Feasibility of Reducing Operator-to-Passenger Contact for Passenger Screening at the Airport with Respect to the Power Consumption of the System
Abstract
1. Introduction
2. Problem Background
3. State of the Art
3.1. Research on WTMD and BS Devices
3.2. Research on Security Checkpoint Functioning
4. Study on the Improvement of Security Checkpoint Operations
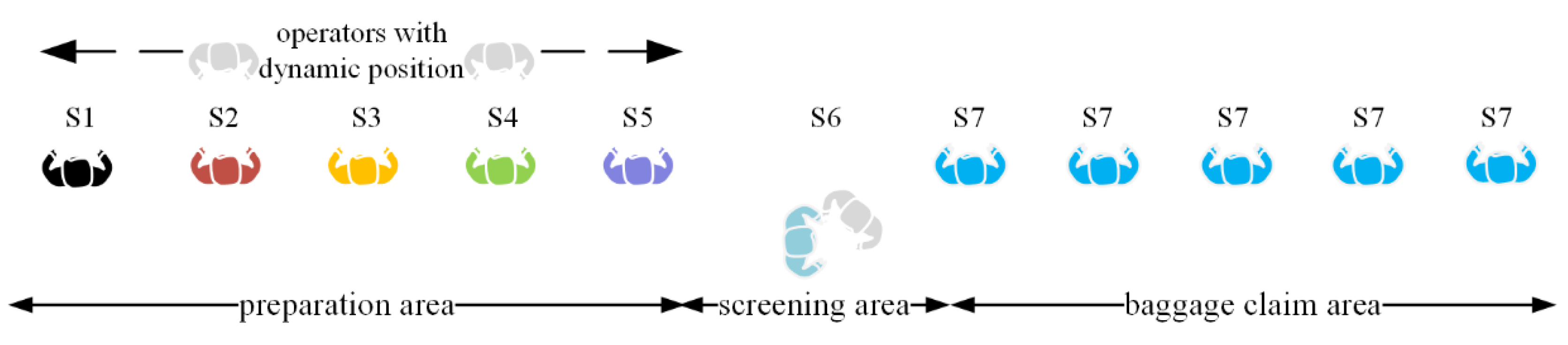
4.1. System Structure and Its Representation in the Simulation Model
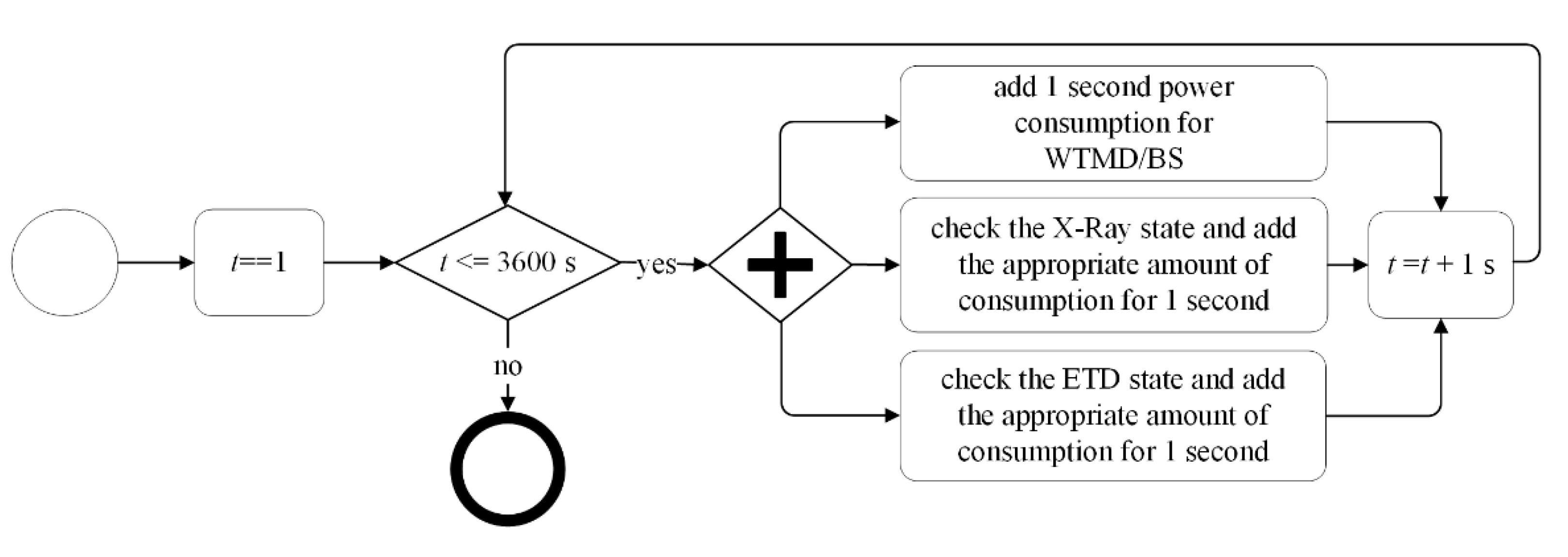
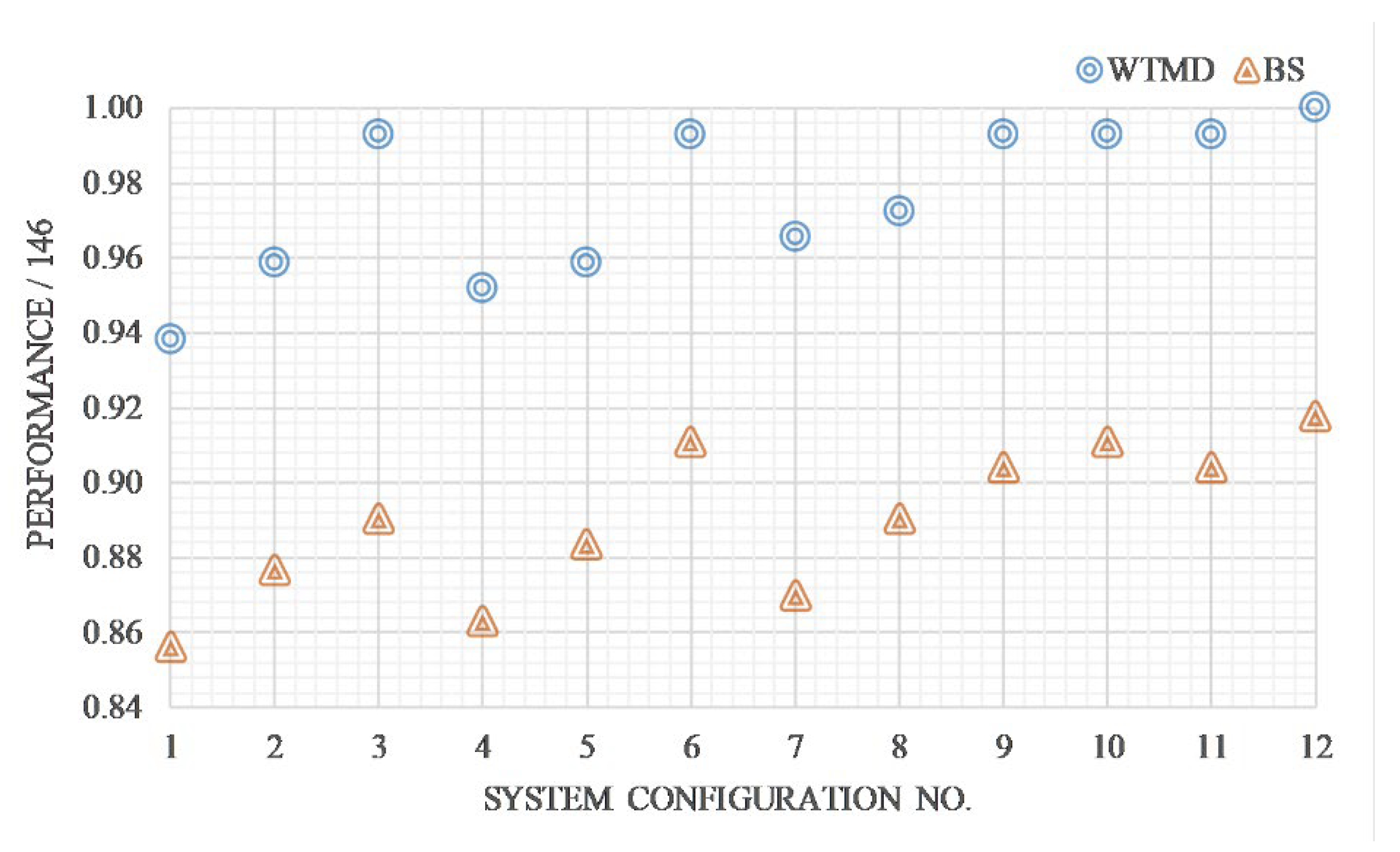
4.2. Study on the Feasibility of Reducing Operator-to-Passenger Contact with Respect to System Performance
- Is it better to use WTMD or BS?
