Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector
Abstract
:1. Introduction
2. Industrial Control System
- Integrity
- Confidentiality
- Availability
2.1. Impact of Industrial Control System: Electric Power Grid Perspective
2.2. Impact of Cyber-Attack: Industrial Control System Perspective
2.3. Impact of Scanning Tools/Techniques: Industrial Control System Perspective
2.3.1. NMAP
2.3.2. SHODAN
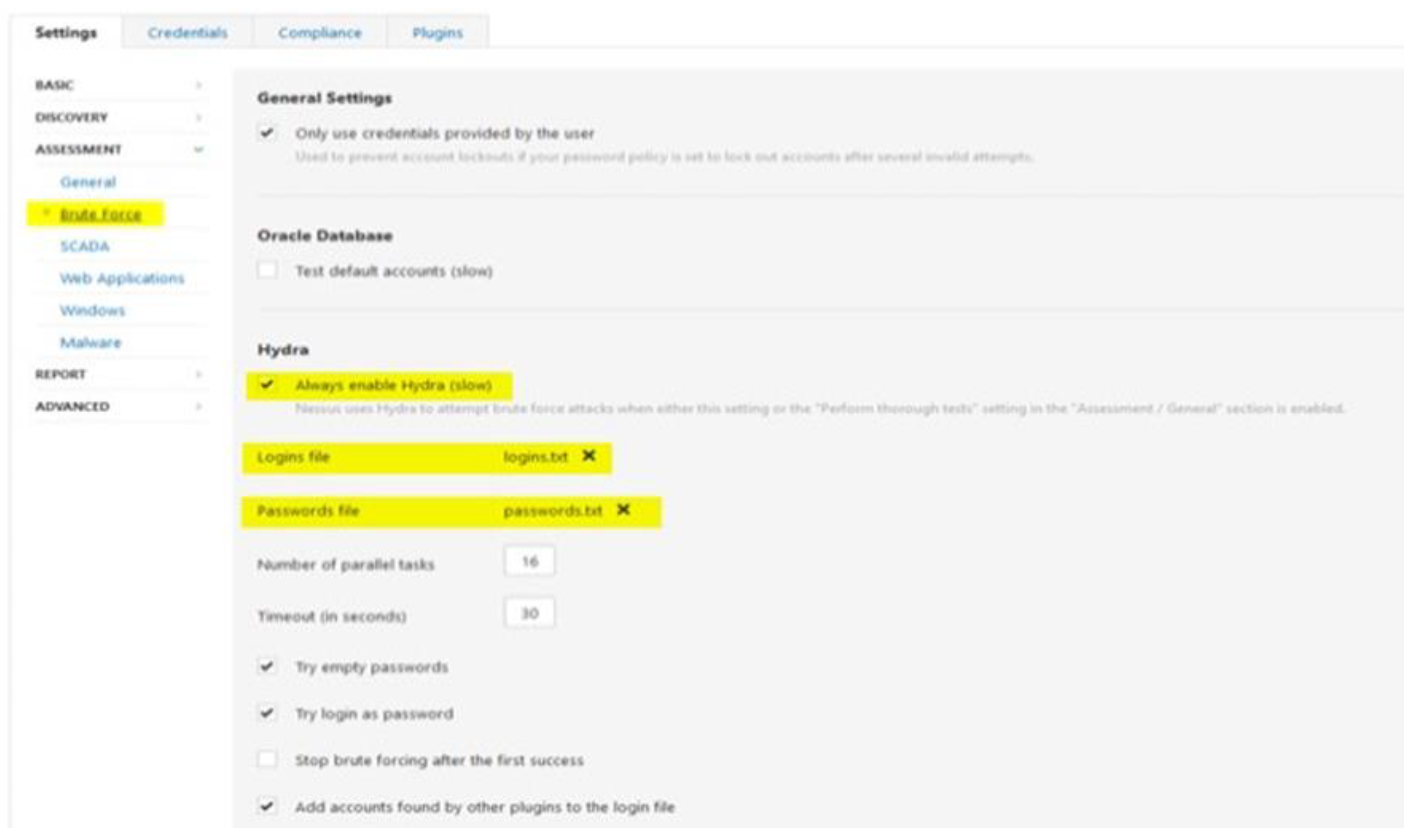
2.3.3. NESSUS
3. Issues and Challenges Related to Industrial Control System
4. Security Attributes in Perspective of Industrial Control System
5. Methodology
- The following written formulas are applied as and n criteria to define alternatives and criteria in TOPSIS.
- Similarly, k is employed to show the numeric count of experts in TOPSIS; denotes the experts.
- The equation is employed in the TOPSIS procedure to signify the HF matrix.
