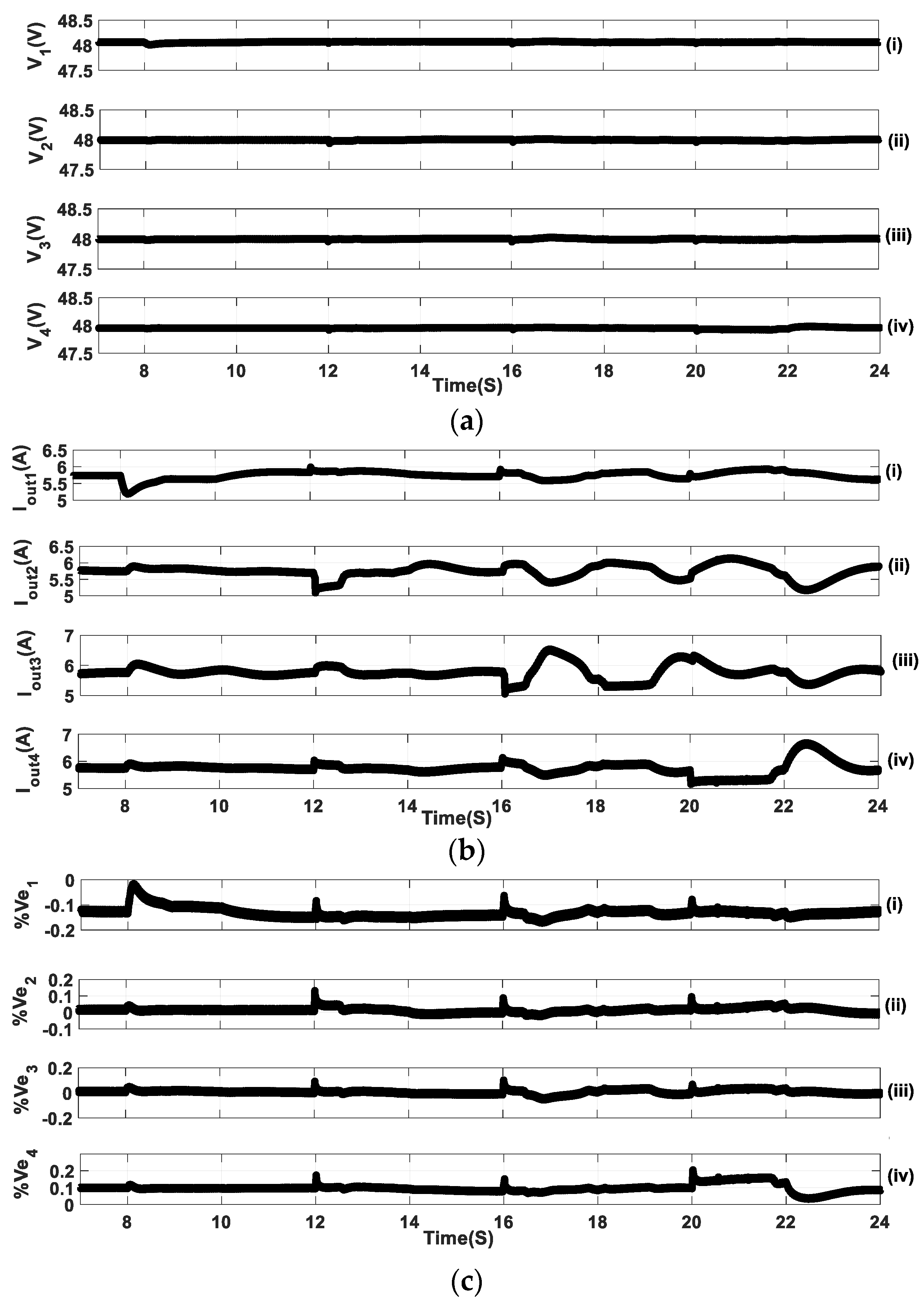
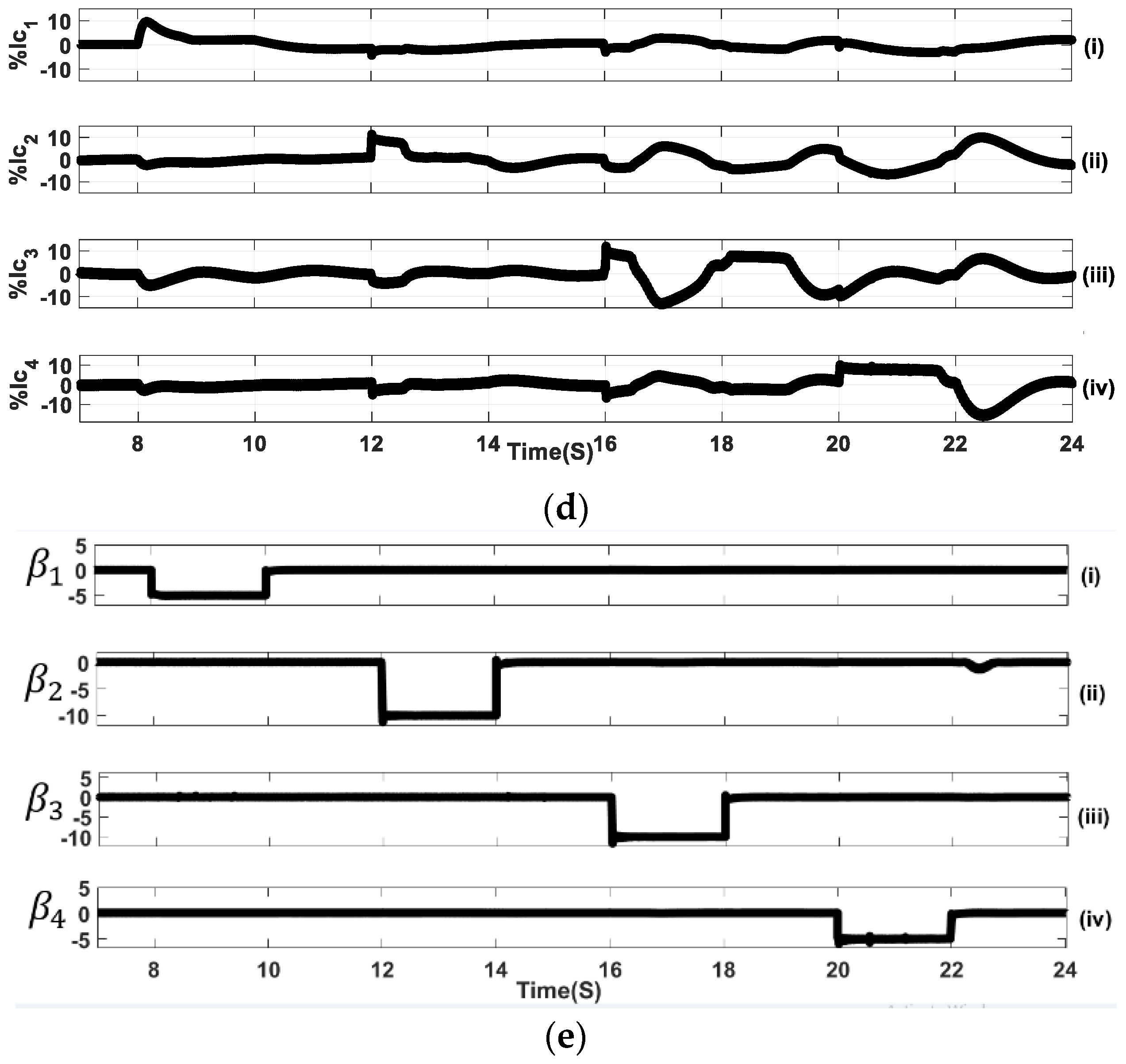
4.5. Mixed Current and Voltage FDIAs on DGUs
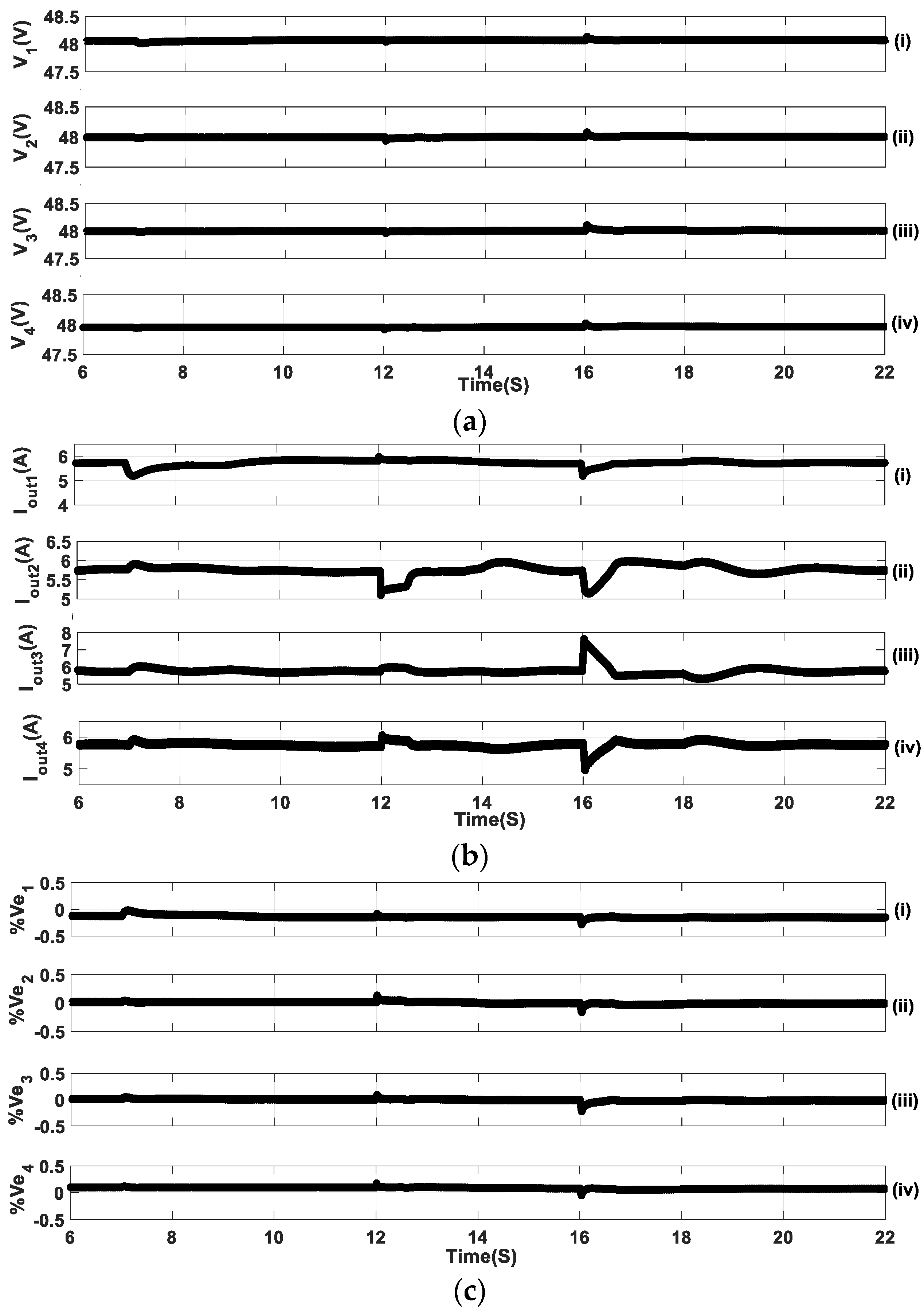
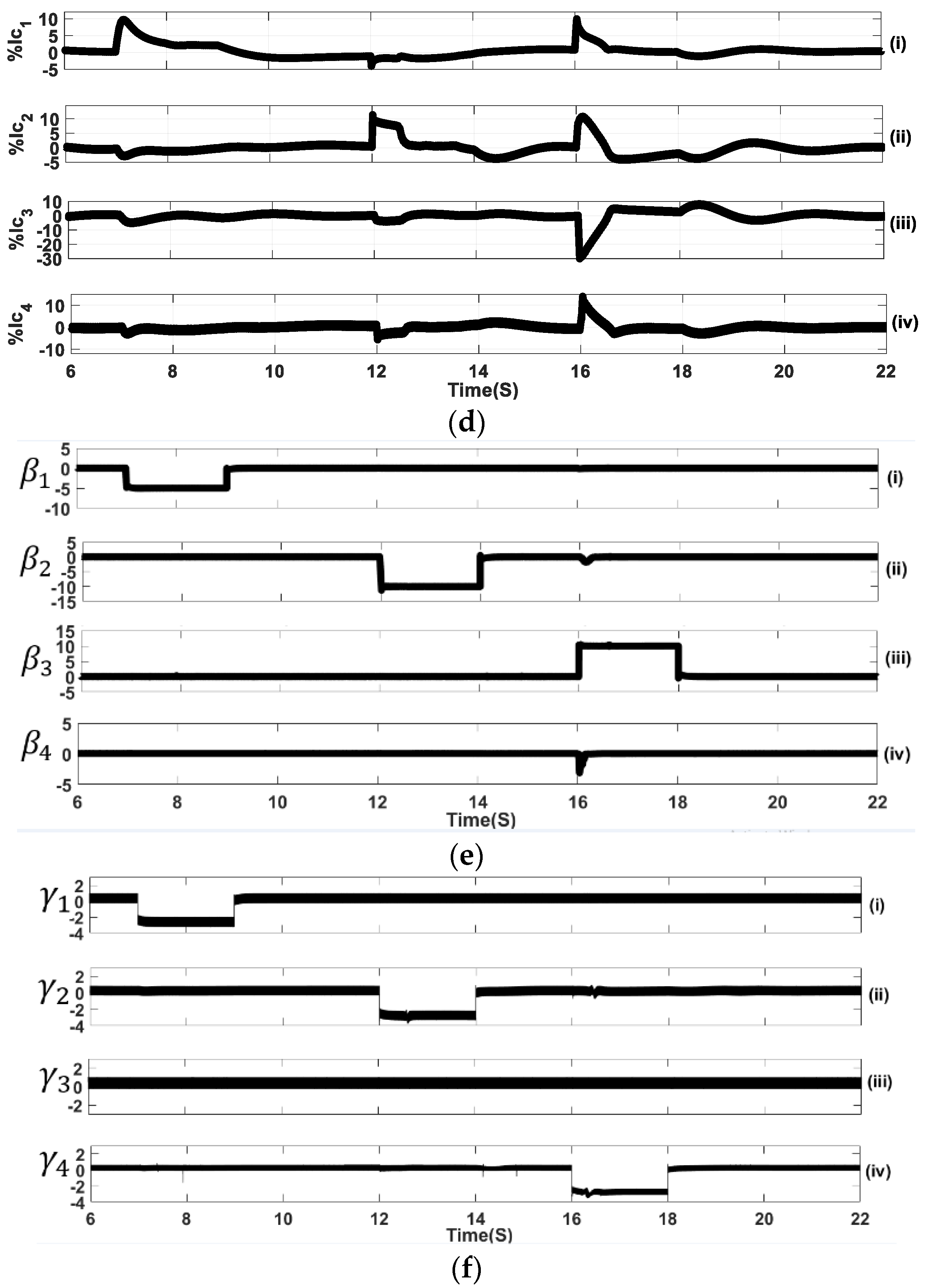
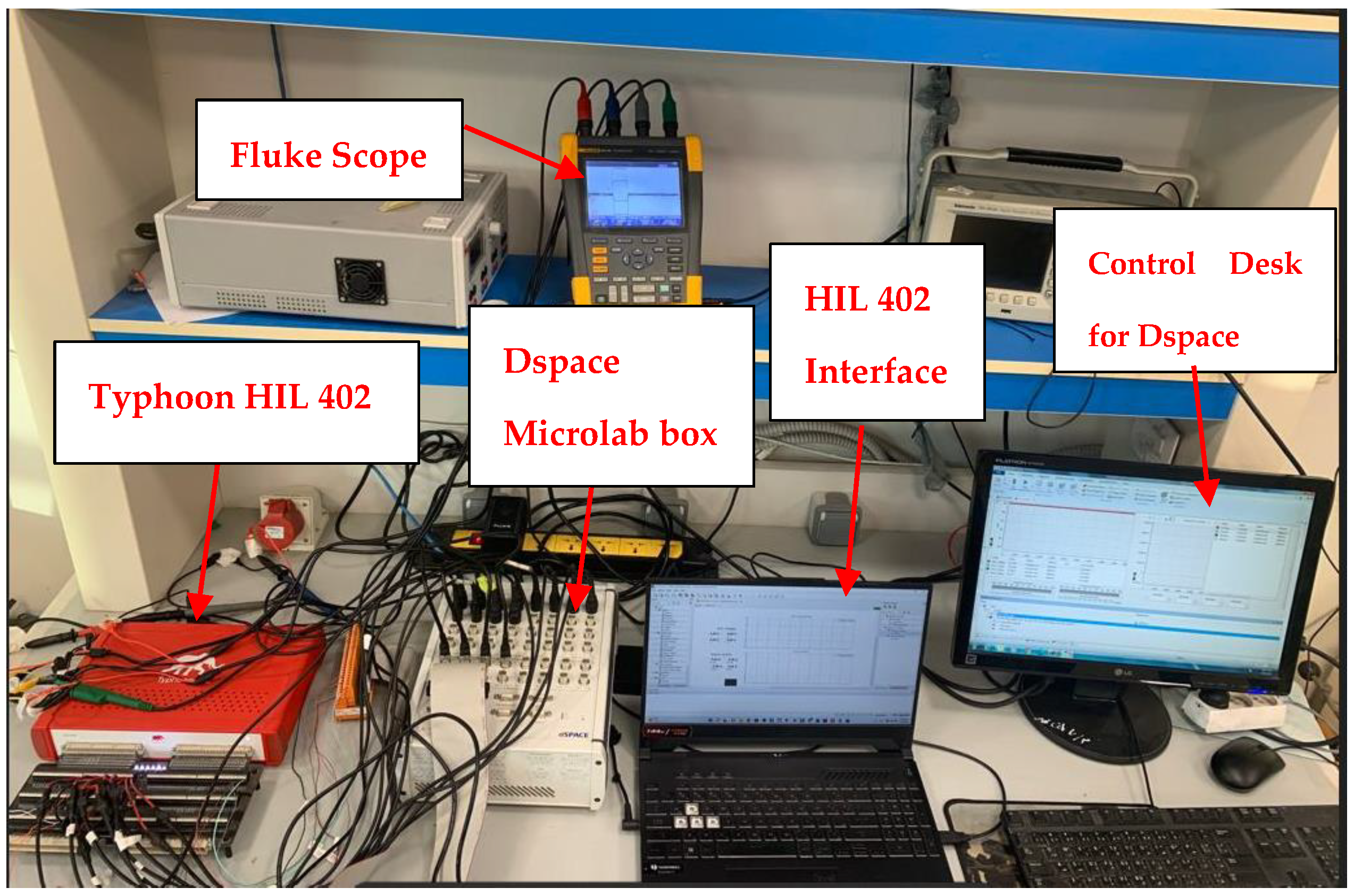
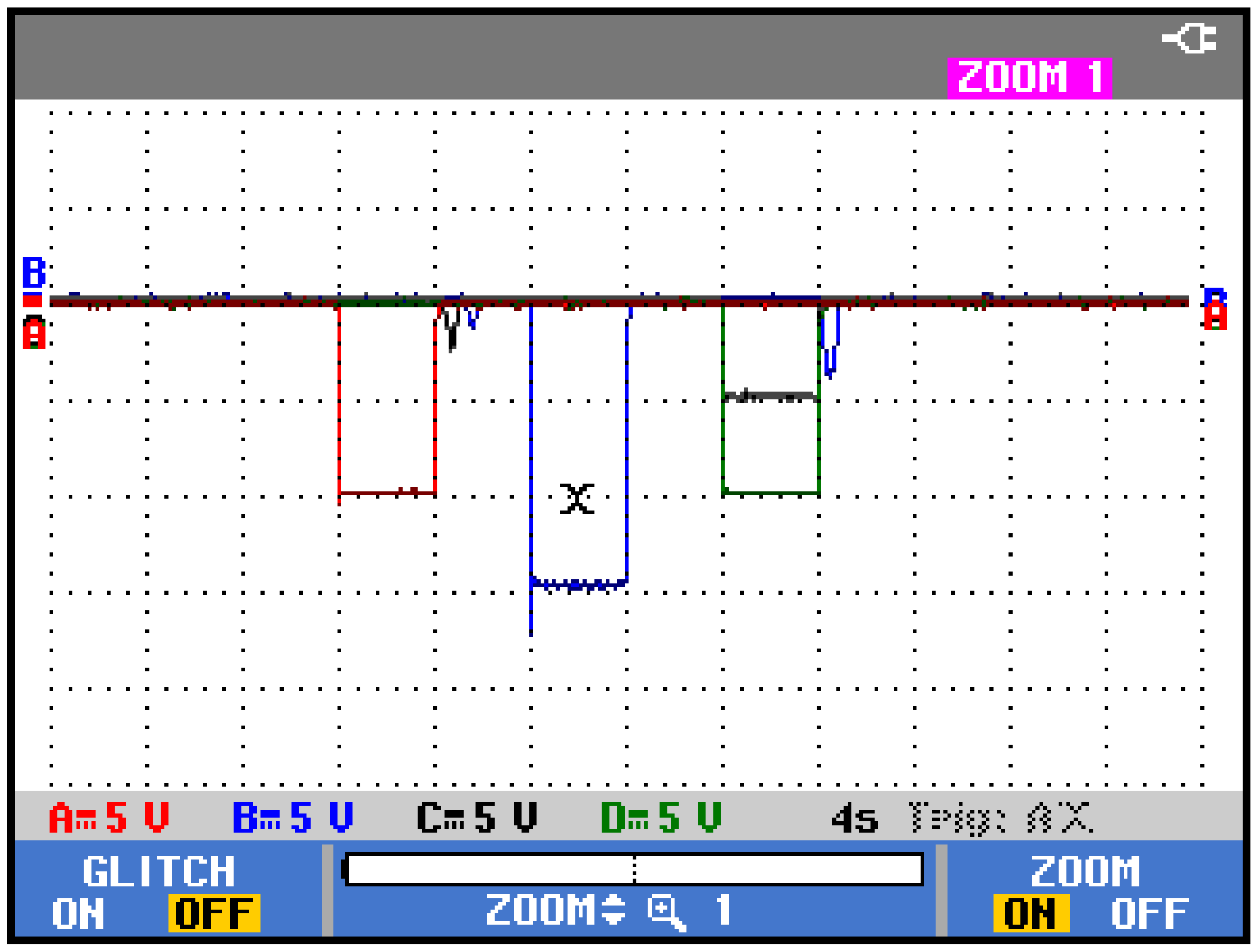
5. Experimental Verification
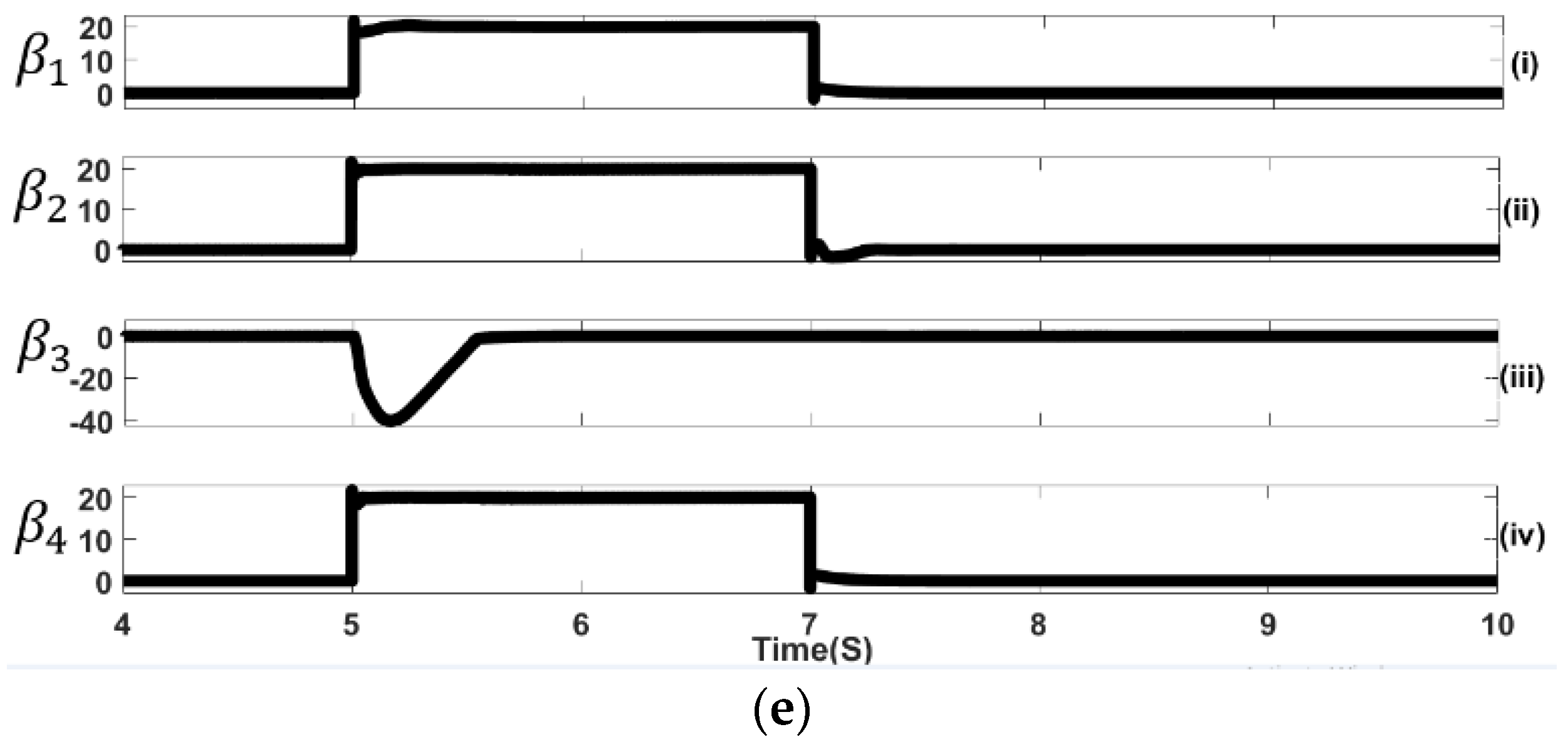
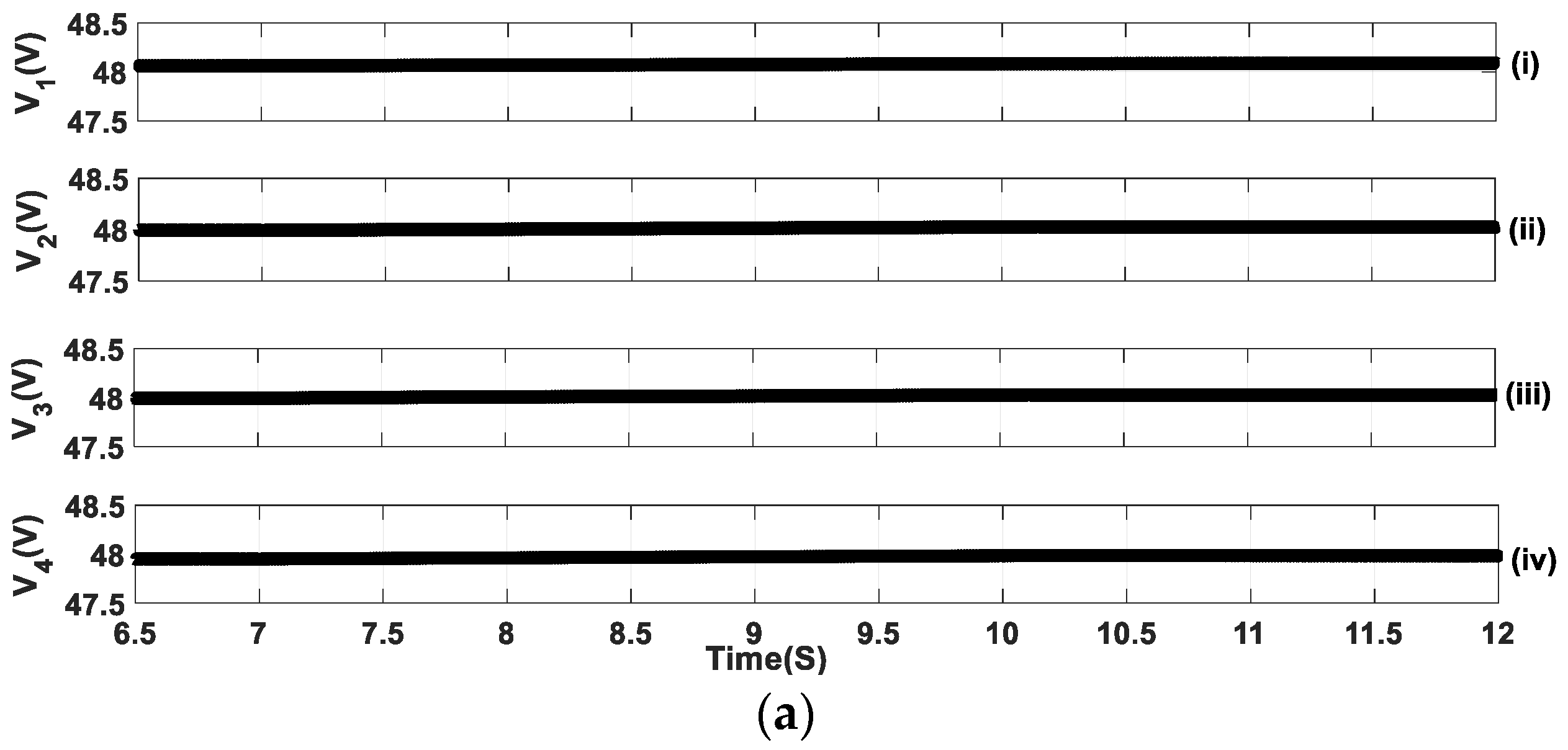
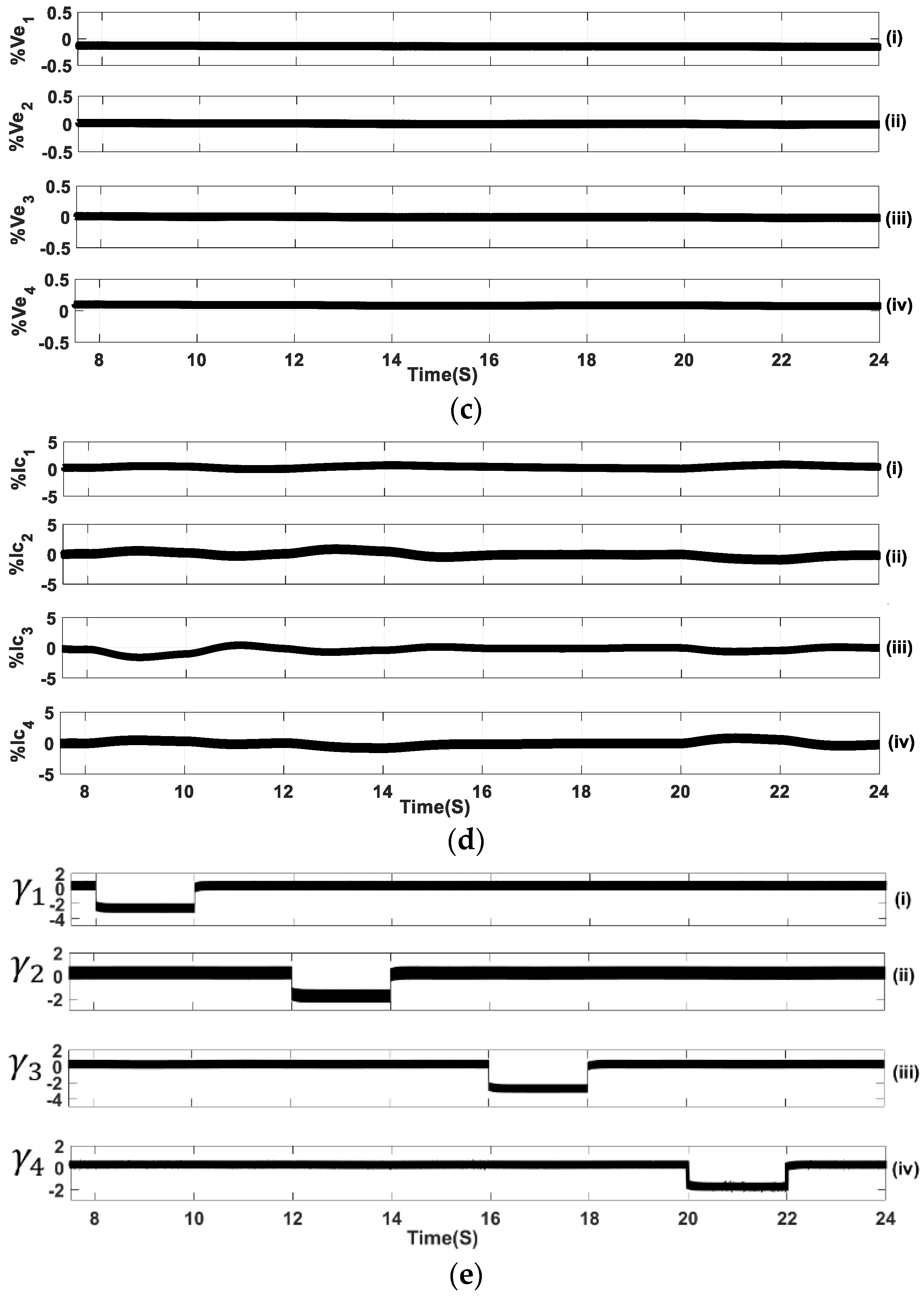
5.1. Sequential FDIA Voltage Attack
5.2. Mixed FDIA Voltage Attack
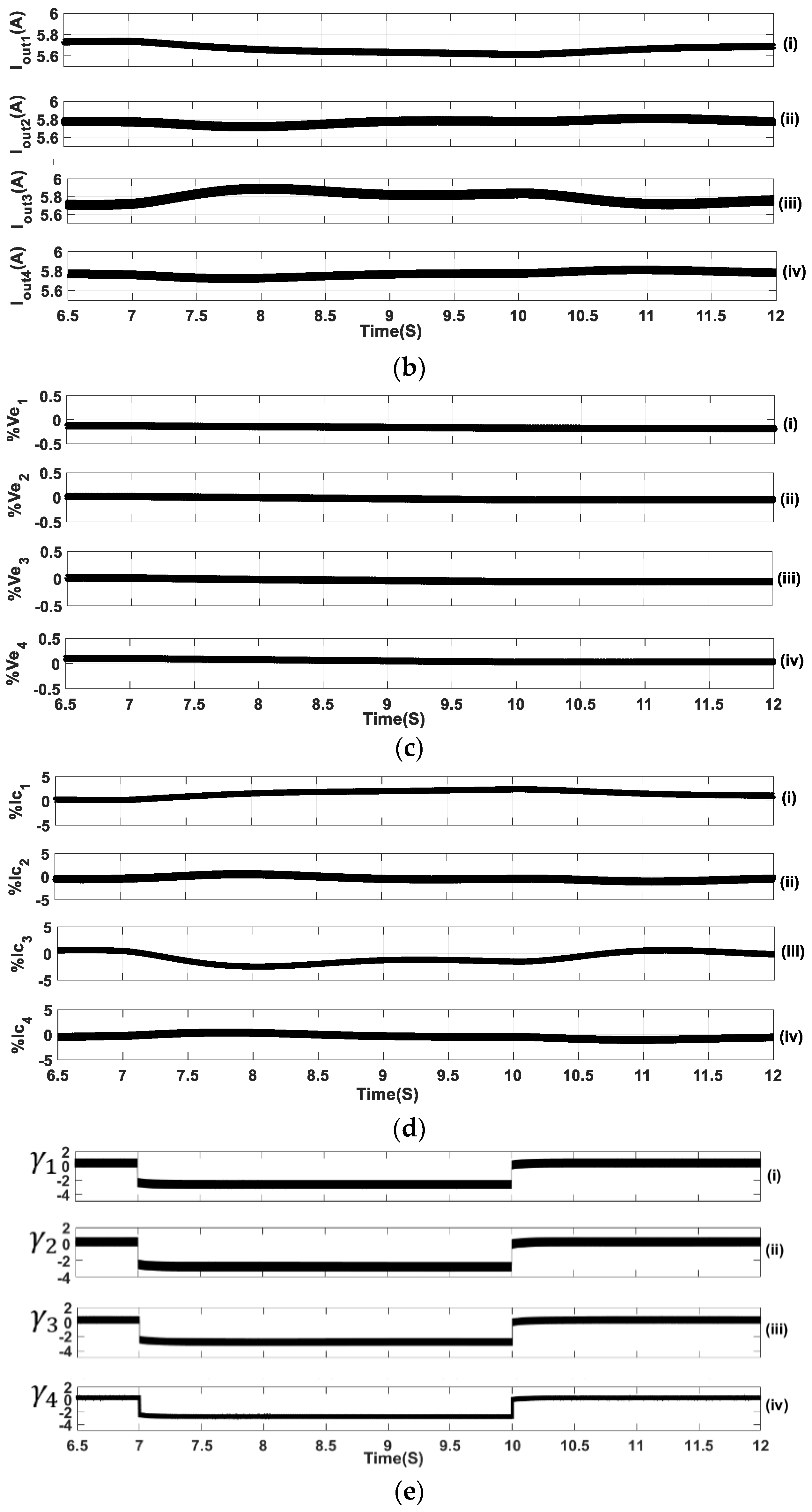
5.3. Sequential FDIA Current Attack
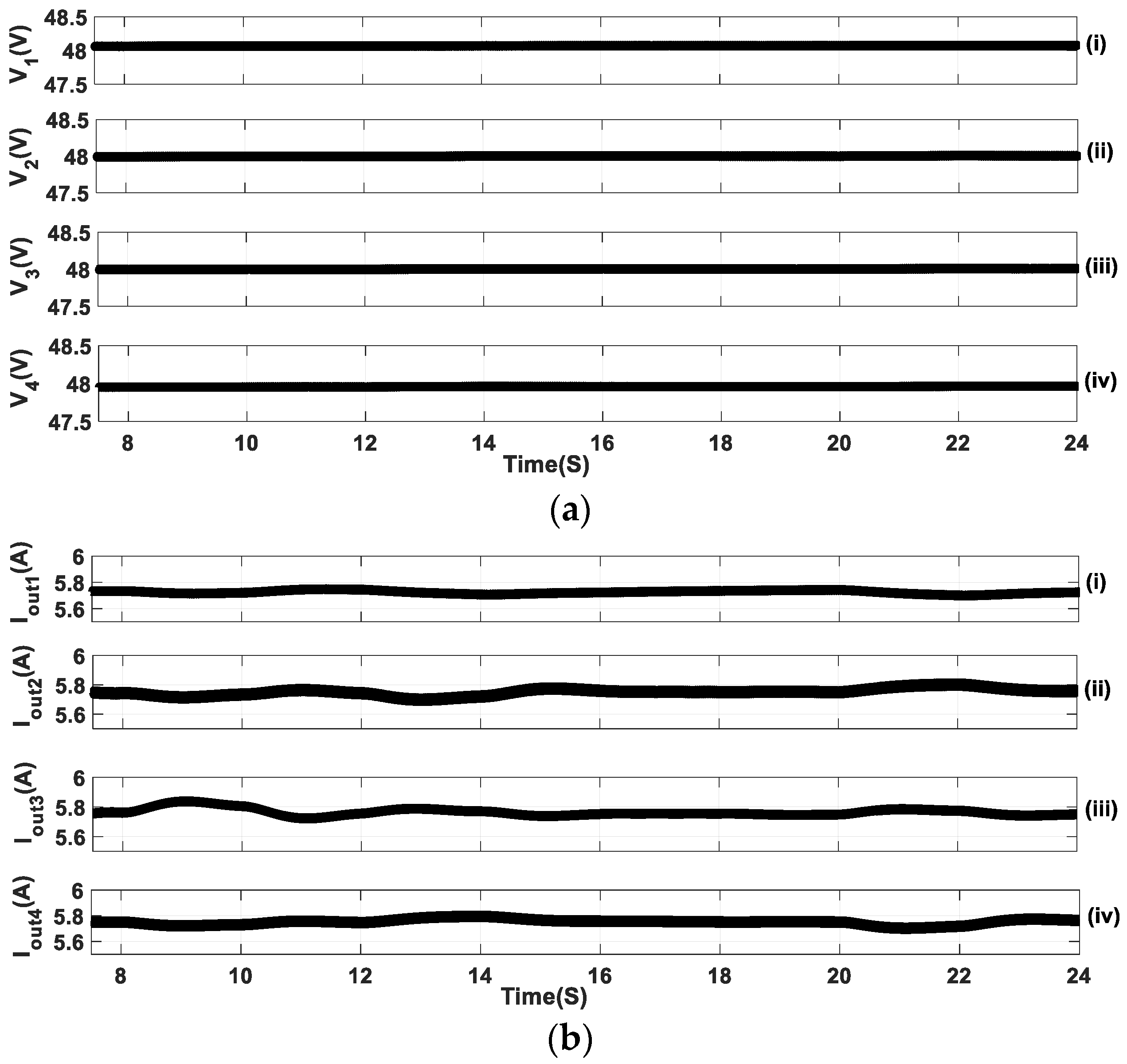
5.4. Simultaneous FDIA Current Attack
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Nomenclature
| Abbreviations | |
| DGU | Distributed Generator Unit. |
| FDIA | False Data Injection Attack. |
| ANN | Artificial Neural Network. |
| RESs | Renewable Energy Sources. |
| ESSs | Energy Storage Systems. |
| EVs | Electric Vehicles. |
| MGs | Microgrids. |
| PV | Photovoltaic. |
| DOS | Denial of Service. |
| RNN | Recurrent Neural Network. |
| NARX | Nonlinear Autoregressive Exogenous. |
| MPC | Model Predictive Control. |
| CBs | Circuit Breakers. |
| LMI | Linear Matrix Inequality. |
| MSE | Mean Square Error. |
| HIL | Hardware In the Loop. |
| Variables and Parameters | |
| DGUi terminal voltage after LC filter. | |
| DGUi terminal voltage before LC filter. | |
| DGUi inductor current. | |
| DGUi local load current. | |
| DGUi LC filter inductance. | |
| DGUi LC filter capacitance. | |
| DGUi terminal resistance. | |
| Resistance of the line connecting DGUs i and j. | |
| Inductance of the line connecting DGUs i and j. | |
| State vector. | |
| Control action input to the DGUi system. | |
