Privacy and Auditability in the Local Energy Market of an Energy Community with Homomorphic Encryption
Abstract
:1. Introduction
2. European and Swiss Regulatory Context
2.1. Energy Communities
- Metering and billing is the responsibility of the ZEV, which is free to choose its own hardware and billing procedures, subject only to generic law requirements;
- The ZEV is in charge of the distribution of electricity inside the ZEV itself, and therefore ownership and operation are separated from the rest of the distribution grid.
2.2. Open Participation and Data Protection
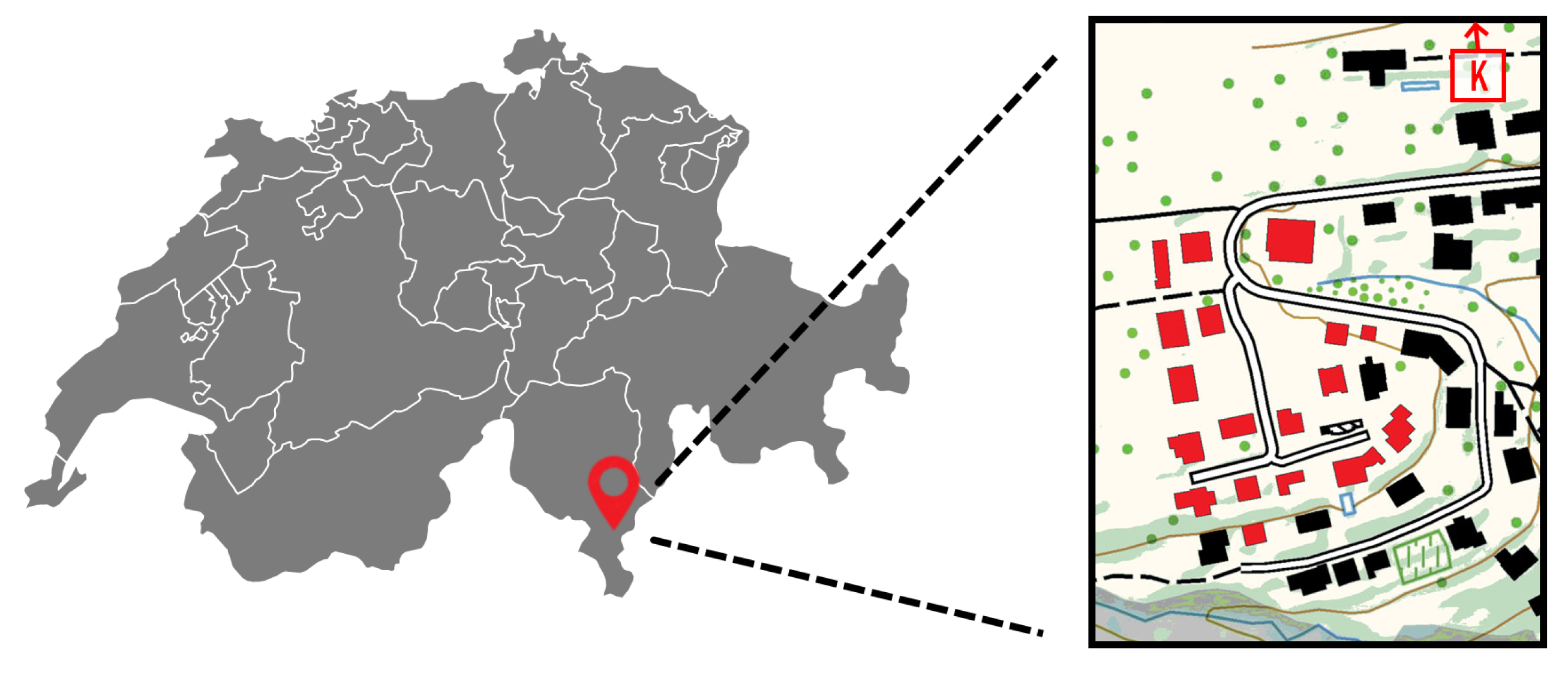
3. The LIC Energy Community
3.1. Motivation
- Evaluate the needs and requirements to the realization of LIC in a real environment. Provide recommendations on how to allow and facilitate the replicability and scalability of peer-to-peer SCCs.
