High-Quality Video Watermarking Based on Deep Neural Networks for Video with HEVC Compression †
Abstract
1. Introduction
2. Literature Review
3. Proposed Method
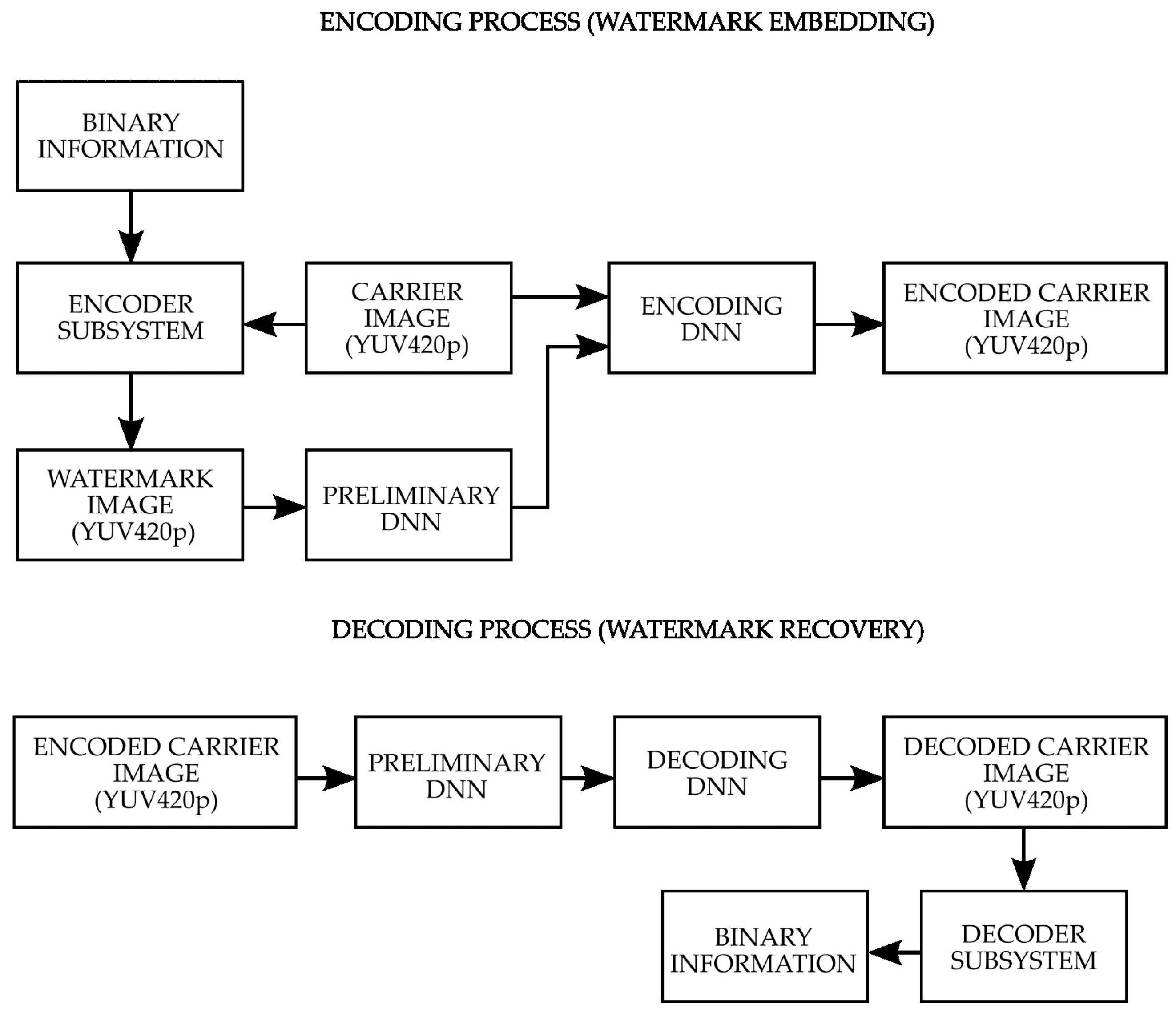
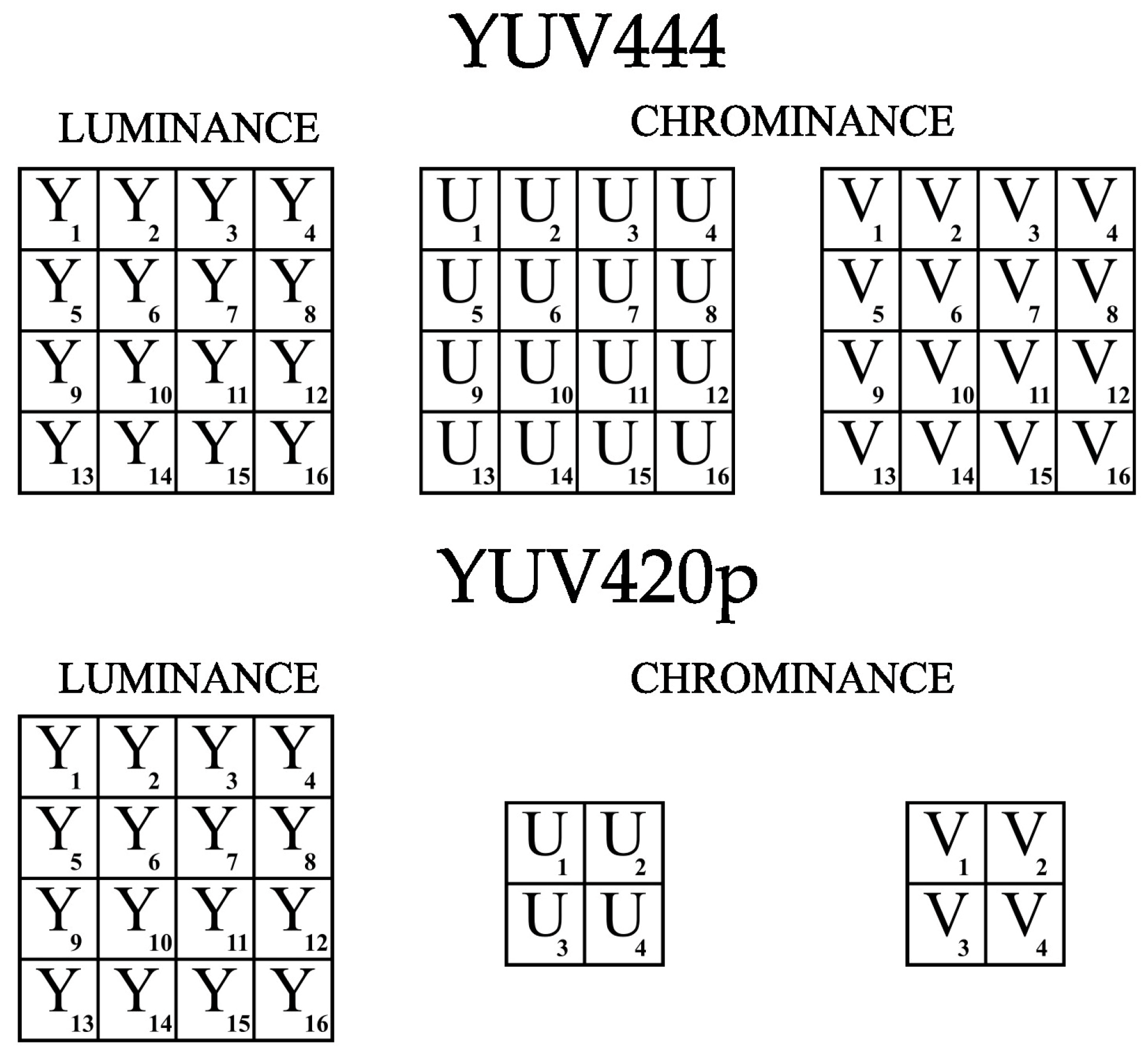
3.1. Presentation of the Concept of the Proposed Method
3.2. HEVC Compression Learning Process
3.3. Watermarking Learning Process
3.4. Edge Effect
4. Results
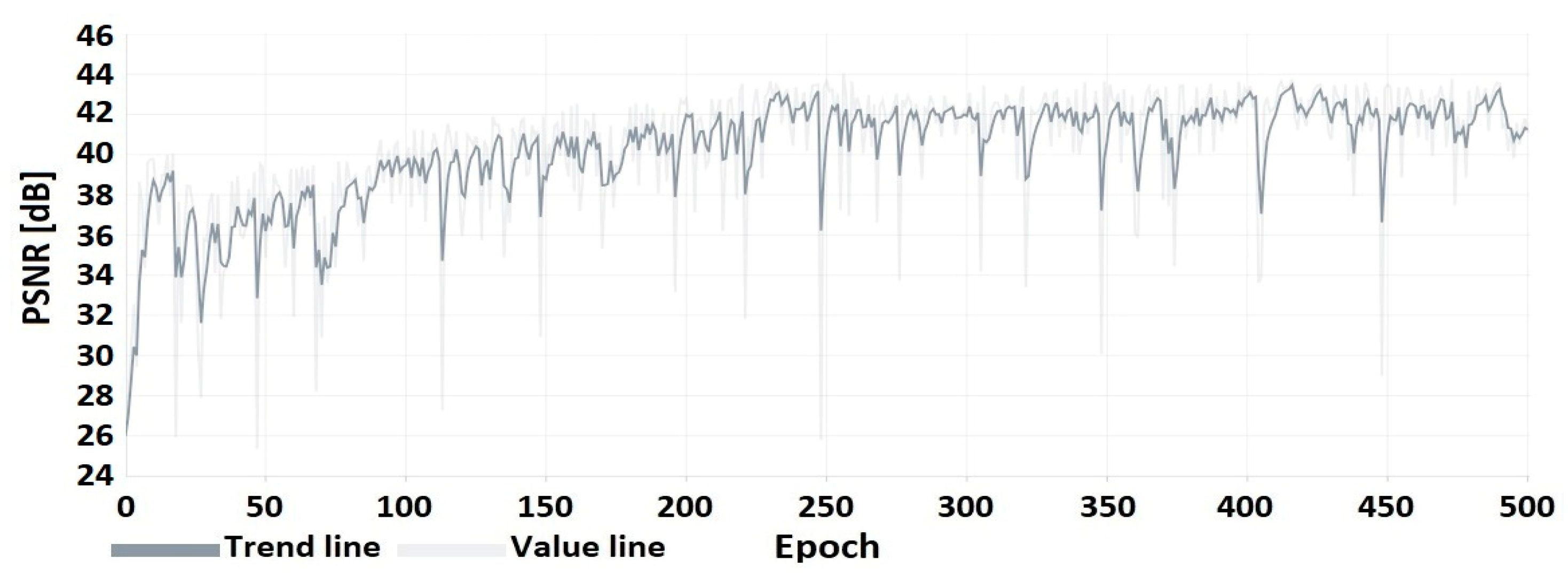
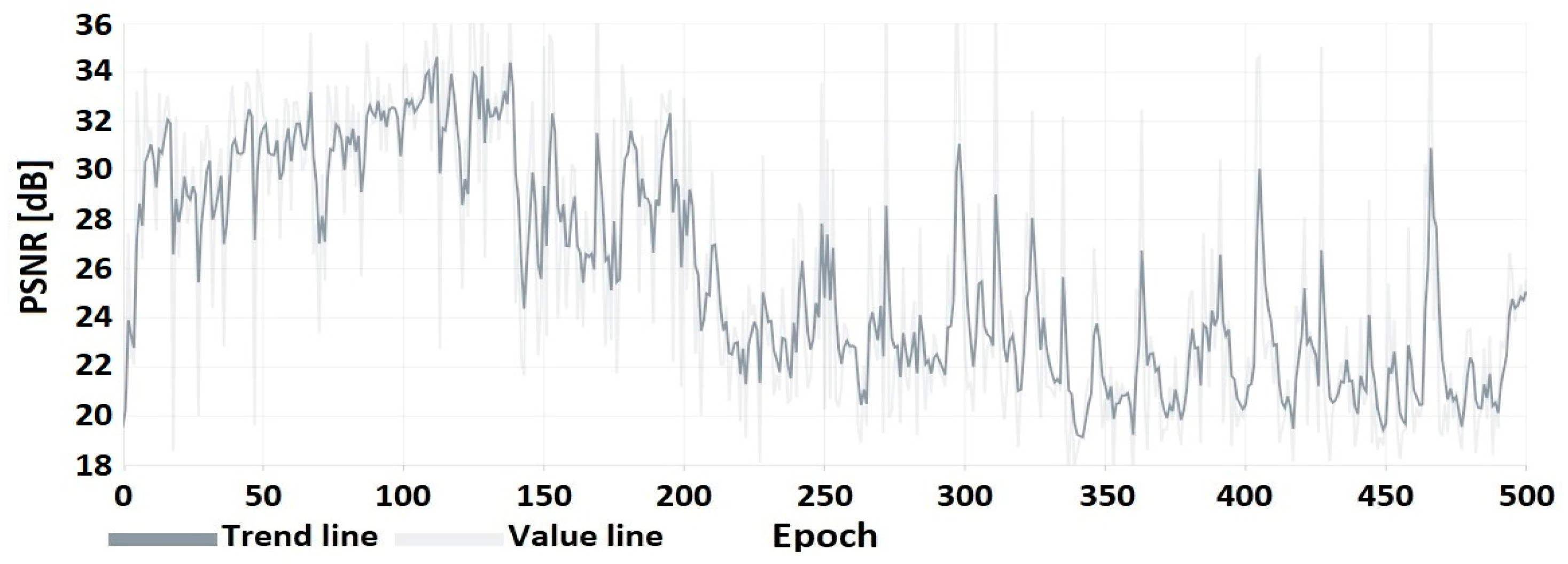
4.1. HEVC Compression Research Results
4.2. Watermarking Research Results
4.3. Comparison with Other Methods
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, X.; Wang, Z.; Yu, J.; Qian, Z. Reversible visible watermark embedded in encrypted domain. In Proceedings of the 2015 IEEE China Summit and International Conference on Signal and Information Processing (ChinaSIP), Chengdu, China, 12–15 July 2015; pp. 826–830. [Google Scholar] [CrossRef]
- Hu, Y.; Jeon, B. Reversible Visible Watermarking Technique for Images. In Proceedings of the 2006 International Conference on Image Processing, Atlanta, GA, USA, 8–11 October 2006; pp. 2577–2580. [Google Scholar] [CrossRef]
- Kumar, N.V.; Sreelatha, K.; Kumar, C.S. Invisible watermarking in printed images. In Proceedings of the 2016 1st India International Conference on Information Processing (IICIP), Delhi, India, 12–14 August 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Chacko, S.E.; Mary, I.T.B.; Raj, W.N.D. Embedding invisible watermark in digital image using interpolation and histogram shifting. In Proceedings of the 2011 3rd International Conference on Electronics Computer Technology, Kanyakumari, India, 8–10 April 2011; pp. 89–93. [Google Scholar] [CrossRef]
- Dong, L.; Yan, Q.; Liu, M.; Pan, Y. Maximum likelihood watermark detection in absolute domain using Weibull model. In Proceedings of the 2014 IEEE Region 10 Symposium, Kuala Lumpur, Malaysia, 14–16 April 2014; pp. 196–199. [Google Scholar] [CrossRef]
- Hu, L.; Jiang, L. Blind Detection of LSB Watermarking at Low Embedding Rate in Grayscale Images. In Proceedings of the 2007 Second International Conference on Communications and Networking in China, Shanghai, China, 22–24 August 2007; pp. 413–416. [Google Scholar] [CrossRef]
- Xu, C.; Lu, Y.; Zhou, Y. An automatic visible watermark removal technique using image inpainting algorithms. In Proceedings of the 2017 4th International Conference on Systems and Informatics (ICSAI), Hangzhou, China, 11–13 November 2017; pp. 1152–1157. [Google Scholar] [CrossRef]
- Liu, Y.; Zhu, Z.; Bai, X. WDNet: Watermark-Decomposition Network for Visible Watermark Removal. In Proceedings of the 2021 IEEE Winter Conference on Applications of Computer Vision (WACV), Waikoloa, HI, USA, 3–8 January 2021; pp. 3684–3692. [Google Scholar] [CrossRef]
- An, Z.; Liu, H. Research on Digital Watermark Technology Based on LSB Algorithm. In Proceedings of the 2012 Fourth International Conference on Computational and Information Sciences, Chongqing, China, 17–19 August 2012; pp. 207–210. [Google Scholar] [CrossRef]
- Giri, K.J.; Peer, M.A.; Nagabhushan, P. A channel wise color image watermarking scheme based on Discrete Wavelet Transformation. In Proceedings of the 2014 International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 5–7 March 2014; pp. 758–762. [Google Scholar] [CrossRef]
