1. Introduction
In order to facilitate the community to achieve stable and reliable power supply, a lot of new technologies and equipment are extensively integrated into the modern power grid, such as advanced metering infrastructure (AMI) and intelligent electronic device (IED). Definitely, the integration of new items complicates the network, leading to a reduction of system invulnerability since more accessories mean higher failure probability and the supervisory control and data acquisition (SCADA) is more difficult to implement in complex systems [
1]. In addition to critical reliability issues, the power grid suffers various types of threats, e.g., accidental natural disaster attacks [
2,
3] and deliberate artificial attacks (military or terrorist, since power grid is a critical infrastructure) [
4], causing huge economic losses and major social impacts due to the resulting cascading failures. Therefore, the power system fortification has attracted great concerns in the community of academics, industry, and military.
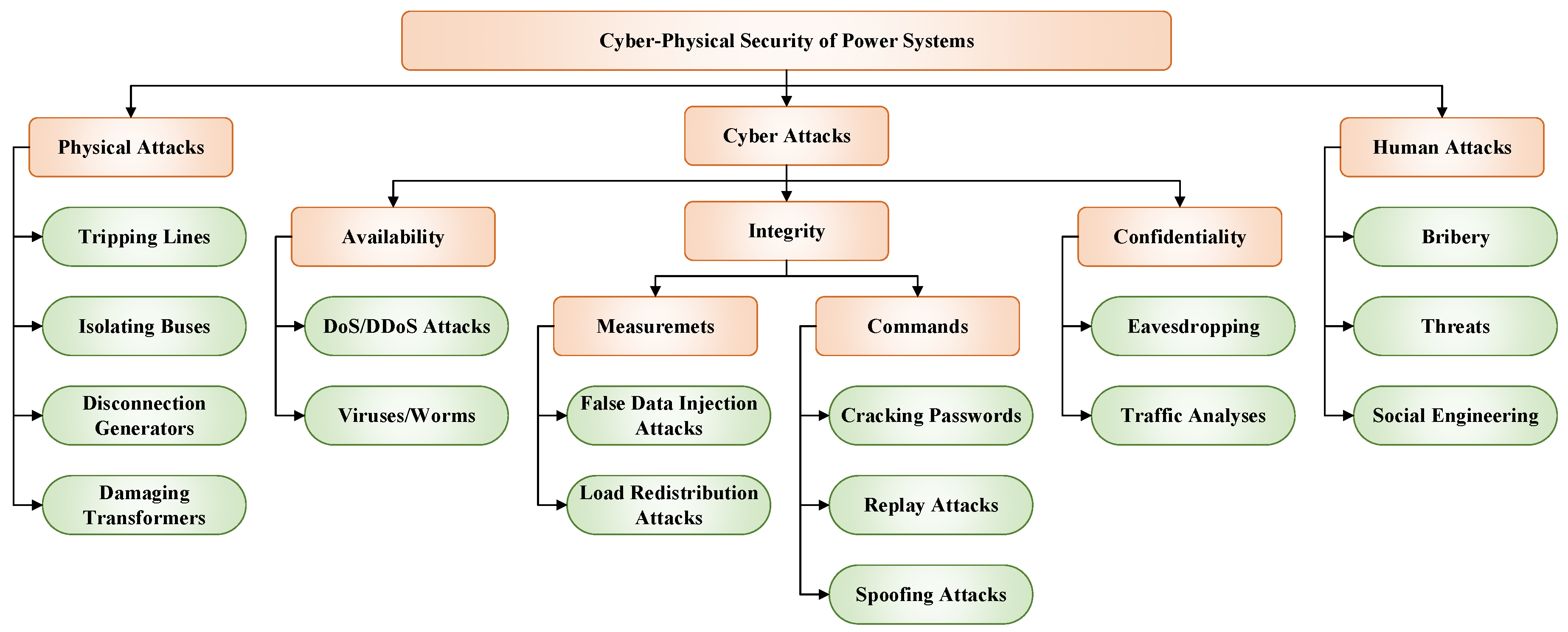
In order to design a robust fortification plan, the target attack pattern should be determined first. It is reported in [
5] that attacks are mainly implemented on three aspects: physical, cyber, and human since the power grid is a cyber-physical interconnected network operated by engineers. For quick reference,
Figure 1 depicts a full scheme of different attacks, where each type is investigated in the literature with either separated or coordinated pattern. In [
6], a general mathematical framework for cyber-physical systems, attacks, and monitors is proposed for power systems, transportation networks, industrial control processes, and critical infrastructures. In [
7], several physical attack scenarios are fabricated and investigated, where system potential cascading events are modeled with power flow calculation, hidden failures are simulated by the Monte Carlo method, and operator performance is analyzed via a simple human reliability model. Cyber systems are extensively integrated in the physical grid for power generation, transmission, and distribution, such as communication networks, metering units, and control centers, etc. [
8]. In cyber-physical systems, deliberate attacks are implemented not only on their physical infrastructure, but also on their data management and communication layer [
6]. A comprehensive review of false data injection attack (FDIA) is given in [
9], where theoretical basis, physical and economical impacts, defensive strategies, and potential future research directions of FDIA are investigated and discussed. The optimal attacks implemented on substations and transmission lines are investigated in [
10] based on the proposed component interdependency graph. The contribution and impact of branches when they are employed or removed from a power system are analyzed in [
11], leading to the identification of sensitive regions of each line based on a cyclic addition algorithm. In Refs. [
12] and [
13], the cascading failures caused by line breakdown is investigated using complex network theories, such as small-world and scale-free networks, where electrical characteristics of nodes are considered on the basis of pure structure topology. Although there are various types of attacks, physical attack via tripping lines is determined as the target attack pattern in this paper. We intend to claim that, although the exemplified attack is tripping lines, the solution methodology reported in this paper can be easily extended to other types of attacks.
