Privacy-Preserving Electricity Billing System Using Functional Encryption †
Abstract
:1. Introduction
2. Preliminaries: Function-Hiding Inner Product Functional Encryption
- : Given a security parameter , the setup algorithm outputs the public parameters and the master secret key corresponding to . More precisely, the setup algorithm samples an asymmetric bilinear group , where and are two distinct groups of prime order q, and is a function that maps two elements from and onto a target group , also of prime order q. The setup algorithm then chooses generators and . Next, the algorithm samples , where is the general linear group of matrices over . Throughout the paper, bold uppercase letters, e.g., , refer to matrices. Then, the algorithm sets , where and denote the determinant of and the transpose matrix of , respectively. Finally, the setup algorithm outputs the public parameters and the master secret key .
- : Given the master secret key and a vector , the key generation algorithm chooses a uniformly random element and outputs a secret key:Note that the second component of is a vector of group elements. That is, according to the notation in Reference [30], for a group element and a row vector , denotes the vector of group elements, .
- : Given the master secret key and an input vector , the encryption algorithm chooses a uniformly random element and outputs a ciphertext:
- : Given the public parameters , a secret key , and a ciphertext , the decryption algorithm computes:Then, the algorithm checks whether there exists z, such that , and either outputs z or an error symbol implying that decryption is impossible. If there is such z, it satisfies . In other words, z is the inner product of and .