- The standards are written for TOPSIS to determine the criteria and effect of outcomes:
6. Data Analysis and Results
7. Conclusions
- To serve as a prototype for a shared technical platform for the establishment of future industrial control systems cybersecurity test centers.
- To give businesses a cost-effective test platform that lowers simulation and testing costs while delivering more noteworthy outcomes than a standard testbed.
- To perform cyber-attacks against a hybrid framework of real-world monitoring and control systems in the energy sector.
- To create an easy-to-use testbed that is more realistic than simulations and less expensive.
- To prepare hybrid datasets for machine learning frameworks to train on in order to develop robust intrusion detection systems for industrial control systems.
- By focusing on industrial control system cyber security factors, security approaches will be improved, analyzed, identified, and prioritized.
- To analyze the security evaluation of industrial control systems, MCDM methodologies, such as the hesitant fuzzy sets-based AHP-TOPSIS procedure are employed.
- Hesitant fuzzy sets based on the AHP method and hesitant fuzzy sets based on the TOPSIS procedure are well-known and widely employed for resolving multi-criteria decision-making issues, and they produce accurate and effective answers.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Stouffer, K.A.; Pillitteri, V.Y.; Lightman, S.; Abrams, M.; Hahn, A. Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015.
- Alosaimi, W.; Ansari, T.J.; Alharbi, A.; Alyami, H.; Ali, S.; Agrawal, A.; Khan, R.A. Toward a Unified Model Approach for Evaluating Different Electric Vehicles. Energies 2021, 14, 6120. [Google Scholar] [CrossRef]
- Bonandir, N.A.; Jamil, N.; Nawawi, N.A.; Jidin, R.; Rusli, M.E.; Yan, L.K.; Maudau, L.L.A.D. A Review of Cyber Security Assessment (CSA) for Industrial Control Systems (ICS) and Their Impact on The Availability of the ICS Operation. J. Phys. Conf. Ser. 2021, 1860, 012015. [Google Scholar] [CrossRef]
- Toshiba Energy Systems & Solutions Corporation. Power System Monitoring and Control Systems that Contribute to Improving the Supply-Demand Adjustment Performance. Product/Technical Services: Transmission & Distribution. Available online: https://www.toshiba-energy.com/en/transmission/product/power-stabilization.htm (accessed on 9 November 2021).
- Bhamare, D.; Zolanvari, M.; Erbad, A.; Jain, R.; Khan, K.; Meskin, N. Cybersecurity for industrial control systems: A survey. Comput. Secur. 2020, 89, 101677. [Google Scholar] [CrossRef] [Green Version]
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef] [Green Version]
- Knowles, W.; Prince, D.; Hutchison, D.; Disso, J.F.P.; Jones, K. A survey of cyber security management in industrial control systems. Int. J. Crit. Infrastruct. Prot. 2015, 9, 52–80. [Google Scholar] [CrossRef]
- Sajid, A.; Abbas, H.; Saleem, K. Cloud-Assisted IoT-Based SCADA Systems Security: A Review of the State of the Art and Future Challenges. IEEE Access 2016, 4, 1375–1384. [Google Scholar] [CrossRef]
- Ding, D.; Han, Q.L.; Wang, Z.; Ge, X. A Survey on Framework based Distributed Control and Filtering for Industrial Cyber Physical Systems. IEEE Trans. Ind. 2019, 15, 2483–2499. [Google Scholar] [CrossRef] [Green Version]
- Molina, E.; Jacob, E. Software-defined networking in cyber-physical systems: A survey. Comput. Electr. Eng. 2018, 66, 407–419. [Google Scholar] [CrossRef]