- Assess blockchain as a decentralized billing management method introduced by the utility.
- Compare centralized vs. decentralized load management methods from the DSO point of view (grid costs), from both an energy consumption and economic standpoint.
- Help to assess the local flexibility potential and the different technical means in which it could be exploited.
- Evaluate the degree of knowledge, acceptance, and willingness to participate in a SCC among the community stakeholders.
3.2. Hardware
4. Blockchain-Based Market Implementation
Development and Deployment
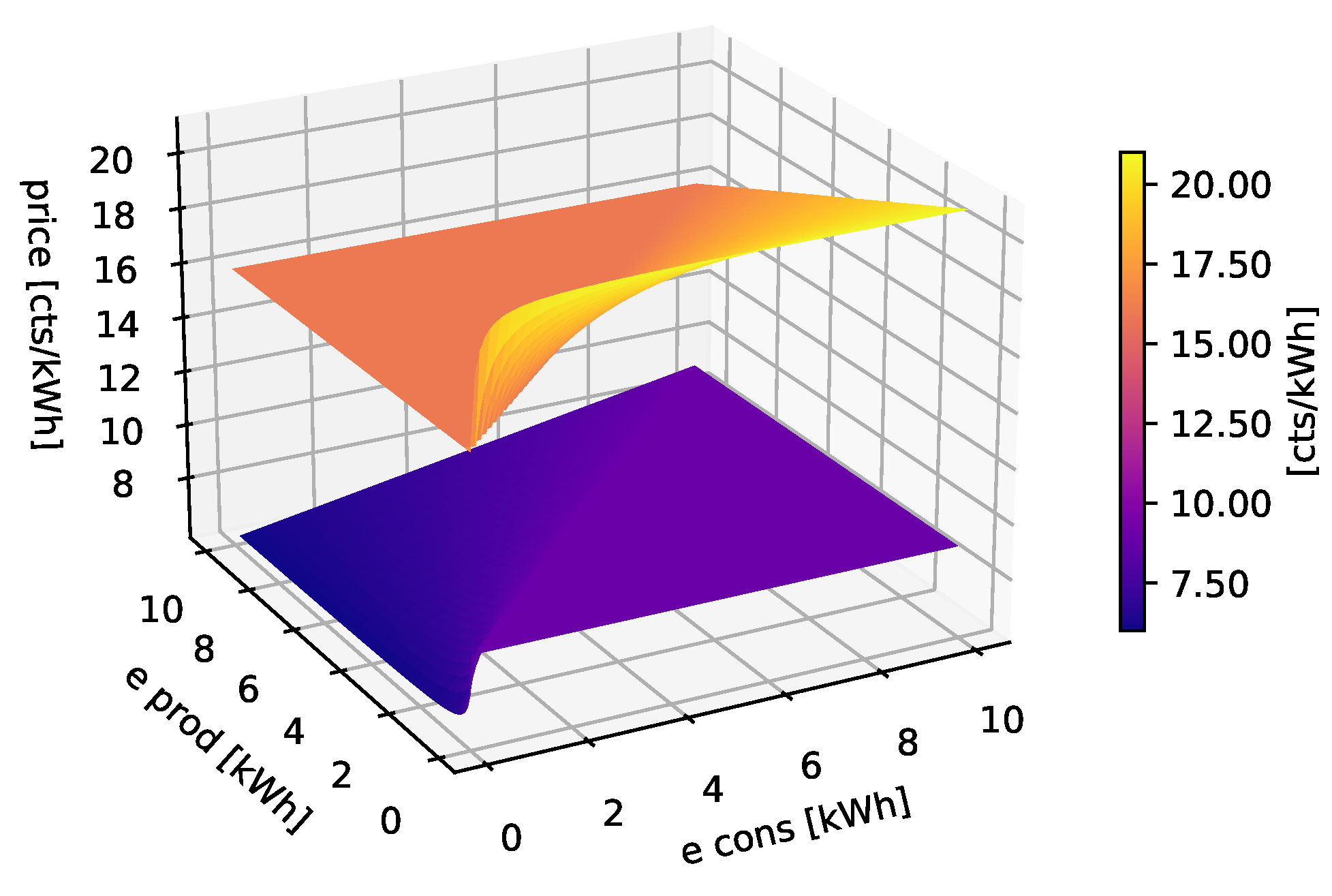
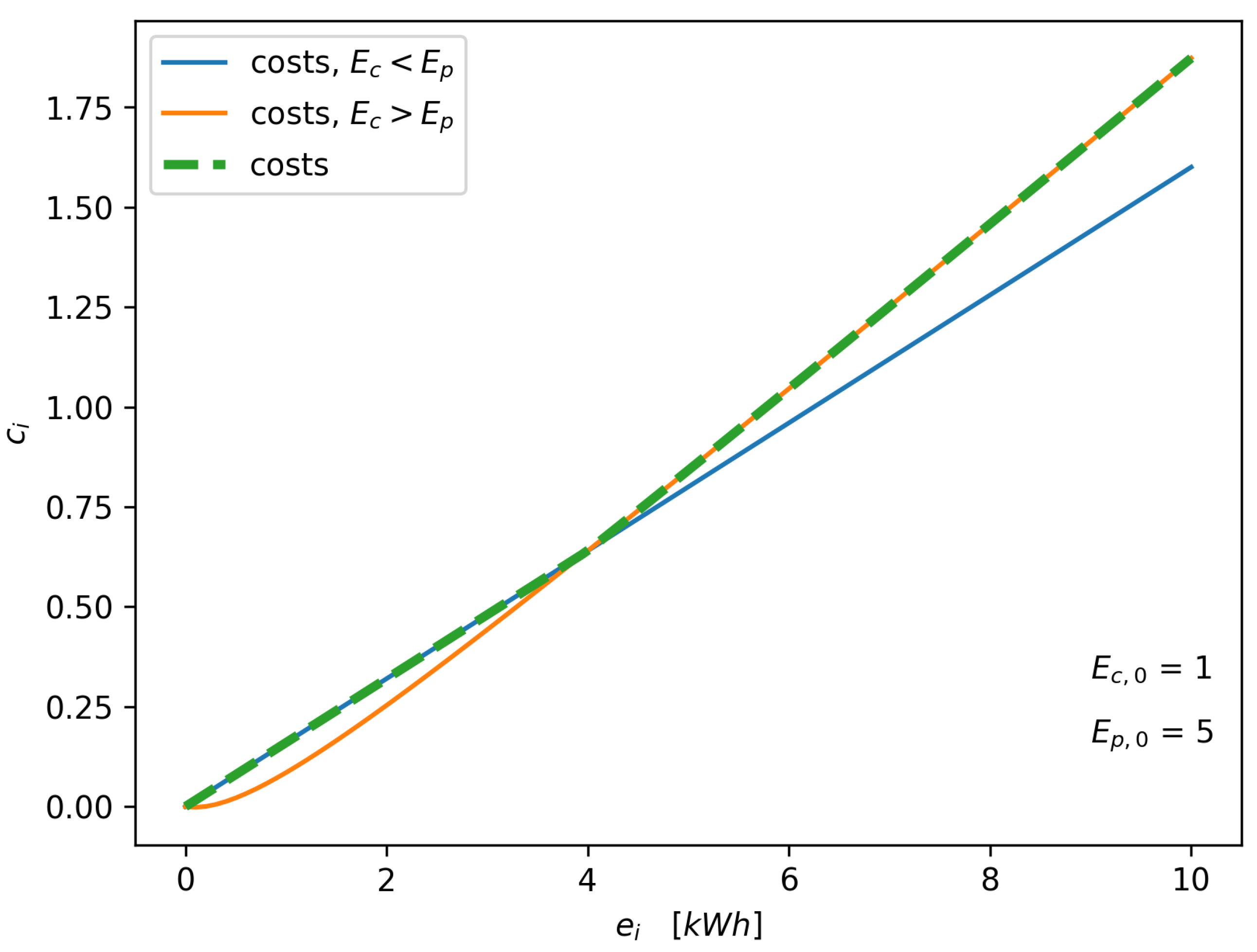
5. Electricity Market
- A fair redistribution of money among the market players, according to their contribution to the market’s intended outcome;
- Variance reduction in the aggregated power profile;
- Compatibility with the current legal energy billing framework, considering both produced and consumed energy in a given time slot;
- Promotion of self-consumption at the community level, while retaining the ability to steer the overall power profile at the will of a third party (administrator).
