Resilient Event-Triggered Control for LFC-VSG Scheme of Uncertain Discrete-Time Power System under DoS Attacks †
Abstract
1. Introduction
1.1. Related Work
1.2. Our Contributions
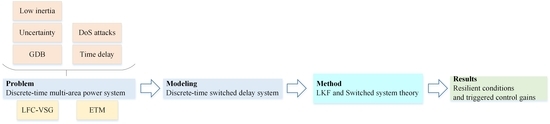
2. Problem Statement
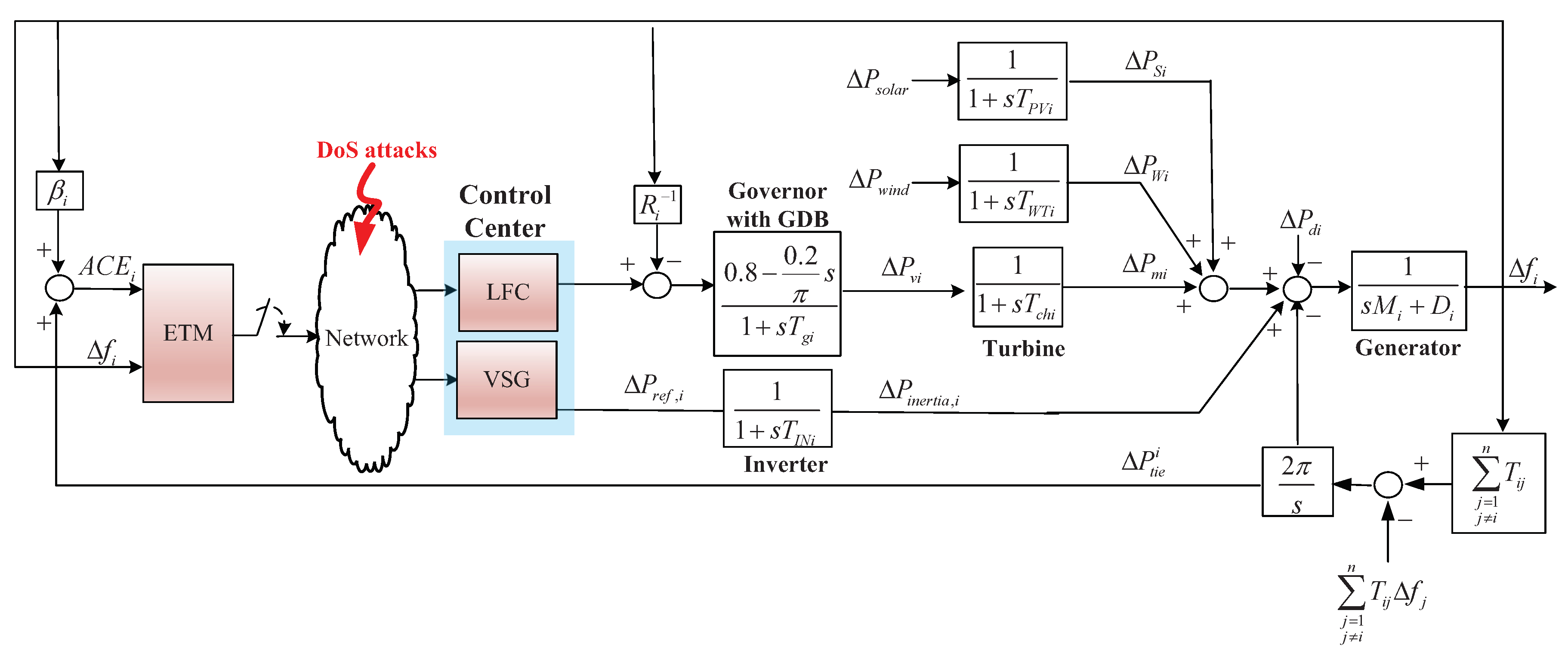
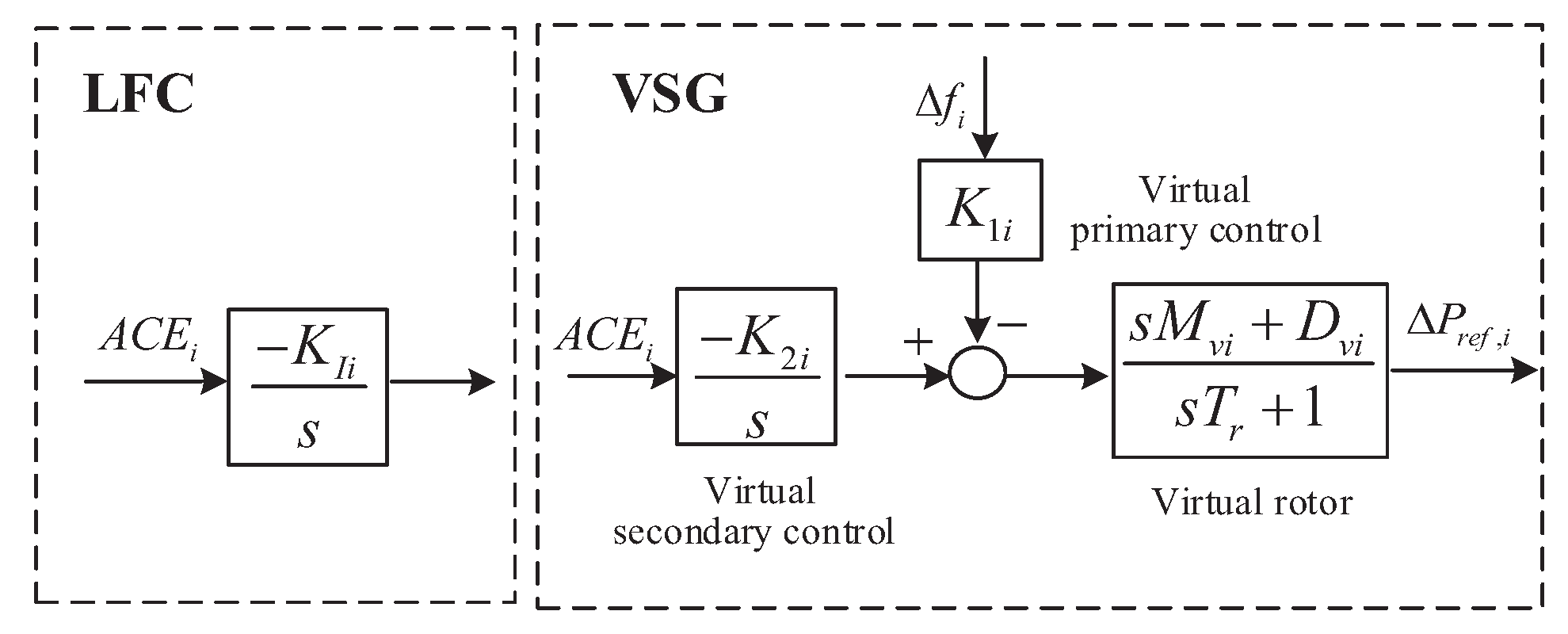
2.1. Discrete-Time Model of Multi-Area Power System with GDB and Uncertainty under LFC-VSG Scheme
2.2. Discrete-Time Power System under DoS Attacks and Event-Triggered Mechanism
3. Analysis of Weighted Performance
4. Design of Resilient Triggering Control
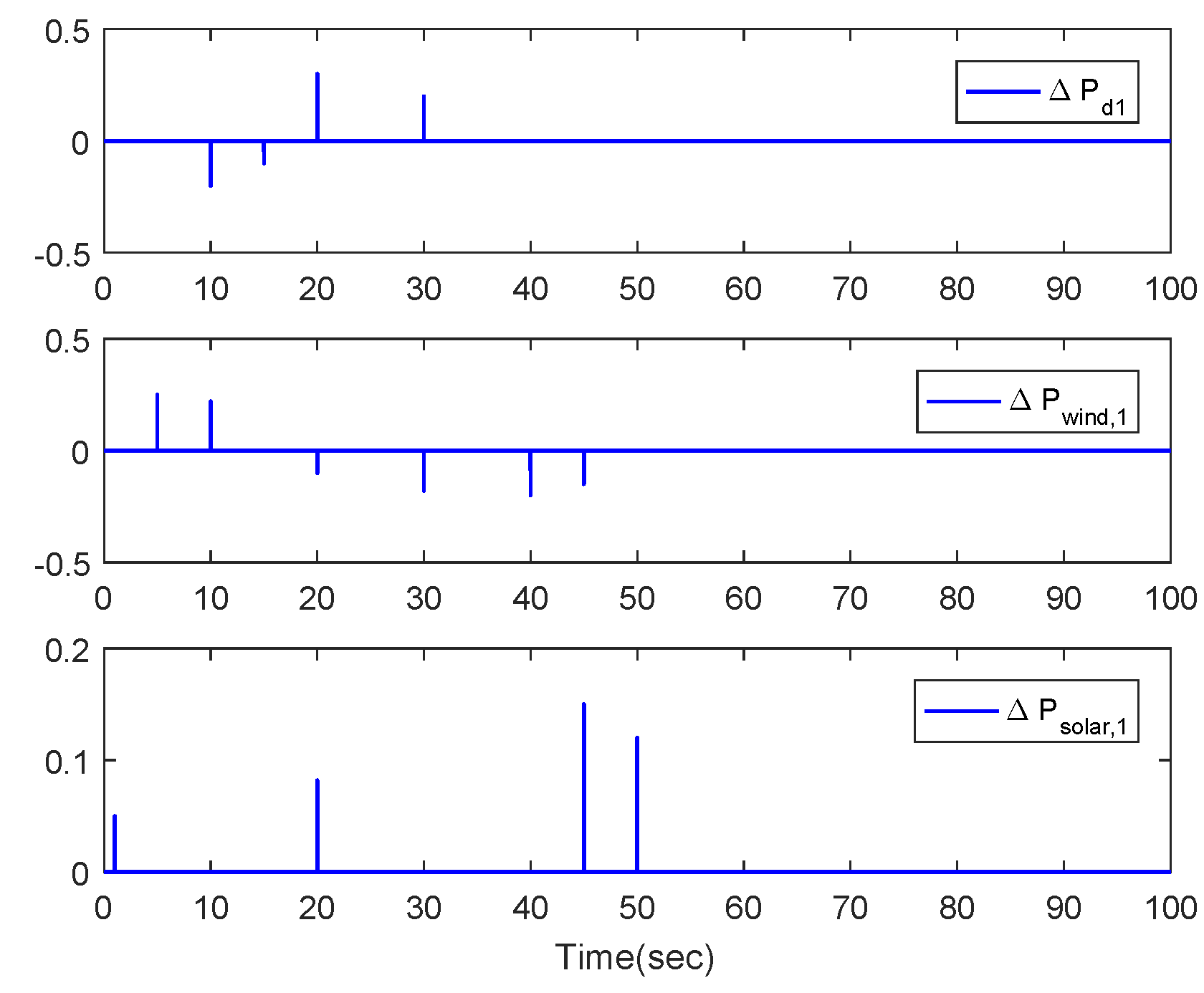
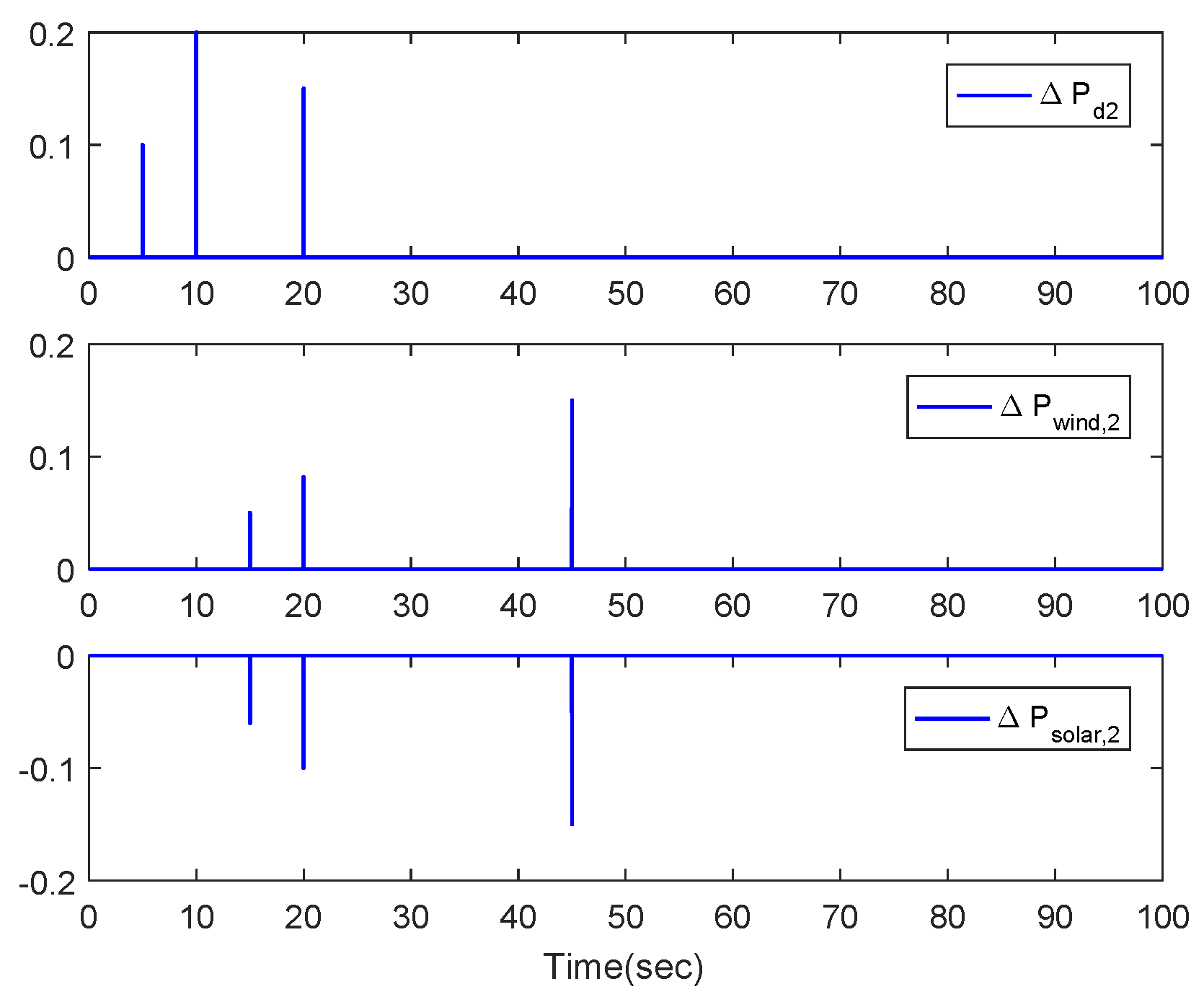
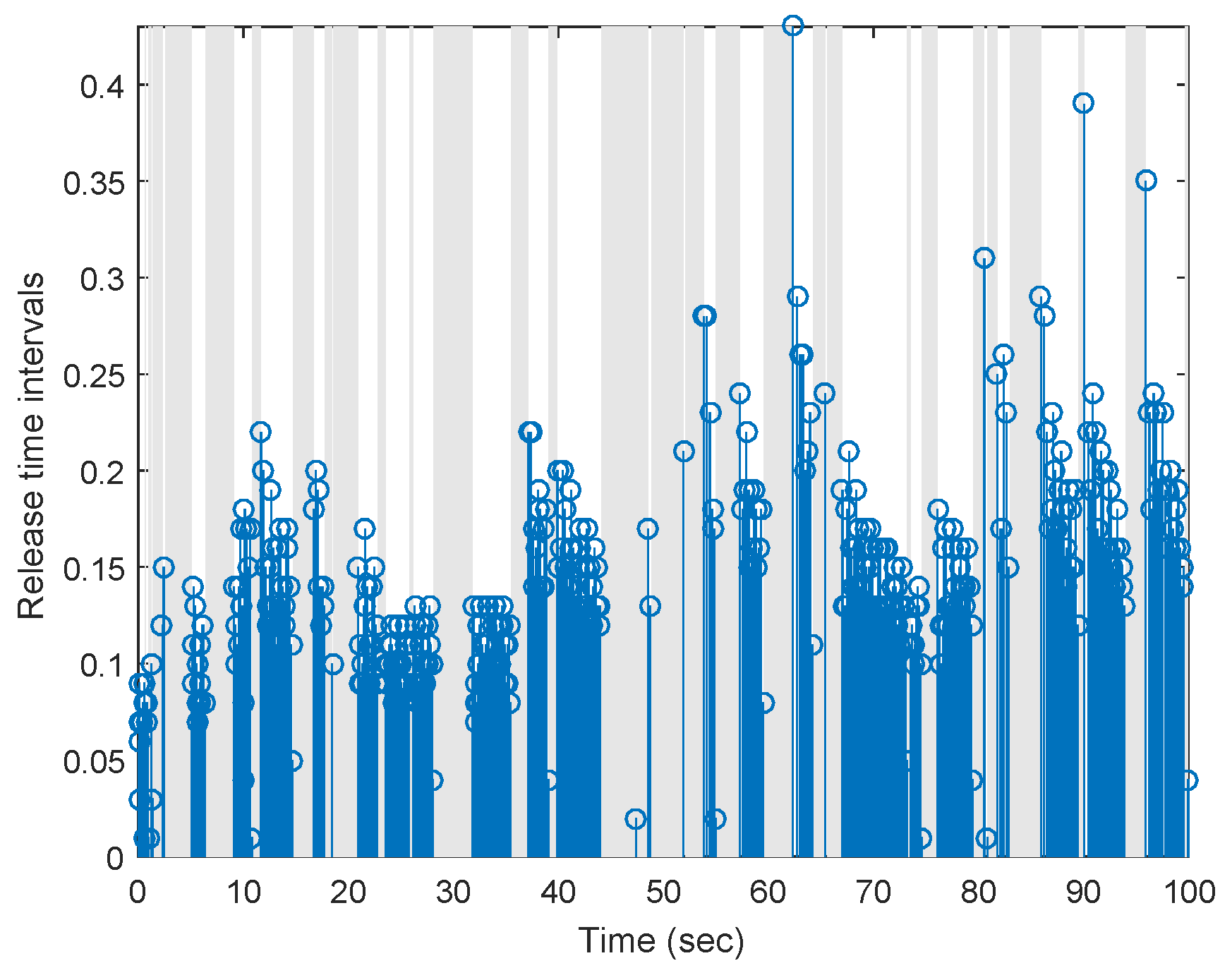
5. Simulation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
Appendix A.1. Proof of Theorem 1
Appendix A.2. Proof of Theorem 2
References
- Bevrani, H.; Ghosh, A.; Ledwich, G. Renewable energy sources and frequency regulation: Survey and new perspectives. IET Renew. Power Gener. 2010, 4, 438–457. [Google Scholar] [CrossRef]
- Dreidy, M.; Mokhlis, H.; Mekhilef, S. Inertia response and frequency control techniques for renewable energy sources: A review. Renew. Sustain. Energy Rev. 2017, 69, 144–155. [Google Scholar] [CrossRef]