- Zeng, P.; Zhou, P. Intrusion Detection in SCADA System: A Survey; Springer: Singapore, 2018; pp. 342–351. [Google Scholar]
- Krotofil, M.; Cárdenas, A.A. Resilience of Process Control Systems to Cyber-Physical Attacks. In Proceedings of the Nordic Conference on Secure IT Systems, Ilulissat, Greenland, 18–21 October 2013; pp. 166–182. [Google Scholar]
- Stefanidis, K.; Voyiatzis, A.G. An HMM-Based Anomaly Detection Approach for SCADA Systems. In Proceedings of the IFIP International Conference on Information Security Theory and Practice, Crete, Greece, 26–27 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 85–99. [Google Scholar]
- Byres, E.; Lowe, J. The Myths and Facts Behind Cyber Security Risks for Industrial Control Systems. In Proceedings of the VDE Kongress, Berlin, Germany, 8–20 October 2004; Volume 116, pp. 213–218. [Google Scholar]
- Alfakeeh, A.S.; Almalawi, A.; Alsolami, F.J.; Abushark, Y.B.; Khan, A.I.; Bahaddad, A.A.S.; Agrawal, A.; Kumar, R.; Khan, R.A. Hesitant Fuzzy-Sets Based Decision-Making Model for Security Risk Assessment. CMC-Comput. Mater. Contin. 2022, 70, 2297–2317. [Google Scholar] [CrossRef]
- Pollet, J. Developing a solid SCADA security strategy. In Proceedings of the 2nd ISA/IEEE Sensors for Industry Conference, Houston, TX, USA, 19–21 November 2002; pp. 148–156. [Google Scholar]
- Igure, V.M.; Laughter, S.A.; Williams, R.D. Security issues in SCADA networks. Comput. Secur. 2006, 25, 498–506. [Google Scholar] [CrossRef]
- Nicholson, A.; Webber, S.; Dyer, S.; Patel, T.; Janicke, H. SCADA security in the light of Cyber-Warfare. Comput. Secur. 2012, 31, 418–436. [Google Scholar] [CrossRef]
- Wang, C.; Fang, L.; Dai, Y. A Simulation Environment for SCADA Security Analysis and Assessment. In Proceedings of the 2010 International Conference on Measuring Technology and Mechatronics Automation, Changsha, China, 13–14 March 2010; Volume 1, pp. 342–347. [Google Scholar]
- Ansari, T.J.; Pandey, D.; Alenezi, M. STORE: Security Threat Oriented Requirements Engineering Methodology. J. King Saud Univ.-Comput. Inf. Sci. 2018. in press. [Google Scholar]
- Queiroz, C.; Mahmood, A.; Hu, J.; Tari, Z.; Yu, X. Building a SCADA Security Testbed. In Proceedings of the 2009 Third International Conference on Network and System Security, Gold Coast, QLD, Australia, 19–21 October 2009; pp. 357–364. [Google Scholar]
- Ansari, T.J.; Pandey, D. An Integration of Threat Modeling with Attack Pattern and Misuse Case for Effective Security Requirement Elicitation. Int. J. Adv. Res. Comput. Sci. 2017, 8, 16–20. [Google Scholar]
- Shahzad, A.; Musa, S.; Aborujilah, A.; Irfan, M. Industrial control systems (ICSs) vulnerabilities analysis and SCADA security enhancement using testbed encryption. In Proceedings of the 8th International Conference on Ubiquitous Information Management and Communication—ICUIMC ’14, Siem Reap, Cambodia, 9–11 January 2014; ACM Press: New York, NY, USA, 2014; pp. 1–6. [Google Scholar]
- Qin, Y.; Cao, X.; Liang, P.; Hu, Q.; Zhang, W. Research on the Analytic Factor Neuron Framework Based on Cloud Generator and Its Application in Oil & Gas SCADA Security Defense. In Proceedings of the 2014 IEEE 3rd International Conference on Cloud Computing and Intelligence Systems, Shenzhen, China, 27–29 November 2014; pp. 155–159. [Google Scholar]
