Abstract
The development of smart meters that can frequently measure and report power consumption has enabledelectricity providers to offer various time-varying rates, including time-of-use and real-time pricing plans. High-resolution power consumption data, however, raise serious privacy concerns because sensitive information regarding an individual’s lifestyle can be revealed by analyzing these data. Although extensive research has been conducted to address these privacy concerns, previous approaches have reduced the quality of measured data. In this paper, we propose a new privacy-preserving electricity billing method that does not sacrifice data quality for privacy. The proposed method is based on the novel use of functional encryption. Experimental results on a prototype system using a real-world smart meter device and data prove the feasibility of the proposed method.
1. Introduction
The traditional electricity metering and billing method, in particular for residential consumers, involved installing simple electromechanical meters that could be read manually. Meters were typically read monthly, and customers were charged a rate proportional to their monthly usage. In this situation, the only option an electricity provider could offer was a “flat” or “fixed” rate, with only slight variations such as increasing the unit price as consumption increases over the course of the billing period [1]. A typical implementation of this policy is a “tiered” rate plan [2].
With the development and extensive deployment of smart meters, however, providers are now offering various time-varying rates. The time-of-use (TOU) rate plan divides the day into time periods and sets a different rate for each period [1]. There are other pricing variations as well, such as critical peak pricing (CPP) and peak-time rebates (PTR). The most advanced type of plan is real-time pricing (RTP), which allows price change per hour or even half hour [1,3]. The billing formula for these nonflat rates can be simplified as follows:
where n is the number of unit time periods per billing period, is the electricity price for time period i, and is the amount of electricity consumed in time period i. Alternatively, the electricity charge can be represented as the inner product:
of two n-dimensional vectors, and .
When smart meters measure and report power consumption data more frequently, consumers can adopt more fine-grained plans regarding their usage. Currently deployed smart meters already deliver load data with very high resolution, e.g., at five-minute intervals [4]. However, these detailed power consumption data raise serious privacy concerns, because personal data can be inferred from the energy use profiles measured by smart meters [5]. Recent advances in non-intrusive appliance load monitoring (NIALM) and disaggregation techniques make it possible to extract the energy consumption statistics of an individual appliance from aggregated data involving many appliances [6,7,8,9,10,11,12,13]. Although the primary goal of these algorithms is to provide the consumer with useful energy feedback, such NIALM analyses might be misused, compromising privacy by monitoring the consumer’s appliance usage patterns [14]. Advanced NIALM analysis can reveal significant information regarding the persons in a household, such as their presence, sleep schedule, and meal times [15]. In extreme cases, if the sampling interval is sufficiently small, even the television channel that is being watched can be identified, along with audiovisual content [16]. According to the quantitative analysis in Reference [14], to guarantee that all appliances are privacy-safe, the measurement interval of a smart meter should be at least one hour, which is significantly longer than the time resolution of state-of-the-art smart meters.
Consequently, there has been extensive research to resolve this privacy issue [17,18,19]. Previous approaches can be classified into the following three categories: (i) Providing only low-resolution data, i.e., data with decreased time granularity [14,17,18,20], (ii) perturbation or obfuscation of the measured data by adding controlled noise [21,22,23], and (iii) aggregation of data from multiple smart meters using a trusted third party [21], masking [24,25], or additive homomorphic encryption [23,26,27]. However, all of the above methods essentially reduce the quality of the measured data. Consequently, they cannot be used for granular billing that requires high-resolution metering data from a single smart meter. As such, there is a tradeoff between the functionality of smart meters and the privacy of customers.
In this paper, we aim at achieving both functionality and privacy by taking a completely different approach to privacy-preserving billing methods. Our method allows a smart meter to send the provider all measured data with full granularity and without privacy leaks. Our proposal is based on the novel use of a recently developed advanced cryptographic primitive, viz. the functional encryption (FE) algorithm [28,29,30]. Using the proposed system, a smart meter encrypts the measured consumption data and sends them to the electricity provider. The provider is provided with a restricted decryption key associated with , with which it cannot directly recover u, and only obtains the weighted sum (Equation (2)). This approach naturally resolves the privacy issue because the provider never sees the individual consumption statistic for each time period. To verify the feasibility of the proposed method, we implemented a prototype billing system composed of a smart meter, a provider’s billing server, and a regulatory agency. In particular, we used an off-the-shelf smart meter device to represent a real-world scenario. The proposed system does not require special-purpose hardware. It is realized merely through a software update of the smart meter. Our experimental results with real measurement data prove that the proposed system performs well with currently deployed smart meters, eliminating the need to decrease data granularity. According to the experimental results, only 0.5 s are required for the entire procedure, including the tasks for the smart meter to encrypt the consumption data u and for the provider to compute the weighted sum. It should be noted that the proposed method does not render previous methods obsolete; rather, it can be combined for advanced services. For example, it may be possible to use the new method for billing and either an aggregation or perturbation method for power generation and distribution network control.
2. Preliminaries: Function-Hiding Inner Product Functional Encryption
Functional encryption (FE)is an encryption schemethat supports operations on encrypted data [28,29]. In FE schemes, the owner of the master key can delegate arbitrary secret keys that allow decryptors to learn only specific functions of the data. For example, given a ciphertext of a message x and a secret key restricted to a function f, the decryptor only receives the value , and does not learn anything about x. If the data of FE are represented as a vector and the function f is defined as the inner product of with a predefined vector , then a decryptor can recover the inner product by inputting the ciphertext of vector and the restricted secret key associated with . This FE scheme is called an inner product encryption (IPE) scheme [30,31,32,33,34].
Some IPE schemes provide an additional property, viz. function hiding. In these schemes, both and are kept secret from the decryptor, even though the decryptor possesses the secret key associated with . In 2015, Bishop et al. first proposed function-hiding inner product encryption (FHIPE), which considered these capabilities [31]. Moreover, extensive research is currently under way to improve the performance of the FHIPE [30,32,33,34]. In this paper, we used the practical scheme proposed by Kim et al. in 2018 [30]. The scheme consists of four probabilistic polynomial time (PPT) algorithms, and as follows. For more details regarding the operations using bilinear groups, refer to Reference [30].
- : Given a security parameter , the setup algorithm outputs the public parameters and the master secret key corresponding to . More precisely, the setup algorithm samples an asymmetric bilinear group , where and are two distinct groups of prime order q, and is a function that maps two elements from and onto a target group , also of prime order q. The setup algorithm then chooses generators and . Next, the algorithm samples , where is the general linear group of matrices over . Throughout the paper, bold uppercase letters, e.g., , refer to matrices. Then, the algorithm sets , where and denote the determinant of and the transpose matrix of , respectively. Finally, the setup algorithm outputs the public parameters and the master secret key .
- : Given the master secret key and a vector , the key generation algorithm chooses a uniformly random element and outputs a secret key:Note that the second component of is a vector of group elements. That is, according to the notation in Reference [30], for a group element and a row vector , denotes the vector of group elements, .