| External input. | |
| Vector represents the coupling of DGUi with each neighboring DGUj. | |
| Measured output vector. | |
| Controlled output variable. | |
| Reference voltage of DGUi. | |
| D | Duty cycle of the buck converter. |
| e[i](t) | Steady state error of the controlled variable. |
| Dynamics of the integrator effect. | |
| Updated state vector after adding the integrator dynamics. | |
| Updated external input after adding the integrator dynamics. | |
| Updated vector representing the coupling of DGUi with each neighboring DGUj, after adding the integrator dynamics. | |
| Updated measured output vector after adding the integrator dynamics. | |
| Updated controlled output variable after adding the integrator dynamics. | |
| Input voltage of the buck converter. | |
| Primary controller gain. | |
| Secondary controller gain. | |
| DGUi injected output current. | |
| Correction term generated by secondary controller. | |
| Manipulated voltage of DGUi. | |
| False injected term to voltage measurement of DGUi. | |
| The final steady state value of | |
| Manipulated output current of DGUi. | |
| False injected term to output current measurement of DGUi. | |
| Corrected voltage measurement of DGUi. | |
| Voltage attack mitigation signal. | |
| Input current of DGUi. | |
| DGUi voltage error. | |
| Estimated terminal voltage of DGUi. | |
| Estimated output current of DGUi. | |
| Corrected current measurement of DGUi. | |
| Current attack mitigation signal. | |
| Target output of the ANN. | |
| Estimated output of the ANN. | |
| Percentage voltage error DGUi. | |
| Percentage change in current sharing for DGUi. | |
| Equal current sharing value. | |
References
