EGCIR: Energy-Aware Graph Clustering and Intelligent Routing Using Supervised System in Wireless Sensor Networks
Abstract
1. Introduction
- A review of the literature on various secure and efficient routing protocols for low-power WSNs;
- Proposal of an energy-aware graph clustering with fault-tolerant routing using a supervised system for improving the network lifetime with secure data transmission;
- The improvement of network performance by the EGCIR protocol for different metrics in the comparison of other state-of-the-art solutions.
2. Related Work
3. Problem Background
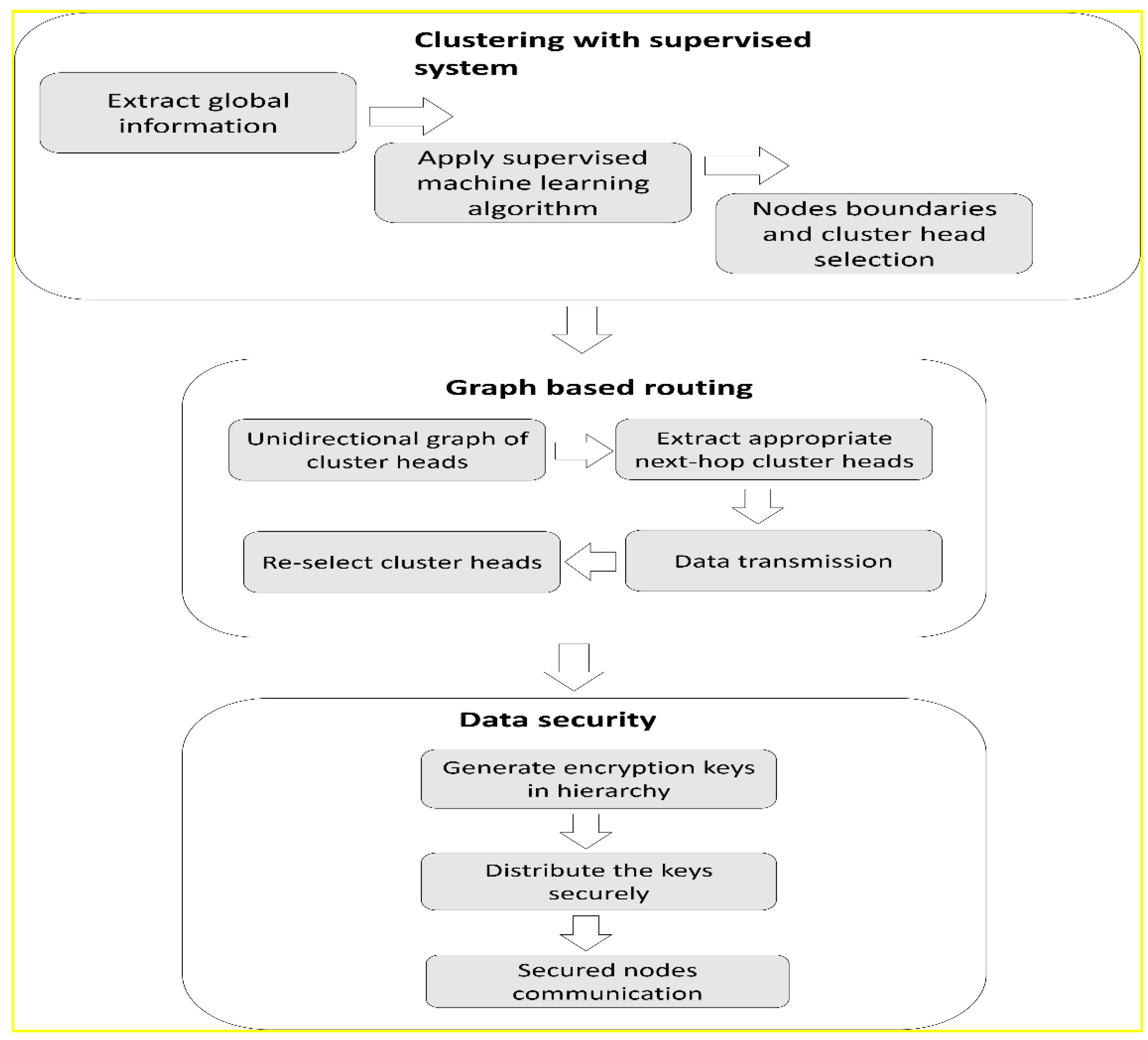
4. EGCIR Protocol
4.1. Assumptions
- i.