- : Given the master secret key and an input vector , the encryption algorithm chooses a uniformly random element and outputs a ciphertext:
- : Given the public parameters , a secret key , and a ciphertext , the decryption algorithm computes:Then, the algorithm checks whether there exists z, such that , and either outputs z or an error symbol implying that decryption is impossible. If there is such z, it satisfies . In other words, z is the inner product of and .
An important property of the above FHIPE is that the decryptor computes from and but does not learn anything about either or . It should be noted that the roles of and are symmetric. This symmetry is used to design our system, as explained in the next section (see Section 3.3).
3. Privacy-Preserving Electricity Billing System
3.1. System Model
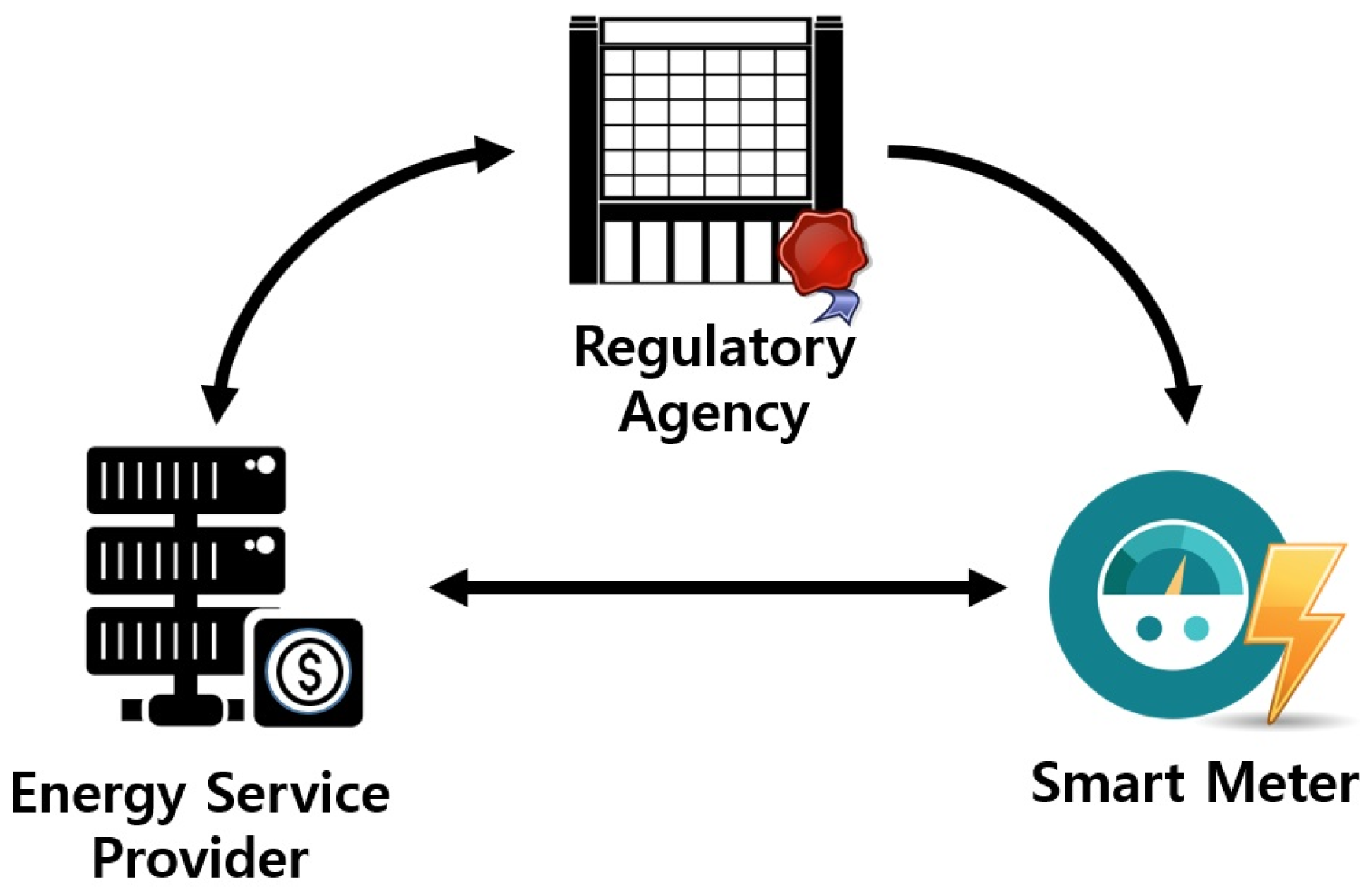
Figure 1 shows the proposed system model. We considered a system involving three parties: An energy service provider (ESP), a smart meter, and a regulatory agency (RA). The ESP is a company that wants to collect electricity charges in return for the electricity used by smart meter owners. The smart meter is a device that periodically reports the power consumption of its owner, who agrees to pay the electricity charges, yet prefers to hide power usage patterns from the ESP. Because electric power companies are generally monopolies, it is common for RAs to approve prices for electricity [35]. Our model reflects this situation and considers the RA to be a trusted third party with the following roles: (i) Generating the master secret key and public parameters for FHIPE at the registration stage of a smart meter, and (ii) encoding the electricity price for each time period according to the request of the ESP. We remark that the security of the proposed system relies on the trusted RA. That is, if the RA is compromised, the privacy of users may be invaded. Therefore, appropriate technical measures should be provided to protect the RA. In addition, we should consider the possibility that the RA might collude with the ESP. However, as the examples of RA, we considered government agencies such as the Korea Electricity Regulatory Commission or the US Federal Energy Regulatory Commission [36,37]. These government agencies aim to protect consumers’ rights and interests [36] and assist consumers in obtaining economically efficient, safe, reliable, and secure energy services at a reasonable cost through appropriate regulatory and market means [37]. Therefore, it is reasonable to assume that they would not collude with the ESP. Because RA is a trusted party, it never deviates from the protocol. We assume that the smart meter is tamper-proof, and accurately measures and reports the electricity usage. Finally, we assume that ESP is honest-but-curious, i.e., it performs the billing protocol honestly and correctly, but might try to extract useful information about the electricity usage patterns if the data from the smart meter are not encrypted.
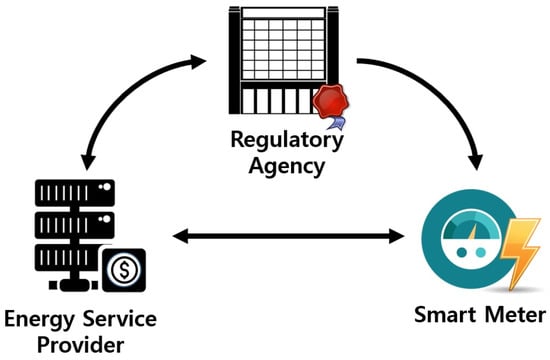
Figure 1.
Proposed system model.
