1. Introduction
The systems that comprise current energy networks and those inherited from old infrastructures exhibit considerable variety, resulting in a diverse collection of interfaces with varying features and security needs [
1]. Unfortunately, architectural standardizations do not enable varied system organizations depending on security needs. Implementing an integrated and effective energy network security strategy requires a standard vertical assessment method to manage emerging threats and vulnerabilities in applications and equipment [
2]. A strong belief should support this viewpoint among all stakeholders, noting that modern energy infrastructure systems are a possible target. As a result, a solid structure for deploying the appropriate resources should be standardized to limit the consequences of security breaches [
3]. There is no silver bullet for designing a security plan that completely protects the critical infrastructures, so innovative high-level solutions that effectively coordinate security perimeter deployment without direct human resources should be deployed.
The security management process in utilities is one of the most severe smart grid security concerns. System suppliers play an essential role in safeguarding intelligent grids. It is not easy to protect the power grid if products are developed without security capabilities or do not address security needs throughout the development cycle. Grid operators must evaluate the security of current systems, particularly ICS and future infrastructure installations. Furthermore, they must consider and plan new investments to improve the security posture, define security policies and procedures, train employees, and, last but not least, establish an information security management framework to ensure that all of these objectives are met and improved continuously. In this context, sophisticated security solutions are needed that can promote intelligent utilities that are not based entirely on the human experience.
Based on the above research gaps, the proposed approach aims to provide a comprehensive view of machine learning algorithms that can be applied to enhance the intelligence and capabilities of a data-driven security application. Based on this assumption, the critical contribution of the proposed method is to define the scope of our study by taking into account the nature and characteristics of various types of real-world intelligent grid data and the capabilities of various learning techniques. This can be done by exploring the applicability of machine learning-based solutions in different real-world application scenarios in the smart grid domain. We can thus expand the research area by highlighting and summarizing the potential research directions within the scope of our study, for intelligent data analysis and high-level cybersecurity services.
The current situation emphasizes the human aspect, experience, and expert opinion, using assistive technologies to analyze and manage risks and hazards. For the most remarkable results, there should be up-to-date threat information, incident reports, vulnerability warnings, and real-time security procedures. The above formulation leads to adopting automated solutions of Artificial Intelligence and, simultaneously, termination or minimization of human intervention in the empirical analysis of large volumes of data for the real-time detection of cyber threats or corresponding anomalies [
4]. This strategy focuses on reducing the risk of critical assets through a graded approach of automated security troubleshooting while ensuring the high availability of the infrastructure in question [
5].
It should be noted that the most significant innovation of the proposed approach is that it employs optimally spiking neural networks, Clonal Selection Algorithm (CSA) [
6], ensemble theory, and advanced Transfer Learning algorithms in an efficient hybrid method that has excellent generalizability to non-linearly separable data. Based on the proposed architecture, it is possible to generate nonlinear models that lead to linearity in larger areas using the suggested technique. Furthermore, in relation to other comparable procedures, the number of parameters that must be set is minimized. Similarly, for the classification of a new element in a class, the classification process is focused only on the unknown element’s resemblance to the algorithm and the most critical components of each class, significantly minimizing false positives.
In summary, advanced cybersecurity solutions that adapt to dynamic environments are required to intelligently protect critical energy infrastructure [
7]. The solutions in question should be interoperable and beyond the previous systems proposed in the relevant literature.
3. The Proposed Artificial Immune System
The proposed standardization follows the philosophy of AIS [
22,
23], where in a computationally intelligent way the functional and organizational behavior of the natural immune system is modeled [
24,
25], with the aim of its application in non-biological environments, such as the examined framework of digital security of energy infrastructures [
26,
27]. The primary inspiration principles simulated by the proposed system concern the capabilities of natural immune systems [
28,
29]:
distinguish normal from foreign cells;
decide whether a foreign cell is hazardous;
employ lymphocyte cloning and mutation to adapt to foreign cells in the body;
respond directly to foreign chemicals released by a pathogen that activates the immune system reaction (antigens) that the body has previously encountered, thanks to memory cells [
30]. Furthermore, a crucial aspect that provides inspiration and modeling involves the numerous levels, the in-depth scaling strategy, and the overlap of natural immune system defense achieved with the suggested Ensemble architecture [
31,
32] and Transfer Learning [
33,
34] techniques.
To better understand the proposed strategy and how it is scaled in depth, a simple example is given inspired by the biological function of the human body’s defense by its immune system. The proposed method and its properties are recreated using a model of how the skin of biological organisms works. The epidermis, nose hairs, and so on serve as the first line of defense, preventing diseases such as foreign particles, viruses, bacteria, and fungi from entering the body [
35]. The upper zone is aided and strengthened by feedback mechanisms such as fluid infusion from the body, saliva, sweat, tears, and so on, which assist and support the average defense by eliminating pathogens from the body or carrying digesting enzymes. When pathogens enter the cells of a living creature, individual immune cells called T-lymphocytes trigger an immunological response that translates into particular cytotoxic processes that kill infected cells, and so on [
23].
Combining natural and acquired immunization mimics the suggested system. The innate immune system employs molecular patterns to recognize infections from birth and does not adapt. This function is simulated with the initial training of the intelligent system on a set of possible attacks. On the other hand, the acquired immune system creates the body’s response to pathogens and the retrieval of the invaders’ history and how they can be treated [
36]. These functions are implemented through the Transfer Learning process. In an acquired way, i.e., through knowledge transfer, the system learns to deal with new attacks and patterns related to zero-day attacks. When a pathogen attempts to infiltrate the organism, the innate and acquired immune systems work together to combat the invasion [
28,
37]. This combination function inspired the Ensemble architecture of the proposed method, which offers better predictability and a more stable categorization model.
The proposed methodology uses an array of EINNs in an Ensemble architecture, which best integrates Transfer Learning techniques. The main categorizer is the Izhikevich Spiking Neural Networks [
38], which base their operation on the theory of dynamic systems. The Izhikevich model is a biological model that offers low computational complexity [
39,
40] like the Integrate-and-Fire models, as a neuron is treated as a homogeneous set of receiving and transmitting peaks, defined by the membrane’s internal potentials [
41,
42].
The Izhikevich Spiking Neural Network used, due to its dynamic configuration [
43,
44], can reproduce different spikes and different triggering behaviors of neurons. Specifically, the dynamics of the model were governed by two key variables [
45,
46]. The following equation describes the membrane potential [
38,
47]:
and the membrane return function described by the following equation:
where
υ represents the neuron’s membrane potential and
u is the membrane return variable that predicts a negative sign for
υ.
When the membrane potential reaches the threshold
θ, a peak is activated, and the reset of
θ and
u occurs. The peak activation function is described by the following equation:
and the return of the membrane after a peak is described by the following equation:
The parameters of the model are represented by the variables
a,
b,
c, and
d, where
a represents the rate of decomposition of the membrane potential,
b is the sensitivity of the membrane recovery, and c and d reset
υ and
u, respectively. Depending on the values of
α and
b, the neuron can be an integrator (
b < 0) or resonator (
b > 0). The parameters
c and
d do not affect the general behavior at a steady state, while on the contrary, they affect the model in the post-firing period. The parameter
υ is the membrane potential,
u the recovery current,
C the membrane capacitance,
υr the resting membrane potential, and
υt the instantaneous threshold [
48].