- Zhang, W.W.; Cao, X.D.; Hu, Q.C.; Liang, P.; Qin, Y. Research on FPN-Based Security Defense Framework of Oil and Gas SCADA Network. In Proceedings of the Computational Intelligence in Industrial Application: The 2014 Pacific-Asia Workshop on Computer Science in Industrial Application (CIIA 2014), Singapore, 8–9 December 2014; CRC Press: Boca Raton, FL, USA, 2015; p. 31. [Google Scholar]
- Colombo, A.W.; Bangemann, T.; Karnouskos, S.; Delsing, J.; Stluka, P.; Harrison, R.; Lastra, J.L. Industrial Cloud-Based Cy-ber-Physical Systems. IMC-AESOP Approach 2014, 22, 4–5. [Google Scholar]
- Stouffer, K.; Falco, J.; Scarfone, K. Guide to Industrial Control Systems (ICS) Security—Rev. 2; NIST Special Publication: Gaithersburg, MD, USA, 2014. [Google Scholar]
- Morris, T.; Thornton, Z.; Turnipseed, I. Industrial Control System Simulation and Data Logging for Intrusion Detection System Research. In Proceedings of the 7th Annual Southeastern Cyber Security Summit, Huntsville, AL, USA, 3–4 June 2015. [Google Scholar]
- Simmhan, Y.; Aman, S.; Kumbhare, A.; Liu, R.; Stevens, S.; Zhou, Q.; Prasanna, V. Cloud-Based Software Platform for Big Data Analytics in Smart Grids. Comput. Sci. Eng. 2013, 15, 38–47. [Google Scholar] [CrossRef]
- Khan, A.I.; ALGhamdi, A.S.A.M.; Alsolami, F.J.; Abushark, Y.B.; Almalawi, A.; Ali, A.M.; Agrawal, A.; Kumar, R.; Khan, R.A. Integrating Blockchain Technology into Healthcare Through an Intelligent Computing Technique. CMC-Comput. Mater. Contin. 2022, 70, 2835–2860. [Google Scholar] [CrossRef]
- Abushark, Y.B.; Khan, A.I.; Alsolami, F.J.; Almalawi, A.; Alam, M.; Agrawal, A.; Kumar, R.; Khan, R.A. Usability Evaluation Through Fuzzy AHP-TOPSIS Approach: Security Requirement Perspective. Comput. Mater. Contin. 2021, 68, 1203–1218. [Google Scholar] [CrossRef]
- Coffey, K.; Smith, R.; Maglaras, L.; Janicke, H. Vulnerability Analysis of Network Scanning on SCADA systems. Secur. Commun. Netw. 2018, 2018, 3794603. [Google Scholar] [CrossRef]
- Samtani, S.; Yu, S.; Zhu, H.; Patton, M.; Matherly, J.; Chen, H. Identifying SCADA Systems and Their Vulnerabilities on the Internet of Things: A Text-Mining Approach. IEEE Intell. Syst. 2018, 33, 63–73. [Google Scholar] [CrossRef]
- Alosaimi, W.; Alharbi, A.; Alyami, H.; Ahmad, M.; Pandey, A.K.; Kumar, R.; Khan, R.A. Impact of Tools and Techniques for Securing Consultancy Services. Comput. Syst. Sci. Eng. 2021, 37, 347–360. [Google Scholar] [CrossRef]
- Roy, B.; Misra, S.K. An Integrated Fuzzy ANP and TOPSIS Methodology for Software Selection under MCDM Perspective. Int. J. Innov. Res. Comput. Commun. Eng. 2018, 6, 492–501. [Google Scholar]
- Tavana, M.; Zandi, F.; Katehakis, M.N. A hybrid fuzzy group ANP–TOPSIS framework for assessment of e-government readiness from a CiRM perspective. Inf. Manag. 2013, 50, 383–397. [Google Scholar] [CrossRef]
- Li, B.Z.; Bi, R. The Application of Fuzzy-ANP in Evaluation Index System of Computer Security. Key Eng. Mater. 2010, 439–440, 754–759. [Google Scholar] [CrossRef]
- Kumar, R.; Khan, A.I.; Abushark, Y.B.; Alam, M.; Agrawal, A.; Khan, R.A. An Integrated Approach of Fuzzy Logic, AHP and TOPSIS for Estimating Usable-Security of Web Applications. IEEE Access 2020, 8, 50944–50957. [Google Scholar] [CrossRef]
- Attaallah, A.; Ahmad, M.; Ansari, T.J.; Pandey, A.K.; Kumar, R.; Khan, R.A. Device Security Assessment of Internet of Healthcare Things. Intell. Autom. Soft Comput. 2020, 27, 593–603. [Google Scholar] [CrossRef]
- Alosaimi, W.; Ansari, T.J.; Alharbi, A.; Alyami, H.; Seh, A.; Pandey, A.; Agrawal, A.; Khan, R. Evaluating the Impact of Different Symmetrical Models of Ambient Assisted Living Systems. Symmetry 2021, 13, 450. [Google Scholar] [CrossRef]
