Observer-Based H∞ Load Frequency Control for Networked Power Systems with Limited Communications and Probabilistic Cyber Attacks
Abstract
:1. Introduction
- (1)
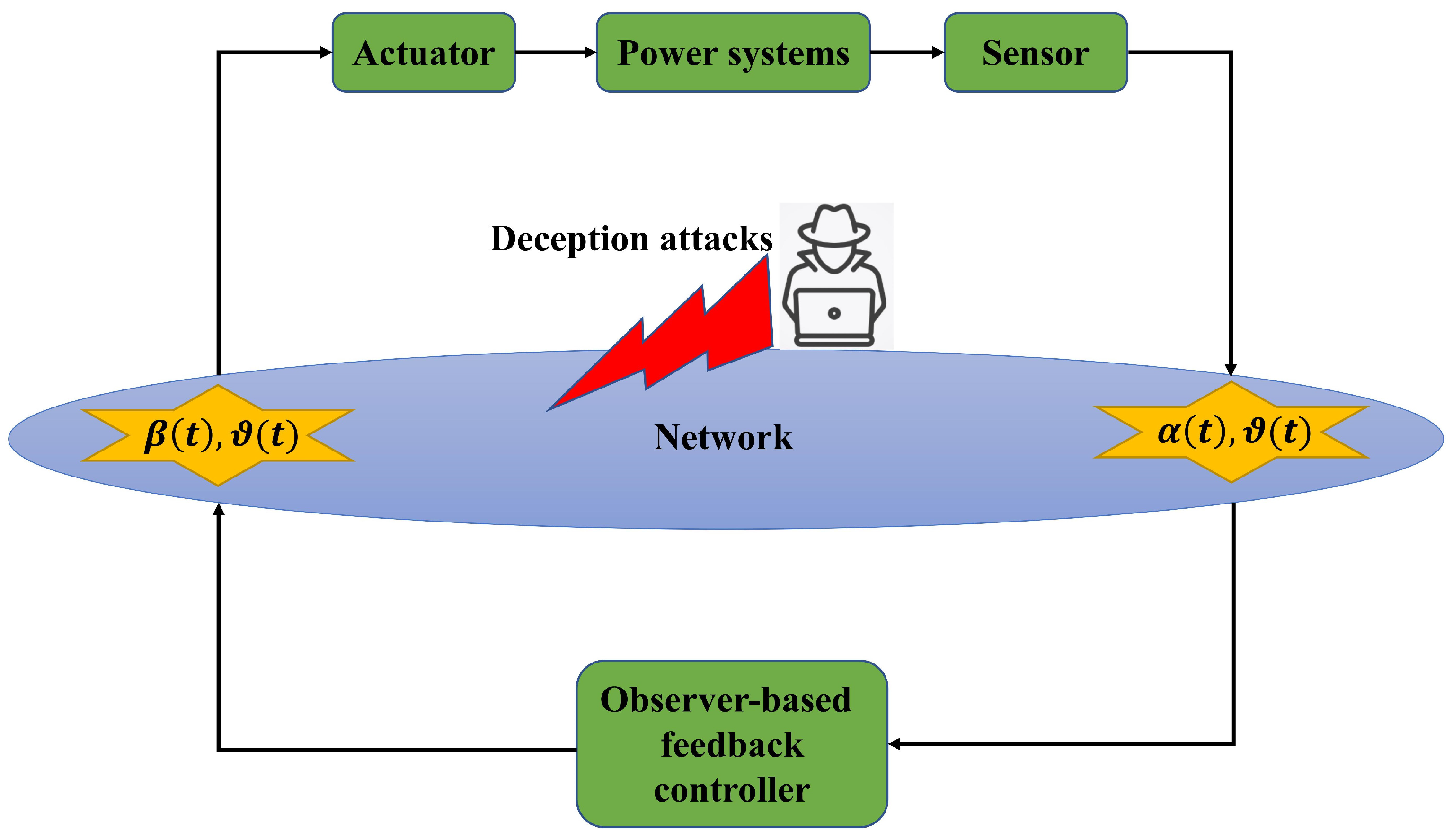
- An observer-based LFC model is established for networked power systems, which not only takes into account multi-path missing measurements and input–output time-varying delays in the communication channel but also considers the influences of random cyber attacks on data transmission.