The change in synaptic weight is the difference between the arrival time
of a presynaptic peak and the time
of an action potential emitted by the neuron, described by a function
which determines how the time window works in the algorithm. Typical
W approaches are [
47,
49]:
where the parameters
and
specify the time sequence of the pre- and post-synaptic interval, while the parameters
and
specify the maximum values during the synaptic modification if the variables
are close to zero. The parameters
,
are adjusted according to the specific neuron being modeled, while window
W is usually time asymmetric, i.e.,
. It should be noted that the various options of the above parameters can lead to different inherent operating patterns, depending on the type of attacks that this model is called to resolve; depending on the configuration of these parameters, a wide variety of neural characteristics can be modeled [
50].
The Encoding by Resonant Burst (ERB) technique was used to match the actual values of the data set that models the problem of digital security of energy infrastructure. The ERB allows the fundamental values of the data set to be mapped to an explosion of peaks based on a set of receptive fields. Receptive fields feature a specified set of values and only take input to these values, allowing for continuous value encoding via a network of overlapping neurons with varying sensitivity profiles. This method’s rationale is based on the fact that each input variable is encoded independently of a set of one-dimensional receptive fields with comparable periods [
47,
49].
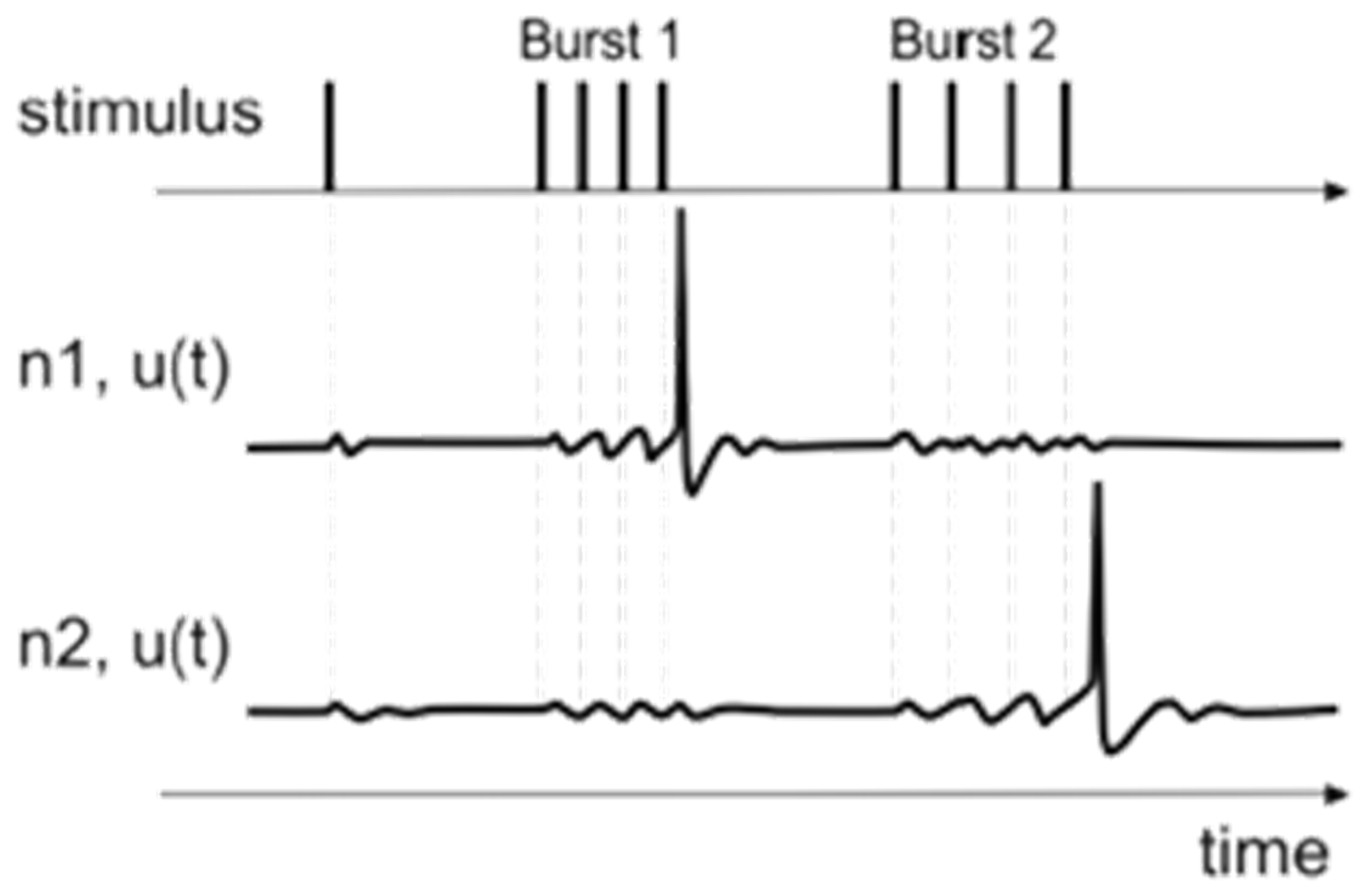
Given that determining the frequency of a peak explosion can determine the active neurons involved in it and, in particular, using the resonant effect: if the burst frequency is matched to the peak oscillations of the membrane potential of target neurons, a short burst of spikes can elicit a robust post-synaptic response. On the other hand, the same explosion would not affect the post-synaptic potential of the membrane if the explosion were not coordinated, as shown in the
Figure 1 below.
Based on this operating standard, sending a short peak explosion instead of a serial peak array increases the likelihood that at least one of these peaks could avoid synaptic transmission failure. The exact timing of the peaks during the explosion does not play an important role. On the contrary, the information on the interval between the peaks and their period is considered very important. In particular, the shorter the interspike interval, the more likely the synaptic transmission is to be activated and, conversely, the longer this interval is, the more likely the transmission is to be completed. In the case of bursts from continuous dense peaks, these are taken as a combined function that activates the post-synaptic potential.
This function is enhanced because each peak causes an oscillation of the membrane potential, which leads to a fluctuation of the distance to the threshold and hence an instability of the probability of contraction. It should be noted that all peaks included in an explosion have the same or about the same period. So, suppose the interval between peaks is relatively short and the period is similar. In that case, the second peak reached during the increasing phase of the oscillation will increase the oscillation amplitude even further as the peak effects work cumulatively, thus achieving the synaptic transmission. If the second peak is reached during the oscillation drop, then, in this case, the peaks substantially cancel each other out. The same phenomenon is observed for inhibitory synapses.
Thus, based on the notion that models from the same class exhibit the same or comparable behavior and, as a result, produce a similar firing rate at a neuron’s output, whereas, on the contrary, models from a different class behave differently and thus produce a different firing rate, the proposed Izhikevich Neural Network is used to intelligently identify suspicious patterns associated with digital threats. In particular, each time an input signal changes, the network response also changes, creating a different trigger rate. The number of peaks created in a time
T is used to compute this firing rate. When a neuron gets an input signal, it is excited for a while
Tms and triggers when a certain peak or series of peaks reaches a given threshold of its potential membrane, resulting in an action potential [
38,
51].
More specifically, D is a set of incoming patterns where k = 1,… K is the class belonging to . Initially, each input pattern is converted to an input signal I, based on the ERB procedure. In this example, the learning process is to modify the model’s synaptic weights so that the different firing rate of each neuron is a class k, duplicating the behavior indicated in the hypothesis. As a result, to address the threat identification problem, the current input I that stimulates the model must be calculated.
Assuming that each characteristic input pattern
xi corresponds to the presynaptic potential of each receptive field, the input current
I that stimulates the neuron is computed as
where
w∈ Rn is the sum of the synaptic weights of the model. Stream of input in the approach,
I is utilized to simulate the model during
Tms. Instead of using the serial peak array produced by the model to perform the categorization, the firing rate of each neuron is calculated as follows [
47,
49]:
where
Nsp is the set of peaks in the time window
T. It is also necessary to calculate each category’s average
AFR firing rates based on the firing rates produced by each input. In this view, the learning process entails determining the mode’s synaptic weights so that each category has a different average firing rate
k.