Faced with different kinds of attacks, the defensive plan could be various. Taking the tripping line attack as an example, the defensive strategy includes: (1) adding new devices (both generators and transmission lines) to improve the redundancy; (2) enhancing the defensive strength to guarantee the protected assets are invulnerable during attacks; and (3) allocating portable components (e.g., distributed generators) to dynamically reconfigure the distribution network. Whatever the attack pattern and defense resource are, the optimization problem of generating an optimal defensive plan is related to two opposite agents, i.e., the defender and attacker to protect and destroy the system respectively. According to the number of action rounds, the game between these agents can be classified as an attacker–defender (AD) model and the defender–attacker–defender (DAD) model. Traditionally, the AD model is formulated as the bi-level min–max programming problem, which is challenging due to its non-convex discrete property. In [
14], an equivalent single-level reformulation of the AD model is proposed to address the optimal defense problem, where transmission line switching is employed for protection. A coordinated cyber-physical attack is analyzed in a proposed bi-level model in [
15], which is transformed into a mixed-integer linear programming (MILP) problem and addressed via a rigorous two-stage solution approach. In order to investigate cyber-attack on multiple transmission lines in economic dispatch, a bi-level MILP model with the capability to overload branches is proposed in [
16], where remarkable computational efficiency is achieved.
On the other hand, the DAD model is usually formulated as a tri-level programming problem with three rounds of action [
17]:
In the first stage (upper-level problem), the defender determines an optimal defensive plan with the goal of minimizing system power imbalance/mismatch, where the reaction of attacker should be considered and the defensive resource is limited.
In the second stage (middle-level problem), the attacker is faced with an enhanced system where the defensive plan generated in the first stage has been implemented, and whose goal is maximizing the unserved energy of the confronted network with restricted attack resources.
In the third stage (lower-level problem), both initial defensive plan and subsequent attack scheme have been carried out, leading to a partially destroyed system, whose power imbalance will be minimized in this stage via system redispatch.
In order to defend against terrorist attacks, a tri-level optimization model of resource allocation is proposed in [
18], which is then tackled by a decomposition approach. The superiority of tri-level optimization over bi-level optimization in electric power network defense is validated with case studies. In [
19], uncertain attacks and load types are integrated into the DAD model for power system protection, which is then addressed by two-stage robust optimization (RO) approach and column-and-constraint generation (CCG) algorithm. The CCG method is proposed in [
20] and [
21], whose performance in RO framework has been extensively verified on different types of power system optimization problems, such as transmission expansion planning [
22], economic dispatch [
23], unit commitment [
24], and distribution network reconfiguration [
25], etc. Based on RO and CCG, a lot of power system defensive research has been implemented, e.g., Ref. [
26] investigates the problem of allocating fortification resources with the objective of maximizing the power system’s immunity against malicious attacks, Ref. [
27] proposes an approach to mitigate network vulnerability toward worst-case spatially localized attacks, and Ref. [
28] develops a practical and efficient tool for utility transmission planners to protect critical facilities from potential physical attacks, etc.