- Bevrani, H.; Ise, T.; Miura, Y. Virtual synchronous generators: A survey and new perspectives. Int. J. Electr. Power Energy Syst. 2014, 54, 244–254. [Google Scholar] [CrossRef]
- Kerdphol, T.; Rahman, F.S.; Mitani, Y. Virtual inertia control application to enhance frequency stability of interconnected power systems with high renewable energy penetration. Energies 2018, 11, 981. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2016, 32, 3317–3318. [Google Scholar] [CrossRef]
- Sgouras, K.I.; Birda, A.D.; Labridis, D.P. Cyber attack impact on critical smart grid infrastructures. In Proceedings of the ISGT 2014, Washington, DC, USA, 19–22 February 2014; pp. 1–5. [Google Scholar]
- Wang, W.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef]
- Ding, D.; Han, Q.L.; Xiang, Y.; Ge, X.; Zhang, X.M. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing 2018, 275, 1674–1683. [Google Scholar] [CrossRef]
- Guan, Y.; Ge, X. Distributed attack detection and secure estimation of networked cyber-physical systems against false data injection attacks and jamming attacks. IEEE Trans. Signal Inf. Process. Over Netw. 2018, 4, 48–59. [Google Scholar] [CrossRef]
- Liu, J.; Tian, E.; Xie, X.; Lin, H. Distributed event-triggered control for networked control systems with stochastic cyber-attacks. J. Frankl. Inst. 2019, 356, 10260–10276. [Google Scholar] [CrossRef]