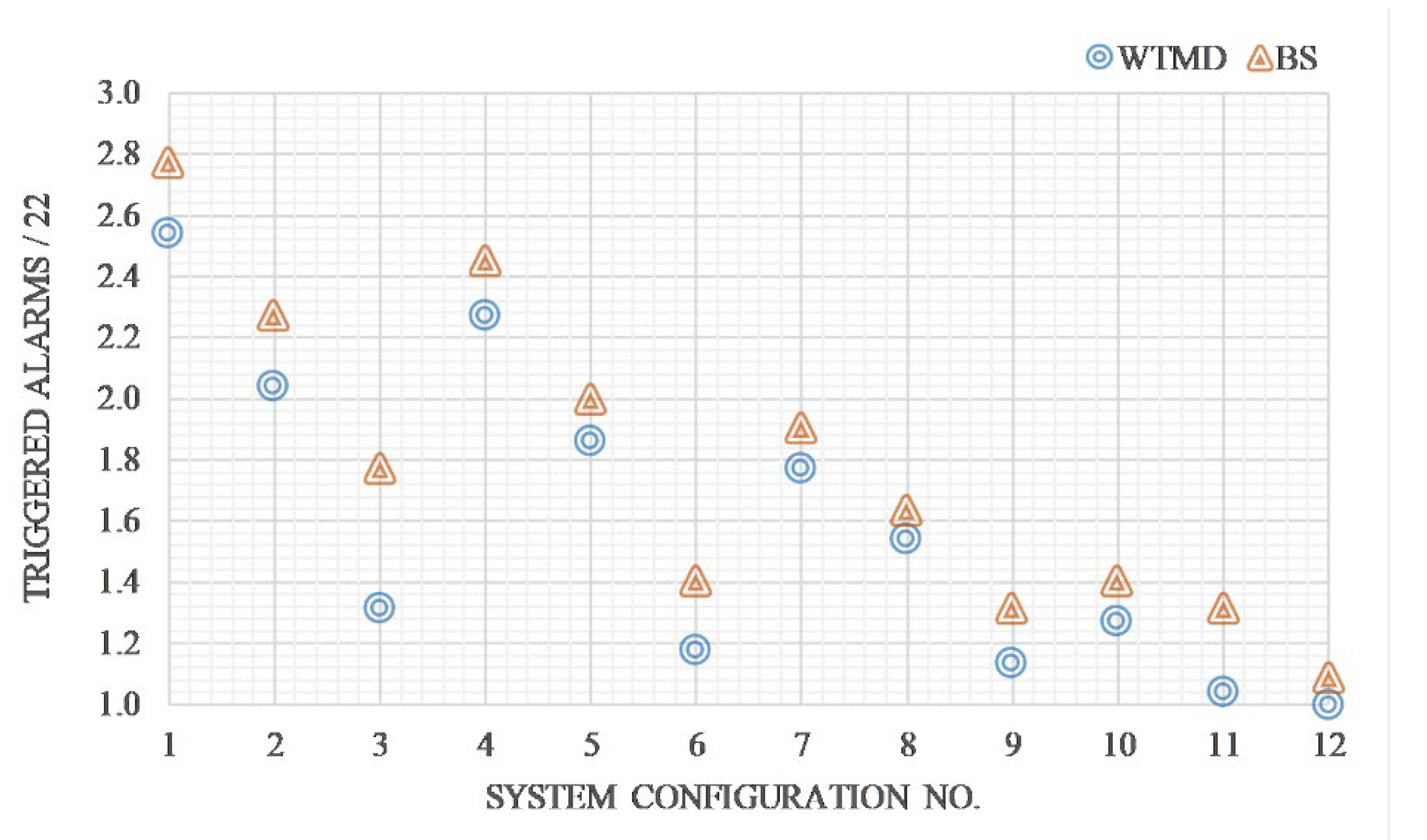
- Does the experience of operators have a significant impact on the number of alarms triggered?
