BiPAD: Binomial Point Process Based Energy-Aware Data Dissemination in Opportunistic D2D Networks
Abstract
1. Introduction
2. BiPAD: Binomial Point Process-Based Energy-Aware Data Dissemination
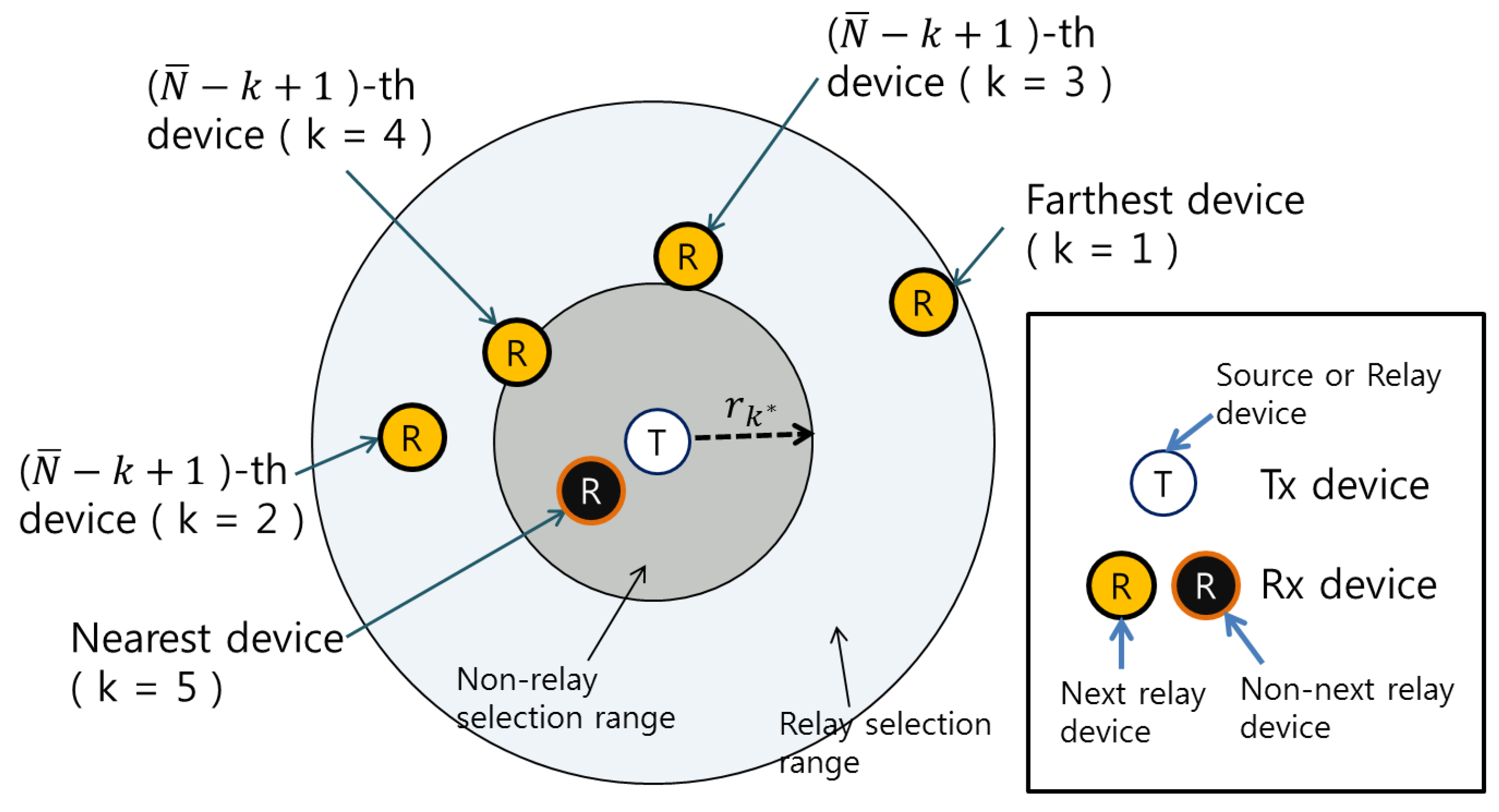
2.1. n-th Nearest Distance by BPP
2.2. Distributed Relay Selection and BPP-Based D2D Data Dissemination
- Step 1.