To obtain the desired behavior at the model’s output, the model’s synaptic weights, which are directly tied to the incoming patterns, must be adjusted. This calculation is based on the biologically inspired heuristic CSA algorithm. The immune system’s reaction to the arrival of a pathogen inspires CSA. It establishes that only lymphocytes that recognize the pathogen better are chosen to be cloned. The goal of the clone selection method is to produce a large number of antibodies that are highly compatible with specific antigens. Antibodies are thought of as possible solutions to CSA. In contrast, antigens are thought of as test data, and the degree of matching between an antibody and an antigen signifies the suitability or quality of the solution. The goal is to create an initial population, apply it to the data set and use it repeatedly to improve the quality of solutions in the population. Another essential feature of this algorithm is the ability to distinguish it to avoid entrapment in local minima. At the same time, the evolution of the solution population is produced having the lowest computational costs.
In the proposed Izhikevich Neural Network, the use of CSA is used to calculate the synaptic weights, which can achieve the minimum categorization error of the model. The following function fitness function is calculated below [
52]:
where
w are the model synapses,
D is a set of input patterns, and
P (
w,
D) is the function that calculates the model’s classification rate. The calculation function of the classification rate is calculated as follows:
where
is the set of correctly categorized standards and
is the number of standards tested. The general methodology followed is described below [
6,
23,
53,
54]:
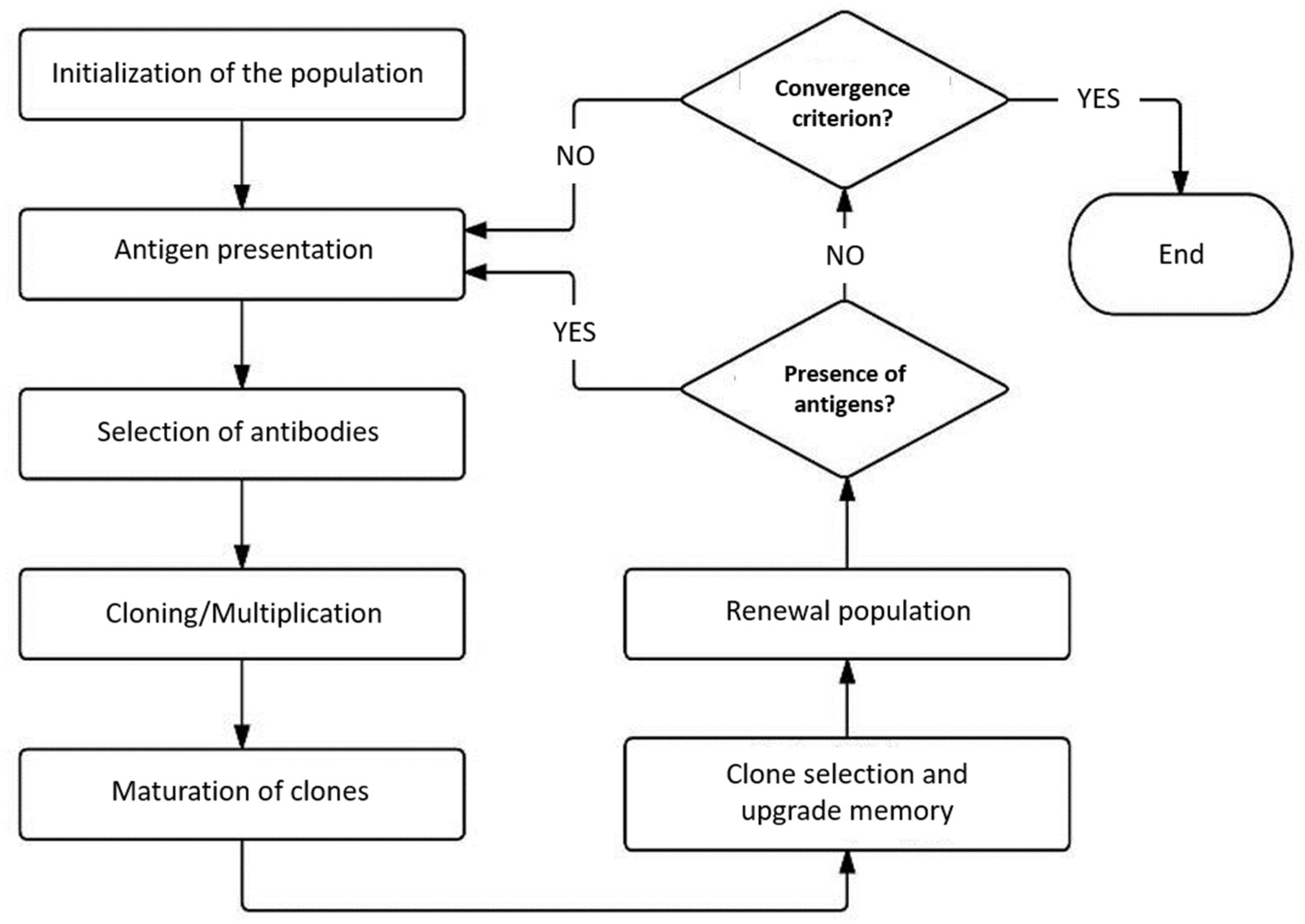
Population initialization: For each antibody a random sequence of symbols is selected and assigned to it . The set is also defined.
Antigen presentation: A random antigen is selected and delivered to the population while the binding function f for each antibody in the population is determined. As a result, the following set is obtained, which indicates the extent to which each antibody in the population binds to the antigen. The antigen is removed from , so .
Selection of antibodies: Based on the data of set V, the antibodies that indicate the best binding quality are selected and constitute the set .
Cloning/amplification: Based on its binding quality to the antigen, each antibody in set B is cloned, with each antibody giving more clones as its quality improves. The generated clones are stored in a new set C.
Clone maturation: Each element of the set C changes at a rate which is determined by the clone’s degree of binding to the antigen. The higher the binding quality, the lower the mutation rate, ensuring that no irreversible alterations to the antibody occur. The set is made up of mutant clones.
Clone selection and memory refresh: The function f is applied to each set element and the set is obtained, which contains the binding quality of each mutant clone, . Based on the best clones are selected which constitute the set . Imaging K is then applied to the antigen to give the set of of the memory antibodies that could be replaced. Based on the algorithm’s memory renewal policy, a final set of cells are obtained such that . The memory cells of the set will be replaced by other selected cells if and only if these cells demonstrate a higher quality of binding, resulting in the condition .
Population renewal: To maintain population diversity, either cells are selected from the set and brought into the population to take the place of others, or worse cells are selected from the population P and replaced with entirely new ones.
Termination condition: If
, the algorithmic approach is then repeated, beginning with the second step of antigen presentation. Otherwise, a condition of memory antibody
M convergence with set
G antigens is verified. In the event of a failed convergence, then
_ and the algorithm is repeated from the second step of the antigen presentation, while otherwise
, at which point the algorithm terminates and completes a generation of evolution [
55,
56].
The schematic representation of CSA is shown in the
Figure 2 below [
51,
54].
The suggested CSA algorithm is a biologically inspired technique for multimodal search and learning. Their coding schemes and evaluation functions are identical to those of other approaches, such as genetic algorithms. Nonetheless, the evolutionary search methods vary in inspiration and evolutionary step sequencing, which creates significant transparency of the process and various configuration options. Furthermore, the CSA method is highly parallel and has excellent tractability regarding computing cost and resources. In any event, it should be noted that the CSA can achieve a diversified range of local optima solutions without being trapped in pointless retrospectives. The other strategies tend to polarize the whole population toward the best candidate answer, while in the CSA algorithm, convergence is implemented in a much more specific solution [
55,
57].