- The sensor nodes are distributed randomly;
- ii.
- Sensor nodes remain static after dispersal with restricted constraints;
- iii.
- After network deployment, nodes cannot be added or removed;
- iv.
- Neither the source nor receiver is faulty or malicious;
- v.
- The BS has unlimited resources in terms of processing, storage, transmission and energy;
- vi.
- Each node has equipped with a global positioning system (GPS) to identify its position.
4.2. Design of the EGCIR Protocol
4.3. Graph-Based Clustering with Supervised System
- i.
- If the source cluster head in graph is only one hop away from the BS, then the route is marked as optimal and data packets are forwarded directly to the BS;
- ii.
- If the source cluster head identifies multiple upstream cluster heads in the graph, the cluster head which meets energy, time edge and least transmission power requirements has given a higher priority;
- iii.
- If the upstream cluster head is already busy in data transmission, then it simply drops the route request (RREQ) packet and the source cluster head extracts the information for the next upstream cluster head in the graph. This leads to distribute the data traffic evenly and avoid the congestion on nodes.
4.4. Data Security with Hierarchical Key Distribution
5. Simulation Setup
6. Simulated Results
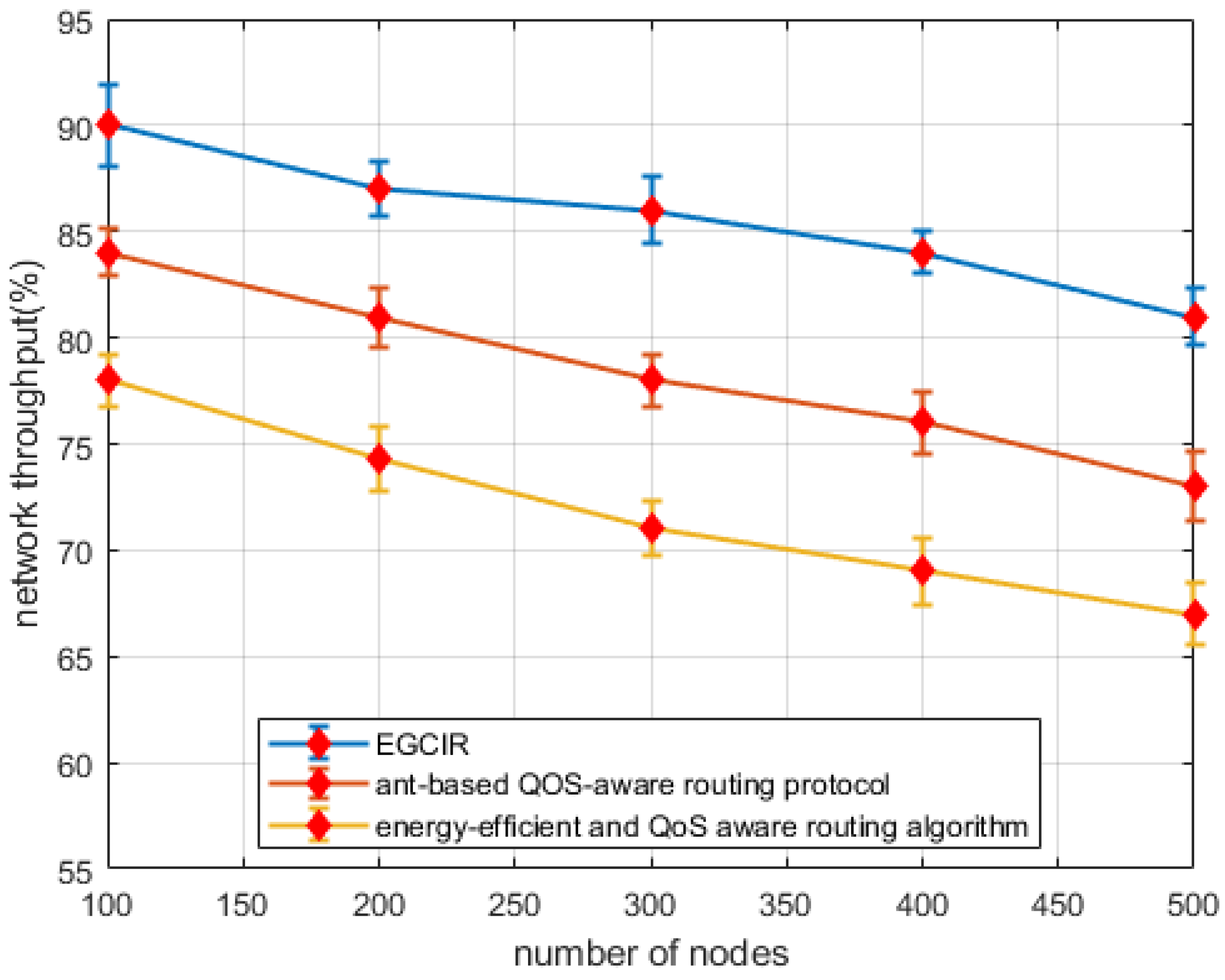
6.1. Network Throughput
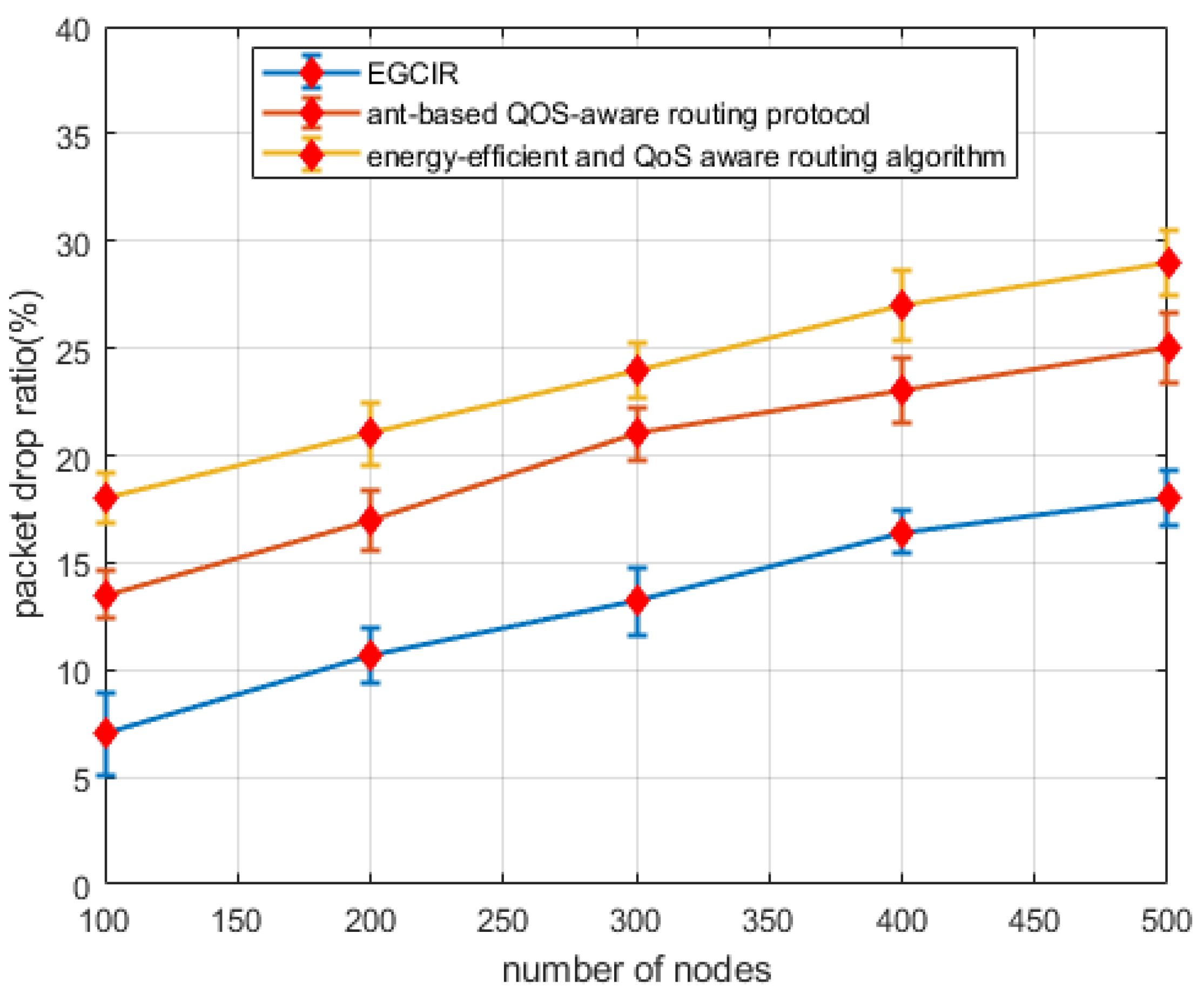
6.2. Packets Drop Ratio
6.3. Data Latency
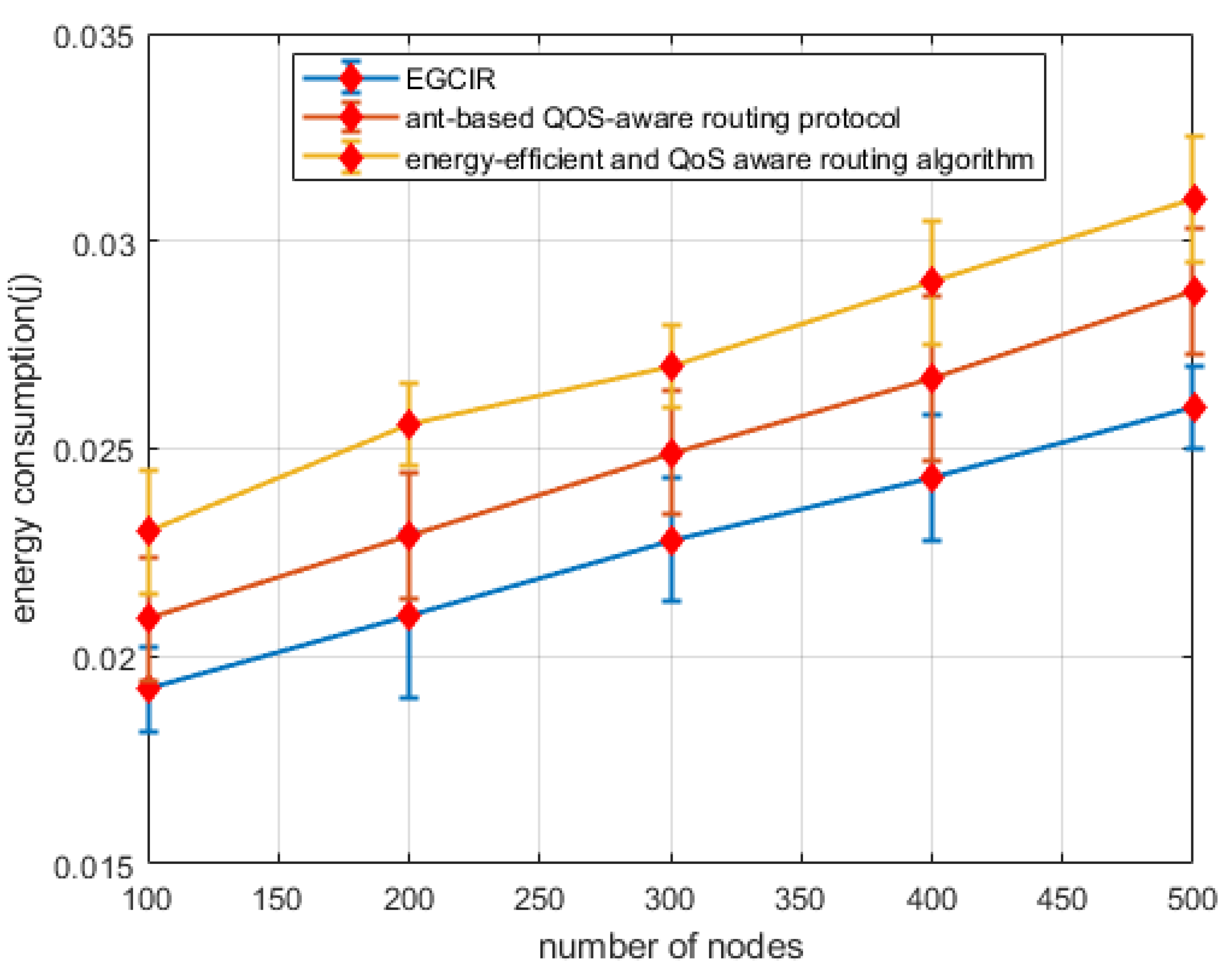
6.4. Energy Consumption
6.5. Data Breaches
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Rawat, P.; Singh, K.D.; Chaouchi, H.; Bonnin, J.M. Wireless sensor networks: A survey on recent developments and potential synergies. J. Supercomput. 2014, 68, 1–48. [Google Scholar] [CrossRef]
- Yang, M.; Li, Y.; Jin, D.; Zeng, L.; Wu, X.; Vasilakos, A.V. Software-defined and virtualized future mobile and wireless networks: A survey. Mob. Netw. Appl. 2015, 20, 4–18. [Google Scholar] [CrossRef]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L.H. A survey of network lifetime maximization techniques in wireless sensor networks. IEEE Commun. Surv. Tutor. 2017, 19, 828–854. [Google Scholar] [CrossRef]
