Do Deterrence Mechanisms Reduce Cyberloafing When It Is an Observed Workplace Norm? A Moderated Mediation Model
Abstract
1. Introduction
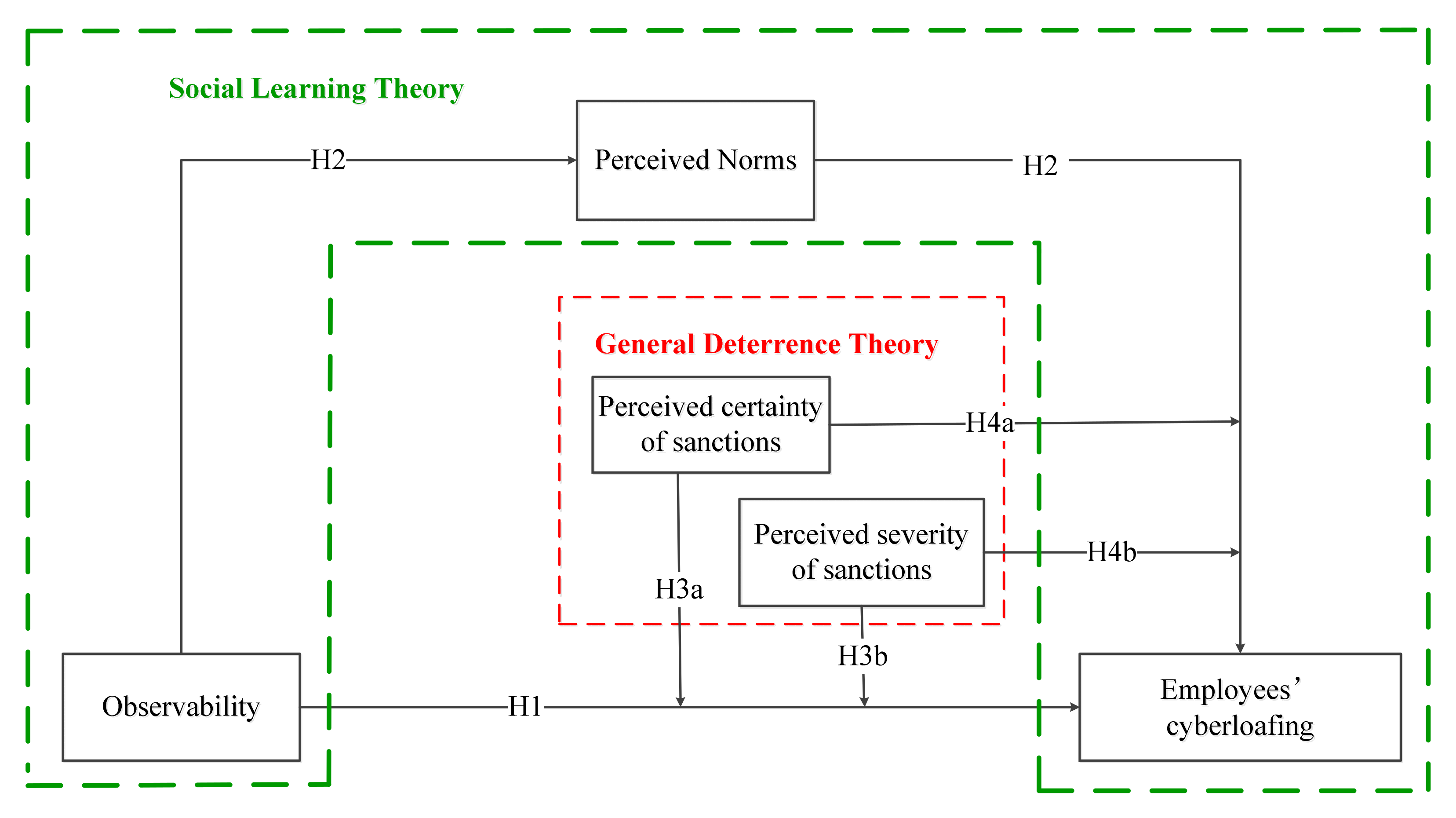
1.1. Theoretical Foundation and Research Model
1.2. The Main Effect of Observability and Employees’ Cyberloafing
1.3. The Mediating Effects of Perceived Norms on the Relationship between Observability and Employees’ Cyberloafing
1.4. The Moderating Effect of Perceived Certainty and Severity of Sanctions on the Relationship between Observability and Employees’ Cyberloafing
1.5. The Moderating Effect of Perceived Certainty and Severity of Sanctions on the Relationship between Perceived Norms and Employees’ Cyberloafing
2. Materials and Methods
2.1. Sampling and Procedures
2.2. Measures
3. Results
3.1. Confirmatory Factor Analysis
3.2. Common Method Biases Analysis
3.3. Correlation Analysis
3.4. Mediation Effect Analysis
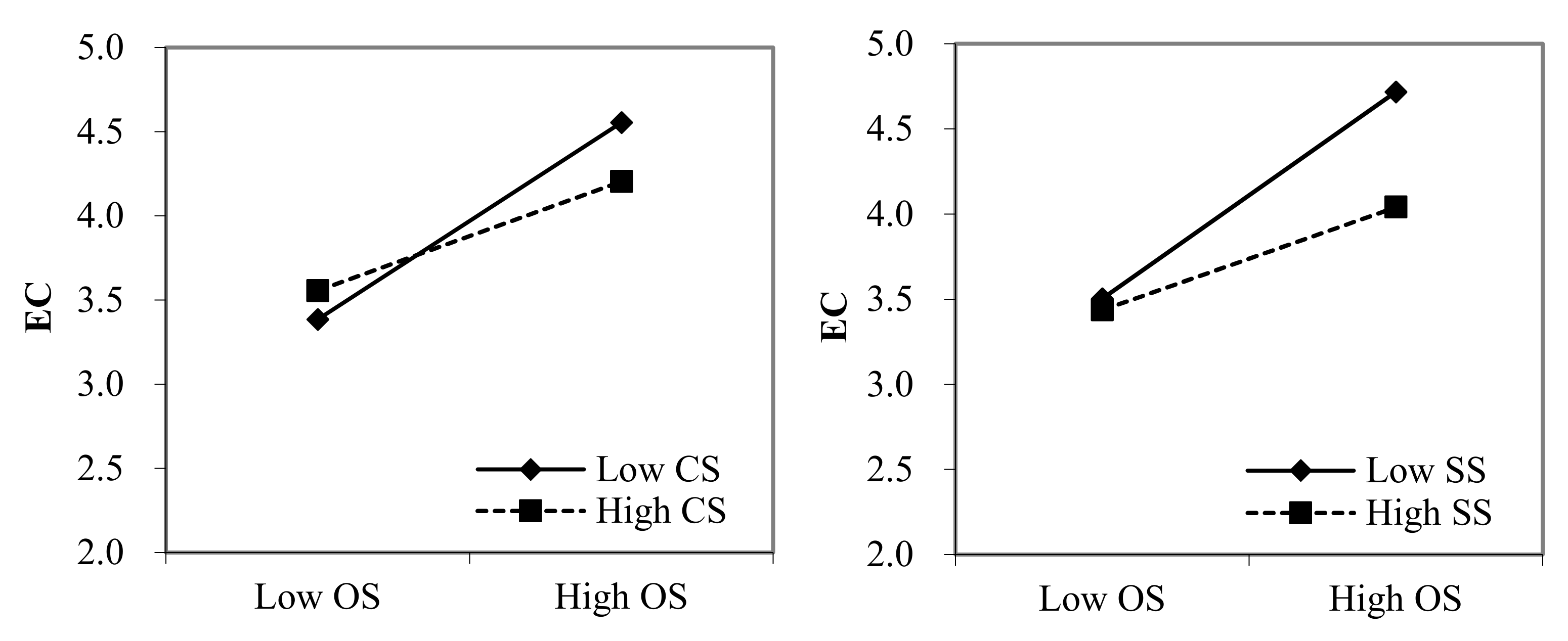
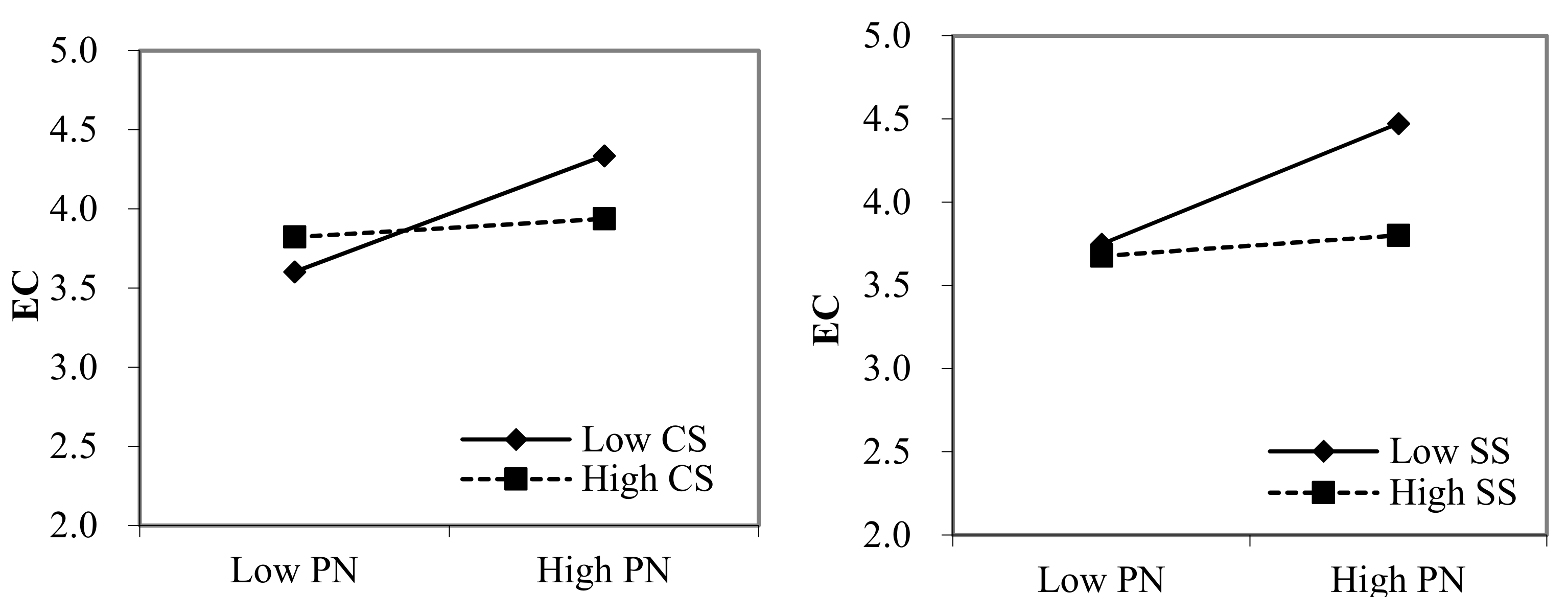
3.5. Moderated Mediation Effect Analysis
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ngai, E.W.; Tao, S.S.; Moon, K.K. Social media research: Theories, constructs, and conceptual frameworks. Int. J. Inf. Manag. 2015, 35, 33–44. [Google Scholar] [CrossRef]
- Sherlyanita, A.K.; Rakhmawati, N.A. Pengaruh Dan Pola Aktivitas Penggunaan Internet Serta Media Sosial Pada Siswa SMPN 52 Surabaya. J. Inf. Syst. Eng. Bus. Intell. 2016, 2, 17. [Google Scholar] [CrossRef][Green Version]
- Lim, V.K.G.; Chen, D.J.Q. Cyberloafing at the Workplace: Gain or Drain on Work? Behav. Inf. Technol. 2012, 31, 343–353. [Google Scholar] [CrossRef]
- Restubog, S.L.D.; Garcia, P.R.J.M.; Toledano, L.S.; Amarnani, R.K.; Tolentino, L.R.; Tang, R.L. Yielding to cyber-temptation:Exploring the buffering role of self-control in the relationship between organizational justice and cyberloafing behavior in the workplace. J. Res. Personal. 2011, 45, 247–251. [Google Scholar] [CrossRef]
- Lim, V.K.G. The IT Way of Loafing on the Job: Cyberloafing, Neutralizing and Organizational Justice. J. Organ. Behav. 2002, 23, 675–694. [Google Scholar] [CrossRef]
- Koay, K.Y.; Soh, P.C. Should Cyberloafing Be Allowed in the Workplace? Hum. Resour. Manag. Int. Dig. 2018, 26, 4–6. [Google Scholar] [CrossRef]
- D’Abate, C.P.; Eddy, E.R. Engaging in Personal Business on the Job: Extending the Presenteeism Construct. Hum. Resour. Dev. Q. 2007, 18, 361–383. [Google Scholar] [CrossRef]
- Wu, J.; Mei, W.; Liu, L.; Ugrin, J.C. The bright and dark sides of social cyberloafing: Effects on employee mental health in China. J. Bus. Res. 2020, 112, 56–64. [Google Scholar] [CrossRef]