- (2)
- To implement the load frequency controller, delay-dependent stability criterion including time delays and packet dropout as well as cyber attacks phenomena are derived with the help of Lyapunov–Krasovskii function approach in LMI framework.
- (3)
- On the basis of the resulting stability criteria, the stability gains of the observer and controller are calculated with the assistance of the LMI toolbox.
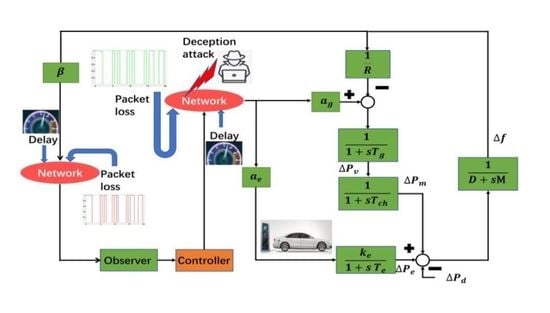
2. Model Description and Preliminaries
3. Results
3.1. Stability and Performance Analysis
3.2. The Observer-Based Feedback Controller Design
- (1)
- By Lemma 1, To address nonlinear term , Let .
- (2)
- To address the nonlinear term , let .From the above transformation, matrix inequality (14) can be translated into the typical LMI. This completes the proof.
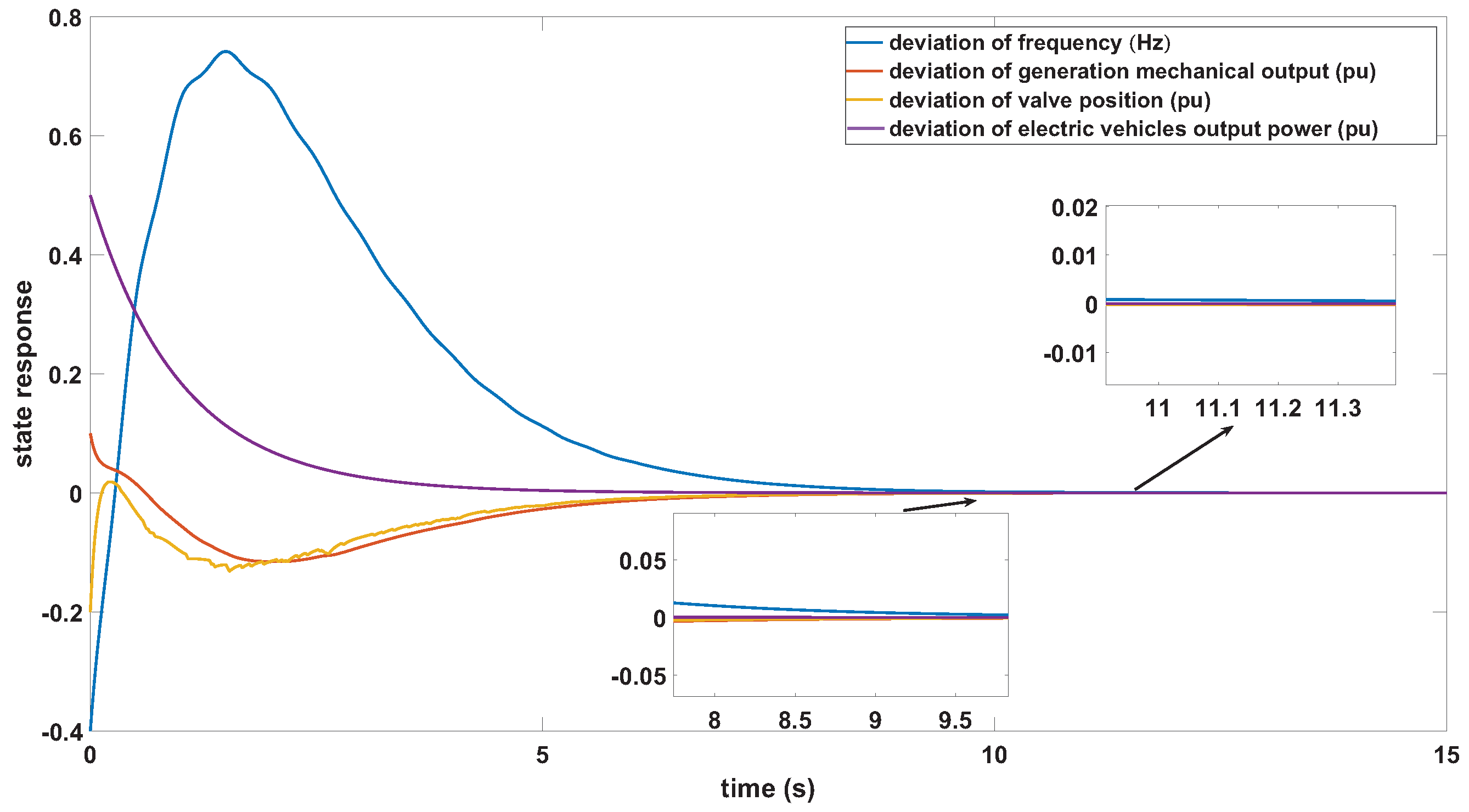
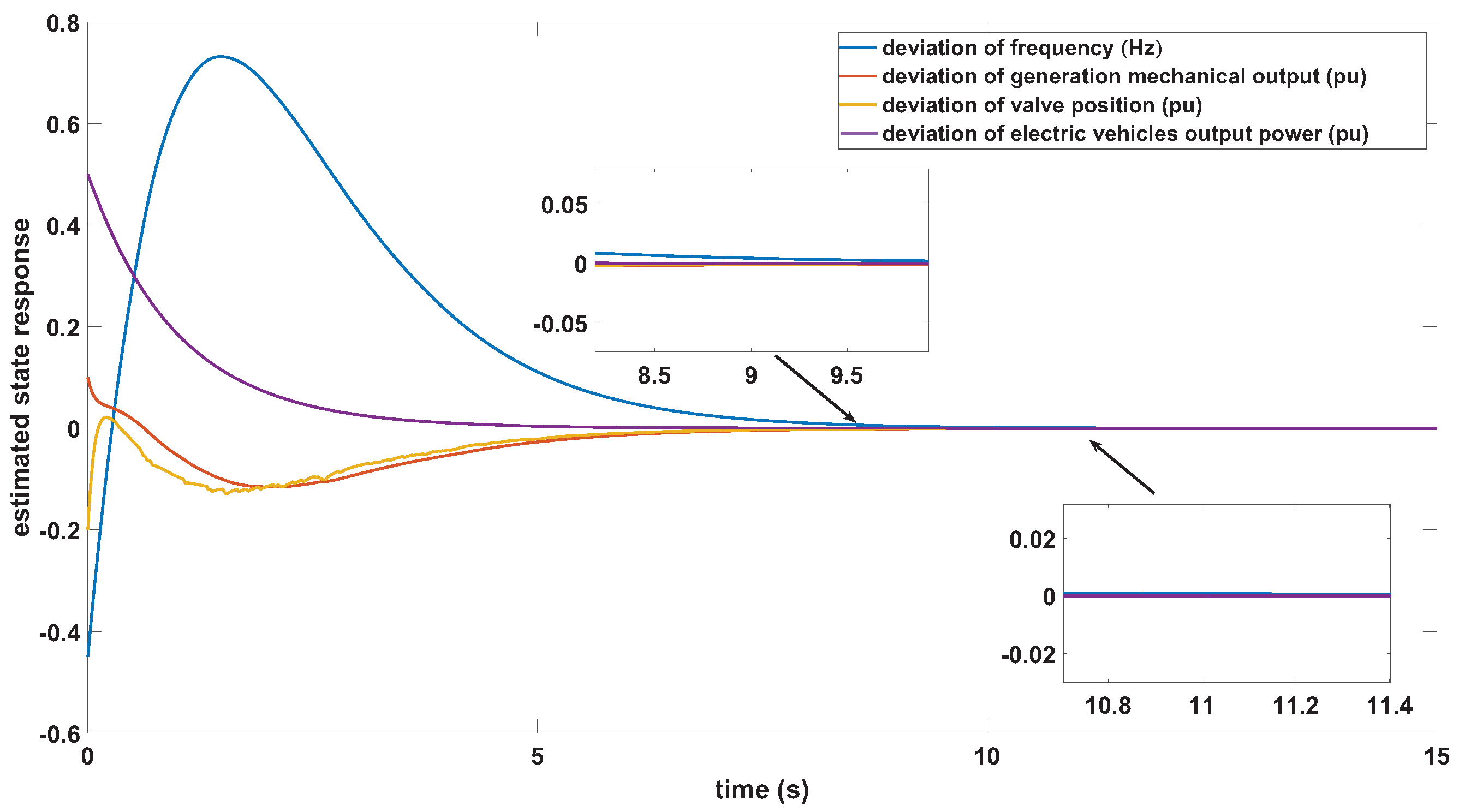
4. A Case Study
| Algorithm 1: Load frequency controller and observer design for networked power systems |
|
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wu, Z.; Mo, H.; Xiong, J.; Xie, M. Adaptive event-triggered observer-based output feedback L∞ load frequency control for networked power systems. IEEE Trans. Ind. Inform. 2019, 16, 3952–3962. [Google Scholar] [CrossRef]
- Singh, V.; Kishor, N.; Samuel, P. Load frequency control with communication topology changes in smart grid. IEEE Trans. Ind. Inform. 2016, 12, 1943–1952. [Google Scholar] [CrossRef]