- Din, I.U.; Asmat, H.; Guizani, M. A review of information centric network-based internet of things: Communication architectures, design issues, and research opportunities. Multimed. Tools Appl. 2019, 78, 30241–30256. [Google Scholar] [CrossRef]
- Ahmed, G.; Zou, J.; Zhao, X.; Fareed, M.M.S. Markov chain model-based optimal cluster heads selection for wireless sensor networks. Sensors 2017, 17, 440. [Google Scholar] [CrossRef]
- Hu, S.; Han, J.; Wei, X.; Chen, Z. A multi-hop heterogeneous cluster-based optimization algorithm for wireless sensor networks. Wirel. Netw. 2015, 21, 57–65. [Google Scholar] [CrossRef]
- Ucar, S.; Ergen, S.C.; Ozkasap, O. Multihop-cluster-based IEEE 802.11 p and LTE hybrid architecture for VANET safety message dissemination. IEEE Trans. Veh. Technol. 2015, 65, 2621–2636. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.; Guizani, M.; Khan, S. StabTrust—A stable and centralized trust-based clustering mechanism for IoT enabled vehicular ad-hoc networks. IEEE Access 2020, 8, 21159–21177. [Google Scholar] [CrossRef]
- Yuan, J.; Zhang, J.; Ding, S.; Dong, X. Cooperative localization for disconnected sensor networks and a mobile robot in friendly environments. Inf. Fusion 2017, 37, 22–36. [Google Scholar] [CrossRef]
- Bouaziz, M.; Rachedi, A.; Belghith, A. EC-MRPL: An energy-efficient and mobility support routing protocol for Internet of Mobile Things. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017. [Google Scholar]
- Chen, R.; Guo, J. Hierarchical trust management of community of interest groups in mobile ad hoc networks. Ad Hoc Netw. 2015, 33, 154–167. [Google Scholar] [CrossRef]
- Ullah, U.; Khan, A.; Zareei, M.; Ali, I.; Khattak, H.A.; Din, I.U. Energy-effective cooperative and reliable delivery routing protocols for underwater wireless sensor networks. Energies 2019, 12, 2630. [Google Scholar] [CrossRef]