The suggested system’s major innovation is implementing the Transfer Learning [
34] process as a simulation of the acquired immune system which is the creation of the body’s exposure to infections and the retrieval of invasion history and treatment options. These functions, which are gained in an acquired way, i.e., by transferring knowledge, perform a process of dealing with new attacks and patterns related to zero-day attacks. To be more specific, after successfully training the model, it is essential to determine the firing rate produced by the trained neuron to identify the category to which an unknown input pattern x belongs. This rate is compared to the category’s average firing rate. The slightest difference between the firing rate and the mean firing rate determines the class of an unknown pattern. The following equation compares the firing rate and the regular mean firing rates [
49,
58]:
where
fr is the trigger rate of a neuron for an incoming standard
x.
To strengthen the acquired immune system and, in particular the memory cells that will provide acquired knowledge to the system, an algorithmic addition was added to step 6 of the CSA [
56], which strengthens the memory cells with additional knowledge, so that they can provide Transfer Learning to the general system. In particular, the unknown, incorrectly classified samples follow a process of identification through an unsupervised identification technique. Essentially, the centers are calculated, and the unknown points are assigned to centers of a vector space using the Euclidean distance. This process, based on the general fuzzy c-means algorithm, is repeated until the centers are stabilized. In contrast, the algorithm directly constrains the membership degree function for each point. The process is described by the following mathematical relation [
59,
60]:
where
p is the number of classes,
k is the number of data points,
xi is the
i-th point, and
μj(
xi) is the function that returns
x member degree in the
j-th class,
i is a data vector where
i = 1, 2,
k. Thus, the sum of the membership points for each point in all classes should be 1. The following equation is used to calculate the value of a new cluster center:
where
cj is the center of the
j-th cluster with (
j = 1, 2…
p),
xi is the
i-th point, and
m is the ambiguity parameter. The amplitude of
m was calculated between [1.25, 2], based on the trial-and-error method.
So, for the unknown samples, e.g., zero-day attacks that are difficult to categorize, we can assign them a new target based on their new position and the new condition of the samples in space. In the first iteration of the method, we set the class centers to arbitrary values, usually zero, and calculate the membership points of the points for them. First, to determine the distance of each unknown sample
xi from the center of the correct class
c1…j, the Euclidean distance is calculated using the following equation [
61]:
where
dji is the distance of
xi from the center of the class
cj. The degree of membership of a point in a class is then calculated by the following equation:
where
dki is the distance of
xi from the center of the class
ck.
Based on the memory refresh policy as described in step 6 of the CSA algorithm [
54,
55], a new set of memory cells emerges that are better than their original categorization and enhance the algorithm’s better connection quality, transferring knowledge from the parallel unsupervised learning process. More specifically, the memory cells are represented by the
sets, which are subsets of
.
During the operation of the algorithm,
is a dynamic slider containing the most recent
m examples of the data stream containing the
Minnate memory cells:
retains all the other memory cells that have been created, and unlike
, it is not even a continuous part of the data stream but a set of static points
p:
Combined memory
is the union of both memories with size
m + p:
Each set includes an EINN classifier for each
. Specifically,
. The EINN function assigns a label to a given point
x based on a set
such that [
31,
32,
33,
47]:
where
is the Euclidean Distance between two points and
returns the set
k of the nearest classes of
x to
Z. With this tactic, we have a constant updating of the model by transferring knowledge between memory cells. Furthermore, the combined action of the innate and acquired immune systems in dealing with the invasion effectively generates the Ensemble architecture, which has been demonstrated to give superior predictability and a more stable categorization model due to the system’s robust and predictable behavior.
4. Dataset and Results
Modern power grid threats include undermining actuator or sensor operations in the physical layer, attacks on device connections in the data link layer, and more specialized efforts to undermine particular control systems in the SCADA layer. Consequently, optimal energy grid security needs real-time analysis of large-scale data produced in the networks by millions of sensors and smart meters [
62]. For the validation of the methodology as well as the individual experiments in the preparation of the final parameters of the model, which were selected mainly by trial and error, a highly complex data set was used that fully reflects the dynamics of the proposed system.
The Electric Power and Intelligent Control (EPIC) [
63,
64] dataset was chosen specifically because it best represents the routine operation of all active media utilized in modern power grids. EPIC is a power grid testbed that combines the four primary stages of energy networks: generation, transmission, microgrid, and smart home. It is available to researchers to run experiments to test the effectiveness of novel cyber defensive measures.
Its architecture includes segmented communications networks, wired and wireless communications systems, distributed dynamic control mechanisms, the interconnection between other test centers, and full access to control automation through Programmable Logic Controllers (PLCs) and Human Machine Interfaces (HM).
In particular, the set includes the normal operation of the network. It includes examples of advanced cyber-attacks that evolved through isolation tactics of properly modelled local and global vulnerabilities and their complicated user interface, resulting in 12 separate high-complexity scenarios. From these scenarios, network traffic log data, flagged network transactions during normal operation, and transactions during various cyber-attacks were collected. Included also are data on abnormalities detected during malicious operation of the equipment and data identifying statistical information that can determine how a network operates.
Power outages were the focus of the experimental process to make the research much more specific. In particular, the scenarios investigate whether the intruder operates the circuit breakers at each of the different stages of the energy infrastructure, where one or more circuit breakers can be closed or opened. In the second level, the intruder manipulates the power settings at multiple stages by adjusting the maximum power settings at various power sources.
In the first example, each step of the energy network (Generation, Transmission, Micro-grid, and Smart Home) has its own PLC controller and communication channels between SCADA, DCS, EMS, and PLC controllers [
19]. It must be noted that there is not another comparable model in the literature to use as a benchmark. Consequently, to avoid bias or incorrect impressions, we present the performance of the proposed model without making any comparisons with any other alternative models except that shown in the tables below.
In addition, to evaluate and validate the results regardless of the accuracy of the inference and the generalization performance, the following tables list the patterns between the expected and trained prediction results by counting how many results are categorized correctly into each class. Because the training data of the dataset under consideration are skewed, the accuracy of the inference cannot guarantee a likelihood. The ratio of correct to incorrect results was evaluated to validate the inference performance based on the appropriate performance metrics. Specifically, the inference performance was evaluated based on the inference accuracy, precision, recall, F-score and AUC (Area Under the Curve).
The four modeled cases are:
Intrusion into the communication network and conversion of control commands issued by PLC controllers. This is a binary classification problem in which the results of the proposed system in comparison with respective machine learning techniques (Support Vector Machines—SVM, k-Nearest Neighbors—k-NN, and Random Forest—RF) are presented. The results are presented in
Table 1 and respectively
Figure 3 below:
- 2.