- Dragičević, T.; Lu, X.; Vasquez, J.C.; Guerrero, J.M. DC Microgrids—Part I: A Review of Control Strategies and Stabilization Techniques. IEEE Trans. Power Electron. 2016, 31, 4876–4891. [Google Scholar]
- Lee, H.; Kang, J.-W.; Choi, B.-Y.; Kang, K.-M.; Kim, M.-N.; An, C.-G.; Yi, J.; Won, C.-Y. Energy Management System of DC Microgrid in Grid-Connected and Stand-Alone Modes: Control, Operation and Experimental Validation. Energies 2021, 14, 581. [Google Scholar] [CrossRef]
- Aluko, A.; Swanson, A.; Jarvis, L.; Dorrell, D. Modeling and Stability Analysis of Distributed Secondary Control Scheme for Stand-Alone DC Microgrid Applications. Energies 2022, 15, 5411. [Google Scholar] [CrossRef]
- Lema, M.; Pavon, W.; Ortiz, L.; Asiedu-Asante, A.B.; Simani, S. Controller Coordination Strategy for DC Microgrid Using Distributed Predictive Control Improving Voltage Stability. Energies 2022, 15, 5442. [Google Scholar] [CrossRef]
- Mokhtar, M.; Marei, M.I.; El-Sattar, A.A. A control scheme for islanded and grid-connected DC microgrids. In Proceedings of the 2017 19th International IEEE Middle East Power Systems Conference (MEPCON), Cairo, Egypt, 19–21 December 2017; pp. 176–180. [Google Scholar]
- Meng, L.; Shafiee, Q.; Trecate, G.F.; Karimi, H.; Fulwani, D.; Lu, X.; Guerrero, J.M. Review on Control of DC Microgrids and Multiple Microgrid Clusters. IEEE J. Emerg. Sel. Top. Power Electron. 2017, 5, 928–948. [Google Scholar]
- Kumar, R.; Pathak, M.K. Distributed droop control of dc microgrid for improved voltage regulation and current sharing. IET Renew. Power Gener. 2020, 14, 2499–2506. [Google Scholar] [CrossRef]
- Mokhtar, M.; Marei, M.I.; El-Sattar, A.A. Improved current sharing techniques for DC microgrids. Electr. Power Compon. Syst. 2018, 46, 757–767. [Google Scholar] [CrossRef]