- Fan, D.; Zhang, X.; Kang, W.; Zhao, H.; Lv, Y. Video Watermarking Algorithm Based on NSCT, Pseudo 3D-DCT and NMF. Sensors 2022, 22, 4752. [Google Scholar] [CrossRef] [PubMed]
- El’arbi, M.; Amar, C.B.; Nicolas, H. Video Watermarking Based on Neural Networks. In Proceedings of the 2006 IEEE International Conference on Multimedia and Expo, Toronto, ON, Canada, 9–12 July 2006; pp. 1577–1580. [Google Scholar] [CrossRef]
- Mishra, A.; Agarwal, C.; Chetty, G. Lifting Wavelet Transform based Fast Watermarking of Video Summaries using Extreme Learning Machine. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Wagdarikar, A.M.U.; Senapati, R.K. Robust and novel blind watermarking scheme for H.264 compressed video. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems, Guntur, India, 2–3 January 2015; pp. 276–280. [Google Scholar] [CrossRef]
- Meerwald, P.; Uhl, A. Robust Watermarking of H.264-Encoded Video: Extension to SVC. In Proceedings of the 2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Darmstadt, Germany, 15–17 October 2010; pp. 82–85. [Google Scholar] [CrossRef]
- Zhou, Y.; Wang, C.; Zhou, X. An Intra-Drift-Free Robust Watermarking Algorithm in High Efficiency Video Coding Compressed Domain. IEEE Access 2019, 7, 132991–133007. [Google Scholar] [CrossRef]
- Gaj, S.; Sur, A.; Bora, P.K. A robust watermarking scheme against re-compression attack for H.265/HEVC. In Proceedings of the 2015 Fifth National Conference on Computer Vision, Pattern Recognition, Image Processing and Graphics (NCVPRIPG), Patna, India, 16–19 December 2015; pp. 1–4. [Google Scholar] [CrossRef]
- Sullivan, G.J.; Ohm, J.-R.; Han W., -J.; Wiegand, T. Overview of the High Efficiency Video Coding (HEVC) Standard. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 12. [Google Scholar] [CrossRef]
- Jiang, X.; Feng, J.; Song, T.; Katayama, T. Low-Complexity and Hardware-Friendly H.265/HEVC Encoder for Vehicular Ad-Hoc Networks. Sensors 2019, 19, 1927. [Google Scholar] [CrossRef] [PubMed]
- Pan, Z.; Chen, L.; Sun, X. Low Complexity HEVC Encoder for Visual Sensor Networks. Sensors 2015, 15, 30115–30125. [Google Scholar] [CrossRef]
- Jiang, X.; Song, T.; Zhu, D.; Katayama, T.; Wang, L. Quality-Oriented Perceptual HEVC Based on the Spatiotemporal Saliency Detection Model. Entropy 2019, 21, 165. [Google Scholar] [CrossRef] [PubMed]
- Kaczyński, M.; Piotrowski, Z. High-Quality Video Watermarking Based on Deep Neural Networks and Adjustable Subsquares Properties Algorithm. Sensors 2022, 22, 5376. [Google Scholar] [CrossRef]
- Upadhyay, J.; Mishra, B.; Patel, P. A modified approach of video watermarking using DWT-BP based LSB algorithm. In Proceedings of the 2017 International Conference on Information, Communication, Instrumentation and Control (ICICIC), Indore, India, 17–19 August 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Dehkordi, A.B.; Nader-Esfahani, S.; Avanaki, A.N. Robust LSB watermarking optimized for local structural similarity. In Proceedings of the 19th Iranian Conference on Electrical Engineering, Tehran, Iran, 17–19 May 2011. [Google Scholar]
- Pehlivanoğlu, M.K.; Savaş, B.K.; Duru, N. LSB based steganography over video files using Koblitz’s Method. In Proceedings of the 23nd Signal Processing and Communications Applications Conference (SIU), Malatya, Turkey, 16–19 May 2015; pp. 1034–1037. [Google Scholar] [CrossRef]