- A source device sends a message, including its location information and the desired number of relays, k. Here, k is determined as the number required to achieve the same message delivery ratio as the epidemic routing algorithm.
- Step 2.
- If a device receives the message from the source, it calculates the k-th furthest distance from the source device to the furthest k-th device () using the received k value and the total number of devices within the transmission range of the receiver, as estimated by the network user density.
- Step 3.
- The receiver calculates the distance from the source device to itself, . If , the receiver prepares to forward the received message including its location information and the k value to its neighboring devices. Then, the receiver forwards this message to its neighbors. In our proposed BiPAD algorithm, using the value, the source device can select almost exactly the number of relay devices using this distributed forwarding decision based on BPP.
- Step 4.
- Repeat Step 1 to Step 3 until the messages are disseminated to the entire network.
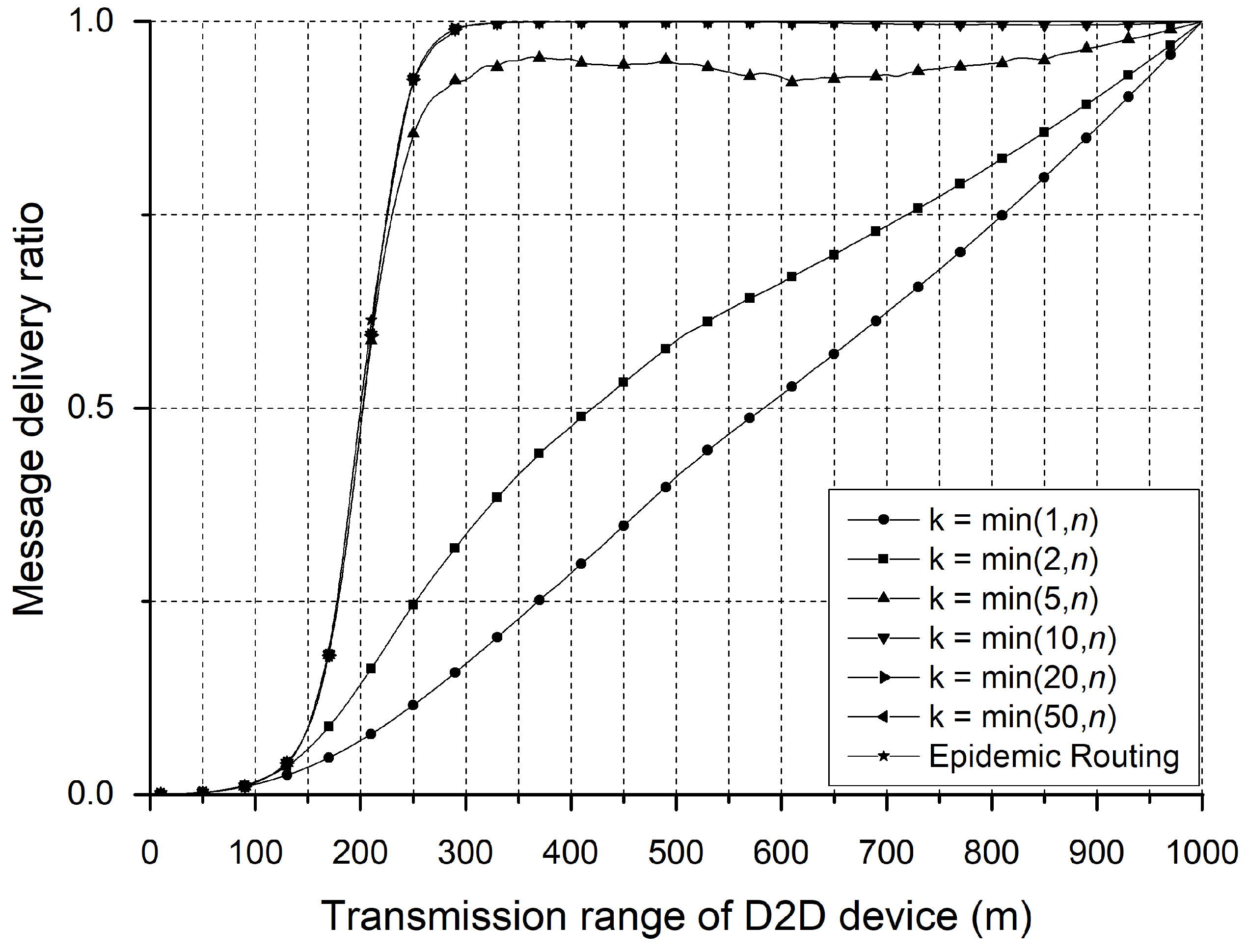
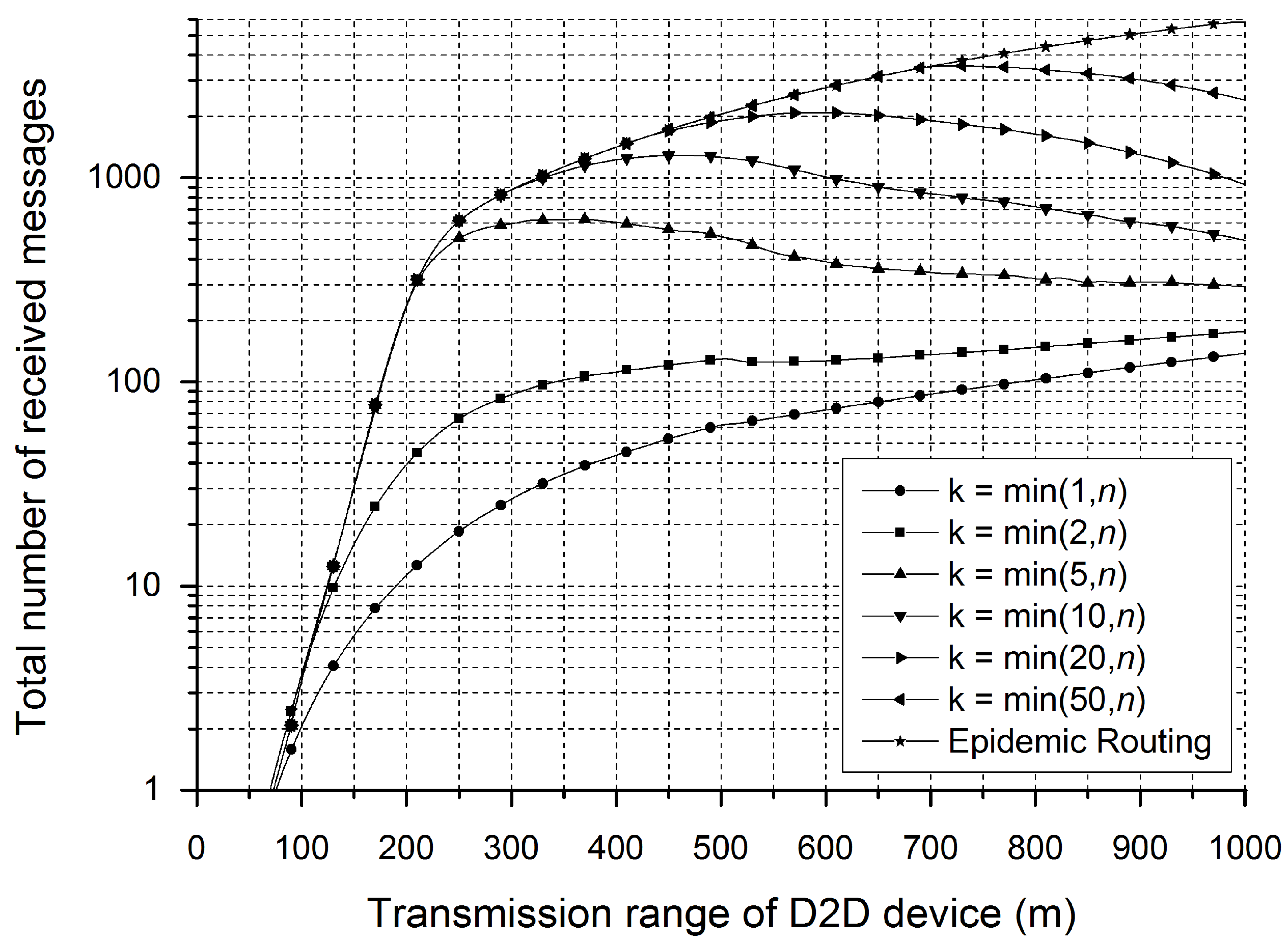