- Tucci, M.; Meng, L.; Guerrero, J.M.; Trecate, G.F. Stable current sharing and voltage balancing in DC microgrids: A consensus-based secondary control layer. Automatica 2018, 95, 1–13. [Google Scholar] [CrossRef]
- Mohamed, S.; Mokhtar, M.; Marei, M.I. An Adaptive Control of Remote Hybrid Microgrid based on the CMPN Algorithm. Electr. Power Syst. Res. 2022, 213, 108793. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S.; Peng, J.C.-H.; Dragičević, T. A Stealth Cyber-Attack Detection Strategy for DC Microgrids. IEEE Trans. Power Electron. 2019, 34, 8162–8174. [Google Scholar] [CrossRef]
- Beg, O.A.; Johnson, T.T.; Davoudi, A. Detection of False-Data Injection Attacks in Cyber-Physical DC Microgrids. IEEE Trans. Ind. Inform. 2017, 13, 2693–2703. [Google Scholar] [CrossRef]
- Kosut, O.; Jia, L.; Thomas, R.J.; Tong, L. Malicious Data Attacks on the Smart Grid. IEEE Trans. Smart Grid 2011, 2, 645–658. [Google Scholar] [CrossRef]
- Xie, L.; Mo, Y.; Sinopoli, B. Integrity Data Attacks in Power Market Operations. IEEE Trans. Smart Grid 2011, 2, 659–666. [Google Scholar] [CrossRef]
- Bobba, R.B.; Rogers, K.M.; Wang, Q.; Khurana, H.; Nahrstedt, K.; Overbye, J. Detecting false data injection attacks on DC state estimation. In Proceedings of the Preprints 1st Workshop Secure Control Systems (CPSWEEK), Stockholm, Sweden, 12 April 2010; pp. 1–9. [Google Scholar]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. False Data Injection Cyber-Attacks Mitigation in Parallel DC/DC Converters Based on Artificial Neural Networks. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 717–721. [Google Scholar] [CrossRef]