- Will adding an additional operator to the system reduce the number of alarms triggered?
- How do the investigated system parameters relate to power consumption?
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- EU. Commission Implementing Regulation (EU) 2015/1998 of 5 November 2015 Laying down Detailed Measures for the Implementation of the Common Basic Standards on Aviation Security. 2015. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32015R1998&from=EN (accessed on 15 September 2021).
- WHO. Interim Recomenndation on Obligatory Hand Hygiene against Transmission of COVID-19; World Health Organization: Geneva, Switzerland, 2020. [Google Scholar]
- Agruto, A.; Li, Y.; Tian, G.Y.; Bowring, N.; Lockwood, S. A Review of Concealed Weapon Detection and Research in Perspective. In Proceedings of the 2007 IEEE International Conference on Networking, Sensing and Control, London, UK, 15–17 April 2007; pp. 443–448. [Google Scholar]
- Makkonen, J. Classification of Metallic Targets Using a Walk—Through Metal Detection Portal; Tampereen Teknillinen Yliopisto—Tampere University of Technology: Tempere, Finland, 2016; pp. 1–69. [Google Scholar]
- Kottler, D.K.; Roybal, L.G.; Polk, R.E. Detection and classification of concealed weapons using a magnetometer-based portal. In Proceedings Sensors, and Command, Control, Communications, and Intelligence (C3I) Technologies for Homeland Defense and Law Enforcement; SPIE: Orlando, FL, USA, 2009; Volume 4708, pp. 1–8. [Google Scholar]
- Kauppila, J.; Ala-Kleemola, T.; Vihonen, J.; Jylhä, J.; Ruotsalainen, M.; Järvi, A.; Visa, A. Classification of items in a walk-through metal detector using time series of eigenvalues of the polarizability tensor. In Proceedings Detection and Sensing of Mines, Explosive Objects, and Obscured Targets XIV; SPIE: Orlando, FL, USA, 2009; Volume 7303, pp. 1–15. [Google Scholar]
