How Are Bystanders Involved in Cyberbullying? A Latent Class Analysis of the Cyberbystander and Their Characteristics in Different Intervention Stages
Abstract
1. Introduction
1.1. Latent Classes of Bystanders in Cyberbullying
1.2. Intervention Characteristics of Cyberbystanders
1.3. Influencing Factors of Cyberbystanders
2. Materials and Methods
2.1. Participants and Procedure
2.2. Measures
2.3. Data Analysis
3. Results
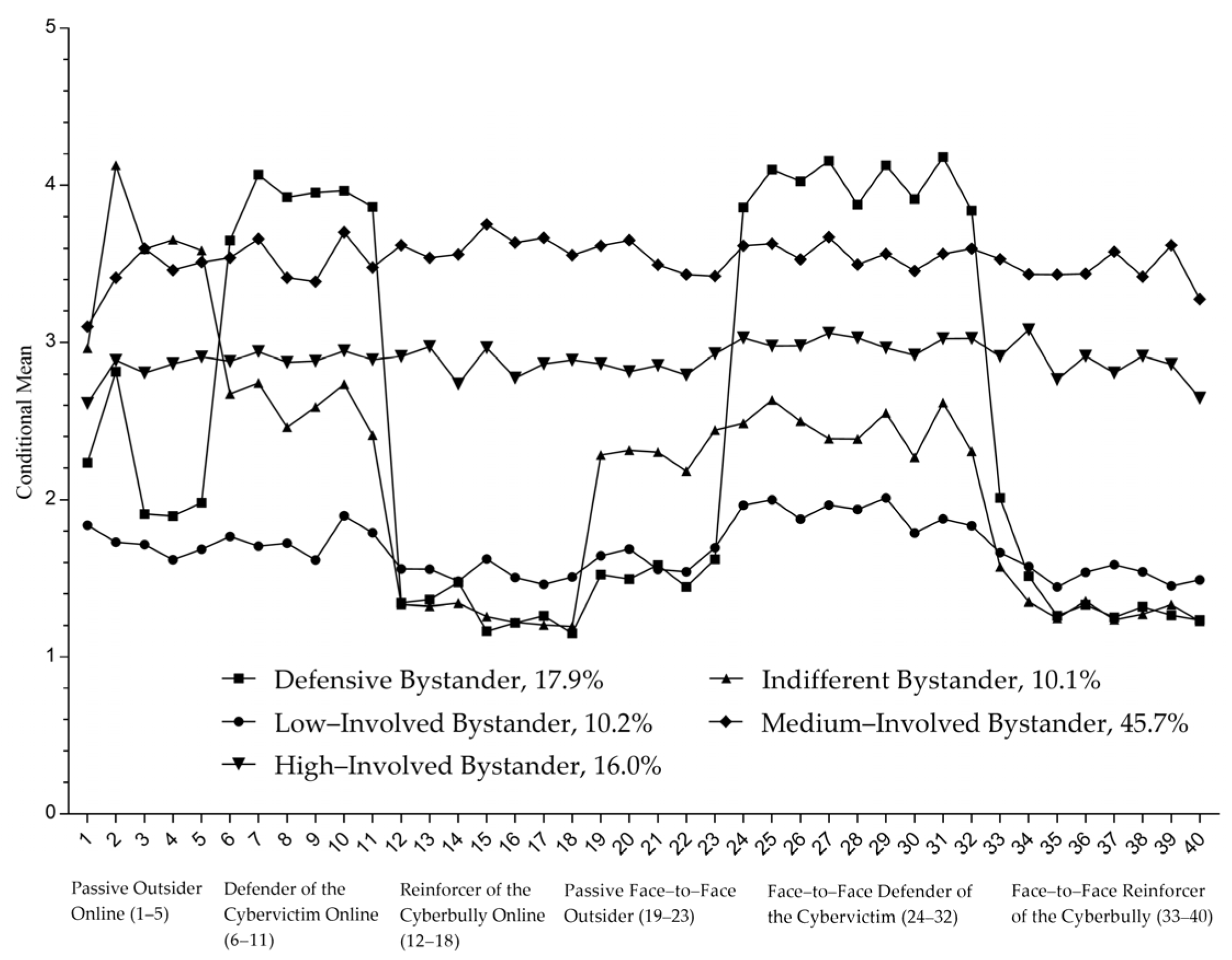
3.1. Identification and Delimitation of the Latent Classes of Cyberbullying Bystanders
3.2. Characteristics of the Cyberbullying Bystanders in Different Stages of the Bullying Intervention
3.3. Multiple Logistic Regression Analysis
4. Discussion
4.1. Co-Occurrence and Heterogeneity of the Cyberbullying Bystander Subcategory
4.2. Intervention Characteristics of the Cyberbystanders
4.3. Influencing Factors of Cyberbystanders
5. Limitation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Huang, X.J.; Chu, X.W.; Liu, Q.Q.; Zhou, Z.K.; Fan, C.Y. Bystander behavior in cyberbullying. Adv. Psychol. Sci. 2019, 27, 1248–1257. [Google Scholar] [CrossRef]
- Lambe, L.J.; Cioppa, V.D.; Hong, I.K.; Craig, W.M. Standing up to bullying: A social ecological review of peer defending in offline and online contexts. Aggress. Violent Behav. 2019, 45, 51–74. [Google Scholar] [CrossRef]
- Dorit, O.-S.; Tali, H.; Sigal, E. Bystanders’ behavior in cyberbullying episodes: Active and passive patterns in the context of personal-socio-emotional factors. J. Interpers. Violence 2017, 32, 23–48. [Google Scholar]
- Zych, I.; Farrington, D.P.; Ttofi, M.M. Protective factors against bullying and cyberbullying: A systematic review of meta-analyses. Aggress. Violent Behav. 2019, 45, 4–19. [Google Scholar] [CrossRef]
- Quirk, R.; Campbell, M. On standby? A comparison of online and offline witnesses to bullying and their bystander behaviour. Educ. Psychol. 2015, 35, 430–448. [Google Scholar] [CrossRef]
- Gahagan, K.; Vaterlaus, J.M.; Frost, L.R. College student cyberbullying on social networking sites: Conceptualization, prevalence, and perceived bystander responsibility. Comput. Hum. Behav. 2016, 55, 1097–1105. [Google Scholar] [CrossRef]
- Doane, A.N.; Ehlke, S.; Kelley, M.L. Bystanders Against Cyberbullying: A Video Program for College Students. Int. J. Bullying Prev. 2019, 2, 41–52. [Google Scholar] [CrossRef]