- Kumar, R.; Ansari, M.T.J.; Baz, A.; Alhakami, H.; Agrawal, A.; Khan, R.A. A multi-perspective benchmarking framework for esti-mating usable-security of hospital management system software based on fuzzy logic, ANP and TOPSIS methods. KSII Trans. Internet Inf. Syst. 2021, 15, 240–263. [Google Scholar]
- Chong, C.Y.; Lee, S.P.; Ling, T.C. Prioritizing and fulfilling quality attributes for virtual lab development through application of fuzzy analytic hierarchy process and software development guidelines. Malays. J. Comput. Sci. 2014, 27, 1–19. [Google Scholar]
- Onar, S.C.; Oztaysi, B.; Kahraman, C. Strategic Decision Selection Using Hesitant fuzzy TOPSIS and Interval Type-2 Fuzzy AHP: A case study. Int. J. Comput. Intell. Syst. 2014, 7, 1002–1021. [Google Scholar] [CrossRef] [Green Version]
- Wang, C.N.; Thanh, N.V.; Su, C.C. The Study of a Multicriteria Decision Making Model for Wave Power Plant Location Se-lection in Vietnam. Processes 2019, 7, 650. [Google Scholar] [CrossRef] [Green Version]
- Kahraman, C. (Ed.) Fuzzy Multi-Criteria Decision Making: Theory and Applications with Recent Developments; Springer Science & Business Media: Berlin, Germany, 2008; Volume 16. [Google Scholar]
- Ansari, T.J.; Baz, A.; Alhakami, H.; Alhakami, W.; Kumar, R.; Khan, R.A. P-STORE: Extension of STORE Methodology to Elicit Privacy Requirements. Arab. J. Sci. Eng. 2021, 46, 8287–8310. [Google Scholar] [CrossRef]
- Ansari, M.T.J.; Khan, N.A. Worldwide COVID-19 Vaccines Sentiment Analysis through Twitter Content. Electron. J. Gen. Med. 2021, 18, 10. [Google Scholar] [CrossRef]
- Kumar, R.; Alenezi, M.; Ansari, M.T.J.; Gupta, B.K.; Agrawal, A.; Khan, R.A. Evaluating the Impact of Malware Analysis Techniques for Securing Web Applications through a Decision-Making Framework under Fuzzy Environment. Int. J. Intell. Eng. Syst. 2020, 13, 94–109. [Google Scholar] [CrossRef]
- Torra, V.; Narukawa, Y. On hesitant fuzzy sets and decision. In Proceedings of the 2009 IEEE International Conference on Fuzzy Systems, Jeju, Korea, 20–24 August 2009; pp. 1378–1382. [Google Scholar]
- Zarour, M.; Alenezi, M.; Ansari, T.J.; Pandey, A.K.; Ahmad, M.; Agrawal, A.; Kumar, R.; Khan, R.A. Ensuring data integrity of healthcare information in the era of digital health. Health Technol. Lett. 2021, 8, 66–77. [Google Scholar] [CrossRef] [PubMed]
- AlHakami, W.; Binmahfoudh, A.; Baz, A.; AlHakami, H.; Ansari, T.J.; Khan, R.A. Atrocious Impinging of COVID-19 Pandemic on Software Development Industries. Comput. Syst. Sci. Eng. 2021, 36, 323–338. [Google Scholar] [CrossRef]
- Alyami, H.; Nadeem, M.; Alharbi, A.; Alosaimi, W.; Ansari, T.J.; Pandey, D.; Kumar, R.; Khan, R.A. The Evaluation of Software Security through Quantum Computing Techniques: A Durability Perspective. Appl. Sci. 2021, 11, 11784. [Google Scholar] [CrossRef]
- Kumar, R.; Baz, A.; Alhakami, H.; Alhakami, W.; Agrawal, A.; Khan, R.A. A hybrid fuzzy rule-based multi-criteria framework for sustainable-security assessment of web application. Ain Shams Eng. J. 2021, 12, 2227–2240. [Google Scholar] [CrossRef]




| Cyber Occurrence Name | Place Happened | Year | Impact |
|---|---|---|---|
| BlackEnergy | Ukraine Power Grid | 2014/ 2015 | In Ukraine, a 6-h power outage occurs, affecting an estimated 230,000 people. |