- The energy consumed from the external grid shall be paid for as if the consumer were not part of the community;
- The energy consumed from inside the community is paid for at a total price lower than the standard tariff of the energy supplier and DSO, with a discount proportional to the ratio of the total produced and consumed energy;
- The energy injected into the external grid shall be remunerated as if the consumer were not part of the community;
- The energy injected that is consumed inside the community is remunerated at a price higher than the standard tariff of the energy supplier, with a discount proportional to the ratio of the total consumed and produced energy;
- The self-consumed energy is equally split among the community members proportionally to their consumption and production;
- The instantaneous buying and selling prices are dynamic, but for a given time slot, they are the same for everyone;
- The difference between the community buying and selling prices covers the cost to set up, operate, and maintain the community infrastructure.
6. Full Anonymization of Participants
6.1. Homomorphic Encryption Protocol
- The admin updates the list of the participants to the aggregation round and broadcasts it. With this information, each agent will be able to know when it has received all the information broadcast by the other participants at each step, so that it knows when to proceed with the following step.
- Each participant decides on a “vote” to express, that is, a private integer value .
- Each participant selects a random integer value , and therefore a . The value , termed registration key, is broadcast.
- Each participant can reconstruct a list of keys, one for each participant i, with the following formula: . Notice that the calculation of requires the knowledge of the registration keys of all the other participants. Being calculated by repeated multiplication or inversion of elements of G, is still an element of G, and is therefore representable as . The above formula ensures structurally that .
- Each voter broadcasts their hashed vote .
- The aggregated value can be calculated by every participant or observer.
- Since , by product associativity and therefore the aggregated value can be retrieved by solving the discrete logarithm equation by exhaustive search.
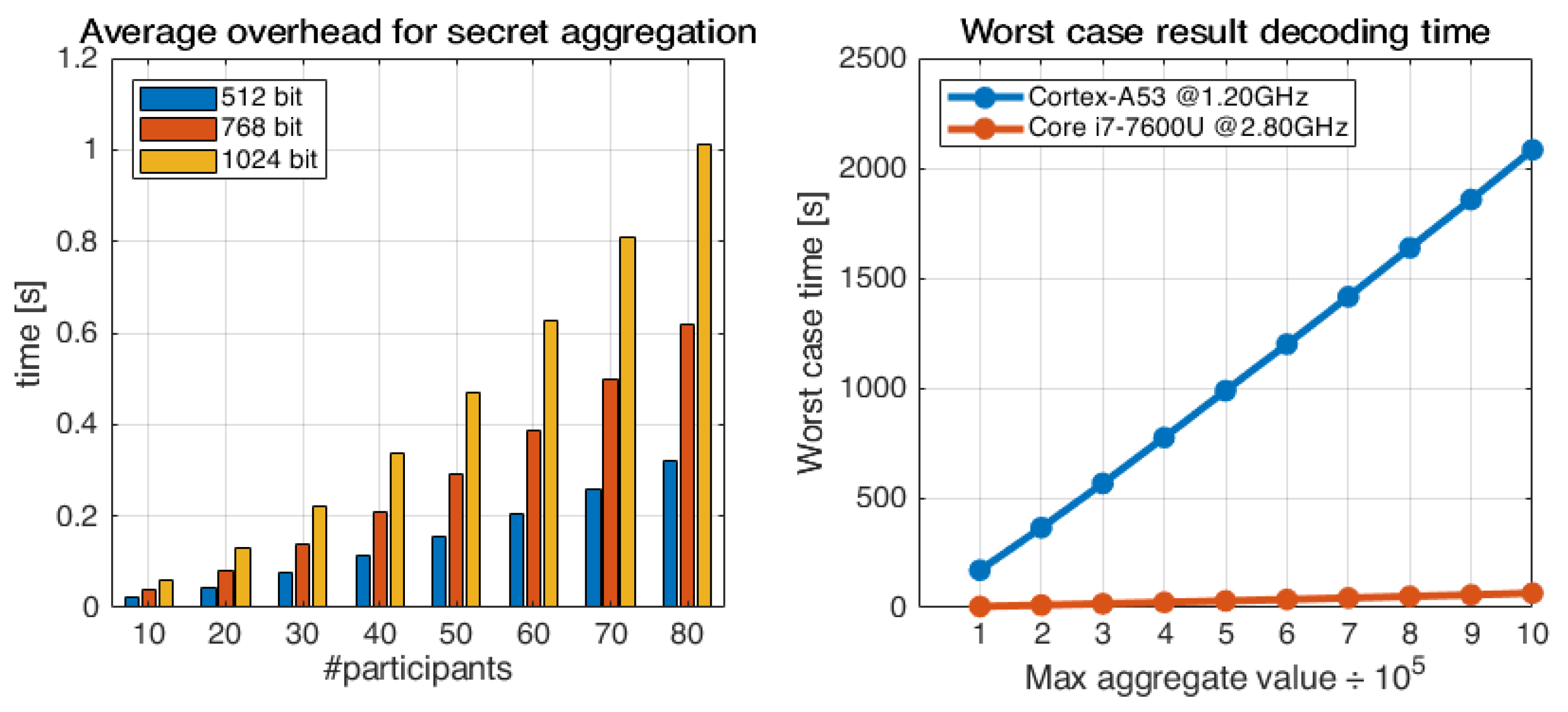
6.2. Overhead Analysis
6.3. Deployment
6.4. Applicability of the Protocol
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AEM | Azienda Elettrica di Massagno |
| AMM | Automated Market Making |
| BFT | Byzantine-Fault-Tolerant |
| CEC | Citizen Energy Community |
| CEP | Clean Energy Package |
| CPU | Central Processing Unit |
| DDH | Decisional Diffie–Hellman (assumption) |
| DSO | Distribution System Operator |
| EC | Energy Community |
| EU | European Union |
| FADP | Federal Act on Data Protection |
| GDPR | General Data Protection Regulation |
| IoT | Internet of Things |
| LEM | Local Energy Market |
| LIC | Lugaggia Innovation Community |
| POD | Point of Delivery |
| PoS | Proof of Stake |
| PV | Photovoltaic |
| REC | Renewable Energy Community |
| RES | Renewable Energy Sources |
| SCC | Self Consumption Community |
| V2G | Vehicle-to-Grid |
| VPN | Virtual Private Network |
| ZEV/RCP | Zusammenschluss zum Eigenverbrauch |
References
- Cosmos Network. Available online: https://cosmos.network/ (accessed on 25 July 2022.).