- Amin, S.; Cárdenas, A.A.; Sastry, S.S. Safe and secure networked control systems under denial-of-service attacks. In Proceedings of the International Workshop on Hybrid Systems: Computation and Control, San Francisco, CA, USA, 13–15 April 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 31–45. [Google Scholar]
- Pang, Z.H.; Liu, G.P.; Zhou, D.; Hou, F.; Sun, D. Two-channel false data injection attacks against output tracking control of networked systems. IEEE Trans. Ind. Electron. 2016, 63, 3242–3251. [Google Scholar] [CrossRef]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-service (DoS) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control. Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Zhang, H.; Qi, Y.; Wu, J.; Fu, L.; He, L. DoS attack energy management against remote state estimation. IEEE Trans. Control. Netw. Syst. 2018, 5, 383–394. [Google Scholar] [CrossRef]
- Xiao, S.; Han, Q.L.; Ge, X.; Zhang, Y. Secure Distributed Finite-Time Filtering for Positive Systems Over Sensor Networks Under Deception Attacks. IEEE Trans. Cybern. 2019. [Google Scholar] [CrossRef] [PubMed]
- De Persis, C.; Tesi, P. Input-to-state stabilizing control under denial-of-service. IEEE Trans. Autom. Control 2015, 60, 2930–2944. [Google Scholar] [CrossRef]