3.2. Representation of Power Consumption Data
For our billing system, we generalized the billing Formulas (1) and (2) as follows. We first defined a reporting period as the time interval at which the smart meter reports the measured data to the ESP. This is not necessarily the same as the measurement interval. Therefore, let n be the number of measurements of power consumption data in each reporting period. For example, if the length of a reporting period is two hours and the measurement interval is 15 min, then . Let be the electricity consumption measured at the i-th measurement interval in a reporting period. Let be the electricity rate at the i-th interval. Then, the electricity charge c for this reporting period can be determined by the inner product:
of the rate vector with the consumption vector .
3.3. Redefining the Roles of KeyGen and Encrypt
In this paper, we used the FHIPE scheme proposed in Reference [30]. As explained in Section 2, the algorithms and hide the vectors and , respectively, from the decryptor. Although was named “key generation” and its result was defined as a secret key associated with , can also be viewed as a ciphertext of . Then, the decryption algorithm essentially computes the inner product of the two hidden vectors and given the two input ciphertexts and . This property was already mentioned in Reference [30] as a building block to construct a general two-input functional encryption. In Reference [38] (the full version of [30]), and were redefined as “left” and “right” encryption algorithms, respectively. Moreover, it was estimated in Reference [30] that the speed of was faster than that of by 1.8 to 5.3 times. Because it is reasonable to assume that the smart meter is the most resource-constrained among the three parties in Figure 1, we designed our protocol such that the smart meter can hide the measured power consumption data vector by performing the lighter algorithm (i.e., the left encryption ), instead of (i.e., the right encryption).
3.4. Proposed Privacy-Preserving Electricity Billing Protocol
In this section, we present the privacy-preserving electricity billing protocol, , for our system. The protocol comprises two stages: The registration stage and the reporting stage.
3.4.1. Registration Stage of Proposed Protocol
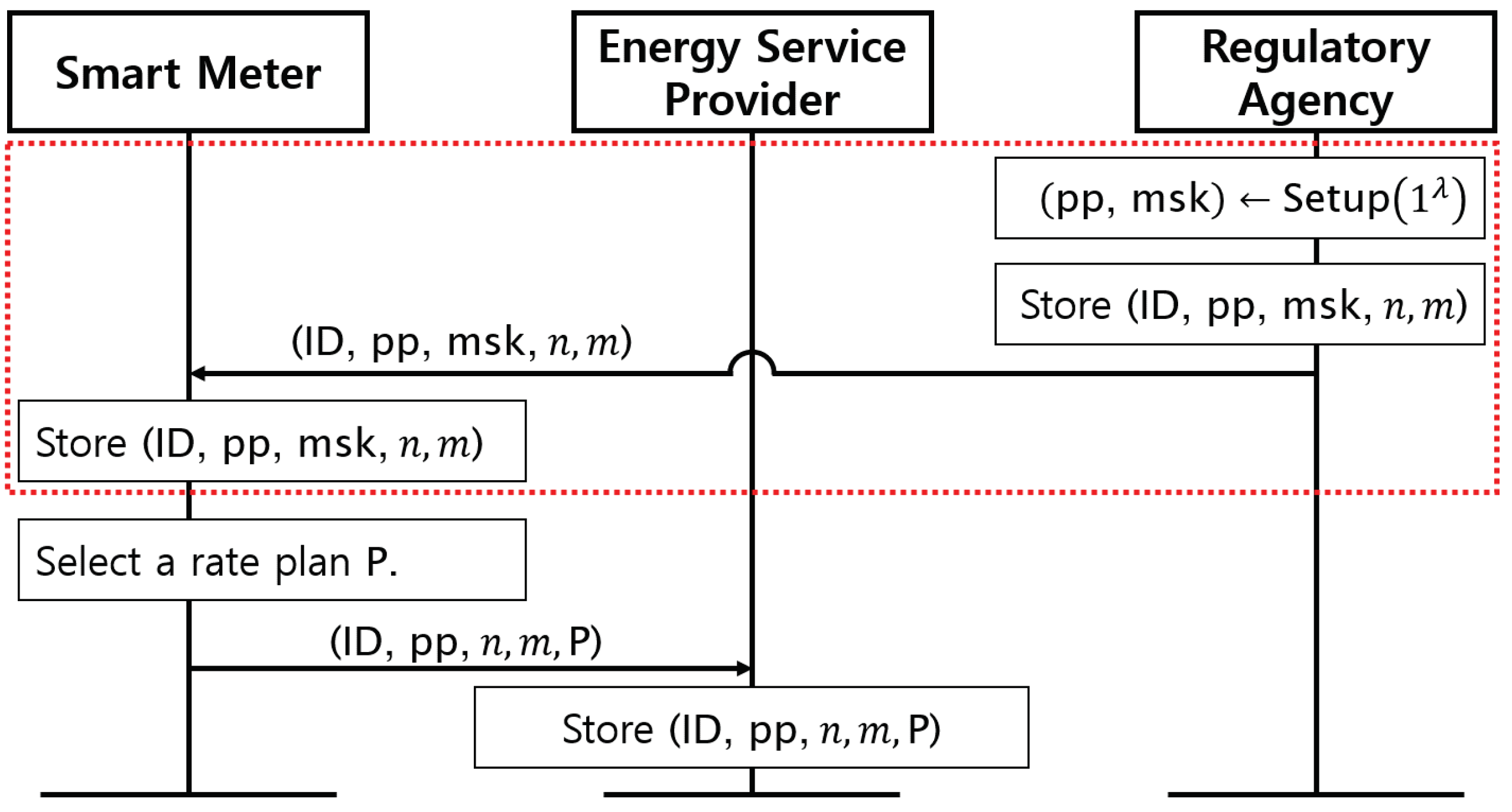
Figure 2 shows the registration stage of our protocol. This stage begins with the RA performing the algorithm of FHIPE. That is, the RA generates a master secret key and public parameters satisfying the security parameter for the smart meter. Next, the RA sets an identifier and n, the number of measurements of power consumption per reporting period. In addition, the measurement interval, m, is also set. For example, if the measurement interval m is 15 min and , the reporting period will be two hours. This information is also stored in the smart meter. The above process is performed when the smart meter is deployed and is marked with the red dotted box in Figure 2. Next, for every billing period, e.g., a month, the smart meter subscribes to an electricity rate plan and transmits the tuple to the ESP. Subscriptions to rate plans can be changed as often as desired after deployment. In this paper, we considered the electricity rate plans capable of dividing a day into multiple time periods, as with TOU or RTP. Finally, the ESP stores the tuple .
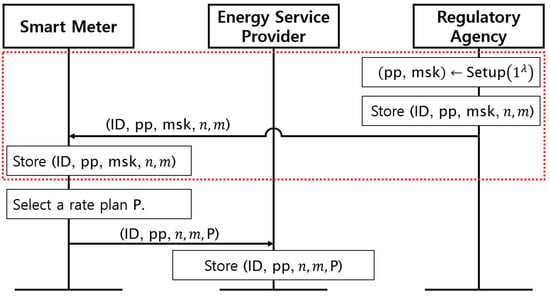
Figure 2.
Registration stage of our protocol.