- Glassman, J.; Prosch, M.; Shao, B.B.M. To Monitor or not to Monitor: Effectiveness of a Cyberloafing Countermeasure. Inf. Manag. 2015, 52, 170–182. [Google Scholar] [CrossRef]
- Alharthi, S.; Levy, Y.; Wang, L.; Hur, I. Employees‘ Mobile Cyberslacking and Their Commitment to the Organization. J. Comput. Inf. Syst. 2019, 61, 1–13. [Google Scholar] [CrossRef]
- Baturay, M.H.; Toker, S. An investigation of the impact of demographics on cyberloafing from an educational setting angle. Comput. Hum. Behav. 2015, 50, 358–366. [Google Scholar] [CrossRef]
- Dursun, O.O.; Donmez, O.; Akbulut, Y. Predictors of Cyberloafing among Preservice Information Technology Teachers. Contemp. Educ. Technol. 2018, 9, 22–41. [Google Scholar]
- Sheikh, A.; Atashgah, M.S.; Adibzadegan, M. The antecedents of cyberloafing: A case study in an Iranian copper industry. Comput. Hum. Behav. 2015, 51, 172–179. [Google Scholar] [CrossRef]
- Ugrin, J.C.; Pearson, J.M. The Effects of Sanctions and Stigmas on Cyberloafing. Comput. Hum. Behav. 2013, 29, 812–820. [Google Scholar] [CrossRef]
- Cheng, B.; Zhou, X.; Guo, G.; Yang, K. Perceived Overqualification and Cyberloafing: A Moderated-Mediation Model Based on Equity Theory. J. Bus. Ethics 2020, 164, 565–577. [Google Scholar] [CrossRef]
- Carpenter, N.C.; Berry, C.M. Are counterproductive work behavior and withdrawal empirically distinct? A meta-analytic investigation. J. Manag. 2014, 43, 834–863. [Google Scholar] [CrossRef]
- Pindek, S.; Krajcevska, A.; Spector, P.E. Cyberloafing as a coping mechanism: Dealing with workplace boredom. Comput. Hum. Behav. 2018, 86, 147–152. [Google Scholar] [CrossRef]
- Zoghbi-Manrique-de-Lara, P.; Sharifiatashgah, M. The relationship between perceived crowding and cyberloafing in open offices at Iranian IT-based companies. Cogn. Technol. Work 2020, 23, 331–342. [Google Scholar] [CrossRef]
- Przemysław, G.; Hensel, K.A. Job Overload, Organizational Commitment, and Motivation as Antecedents of Cyberloafing: Evidence from Employee Monitoring Software. Eur. Manag. Rev. 2020. [Google Scholar] [CrossRef]
- Zoghbi-Manrique-de-Lara, P. Relationship between Organizational Justice and Cyberloafing in the Workplace: Has “Anomia“ a Say in the Matter? Cyberpsychol. Behav. 2007, 10, 464–470. [Google Scholar] [CrossRef] [PubMed]
- Usman, M.; Javed, U.; Shoukat, A.; Bashir, N.A. Does meaningful work reduce cyberloafing? Important roles of affective commitment and leader-member exchange. Behav. Inf. Technol. 2019. [Google Scholar] [CrossRef]
- Hensel, P.G.; Agnieszka, K. Curbing cyberloafing: Studying general and specific deterrence effects with field evidence. Eur. J. Inf. Syst. 2020, 30, 219–235. [Google Scholar] [CrossRef]
- Degoey, P. Contagious justice: Exploring the social construction of justice in organizations. Res. Organ. Behav. 2000, 22, 51–102. [Google Scholar] [CrossRef]
