Model, Characterization, and Analysis of Steady-State Security Region in AC/DC Power System with a Large Amount of Renewable Energy
Abstract
:1. Introduction
2. Model of the Steady-State Security Region of an AC/DC Power System
2.1. AC/DC System Equality Constraints
2.2. AC/DC System Inequality Constraints
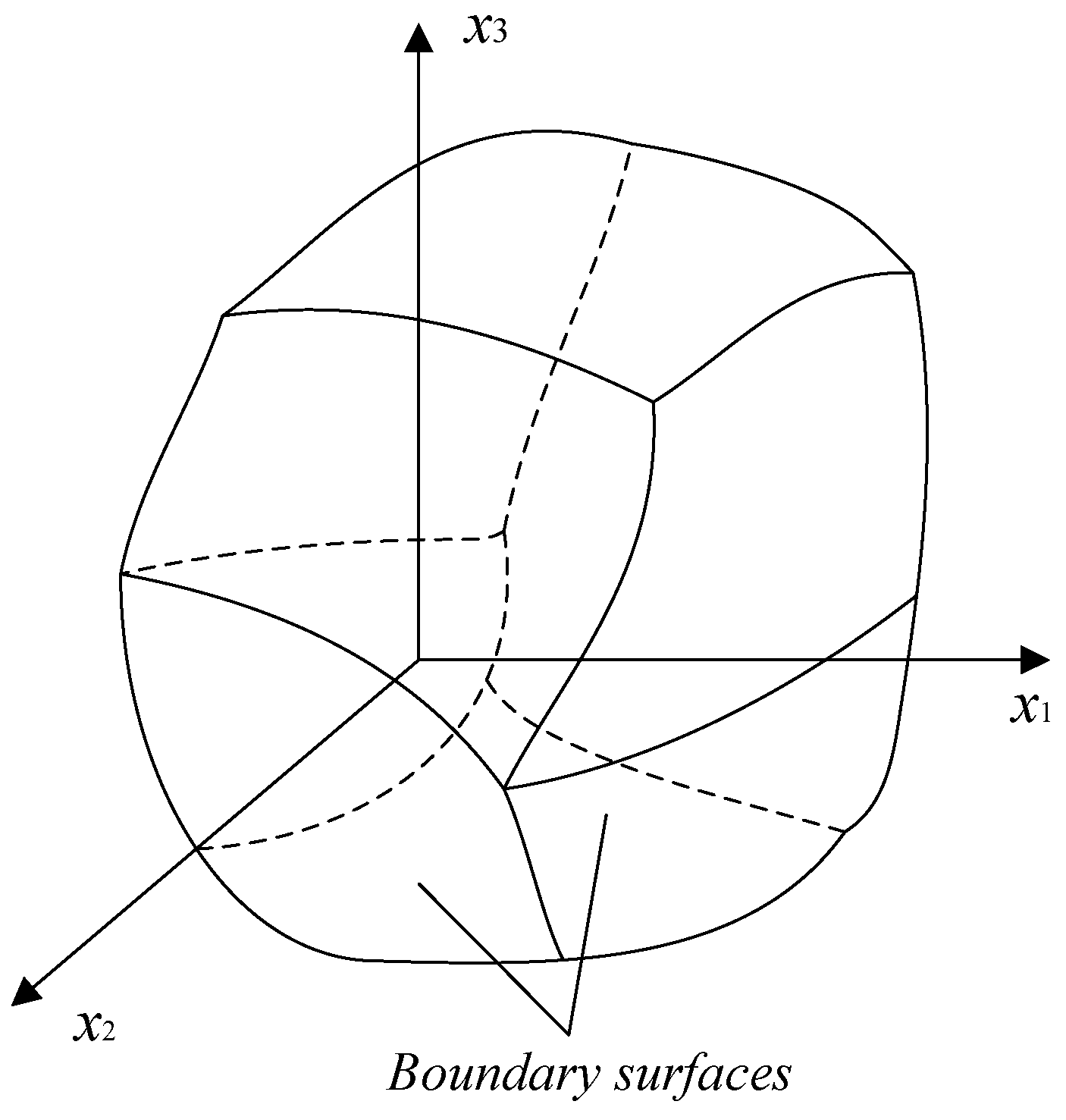
2.3. Definition of the Steady-State Security Region of an AC/DC Hybrid System
3. Characterization and Analysis of the Steady-State Security Region of an AC/DC System
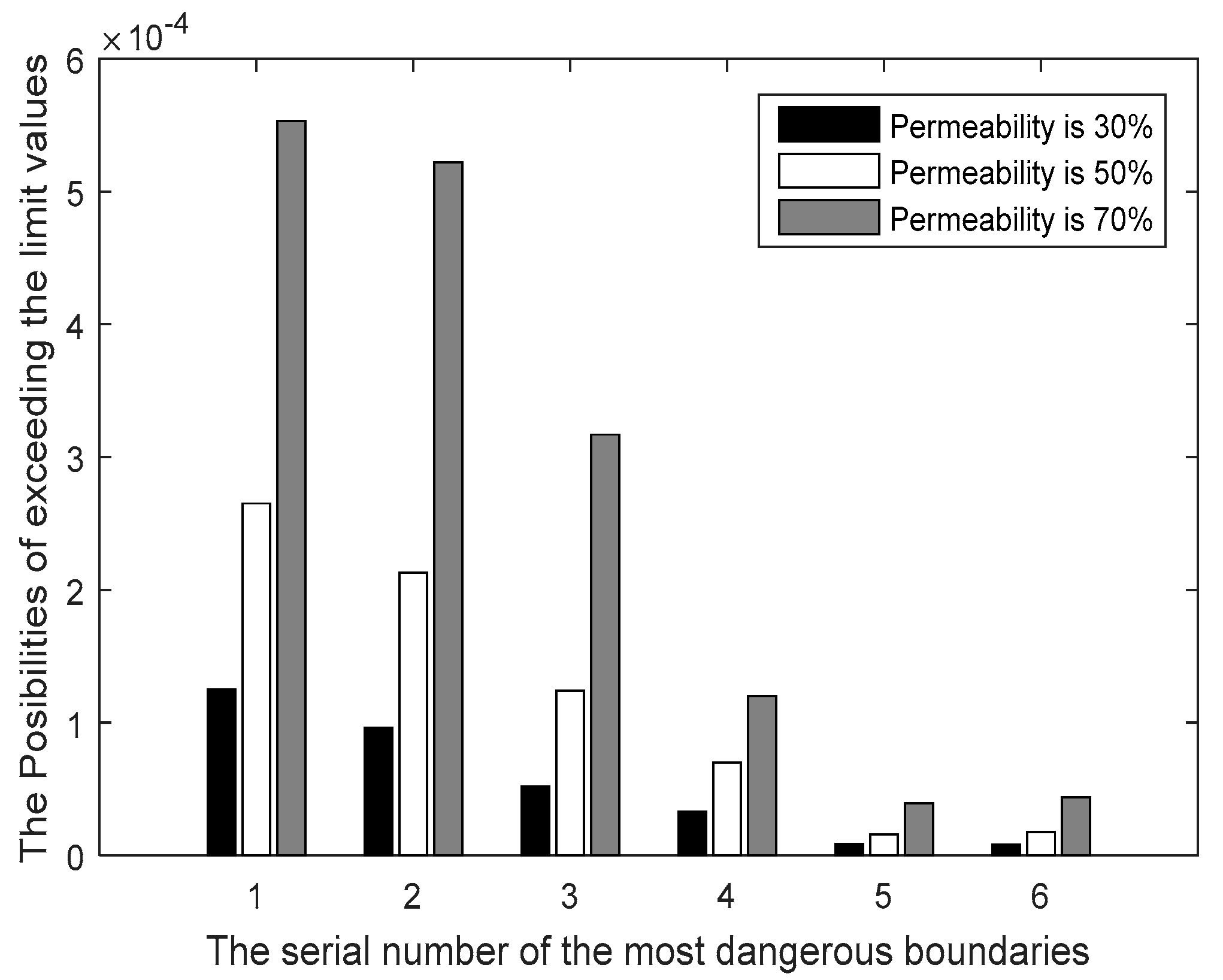
3.1. The Effective Boundaries Screening and the Solution of Distances between the Operating Point and the Effective Boundaries
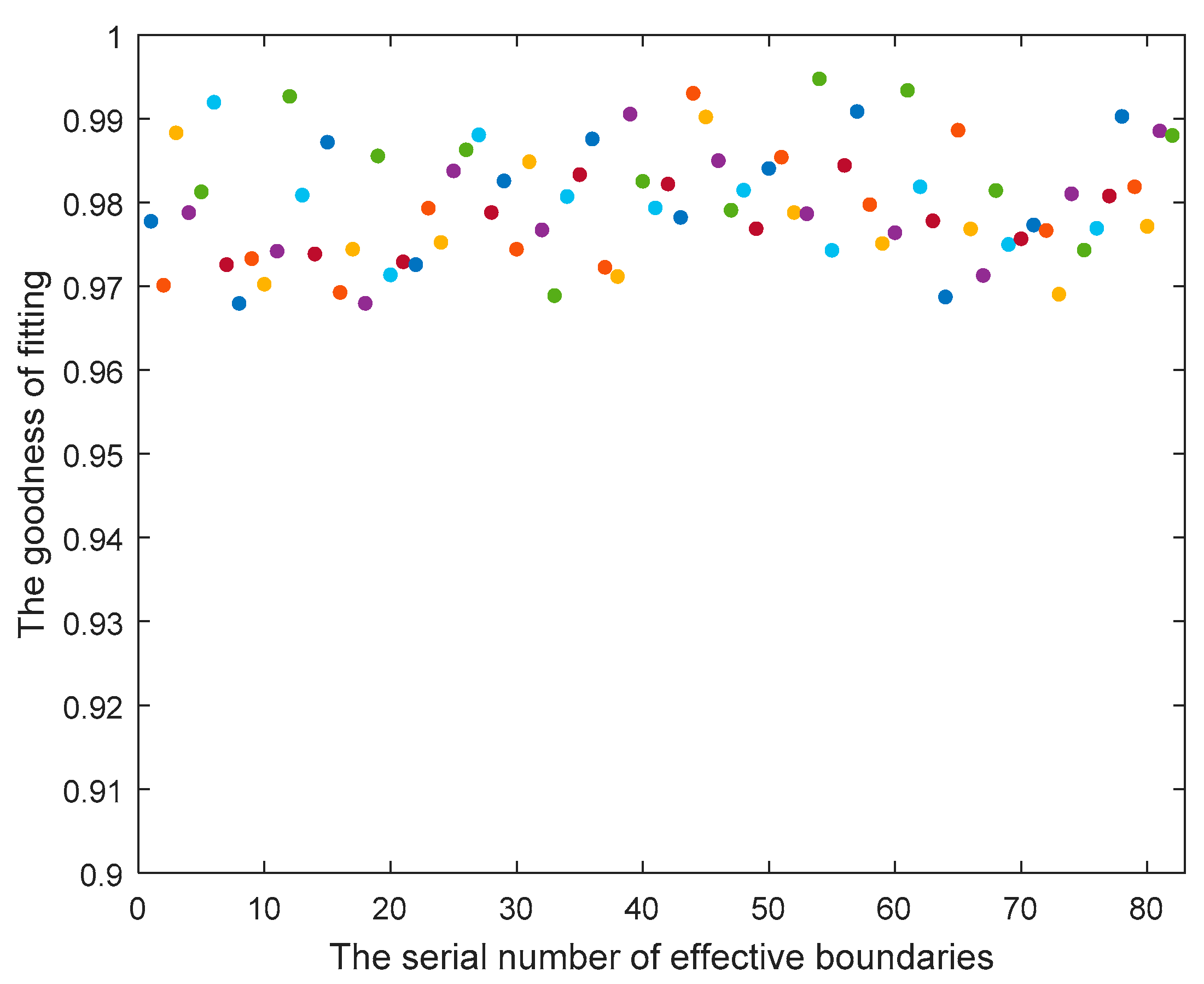
3.2. Regression of Effective Boundaries
3.3. Safety Judgment of the Operating Point
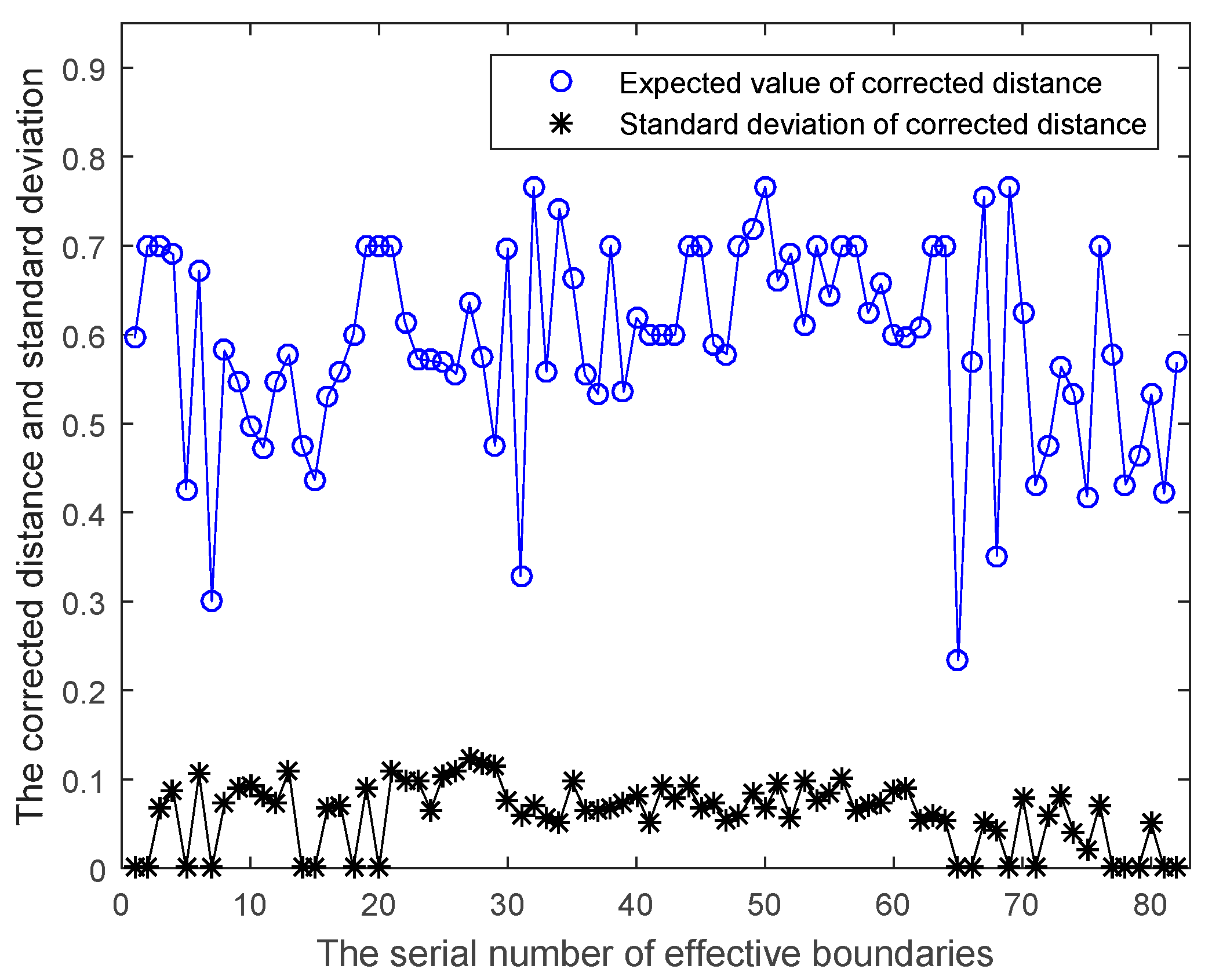
3.4. The Solution of Distance and Corrected Distance Based on the Regression Results
3.5. The Physical Meaning of the Corrected Distance
3.6. Probabilistic Analysis of Corrected Distance Considering the Fluctuations of Renewable Energy
4. Case Study
4.1. Example of IEEE14 Standard Test System
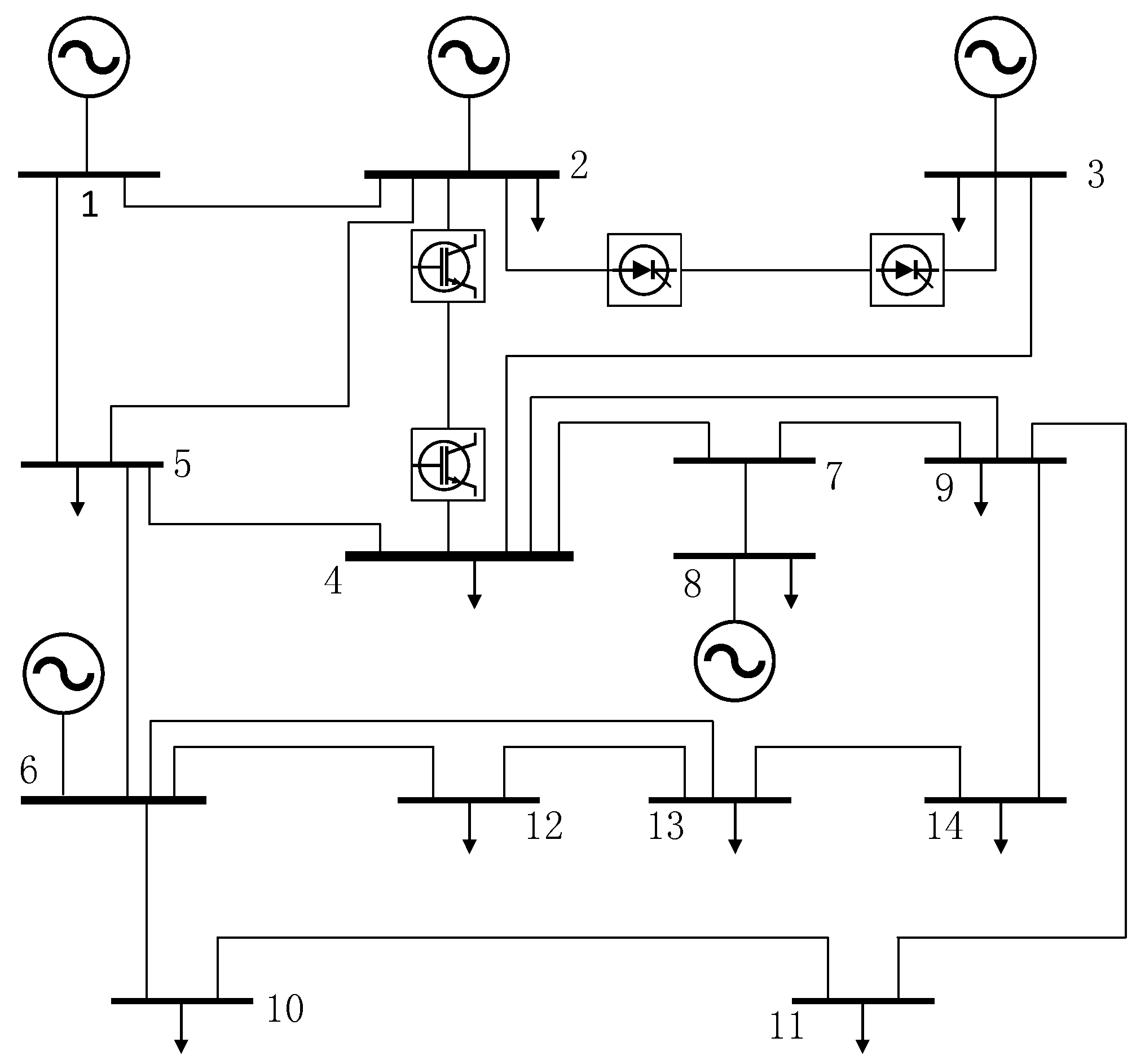
4.2. Example of Actual Power Grid