- Jiang, L.; Yao, W.; Wen, J.; Chen, S.; Wu, Q. Delay-dependent stability for load frequency control with constant and time-varying delays. IEEE Trans. Power Syst. 2012, 27, 932–941. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, X. A note on L2-gain analysis for power systems with delayed load frequency control schemes. J. Frankl. Inst. 2021, 358, 7586–7602. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, J.; Xu, S. H∞ load frequency control of networked power systems via an event-triggered scheme. IEEE Trans. Ind. Electron. 2020, 67, 7104–7113. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, T. Decentralized switching control strategy for load frequency control in multi-area power systems with time delay and packet losses. IEEE Access 2020, 8, 15838–15850. [Google Scholar] [CrossRef]
- Pradhan, S.; Das, D. H∞ controller design for frequency control of delayed power system with actuator saturation and wind source integration. Arab. J. Sci. Eng. 2022, 67. [Google Scholar] [CrossRef]
- Feng, W.; Xie, Y.; Luo, F.; Zhang, X.; Duan, W. Enhanced stability criteria of network-based load frequency control of power systems with time-varying delays. Energies 2021, 14, 5820. [Google Scholar] [CrossRef]
- Zhao, F.; Yuan, J.; Wang, N.; Zhang, Z.; Wen, H. Secure load frequency control of smart grids under deception attack: A piecewise delay approach. Energies 2019, 12, 2266. [Google Scholar] [CrossRef] [Green Version]