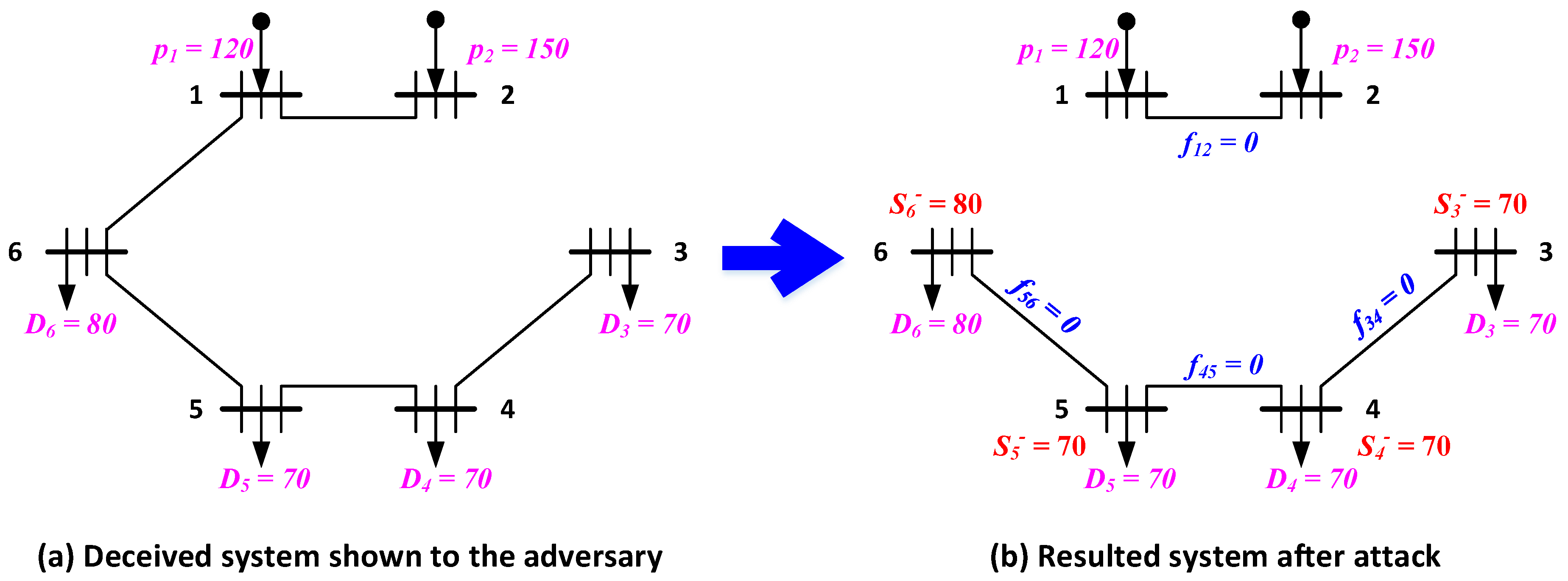
Although advanced algorithms and sophisticated problem formulations are proposed in the literature, one limitation is shared in the above references, i.e., the attacker is assumed to be capable of accessing sufficient information. The attacker’s decision is made in the second stage based on all information revealed at that time. In the literature, it is commonly assumed that all information is accessible by the attacker including network topology, device parameters, physical capacity, and defensive decisions made by the defender in the first stage. Nevertheless, it is very difficult or even impossible to get access all information, especially in war and terrorist attacks where the defender is supposed to hide some critical information or even do some deception activities. Actually, in a DAD model, the attacker is exposed to the defender due to: (1) the attacker always intends to cause the worst consequence, thus the decision can be figured out if the input information is fixed; and (2) the defender’s decision can withstand the worst case incurred by the attacker, not to mention those randomly generated attack plans. It can be concluded that there is an information asymmetry between the defender and attacker, which can be utilized to squeeze benefits. For example, given a real configuration A, if the information is symmetry, then the worst attack plan B will be proposed by the attacker, leading to a system power imbalance M. On the other hand, if the deception strategy is implemented to show a fake configuration to the attacker, then the worst attack plan will be generated, whose power mismatch is . For real configuration A, as the DAD model is targeted at the worst case, it can be concluded that there is no attack can produce larger power mismatch than M, i.e., , thus the system power imbalance might be reduced by information asymmetry.