- Guleria, K.; Verma, A.K. Comprehensive review for energy efficient hierarchical routing protocols on wireless sensor networks. Wirel. Netw. 2019, 25, 1159–1183. [Google Scholar] [CrossRef]
- Naureen, A.; Zhang, N.; Furber, S. Identifying energy holes in randomly deployed hierarchical wireless sensor networks. IEEE Access 2017, 5, 21395–21418. [Google Scholar] [CrossRef]
- Habib, M.A.; Moh, S. Game theory-based routing for wireless sensor networks: A comparative survey. Appl. Sci. 2019, 9, 2896. [Google Scholar] [CrossRef]
- Haseeb, K.; Islam, N.; Almogren, A.; Din, I.U. Intrusion prevention framework for secure routing in WSN-based mobile Internet of Things. IEEE Access 2019, 7, 185496–185505. [Google Scholar] [CrossRef]
- Pan, J.-S.; Dao, T.-K. A compact bat algorithm for unequal clustering in wireless sensor networks. Appl. Sci. 2019, 9, 1973. [Google Scholar]
- Jadoon, R.N.; Zhou, W.; Jadoon, W.; Khan, I.A. RARZ: Ring-zone based routing protocol for wireless sensor networks. Appl. Sci. 2018, 8, 1023. [Google Scholar] [CrossRef]
- Tang, L.; Chen, Z.; Cai, J.; Guo, H.; Wu, R.; Guo, J. Adaptive Energy Balanced Routing Strategy for Wireless Rechargeable Sensor Networks. Appl. Sci. 2019, 9, 2133. [Google Scholar] [CrossRef]
- Abuarqoub, A.; Hammoudeh, M.; Adebisi, B.; Jabbar, S.; Bounceur, A.; Al-Bashar, H. Dynamic clustering and management of mobile wireless sensor networks. Comput. Netw. 2017, 117, 62–75. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security in the integration of low-power Wireless Sensor Networks with the Internet: A survey. Ad Hoc Netw. 2015, 24, 264–287. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. Cyber physical systems security: Analysis, challenges and solutions. Comput. Secur. 2017, 68, 81–97. [Google Scholar] [CrossRef]
- Haseeb, K.; Islam, N.; Almogren, A.; Din, I.U.; Almajed, H.N.; Guizani, N. Secret sharing-based energy-aware and multi-hop routing protocol for IoT based WSNs. IEEE Access 2019, 7, 79980–79988. [Google Scholar] [CrossRef]