- Ghrare, S.E.; Adim Mohamad Alamari, A.; Emhemed, H.A. Digital Image Watermarking Method Based on LSB and DWT Hybrid Technique. In Proceedings of the 2022 IEEE 2nd International Maghreb Meeting of the Conference on Sciences and Techniques of Automatic Control and Computer Engineering (MI-STA), Sabratha, Libya, 23–25 May 2022; pp. 465–470. [Google Scholar] [CrossRef]
- Şenol, A.; Dınçer, K.; Sever, H.; Elbaşi, E. Blocked-DWT based vector image watermarking. In Proceedings of the 2015 23nd Signal Processing and Communications Applications Conference (SIU), Malatya, Turkey, 16–19 May 2015; pp. 264–267. [Google Scholar] [CrossRef]
- Choudhary, R.; Parmar, G. „A robust image watermarking technique using 2-level discrete wavelet transform (DWT). In Proceedings of the 2016 2nd International Conference on Communication Control and Intelligent Systems (CCIS), Mathura, India, 18–20 November 2016; pp. 120–124. [Google Scholar] [CrossRef]
- Anushka; Saxena, A. Digital image watermarking using least significant bit and discrete cosine transformation. In Proceedings of the 2017 International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), Kannur, India, 6–7 July 2017; pp. 1582–1586. [Google Scholar] [CrossRef]
- Lee, M.; Chang, H.; Wang, M. Watermarking Mechanism for Copyright Protection by Using the Pinned Field of the Pinned Sine Transform. In Proceedings of the 2009 10th International Symposium on Pervasive Systems, Algorithms, and Networks, Kaohsiung, Taiwan, 14–16 December 2009; pp. 502–507. [Google Scholar] [CrossRef]
- Lang, J.; Sun, J.-Y.; Yang, W.-F. A Digital Watermarking Algorithm Based on Discrete Fractional Fourier Transformation. In Proceedings of the 2012 International Conference on Computer Science and Service System, Nanjing, China, 11–13 August 2012; pp. 691–694. [Google Scholar] [CrossRef]
- Kulkarni, T.S.; Dewan, J.H. Digital video watermarking using Hybrid wavelet transform with Cosine, Haar, Kekre, Walsh, Slant and Sine transforms. In Proceedings of the 2016 International Conference on Computing Communication Control and automation (ICCUBEA), Pune, India, 12–13 August 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Hasan, N.; Islam, M.S.; Chen, W.; Kabir, M.A.; Al-Ahmadi, S. Encryption Based Image Watermarking Algorithm in 2DWT-DCT Domains. Sensors 2021, 21, 5540. [Google Scholar] [CrossRef]
- Huang, T.; Xu, J.; Yang, Y.; Han, B. Robust Zero-Watermarking Algorithm for Medical Images Using Double-Tree Complex Wavelet Transform and Hessenberg Decomposition. Mathematics 2022, 10, 1154. [Google Scholar] [CrossRef]
- Li, L.; Bai, R.; Zhang, S.; Chang, C.-C.; Shi, M. Screen-Shooting Resilient Watermarking Scheme via Learned Invariant Keypoints and QT. Sensors 2021, 21, 6554. [Google Scholar] [CrossRef]
- Abdel-Aziz, M.M.; Hosny, K.M.; Lashin, N.A.; Fouda, M.M. Blind Watermarking of Color Medical Images Using Hadamard Transform and Fractional-Order Moments. Sensors 2021, 21, 7845. [Google Scholar] [CrossRef] [PubMed]
- Wang, L.; Ji, H. A Watermarking Optimization Method Based on Matrix Decomposition and DWT for Multi-Size Images. Electronics 2022, 11, 2027. [Google Scholar] [CrossRef]
- Wegner, K.; Grajek, T.; Karwowski, D.; Stankowski, J.; Klimaszewski, K.; Stankiewicz, O.; Domanski, M. Multi-generation encoding using HEVC All Intra versus JPEG 2000. In Proceedings of the 2015 57th International Symposium ELMAR (ELMAR), Zadar, Croatia, 28–30 September 2015; pp. 41–44. [Google Scholar] [CrossRef]