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zeng, X.J.; Yu, Y.X.; Huang, C.H. Steady-state security region (SSR) and its visualization of bulk high voltage power system. In Proceedings of the International Conference on Power System Technology, Kunming, China, 13–17 October 2002; pp. 1259–1263. [Google Scholar]
- Xiao, J.; Su, B.Y.; Li, X.; Wang, C.S. Secure region of network and comparison with invulnerability. Complex Syst. Complex. Sci. 2016, 4, 41–50. [Google Scholar]
- Galiana, F.D. Analytic properties of the load flow problem. In Proceedings of the International Symposium on Circuits System Special Session on Power System, Philadelphia, PA, USA, 5–7 May 1977; pp. 802–816. [Google Scholar]
- Galiana, F.D.; Lee, K. On the steady stability of power system. In Proceedings of the Power Industry Computer Applications Conference, Toronto, ON, Canada, 9–10 January 1977; pp. 201–210. [Google Scholar]
- Jarjis, J.; Galiana, F.D. Quantitative analysis of steady state stability in power networks. IEEE Trans. Power Appar. Syst. 1981, PAS-100, 318–326. [Google Scholar] [CrossRef]
- Felix, F.W. Steady-state secutity regions of power systems. IEEE Trans. Circuits Syst. 1982, 29, 703–711. [Google Scholar]
- Yu, Y.X.; Feng, F. Active power steady-state security region of power system. Sci. China Ser. A 1990, 33, 664–672. [Google Scholar]