| Industroyer/Crash Override | Ukraine Power Grid (North City of Kiev) | 2016 | 1 h of power outage causes Ukraine to lose 1/5 of its electric capacity, according to estimates. |
| Triton | Oil and Gas Plant Saudi Arabia | 2017 | The attackers intended to produce a plant-wide explosion, however, their scheme was foiled due to a vulnerability and defect in their virus. |
| Software | Objective | Impact on Accessibility |
|---|---|---|
| Nmap | To identify and detect hosts on a network, as well as obtain information about them, such as the services they provide and the ports they open. | Yes |
| Shodan | To execute and conduct searching and scanning for hosts or services that run on internet-connected devices. | No |
| Nessus | To execute vulnerability analysis and host investigation on an identified host, as well as to provide a summary of the discovered vulnerability and a method to fix it. | Yes |
| Rank | Linguistic Term | Abbreviation | Triangular Fuzzy Numbers |
|---|---|---|---|
| 10 | Absolutely High Importance | AHI | (7.00, 9.00, 9.00) |
| 9 | Very High Importance | VHI | (5.00, 7.00, 9.00) |
| 8 | Essentially High Importance | ESHI | (3.00, 5.00, 7.00) |
| 7 | Weakly High Importance | WHI | (1.00, 3.00, 5.00) |
| 6 | Equally High Importance | EHI | (1.00, 1.00, 3.00) |
| 5 | Exactly Equal | EE | (1.00, 1.00, 1.00) |
| 4 | Equally Low Importance | ELI | (0.33, 1.00, 1.00) |
| 3 | Weakly Low Important | WLI | (0.20, 0.33, 1.00) |
| 2 | Essentially Low Importance | ESLI | (0.14, 0.20, 0.33) |
| 1 | Very Low Importance | VLI | (0.11, 0.14, 0.20) |
| 0 | Absolutely Low Importance | ALI | (0.11, 0.11, 0.14) |
| C1 | C2 | |
|---|---|---|
| C1 | 1.00000, 1.00000, 1.00000, 1.00000 | 1.00000, 1.00000, 3.00000, 5.00000 |
| C2 | 0.20000, 0.30030, 1.00000, 1.00000 | 1.00000, 1.00000, 1.00000, 1.00000 |
| Criteria of Level 1 | Local Weights of Level 1 | Criteria of Level 2 | Local Weights of Level 2 | Global Weights of Level 2 | Defuzzified Weights | Normalized Weights | Ranks |
|---|---|---|---|---|---|---|---|
| C1 | 0.050080, 0.130010, 0.240000, 0.450010 | C11 | 0.140010, 0.290010, 0.370010, 0.680070 | 0.005114, 0.006131, 0.019171, 0.125300 | 0.1921120 | 0.079191 | 8 |
| C12 | 0.050080, 0.130010, 0.240000, 0.450010 | 0.001150, 0.021119, 0.122264, 0.880081 | 0.1654270 | 0.068191 | 9 | ||
| C13 | 0.090020, 0.180000, 0.330040, 0.690090 | 0.000211, 0.001560, 0.022595, 0.235612 | 0.2157120 | 0.088919 | 3 | ||
| C14 | 0.040070, 0.130070, 0.250040, 0.350050 | 0.001412, 0.007788, 0.045673, 0.225336 | 0.1397560 | 0.057609 | 12 | ||
| C15 | 0.030010, 0.060040, 0.120090, 0.270000 | 0.005950, 0.025419, 0.125864, 0.887381 | 0.1956340 | 0.080643 | 6 | ||
| C16 | 0.030050, 0.080080, 0.180030, 0.340020 | 0.005212, 0.002688, 0.042773, 0.222336 | 0.2924730 | 0.120561 | 2 | ||
| C17 | 0.300100, 0.400100, 0.902000, 1.612000 | 0.004720, 0.014628, 0.044873, 0.322227 | 0.1624520 | 0.066965 | 10 | ||
| C2 | 0.141200, 0.245000, 0.640000, 0.693000 | C21 | 0.200040, 0.290010, 0.530050, 1.123000 | 0.002650, 0.024719, 0.124364, 0.885581 | 0.1994790 | 0.082228 | 5 |
| C22 | 0.120010, 0.230070, 0.500000, 1.120000 | 0.005604, 0.007531, 0.013581, 0.118973 | 0.1934550 | 0.079745 | 7 | ||
| C23 | 0.070090, 0.190080, 0.240050, 0.740040 | 0.015409, 0.048871, 0.157456, 0.165693 | 0.2955260 | 0.121820 | 1 | ||
| C24 | 0.030090, 0.090090, 0.180300, 0.450010 | 0.005920, 0.015228, 0.045373, 0.325727 | 0.1622270 | 0.066872 | 11 | ||
| C25 | 0.040090, 0.140050, 0.190040, 0.480010 | 0.005568, 0.035645, 0.125432, 0.335524 | 0.2116750 | 0.087255 | 4 |