- Lu, G.; Ouyang, W.; Xu, D.; Zhang, X.; Cai, C.; Gao, Z. DVC: An End-to-end Deep Video Compression Framework (Version 3). arXiv 2019, arXiv:1812.00101. [Google Scholar]
- Luo, X.; Li, Y.; Chang, H.; Liu, C.; Milanfar, P.; Yang, F. DVMark: A Deep Multiscale Framework for Video Watermarking. arXiv 2021, arXiv:2104.12734. [Google Scholar]
- Gao, Y.; Kang, X.; Chen, Y. A robust video zero-watermarking based on deep convolutional neural network and self-organizing map in polar complex exponential transform domain. Multimed Tools Appl. 2021, 80, 6019–6039. [Google Scholar] [CrossRef]
- Yang, Q.; Zhang, Y.; Wang, L.; Zhao, W. Watermark Image Reconstruction Based on Deep Learning. In Proceedings of the 2019 International Conference on Sensing, Diagnostics, Prognostics, and Control (SDPC), Beijing, China, 15–17 August 2019; pp. 739–743. [Google Scholar] [CrossRef]
- Hao, K.; Feng, G.; Zhang, X. Robust image watermarking based on generative adversarial network. China Commun. 2020, 20, 131–140. [Google Scholar] [CrossRef]
- Samek, W.; Montavon, G.; Lapuschkin, S.; Anders, C.J.; Müller, K.-R. Explaining Deep Neural Networks and Beyond: A Review of Methods and Applications. Proc. IEEE 2021, 109, 247–278. [Google Scholar] [CrossRef]
- Nalini, M.K.; Radhika, K.R. Comparative analysis of deep network models through transfer learning. In Proceedings of the 2020 Fourth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 7–9 October 2020; pp. 1007–1012. [Google Scholar] [CrossRef]
- Schmidhuber, J. Deep learning in neural networks: An overview. Neural Networks. 2015, 61, 85. [Google Scholar] [CrossRef]
- Zhang, T.; Chen, S.; Wei, S.; Chen, J. A data-efficient training model for signal integrity analysis based on transfer learning. In Proceedings of the 2019 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Bangkok, Thailand, 11–14 November 2019; pp. 186–189. [Google Scholar] [CrossRef]
- Sun, Y.; Wang, J.; Huang, H.; Chen, Q. Research on scalable video watermarking algorithm based on H.264 compressed domain. Opt. Int. J. Light Electron Opt. 2020, 227, 165911. [Google Scholar] [CrossRef]
- Li, C.; Yang, Y.; Liu, K.; Tian, L. A Semi-Fragile Video Watermarking Algorithm Based on H.264/AVC. Wirel. Commun. Mob. Comput. 2020, 2020, 8848553. [Google Scholar] [CrossRef]
- Dhevanandhini, G.; Yamuna, G. An effective and secure video watermarking using hybrid technique. Multimed. Syst. 2021, 27, 953–967. [Google Scholar] [CrossRef]
- Liu, Y.; Zhao, H.; Liu, S.; Feng, S.; Liu, S. A Robust and Improved Visual Quality Data Hiding Method for HEVC. IEEE Access 2018, 6, 53984–53997. [Google Scholar] [CrossRef]
- Sara, U.; Akter, M.; Uddin, M. Image Quality Assessment through FSIM, SSIM, MSE and PSNR—A Comparative Study. J. Comput. Commun. 2019, 7, 8. [Google Scholar] [CrossRef]
- Zhang, Z. Improved adam optimizer for deep neural networks. In Proceedings of the 2018 IEEE/ACM 26th International Symposium on Quality of Service (IWQoS), Banff, AB, Canada, 4–6 June 2018; pp. 1–2. [Google Scholar] [CrossRef]
- LG: Spain and Patagonia. Available online: https://4kmedia.org/lg-spain-and-patagonia-uhd-4k-demo/ (accessed on 17 September 2022).