- Strepparava, D.; Nespoli, L.; Kapassa, E.; Touloupou, M.; Katelaris, L.; Medici, V. Deployment and analysis of a blockchain-based local energy market. Energy Rep. 2022, 8, 99–113. [Google Scholar] [CrossRef]
- Caramizaru, A.; Uihlein, A. Energy Communities: An Overview of Energy and Social Innovation, 2020; Publications Office of the European Union: Luxembourg, 2020. [Google Scholar] [CrossRef]
- Lowitzsch, J.; Hoicka, C.E.; van Tulder, F.J. Renewable energy communities under the 2019 European Clean Energy Package–Governance model for the energy clusters of the future? Renew. Sustain. Energy Rev. 2020, 122, 109489. [Google Scholar] [CrossRef]
- Dóci, G.; Vasileiadou, E.; Petersen, A.C. Exploring the transition potential of renewable energy communities. Futures 2015, 66, 85–95. [Google Scholar] [CrossRef] [Green Version]
- De Brauwer, C.P.S.; Cohen, J.J. Analysing the potential of citizen-financed community renewable energy to drive Europe’s low-carbon energy transition. Renew. Sustain. Energy Rev. 2020, 133, 110300. [Google Scholar] [CrossRef]
- Weckesser, T.; Dominković, D.F.; Blomgren, E.M.V.; Schledorn, A.; Madsen, H. Renewable Energy Communities: Optimal sizing and distribution grid impact of photo-voltaics and battery storage. Appl. Energy 2021, 301, 117408. [Google Scholar] [CrossRef]
- Liu, C.; Chau, K.T.; Wu, D.; Gao, S. Opportunities and Challenges of Vehicle-to-Home, Vehicle-to-Vehicle, and Vehicle-to-Grid Technologies. Proc. IEEE 2013, 101, 2409–2427. [Google Scholar] [CrossRef] [Green Version]
- Seyfang, G.; Haxeltine, A.; Hargreaves, T.; Longhurst, N. Energy and Communities in Transition: Towards a New Research Agenda on Agency and Civil Society in Sustainability Transitions; Technical Report 10-13, CSERGE Working Paper EDM; University of East Anglia, The Centre for Social and Economic Research on the Global Environment (CSERGE): Norwich, UK, 2010. [Google Scholar]
- Moncecchi, M.; Meneghello, S.; Merlo, M. A Game Theoretic Approach for Energy Sharing in the Italian Renewable Energy Communities. NATO Adv. Sci. Inst. Ser. E Appl. Sci. 2020, 10, 8166. [Google Scholar] [CrossRef]
- Wüstenhagen, R.; Wolsink, M.; Bürer, M.J. Social acceptance of renewable energy innovation: An introduction to the concept. Energy Policy 2007, 35, 2683–2691. [Google Scholar] [CrossRef] [Green Version]
- Energiegesetz 1998. Available online: https://fedlex.data.admin.ch/eli/cc/1999/27 (accessed on 25 July 2022.).
- Energiegesetz 2018. Available online: https://fedlex.data.admin.ch/eli/cc/2017/762 (accessed on 25 July 2022.).
- Satariano, A. What the GDPR, Europe’s Tough New Data Law, Means for You. The New York Times, 6 May 2018. [Google Scholar]
- Tankard, C. What the GDPR means for businesses. Netw. Secur. 2016, 2016, 5–8. [Google Scholar] [CrossRef]
- Schneider, B.; Bontempo, N.; Asprion, P.M.; Habbabeh, A. Storytelling and Gamification in E-Learning-An Empirical Study to Educate Swiss Microenterprises in Data Protection. In Proceedings of the Expanding Horizons: Business, Management and Technology for Better Society, Online, 20–22 May 2020. [Google Scholar]
- Borges, C.E.; Kapassa, E.; Touloupou, M.; Legarda Macón, J.; Casado-Mansilla, D. Blockchain application in P2P energy markets: Social and legal aspects. Connect. Sci. 2022, 31, 1066–1088. [Google Scholar] [CrossRef]
- Byzantine Fault Tolerance. Available online: https://en.wikipedia.org/wiki/Byzantine_fault (accessed on 25 July 2022.).