| Criteria/Alternatives | A1 | A2 | A3 | A4 | A5 | A6 |
|---|---|---|---|---|---|---|
| C11 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.9100, 3.7300, 5.7300, 7.5100 |
| C12 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.8200, 2.2700, 4.2700, 6.6500 |
| C13 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 |
| C14 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 |
| C15 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.9100, 3.7300, 5.7300, 7.5100 |
| C16 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.8200, 2.2700, 4.2700, 6.6500 |
| C17 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 |
| C21 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 |
| C22 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 |
| C23 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 |
| C24 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 0.9100, 2.4500, 4.4500, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.9100, 3.7300, 5.7300, 7.5100 | 2.8200, 4.6400, 6.6400, 8.5100 |
| C25 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 2.8200, 4.6400, 6.6400, 8.5100 | 1.4500, 3.0700, 4.9100, 5.6500 | 0.8200, 2.2700, 4.2700, 6.6500 | 2.8200, 4.6400, 6.6400, 8.5100 |
| Criteria/Alternatives | A1 | A2 | A3 | A4 | A5 | A6 |
|---|---|---|---|---|---|---|
| C11 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 |
| C12 | 0.4520, 0.6680, 0.7610, 0.8980 | 0.5740, 0.7250, 0.7920, 0.8960 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.6110, 0.7720, 0.8560, 0.9450 | 0.4520, 0.6680, 0.7610, 0.8980 |
| C13 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2750, 0.4560, 0.5330, 0.7330 |
| C14 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.4520, 0.6680, 0.7610, 0.8980 |
| C15 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.4520, 0.6680, 0.7610, 0.8980 |
| C16 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 |
| C17 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.03980, 0.10000, 0.19200, 0.3840 |
| C21 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 |
| C22 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 |
| C23 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 |
| C24 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 |
| C25 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.3340, 0.5240, 0.6180, 0.7800 | 0.03980, 0.10000, 0.19200, 0.3840 | 0.5740, 0.7250, 0.7920, 0.8960 | 0.2750, 0.4560, 0.5330, 0.7330 | 0.2750, 0.4560, 0.5330, 0.7330 |
| Criteria/Alternatives | A1 | A2 | A3 | A4 | A5 | A6 |
|---|---|---|---|---|---|---|
| C11 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0190, 0.0325, 0.0380, 0.0510 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0470, 0.0530, 0.0630 | 0.1420, 0.1790, 0.1980, 0.2190 |
| C12 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0470, 0.0530, 0.0630 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0190, 0.0325, 0.0380, 0.0510 |
| C13 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0470, 0.0530, 0.0630 |
| C14 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0190, 0.0325, 0.0380, 0.0510 |
| C15 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0470, 0.0530, 0.0630 |
| C16 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0190, 0.0325, 0.0380, 0.0510 |
| C17 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0470, 0.0530, 0.0630 |
| C21 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0190, 0.0325, 0.0380, 0.0510 |