- Berrou, C.; Glavieux, A.; Thitimajshima, P. Near Shannon limit error-correcting coding and decoding: Turbo-codes.1. In Proceedings of the ICC’93-IEEE International Conference on Communications, Geneva, Switzerland, 23–26 May 1993; Volume 2, pp. 1064–1070. [Google Scholar] [CrossRef]
- Li, J.; Wang, X.; He, J.; Su, C.; Shan, L. Turbo Decoder Design based on an LUT-Normalized Log-MAP Algorithm. Entropy 2019, 21, 814. [Google Scholar] [CrossRef]
- El-Abbasy, K.; Taki Eldin, R.; El Ramly, S.; Abdelhamid, B. Optimized Polar Codes as Forward Error Correction Coding for Digital Video Broadcasting Systems. Electronics 2021, 10, 2152. [Google Scholar] [CrossRef]
- Cao, Y.; Li, W.; Zhang, J.; Peng, X.; Li, Y. The Polar Code Construction Method in Free Space Optical Communication. Photonics 2022, 9, 599. [Google Scholar] [CrossRef]






| Digit | Value Range | RGB Value Range |
|---|---|---|
| 0 | ||
| 1 | ||
| 2 | ||
| 3 | ||
| 4 | ||
| 5 | ||
| 6 | ||
| 7 |
| Layer Number | Layer Type |
|---|---|
| 1 | Convolution 2D layer |
| 2 | Batch Normalization |
| 3 | Convolution 2D layer |
| 4 | Batch Normalization |
| 5 | Convolution 2D layer |
| 6 | Batch Normalization |
| Layer Number | Layer Type | Parameters |
|---|---|---|
| 1 | BL | activation function: LeakyReLU |
| kernel size: 3 × 3 | ||
| filter number: 63 | ||
| 2 | BL | activation function: LeakyReLU |
| kernel size: 5 × 5 | ||
| filter number: 63 | ||
| 3 | Concatenate ((1, 2), axis = 3) | - |
| 4 | BL | activation function: LeakyReLU |
| kernel size: 5 × 5 | ||
| filter number: 63 | ||
| 5 | BL | activation function: LeakyReLU |
| kernel size: 3 × 3 | ||
| filter number: 63 | ||
| 6 | Concatenate ((4, 5), axis = 3) | - |
| Layer Number | Layer Type | Parameters |
|---|---|---|
| 1 | BL | activation function: LeakyReLU |
| kernel size: 3 × 3 | ||
| filter number: 63 | ||
| 2 | BL | activation function: LeakyReLU |
| kernel size: 5 × 5 | ||
| filter number: 63 | ||
| 3 | BL | activation function: LeakyReLU |
| kernel size: 7 × 7 | ||
| filter number: 63 | ||
| 4 | Concatenate ((1, 2, 3), axis = 3) | - |
| 5 | Batch Normalization (4) | |
| 6 | BL | activation function: LeakyReLU |
| kernel size: 3 × 3 | ||
| filter number: 63 | ||
| 7 | BL | activation function: LeakyReLU |
| kernel size: 7 × 7 | ||
| filter number: 63 | ||
| 8 | Concatenate ((6, 7), axis = 3) | - |
| 9 | Batch Normalization (8) | |
| 10 | BL | activation function: LeakyReLU |
| kernel size: 7 × 7 | ||
| filter number: 63 | ||
| 11 | BL | activation function: LeakyReLU |
| kernel size: 5 × 5 | ||
| filter number: 63 | ||
| 12 | BL | activation function: LeakyReLU |
| kernel size: 3 × 3 | ||
| filter number: 63 | ||
| 13 | Concatenate ((10, 11, 12), axis = 3) | - |
| Batch Normalization (13) | ||
| 14 | Convolution 2D layer | activation function: LeakyReLU |
| kernel size: 1 |
| Type | InputTensor Size | Number of Weights | Size on Disk | Processing Time for a Single Tensor [ms] | GPU Processor |
|---|---|---|---|---|---|
| Coder | (192, 128, 1) | 5771494 | 69.00 MB | 61.551 | GeForce 1080Ti GTX 11GB |
| Type | Input Tensor Size | Number of Weights | Size on Disk | Processing Time for a Single Tensor [ms] | GPU Processor |
|---|---|---|---|---|---|
| Encoder | (2, 192, 128, 1) | 5776723 | 69.10 MB | 62.234 | GeForce 1080Ti GTX 11GB |
| Decoder | (192, 128, 1) | 5771494 | 69.00 MB | 61.424 |