- Sarmiento, A.; Herrera-López, M.; Zych, I. Is cyberbullying a group process? Online and offline bystanders of cyberbullying act as defenders, reinforcers and outsiders. Comput. Hum. Behav. 2019, 99, 328–334. [Google Scholar] [CrossRef]
- Clark, M.; Bussey, K. The role of self-efficacy in defending cyberbullying victims. Comput. Hum. Behav. 2020, 2020, 106340. [Google Scholar] [CrossRef]
- Domínguez-Hernández, F.; Bonell, L.; Martínez-González, A. A systematic literature review of factors that moderate bystanders’ actions in cyberbullying. Cyberpsychol. J. Psychosoc. Res. Cyberspace 2018, 12, 1. [Google Scholar] [CrossRef]
- Cleveland, M.J.; Collins, L.M.; Lanza, S.T.; Greenberg, M.T.; Feinberg, M.E. Does individual risk moderate the effect of contextual-level protective factors? A latent class analysis of substance use. J. Prev. Interv. Community 2010, 38, 213–228. [Google Scholar] [CrossRef] [PubMed]
- Salmivalli, C. Bullying and the peer group: A review. Aggress. Violent Behav. 2010, 1, 112–120. [Google Scholar] [CrossRef]
- Pepler, D.; Craig, W.; O’Connell, P. Peer processes in bullying: Informing prevention and intervention strategies. In Handbook of Bullying in Schools: An International Perspective; Jimerson, S.R., Swearer, S.M., Espelage, D.L., Eds.; Routledge: London, UK, 2010; pp. 469–479. [Google Scholar]
- Latané, B.; Darley, J.M. The Unresponsive Bystander: Why Doesn’t He Help? Appleton-Century-Croft: New York, NY, USA, 1970. [Google Scholar]
- Dillon, K.P.; Bushman, B.J. Unresponsive or un-noticed? Cyberbystander intervention in an experimental cyberbullying context. Comput. Hum. Behav. 2015, 45, 144–150. [Google Scholar] [CrossRef]
- Choi, K.S. Computer crime victimization and integrated theory: An empirical assessment. Int. J. Cyber Criminol. 2008, 2, 308. [Google Scholar]
- Yu, M.; Riddle, K. An Experimental Test of the Effects of Digital Content Permanency on Perceived Anonymity and Indirect Effects on Cyber Bullying Intentions. Soc. Media Soc. 2022, 8, 20563051221087255. [Google Scholar] [CrossRef]
- Lapidot-Lefler, N.; Barak, A. Effects of anonymity, invisibility, and lack of eye-contact on toxic online disinhibition. Comput. Hum. Behav. 2012, 28, 434–443. [Google Scholar] [CrossRef]
- Barlińska, J.; Szuster, A.; Winiewski, M. Cyberbullying among adolescent bystanders: Role of the communication medium, form of violence, and empathy. J. Community Appl. Soc. Psychol. 2013, 23, 37–51. [Google Scholar] [CrossRef]