- Ferguson, M.J. From Bad to Worse: A Social Contagion Model of Organizational Misbehavior. SSRN Electron. J. 2006. [Google Scholar] [CrossRef][Green Version]
- Khansa, L.; Kuem, J.; Siponen, M.; Kim, S.S. To Cyberloaf or Not to Cyberloaf: The Impact of the Announcement of Formal Organizational Controls. J. Manag. Inf. Syst. 2017, 34, 141–176. [Google Scholar] [CrossRef]
- Askew, K.L.; Ilie, A.; Bauer, J.A.; Simonet, D.V.; Buckner, J.E.; Roberts, T.A. Disentangling How Coworkers and Supervisors Influence Employee Cyberloafing: What Normative Information Are Employees Attending To? J. Leadersh. Organ. Stud. 2018, 26, 526–544. [Google Scholar] [CrossRef]
- Robinson, S.L.; O’Leary-Kelly, A.M. Monkey See, Monkey Do: The Influence of Work Groups on the Antisocial Behavior of Employees. Acad. Manag. J. 1998, 41, 658–672. [Google Scholar]
- Bandura, A. Social Learning Theory; Prentice-Hall: Englewood Cliffs, NJ, USA, 1977. [Google Scholar]
- Cheng, L.; Li, W.; Zhai, Q.; Smyth, R. Understanding personal use of the Internet at work: An integrated model of neutralization techniques and general deterrence theory. Comput. Hum. Behav. 2014, 38, 220–228. [Google Scholar] [CrossRef]
- D’Arcy, J.; Hovav, A.; Galletta, D. User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach. Inf. Syst. Res. 2009, 20, 79–98. [Google Scholar] [CrossRef]
- Wenzel, M. The social side of sanctions: Personal and social norms as moderators of deterrence. Law Hum. Behav. 2004, 28, 547–567. [Google Scholar] [CrossRef]
- Beccaria, C. On Crimes and Punishments; Prentice Hall: Upper Saddle River, NJ, USA, 1963. [Google Scholar]
- Laland, K.N. Social learning strategies. Learn. Behav. 2004, 32, 4–14. [Google Scholar] [CrossRef]
- Akers, R.L.; Krohn, M.D.; Lanza-Kaduce, L.; Rodosevich, M. Social learning and deviant behavior: A specific test of a general theory. Am. Sociol. Rev. 1979, 44, 636–655. [Google Scholar] [CrossRef] [PubMed]
- Kura, K.M.; Shamsudin, F.M.; Chauhan, A. Perceived group norms as predictors of deviant behaviour at work. Int. Bus. Manag. 2013, 7, 121–126. [Google Scholar]
- Bikhchandani, S.; Hirshleifer, D.; Welch, I. Learning from the Behavior of Others: Conformity, Fads, and Informational Cascades. J. Econ. Perspect. 1998, 12, 151–170. [Google Scholar] [CrossRef]
- Akers, R.L. Social Learning and Social Structure: A General Theory of Crime and Deviance; Northeastern University Press: Boston, MA, USA, 1998. [Google Scholar]
- Straub, D.W. Effective IS Security: An Empirical Study. Inf. Syst. Res. 1990, 1, 255–276. [Google Scholar] [CrossRef]
- Bennett, R.; Robinson, S. Development of a measure of workplace deviance. J. Appl. Psychol. 2000, 85, 349–360. [Google Scholar] [CrossRef]