- Zhao, X.; Zou, X.; Wang, N.; Zhong, M. Decentralized resilient H∞ load frequency control for cyber-physical power systems under DoS attacks. IEEE/CAA J. Autom. Sin. 2021, 8, 1737–1751. [Google Scholar] [CrossRef]
- Fayek, H. 5G Poor and Rich Novel Control Scheme Based Load Frequency Regulation of a Two-Area System with 100% Renewables in Africa. Fractal Fract. 2021, 5, 2. [Google Scholar] [CrossRef]
- Zhang, C.; Jiang, L.; Wu, Q.; He, Y.; Wu, M. Delay-dependent robust load frequency control for time delay power systems. IEEE Trans. Power Syst. 2013, 28, 2192–2201. [Google Scholar] [CrossRef]
- Sargolzaei, A.; Kang, K.; Lghani, M.; Mehbodniya, A.; Sargolzaei, S. A novel technique for detection of time delay switch attack on load frequency control. Intell. Control Autom. 2015, 6, 205–214. [Google Scholar] [CrossRef]
- Pradhan, S.; Das, D. H∞ load frequency control design based on delay discretization approach for interconnected power systems with time delay. J. Mod. Power Syst. Clean Energy 2021, 9, 1468–1477. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, Y.; Wei, Z.; Sun, G.; Wu, X. Robust H∞ load frequency control of multi-area power system with time delay: A sliding mode control approach. IEEE/CAA J. Autom. Sin. 2018, 5, 610–617. [Google Scholar] [CrossRef]
- Ahuja, A.; Narayan, S.; Kumar, J. Two degrees of freedom observer controller for load frequency control with communication delay. J. Control Instrum. 2017, 8, 35–44. [Google Scholar]