3. Privacy-Preserving Electricity Billing System
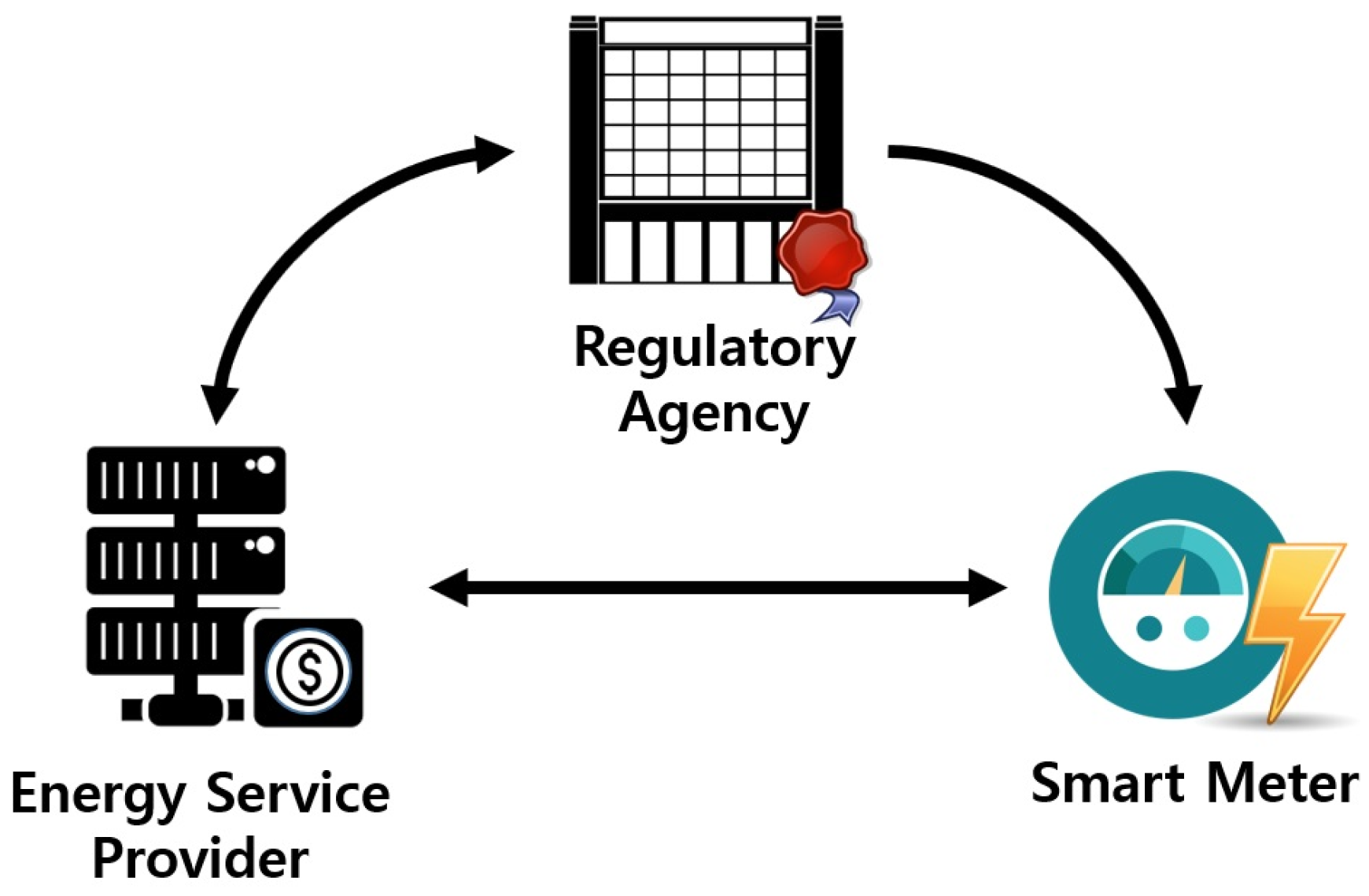
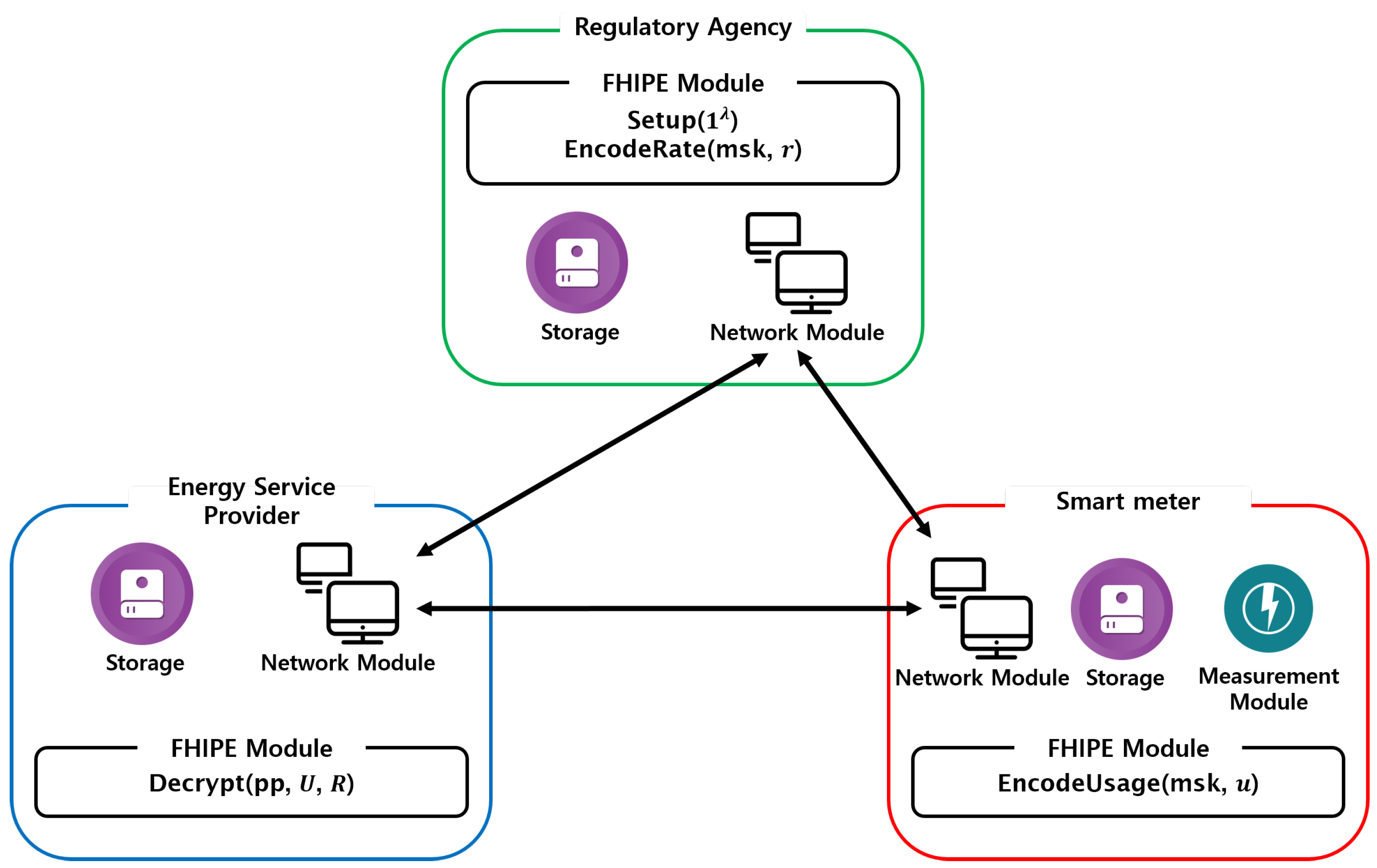
3.1. System Model
3.2. Representation of Power Consumption Data
3.3. Redefining the Roles of KeyGen and Encrypt
3.4. Proposed Privacy-Preserving Electricity Billing Protocol
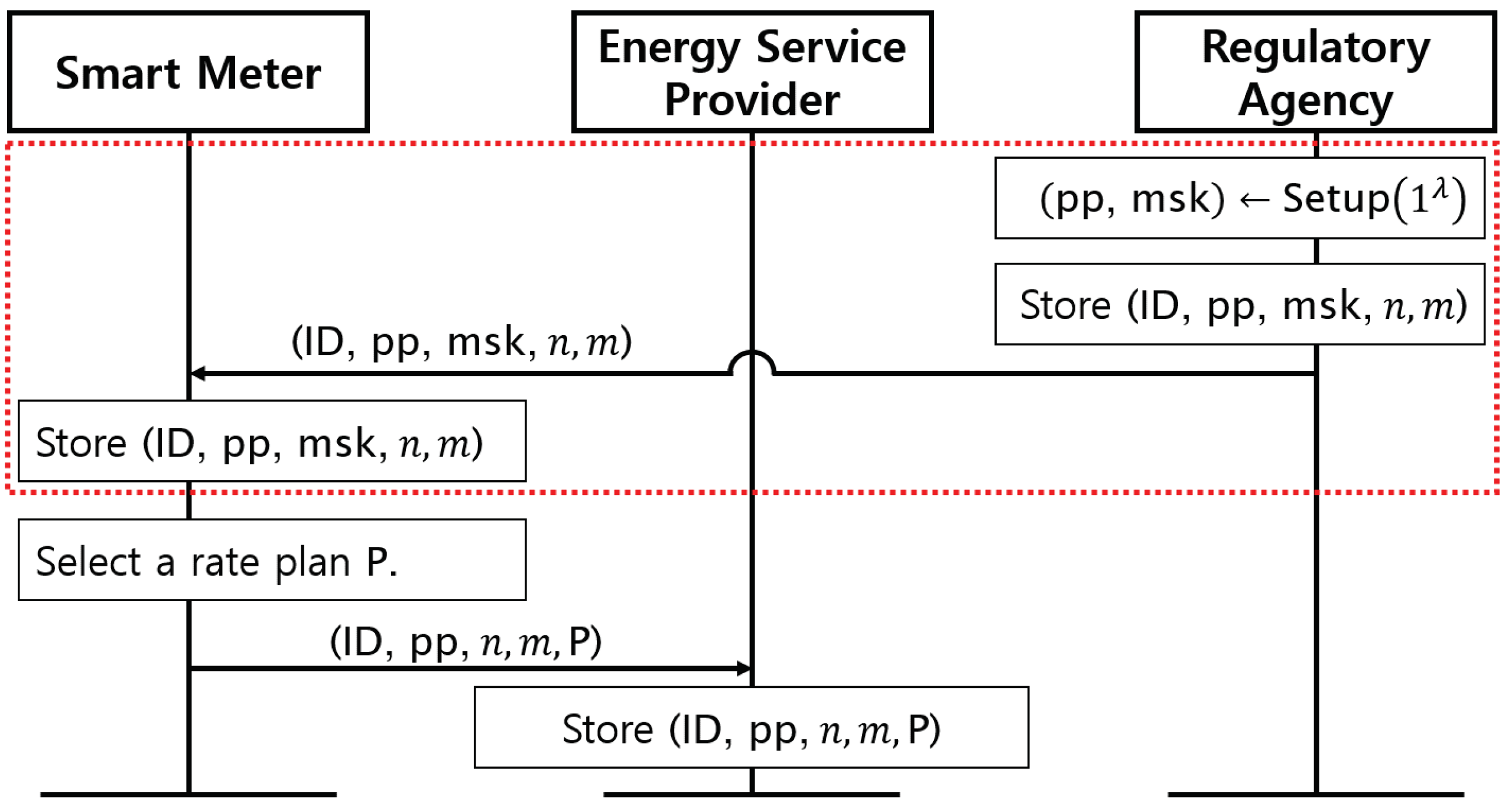
3.4.1. Registration Stage of Proposed Protocol
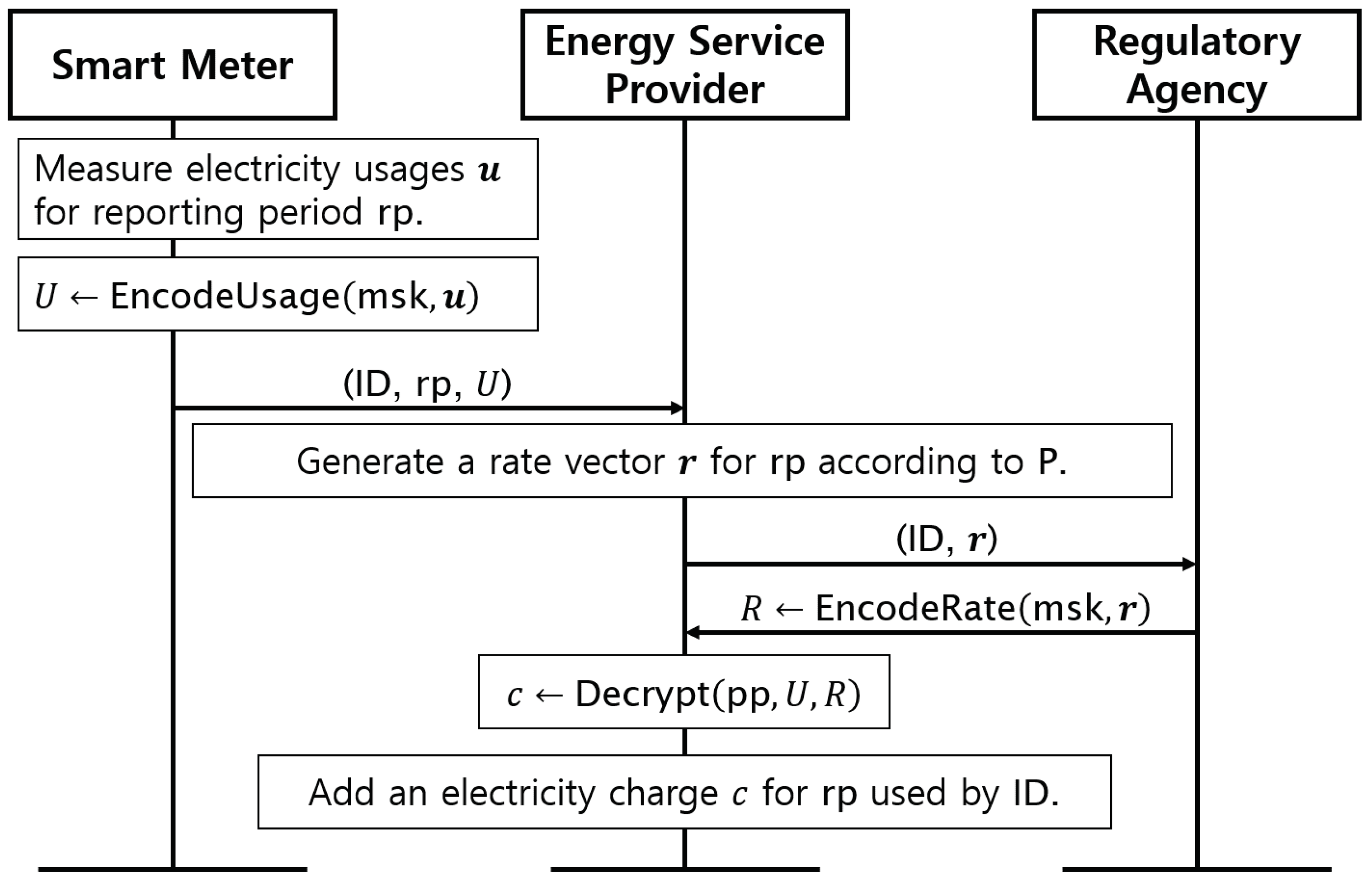
3.4.2. Reporting Stage of Proposed Protocol
4. Security Analysis
4.1. Review of Security for the FHIPE Scheme
- -
- Key generation oracle.On inputting a pair of vectors , the challenger computes and returns .
- -
- Encryption oracle.On inputting a pair of vectors , the challenger computes and returns .