| Frame # | Original | CRF 0 | CRF 7 | CRF 16 | CRF 23 | CRF 24 | CRF 28 | CRF 31 | CRF 41 | CRF 51 |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | PSNR 1: 52.18 | PSNR: 52.18 | PSNR: 52.18 | PSNR: 52.17 | PSNR: 52.10 | PSNR: 52.08 | PSNR: 51.97 | PSNR: 51.78 | PSNR: 50.82 | PSNR: 44.27 |
| MSE 2: 4.29 × 10−7 | MSE: 4.36 × 10−7 | MSE: 4.36 × 10−7 | MSE: 4.77 × 10−7 | MSE: 6.33 × 10−7 | MSE: 6.69 × 10−7 | MSE: 8.83 × 10−7 | MSE: 1.19 × 10−6 | MSE: 2.70 × 10−6 | MSE: 1.95 × 10−5 | |
| 5 | PSNR: 51.73 | PSNR: 51.72 | PSNR: 51.72 | PSNR: 51.51 | PSNR: 51.03 | PSNR: 50.94 | PSNR: 50.35 | PSNR: 49.72 | PSNR: 47.11 | PSNR: 44.32 |
| MSE: 5.00 × 10−7 | MSE: 5.23 × 10−7 | MSE: 5.23 × 10−7 | MSE: 1.04 × 10−6 | MSE: 2.27 × 10−6 | MSE: 2.51 × 10−6 | MSE: 4.07 × 10−6 | MSE: 5.58 × 10−6 | MSE: 1.46 × 10−5 | MSE: 3.40 × 10−5 | |
| 10 | PSNR: 53.44 | PSNR: 53.42 | PSNR: 53.42 | PSNR: 52.75 | PSNR: 51.38 | PSNR: 51.11 | PSNR: 49.65 | PSNR: 48.44 | PSNR: 44.25 | PSNR: 40.68 |
| MSE: 6.42 × 10−7 | MSE: 6.71 × 10−7 | MSE: 6.70 × 10−7 | MSE: 1.57 × 10−6 | MSE: 3.93 × 10−6 | MSE: 4.52 × 10−6 | MSE: 8.13 × 10−6 | MSE: 1.18 × 10−5 | MSE: 3.56 × 10−5 | MSE: 8.35 × 10−5 | |
| 15 | PSNR: 52.33 | PSNR: 52.31 | PSNR: 52.31 | PSNR: 51.60 | PSNR: 50.19 | PSNR: 49.89 | PSNR: 48.37 | PSNR: 47.02 | PSNR: 42.27 | PSNR: 38.52 |
| MSE: 7.63 × 10−7 | MSE: 7.97 × 10−7 | MSE: 7.97 × 10−7 | MSE: 2.03 × 10−6 | MSE: 5.07 × 10−6 | MSE: 5.85 × 10−6 | MSE: 1.06 × 10−5 | MSE: 1.61 × 10−5 | MSE: 5.64 × 10−5 | MSE: 1.38 × 10−4 | |
| 20 | PSNR: 52.54 | PSNR: 52.52 | PSNR: 52.52 | PSNR: 51.66 | PSNR: 49.98 | PSNR: 49.63 | PSNR: 47.81 | PSNR: 46.22 | PSNR: 40.82 | PSNR: 36.69 |
| MSE: 8.48 × 10−7 | MSE: 8.82 × 10−7 | MSE: 8.83 × 10−7 | MSE: 2.38 × 10−6 | MSE: 6.13 × 10−6 | MSE: 7.10 × 10−6 | MSE: 1.34 × 10−5 | MSE: 2.09 × 10−5 | MSE: 8.07 × 10−5 | MSE: 2.12 × 10−4 | |
| 25 | PSNR: 51.92 | PSNR: 51.91 | PSNR: 51.91 | PSNR: 51.04 | PSNR: 49.37 | PSNR: 49.01 | PSNR: 47.17 | PSNR: 45.49 | PSNR: 39.78 | PSNR: 35.34 |
| MSE: 1.02 × 10−6 | MSE: 1.06 × 10−6 | MSE: 1.06 × 10−6 | MSE: 2.86 × 10−6 | MSE: 7.12 × 10−6 | MSE: 8.22 × 10−6 | MSE: 1.53 × 10−5 | MSE: 2.46 × 10−5 | MSE: 1.03 × 10−4 | MSE: 2.90 × 10−4 | |
| 30 | PSNR: 52.02 | PSNR: 52.00 | PSNR: 51.99 | PSNR: 51.00 | PSNR: 49.13 | PSNR: 48.73 | PSNR: 46.79 | PSNR: 45.03 | PSNR: 39.08 | PSNR: 34.51 |
| MSE: 1.26 × 10−6 | MSE: 1.30 × 10−6 | MSE: 1.30 × 10−6 | MSE: 3.34 × 10−6 | MSE: 8.18 × 10−6 | MSE: 9.45 × 10−6 | MSE: 1.75 × 10−5 | MSE: 2.81 × 10−5 | MSE: 1.21 × 10−4 | MSE: 3.52 × 10−4 |
| Frame # | CRF 0 | CRF 7 | CRF 12 | CRF 16 | CRF 20 | CRF 22 | CRF 23 | CRF 24 | CRF 25 |
|---|---|---|---|---|---|---|---|---|---|
| 1 | PSNR 1: 49.61 | PSNR: 49.61 | PSNR: 49.57 | PSNR: 49.61 | PSNR: 49.98 | PSNR: 50.22 | PSNR: 50.40 | PSNR: 50.57 | PSNR: 51.01 |
| MSE 2: 1.09 × 10−5 | MSE: 1.10 × 10−5 | MSE: 1.10 × 10−5 | MSE: 1.09 × 10−5 | MSE: 1.00 × 10−5 | MSE: 9.52 × 10−6 | MSE: 9.13 × 10−6 | MSE: 8.76 × 10−6 | MSE: 7.93 × 10−6 | |
| 5 | PSNR: 50.13 | PSNR: 50.13 | PSNR: 49.94 | PSNR: 49.65 | PSNR: 49.73 | PSNR: 49.82 | PSNR: 49.89 | PSNR: 50.08 | PSNR: 50.27 |
| MSE: 9.70 × 10−6 | MSE: 9.70 × 10−6 | MSE: 1.01 × 10−5 | MSE: 1.08 × 10−5 | MSE: 1.06 × 10−5 | MSE: 1.04 × 10−5 | MSE: 1.03 × 10−5 | MSE: 9.82 × 10−6 | MSE: 9.41 × 10−6 | |
| 10 | PSNR: 47.99 | PSNR: 47.98 | PSNR: 47.79 | PSNR: 47.48 | PSNR: 47.38 | PSNR: 47.32 | PSNR: 47.24 | PSNR: 47.35 | PSNR: 47.34 |