- Wang, Y.; Yan, W.; Zhang, H.; Xie, X. Observer-based dynamic event-triggered H∞ LFC for power systems under actuator saturation and deception attack. Appl. Math. Comput. 2022, 420. [Google Scholar] [CrossRef]
- Sathishkumar, M.; Liu, Y. Resilient annular finite-time bounded and adaptive event-triggered control for networked switched systems with deception attacks. IEEE Access 2021, 9, 92288–92299. [Google Scholar] [CrossRef]
- Tian, E.; Peng, C. Memory-based event-triggering H∞ load frequency control for power systems under deception attacks. IEEE Trans. Cybern. 2020, 50, 4610–4618. [Google Scholar] [CrossRef]
- Shen, Z.; Yang, F.; Chen, J.; Zhang, J.; Hu, A.; Hu, M. Adaptive event-triggered synchronization of uncertain fractional order neural networks with double deception attacks and time-varying delay. Entropy 2021, 23, 1291. [Google Scholar] [CrossRef]
- Tapin, L.; Mehta, R. An integral with feed forward control for primary load frequency control loop using pole-placement design. Int. J. Electr. Electron. Data Commun. 2014, 2, 38–45. [Google Scholar]
- Vrdoljak, K.; Peri, N.; Petrovi, I. Sliding mode based load-frequency control in power systems. Electr. Power Syst. Res. 2010, 80, 514–527. [Google Scholar] [CrossRef]
- Fernando, T.; Emami, K.; Yu, S.; Iu, H.; Wong, K. A novel quasi-decentralized functional observer approach to LFC of interconnected power systems. IEEE Power Energy Soc. Gen. Meet. 2016, 31, 3139–3151. [Google Scholar]