- Huang, C.H.; Yu, Y.X.; Ge, S.Y. Reactive power steady state security region. J. Tianjin Univ. 1987, 8, 77–86. [Google Scholar]
- Hnyilina, E.; Lee, S.T.Y.; Schweppe, F.C. Steady-state security regions: The set-theoretic approach. In Proceedings of the PICA Conference, Vancouver, BC, Canada, 28–31 May 1975; pp. 347–355. [Google Scholar]
- Fischl, R.; DeMaio, J.A. Fast identification of the steady-state security regions for power system security enhancement. In Proceedings of the IEEE PES Winter Meeting, Detroit, MI, USA, 11–15 January 1976. Paper No. A76-076-0. [Google Scholar]
- Chen, S.J.; Chen, Q.X.; Xia, Q. Steady-state security assessment method based on distance to security region boundaries. IET Gener. Transm. Distrib. 2013, 7, 288–297. [Google Scholar] [CrossRef]
- Chen, S.J.; Chen, Q.X.; Xia, Q. N−1 security assessment approach based on the steady-state security distance. IET Gener. Transm. Distrib. 2015, 9, 2419–2426. [Google Scholar] [CrossRef]
- Hu, L.L.; Zhao, J.L.; Jia, H.J.; Guo, X.L.; Zeng, Q. Computing the boundary of simple power system feasible region based on the optimization method. In Proceedings of the Innovative Smart Grid Technologies—Asia (ISGT Asia), Tianjin, China, 21–24 May 2012; pp. 1–6. [Google Scholar]