- DeSmet, A.; Van Cleemput, K.; Bastiaensens, S.; Poels, K.; Vandebosch, H.; Malliet, S.; Verloigne, M.; Vanwolleghem, G.; Mertens, L.; Cardon, G.; et al. Bridging behavior science and gaming theory: Using the intervention mapping protocol to design a serious game against cyberbullying. Comput. Hum. Behav. 2016, 56, 337–351. [Google Scholar] [CrossRef]
- Choi, K.; Cho, S.; Lee, J.R. Impacts of online risky behaviors and cybersecurity management on cyberbullying and traditional bullying victimization among Korean youth: Application of cyber-routine activities theory with latent class analysis. Comput. Hum. Behav. 2019, 100, 1–10. [Google Scholar] [CrossRef]
- Jenkins, L.N.; Nickerson, A.B. Bystander Intervention in Bullying: Role of Social Skills and Gender. J. Early Adolesc. 2019, 39, 141–166. [Google Scholar] [CrossRef]
- Barlett, C.P.; Gentile, D.A. Attacking others online: The formation of cyberbullying in late adolescence. Psychol. Pop. Media Cult. 2012, 1, 123–135. [Google Scholar] [CrossRef]
- Ellison, N.B.; Steinfield, C.; Lampe, C. The Benefits of Facebook Friends: Social Capital and College Students’ Use of Online Social Network Sites. J. Comput. Mediat. Commun. 2007, 12, 1143–1168. [Google Scholar] [CrossRef]
- Erdur-Baker, Ö.; Kavsut, F. Cyber bullying: A new face of peer bullying. Eurasian J. Educ. Res. 2007, 27, 31–42. [Google Scholar]
- Weber, M.; Ziegele, M.; Schnauber, A. Blaming the Victim: The Effects of Extraversion and Information Disclosure on Guilt Attributions in Cyberbullying. Cyberpsychol. Behav. Soc. Netw. 2013, 16, 254–259. [Google Scholar] [CrossRef]
- Holfeld, B. Perceptions and attributions of bystanders to cyber bullying. Comput. Hum. Behav. 2014, 38, 1–7. [Google Scholar] [CrossRef]
- DeWall, C.N.; Richman, S.B. Social Exclusion and the Desire to Reconnect. Soc. Personal. Psychol. Compass 2011, 5, 919–932. [Google Scholar] [CrossRef]
- DeWall, C.N. Forming a basis for acceptance: Excluded people form attitudes to agree with potential affiliates. Soc. Influ. 2010, 5, 245–260. [Google Scholar] [CrossRef]
- Mead, N.L.; Baumeister, R.F.; Stillman, T.F.; Rawn, C.; Vohs, K.D. Social Exclusion Causes People to Spend and Consume Strategically in the Service of Affiliation. J. Consum. Res. 2011, 37, 902–919. [Google Scholar] [CrossRef]