- Elgwel, A.; Harmer, S.W.; Bowring, N.J.; Shaofei, Y. Resolution of Multiple Concealed Threat Objects Using Electromagnetic Pulse Induction. Prog. Electromagn. Res. M 2012, 26, 55–68. [Google Scholar] [CrossRef][Green Version]
- Al-Qubba, A.R.; Al-Shiha, A.; Tian, G.Y. Threat Target Classification Using ANN and SVM Based on a New Sensor Array System. Prog. Electromagn. Res. B 2014, 61, 69–85. [Google Scholar] [CrossRef][Green Version]
- Mironenko, O. Body scanners versus privacy and data protection. Comput. Law Secur. Rev. 2011, 27, 232–244. [Google Scholar] [CrossRef]
- Mery, D.; Svec, E.; Arias, M.; Riffo, V.; Saavedra, J.M.; Banerjee, S. Modern Computer Vision Techniques for X-Ray Testing in Baggage Inspection. IEEE Trans. Syst. Man Cybern. Syst. 2017, 4, 682–692. [Google Scholar] [CrossRef]
- Akçay, S.; Breckon, T. Towards Automatic Threat Detection: A Survey of Advances of Deep Learning within X-ray Security Imaging. arXiv 2020, arXiv:2001.01293, 1–32. [Google Scholar]
- Jinyi, L.; Leng, J.; Liu, Y. Deep Convolutional Neural Network Based Object Detector for X-Ray Baggage Security Imagery. In Proceedings of the International Conference on Tools with Artificial Intelligence (ICTAI), Portland, OR, USA, 4–6 November 2019; pp. 1–10. [Google Scholar]
- Liang, K.J.; Sigman, J.B.; Spell, G.P.; Strellis, D.; Chang, W.; Liu, F.; Mehta, T.; Carin, L. Toward Automatic Threat Recognition for Airport X-ray Baggage Screening with Deep Convolutional Object Detection. Computer Vision and Pattern Recognition (cs.CV). arXiv 2019, arXiv:1912.06329, 1–11. [Google Scholar]
- Liu, Z.; Li, J.; Shu, Y.; Zhang, D. Detection and Recognition of Security Detection Object Based on Yolo9000. In Proceedings of the International Conference on Systems and Informatics (ICSAI), Nanjing, China, 10–12 November 2018; pp. 278–282. [Google Scholar]