- Erol-Kantarci, M.; Mouftah, H.T. Wireless multimedia sensor and actor networks for the next generation power grid. Ad Hoc Netw. 2011, 9, 542–551. [Google Scholar] [CrossRef]
- Minoli, D.; Sohraby, K.; Occhiogrosso, B. IoT considerations, requirements, and architectures for smart buildings—Energy optimization and next-generation building management systems. IEEE Internet Things J. 2017, 4, 269–283. [Google Scholar] [CrossRef]
- García Villalba, L.J.; Sandoval Orozco, A.L.; Cabrera, A.T.; Abbas, C.J.B. Routing protocols in wireless sensor networks. Sensors 2009, 9, 8399–8421. [Google Scholar] [CrossRef]
- Bapu, B.T.; Gowd, L.S. Link quality based opportunistic routing algorithm for QOS: Aware wireless sensor networks security. Wirel. Pers. Commun. 2017, 97, 1563–1578. [Google Scholar] [CrossRef]
- Din, I.U.; Guizani, M.; Hassan, S.; Kim, B.-S.; Khan, M.K.; Atiquzzaman, M.; Ahmed, S.H. The Internet of Things: A review of enabled technologies and future challenges. IEEE Access 2018, 7, 7606–7640. [Google Scholar] [CrossRef]
- Virrankoski, R.; Savvidees, A. TASC: Topology adaptive spatial clustering for sensor networks. In Proceedings of the IEEE International Conference on Mobile Adhoc and Sensor Systems Conference, Washington, DC, USA, 7 November 2005. [Google Scholar]
- Shigei, N.; Morishita, H.; Miyajima, H. Energy efficient clustering communication based on number of neighbors for wireless sensor networks. In Proceedings of the International multi-conference on engineers and computer scientists (IMECS), Hong Kong, China, 17–19 March 2010. [Google Scholar]
- Bernas, M.; Płaczek, B. Fully connected neural networks ensemble with signal strength clustering for indoor localization in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 403242. [Google Scholar] [CrossRef]
- Srivastava, J.R.; Sudarshan, T. A genetic fuzzy system based optimized zone based energy efficient routing protocol for mobile sensor networks (OZEEP). Appl. Soft Comput. 2015, 37, 863–886. [Google Scholar] [CrossRef]