| MSE: 1.59 × 10−5 | MSE: 1.59 × 10−5 | MSE: 1.67 × 10−5 | MSE: 1.79 × 10−5 | MSE: 1.83 × 10−5 | MSE: 1.86 × 10−5 | MSE: 1.89 × 10−5 | MSE: 1.84 × 10−5 | MSE: 1.85 × 10−5 | |
| 15 | PSNR: 47.62 | PSNR: 47.62 | PSNR: 47.63 | PSNR: 47.03 | PSNR: 46.91 | PSNR: 46.78 | PSNR: 46.74 | PSNR: 46.75 | PSNR: 46.73 |
| MSE: 1.73 × 10−5 | MSE: 1.73 × 10−5 | MSE: 1.83 × 10−5 | MSE: 1.98 × 10−5 | MSE: 2.04 × 10−5 | MSE: 2.10 × 10−5 | MSE: 2.12 × 10−5 | MSE: 2.11 × 10−5 | MSE: 2.12 × 10−5 | |
| 20 | PSNR: 46.74 | PSNR: 46.74 | PSNR: 46.49 | PSNR: 46.17 | PSNR: 45.96 | PSNR: 45.84 | PSNR: 45.84 | PSNR: 45.79 | PSNR: 45.69 |
| MSE: 2.12 × 10−5 | MSE: 2.12 × 10−5 | MSE: 2.24 × 10−5 | MSE: 2.42 × 10−5 | MSE: 2.54 × 10−5 | MSE: 2.61 × 10−5 | MSE: 2.61 × 10−5 | MSE: 2.63 × 10−5 | MSE: 2.70 × 10−5 | |
| 25 | PSNR: 46.35 | PSNR: 46.35 | PSNR: 46.07 | PSNR: 45.75 | PSNR: 45.52 | PSNR: 45.36 | PSNR: 45.34 | PSNR: 45.26 | PSNR: 45.13 |
| MSE: 2.32 × 10−5 | MSE: 2.32 × 10−5 | MSE: 2.47 × 10−5 | MSE: 2.66 × 10−5 | MSE: 2.81 × 10−5 | MSE: 2.91 × 10−5 | MSE: 2.93 × 10−5 | MSE: 2.98 × 10−5 | MSE: 3.07 × 10−5 | |
| 30 | PSNR: 46.03 | PSNR: 46.03 | PSNR: 45.75 | PSNR: 45.41 | PSNR: 45.12 | PSNR: 45.00 | PSNR: 44.94 | PSNR: 44.84 | PSNR: 44.73 |
| MSE: 2.50 × 10−5 | MSE: 2.50 × 10−5 | MSE: 2.66 × 10−5 | MSE: 2.88 × 10−5 | MSE: 3.08 × 10−5 | MSE: 3.17 × 10−5 | MSE: 3.21 × 10−5 | MSE: 3.28 × 10−5 | MSE: 3.36 × 10−5 |
| Frame # | CRF 0 | CRF 7 | CRF 12 | CRF 16 | CRF 20 | CRF 22 | CRF 23 | CRF 24 | CRF 25 |
|---|---|---|---|---|---|---|---|---|---|
| 1 | AVG 1: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0536 | AVG: 0.1518 |
| COM 2: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0804 | COM: 0.0714 | COM: 0.2143 | COM: 0.3571 | |
| MED 3: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0179 | MED: 0.0625 | |
| 5 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0089 | AVG: 0.0089 | AVG: 0.1071 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0357 | COM: 0.0447 | COM: 0.0893 | COM: 0.25 | COM: 0.2589 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0089 | MED: 0.0089 | MED: 0.0536 | |
| 10 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0089 | AVG: 0.0089 | AVG: 0.0089 | AVG: 0.1161 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0179 | COM: 0.0357 | COM: 0.1429 | COM: 0.2679 | COM: 0.4821 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0446 | |
| 15 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0089 | AVG: 0.0089 | AVG: 0.0625 | AVG: 0.1875 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0179 | COM: 0.0804 | COM: 0.2768 | COM: 0.3482 | COM: 0.4464 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0089 | MED: 0.0089 | MED: 0.0714 | |
| 20 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0089 | AVG: 0.0089 | AVG: 0.0714 | AVG: 0.2143 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0714 | COM: 0.1429 | COM: 0.25 | COM: 0.4375 | COM: 0.5 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0089 | MED: 0.0089 | MED: 0.1071 | |
| 25 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0179 | AVG: 0.0357 | AVG: 0.2321 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0 | COM: 0.0179 | COM: 0.1161 | COM: 0.3839 | COM: 0.3839 | COM: 0.3571 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0089 | MED: 0.0089 | MED: 0.0893 | |
| 30 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0 | AVG: 0.0179 | AVG: 0.0714 | AVG: 0.1607 |