3.4.2. Reporting Stage of Proposed Protocol
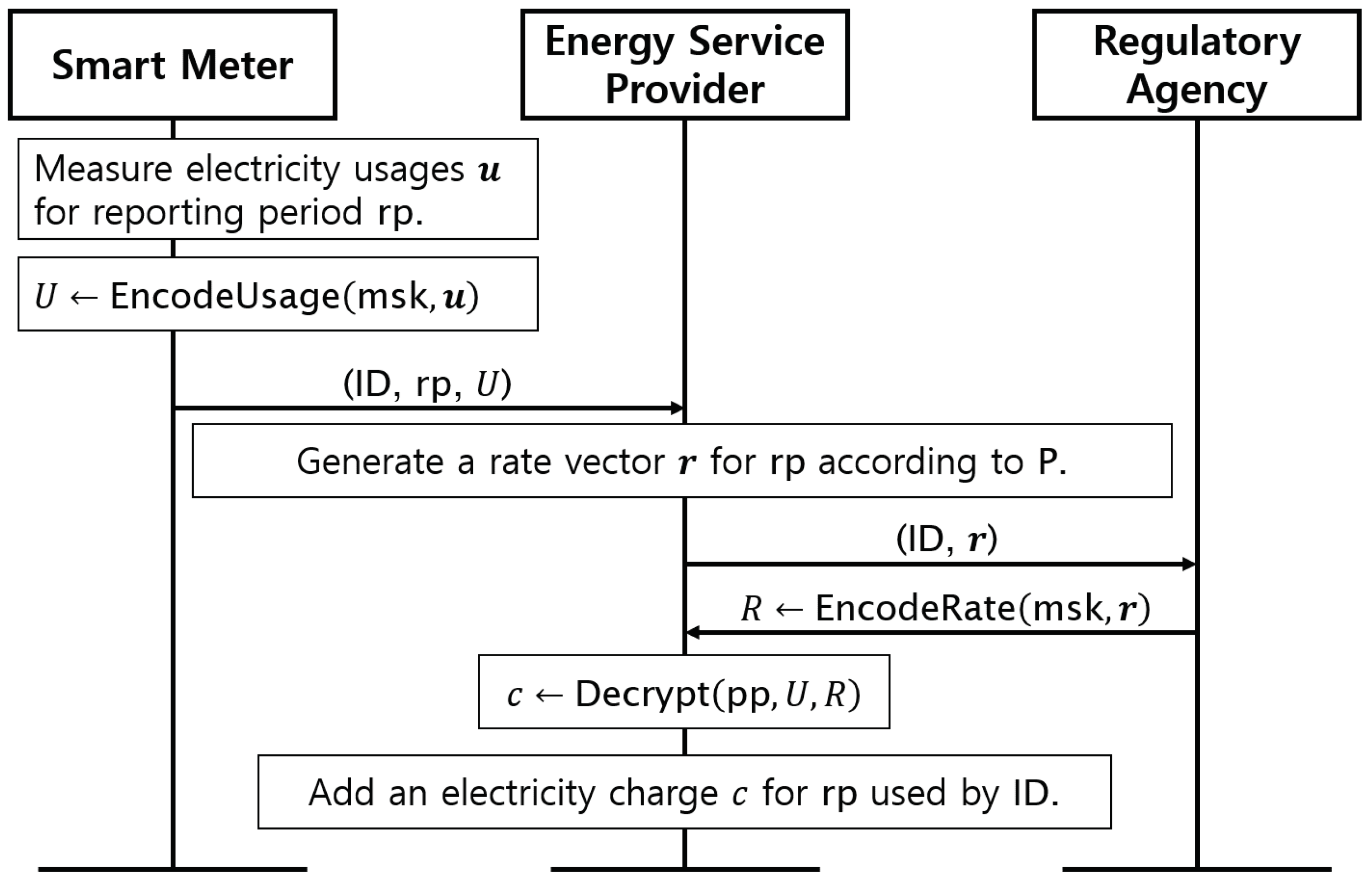
Figure 3 shows the reporting stage of our protocol. This stage should only be performed after completing the registration stage. In the reporting stage, the smart meter measures electricity consumption during a certain reporting period . Specifically, the smart meter measures the consumption n times during and represents the measured data to vector . The smart meter then encodes this vector to U using the algorithm, which is defined as . That is, performs the left encryption algorithm of FHIPE using the master secret key . Next, the smart meter transmits the tuple to the ESP. Upon receiving the tuple, the ESP generates an n-dimensional rate vector for according to the rate plan and transmits and to the RA. The RA checks whether the claimed rate is reasonable and approves by encoding it using associated with . For this purpose, the RA performs , which is defined as . That is, performs the right encryption algorithm of FHIPE. Note that does not need to be done for every reporting period unless the rate changes frequently. In this case, can be performed once in advance, and the result R can be used for many reporting periods. However, we designed our protocol, as shown in Figure 3, to cover even the most dynamic rate plans (e.g., RTP) where the price changes in real time. Smart meter users can optimize their power usage while continuously monitoring real-time price fluctuations during the reporting period. Immediately after the end of the reporting period, the ESP generates a rate vector that reflects the tariff for the most recent reporting period. Upon receiving the approval from the RA, i.e., the encoded rate R, the ESP calculates the electricity charge c by performing the FHIPE decryption using , U, and R. Finally, the ESP adds the charge c for the reporting period to the bill of the smart meter, which has as an identifier. This stage is performed once each reporting period.
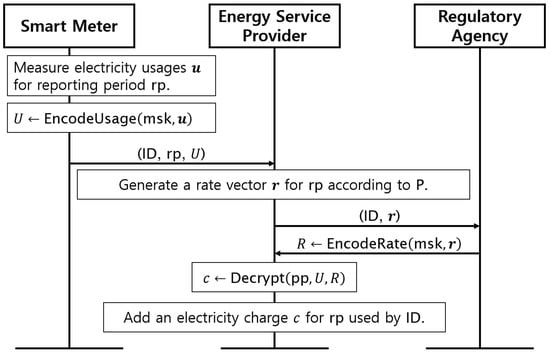
Figure 3.
Reporting stage of our protocol.
Importantly, the ESP does not learn anything about individual even though it is given U and can recover the charge (Equation (3)) by decrypting U. That is, our security objective is met according to the nature of FHIPE, which is proven in the next section. The FHIPE scheme [30] also protects from a decryptor through right encryption. However, we do not require this property because does not need to be secret. In fact, it is generated by the decryptor itself, viz. the ESP, in our protocol.
4. Security Analysis
In this section, we review the security properties of the scheme proposed in Reference [30] and prove the security of the proposed method using reduction from .
4.1. Review of Security for the FHIPE Scheme
Existing inner product encryption schemes, including the scheme [30] we use, considered an indistinguishability notion of security [30,31,32,33,34]. Here, we review the security notion for . In Reference [30], an experiment between a challenger and an adversary that can make key generation and encryption oracle queries is defined as follows:
Definition 1
(Experiment [30]). Let . The challenger computes , gives to the adversary , and then responds to each oracle query type made by in the following manner.