- Femminella, M.; Reali, G.; Valocchi, D.; Francescangeli, R.; Schulzrinne, H. Advanced caching for distributing sensor data through programmable nodes. In Proceedings of the 2013 19th IEEE Workshop on Local & Metropolitan Area Networks (LANMAN), Bussels, Belgium, 10–12 April 2013. [Google Scholar]
- Shabbir, N.; Hassan, S.R. Routing protocols for wireless sensor networks (WSNs). Wirel. Sens. Netw. Insights Innov. 2017. [Google Scholar] [CrossRef]
- Razzaque, M.A.; Ahmed, M.H.U.; Hong, C.S.; Lee, S. QoS-aware distributed adaptive cooperative routing in wireless sensor networks. Ad Hoc Netw. 2014, 19, 28–42. [Google Scholar] [CrossRef]
- Malik, S.K.; Dave, M.; Dhurandher, S.K.; Woungang, I.; Barolli, L. An ant-based QoS-aware routing protocol for heterogeneous wireless sensor networks. Soft Comput. 2017, 21, 6225–6236. [Google Scholar] [CrossRef]
- Zhang, W.; Liu, Y.; Han, G.; Feng, Y.; Zhao, Y. An energy efficient and QoS aware routing algorithm based on data classification for industrial wireless sensor networks. IEEE Access 2018, 6, 46495–46504. [Google Scholar] [CrossRef]
- Soucy, P.; Mineau, G.W. A simple KNN algorithm for text categorization. In Proceedings of the 2001 IEEE international Conference on Data Mining, San Jose, CA, USA, 29 November–2 December 2001. [Google Scholar]
- Pan, L.; Li, J. K-nearest neighbor based missing data estimation algorithm in wireless sensor networks. Wirel. Sens. Netw. 2010, 2, 115. [Google Scholar] [CrossRef]
- Singla, A.; Karambir, M. Comparative analysis & evaluation of euclidean distance function and manhattan distance function using k-means algorithm. Int. J. 2012, 2, 298–300. [Google Scholar]
- Mohibullah, M.; Hossain, M.Z.; Hasan, M. Comparison of euclidean distance function and manhattan distance function using k-mediods. Int. J. Comput. Sci. Inf. Secur. 2015, 13, 61. [Google Scholar]
- Zhou, X.; Tang, X. Research and implementation of RSA algorithm for encryption and decryption. In Proceedings of the 2011 6th International Forum on Strategic Technology, Harbin, Heilongjiang, China, 22–24 August 2011. [Google Scholar]