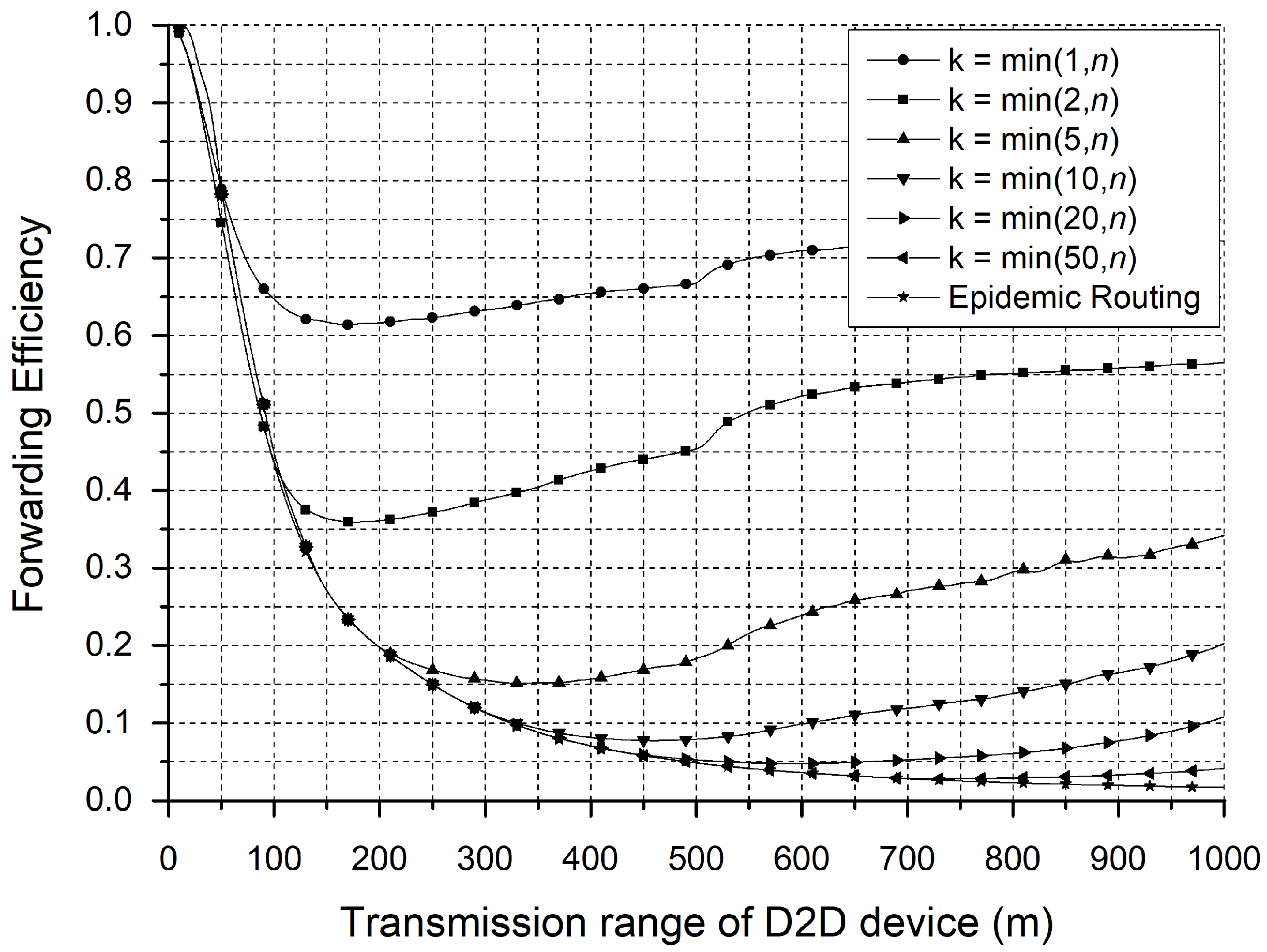
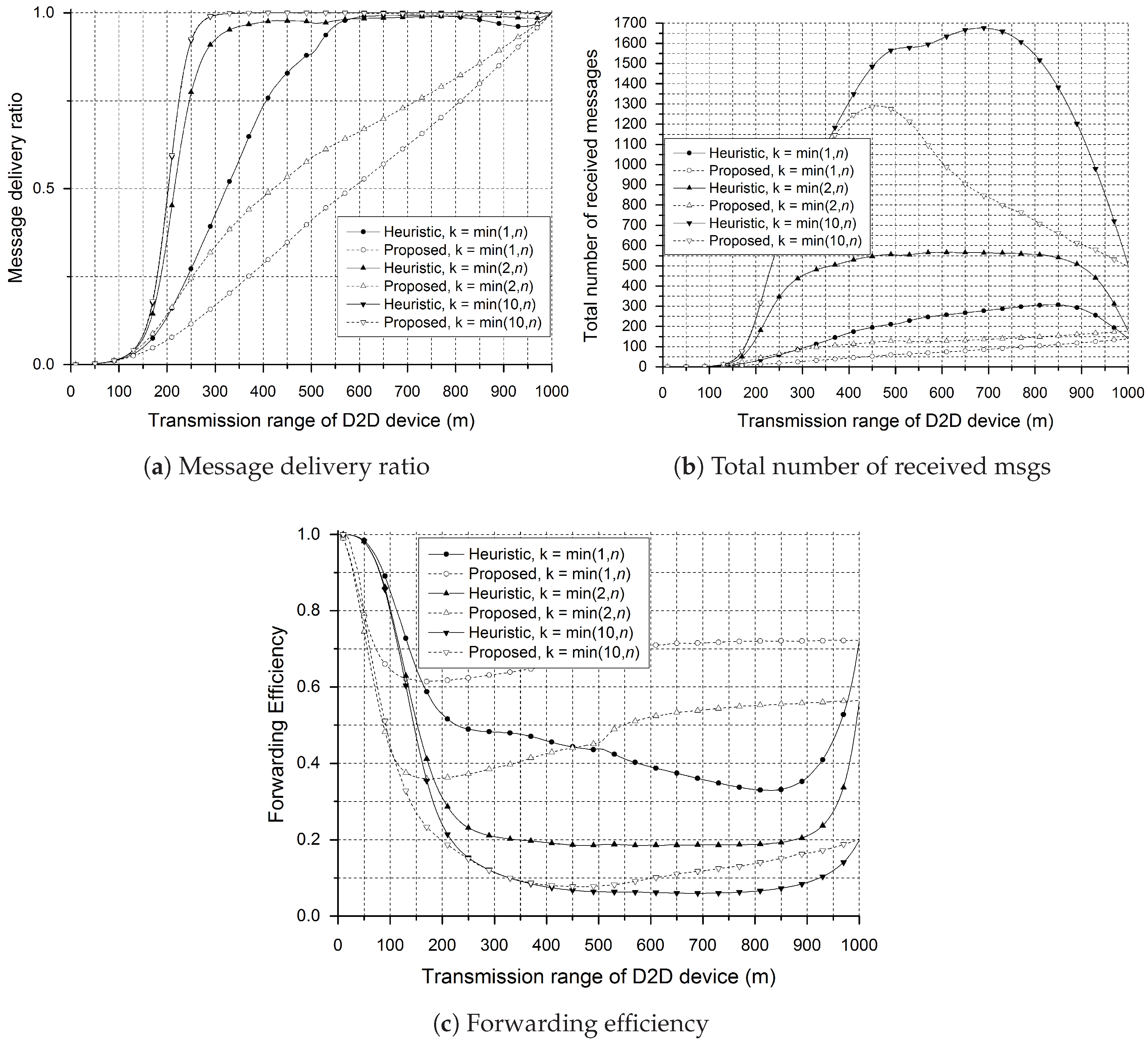
3. Simulation Results
4. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Series, M. IMT Vision—Framework and Overall Objectives of the Future Development of IMT for 2020 and Beyond; Recommendation ITU-R: Geneva, Switzerland, 2015. [Google Scholar]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Boccardi, F.; Heath, R.W.; Lozano, A.; Marzetta, T.L.; Popovski, P. Five disruptive technology directions for 5G. IEEE Commun. Mag. 2014, 52, 74–80. [Google Scholar] [CrossRef]
- Asadi, A.; Wang, A.Q.; Mancuso, V. A survey on device-to-device communication in cellular networks. IEEE Commun. Surv. Tutor. 2014, 16, 1801–1819. [Google Scholar] [CrossRef]
- Liu, J.; Kato, N.; Ma, J.; Kadowaki, N. Device-to-device communication in LTE-advanced networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1923–1940. [Google Scholar] [CrossRef]
- Choi, K.W.; Han, Z. Device-to-device discovery for proximitybased service in LTE-advanced system. IEEE J. Sel. Areas Commun. 2015, 33, 55–66. [Google Scholar] [CrossRef]