- Sahoo, S.; Peng, J.C.; Devakumar, A.; Mishra, S.; Dragičević, T. On Detection of False Data in Cooperative DC Microgrids—A Discordant Element Approach. IEEE Trans. Ind. Electron. 2020, 67, 6562–6571. [Google Scholar] [CrossRef]
- Beg, O.A.; Nguyen, L.V.; Johnson, T.T.; Davoudi, A. Signal Temporal Logic-Based Attack Detection in DC Microgrids. IEEE Trans. Smart Grid 2019, 10, 3585–3595. [Google Scholar] [CrossRef]
- Habibi, M.R.; Sahoo, S.; Rivera, S.; Dragičević, T.; Blaabjerg, F. Decentralized Coordinated Cyberattack Detection and Mitigation Strategy in DC Microgrids Based on Artificial Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4629–4638. [Google Scholar] [CrossRef]
- Gallo, A.J.; Turan, M.S.; Nahata, P.; Boem, F.; Parisini, T.; Ferrari-Trecate, G. Distributed Cyber-Attack Detection in the Secondary Control of DC Microgrids. In Proceedings of the 2018 European Control Conference (ECC), Limassol, Cyprus, 12–15 June 2018; pp. 344–349. [Google Scholar]
- Gallo, A.J.; Turan, M.S.; Boem, F.; Parisini, T.; Ferrari-Trecate, G. A Distributed Cyber-Attack Detection Scheme with Application to DC Microgrids. IEEE Trans. Autom. Control 2020, 65, 3800–3815. [Google Scholar] [CrossRef]
- Zhang, D.; Zhang, C. A NDO Based Attack Detection Observer and Isolation Strategy in Distributed DC Microgrid with FDIA. J. Phys. Conf. Ser. 2021, 1754, 012011. [Google Scholar] [CrossRef]
- Shi, D.; Lin, P.; Wang, Y.; Chu, C.-C.; Xu, Y.; Wang, P. Deception Attack Detection of Isolated DC Microgrids Under Consensus-Based Distributed Voltage Control Architecture. IEEE J. Emerg. Sel. Top. Circuits Syst. 2021, 11, 155–167. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of False Data Injection Cyber-Attacks in DC Microgrids Based on Recurrent Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 5294–5310. [Google Scholar] [CrossRef]