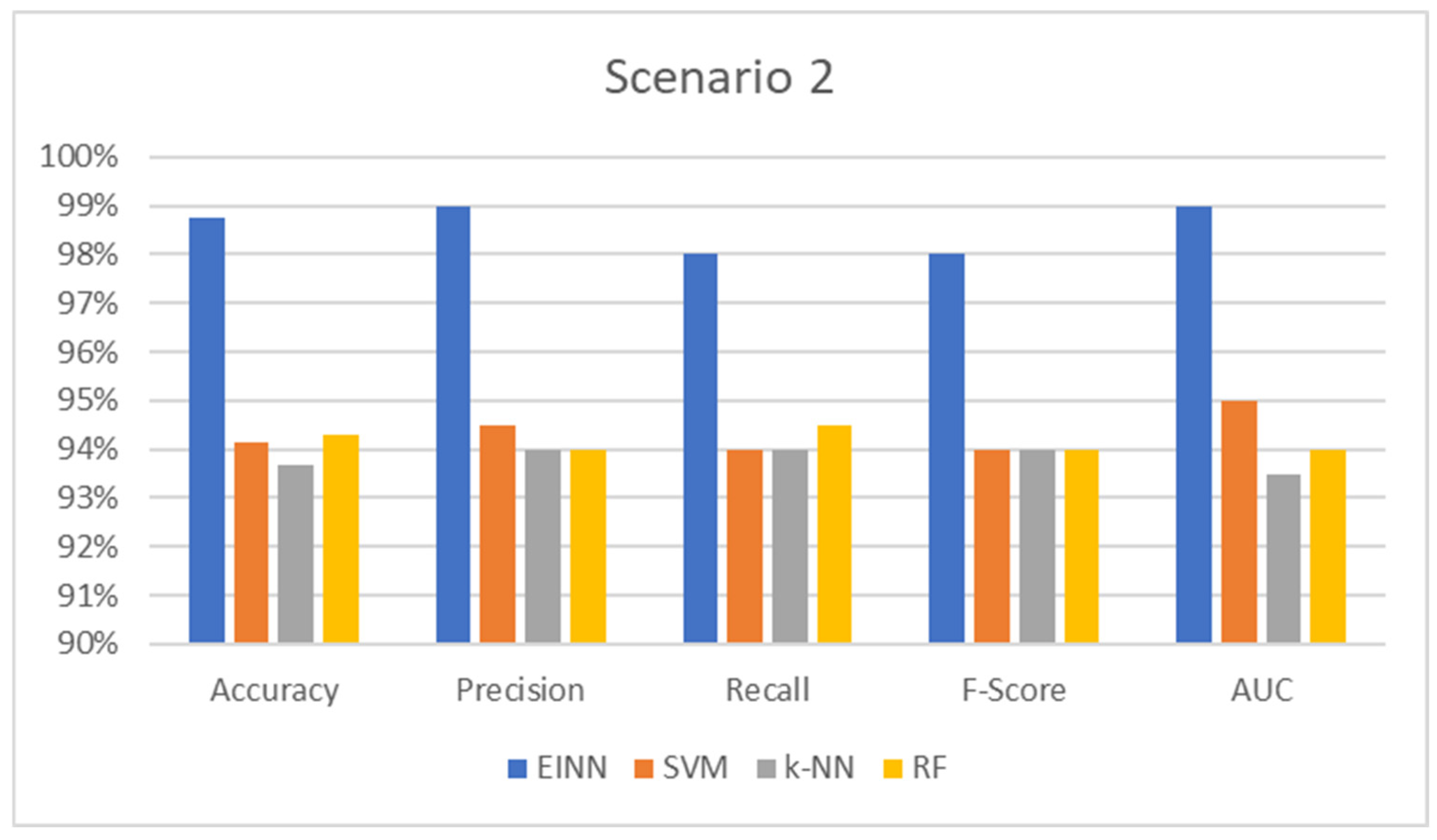
Targeting PLC controllers to execute a DDoS attack to make them inactive. This is a binary classification problem for which the results are presented in
Table 2 and respectively
Figure 4 below:
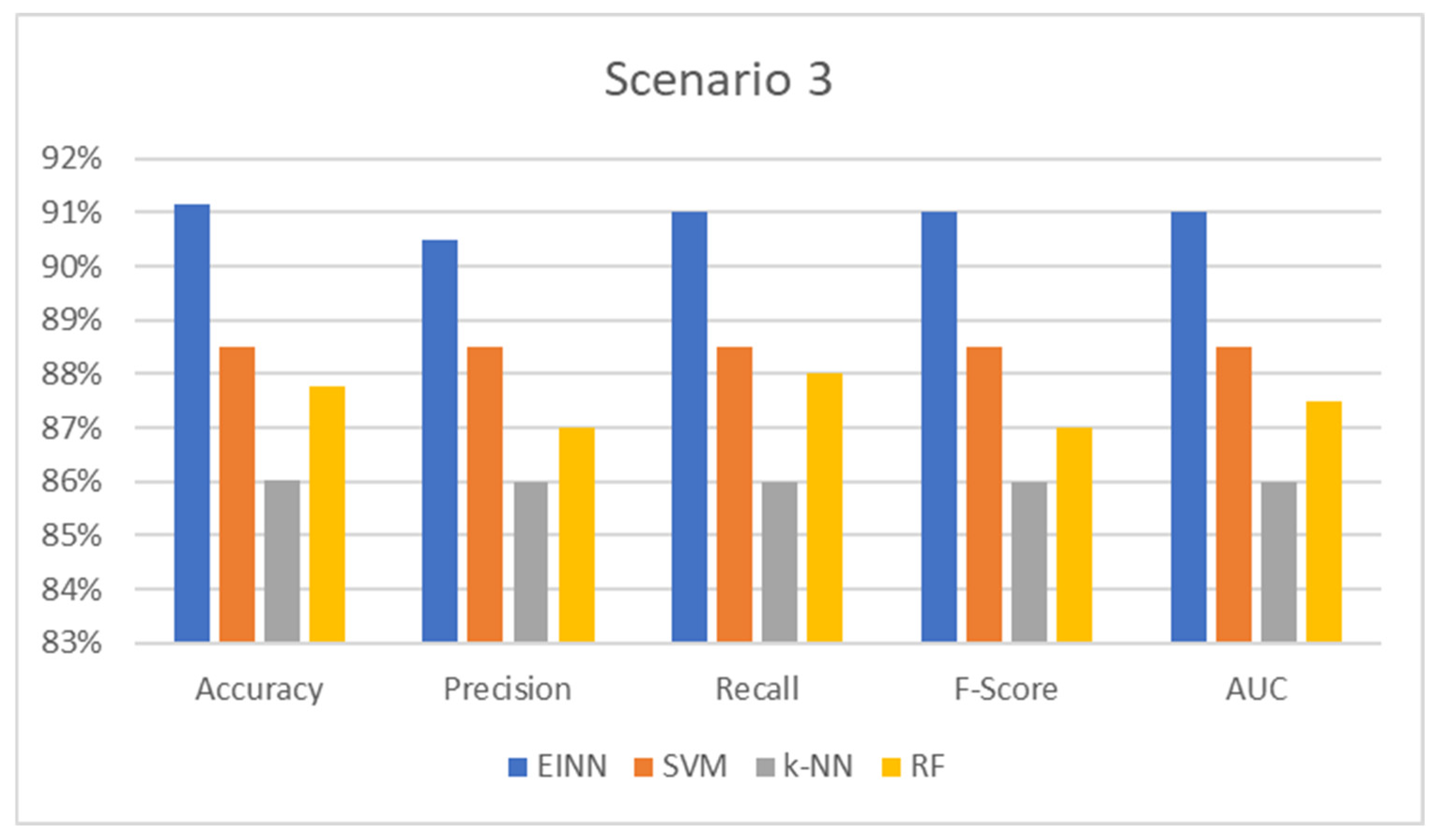
- 3.
Targeting any of the PLC controllers to execute general vulnerability exploitation attacks to make them inactive. This is a binary classification problem where anomalies are detected. The results are presented in
Table 3 and respectively
Figure 5 below:
- 4.