- Peng, C.; Li, J.; Fei, M. Resilient Event-Triggering H∞ Load Frequency Control for Multi-Area Power Systems With Energy-Limited DoS Attacks. IEEE Trans. Power Syst. 2017, 32, 4110–4118. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Xie, X.; Chen, X.; Yin, X. Resilient event-triggered controller synthesis of networked control systems under periodic DoS jamming attacks. IEEE Trans. Cybern. 2018, 49, 4271–4281. [Google Scholar] [CrossRef]
- Chen, X.; Wang, Y.; Hu, S. Event-based robust stabilization of uncertain networked control systems under quantization and denial-of-service attacks. Inf. Sci. 2018, 459, 369–386. [Google Scholar] [CrossRef]
- Cheng, Z.; Yue, D.; Hu, S.; Xie, X.; Huang, C. Detection-based weighted H∞ LFC for multi-area power systems under DoS attacks. IET Control Theory Appl. 2019, 13, 1909–1919. [Google Scholar] [CrossRef]
- Ding, D.; Wang, Z.; Wei, G.; Alsaadi, F.E. Event-based security control for discrete-time stochastic systems. IET Control. Theory Appl. 2016, 10, 1808–1815. [Google Scholar] [CrossRef]
- Su, L.; Ye, D. A cooperative detection and compensation mechanism against Denial-of-Service attack for cyber-physical systems. Inf. Sci. 2018, 444, 122–134. [Google Scholar] [CrossRef]
- Sun, H.; Peng, C.; Yang, T.; Zhang, H.; He, W. Resilient control of networked control systems with stochastic denial of service attacks. Neurocomputing 2017, 270, 170–177. [Google Scholar] [CrossRef]