- Cecilia, A.; Sahoo, S.; Dragičević, T.; Costa-Castelló, R.; Blaabjerg, F. Detection and Mitigation of False Data in Cooperative DC Microgrids With Unknown Constant Power Loads. IEEE Trans. Power Electron. 2021, 36, 9565–9577. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragicevic, T. Secure MPC/ANN-Based False Data Injection Cyber-Attack Detection and Mitigation in DC Microgrids. IEEE Syst. J. 2021, 16, 1487–1498. [Google Scholar] [CrossRef]
- Yan, J.; Tang, B.; He, H. Detection of false data attacks in smart grid with supervised learning. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), Vancouver, BC, Canada, 24–29 July 2016; pp. 1395–1402. [Google Scholar]
- Demertzis, K.; Iliadis, L.S.; Anezakis, V.-D. An innovative soft computing system for smart energy grids cybersecurity. Adv. Build. Energy Res. 2018, 12, 3–24. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27. [Google Scholar] [CrossRef]
- Ma, L.; Xu, G. Distributed Resilient Voltage and Reactive Power Control for Islanded Microgrids under False Data Injection Attacks. Energies 2020, 13, 3828. [Google Scholar] [CrossRef]
- Mbungu, N.T.; Naidoo, R.M.; Bansal, R.C.; Vahidinasab, V. Overview of the Optimal Smart Energy Coordination for Microgrid Applications. IEEE Access 2019, 7, 163063–163084. [Google Scholar] [CrossRef]
- Fortuna, L.; Buscarino, A. Nonlinear Technologies in Advanced Power Systems: Analysis and Control. Energies 2022, 15, 5167. [Google Scholar] [CrossRef]
- Tucci, M.; Riverso, S.; Vasquez, J.C.; Guerrero, J.M.; Ferrari-Trecate, G. A Decentralized Scalable Approach to Voltage Control of DC Islanded Microgrids. IEEE Trans. Control. Syst. Technol. 2016, 24, 1965–1979. [Google Scholar] [CrossRef]