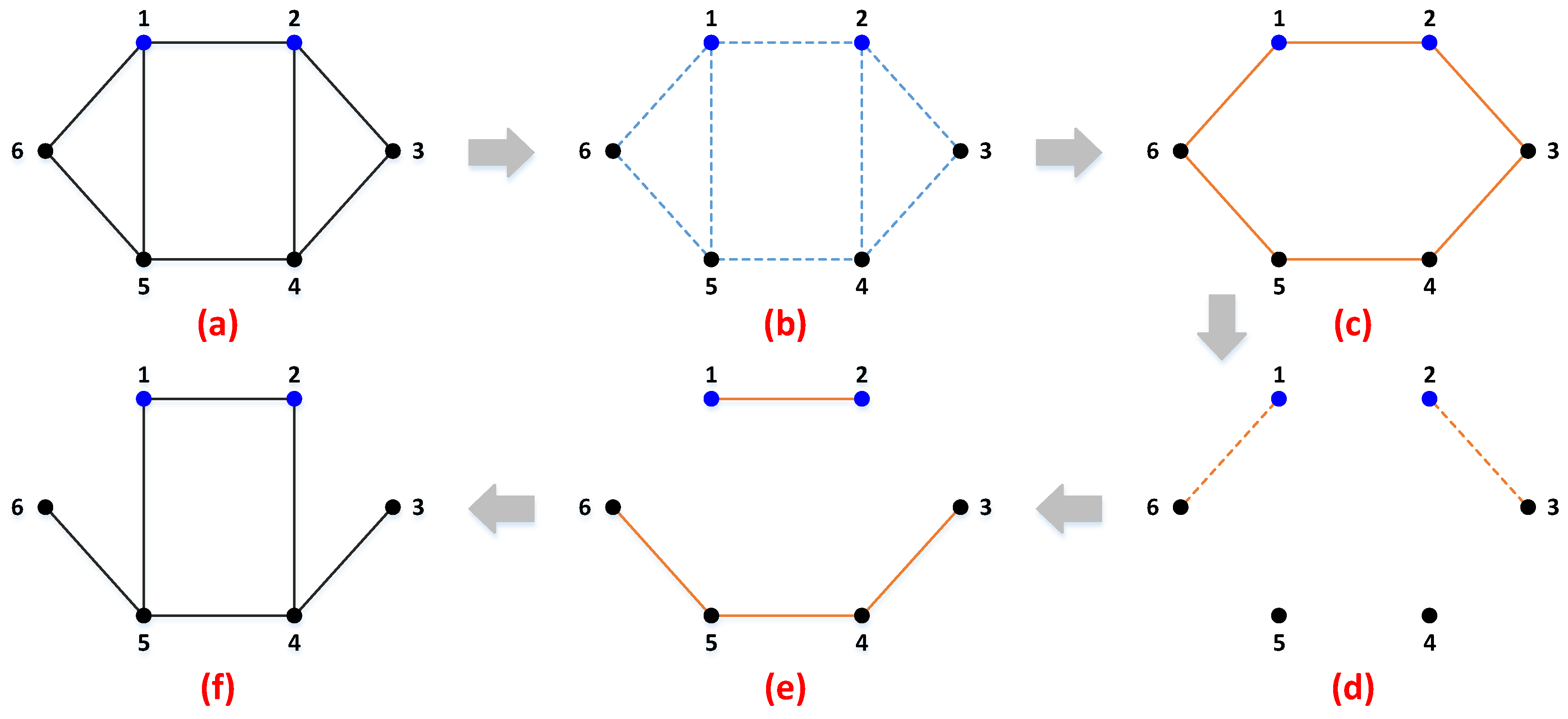
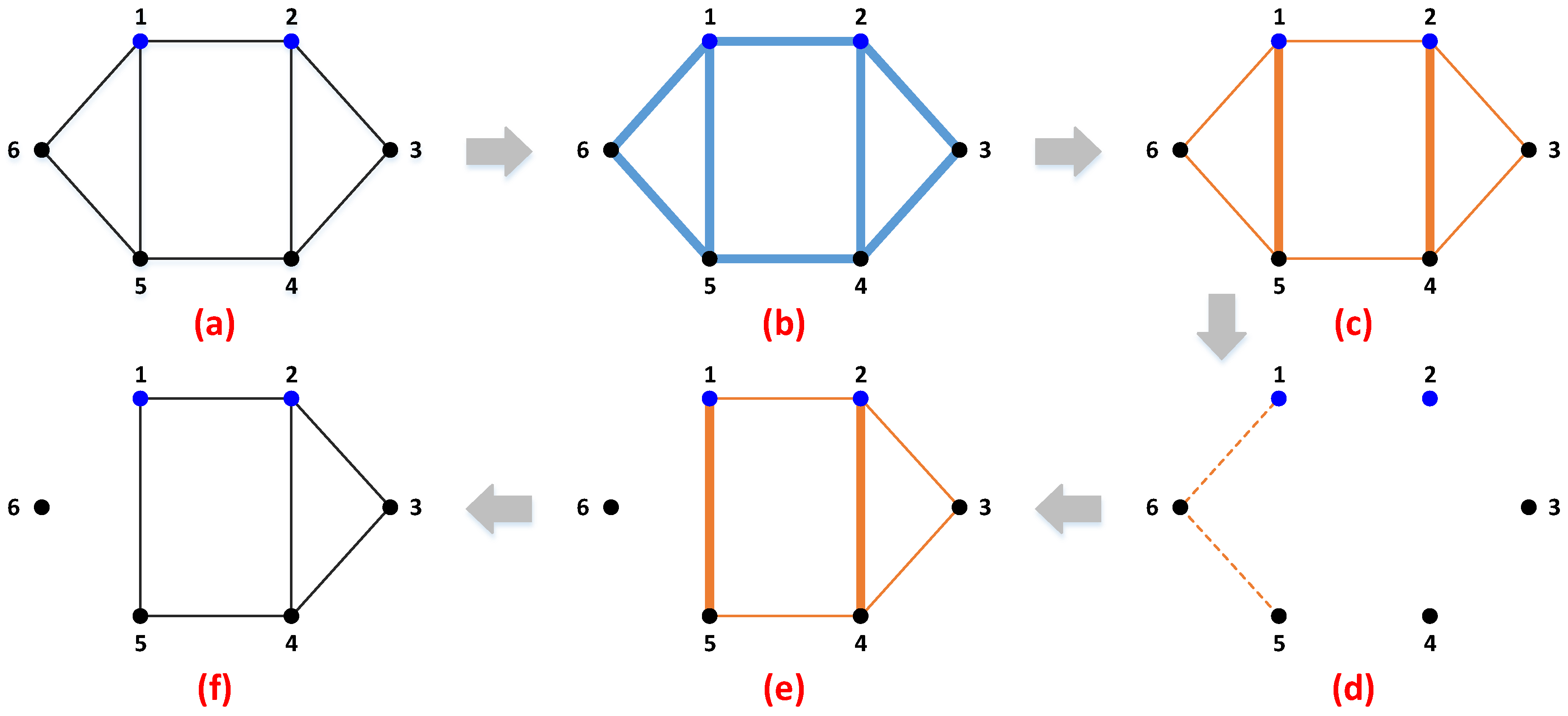
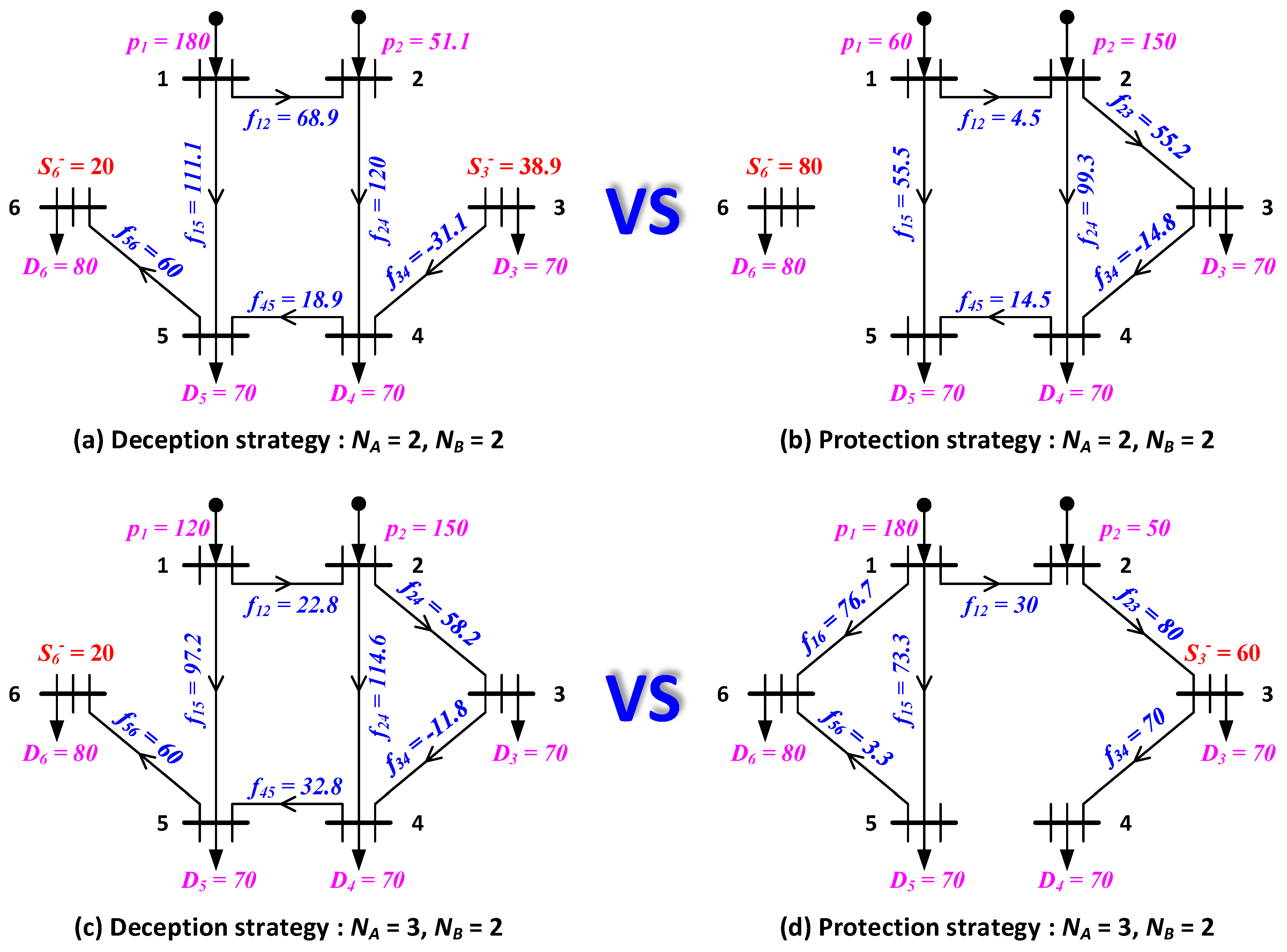
In this paper, we intend to investigate the optimal deception strategies in power system fortification against deliberate attacks. The deception strategy is described in detail based on a full comparison with the traditional protection strategy in
Section 2. According to the step-by-step theoretical analysis of a 6-bus system, the potential of deception strategy is revealed. In order to numerically derive the optimal deception and protection strategy, tri-level programming problems are established based on the DAD model. In accordance with the literature, the tri-level programming problem is addressed with RO in