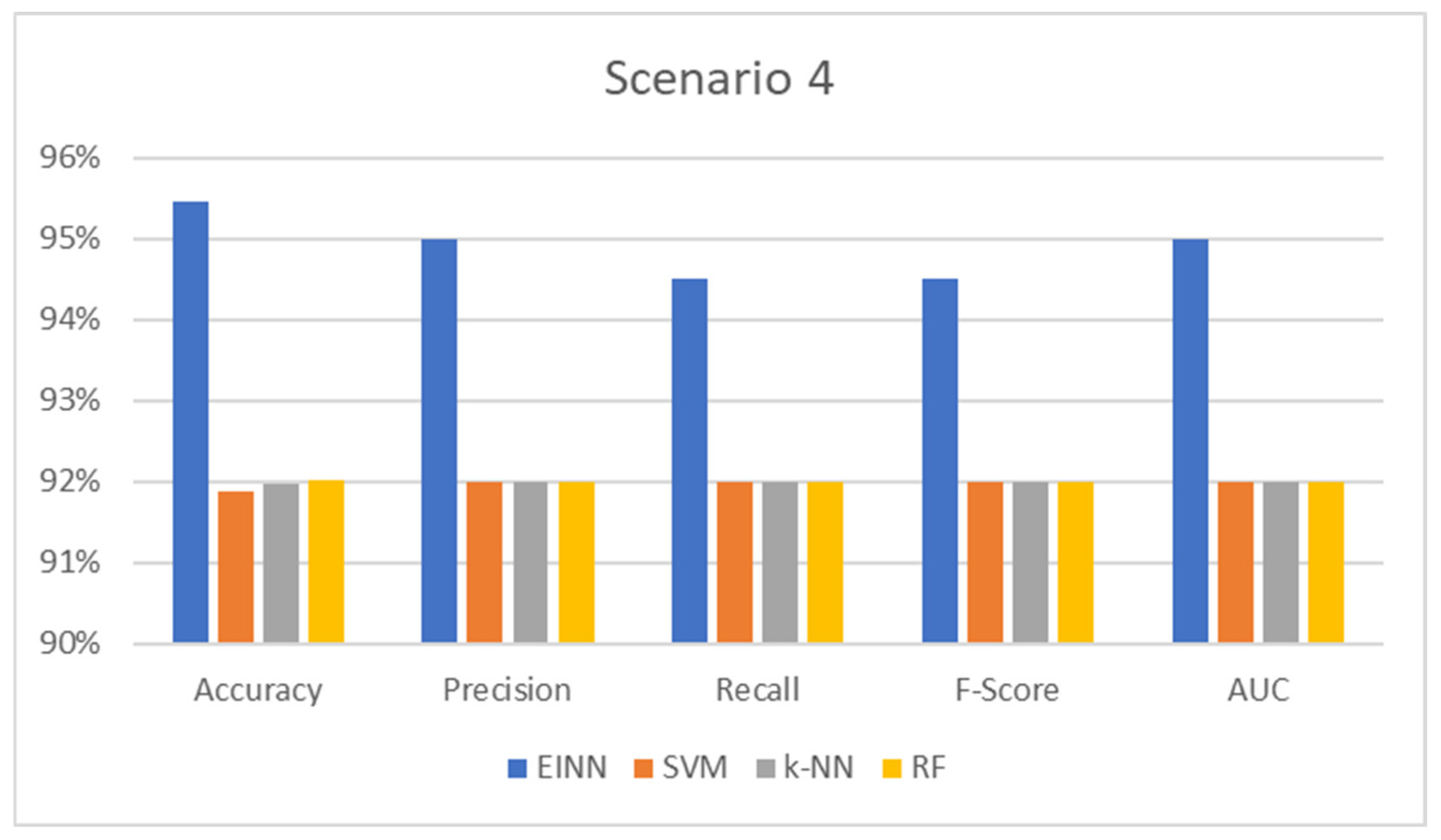
To undertake power outage attacks, enter the SCADA workstation and change the various settings to control different actuators, circuit breakers, and other regions of the smart grid. Anomalies are found in this binary classification task.
Table 4 and respectively
Figure 6 below summarizes the findings:
In the second case of the experimental process, the intruder handles the power settings at different stages to achieve a power outage. The three cases modeled along with the system results are as follows:
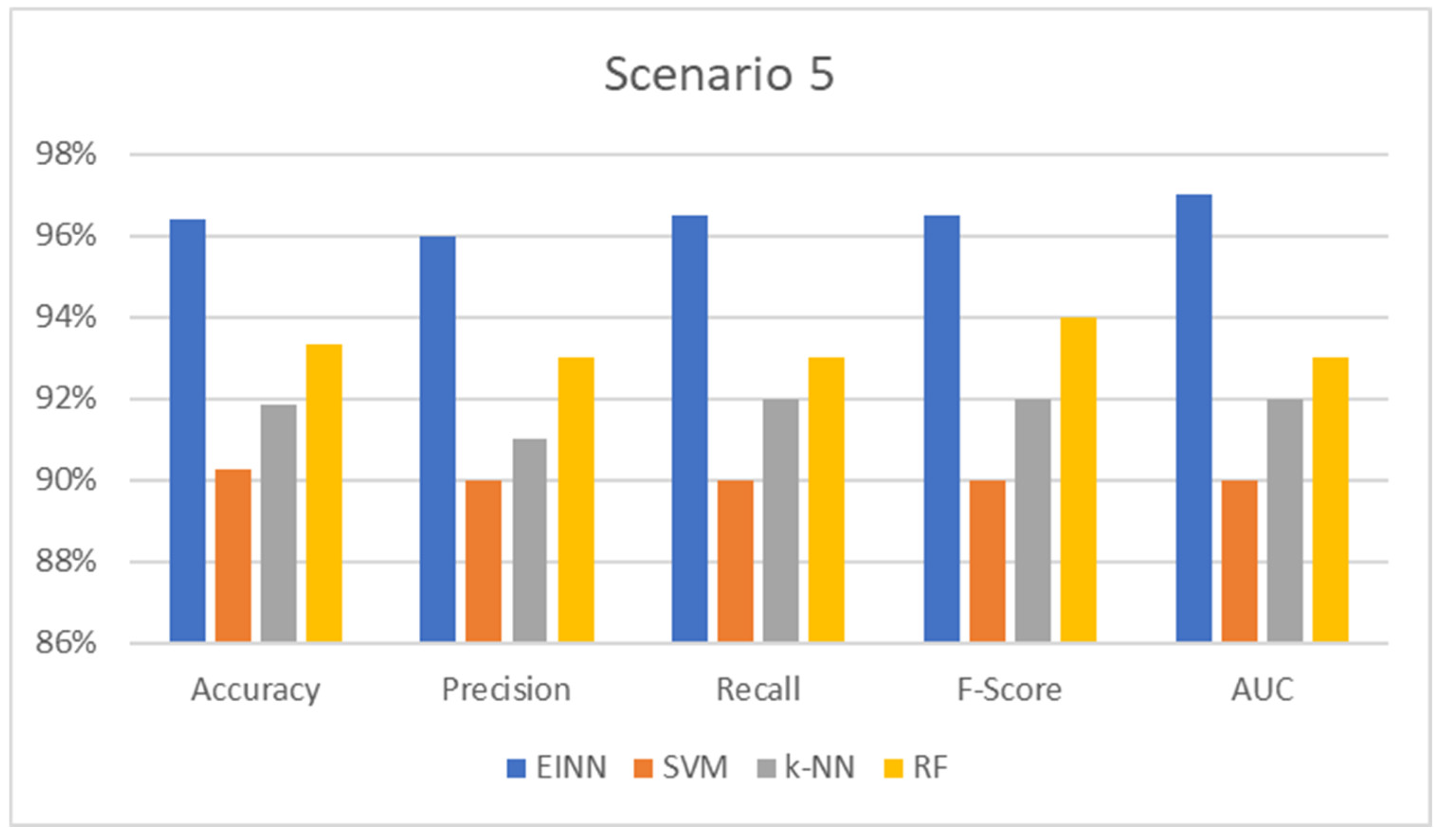
Adding malicious code to the PLC that sends Variable Speed Drives (VSDs) at faster speeds and more extraordinary power upsets the power balance and crashes the system. This is a binary classification problem where anomalies are detected. The results are presented in
Table 5 and respectively
Figure 7 below:
- 2.