4.2. Security for the Proposed Privacy-Preserving Electricity Billing Protocol
- -
- Usage encoding oracle.On inputting a pair of vectors , the challenger computes and returns using of .
- -
- Rate encoding oracle.On inputting a vector , the challenger computes and returns using of .
| Algorithm 1 Construction of using |
| Input: public parameters . Output: a bit .
|
5. Experimental Results
6. Discussion
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| TOU | Time-Of-Use |
| RTP | Real-Time Pricing |
| NIALM | Non-Intrusive Appliance Load Monitoring |
| FHIPE | Function-Hiding Inner Product Encryption |
| ESP | Energy Service Provider |
| RA | Regulatory Agency |
References
- Faruqui, A.; Hledik, R.; Palmer, J. Time-Varying and Dynamic Rate Design. 2012. Available online: https://www.raponline.org/knowledge-center/time-varying-and-dynamic-rate-design/ (accessed on 17 January 2019).
- PG&E. Understand the PG&E Tiered Rate Plan. Available online: https://www.pge.com/enUS/residential/rate-plans/rate-plan-options/tiered-base-plan/tiered-base-plan.page (accessed on 17 January 2019).
- Wang, Z.; Li, F. Critical peak pricing tariff design for mass consumers in Great Britain. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–29 July 2011; pp. 1–6. [Google Scholar] [CrossRef]
- US Department of Energy’s Office of Electricity Delivery and Energy Reliability. Advanced Metering Infrastructure and Customer Systems: Results from the Smart Grid Investment Grant Program. Available online: https://www.smartgrid.gov/document/SGIG_Results_for_AMI_and_Customer_Systems_2016.html (accessed on 17 January 2019).