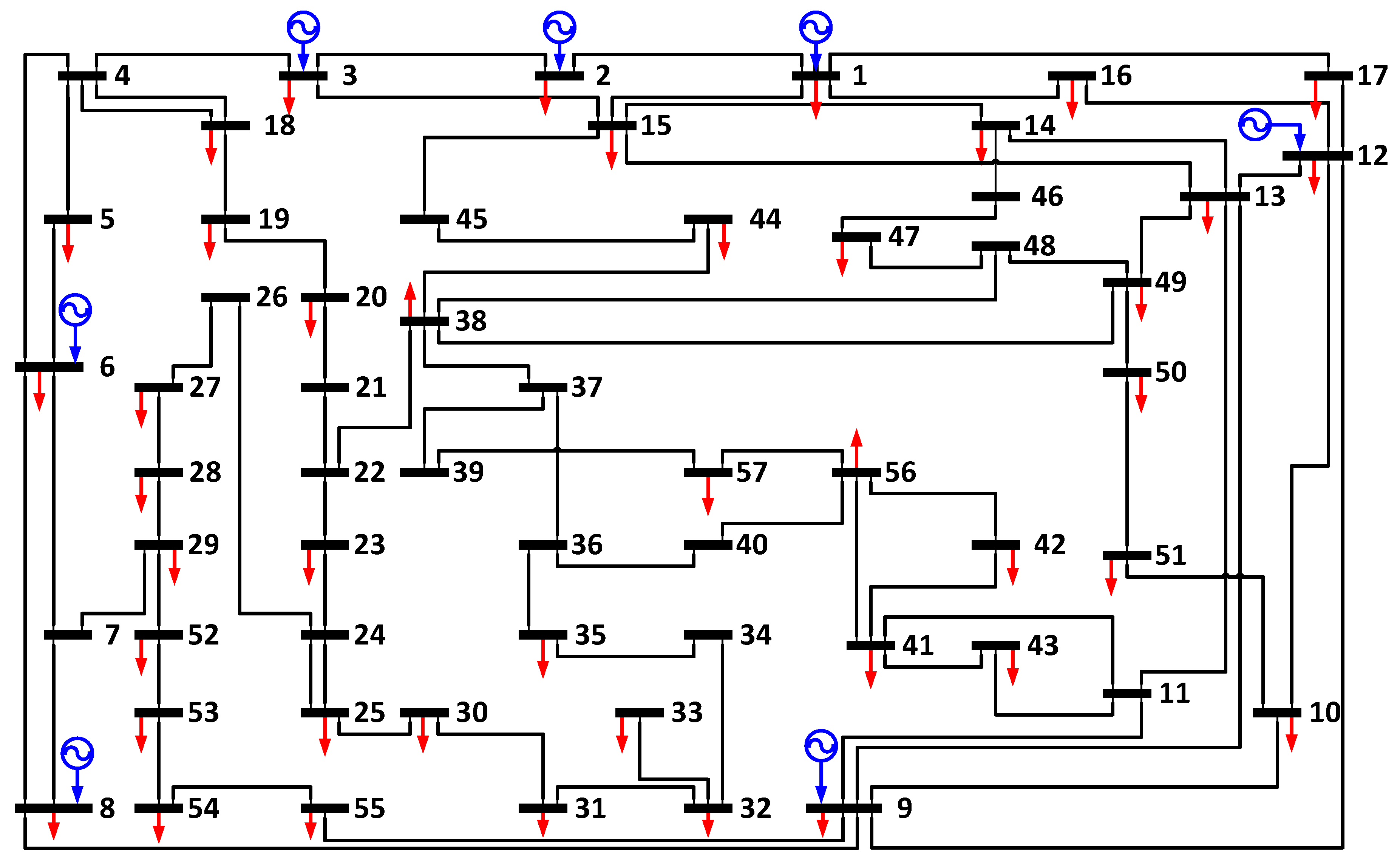
Section 3, where both subproblem and master problem are explicitly formulated based on dual theory, big-M method, and CCG constraints. Case studies are implemented on a 6-bus system and the IEEE 57-bus system in
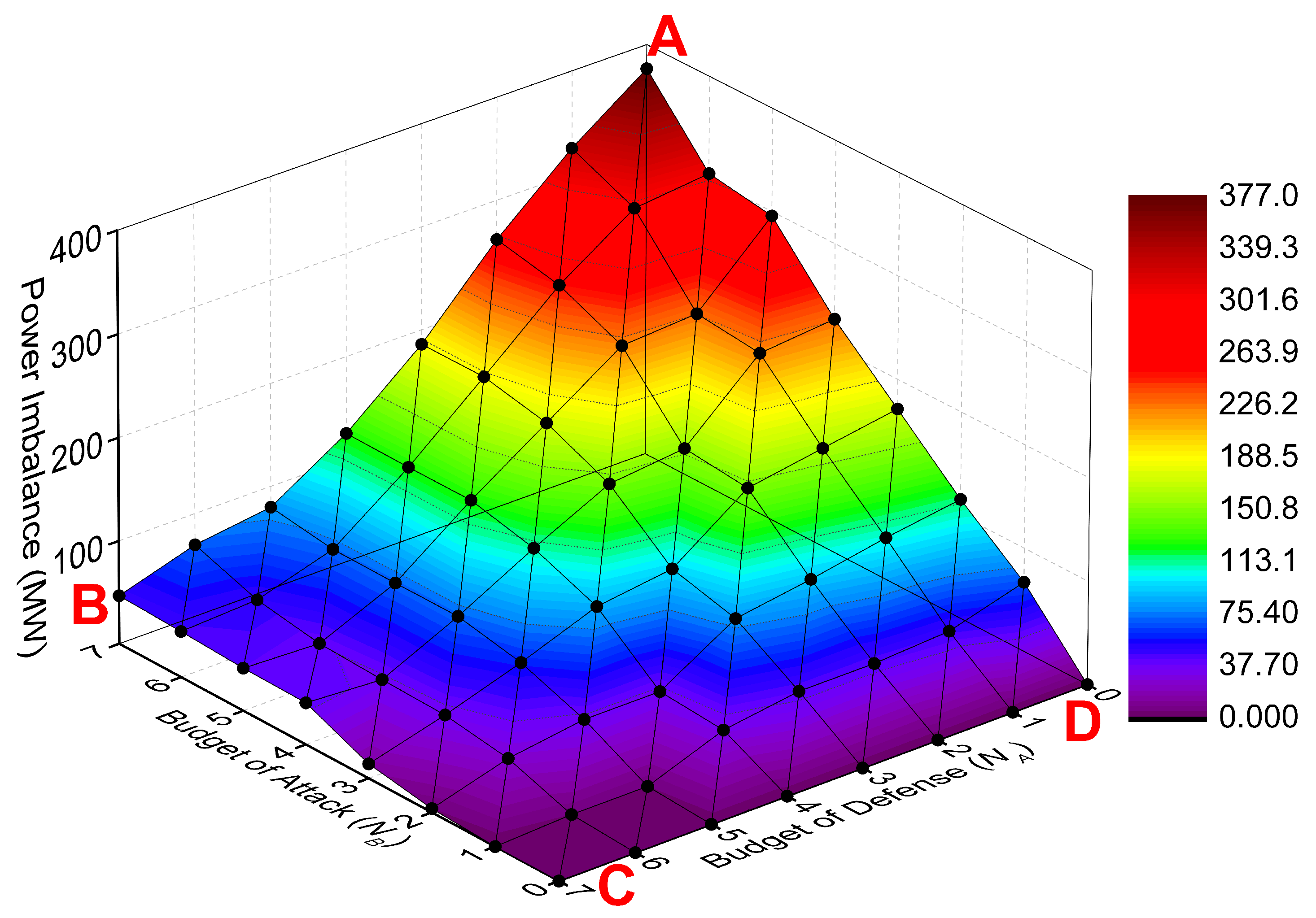
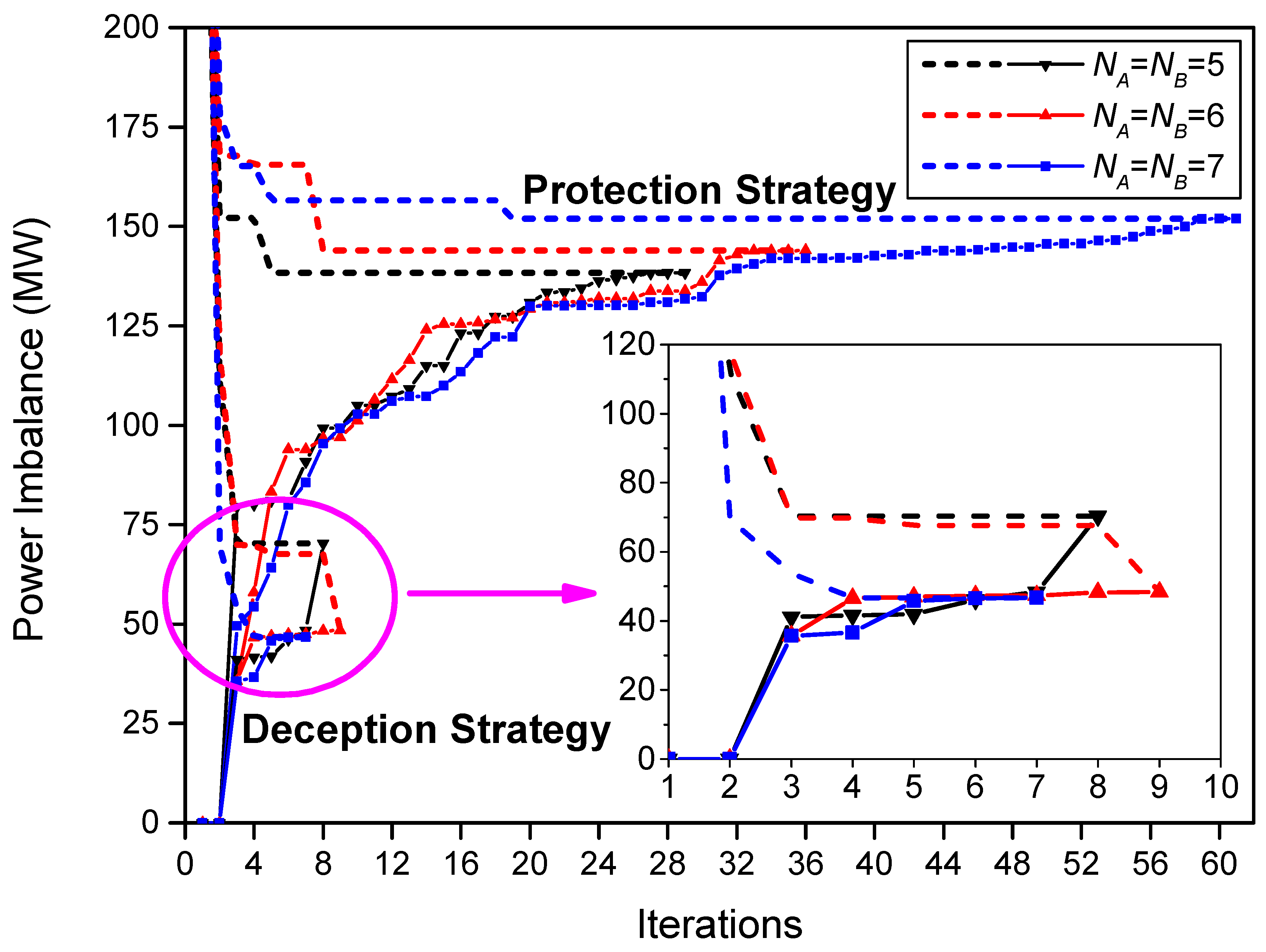
Section 4, where the smaller network is utilized to identify the superiority and analyze the inner mechanism, while the larger system is employed to investigate the performance under different circumstance and discuss the convergence property. Results indicate that the deception strategy achieves less unserved power and faster convergence rate. Finally, conclusions and future work are summarized in