- -
- Key generation oracle.On inputting a pair of vectors , the challenger computes and returns .
- -
- Encryption oracle.On inputting a pair of vectors , the challenger computes and returns .
Eventually, outputs a bit , which is also the output of the experiment, denoted by .
Then, the security of an FHIPE scheme is defined using an indistinguishability notion as follows:
Definition 2
(Admissibility of [30]). For an adversary , let and be the total number of key generation and encryption oracle queries made by , respectively. For , let and be the corresponding vectors that submits to the key generation and encryption oracles, respectively. We say that is admissible if for all and , and we have that:
Definition 3
(IND-Security for IPE [30]). We define an inner product encryption scheme denoted as as fully-secure if for all efficient and admissible adversaries :
where denotes a negligible function in λ.
Theorem 1
([30]). The inner product encryption scheme is -secure in the generic group model.
Remark 1
The original statement in Theorem 7 in Reference [30] is that is -secure in the generic group model. It was also remarked in Remark 5 in Reference [30] that a -secure scheme is also -secure. We merged these two statements into the above theorem. For more details regarding the -security and a generic group model, refer to Reference [30].
4.2. Security for the Proposed Privacy-Preserving Electricity Billing Protocol
In the system model of the proposed system, we assumed that an ESP is honest-but-curious. That is, the ESP might attempt to extract useful information regarding the consumption vector . As our security goal against the honest-but-curious ESP, we defined an indistinguishability notion of security (-security) for . Then, we proved the -security of using that of .
We began by defining the following experiment between a challenger and an adversary that can make usage encoding and rate encoding oracle queries. Although the experiment is designed similarly to that in Definition 1, the adversary provides the rate encoding oracle with only a single vector , instead of a pair of vectors. This definition reflects the situation where the ESP already knows .
Definition 4
(Experiment ). Let . The challenger computes using , gives to the adversary , and then responds to each oracle query type made by in the following manner.
- -
- Usage encoding oracle.On inputting a pair of vectors , the challenger computes and returns using of .
- -
- Rate encoding oracle.On inputting a vector , the challenger computes and returns using of .
Eventually, outputs a bit , which is also the output of the experiment, denoted by .
Then, the security of a billing scheme is defined using an indistinguishability notion as follows:
Definition 5
(Admissibility of ). For an adversary , let and be the total number of usage encoding and rate encoding oracle queries made by , respectively. For , let and be the corresponding vectors that submits to the usage encoding and rate encoding oracles, respectively. We say that is admissible if for all and , and we have that:
Definition 6
(-Security for ). We define a privacy-preserving electricity billing protocol as fully-secure if for all efficient and admissible adversaries :
Theorem 2.
If is -secure (according to Definition 3) in the generic group model, then that is defined using is -secure (according to Definition 6) in the generic group model.
Proof of Theorem 2.
To conduct a reduction proof, assume that there exists an efficient and admissible adversary . We showed that can be used as a subroutine for the adversary . We designed such that it can simulate usage encoding and rate encoding oracles by forwarding ’s corresponding queries to key generation and encryption oracles, respectively. Algorithm 1 shows our construction of . It is straightforward to see that if is an admissible, polynomial time algorithm, Algorithm 1 is so, too. In addition, ’s advantage is the same as that of . That is, . However, this construction contradicts Theorem 1, which states that an admissible with non-negligible advantage does not exist. This completes the proof. □
| Algorithm 1 Construction of using |
| Input: public parameters . Output: a bit .
|
5. Experimental Results
In this section, we verify the feasibility of the proposed privacy-preserving billing system through implementation on a real-world smart meter device. To implement the system presented in Figure 1, we constructed an ESP and RA on separate servers. Both servers were equipped with an Intel Core i7-7700 CPU (3.60 GHz) and 16 GB RAM. For the smart meter, we used DS-125 Aggregator, a smart meter device manufactured and deployed by RETIGRID, a company providing smart grid solutions in Korea. This device was equipped with an ARM Cortex-A8 processor and 512 MB RAM. The software for the RA, ESP, and the smart meter was implemented in the C programming language. We used the Pairing-Based Cryptography library (PBC) [39] for cryptographic operations involving bilinear map computation e, as well as the GNU Multiple Precision Arithmetic Library (GMP) [40] for big-number arithmetic operations, and the Library for doing Number Theory (NTL) [41] for operations over a finite field, vector, and matrix.
The decryption operation to find z satisfying essentially solves a discrete logarithm problem for a small restricted space for z. To accelerate this process, we used the baby-step giant-step method [42].
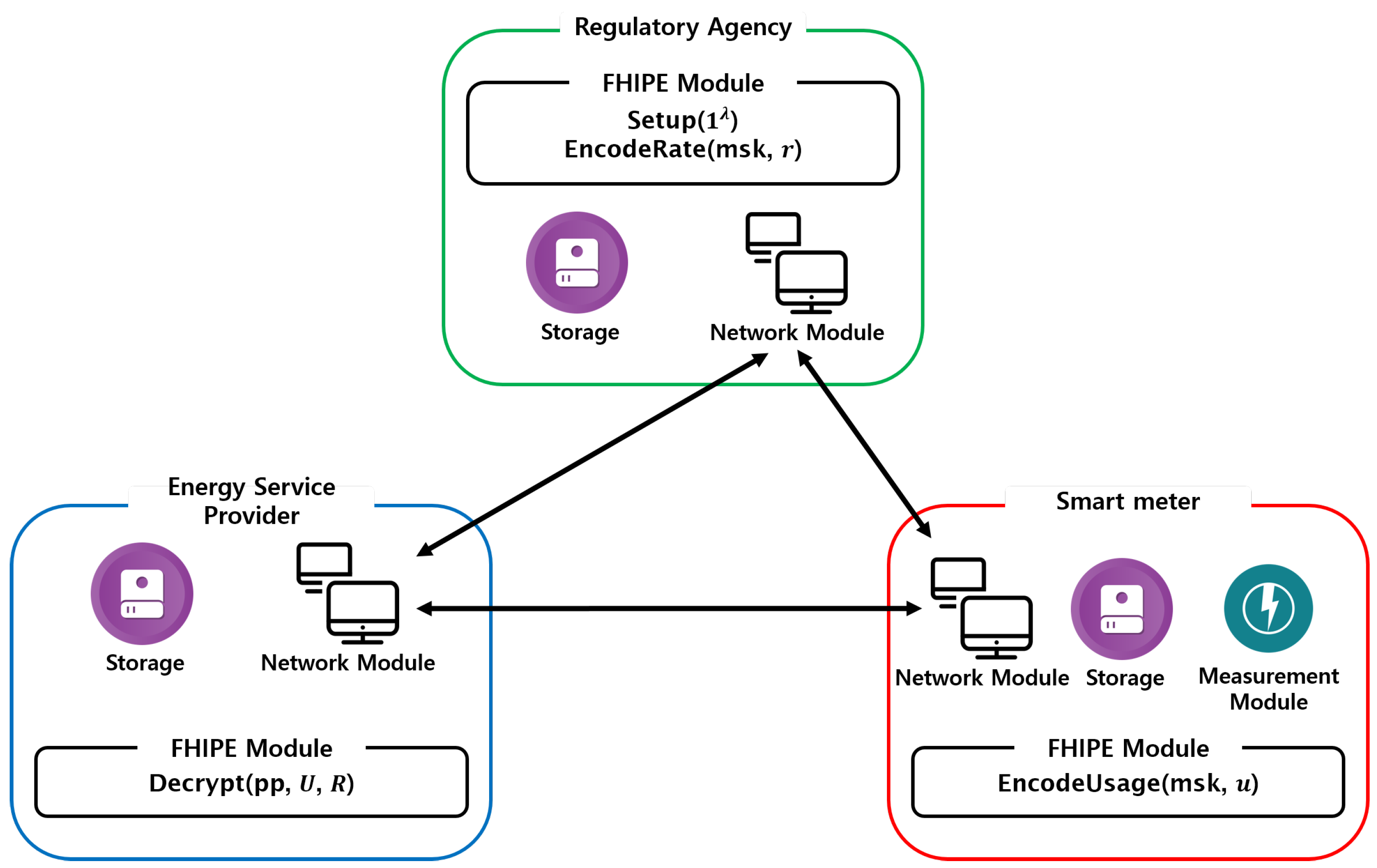
Figure 4 shows the software and hardware components of the RA, ESP, and the smart meter. The storage and network modules were in common, and DS-125 Aggregator contained a measurement module to measure the amount of consumed electricity. The RA, ESP, and smart meter also differed with regard to their FHIPE modules. Although their subcomponents were common and all used PBC, GMP, and NTL, their high-level functions were different, as explained in Section 3.4. That is, the FHIPE module in RA performed and , whereas the FHIPE module in the ESP performed , and that in the DS-125 Aggregator performed .