- McDaniel, P.D.; McLaughlin, S.E. Security and Privacy Challenges in the Smart Grid. IEEE Secur. Priv. 2009, 7, 75–77. [Google Scholar] [CrossRef]
- Hart, G.W. Nonintrusive appliance load monitoring. Proc. IEEE 1992, 80, 1870–1891. [Google Scholar] [CrossRef]
- Baranski, M.; Voss, J. Genetic algorithm for pattern detection in NIALM systems. In Proceedings of the 2004 IEEE International Conference on Systems, Man and Cybernetics (IEEE Cat. No.04CH37583), The Hague, The Netherlands, 10–13 October 2004; pp. 3462–3468. [Google Scholar] [CrossRef]
- Zeifman, M.; Roth, K. Nonintrusive appliance load monitoring: Review and outlook. IEEE Trans. Consum. Electron. 2011, 57, 76–84. [Google Scholar] [CrossRef]
- Kim, H.; Marwah, M.; Arlitt, M.F.; Lyon, G.; Han, J. Unsupervised Disaggregation of Low Frequency Power Measurements. In Proceedings of the Eleventh SIAM International Conference on Data Mining, Mesa, AZ, USA, 28–30 April 2011; pp. 747–758. [Google Scholar] [CrossRef]
- Kolter, J.Z.; Jaakkola, T.S. Approximate Inference in Additive Factorial HMMs with Application to Energy Disaggregation. In Proceedings of the Fifteenth International Conference on Artificial Intelligence and Statistics, La Palma, Spain, 21–23 April 2012; pp. 1472–1482. [Google Scholar]
- Zoha, A.; Gluhak, A.; Imran, M.A.; Rajasegarar, S. Non-intrusive load monitoring approaches for disaggregated energy sensing: A survey. Sensors 2012, 12, 16838–16866. [Google Scholar] [CrossRef] [PubMed]
- Parson, O.; Ghosh, S.; Weal, M.J.; Rogers, A. Non-Intrusive Load Monitoring Using Prior Models of General Appliance Types. In Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence, Toronto, ON, Canada, 22–26 July 2012; pp. 356–362. [Google Scholar]
- Vogiatzis, E.; Kalogridis, G.; Denic, S.Z. Real-time and low cost energy disaggregation of coarse meter data. In Proceedings of the 4th IEEE PES Innovative Smart Grid Technologies Europe, Lyngby, Denmark, 6–9 October 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Eibl, G.; Engel, D. Influence of data granularity on smart meter privacy. IEEE Trans. Smart Grid 2015, 6, 930–939. [Google Scholar] [CrossRef]
- Lisovich, M.A.; Mulligan, D.K.; Wicker, S.B. Inferring Personal Information from Demand-Response Systems. IEEE Secur. Priv. 2010, 8, 11–20. [Google Scholar] [CrossRef]
- Greveler, U.; Justus, B.; Löhr, D. Multimedia Content Identification Through Smart Meter Power Usage Profiles. In Proceedings of the Computers, Privacy and Data Protection (CPDP 2012), Brussels, Belgium, 25–27 January 2012. [Google Scholar]
- Engel, D. Wavelet-based load profile representation for smart meter privacy. In Proceedings of the IEEE PES Innovative Smart Grid Technologies Conference, Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Engel, D.; Eibl, G. Multi-resolution load curve representation with privacy-preserving aggregation. In Proceedings of the 4th IEEE PES Innovative Smart Grid Technologies Europe, Lyngby, Denmark, 6–9 October 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Erkin, Z.; Troncoso-pastoriza, J.R.; Lagendijk, R.L.; Perez-Gonzalez, F. Privacy-preserving data aggregation in smart metering systems: An overview. IEEE Signal Process. Mag. 2013, 30, 75–86. [Google Scholar] [CrossRef]
- Efthymiou, C.; Kalogridis, G. Smart Grid Privacy via Anonymization of Smart Metering Data. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar] [CrossRef]