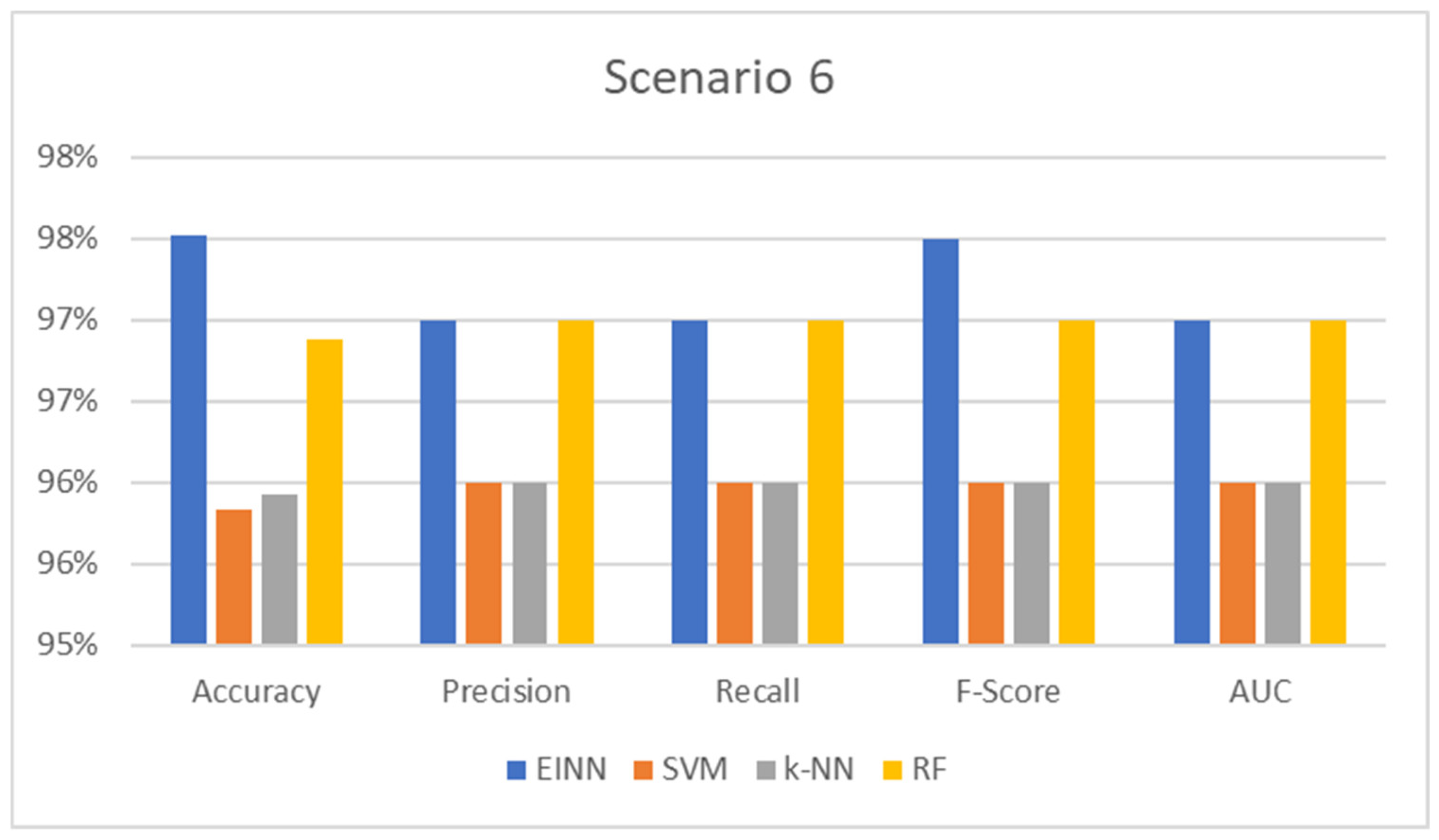
Through changes in the SCADA application settings, the maximum power of the two-way inverter in the micro-grid is set higher than the maximum load demand, which causes power imbalance and system shutdown. This is a binary classification problem where anomalies are detected. The results are presented in
Table 6 and respectively
Figure 8 below:
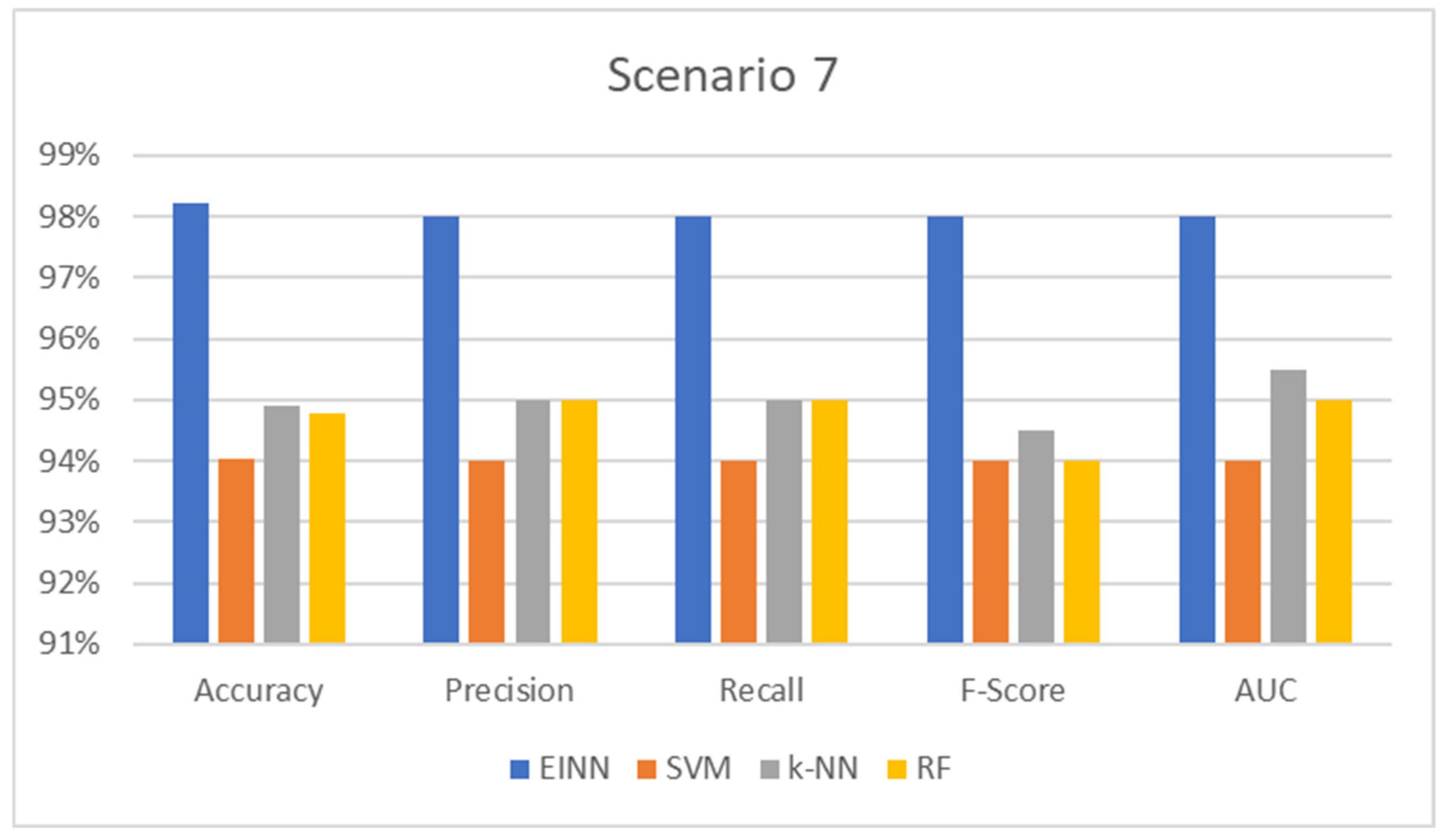
- 3.