- Haus, M.; Waqas, M.; Ding, A.Y.; Li, Y.; Tarkoma, S.; Ott, J. Security and privacy in device-to-device (D2D) communication: A review. IEEE Commun. Surv. Tutor. 2017, 19, 1054–1079. [Google Scholar] [CrossRef]
- Huang, J.; Xing, C.; Qian, Y.; Haas, Z.J. Resource allocation for multicell device-to-device communications underlaying 5G networks: A game theoretic mechanism with incomplete information. IEEE Trans. Veh. Technol. 2018, 67, 2557–2570. [Google Scholar] [CrossRef]
- Chakchouk, N. A survey on opportunistic routing in wireless communication networks. IEEE Commun. Surv. Tutor. 2015, 17, 2214–2241. [Google Scholar] [CrossRef]
- Han, S.; Lee, H.; Kim, J.; Lee, W. On the Connectivity in Opportunistic D2D Networks with Hierarchical/Non-Hierarchical Clustering. In Proceedings of the IEEE GLOBECOM’16 Workshop on Wireless for Big Data and Big Data for Wireless, Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Chi, K.; Huang, L.; Li, Y.; Zhu, Y.; Tian, X.; Xia, M. Efficient and reliable multicast using device-to-device communication and network coding for a 5G network. IEEE Netw. 2017, 31, 78–84. [Google Scholar] [CrossRef]
- Chen, G.; Tang, J.; Coon, J.P. Optimal routing for multi-hop social based d2d communications in the internet of things. IEEE Int. Things J. 2018, 5, 1880–1889. [Google Scholar] [CrossRef]