- Zhang, J.; Peng, C.; Masroor, S.; Sun, H.; Chai, L. Stability analysis of networked control systems with denial-of-service attacks. In Proceedings of the 2016 UKACC 11th International Conference on Control (CONTROL), Belfast, UK, 31 August–2 September 2016; pp. 1–6. [Google Scholar]
- Cheng, Z.; Yue, D.; Hu, S.; Chen, L. Resilient H∞ triggering control for uncertain discrete-time system against DoS attacks. In Proceedings of the IECON 2019-45th Annual Conference of the IEEE Industrial Electronics Society, Lisbon, Portugal, 14–17 October 2019; Volume 1, pp. 6285–6290. [Google Scholar]
- Magdy, G.; Shabib, G.; Elbaset, A.A.; Mitani, Y. Renewable power systems dynamic security using a new coordination of frequency control strategy based on virtual synchronous generator and digital frequency protection. Int. J. Electr. Power Energy Syst. 2019, 109, 351–368. [Google Scholar] [CrossRef]
- Gozde, H.; Taplamacioglu, M.C. Automatic generation control application with craziness based particle swarm optimization in a thermal power system. Int. J. Electr. Power Energy Syst. 2011, 33, 8–16. [Google Scholar] [CrossRef]
- Liu, S.; Luo, W.; Wu, L. Co-Design of Distributed Model-Based Control and Event-Triggering Scheme for Load Frequency Regulation in Smart Grids. IEEE Trans. Syst. Man, Cybern. Syst. 2018. [Google Scholar] [CrossRef]
- Wang, Y.; Xie, L.; De Souza, C.E. Robust control of a class of uncertain nonlinear systems. Syst. Control. Lett. 1992, 19, 139–149. [Google Scholar] [CrossRef]


| frequency deviation | generator inertia constant | ||
| generator mechanical output | generator damping coefficient | ||
| governor valve position | turbine time constant | ||
| wind farm power | governor time constant | ||
| solar farm power | drop constant | ||
| reference power from VSG | wind turbine time constant | ||
| virtual inertia power | solar system time constant | ||
| tie-line power | virtual rotor time constant | ||
| load change | inverter time constant | ||
| wind farm disturbance | synchronizing coefficient | ||
| solar farm disturbance | frequency bias | ||
| area control error | LFC gain | ||
| virtual primary control gain | virtual secondary control gain | ||
| virtual generator inertia constant | virtual generator damping coefficient |
| PARM | D | M | R | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Area 1 | 0.015 | 0.166 | 0.08 | 0.4 | 3 | 0.08 | 0.3493 | 1.3 | 1.5 | 0.04 | 0.9 | 10.4 | |
| Area 2 | 0.016 | 0.202 | 0.08 | 0.44 | 2.73 | 0.06 | 0.3827 | 1.3 | 1.5 | 0.04 | 0.9 | 10.4 |