- Akçay, S.; Breckon, T. An Evaluation of Region-Based Object Detection Strategies within X-ray Baggage Security Imagery. In Proceedings of the IEEE International Conference on Image Processing (ICIP), Beijing, China, 17–20 September 2017; pp. 1337–1341. [Google Scholar]
- Choi, J.H. Changes in airport operating procedures and implications for airport strategies post-COVID-19. J. Air Transp. Manag. 2021, 94, 102065. [Google Scholar] [CrossRef]
- Štimac, I.; Bračić, M.; Pivac, J.; Oleksa, I. Analysis of Recommended Measures in the Conditions of the COVID-19 Pandemic at Croatian Airports. Transp. Res. Procedia 2020, 51, 141–151. [Google Scholar] [CrossRef]
- Kierzkowski, A.; Kisiel, T. Simulation model of security control lane operation in the state of the COVID-19 epidemic. J. Air Transp. Manag. 2020, 88, 101868. [Google Scholar] [CrossRef] [PubMed]
- Di Mascio, P.; Moretti, L.; Piacitelli, M. Airport Landside Sustainable Capacity and Level of Service of Terminal Functional Subsystems. Sustainability 2020, 12, 8784. [Google Scholar] [CrossRef]
- IATA—International Air Transport Association. Airport Development Reference Manual, 10th ed.; IATA: Montreal, QC, Canada, 2014. [Google Scholar]
- Skorupski, J.; Uchroński, P. Managing the process of passenger security control at an airport using the fuzzy inference system. Expert Syst. Appl. 2016, 54, 284–293. [Google Scholar] [CrossRef]
- Li, Y.; Gao, X.; Xu, Z.; Zhou, X. Network-based queuing model for simulating passenger throughput at an airport security checkpoint. J. Air Transp. Manag. 2018, 66, 13–24. [Google Scholar] [CrossRef]
- Hotle, S.; Mumbower, S. The impact of COVID-19 on domestic U.S. air travel operations and commercial airport service. Transp. Res. Interdiscip. Perspect. 2021, 9, 100277. [Google Scholar]
- Schultz, M.; Soolaki, M. Analytical approach to solve the problem of aircraft passenger boarding during the coronavirus pandemic. Transp. Res. Part C Emerg. Technol. 2021, 124, 102931. [Google Scholar] [CrossRef] [PubMed]