- Robinson, S.; Bennett, R. A typology of deviant workplace behaviors: A multidimensional scaling study. Acad. Manag. J. 1995, 38, 555–572. [Google Scholar]
- Kaptein, M. Understanding unethical behavior by unraveling ethical culture. Hum. Relat. 2011, 64, 843–869. [Google Scholar] [CrossRef]
- Whitty, M.T.; Carr, A.N. New rules in the workplace: Applying object-relations theory to explain problem Internet and email behaviour in the workplace. Comput. Hum. Behav. 2006, 22, 235–250. [Google Scholar] [CrossRef]
- Greenfield, D.; Davis, R. Lost in Cyberspace: The Web at Work. Cyberpsychol. Behav. Impact Internet Multimed. Virtual Real. Behav. Soc. 2002, 5, 347–353. [Google Scholar] [CrossRef]
- Akinyele, S. Needs Satisfaction: An Effective Tool for Workers Commitment to Work. Res. J. Bus. Manag. 2007, 1, 72–79. [Google Scholar]
- Andel, S.A.; Kessler, S.R.; Pindek, S.; Kleinman, G.; Spector, P. Is cyberloafing more complex than we originally thought? Cyberloafing as a coping response to workplace aggression exposure. Comput. Hum. Behav. 2019, 101, 124–130. [Google Scholar] [CrossRef]
- Wagner, D.T.; Barnes, C.M.; Lim, V.; Ferris, D.L. Lost sleep and cyberloafing: Evidence from the laboratory and a daylight saving time quasi-experiment. J. Appl. Psychol. 2012, 97, 1068–1076. [Google Scholar] [CrossRef] [PubMed]
- Yoshikawa, K.; Wu, C.-H.; Lee, H. Generalized Social Exchange and Its Relevance to New Era Workplace Relationships. Ind. Organ. Psychol. 2018, 11, 486–492. [Google Scholar] [CrossRef]
- Yamagishi, T.; Cook, K. Generalized Exchange and Social Dilemmas. Soc. Psychol. Q. 1993, 56, 235–248. [Google Scholar] [CrossRef]
- Sutherland, E.H. Principles of Criminology, 4th ed.; Lippincott: Philadelphia, PA, USA, 1947. [Google Scholar]
- Burgess, R.L.; Akers, R.L. A Differential Association-Reinforcement Theory of Criminal Behavior. Soc. Probl. 1966, 14, 128–147. [Google Scholar] [CrossRef]
- Bird, C.; Miller, N.E.; Dollard, J. Social Learning and Imitation. Am. J. Psychol. 1942, 55, 459. [Google Scholar] [CrossRef]
- Brummelhuis, L.T.; Johns, G.; Lyons, B.; Hoeven, C.T. Why and when do employees imitate the absenteeism of co-workers? Organ. Behav. Hum. Decis. Process. 2016, 134, 16–30. [Google Scholar] [CrossRef]
- Sykes, G.; Matza, D. Techniques of Neutralization: A Theory of Delinquency. Am. Sociol. Rev. 1957, 22, 664–670. [Google Scholar] [CrossRef]
- Hinduja, S. Neutralization theory and online software piracy: An empirical analysis. Ethics Inf. Technol. 2007, 9, 187–204. [Google Scholar] [CrossRef]
- Willison, R. Understanding the Perpetration of Employee Computer Crime in the Organisational Context. Inf. Organ. 2006, 16, 304–324. [Google Scholar] [CrossRef]