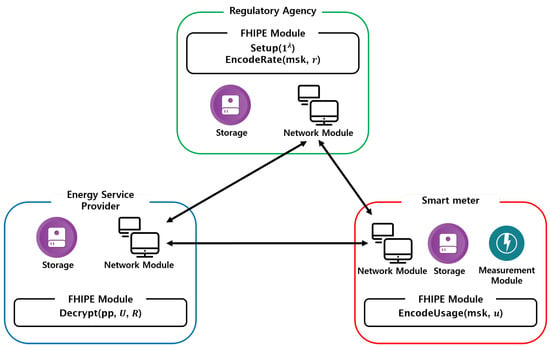
Figure 4.
Component modules of proposed system.
To evaluate the proposed system with real-world data, we used measurement data collected by the Korea Electric Power Corporation (KEPCO) [43] from three sources, viz. an apartment building, a commercial building, and a factory. Each record in these datasets represents the daily electricity usage measured at 15-min intervals. The unit of measurement is kWh, and the valid digit of measured values is up to the second decimal place. Table 1 presents more details of the data, including the measured period, the number of records, minimum usage, maximum usage, and average usage.

Table 1.
Electricity data details [43].
Along with the above data, we considered the rate plans proposed by KEPCO [44]. The rate plans were TOU rate plans, and the rates were determined by the month ∈ {summer (June to August), spring/fall (March to May and September to October), winter (November to February)}, the hour in a day ∈ {the off-peak period of spring/summer/fall/winter (23:00–09:00), the shoulder period of spring/summer/fall (09:00–10:00, 12:00–13:00, 17:00–23:00), the shoulder period of winter (09:00–10:00, 12:00–17:00, 20:00–22:00), the peak period of spring/summer/fall (10:00–12:00, 13:00–17:00), the peak period of winter (10:00–12:00, 17:00–20:00, 22:00–23:00)}, and the purpose of electricity usage ∈ {general, industrial}. The range of the unit rate varied between 21.6 KRW/kWh and 244.1 KRW/kWh, and the valid digit was up to the first decimal place. We assumed that Datasets A and C used the general rate plan and that Dataset F used the industrial rate plan. We further assumed that the smart meter reported the electricity consumption data every two hours. That is, according to the definition in Section 3.2, the reporting period length was two hours. Because the measurement interval in all datasets was 15 min, the number of measured items per reporting period, i.e., the length of the consumption vector , was . The rationale for setting the reporting period length at two ours was as follows. According to the analysis in Reference [14], the minimum interval to retain privacy is one hour, as mentioned in the introduction above. We thus provided a reasonable security margin by setting the interval as twice the minimum.
The power consumption amount recorded in the datasets listed in Table 1 and the above rates are represented with decimal fractions. Meanwhile, the operations of the FHIPE scheme [30] are only defined over integers. Therefore, to use the FHIPE operations properly without losing significant digits, and need to be quantized. For this purpose, and are converted to integer vectors before encoding. Because the valid digits in are up to the second decimal place, the elements in are quantized by . Similarly, is quantized by performing , because the valid digits in the original are up to the first decimal place. Then, the correct electricity charge is recovered by computing , i.e., .
Here, we present our experimental results. The experiments separately measured the execution times and data volume exchanged in the two stages: Registration and reporting. The experimental results for the execution time of the registration stage are presented in Table 2. Note that the performance of this stage depends on the security parameter and the vector size n, which also decides the dimension s of the matrices in the master secret key. We used the MNT 159 curve for bilinear group operations. It corresponds to , which implies that the time complexity of the best-known attack algorithm to break the underlying FHIPE is roughly . We set , as explained above. The measured times are the averages over 10,000 executions. The column Setup represents the time for the operation by the RA. The columns Store, Store, and Store represent the times to perform by the RA, by the smart meter, and by the ESP, respectively. The Network column represents the overall network overhead for the registration stage. As shown in the table, the registration stage completed quickly, i.e., in less than 50 ms in total.

Table 2.
Breakdown of execution time of the registration stage (milliseconds).
Next, Table 3 presents the experimental results for the execution time of the reporting stage. The datasets listed in Table 1 and the above rate plans provide us with the electricity consumption vectors and the rate vectors , respectively, for the corresponding reporting periods. Because the length of a reporting period is 2 hours, the number of reports per day is 12. Because every record in the datasets corresponds to a single day’s usage, the total number of reports for a dataset is calculated by #Records . The columns Encode, Encode, and Decrypt represent the time required for the operations , , and in Figure 3, respectively. The figures in Table 3 were obtained by applying these operations for each reporting period and computing the 10% trimmed means (after eliminating outliers) over each dataset. We did not separately present the time for generating in the table because it was negligible. That is, its average execution time was less than 0.01 ms. However, it was counted in the total time. As shown in the table, the reporting stage can be completed in less than 1 s. Note that the operation required more time than , even though the complexity of , i.e., , is lower than that of , i.e., , according to Reference [30]. This is because was performed on a relatively resource-constrained device. This proves that our design strategy of assigning the smart meter instead of was effective.

Table 3.
Breakdown of execution time of the reporting stage (milliseconds).