- Shaikh, F.S.; Wismuller, R. Routing in multi-hop cellular device-to-device (D2D) networks: A survey. IEEE Commun. Surv. Tutor. 2018. [Google Scholar] [CrossRef]
- Aldawsari, B.; Baker, T.; England, D. Trusted Energy-Efficient Cloud-Based Services Brokerage Platform. Int. J. Intell. Comput. Res. 2015, 6, 630–639. [Google Scholar] [CrossRef]
- Baker, T.; Asim, M.; Tawfik, H.; Aldawsari, B.; Buyya, R. An energy-aware service composition algorithm for multiple cloud-based IoT applications. J. Netw. Comput. Appl. 2017, 89, 96–108. [Google Scholar] [CrossRef]
- Baker, T.; Ngoko, Y.; Tolosana-Calasanz, R.; Rana, O.F.; Randles, M. Energy Efficient Cloud Computing Environment via Autonomic Meta-director Framework. In Proceedings of the 2013 Sixth International Conference on IEEE Developments in eSystems Engineering, Abu Dhabi, UAE, 16–18 December 2013; pp. 198–203. [Google Scholar]
- Baker, T.; Al-Dawsari, B.; Tawfik, H.; Reid, D.; Ngoko, Y. GreeDi: An energy efficient routing algorithm for big data on cloud. Ad. Hoc. Netw. 2015, 35, 83–96. [Google Scholar] [CrossRef]