- Blanchard, A.L.; Henle, C.A. Correlates of different forms of cyberloafing: The role of norms and external locus of control. Comput. Hum. Behav. 2008, 24, 1067–1084. [Google Scholar] [CrossRef]
- Lim, V.K.G.; Teo, T.S.H. Prevalence, perceived seriousness, justification and regulation of cyberloafing in Singapore: An exploratory study. Inf. Manag. 2005, 42, 1081–1093. [Google Scholar] [CrossRef]
- Askew, K.; Buckner, J.E.; Taing, M.U.; Ilie, A.; Bauer, J.A.; Coovert, M.D. Explaining cyberloafing: The role of the theory of planned behavior. Comput. Hum. Behav. 2014, 36, 510–519. [Google Scholar] [CrossRef]
- Tyler, T.R.; Blader, S.L. Can Business Effectively Regulate Employee Conduct? The Antecedents of Rule Following in Work Settings. Acad. Manag. J. 2005, 48, 1143–1158. [Google Scholar] [CrossRef]
- Braithwaite, J.; Geis, G. On Theory and Action for Corporate Crime Control. Crime Delinq. 1982, 28, 292–314. [Google Scholar] [CrossRef]
- Siponen, M.; Vance, A. Neutralization: New insights into the problem of employee information systems security policy violations. MIS Q. 2010, 34, 487–502. [Google Scholar] [CrossRef]
- Piquero, A.; Paternoster, R.; Pogarsky, G.; Loughran, T.A. Elaborating the Individual Difference Component in Deterrence Theory. Annu. Rev. Law Soc. Sci. 2011, 7, 335–360. [Google Scholar] [CrossRef]
- Williams, K.R.; Hawkins, R. Perceptual Research on General Deterrence: A Critical Review. Law Soc. Rev. 1986, 20, 545–572. [Google Scholar] [CrossRef]
- Berry, M.J.; Westfall, A. Dial D for distraction: The making and breaking of cell phone policies in the college classroom. Coll. Teach. 2015, 63, 62–71. [Google Scholar] [CrossRef]
- Brinda, S.; Basu, P.A. Cyberloafing: The Di(sguised)gital Way of Loafing on the Job. Iup J. Organ. Behav. 2017, 16, 19–37. [Google Scholar]
- Gibbs, J.P. Crime, Punishment, and Deterrence; Elsevier: New York, NY, USA, 1975. [Google Scholar]
- Rogers, E.M. Diffusion of Innovation; The Free Press: New York, NY, USA, 1995. [Google Scholar]
- Lee, J.; Lee, Y. A holistic model of computer abuse within organizations. Inf. Manag. Comput. Secur. 2002, 10, 57–63. [Google Scholar] [CrossRef]
- Friedman, R.; Simons, T.; Liu, L. Behavior integrity as a driver of cross-race differences in employee attitudes. In Proceedings of the Academy of Management Annual Meetings, Seattle, WA, USA, 3–6 August 2003. [Google Scholar]
- Che, H.L.; Yang, C. Examining WeChat users’ motivations, trust, attitudes, and positive word-of-mouth: Evidence from China. Comput. Hum. Behav. 2014, 41, 104–111. [Google Scholar]
- Wu, J.; Liu, L.; Huang, L. Consumer acceptance of mobile payment across time. Ind. Manag. Data Syst. 2017, 117, 1761–1776. [Google Scholar] [CrossRef]