Finally, we evaluated the data volume exchanged among the involved entities in the two stages. Table 4 presents the experimental results for the packet sizes in each stage. In the table, represents the average size of the packet transmitted from A to B, including the network header and payload. According to the experimental results, all packets require only moderate bandwidth. The packet from the RA to the smart meter in the registration stage, which contains with two matrices and , consumes the most traffic, but its size is smaller than 8KB. However, we have to examine the reporting stage more carefully because it is expected to occur more frequently than registration. In particular, we should also consider the situation where the ESP receives reports from multiple smart meters. As shown in Table 4, the data volume exchanged between one smart meter, the ESP, and the RA during a reporting stage is approximately 6 KB in total. If there are N smart meters, the amount of data exchanged in a reporting stage will be KB. This capacity will be sufficient to cover a reasonable number of smart meters, but it should be verified though an implementation involving multiple smart meters. We leave this issue for future research.

Table 4.
Data volume exchanged among the entities in the two stages (bytes).
6. Discussion
In this paper, we proposed a privacy-preserving electricity billing method using FHIPE. To our knowledge, this is the first method that does not sacrifice data granularity for privacy. We implemented a prototype billing system composed of a smart meter, an ESP, and an RA. The experimental results with real measurement data show that the power consumption data of a smart meter can be reported to a service provider and accumulated for invoicing in less than 1 s and in a privacy-preserving manner. This proves the feasibility of the proposed system.
We remark that although our experiment was done with TOU, where the rates do not change frequently, the proposed method can be just as effectively applied to RTP, because the performance of our cryptographic operations—e.g., and —does not depend on whether the values of are identical or distinct.
We finally remark that for advanced services, the proposed method may be combined with other privacy-preserving protocols. For example, consider a situation where the ESP wants to use the collected data for a real-time load shedding purpose apart from billing. In this case, the ESP requires fine-grained readings, i.e., each , to control power generation and distribution in real time, which is not possible with the proposed method. However, note that for this real-time control purpose, the electricity usage data from each individual smart meter are not necessary, but the aggregate data from multiple smart meters in a certain geographic region are sufficient. Therefore, we may adopt the previous research results aiming at spatially aggregating data from multiple smart meters in a cluster. For example, the method in Reference [23] aggregates spatial consumption of smart meters using a modified version of the Paillier homomorphic encryption [45]. In the spatial consumption aggregation protocol proposed in Reference [23], each smart meter j performs a modified Paillier encryption using a public key , where is the measurement of smart meter in the i-th interval . Then, any smart meter can play the role of an aggregator and aggregates the encrypted data from N smart meters into . According to the property of the Paillier cryptosystem, , where denotes decryption using the private key . This protocol can be combined with ours as follows: The key pair can be set up in the registration stage of the proposed method, and aggregation may be performed in the reporting stage. However, the aggregation should be performed n times in each reporting period. It is also possible to set independent reading granularity for each purpose, e.g., 15 min for billing and 5 min for real-time control. However, to realize the combination of the proposed method and spatial aggregation protocol, many practical issues, such as optimal parameter-tuning to make the most of the limited resource of a smart meter, should be addressed through implementation and experiments. We leave these issues for future research.
Author Contributions
J.-H.I. designed the protocol and implemented the prototype system. H.-Y.K. collected the datasets and performed experiments. S.-Y.J. implemented the prototype system. M.-K.L. proposed the main idea for this research and organized the entire process.
Funding
This work was supported in part by the Korea Institute of Energy Technology Evaluation and Planning (KETEP) and the Ministry of Trade, Industry & Energy (MOTIE) of the Republic of Korea (No. 20161210200610), and in part by Korea Electric Power Corporation (Grant number: R18XA01).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| TOU | Time-Of-Use |
| RTP | Real-Time Pricing |
| NIALM | Non-Intrusive Appliance Load Monitoring |
| FHIPE | Function-Hiding Inner Product Encryption |
| ESP | Energy Service Provider |
| RA | Regulatory Agency |
References
- Faruqui, A.; Hledik, R.; Palmer, J. Time-Varying and Dynamic Rate Design. 2012. Available online: https://www.raponline.org/knowledge-center/time-varying-and-dynamic-rate-design/ (accessed on 17 January 2019).
- PG&E. Understand the PG&E Tiered Rate Plan. Available online: https://www.pge.com/enUS/residential/rate-plans/rate-plan-options/tiered-base-plan/tiered-base-plan.page (accessed on 17 January 2019).
- Wang, Z.; Li, F. Critical peak pricing tariff design for mass consumers in Great Britain. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–29 July 2011; pp. 1–6. [Google Scholar] [CrossRef]
- US Department of Energy’s Office of Electricity Delivery and Energy Reliability. Advanced Metering Infrastructure and Customer Systems: Results from the Smart Grid Investment Grant Program. Available online: https://www.smartgrid.gov/document/SGIG_Results_for_AMI_and_Customer_Systems_2016.html (accessed on 17 January 2019).