- Tucci, M.; Meng, L.; Guerrero, J.M.; Ferrari-Trecate, G. Consensus Algorithms and Plug-and-Play Control for Current Sharing in DC Microgrids; Technical Report; IGM Institute of Mechanical Engineering: Lausanne, Switzerland, 2016. [Google Scholar]
- El-Ebiary, A.H.; Attia, M.A.; Marei, M.I.; Sameh, M.A. An Integrated Seamless Control Strategy for Distributed Generators Based on a Deep Learning Artificial Neural Network. Sustainability 2022, 14, 13506. [Google Scholar] [CrossRef]
- Lv, C.; Xing, Y.; Zhang, J.; Na, X.; Li, Y.; Liu, T.; Cao, D.; Wang, F. Levenberg–Marquardt Backpropagation Training of Multilayer Neural Networks for State Estimation of a Safety-Critical Cyber-Physical System. IEEE Trans. Ind. Inform. 2018, 14, 3436–3446. [Google Scholar] [CrossRef]








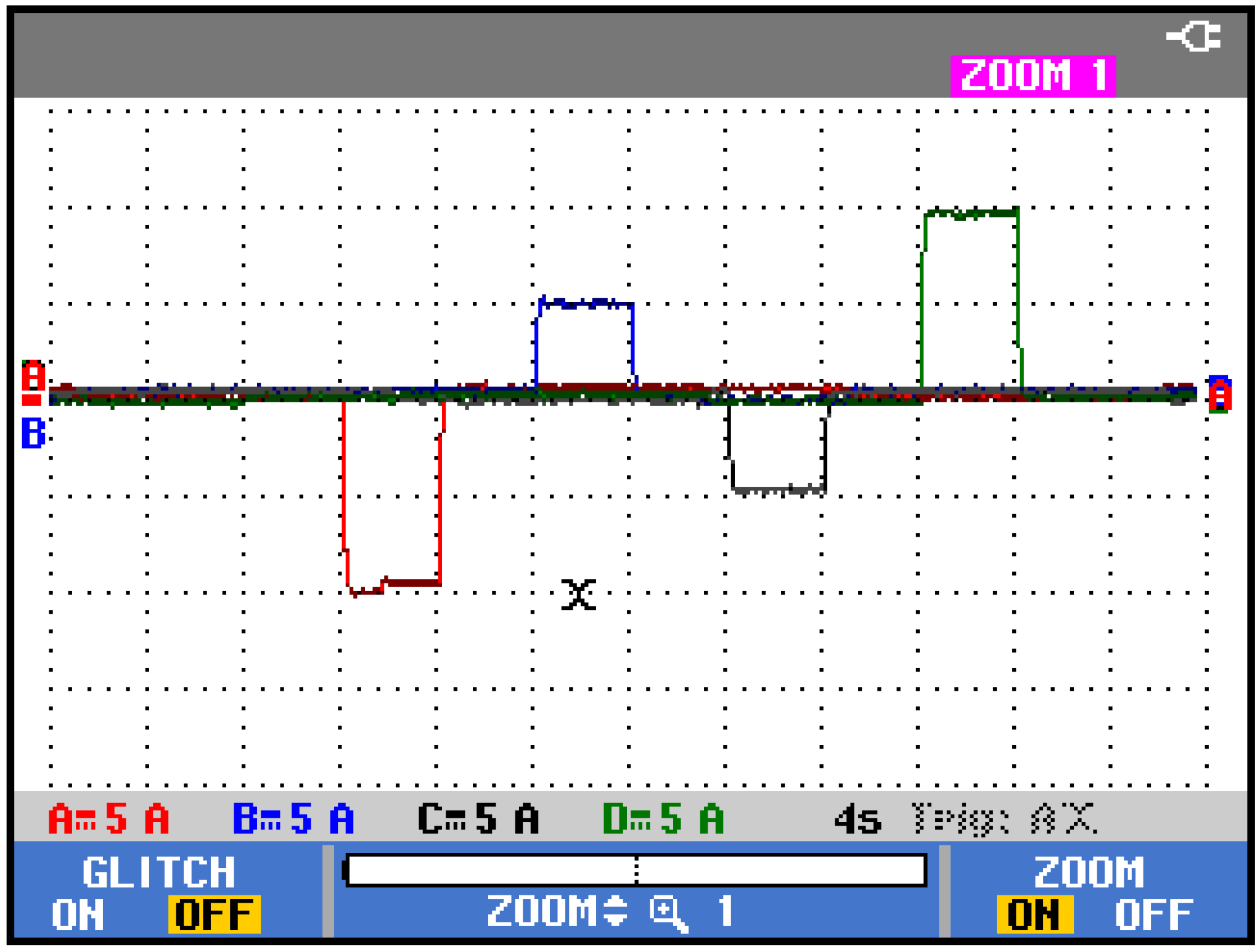

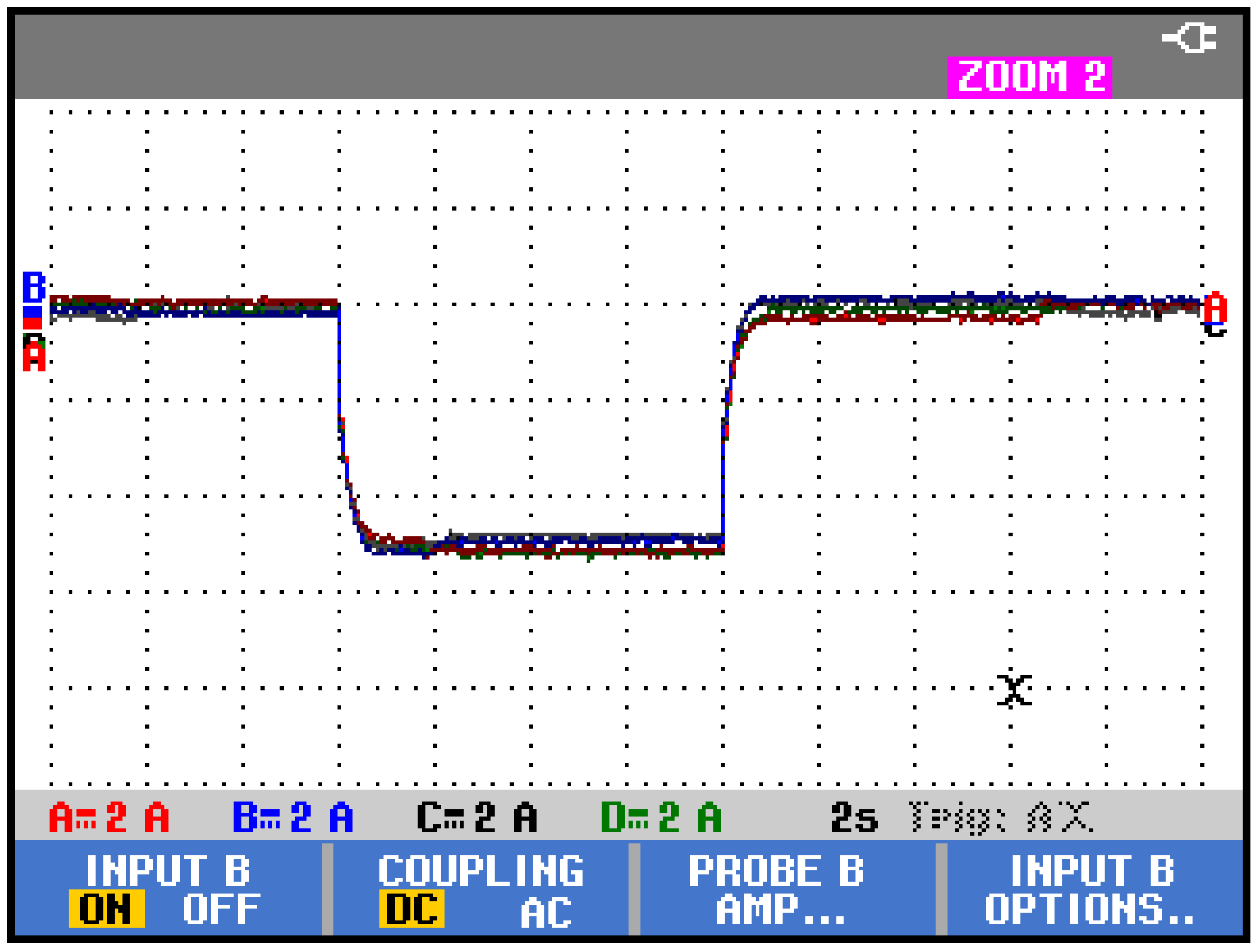
| Connected DGUs (i,j) | Resistance Rij (Ω) | Inductance Lij (µH) |
|---|---|---|
| Line 1–3 | 0.07 | 2.1 |
| Line 2–3 | 0.04 | 2.3 |
| Line 2–4 | 0.08 | 1.8 |
| Line 3–4 | 0.07 | 1 |
| Input/Output Voltages: 100 V /48 V | ||||
|---|---|---|---|---|
| DGU i | Resistance Rti (Ω) | Inductance Lti (mH) | Capacitance Cti (mF) | Local Load (Ω) |
| DGU 1 | 0.2 | 1.8 | 2.2 | 10 |
| DGU 2 | 0.3 | 2.0 | 1.9 | 9 |
| DGU 3 | 0.1 | 2.2 | 1.7 | 8 |
| DGU 4 | 0.5 | 3.0 | 2.5 | 7 |
| Primary Controllers’ Gains | |
|---|---|
| DGU 1 | = |
| DGU 2 | |
| DGU 3 | |
| DGU 4 | |
| Secondary Integral Controller Gain: = 0.02 | |
| DGU i | FDIA Value | Attack Instant |
|---|---|---|
| DGU 1 | t = [8–10 s] | |
| DGU 2 | t = [12–14 s] | |
| DGU 3 | t = [16–18 s] | |
| DGU 4 | t = [20–22 s] |
| DGU i | FDIA Value | Attack Instant |
|---|---|---|
| DGU 1 | t = [5–7 s] | |
| DGU 2 | t = [5–7 s] | |
| DGU 4 | t = [5–7 s] |