| C22 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0470, 0.0530, 0.0630 |
| C23 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.1420, 0.1790, 0.1980, 0.2190 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0190, 0.0325, 0.0380, 0.0510 |
| C24 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0320, 0.0530, 0.0720, 0.0980 |
| C25 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0555, 0.0870, 0.1040, 0.1220 | 0.0320, 0.0530, 0.0720, 0.0980 |
| Alternatives | d+i | d-i | Gap Degree of CC+i | Satisfaction Degree of CC-i |
|---|---|---|---|---|
| A1 | 0.043125254 | 0.025569685 | 0.378856965 | 0.644585699 |
| A2 | 0.034566598 | 0.049656387 | 0.644856974 | 0.336636544 |
| A3 | 0.044555269 | 0.036552654 | 0.387785859 | 0.635659756 |
| A4 | 0.033363657 | 0.040225254 | 0.563635544 | 0.466967721 |
| A5 | 0.040152547 | 0.045666398 | 0.533636598 | 0.446325454 |
| A6 | 0.039665874 | 0.024555696 | 0.388854745 | 0.623655987 |
| Tryouts | A1 | A2 | A3 | A4 | A5 | A6 | |
|---|---|---|---|---|---|---|---|
| Tryout-0 | Satisfaction Degree (CC-i) | 0.6445857 | 0.3366365 | 0.63565976 | 0.4669677 | 0.4463255 | 0.6236560 |
| Tryout-1 | 0.6444452 | 0.3367587 | 0.63555669 | 0.4669697 | 0.4464576 | 0.6234576 | |
| Tryout-2 | 0.6445587 | 0.3377874 | 0.63885687 | 0.4669696 | 0.4463364 | 0.6239464 | |
| Tryout-3 | 0.6445523 | 0.3385691 | 0.63464579 | 0.4669789 | 0.4466658 | 0.6231346 | |
| Tryout-4 | 0.6444472 | 0.3314474 | 0.63546546 | 0.4666355 | 0.4466679 | 0.6236379 | |
| Tryout-5 | 0.6444526 | 0.3378898 | 0.63545794 | 0.4667458 | 0.4499776 | 0.6233469 | |
| Tryout-6 | 0.6444587 | 0.3377458 | 0.63445131 | 0.4666325 | 0.4415644 | 0.6237798 | |
| Tryout-7 | 0.6446589 | 0.3477758 | 0.63454697 | 0.4696345 | 0.4465467 | 0.6236577 | |
| Tryout-8 | 0.6458577 | 0.3563685 | 0.63445164 | 0.4662567 | 0.4444576 | 0.6236397 | |
| Tryout-9 | 0.6455869 | 0.3445784 | 0.63457846 | 0.4669646 | 0.4445677 | 0.6236599 | |
| Tryout-10 | 0.6455869 | 0.3365558 | 0.63454697 | 0.4661245 | 0.4464576 | 0.6238875 | |
| Tryout-11 | 0.6477587 | 0.3367895 | 0.63445796 | 0.4667435 | 0.4445465 | 0.6236397 | |
| Tryout-12 | 0.6456988 | 0.3355874 | 0.63445794 | 0.4664456 | 0.4463257 | 0.6236688 |
| Procedures/Alternatives | A1 | A2 | A3 | A4 | A5 | A6 |
|---|---|---|---|---|---|---|
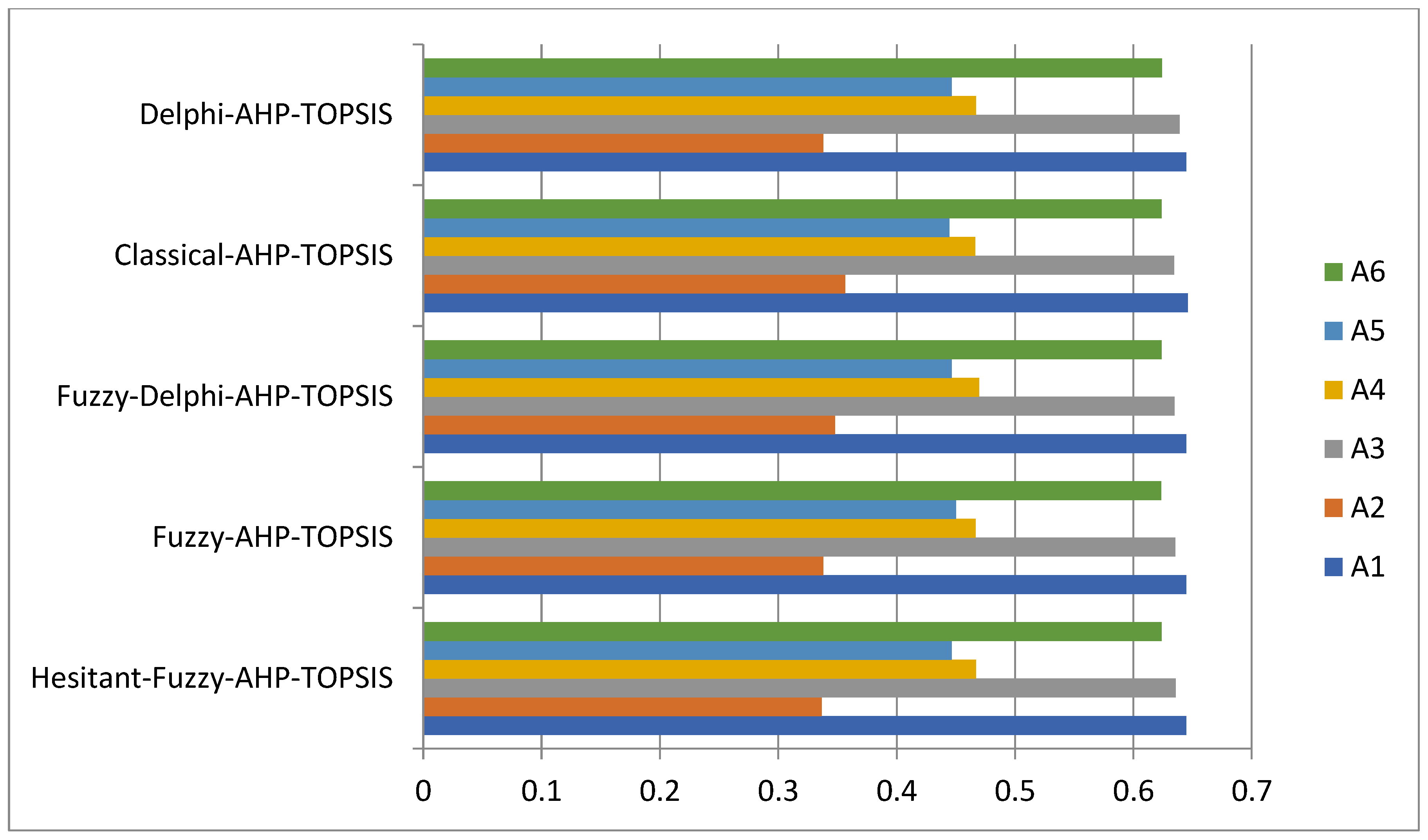
| Hesitant-Fuzzy-AHP-TOPSIS | 0.6445857 | 0.3366365 | 0.63565976 | 0.4669677 | 0.4463255 | 0.6236560 |
| Fuzzy-AHP-TOPSIS | 0.6444526 | 0.3378898 | 0.63545794 | 0.4667458 | 0.4499776 | 0.6233469 |
| Fuzzy-Delphi-AHP-TOPSIS | 0.6446589 | 0.3477758 | 0.63454697 | 0.4696345 | 0.4465467 | 0.6236577 |
| Classical-AHP-TOPSIS | 0.6458577 | 0.3563685 | 0.63445164 | 0.4662567 | 0.4444576 | 0.6236397 |
| Delphi-AHP-TOPSIS | 0.6445587 | 0.3377874 | 0.63885687 | 0.4669696 | 0.4463364 | 0.6239464 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alghassab, M. Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector. Energies 2022, 15, 218. https://doi.org/10.3390/en15010218
Alghassab M. Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector. Energies. 2022; 15(1):218. https://doi.org/10.3390/en15010218
Chicago/Turabian StyleAlghassab, Mohammed. 2022. "Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector" Energies 15, no. 1: 218. https://doi.org/10.3390/en15010218
APA StyleAlghassab, M. (2022). Analyzing the Impact of Cybersecurity on Monitoring and Control Systems in the Energy Sector. Energies, 15(1), 218. https://doi.org/10.3390/en15010218