- Yao, R.; Liu, F.; He, G.Y.; Fang, B.; Huang, L. Static security region calculation with improved CPF considering generation regulation. In Proceedings of the 2012 IEEE International Conference on Power System Technology (POWERCON), Auckland, New Zealand, 30 October–2 November 2012; pp. 1–6. [Google Scholar]
- Rault, P.; Guillaud, X.; Colas, F. Investigation on interactions between AC and DC grids. In Proceedings of the 2013 IEEE Grenoble Conference, Grenoble, France, 16–20 June 2013; pp. 1–6. [Google Scholar]
- Fan, J.C. Dynamic Security Region for AC/DC Parallel System and its Critical Cutset Representation. Ph.D. Thesis, Tianjing University, Tianjin, China, 2005. [Google Scholar]
- Wang, C.C. Practical Dynamic Security Regions of AC/DC Parallel Systems to Guarantee Short-term Voltage Stability of Large Disturbance. Master’s Thesis, Tianjing University, Tianjin, China, 2007. [Google Scholar]
- Shao, C.; Wang, X.; Shahidehpour, M.; Wang, X.; Wang, B. Power system economic dispatch considering steady-state secure region for wind power. IEEE Trans. Sustain. Energy 2017, 1, 268–278. [Google Scholar] [CrossRef]
- Cheng, F.; Yang, M.; Han, X.; Liang, J. Real-time dispatch based on effective steady-state security regions of power systems. In Proceedings of the 2014 IEEE PES General Meeting—Conference & Exposition, National Harbor, MD, USA, 27–31 July 2014; pp. 1–5. [Google Scholar]