- Chester, D.S.; DeWall, C.N.; Pond, R.S., Jr. The push of social pain: Does rejection’s sting motivate subsequent social reconnection? Cogn. Affect. Behav. Neurosci. 2016, 16, 541–550. [Google Scholar] [CrossRef]
- Machácková, H.; Dedkova, L.; Ševčíková, A.; Cerna, A. Bystanders’ Support of Cyberbullied Schoolmates. J. Community Appl. Soc. Psychol. 2013, 23, 25–36. [Google Scholar] [CrossRef]
- Fanti, K.A.; Demetriou, A.; Hawa, V.V. A longitudinal study of cyberbullying: Examining riskand protective factors. Eur. J. Dev. Psychol. 2012, 9, 168–181. [Google Scholar] [CrossRef]
- Wang, G.F. The Progress of Object Relation Theory in Psychoanalysis. J. Nanjing Norm. Univ. (Soc. Sci. Ed.) 2012, 1, 114–119. [Google Scholar]
| Model | K | Log | AIC | BIC | aBIC | Entropy | LMR | BLRT | Class Probability |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 80 | −64,614.53 | 129,389.05 | 129,783.65 | 129,529.56 | ||||
| 2 | 121 | −59,669.95 | 119,581.89 | 120,178.72 | 119,794.41 | 0.98 | 0.00 | 0.00 | 0.40/0.60 |
| 3 | 162 | −57,713,50 | 115,751.00 | 116,550.06 | 116,035.53 | 0.98 | 0.00 | 0.00 | 0.20/0.20/0.60 |
| 4 | 203 | −56,938.43 | 114,282.86 | 115,284.15 | 114,639.40 | 0.95 | 0.00 | 0.00 | 0.19/0.46/0.20/0.16 |
| 5 | 244 | −56,360.86 | 113,209.71 | 114,413.23 | 113,638.26 | 0.95 | 0.00 | 0.00 | 0.10/0.10/0.18/0.46/0.16 |
| 6 | 285 | −56,003.19 | 112,576.39 | 113,982.13 | 113,076.95 | 0.96 | 0.12 | 0.00 | 0.09/0.07/0.14/0.09/0.46/0.16 |
| Defensive Bystander | Indifferent Bystander | Low-Involved Bystander | Medium-Involved Bystander | High-Involved Bystander | F | η2p | |
|---|---|---|---|---|---|---|---|
| Notice | 2.65 ± 1.00 | 2.82 ± 0.95 | 2.93 ± 0.97 | 2.76 ± 0.79 | 3.14 ± 1.00 | 8.17 ** | 0.03 |
| Emergency | 3.57 ± 0.98 | 3.31 ± 0.92 | 3.40 ± 0.89 | 3.01 ± 0.80 | 3.43 ± 0.85 | 12.53 ** | 0.05 |
| Responsibility | 3.42 ± 1.05 | 3.29 ± 0.93 | 3.11 ± 0.88 | 3.03 ± 0.81 | 3.42 ± 0.89 | 10.71 ** | 0.04 |
| Know | 3.46 ± 0.95 | 3.37 ± 0.80 | 3.11 ± 0.82 | 3.11 ± 0.77 | 3.41 ± 0.89 | 8.82 ** | 0.03 |
| Act | 3.35 ± 1.86 | 3.16 ± 0.92 | 2.98 ± 0.89 | 2.91 ± 0.81 | 3.23 ± 0.95 | 11.67 ** | 0.04 |
| Factors | Defensive Bystander | Indifferent Bystander | Medium-Involved Bystander | High-Involved Bystander | |||||
|---|---|---|---|---|---|---|---|---|---|
| OR | CI (95%) | OR | CI (95%) | OR | CI (95%) | OR | CI (95%) | ||
| Gender | Female | 1.00 | 1.00 | 1.00 | 1.00 | ||||