| 1.5623 | 0.8325 | 212.1875 | |||
| 1.9073 | 0.7330 | 173.0745 | |||
| 2.2012 | 0.6788 | 159.1523 | |||
| 2.5284 | 0.6363 | 150.3286 | |||
| 2.9481 | 0.5981 | 143.5351 |
| 1000 | 0.6923 | 165.7411 | |||
| 500 | 0.7068 | 167.7314 | |||
| 333 | 0.7166 | 168.4863 | |||
| 250 | 0.7242 | 168.6135 | |||
| 200 | 0.7328 | 168.9756 |
| 5 | 1.2166 | ||
| 10 | 1.2392 | ||
| 15 | 1.2626 | ||
| 20 | 1.2870 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, Z.; Hu, S.; Ma, J. Resilient Event-Triggered Control for LFC-VSG Scheme of Uncertain Discrete-Time Power System under DoS Attacks. Energies 2020, 13, 1820. https://doi.org/10.3390/en13071820
Cheng Z, Hu S, Ma J. Resilient Event-Triggered Control for LFC-VSG Scheme of Uncertain Discrete-Time Power System under DoS Attacks. Energies. 2020; 13(7):1820. https://doi.org/10.3390/en13071820
Chicago/Turabian StyleCheng, Zihao, Songlin Hu, and Jieting Ma. 2020. "Resilient Event-Triggered Control for LFC-VSG Scheme of Uncertain Discrete-Time Power System under DoS Attacks" Energies 13, no. 7: 1820. https://doi.org/10.3390/en13071820
APA StyleCheng, Z., Hu, S., & Ma, J. (2020). Resilient Event-Triggered Control for LFC-VSG Scheme of Uncertain Discrete-Time Power System under DoS Attacks. Energies, 13(7), 1820. https://doi.org/10.3390/en13071820