- Milanov, E. The RSA algorithm. RSA Labs. 2009, pp. 1–11. Available online: https://sites.math.washington.edu/~morrow/336_09/papers/Yevgeny.pdf (accessed on 4 August 2020).
- Kumar, A.A.; Rao, S.; Goswami, D. Ns3 simulator for a study of data center networks. In Proceedings of the 2013 IEEE 12th International Symposium on Parallel and Distributed Computing, Bucharest, Romania, 27–30 June 2013. [Google Scholar]
- Katkar, P.S.; D.Ghorpade, V.R. Comparative study of network simulator: NS2 and NS3. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2016, 6, 608–612. [Google Scholar]


| Id | and | Status | |||
|---|---|---|---|---|---|
| --- | ----------- | ----------- | ------------ | -------------- | -------- |
| Parameter | Value |
|---|---|
| Simulation area | 300 × 300 m2 |
| Deployment | Random |
| Sensor nodes | 100 to 500 |
| Simulation time | 1000 s |
| Malicious nodes | 10 |
| Packet size, k | 64 bits |
| Energy level | 5 J |
| Control message | 25 bits |
| Transmission range | 20 m |
| Traffic type | CBR |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saba, T.; Haseeb, K.; Ud Din, I.; Almogren, A.; Altameem, A.; Fati, S.M. EGCIR: Energy-Aware Graph Clustering and Intelligent Routing Using Supervised System in Wireless Sensor Networks. Energies 2020, 13, 4072. https://doi.org/10.3390/en13164072
Saba T, Haseeb K, Ud Din I, Almogren A, Altameem A, Fati SM. EGCIR: Energy-Aware Graph Clustering and Intelligent Routing Using Supervised System in Wireless Sensor Networks. Energies. 2020; 13(16):4072. https://doi.org/10.3390/en13164072
Chicago/Turabian StyleSaba, Tanzila, Khalid Haseeb, Ikram Ud Din, Ahmad Almogren, Ayman Altameem, and Suliman Mohamed Fati. 2020. "EGCIR: Energy-Aware Graph Clustering and Intelligent Routing Using Supervised System in Wireless Sensor Networks" Energies 13, no. 16: 4072. https://doi.org/10.3390/en13164072
APA StyleSaba, T., Haseeb, K., Ud Din, I., Almogren, A., Altameem, A., & Fati, S. M. (2020). EGCIR: Energy-Aware Graph Clustering and Intelligent Routing Using Supervised System in Wireless Sensor Networks. Energies, 13(16), 4072. https://doi.org/10.3390/en13164072