Section 5.
The main contributions of this paper are as follows: (1) the deception conception is proposed and formulated, providing a general framework for more complicated defensive strategies based on information asymmetry in the future; (2) an RO solution framework for the optimal deception strategy is developed on the basis of CCG constraints, and the convergence property is discussed; and (3) comprehensive numerical experiments are implemented to verify the advantageous of deception strategy, including less objective value and faster convergence rate.
5. Conclusions
The power system fortification problem against deliberate attacks is investigated in this paper. Different from traditional protection strategy, where the attacker is assumed to be capable of accessing sufficient information, including network topology, device parameters, physical capacity, and defensive decision, the information asymmetry between defender and attacker is introduced in this work, resulting in an optimal deception strategy problem. In order to explicitly reveal the advantageous and significance of information in the two-player game, both deception and protection strategies are described in detail with the invented 6-bus system, formulated into the tri-level MILP problem, and solved via two-stage RO and CCG algorithms. Numerical experiments are carried out on both the 6-bus system and the IEEE 57-bus system. In the first network, numerical validation of the superiority of deception is presented. On the other hand, performance evaluation and convergence analysis are given based on the second grid. Although deception strategy is integrated into power system fortification, the considered defensive operation is still limited. In the future, more comprehensive deception and attack strategies will be investigated, e.g., setting up fake components (including transmission lines, generators, and loads, etc.), concealing critical loads, and attacking nodes in addition to branches, etc. In addition, different from binary metrics, the success rate/probability of deception and protection operation implemented on each branch will be included in the solution framework.