- Baker, T.; Lamb, D.; Taleb-Bendiab, A.; Al-Jumeily, D. Facilitating Semantic Adaptation of Web Services at Runtime Using a Meta-Data Layer. In Proceedings of the IEEE Developments in eSystems Engineering, London, UK, 6–8 September 2010; pp. 231–236. [Google Scholar]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected Ad Hoc Networks; Technical Report CS-200006; Duke University: Durham, NH, USA, 2000. [Google Scholar]
- Erramilli, V.; Crovella, M.; Chaintreau, A.; Diot, C. Delegation forwarding. In Proceedings of the 9th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hong Kong, China, 26–30 May 2008. [Google Scholar]
- Lindgren, A.; Doria, A.; Schelen, O. Probabilistic Routing in Intermittently Connected Networks. In Service Assurance with Partial and Intermittent Resources; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3126, pp. 239–254. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. BUBBLE Rap: Social-based forwarding in delay-tolerant networks. IEEE Trans. Mob. Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Srinivasa, S.; Haenggi, M. Distance distributions in finite uniformly random networks: Theory and applications. IEEE Trans. Veh. Technol. 2010, 59, 940–949. [Google Scholar] [CrossRef]
- Press, W.H.; Teukolsky, S.A.; Vetterling, W.T.; Flannery, B.P. Numerical Recipes 3rd Edition: The Art of Scientific Computing; Cambridge University Press: New York, NY, USA, 2007. [Google Scholar]

© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, S.; Lee, K.; Choi, H.-H.; Lee, H. BiPAD: Binomial Point Process Based Energy-Aware Data Dissemination in Opportunistic D2D Networks. Energies 2018, 11, 2073. https://doi.org/10.3390/en11082073
Han S, Lee K, Choi H-H, Lee H. BiPAD: Binomial Point Process Based Energy-Aware Data Dissemination in Opportunistic D2D Networks. Energies. 2018; 11(8):2073. https://doi.org/10.3390/en11082073
Chicago/Turabian StyleHan, Seho, Kisong Lee, Hyun-Ho Choi, and Howon Lee. 2018. "BiPAD: Binomial Point Process Based Energy-Aware Data Dissemination in Opportunistic D2D Networks" Energies 11, no. 8: 2073. https://doi.org/10.3390/en11082073
APA StyleHan, S., Lee, K., Choi, H.-H., & Lee, H. (2018). BiPAD: Binomial Point Process Based Energy-Aware Data Dissemination in Opportunistic D2D Networks. Energies, 11(8), 2073. https://doi.org/10.3390/en11082073