The speed directives supplied to the VSD by the PLCs are modified by changing the communication channel, causing the VSD to function faster than required, affecting the power balance and shutting down the system. Anomalies are found in this binary classification task.
Table 7 and respectively
Figure 9 below summarizes the findings:
The accuracy measure is the ratio of the total number of inferences to the total number of findings that match the predicted value. It is the most frequent and well-known statistic for demonstrating inference performance on the trained model. In all cases, the proposed system prevails up to 5% of the compared models, which means that the model has high generalization performance, producing a deficient error for unseen input data.
In addition, precision is the metric used to show the likelihood of the inference and evaluates the ratio of truly correct results. For example, in power outage detection, an inaccurate result is not allowed; however, it is difficult to achieve completely accurate results. An index is needed to indicate how many of the results are correct; precision is used for this. The precision shows how many results were correct. In every instance, the suggested approach outperforms competing models by 0.3 to 0.5 percentage points.
In addition, the recall is the metric used to show the ratio of correct data against how many errors occur in the target data. In the case of this consideration, it shows the number of correct detections among all observations. In all circumstances, the suggested system outperforms the competing models by up to 0.5 points.
F-score achieving 100% for both precision and recall at the same time is extremely difficult for a real-world model like this. The harmonic mean (F-score) applies both the precision and recall to fully evaluate the compared models. So, regarding the F-score metric, the proposed model produces good reports up to 0.6 points which translates as a way to efficiently estimate the generalization performance progress in the evaluation process.
Finally, AUC represents the degree or measure of separability. It tells how much the model is capable of distinguishing between classes. The higher the AUC, the better the model predicts the area of class separations. As proven by the results, the proposed model achieves the highest AUC, which means that the model can distinguish between normal and abnormal events.
In terms of addressing the examined digital security problem, the proven reliability of the recommended architecture is attributable to a combination of elements. Because of the Ensemble nature, which includes clustering, it can discover and keep crucial features connected to complex patterns that grow and contribute to the timely and accurate prediction of scenarios. The Ensemble technique substantially improves data processing methodology by detecting the intricate relationships that explain them and by capturing the minute differences that separate them. Furthermore, because the overall behavior of the numerous models is less noisy than a comparable individual, the suggested system provides a better prediction and a more stable classification model [
31].
Furthermore, because of the nature of the problem under discussion, which evolves in real-time, data transfer is accomplished using the transfer learning architecture [
34] while considering correlations and interdependencies that might be present in the data flow sequence. The problem with using the shared learning rate of the transfer learning architecture for all parameters and all phases of the learning process adds significantly to the attainment of the above and, in general, to the speed of generalization and convergence.
Another important finding that supports the transfer learning approach is that just the current control batch’s statistics are utilized, resulting in more effective smoothing as the learned parameters do not incorporate data from multiple-use parameters. A non-intelligent program would gather current batch data at all phases of the internal loop learning update, delaying or stopping optimization. A false assumption causes beginning to model and update feature distributions to be similar. Current statistics may be provided with all network internal loop updates—but with a false assumption. Uses should keep statistics across stages and read optimization parameters for each internal loop iteration step by step.
The suggested system achieved the highest accuracy rates when data streams were reviewed rather than a single data set, confirming the high convergence rate. Another critical factor in selecting this architecture was because EINNs take advantage of all traditional machine learning algorithms while avoiding issues such as delayed convergence, fixation at local extremes, and so on [
49,
51]. Finally, the best combination of cellular memory levels given by this method demonstrated the ability to uncover hidden correlations or patterns in data while minimizing errors and enhancing categorization accuracy [
54,
56].
In this way, the proposed system fully automates the strategic security planning of energy networks with computational intelligence methods. It allows the complete control of the digital strategies of the potential infrastructure that frames it, thus contributing to timely and valid decision-making during cyber-attacks.
5. Conclusions
In the present work, an advanced standard for securing energy infrastructure was presented, which automates operational cyber security. The model uses advanced computational intelligence methods in a hybrid system first introduced in the literature. It is an AIS that models the function of the natural immune system, using an Ensemble array of Izhikevich Neural Networks optimized with CSA, which is inspired by how the immune system reacts to the appearance of a pathogen.
Similar nature-inspired optimization methods, as well as more complex optimization methods based on complex mathematical models, have been proposed in the literature to solve practical applications or to solve specialized problems. However, the proposed architecture incorporates optimally advanced Transfer Learning methodologies to fully automate the strategic security planning of energy infrastructures, enable the complete control of digital systems, and contribute to timely and valid decision-making during cyberattacks.
The suggested classifier’s performance is determined not only by the algorithmic mechanism of the classifier (decision technique) but also by the parameters to be applied to it since its performance changes with their usage. Adjusting appropriate hyperparameters of the spiking neural network to better alignment with labeled training set samples considerably improves fit, resulting in dramatically increased classification accuracy. As a result, selecting the appropriate hyperparameters is critical to the final classification model’s success. Due to its dynamic configuration, it can then reproduce different spikes and triggering behaviors of neurons, which model precisely the digital security problem of energy infrastructures, as proved experimentally.
As proven by the results, the proposed model achieves the highest values (almost 5% higher than other models) in Accuracy, Precision, Recall, F-score, and AUC, which means that the model can distinguish between sophisticated normal and abnormal events.
However, the functionality of this system is also associated with a severe drawback, as a complete understanding of the optimum network for each circumstance necessitates specialized expertise and extensive experimentation. It should also be noted that the proposed methodology has more requirements in computing resources, which is also recorded in the disadvantages of the process as an essential issue that should be explored in the development of this research.
It should be highlighted that the suggested approach has excellent generalizability to non-linearly separable data by using optimally spiking neural networks, CSA, ensemble theory, and sophisticated Transfer Learning techniques. Using the proposed strategy, generating nonlinear models that lead to linearity in bigger spaces is feasible. Furthermore, the number of parameters that must be set is reduced compared to other equivalent techniques. Furthermore, for the classification of a new element in a class, the classification process is based only on the similarity of the unknown element to the algorithm and the most relevant components of each class, reducing the false positives dramatically.
As a future extension of the proposed system, it is proposed to explore ways to automatically find and optimize the Ensemble network parameters and its optimization parameters, to achieve even higher categorization accuracy. A further significant development in this proposal is the addition of automatic export capabilities and selection of the most appropriate features from the initially available data of unknown situations, which will allow upgrading its categorization capabilities, thus dealing with unknown attacks. Finally, the system in question must be studied in a more profound architecture, which will be able to model even more complex nonlinear correlations and intermediate representations, which can lead to even more reliable intelligent systems.