- Zheng, J.; Qi, Z.; Dou, Y.; Tan, Y. How Mega Is the Mega? Exploring the Spillover Effects of WeChat Using Graphical Model. Inf. Syst. Res. 2019, 30, 1343–1362. [Google Scholar] [CrossRef]
- Moody, G.D.; Siponen, M. Using the theory of interpersonal behavior to explain non-work-related personal use of the Internet at work. Inf. Manag. 2013, 50, 322–335. [Google Scholar] [CrossRef]
- Agarwal, U.A.; Avey, J.B. Abusive supervisors and employees who cyberloaf: Examining the roles of psychological capital and contract breach. Internet Res. 2020, 30, 789–809. [Google Scholar] [CrossRef]
- Reed, K.; Doty, D.H.; May, D.R. The impact of aging on self-efficacy and computer skill acquisition. J. Manag. Issues 2005, 54, 212–228. [Google Scholar]
- Anderson, J.C.; Gerbing, D.W. Structural Equation Modeling in Practice: A Review and Recommended Two-Step Approach. Psychol. Bull. 1988, 103, 411–423. [Google Scholar] [CrossRef]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Podsakoff, P.M.; Mackenzie, S.B.; Podsakoff, N.P. Sources of method bias in social science research and recommendations on how to control it. Annu. Rev. Psychol. 2012, 63, 539–569. [Google Scholar] [CrossRef]
- Slater, S.F.; Olson, E.M.; Hult, G.T.M. The moderating influence of strategic orientation on the strategy formation capability–performance relationship. Strateg. Manag. J. 2006, 27, 1221–1231. [Google Scholar] [CrossRef]
- Zhao, X.; Lynch, J.; Chen, Q. Reconsidering Baron and Kenny: Myths and Truths about Mediation Analysis. J. Consum. Res. 2010, 37, 197–206. [Google Scholar] [CrossRef]
- Hayes, A. Introduction to Mediation, Moderation, and Conditional Process Analysis: A Regression-Based Approach; The Guilford Press: New York, NY, USA, 2013. [Google Scholar]
- Hayes, A.F. Partial, conditional, and moderated moderated mediation: Quantification, inference, and interpretation. Commun. Monogr. 2018, 85, 4–40. [Google Scholar] [CrossRef]
- Kim, S.J.; Byrne, S. Conceptualizing personal web usage in work contexts: A preliminary framework. Comput. Hum. Behav. 2011, 27, 2271–2283. [Google Scholar] [CrossRef]
- O’Neill, A.; Hambley, A.; Chatellier, G. Cyberslacking, engagement, and personality in distributed work environments. Comput. Hum. Behav. 2014, 40, 152–160. [Google Scholar] [CrossRef]
- Jia, R.; Jia, H.H. An Individual Trait-based Investigation of Employee Cyberloafing. J. Inf. Technol. Manag. 2015, 26, 58–71. [Google Scholar]
- Jia, H.; Jia, R.; Karau, S. Cyberloafing and Personality: The Impact of the Big Five Traits and Workplace Situational Factors. J. Leadersh. Organ. Stud. 2013, 20, 358–365. [Google Scholar] [CrossRef]