- Chen, S.J.; Chen, Q.X.; Xia, Q. Steady-state security distance: Concept, model and meaning. Proc. CSEE 2015, 35, 600–608. (In Chinese) [Google Scholar]
- Kundur, P. Power System Stability and Control; McGraw-Hill Education: New York, NY, USA, 1994; pp. 463–576. [Google Scholar]
- Ni, Y.X.; Chen, S.S.; Sun, B.L. Theory and Analysis of Dynamic Power System; Tsinghua University Press: Beijing, China, 2002; pp. 106–117. [Google Scholar]
- Kim, C.K.; Sood, V.K.; Jang, G.S. HVDC Transmission: Power Conversion Applications in Power Systems; John Wiley & Sons: Singapore, 2009; pp. 125–186. [Google Scholar]
- Sood, V.K. HVDC and Facts Controllers-Applications of Static Converters in Power Systems; Springer Science & Business Media: Boston, MA, USA, 2004; pp. 49–65. [Google Scholar]
- Muhammad, H.R. Power Electronics: Circuits, Devices, and Applications, 3rd ed.; Pearson Education: New Delhi, India, 2004; pp. 226–303. [Google Scholar]
- Dy-Liacco, T.E. Real time computer control of power system. Proc. IEEE 1974, 62, 884–891. [Google Scholar] [CrossRef]

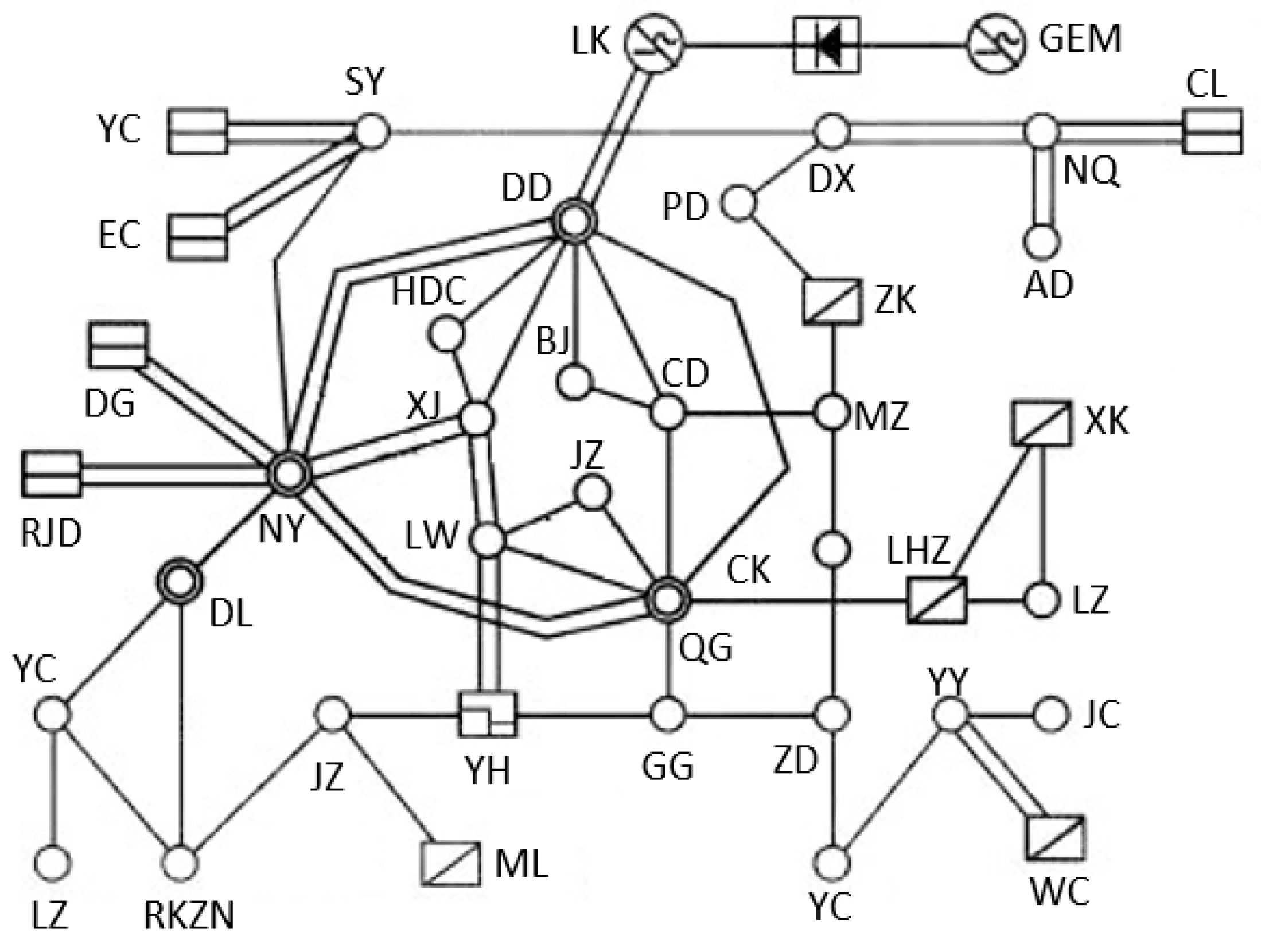
| Quantity | Value |
|---|---|
| DC voltage | 200 kV |
| DC current | 350 A |
| Ignition angle | 21.79° |
| Extinction angle | 23.61° |
| Internal reactance | 0.067 H |