- Bohli, J.; Sorge, C.; Ugus, O. A Privacy Model for Smart Metering. In Proceedings of the 2010 IEEE International Conference on Communications Workshops, Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Kim, Y.; Ngai, E.C.H.; Srivastava, M.B. Cooperative state estimation for preserving privacy of user behaviors in smart grid. In Proceedings of the IEEE Second International Conference on Smart Grid Communications, Brussels, Belgium, 17–20 October 2011; pp. 178–183. [Google Scholar] [CrossRef]
- Erkin, Z.; Tsudik, G. Private Computation of Spatial and Temporal Power Consumption with Smart Meters. In Proceedings of the Applied Cryptography and Network Security-10th International Conference, Singapore, 26–29 June 2012; pp. 561–577. [Google Scholar] [CrossRef]
- Kursawe, K.; Danezis, G.; Kohlweiss, M. Privacy-Friendly Aggregation for the Smart-Grid. In Proceedings of the Privacy Enhancing Technologies-11th International Symposium, Waterloo, ON, Canada, 27–29 July 2011; pp. 175–191. [Google Scholar] [CrossRef]
- Ács, G.; Castelluccia, C. I Have a DREAM! (DiffeRentially privatE smArt Metering). In Proceedings of the 13th International Conference on Information Hiding, Prague, Czech Republic, 18–20 May 2011; pp. 118–132. [Google Scholar] [CrossRef]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar] [CrossRef]
- Garcia, F.D.; Jacobs, B. Privacy-Friendly Energy-Metering via Homomorphic Encryption. In Proceedings of the 6th International Workshop on Security and Trust Management, Athens, Greece, 23–24 September 2010; pp. 226–238. [Google Scholar] [CrossRef]
- Sahai, A.; Seyalioglu, H. Worry-free Encryption: Functional Encryption with Public Keys. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 463–472. [Google Scholar]
- Garg, S.; Gentry, C.; Halevi, S.; Raykova, M.; Sahai, A.; Waters, B. Candidate Indistinguishability Obfuscation and Functional Encryption for All Circuits. In Proceedings of the 2013 IEEE 54th Annual Symposium on Foundations of Computer Science, Berkeley, CA, USA, 26–29 October 2013; pp. 40–49. [Google Scholar]
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption Is Practical. In Proceedings of the Security and Cryptography for Networks (SCN 2018), Amalfi, Italy, 5–7 September 2018; pp. 544–562. [Google Scholar]
- Bishop, A.; Jain, A.; Kowalczyk, L. Function-Hiding Inner Product Encryption. In Proceedings of the 21st International Conference on Advances in Cryptology (ASIACRYPT 2015), Auckland, New Zealand, 29 November–3 December 2015; pp. 470–491. [Google Scholar]
- Abdalla, M.; Bourse, F.; De Caro, A.; Pointcheval, D. Simple Functional Encryption Schemes for Inner Products. In Proceedings of the Public-Key Cryptography—PKC 2015, Gaithersburg, MD, USA, 30 March–1 April 2015; pp. 733–751. [Google Scholar]
- Datta, P.; Dutta, R.; Mukhopadhyay, S. Functional Encryption for Inner Product with Full Function Privacy. In Proceedings of the Public-Key Cryptography—PKC, Taipei, Taiwan, 6–9 March 2016; pp. 164–195. [Google Scholar]
- Kim, S.; Kim, J.; Seo, J.H. A New Approach for Practical Function-Private Inner Product Encryption. Available online: https://eprint.iacr.org/2017/004 (accessed on 29 March 2019).
- US Department of Energy’s Office of Electricity Delivery and Energy Reliability. Time Based Rate Programs. Available online: https://www.smartgrid.gov/recovery_act/time_based_rate_programs.html (accessed on 17 January 2019).