- Vitak, J.; Crouse, J.; LaRose, R. Personal Internet use at work: Understanding cyberslacking. Comput. Hum. Behav. 2011, 27, 1751–1759. [Google Scholar] [CrossRef]
- Henle, C.A.; Blanchard, A.L. The Interaction of Work Stressors and Organizational Sanctions on Cyberloafing. J. Manag. Issues 2008, 20, 383–400. [Google Scholar]
- Ugrin, J.C.; Pearson, J.M.; Odom, M.D. Profiling Cyber-Slackers in the Workplace: Demographic, Cultural, and Workplace Factors. J. Internet Commer. 2008, 6, 75–89. [Google Scholar] [CrossRef]
- Koay, K.Y.; Soh, P.C.-H.; Chew, K.W. Do employees’ private demands lead to cyberloafing? The mediating role of job stress. Manag. Res. Rev. 2017, 40, 1025–1038. [Google Scholar] [CrossRef]
- Nivedhitha, K.S.; Sheik Manzoor, A.K. Get employees talking through enterprise social media! Reduce cyberslacking: A moderated mediation model. Internet Res. 2020, 30, 1167–1202. [Google Scholar]
- Weatherbee, T.G. Counterproductive use of technology at work: Information & communications technologies and cyberdeviancy. Hum. Resour. Manag. Rev. 2010, 20, 35–44. [Google Scholar]
- Mercado, B.K.; Giordano, C.; Dilchert, S. A meta-analytic investigation of cyberloafing. Career Dev. Int. 2017, 22, 546–564. [Google Scholar] [CrossRef]
- Ugrin, J.C.; Pearson, J.M. Exploring Internet Abuse in the Workplace: How Can We Maximize Deterrence Efforts? Rev. Bus. 2008, 28, 29–39. [Google Scholar]
- Higgins, G.E.; Wilson, A.L.; Fell, B.D. An Application of Deterrence Theory to Software Piracy. J. Crim. Justice Pop. Cult. 2005, 12, 166–184. [Google Scholar]
| Model | χ2 | df | χ2/df | CFI | TLI | SRMR | RMSEA | ∆χ2(∆df) |
|---|---|---|---|---|---|---|---|---|
| Single-factor model | 1365.244 | 90 | 15.169 | 0.349 | 0.241 | 0.174 | 0.206 | 1200.4 (10) *** |
| Two-factor model | 1104.685 | 89 | 112.412 | 0.482 | 0.389 | 0.169 | 0.185 | 939.9(9) *** |
| Three-factor model | 900.956 | 87 | 10.356 | 0.585 | 0.499 | 0.169 | 0.167 | 736.1 (7) *** |
| Four-factor model | 321.003 | 84 | 3.821 | 0.879 | 0.849 | 0.060 | 0.092 | 156.2(4) *** |
| Five-factor model | 164.808 | 80 | 2.061 | 0.957 | 0.943 | 0.041 | 0.056 |
| Variables | Mean | SD | OS | PN | CS | SS | EC |
|---|---|---|---|---|---|---|---|
| OS | 4.221 | 1.266 | 0.902 | ||||
| PN | 3.908 | 0.901 | 0.568 *** | 0.712 | |||
| CS | 4.228 | 1.211 | −0.148 ** | −0.090 | 0.801 | ||
| SS | 4.895 | 0.977 | −0.034 | −0.080 | 0.506 *** | 0.769 | |
| EC | 3.309 | 1.174 | 0.387 *** | 0.308 *** | −0.216 *** | −0.247 *** | 0.780 |
| Variables | EC | PN | EC | |||
|---|---|---|---|---|---|---|
| β | t | β | t | β | T | |
| GD | −0.094 | −0.761 | 0.024 | 0.276 | −0.099 | −0.798 |
| ED | −0.118 | −0.750 | 0.040 | 0.367 | −0.125 | −0.797 |
| IC | 0.064 | 1.112 | −0.019 | −0.482 | 0.067 | 1.175 |
| MS | −0.283 | −1.625 | 0.071 | 0.591 | −0.295 | −1.703 |