| DGU i | FDIA Value | Attack Instant |
|---|---|---|
| DGU 1 | t = [7–10 s] | |
| DGU 2 | t = [7–10 s] | |
| DGU 3 | t = [7–10 s] | |
| DGU 4 | t = [7–10 s] |
| DGU i | FDIA Value | Attack Instant |
|---|---|---|
| DGU 1 | t = [8–10 s] | |
| DGU 2 | t = [12–14 s] | |
| DGU 3 | t = [16–18 s] | |
| DGU 4 | t = [20–22 s] |
| DGU i | FDIA Value | Attack Instant |
|---|---|---|
| DGU 1 | | t = [7–9 s] |
| DGU 2 | | t = [12–14 s] |
| DGU 3 | t = [16–18 s] | |
| DGU 4 | t = [16–18 s] |
| Case Study | Average Percentage Voltage Error | Average Percentage Change in Current Sharing |
|---|---|---|
| Sequential voltage attack | 0.1% | 10% |
| Simultaneous voltage attack | 1% | 10% |
| Simultaneous current attack | 0% | 2% |
| Sequential current attack | 0% | 0% |
| Mixed current & voltage attack | 0.2% | 5% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
EL-Ebiary, A.H.; Mokhtar, M.; Mansour, A.M.; Awad, F.H.; Marei, M.I.; Attia, M.A. Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters. Energies 2022, 15, 9426. https://doi.org/10.3390/en15249426
EL-Ebiary AH, Mokhtar M, Mansour AM, Awad FH, Marei MI, Attia MA. Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters. Energies. 2022; 15(24):9426. https://doi.org/10.3390/en15249426
Chicago/Turabian StyleEL-Ebiary, Ahmed H., Mohamed Mokhtar, Atef M. Mansour, Fathy H. Awad, Mostafa I. Marei, and Mahmoud A. Attia. 2022. "Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters" Energies 15, no. 24: 9426. https://doi.org/10.3390/en15249426
APA StyleEL-Ebiary, A. H., Mokhtar, M., Mansour, A. M., Awad, F. H., Marei, M. I., & Attia, M. A. (2022). Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters. Energies, 15(24), 9426. https://doi.org/10.3390/en15249426