| DC resistance | 28.54 Ω |
| Filter capacitance | 50 MVar |
| The ratio of converter transformers | 1:1.2 |
| Quantity | Value |
|---|---|
| DC voltage | 200 kV |
| DC current | 266.7 A |
| Reactive power of rectifier | −15.7 MVar |
| Reactive power of inverter | 13.7 MVar |
| Commutation reactance | 11.42 H |
| DC resistance | 37.46 Ω |
| Modulation of rectifier | 1.097 |
| Phase shift angle of rectifier | 1.5616° |
| Modulation of inverter | 0.997 |
| Phase shift angle of inverter | 1.5947° |
| Quantity | Upper Bound | Lower Bound |
|---|---|---|
| Bus voltage | 1.15 | 0.95 |
| Phase difference of line | 15° | −15° |
| Active power of balancing machine | 5 | 0 |
| Reactive power of balancing machine | 2.5 | −2.5 |
| DC voltage of LCC-HVDC | 1.8 | 1.2 |
| DC current of LCC-HVDC | 0.6 | 0.1 |
| Ignition angle | 50° | 5° |
| Extinction angle | 35° | 15° |
| Reactive power compensation capacity | 0.8 | 0 |
| DC voltage of VSC-HVDC | 1.6 | 1.0 |
| DC current of VSC-HVDC | 0.6 | 0.1 |
| Phase shift angle | 3° | 0° |
| Modulation of inverter | 1.4 | 0 |
| Reactive power setting value of VSC-HVDC | 1 | −1 |
| Active power setting value of VSC-HVDC | 1.1 | 0 |
| Effective Boundary | Corrected Distance | Standard Deviation | Probability of Unsafety |
|---|---|---|---|