- Angeris, G.; Kao, H.T.; Chiang, R.; Noyes, C.; Chitra, T. An analysis of Uniswap markets. arXiv 2019, arXiv:1911.03380. [Google Scholar] [CrossRef]
- Angeris, G.; Chitra, T. Improved Price Oracles: Constant Function Market Makers. In Proceedings of the 2nd ACM Conference on Advances in Financial Technologies, New York, NY, USA, 21–23 October 2020; pp. 80–91. [Google Scholar] [CrossRef]
- Paccagnan, D.; Kamgarpour, M.; Gentile, B.; Parise, F.; Lygeros, J.; Paccagnan, D. Distributed computation of Nash Equilibria in aggregative games with coupling constraints. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016; pp. 6123–6128. [Google Scholar] [CrossRef]
- Belgioioso, G.; Grammatico, S. Projected-gradient algorithms for Generalized Equilibrium seeking in Aggregative Games are preconditioned Forward-Backward methods. In Proceedings of the 2018 European Control Conference (ECC), Limassol, Cyprus, 12–15 June 2018; pp. 2188–2193. [Google Scholar] [CrossRef] [Green Version]
- Buchmann, E.; Kessler, S.; Jochem, P.; Böhm, K. The Costs of Privacy in Local Energy Markets. In Proceedings of the 2013 IEEE 15th Conference on Business Informatics, Vienna, Austria, 15–18 July 2013; pp. 198–207. [Google Scholar] [CrossRef]
- Yi, X.; Paulet, R.; Bertino, E. Homomorphic Encryption. In Homomorphic Encryption and Applications; Yi, X., Paulet, R., Bertino, E., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 27–46. [Google Scholar] [CrossRef]
- Regueiro, C.; Seco, I.; de Diego, S.; Lage, O.; Etxebarria, L. Privacy-enhancing distributed protocol for data aggregation based on blockchain and homomorphic encryption. Inf. Process. Manag. 2021, 58, 102745. [Google Scholar] [CrossRef]
- McCorry, P.; Shahandashti, S.F.; Hao, F. A Smart Contract for Boardroom Voting with Maximum Voter Privacy. In Financial Cryptography and Data Security; Springer International Publishing: Cham, Switzerland, 2017; pp. 357–375. [Google Scholar] [CrossRef] [Green Version]
- Boneh, D. The Decision Diffie-Hellman problem. In Algorithmic Number Theory; Springer: Berlin/Heidelberg, Germany, 1998; pp. 48–63. [Google Scholar] [CrossRef]
- Naehrig, M.; Lauter, K.; Vaikuntanathan, V. Can homomorphic encryption be practical? In Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop, CCSW ’11, Chicago, IL, USA, 21 October 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 113–124. [Google Scholar] [CrossRef] [Green Version]
- Gruppi di Autoconsumatori di Energia Rinnovabile che Agiscono Collettivamente e ComunitÀ di Energia Rinnovabile; Technical Report; Gestore Servizi Energetici: Rome, Italy, 2020.


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Strepparava, D.; Rosato, F.; Nespoli, L.; Medici, V. Privacy and Auditability in the Local Energy Market of an Energy Community with Homomorphic Encryption. Energies 2022, 15, 5386. https://doi.org/10.3390/en15155386
Strepparava D, Rosato F, Nespoli L, Medici V. Privacy and Auditability in the Local Energy Market of an Energy Community with Homomorphic Encryption. Energies. 2022; 15(15):5386. https://doi.org/10.3390/en15155386
Chicago/Turabian StyleStrepparava, Davide, Federico Rosato, Lorenzo Nespoli, and Vasco Medici. 2022. "Privacy and Auditability in the Local Energy Market of an Energy Community with Homomorphic Encryption" Energies 15, no. 15: 5386. https://doi.org/10.3390/en15155386
APA StyleStrepparava, D., Rosato, F., Nespoli, L., & Medici, V. (2022). Privacy and Auditability in the Local Energy Market of an Energy Community with Homomorphic Encryption. Energies, 15(15), 5386. https://doi.org/10.3390/en15155386