| Male | 1.25 | 0.71~2.19 | 1.95 * | 1.06~3.56 | 2.01 | 1.22~3.31 | 2.19 ** | 1.27~3.76 | |
| Grade | Grade 4 | 1.00 | 1.00 | 1.00 | 1.00 | ||||
| Grade 1 | 1.03 | 0.47~2.26 | 1.38 | 0.59~3.26 | 1.94 | 0.98~3.83 | 1.84 | 0.87~3.87 | |
| Grade 2 | 1.47 | 0.74~2.90 | 1.53 | 0.71~3.26 | 2.15 | 1.17~3.97 | 1.53 | 0.77~3.03 | |
| Grade 3 | 1.57 | 0.80~3.10 | 1.12 | 0.51~2.44 | 1.45 | 0.78~2.71 | 1.26 | 0.63~2.52 | |
| Left-behind pattern | Not Left-Behind | 1.00 | 1.00 | 1.00 | 1.00 | ||||
| Father Migrant | 0.41 * | 0.19~0.88 | 0.26 ** | 0.10~0.71 | 1.22 | 0.66~2.26 | 1.44 | 0.73~2.82 | |
| Mother Migrant | 0.23 * | 0.07~0.83 | 0.38 | 0.11~1.37 | 2.97 * | 1.30~6.80 | 2.88 * | 1.20~6.93 | |
| Two-Parent-Migrant | 0.58 | 0.30~1.13 | 0.59 | 0.28~1.23 | 0.56 | 0.30~1.03 | 0.56 | 0.27~1.13 | |
| Anonymity | 0.95 | 0.66~1.36 | 0.84 | 0.57~1.21 | 0.85 | 0.62~1.15 | 0.75 | 0.52~1.09 | |
| SNS Intensity | 1.40 | 0.92~2.13 | 1.18 | 0.75~1.87 | 0.81 | 0.56~1.18 | 1.91 * | 1.22~2.97 | |
| Cyber- Victimization Experience | 1.02 | 0.58~1.78 | 0.85 | 0.45~1.60 | 3.52 ** | 2.16~5.74 | 3.99 ** | 2.33~6.84 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jia, Y.; Wu, Y.; Jin, T.; Zhang, L. How Are Bystanders Involved in Cyberbullying? A Latent Class Analysis of the Cyberbystander and Their Characteristics in Different Intervention Stages. Int. J. Environ. Res. Public Health 2022, 19, 16083. https://doi.org/10.3390/ijerph192316083
Jia Y, Wu Y, Jin T, Zhang L. How Are Bystanders Involved in Cyberbullying? A Latent Class Analysis of the Cyberbystander and Their Characteristics in Different Intervention Stages. International Journal of Environmental Research and Public Health. 2022; 19(23):16083. https://doi.org/10.3390/ijerph192316083
Chicago/Turabian StyleJia, Yanru, Yuntena Wu, Tonglin Jin, and Lu Zhang. 2022. "How Are Bystanders Involved in Cyberbullying? A Latent Class Analysis of the Cyberbystander and Their Characteristics in Different Intervention Stages" International Journal of Environmental Research and Public Health 19, no. 23: 16083. https://doi.org/10.3390/ijerph192316083
APA StyleJia, Y., Wu, Y., Jin, T., & Zhang, L. (2022). How Are Bystanders Involved in Cyberbullying? A Latent Class Analysis of the Cyberbystander and Their Characteristics in Different Intervention Stages. International Journal of Environmental Research and Public Health, 19(23), 16083. https://doi.org/10.3390/ijerph192316083