- Pham, T.; Trinh, H.; Le, V. Load frequency control of power systems with electric vehicles and diverse transmission links using distributed functional observers. IEEE Trans. Smart Grid 2015, 7, 238–252. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, Y.; Yang, Z.; Yang, W. Load Frequency Control of Multi-Region Interconnected Power Systems with Wind Power and Electric Vehicles Based on Sliding Mode Control. Energies 2021, 14, 2288. [Google Scholar] [CrossRef]
- Liu, J.; Gu, Y.; Zha, L.; Liu, Y.; Cao, J. Event-triggered H∞ load frequency control for multiarea power systems under hybrid cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1665–1678. [Google Scholar] [CrossRef]
- Wang, J.; Xia, J.; Shen, H.; Xing, M.; Park, J. H∞ synchronization for fuzzy Markov jump chaotic systems with piecewise-constant transition probabilities subject to PDT switching rule. IEEE Trans. Fuzzy Syst. 2021, 29, 3082–3092. [Google Scholar] [CrossRef]
- Liu, J.; Wu, Z.; Yue, D.; Park, J. Stabilization of networked control systems with hybrid-driven mechanism and probabilistic cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 943–953. [Google Scholar] [CrossRef]
- Yan, H.; Zhang, H.; Zhan, X.; Li, Z.; Yang, C. Event-based H∞ fault detection for buck converter with multiplicative noises over network. IEEE Trans. Circuits Syst. Regul. Pap. 2019, 66, 2361–2370. [Google Scholar] [CrossRef]