| COM: 0 | COM: 0 | COM: 0 | COM: 0.0179 | COM: 0.0179 | COM: 0.1339 | COM: 0.0179 | COM: 0.3839 | COM: 0.4911 | |
| MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0 | MED: 0.0089 | MED: 0.0179 | MED: 0.0536 |
| Frame # | CRF 0 | CRF 7 | CRF 12 | CRF 16 | CRF 20 | CRF 22 | CRF 23 | CRF 24 | CRF 25 |
|---|---|---|---|---|---|---|---|---|---|
| 1 | CHAR 1: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 13 |
| 5 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 15 | CHAR: 14 |
| 10 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 14 |
| 15 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 15 | CHAR: 12 |
| 20 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 15 | CHAR: 12 |
| 25 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 15 | CHAR: 13 |
| 30 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 16 | CHAR: 15 | CHAR: 14 | CHAR: 13 |
| Frame # | From 512 × 512 to 128 × 128 | From 512 × 512 to 256 × 256 | From 512 × 512 to 480 × 640 | From 512 × 512 to 1024 × 1024 | From 768 × 512 to 384 × 256 | From 1024 × 1024 to 256 × 256 |
|---|---|---|---|---|---|---|
| 1 | BER 1: 0.531250 | BER: 0 | BER: 0.468750 | BER: 0 | BER: 0.510417 | BER: 0.510417 |
| 5 | BER: 0.479167 | BER: 0 | BER: 0.500000 | BER: 0 | BER: 0.489583 | BER: 0.479167 |
| 10 | BER: 0.395833 | BER: 0 | BER: 0.489583 | BER: 0 | BER: 0.437500 | BER: 0.437500 |
| 15 | BER: 0.427083 | BER: 0 | BER: 0.427083 | BER: 0 | BER: 0.468750 | BER: 0.427083 |
| 20 | BER: 0.437500 | BER: 0 | BER: 0.406250 | BER: 0 | BER: 0.468750 | BER: 0.416667 |
| 25 | BER: 0.447917 | BER: 0 | BER: 0.406250 | BER: 0 | BER: 0.416667 | BER: 0.375000 |
| 30 | BER: 0.416667 | BER: 0 | BER: 0.406250 | BER: 0 | BER: 0.427083 | BER: 0.364583 |
| Type | Average PSNR (dB) | Capacity (Bits/Frame Size) | (Embedding Time/Extraction Time) (ms) for Test Frame with 416 × 240 Resolution | Hardware |
|---|---|---|---|---|
| Method 1 Zhou et al. [16] | 47.519 | 100 bits/416 × 240 | 32.478/5.622 | 3.30 GHz CPU, 4 GB RAM |
| Method 2 Gaj et al. [17] | 46.415 | 100 bits/416 × 240 | 36.855/5.048 | 3.30 GHz CPU, 4 GB RAM |
| Method 3 Liu et al. [51] | 45.462 | 100 bits/416 × 240 | 34.058/5.997 | 3.30 GHz CPU, 4 GB RAM |
| Previously proposed method [22] | 42.617 | 80 bits/128 × 128 | 34,457.92/3759.72 | Geforce 1080Ti GTX 11 GB, 32 GB RAM |
| Proposed method | 47.299 | 96 bits/128 × 128 | 81,132.13 1/82,223.74 1 735.101 2/725.861 2 | Geforce 1080Ti GTX 11 GB, 32 GB RAM |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kaczyński, M.; Piotrowski, Z.; Pietrow, D. High-Quality Video Watermarking Based on Deep Neural Networks for Video with HEVC Compression. Sensors 2022, 22, 7552. https://doi.org/10.3390/s22197552
Kaczyński M, Piotrowski Z, Pietrow D. High-Quality Video Watermarking Based on Deep Neural Networks for Video with HEVC Compression. Sensors. 2022; 22(19):7552. https://doi.org/10.3390/s22197552
Chicago/Turabian StyleKaczyński, Maciej, Zbigniew Piotrowski, and Dymitr Pietrow. 2022. "High-Quality Video Watermarking Based on Deep Neural Networks for Video with HEVC Compression" Sensors 22, no. 19: 7552. https://doi.org/10.3390/s22197552
APA StyleKaczyński, M., Piotrowski, Z., & Pietrow, D. (2022). High-Quality Video Watermarking Based on Deep Neural Networks for Video with HEVC Compression. Sensors, 22(19), 7552. https://doi.org/10.3390/s22197552