- Korea Electricity Regulatory Commission. Available online: http://www.korec.go.kr/intrcn/moveObjectiveAndStatus.do (accessed on 18 March 2019).
- Federal Energy Regulatory Commission. Available online: https://www.ferc.gov/ (accessed on 18 March 2019).
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption Is Practical. Available online: https://eprint.iacr.org/2016/440.pdf (accessed on 29 March 2019).
- The Pairing-Based Cryptography Library (PBC). Available online: https://crypto.stanford.edu/pbc/ (accessed on 17 January 2019).
- GNU Multiple Precision Arithmetic Library (GMP). Available online: https://gmplib.org/ (accessed on 17 January 2019).
- A Library for Doing Number Theory (NTL). Available online: https://www.shoup.net/ntl/ (accessed on 17 January 2019).
- Shanks, D. Class number, a theory of factorization, and genera. Proc. Symp. Math. Soc. 1971, 20, 415–440. [Google Scholar]
- KEPCO Smart Power Management (iSMART). Available online: https://pccs.kepco.co.kr/iSmart/ (accessed on 15 February 2019).
- KEPCO Electricity Tariffs. Available online: http://cyber.kepco.co.kr/ckepco/front/jsp/CY/E/E/CYEEHP00101.jsp (accessed on 15 February 2019).
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
| Dataset | Building Type | Period | #Records | Min. (kWh) | Max. (kWh) | Avg. (kWh) |
|---|---|---|---|---|---|---|
| A | Apartment | January 2018–December 2018 | 365 | 0.04 | 64.84 | 21.58 |
| C | Commercial | January 2018–December 2018 | 365 | 17.47 | 77.62 | 40.36 |
| F | Factory | January 2018–December 2018 | 365 | 3.90 | 1096.50 | 320.18 |
| Setup | Store | Store | Store | Network | Total Time |
|---|---|---|---|---|---|
| 11.54 | 0.53 | 9.51 | 0.02 | 24.39 | 45.99 |
| Dataset | #Reports | Encode | Encode | Decrypt | Network | Total Time |
|---|---|---|---|---|---|---|
| A | 4380 | 60.23 | 42.82 | 397.44 | 14.25 | 514.75 |
| C | 4380 | 60.33 | 42.81 | 400.39 | 14.26 | 517.80 |
| F | 4380 | 60.48 | 42.79 | 424.77 | 14.33 | 542.37 |
| Average | 60.35 | 42.81 | 407.53 | 14.28 | 524.97 | |
| Registration | Reporting | ||||
|---|---|---|---|---|---|
| Dataset | |||||
| 7770 | 860 | A | 1736 | 875 | 3351 |
| C | 1740 | 878 | 3351 | ||
| F | 1735 | 871 | 3351 | ||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Im, J.-H.; Kwon, H.-Y.; Jeon, S.-Y.; Lee, M.-K. Privacy-Preserving Electricity Billing System Using Functional Encryption. Energies 2019, 12, 1237. https://doi.org/10.3390/en12071237
Im J-H, Kwon H-Y, Jeon S-Y, Lee M-K. Privacy-Preserving Electricity Billing System Using Functional Encryption. Energies. 2019; 12(7):1237. https://doi.org/10.3390/en12071237
Chicago/Turabian StyleIm, Jong-Hyuk, Hee-Yong Kwon, Seong-Yun Jeon, and Mun-Kyu Lee. 2019. "Privacy-Preserving Electricity Billing System Using Functional Encryption" Energies 12, no. 7: 1237. https://doi.org/10.3390/en12071237
APA StyleIm, J.-H., Kwon, H.-Y., Jeon, S.-Y., & Lee, M.-K. (2019). Privacy-Preserving Electricity Billing System Using Functional Encryption. Energies, 12(7), 1237. https://doi.org/10.3390/en12071237