- Tian, E.; Wang, K.; Zhao, X.; Shen, S.; Liu, J. An improved memory-event-triggered control for networked control systems. J. Frankl. Inst. 2019, 356, 7210–7223. [Google Scholar] [CrossRef]
- Zhou, Q.; Shi, P.; Xu, S.; Li, H. Observer-based adaptive neural network control for nonlinear stochastic systems with time delay. IEEE Trans. Neural Netw. Learn. Syst. 2013, 23, 71–80. [Google Scholar] [CrossRef] [PubMed]
- Yan, H.; Su, Z.; Zhang, H.; Yang, F. Observer-based H∞ control for discrete-time stochastic systems with quantisation and random communication delays. IET Control. Theory Appl. 2013, 7, 372–379. [Google Scholar] [CrossRef]
- Zhao, Y.; Duan, Z.; Wen, G.; Zhang, Y. Distributed finite-time tracking control for multi-agent systems: An observer-based approach. Syst. Control Lett. 2013, 62, 22–28. [Google Scholar] [CrossRef]
- Tan, F.; Zhou, L. Analysis of random synchronization under bilayer derivative and nonlinear delay networks of neuron nodes via fixed time policies. ISA Trans. 2022. [Google Scholar] [CrossRef] [PubMed]




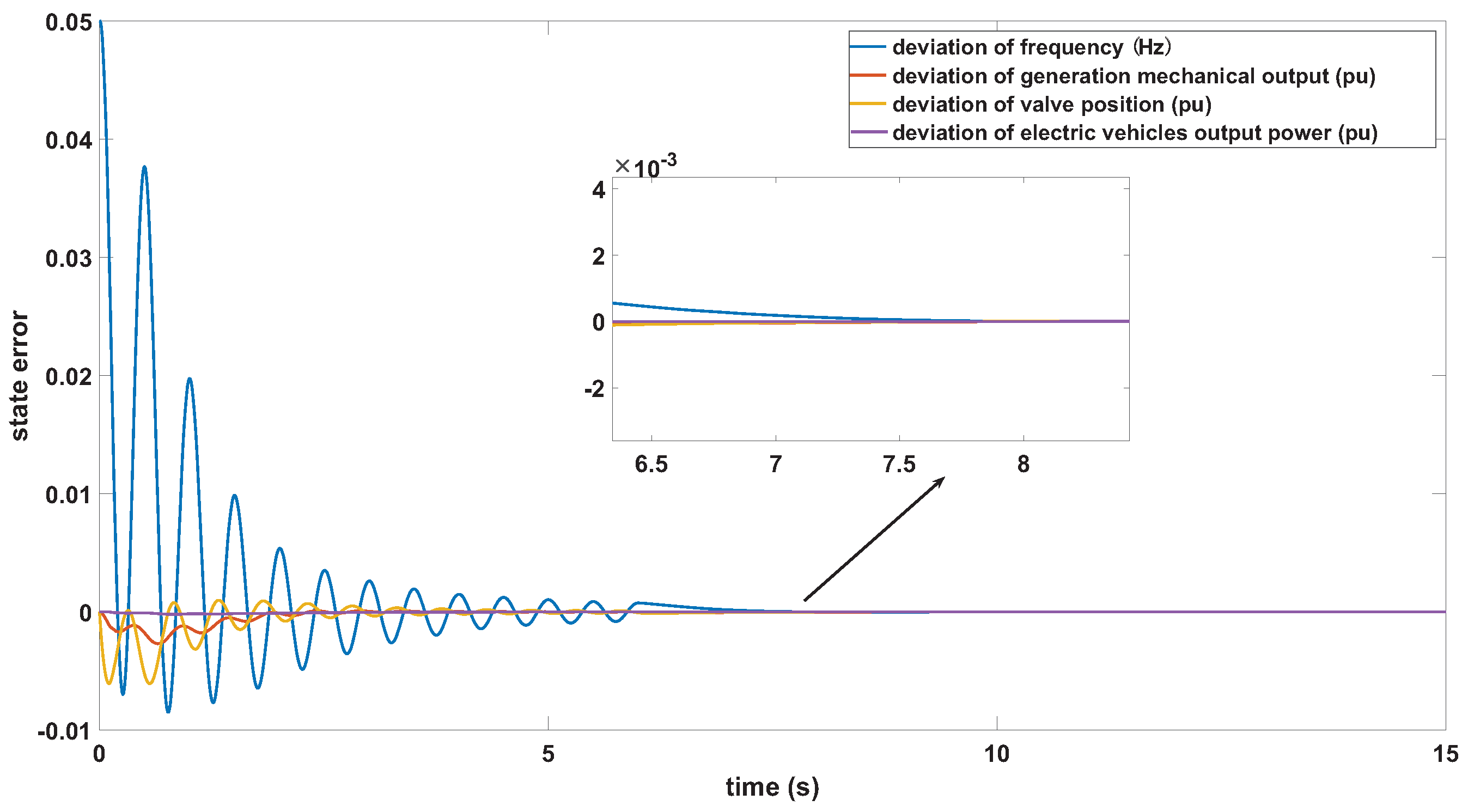
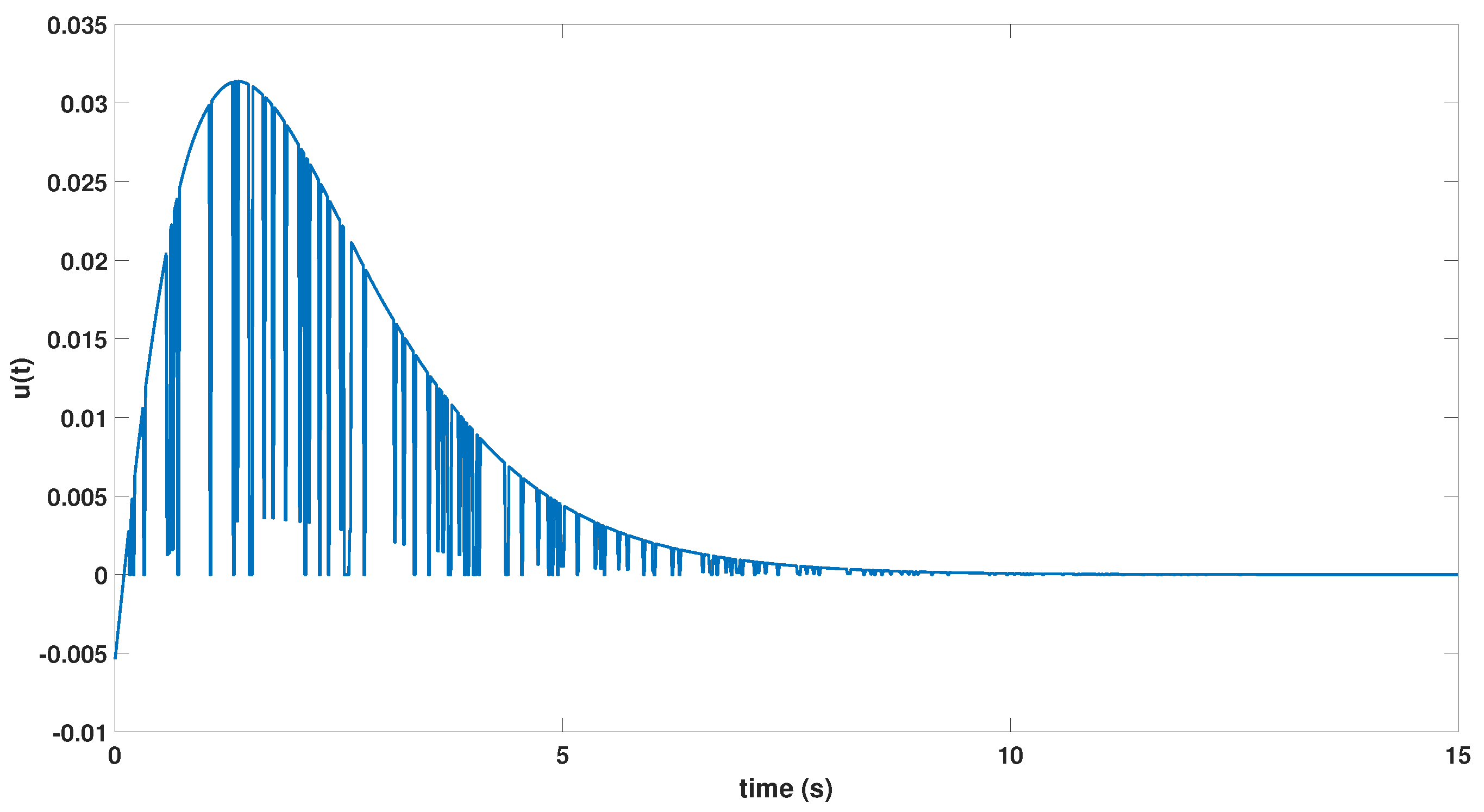


| Symbol | Name |
|---|---|
| the deviations of frequency | |
| the deviations of generation mechanical output | |
| the deviations of valve position | |
| the deviations of load | |
| the deviations of electric vehicles output power | |
| area control error | |
| M | the moment of inertia of the generator |
| D | the generator damping coefficient |