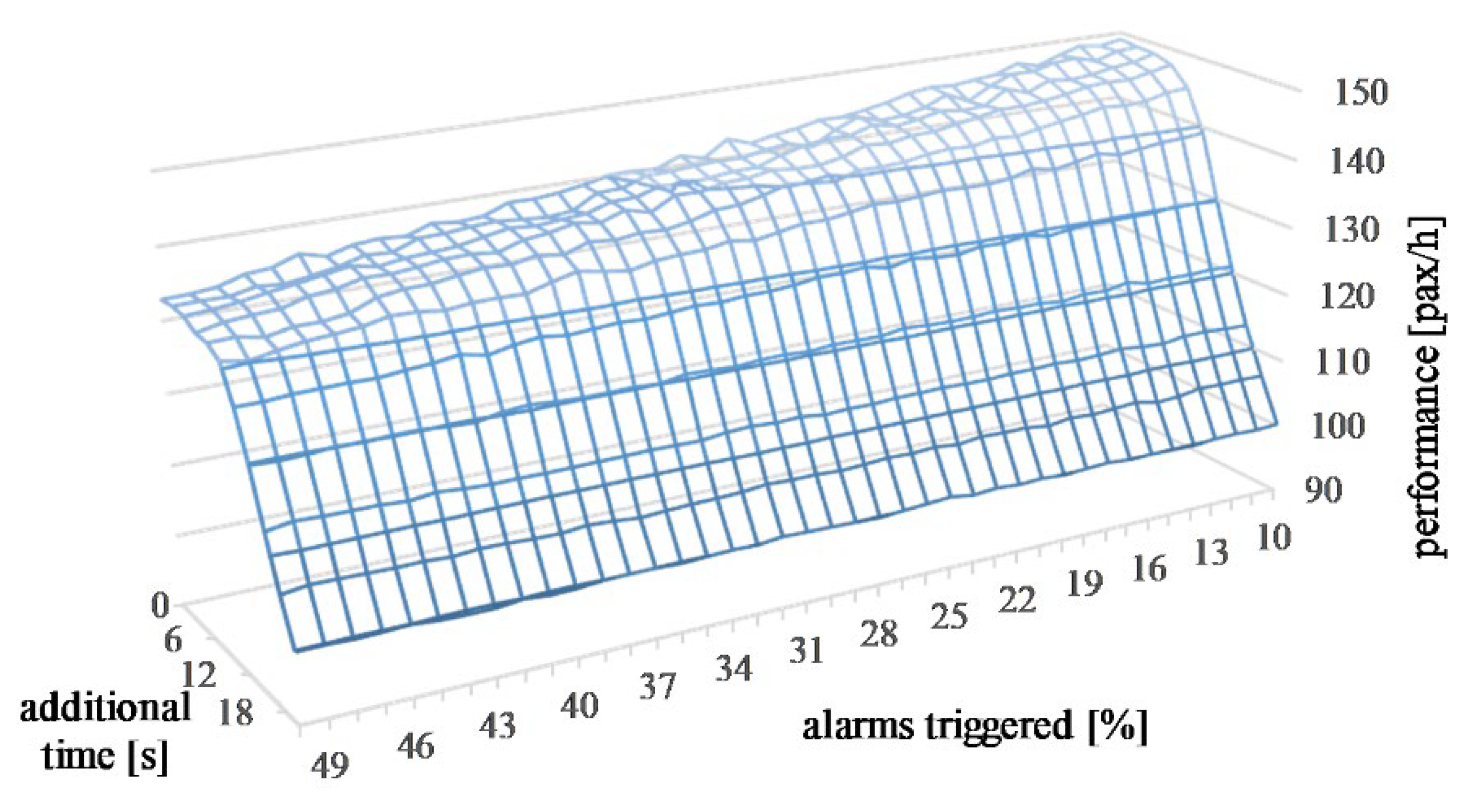
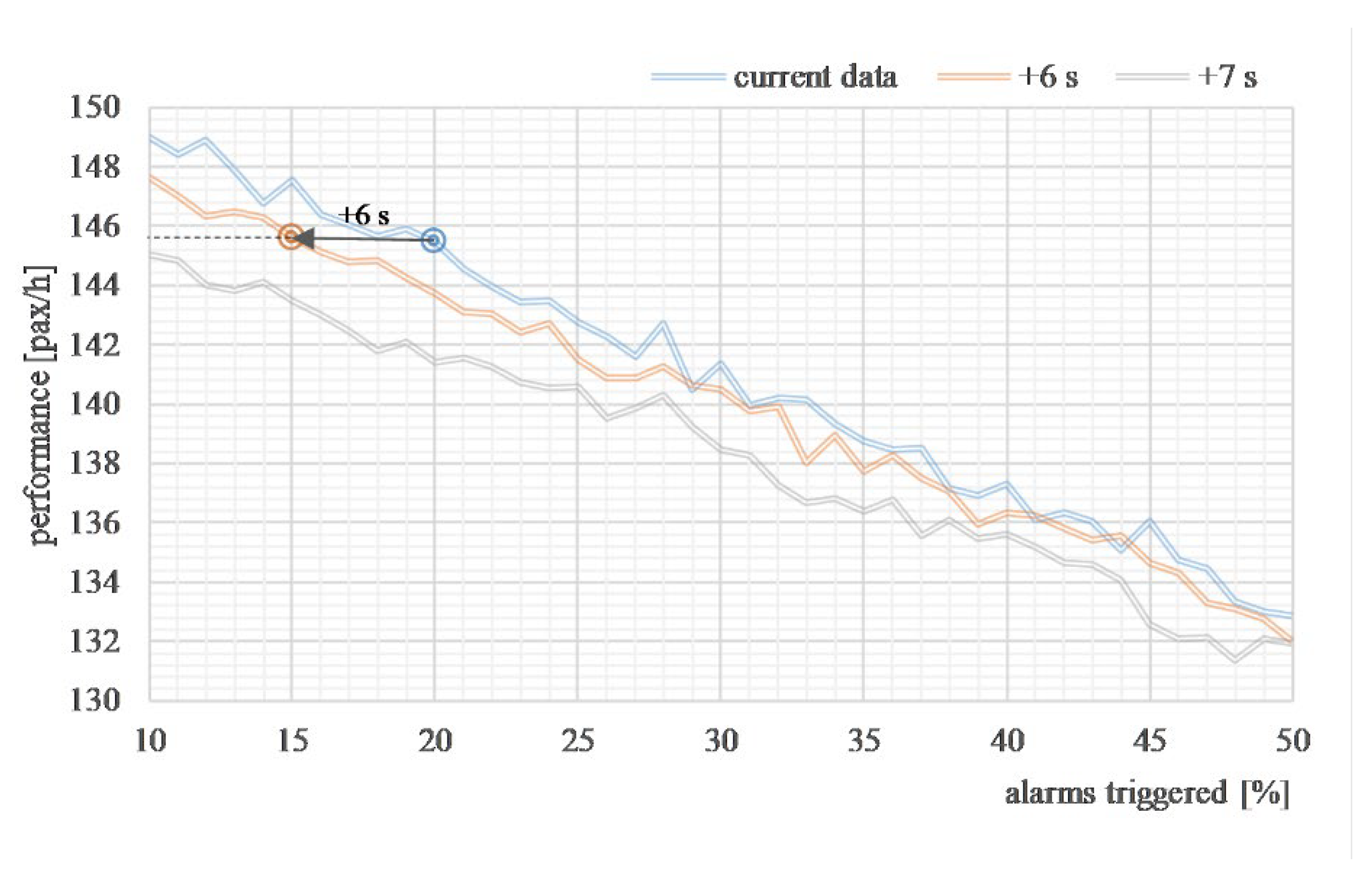
| System Configuration E1 Parameter | Location | Scale | Shape |
|---|---|---|---|
| 1 | 2.011 | 3.642 | 2.760 |
| 2 | 2.186 | 3.959 | 3.000 |
| 3 | 2.252 | 4.078 | 3.014 |
| E2 Parameter | E1 Parameter | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | |||||||
| Location | Scale | Shape | Location | Scale | Shape | Location | Scale | Shape | |
| 1 | 3.778 | 11.209 | 1.205 | 3.905 | 11.586 | 1.246 | 4.118 | 12.216 | 1.313 |
| 2 | 3.990 | 11.838 | 1.273 | 4.245 | 12.594 | 1.354 | 4.372 | 12.972 | 1.395 |
| 3 | 4.160 | 12.342 | 1.327 | 4.415 | 13.098 | 1.408 | 4.500 | 13.350 | 1.435 |
| Variable | Distribution | Parameters | ||
|---|---|---|---|---|
| Location | Scale | Shape | ||
| twtmd | lognormal | 0.000 | 3.014 | 0.113 |
| tbs | pearson V | 2.990 | 9.898 | 2.262 |
| ths1 | erlang | 12.081 | 11.111 | 2.000 |
| ths2 | weibull | 1.289 | 7.440 | 2.337 |
| tw | gamma | 0.000 | 48.148 | 0.395 |
| tS7 | weibull | 9.442 | 96.378 | 2.102 |
| No. | System Configuration | Alarms | Performance | Self-Preparing Time | Power Consumption | |||
|---|---|---|---|---|---|---|---|---|
| NOP | E1 | E2 | SM | [%] | [pax/h] | tps = tS3 + tS5 [s] | Wh/pax | |
| 1 | 1 | 1 | 0 | WTMD | 41 | 137 | 10,516 | 14.0 |
| 2 | 1 | 2 | 0 | WTMD | 32 | 140 | 9771 | 13.5 |
| 3 | 1 | 3 | 0 | WTMD | 20 | 145 | 9241 | 12.7 |
| 4 | 2 | 1 | 1 | WTMD | 36 | 139 | 9057 | 13.7 |
| 5 | 2 | 1 | 2 | WTMD | 29 | 140 | 8826 | 13.5 |
| 6 | 2 | 1 | 3 | WTMD | 18 | 145 | 8418 | 12.6 |
| 7 | 2 | 2 | 1 | WTMD | 28 | 141 | 8324 | 13.4 |
| 8 | 2 | 2 | 2 | WTMD | 24 | 142 | 8135 | 13.1 |
| 9 | 2 | 2 | 3 | WTMD | 17 | 145 | 7864 | 12.6 |
| 10 | 2 | 3 | 1 | WTMD | 19 | 145 | 7838 | 12.7 |
| 11 | 2 | 3 | 2 | WTMD | 16 | 145 | 7690 | 12.5 |