| Upper bound of DC current of LCC | 0.2340 | 0 | 0 |
| Upper bound of voltage amplitude of bus 8 | 0.3000 | 0 | 0 |
| Upper bound of phase angle difference of line 1–5 | 0.3214 | 0.0589 | 0.0144 |
| Lower bound of ignition angle | 0.3514 | 0.0438 | 2.736 × 10−4 |
| Upper bound of DC current of VSC | 0.4178 | 0.0363 | 3.606 × 10−8 |
| Lower bound of reactive injection of rectifier | 0.4215 | 0.0521 | 1.342 × 10−5 |
| Upper bound of voltage amplitude of bus 6 | 0.4265 | 0 | 0 |
| Lower bound of extinction angle | 0.4305 | 0 | 0 |
| Upper bound of reactive injection of inverter | 0.4315 | 0.0398 | 9.721 × 10−8 |
| Lower bound of voltage amplitude of bus 3 | 0.4367 | 0 | 0 |
| Effective Boundary | Probability of Unsafety | Corrected Distance | Standard Deviation |
|---|---|---|---|
| Upper bound of phase angle difference of line 1–5 | 0.0144 | 0.3214 | 0.0589 |
| Upper bound of reactive power of balancing node | 0.0042 | 0.4750 | 0.1043 |
| Upper bound of voltage amplitude of bus 11 | 8.017 × 10−4 | 0.4966 | 0.0904 |
| Upper bound of voltage amplitude of bus 12 | 4.977 × 10−4 | 0.4729 | 0.0829 |
| Lower bound of ignition angle | 2.736 × 10−4 | 0.3514 | 0.0438 |
| Upper bound of voltage amplitude of bus 10 | 5.614 × 10−5 | 0.5484 | 0.0902 |
| Upper bound of phase angle difference of line 7–9 | 2.955 × 10−5 | 0.5357 | 0.0834 |