- McDaniel, P.D.; McLaughlin, S.E. Security and Privacy Challenges in the Smart Grid. IEEE Secur. Priv. 2009, 7, 75–77. [Google Scholar] [CrossRef]
- Hart, G.W. Nonintrusive appliance load monitoring. Proc. IEEE 1992, 80, 1870–1891. [Google Scholar] [CrossRef]
- Baranski, M.; Voss, J. Genetic algorithm for pattern detection in NIALM systems. In Proceedings of the 2004 IEEE International Conference on Systems, Man and Cybernetics (IEEE Cat. No.04CH37583), The Hague, The Netherlands, 10–13 October 2004; pp. 3462–3468. [Google Scholar] [CrossRef]
- Zeifman, M.; Roth, K. Nonintrusive appliance load monitoring: Review and outlook. IEEE Trans. Consum. Electron. 2011, 57, 76–84. [Google Scholar] [CrossRef]
- Kim, H.; Marwah, M.; Arlitt, M.F.; Lyon, G.; Han, J. Unsupervised Disaggregation of Low Frequency Power Measurements. In Proceedings of the Eleventh SIAM International Conference on Data Mining, Mesa, AZ, USA, 28–30 April 2011; pp. 747–758. [Google Scholar] [CrossRef]
- Kolter, J.Z.; Jaakkola, T.S. Approximate Inference in Additive Factorial HMMs with Application to Energy Disaggregation. In Proceedings of the Fifteenth International Conference on Artificial Intelligence and Statistics, La Palma, Spain, 21–23 April 2012; pp. 1472–1482. [Google Scholar]
- Zoha, A.; Gluhak, A.; Imran, M.A.; Rajasegarar, S. Non-intrusive load monitoring approaches for disaggregated energy sensing: A survey. Sensors 2012, 12, 16838–16866. [Google Scholar] [CrossRef] [PubMed]
- Parson, O.; Ghosh, S.; Weal, M.J.; Rogers, A. Non-Intrusive Load Monitoring Using Prior Models of General Appliance Types. In Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence, Toronto, ON, Canada, 22–26 July 2012; pp. 356–362. [Google Scholar]
- Vogiatzis, E.; Kalogridis, G.; Denic, S.Z. Real-time and low cost energy disaggregation of coarse meter data. In Proceedings of the 4th IEEE PES Innovative Smart Grid Technologies Europe, Lyngby, Denmark, 6–9 October 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Eibl, G.; Engel, D. Influence of data granularity on smart meter privacy. IEEE Trans. Smart Grid 2015, 6, 930–939. [Google Scholar] [CrossRef]
- Lisovich, M.A.; Mulligan, D.K.; Wicker, S.B. Inferring Personal Information from Demand-Response Systems. IEEE Secur. Priv. 2010, 8, 11–20. [Google Scholar] [CrossRef]
- Greveler, U.; Justus, B.; Löhr, D. Multimedia Content Identification Through Smart Meter Power Usage Profiles. In Proceedings of the Computers, Privacy and Data Protection (CPDP 2012), Brussels, Belgium, 25–27 January 2012. [Google Scholar]
- Engel, D. Wavelet-based load profile representation for smart meter privacy. In Proceedings of the IEEE PES Innovative Smart Grid Technologies Conference, Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Engel, D.; Eibl, G. Multi-resolution load curve representation with privacy-preserving aggregation. In Proceedings of the 4th IEEE PES Innovative Smart Grid Technologies Europe, Lyngby, Denmark, 6–9 October 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Erkin, Z.; Troncoso-pastoriza, J.R.; Lagendijk, R.L.; Perez-Gonzalez, F. Privacy-preserving data aggregation in smart metering systems: An overview. IEEE Signal Process. Mag. 2013, 30, 75–86. [Google Scholar] [CrossRef]
- Efthymiou, C.; Kalogridis, G. Smart Grid Privacy via Anonymization of Smart Metering Data. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar] [CrossRef]
- Bohli, J.; Sorge, C.; Ugus, O. A Privacy Model for Smart Metering. In Proceedings of the 2010 IEEE International Conference on Communications Workshops, Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar] [CrossRef]
- Kim, Y.; Ngai, E.C.H.; Srivastava, M.B. Cooperative state estimation for preserving privacy of user behaviors in smart grid. In Proceedings of the IEEE Second International Conference on Smart Grid Communications, Brussels, Belgium, 17–20 October 2011; pp. 178–183. [Google Scholar] [CrossRef]
- Erkin, Z.; Tsudik, G. Private Computation of Spatial and Temporal Power Consumption with Smart Meters. In Proceedings of the Applied Cryptography and Network Security-10th International Conference, Singapore, 26–29 June 2012; pp. 561–577. [Google Scholar] [CrossRef]
- Kursawe, K.; Danezis, G.; Kohlweiss, M. Privacy-Friendly Aggregation for the Smart-Grid. In Proceedings of the Privacy Enhancing Technologies-11th International Symposium, Waterloo, ON, Canada, 27–29 July 2011; pp. 175–191. [Google Scholar] [CrossRef]
- Ács, G.; Castelluccia, C. I Have a DREAM! (DiffeRentially privatE smArt Metering). In Proceedings of the 13th International Conference on Information Hiding, Prague, Czech Republic, 18–20 May 2011; pp. 118–132. [Google Scholar] [CrossRef]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar] [CrossRef]
- Garcia, F.D.; Jacobs, B. Privacy-Friendly Energy-Metering via Homomorphic Encryption. In Proceedings of the 6th International Workshop on Security and Trust Management, Athens, Greece, 23–24 September 2010; pp. 226–238. [Google Scholar] [CrossRef]
- Sahai, A.; Seyalioglu, H. Worry-free Encryption: Functional Encryption with Public Keys. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 463–472. [Google Scholar]
- Garg, S.; Gentry, C.; Halevi, S.; Raykova, M.; Sahai, A.; Waters, B. Candidate Indistinguishability Obfuscation and Functional Encryption for All Circuits. In Proceedings of the 2013 IEEE 54th Annual Symposium on Foundations of Computer Science, Berkeley, CA, USA, 26–29 October 2013; pp. 40–49. [Google Scholar]
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption Is Practical. In Proceedings of the Security and Cryptography for Networks (SCN 2018), Amalfi, Italy, 5–7 September 2018; pp. 544–562. [Google Scholar]
- Bishop, A.; Jain, A.; Kowalczyk, L. Function-Hiding Inner Product Encryption. In Proceedings of the 21st International Conference on Advances in Cryptology (ASIACRYPT 2015), Auckland, New Zealand, 29 November–3 December 2015; pp. 470–491. [Google Scholar]
- Abdalla, M.; Bourse, F.; De Caro, A.; Pointcheval, D. Simple Functional Encryption Schemes for Inner Products. In Proceedings of the Public-Key Cryptography—PKC 2015, Gaithersburg, MD, USA, 30 March–1 April 2015; pp. 733–751. [Google Scholar]
- Datta, P.; Dutta, R.; Mukhopadhyay, S. Functional Encryption for Inner Product with Full Function Privacy. In Proceedings of the Public-Key Cryptography—PKC, Taipei, Taiwan, 6–9 March 2016; pp. 164–195. [Google Scholar]
- Kim, S.; Kim, J.; Seo, J.H. A New Approach for Practical Function-Private Inner Product Encryption. Available online: https://eprint.iacr.org/2017/004 (accessed on 29 March 2019).
- US Department of Energy’s Office of Electricity Delivery and Energy Reliability. Time Based Rate Programs. Available online: https://www.smartgrid.gov/recovery_act/time_based_rate_programs.html (accessed on 17 January 2019).
- Korea Electricity Regulatory Commission. Available online: http://www.korec.go.kr/intrcn/moveObjectiveAndStatus.do (accessed on 18 March 2019).
- Federal Energy Regulatory Commission. Available online: https://www.ferc.gov/ (accessed on 18 March 2019).
- Kim, S.; Lewi, K.; Mandal, A.; Montgomery, H.; Roy, A.; Wu, D.J. Function-Hiding Inner Product Encryption Is Practical. Available online: https://eprint.iacr.org/2016/440.pdf (accessed on 29 March 2019).
- The Pairing-Based Cryptography Library (PBC). Available online: https://crypto.stanford.edu/pbc/ (accessed on 17 January 2019).
- GNU Multiple Precision Arithmetic Library (GMP). Available online: https://gmplib.org/ (accessed on 17 January 2019).
- A Library for Doing Number Theory (NTL). Available online: https://www.shoup.net/ntl/ (accessed on 17 January 2019).
- Shanks, D. Class number, a theory of factorization, and genera. Proc. Symp. Math. Soc. 1971, 20, 415–440. [Google Scholar]
- KEPCO Smart Power Management (iSMART). Available online: https://pccs.kepco.co.kr/iSmart/ (accessed on 15 February 2019).
- KEPCO Electricity Tariffs. Available online: http://cyber.kepco.co.kr/ckepco/front/jsp/CY/E/E/CYEEHP00101.jsp (accessed on 15 February 2019).
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).