| 12 | 2 | 3 | 3 | WTMD | 15 | 146 | 7618 | 12.4 |
| No. | System Configuration | Alarms | Performance | Self Preparing Time | Power Consumption | |||
|---|---|---|---|---|---|---|---|---|
| NOP | E1 | E2 | SM | [%] | [pax/h] | tps = tS3 + tS5 [s] | Wh/pax | |
| 1 | 1 | 1 | 0 | BS | 49 | 125 | 119,12 | 29.9 |
| 2 | 1 | 2 | 0 | BS | 39 | 128 | 111,99 | 28.9 |
| 3 | 1 | 3 | 0 | BS | 30 | 130 | 108,20 | 28.0 |
| 4 | 2 | 1 | 1 | BS | 43 | 126 | 104,07 | 29.4 |
| 5 | 2 | 1 | 2 | BS | 34 | 129 | 101,48 | 28.4 |
| 6 | 2 | 1 | 3 | BS | 23 | 133 | 9615 | 27.0 |
| 7 | 2 | 2 | 1 | BS | 33 | 127 | 9819 | 28.8 |
| 8 | 2 | 2 | 2 | BS | 28 | 130 | 9422 | 27.9 |
| 9 | 2 | 2 | 3 | BS | 22 | 132 | 9206 | 27.2 |
| 10 | 2 | 3 | 1 | BS | 23 | 133 | 9122 | 27.0 |
| 11 | 2 | 3 | 2 | BS | 22 | 132 | 9073 | 27.1 |
| 12 | 2 | 3 | 3 | BS | 18 | 134 | 8883 | 26.7 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kierzkowski, A.; Kisiel, T. Feasibility of Reducing Operator-to-Passenger Contact for Passenger Screening at the Airport with Respect to the Power Consumption of the System. Energies 2021, 14, 5943. https://doi.org/10.3390/en14185943
Kierzkowski A, Kisiel T. Feasibility of Reducing Operator-to-Passenger Contact for Passenger Screening at the Airport with Respect to the Power Consumption of the System. Energies. 2021; 14(18):5943. https://doi.org/10.3390/en14185943
Chicago/Turabian StyleKierzkowski, Artur, and Tomasz Kisiel. 2021. "Feasibility of Reducing Operator-to-Passenger Contact for Passenger Screening at the Airport with Respect to the Power Consumption of the System" Energies 14, no. 18: 5943. https://doi.org/10.3390/en14185943
APA StyleKierzkowski, A., & Kisiel, T. (2021). Feasibility of Reducing Operator-to-Passenger Contact for Passenger Screening at the Airport with Respect to the Power Consumption of the System. Energies, 14(18), 5943. https://doi.org/10.3390/en14185943