| Lower bound of reactive injection of rectifier | 1.342 × 10−5 | 0.4215 | 0.0521 |
| Lower bound of voltage amplitude of bus 4 | 1.322 × 10−5 | 0.5307 | 0.0691 |
| Upper bound of phase angle difference of line 5–6 | 2.387 × 10−6 | 0.5333 | 0.0648 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Z.; Chen, H.; Zhuang, M.; Bu, S. Model, Characterization, and Analysis of Steady-State Security Region in AC/DC Power System with a Large Amount of Renewable Energy. Energies 2017, 10, 1181. https://doi.org/10.3390/en10081181
Chen Z, Chen H, Zhuang M, Bu S. Model, Characterization, and Analysis of Steady-State Security Region in AC/DC Power System with a Large Amount of Renewable Energy. Energies. 2017; 10(8):1181. https://doi.org/10.3390/en10081181
Chicago/Turabian StyleChen, Zhong, Hui Chen, Minhui Zhuang, and Siqi Bu. 2017. "Model, Characterization, and Analysis of Steady-State Security Region in AC/DC Power System with a Large Amount of Renewable Energy" Energies 10, no. 8: 1181. https://doi.org/10.3390/en10081181
APA StyleChen, Z., Chen, H., Zhuang, M., & Bu, S. (2017). Model, Characterization, and Analysis of Steady-State Security Region in AC/DC Power System with a Large Amount of Renewable Energy. Energies, 10(8), 1181. https://doi.org/10.3390/en10081181