| the time constant of the governor | |
| the time constant of the turbine | |
| the time constant of the electric vehicles | |
| R | the speed drop |
| turbine proportionality factor | |
| electric vehicles proportionality factor | |
| the frequency bias factor | |
| electric vehicles gain factor |
| R | D | M | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 0.3 | 0.1 | 0.05 | 1 | 10 | 0.4 | 1 | 1 | 0.9 | 0.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ge, Y.; Liu, G.; Zhao, G.; Liu, H.; Sun, J. Observer-Based H∞ Load Frequency Control for Networked Power Systems with Limited Communications and Probabilistic Cyber Attacks. Energies 2022, 15, 4234. https://doi.org/10.3390/en15124234
Ge Y, Liu G, Zhao G, Liu H, Sun J. Observer-Based H∞ Load Frequency Control for Networked Power Systems with Limited Communications and Probabilistic Cyber Attacks. Energies. 2022; 15(12):4234. https://doi.org/10.3390/en15124234
Chicago/Turabian StyleGe, Yixuan, Guobao Liu, Guishu Zhao, Huai Liu, and Ji Sun. 2022. "Observer-Based H∞ Load Frequency Control for Networked Power Systems with Limited Communications and Probabilistic Cyber Attacks" Energies 15, no. 12: 4234. https://doi.org/10.3390/en15124234
APA StyleGe, Y., Liu, G., Zhao, G., Liu, H., & Sun, J. (2022). Observer-Based H∞ Load Frequency Control for Networked Power Systems with Limited Communications and Probabilistic Cyber Attacks. Energies, 15(12), 4234. https://doi.org/10.3390/en15124234