| WY | 0.129 | 2.077 | −0.004 | −0.085 | 0.1298 * | 2.098 |
| PS | −0.141 | −1.627 | −0.056 | −0.934 | −0.131 | −1.522 |
| OS | 0.368 *** | 7.823 | 0.402 *** | 12.349 | 0.299 *** | 5.279 |
| PN | 0.172 * | 2.160 | ||||
| R2 | 0.170 | 0.326 | 0.182 | |||
| F | 9.592 *** | 22.589 *** | 9.070 *** | |||
| PN | EC | |||
|---|---|---|---|---|
| β | T | β | t | |
| GD | 0.024 | 0.276 | 0.025 | 0.230 |
| ED | 0.040 | 0.367 | −0.196 | −1.418 |
| IC | −0.019 | −0.482 | 0.017 | 0.337 |
| MS | 0.071 | 0.591 | −0.199 | −1.313 |
| WY | −0.004 | −0.085 | 0.095 | 1.731 |
| PS | −0.056 | −0.934 | −0.069 | −0.907 |
| OS | 0.402 *** | 12.349 | 0.359 *** | 6.989 |
| CS | −0.037 | −0.715 | ||
| OS*CS | −0.085 * | −2.008 | ||
| SS | −0.190 ** | −3.037 | ||
| OS*SS | −0.123 * | −2.094 | ||
| PN | 0.236 * | 3.327 | ||
| PN*CS | −0.142 * | −2.174 | ||
| PN*SS | −0.171 * | −1.990 | ||
| R2 | 0.326 | 0.390 | ||
| F | 22.589 *** | 14.589 *** | ||
| Moderator Variable | Conditional indirect effects | |||
|---|---|---|---|---|
| Effect | Boot SE | 95% CI | ||
| LLCI | ULCI | |||
| Low CS, Low SS | 0.231 | 0.046 | 0.143 | 0.326 |
| Low CS, High SS | 0.097 | 0.058 | −0.030 | 0.200 |
| High CS, Low SS | 0.093 | 0.062 | −0.017 | 0.227 |
| High CS, High SS | −0.041 | 0.043 | −0.122 | 0.046 |
| Indices of partial moderated mediation | ||||
| Index | Boot SE | 95% CI | ||
| LLCI | ULCI | |||
| CS | −0.057 | 0.027 | −0.107 | −0.0003 |
| SS | −0.069 | 0.032 | −0.134 | −0.011 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, M.; Ugrin, J.; Li, M.; Wu, J.; Guo, S.; Zhang, W. Do Deterrence Mechanisms Reduce Cyberloafing When It Is an Observed Workplace Norm? A Moderated Mediation Model. Int. J. Environ. Res. Public Health 2021, 18, 6751. https://doi.org/10.3390/ijerph18136751
Song M, Ugrin J, Li M, Wu J, Guo S, Zhang W. Do Deterrence Mechanisms Reduce Cyberloafing When It Is an Observed Workplace Norm? A Moderated Mediation Model. International Journal of Environmental Research and Public Health. 2021; 18(13):6751. https://doi.org/10.3390/ijerph18136751
Chicago/Turabian StyleSong, Mengmeng, Joseph Ugrin, Man Li, Jinnan Wu, Shanshan Guo, and Wenpei Zhang. 2021. "Do Deterrence Mechanisms Reduce Cyberloafing When It Is an Observed Workplace Norm? A Moderated Mediation Model" International Journal of Environmental Research and Public Health 18, no. 13: 6751. https://doi.org/10.3390/ijerph18136751
APA StyleSong, M., Ugrin, J., Li, M., Wu, J., Guo, S., & Zhang, W. (2021). Do Deterrence Mechanisms Reduce Cyberloafing When It Is an Observed Workplace Norm? A Moderated Mediation Model. International Journal of Environmental Research and Public Health, 18(13), 6751. https://doi.org/10.3390/ijerph18136751






