Abstract
Medical Internet of Things (IoT) systems are crucial in monitoring the health status of patients. Recently, telemedicine services that manage patients remotely by receiving real-time health information from IoT devices attached to or carried by them have experienced significant growth. A primary concern in medical IoT services is ensuring the security of transmitted information and protecting patient privacy. To address these challenges, various authentication schemes have been proposed. We analyze the authentication scheme by Wang et al. and identified several limitations. Specifically, an attacker can exploit information stored in an IoT device to generate an illegitimate session key. Additionally, despite using a cloud center, the scheme lacks efficiency. To overcome these limitations, we propose an authentication and key distribution scheme that incorporates a physically unclonable function (PUF) and public-key computation. To enhance efficiency, computationally intensive public-key operations are performed exclusively in the cloud center. Furthermore, our scheme addresses privacy concerns by employing a temporary ID for IoT devices used to identify patients. We validate the security of our approach using the formal security analysis tool ProVerif.
1. Introduction
Medical Internet of Things (IoT) services facilitate communication between doctors and patients for monitoring and treating health conditions [1,2]. The COVID-19 pandemic has further accelerated the global demand for telemedicine, expanding medical IoT services beyond hospitals [3,4,5]. While the demand for such services varies by country, they have become particularly important in nations with large elderly populations [6,7], enabling patients to remotely monitor their health and connect with distant hospitals. According to a 2025 report, the global telemedicine market is projected to reach USD 107.52 billion in 2024, USD 121.10 billion in 2025, and USD 432.1 billion by 2032 [8].
Typically, telemedicine services begin with the pre-registration of the patient, attending physician, IoT medical device, and gateway in the hospital’s cloud center [9]. The patient’s health data are then regularly transmitted to the hospital’s cloud center via a gateway (GW) installed at home or in a nearby common location [10]. The physician reviews these data and provides appropriate responses.
In telemedicine services, IoT devices attached to or carried by patients have significantly fewer resources than medical devices within hospitals [11]. Additionally, to collect, process, and manage large volumes of patient data from diverse locations, a high-performance cloud center is essential. Thus, telemedicine imposes additional requirements beyond those of hospital-based medical IoT environments. However, owing to the sensitivity of transmitted data, ensuring mutual authentication among participants and protecting privacy and anonymity are critical. In recent years, various studies have explored these challenges in medical IoT environments.
More recently, authentication schemes have also been proposed that use cloud servers with unlimited computing resources to process information sent from a large number of IoT devices. These authentication schemes can be used in telemedicine, where a large amount of patient information needs to be processed. In 2023, C. Wang et al. [12] proposed a user authentication scheme for cloud-assisted IoT. However, this paper describes the limitation that this authentication scheme can lead to illegitimate session key exchange if an attacker obtains information stored in the user’s smart device or IoT device, which can lead to sensor node impersonation attack. In this paper, we propose a lightweight and efficient authentication scheme that overcomes the limitations of C. Wang et al. [12] and apply it to telemedicine services that used medical IoT devices with limited computing resources, and enhance privacy and anonymity. The key contributions of the proposed scheme are summarized as follows.
- We analyze C. Wang et al.’s work in [12] and find that their proposed authentication scheme is vulnerable to a stolen mobile device attack, which can lead an attacker to generate an illegitimate session key. We also show that the proposed scheme fails to achieve the goal of using cloud centers to increase efficiency by allowing IoT devices to perform public-key cryptographic computation.
- We propose an authentication scheme using cloud centers with unlimited computing resources, similar to the one proposed by C. Wang et al. in [12]. However, unlike C. Wang et al. [12], our scheme improves the efficiency of the authentication scheme by performing public-key cryptographic computation (ECC) only for users (smart devices) and cloud centers that have a certain level of computing resources.
- The proposed scheme minimizes the computation at IoT devices by using a physically unclonable function (PUF). In the scheme, the PUF’s challenge–response pair is transmitted through a private channel during the IoT device registration phase, and only the PUF’s challenge is transmitted through a public channel during the authentication and key distribution phases, making it resistant to PUF modeling attacks.
- The proposed scheme is resistant to user impersonation attacks, stolen-device attacks, PUF modeling attacks, etc., and provides anonymity and untraceability, mutual authentication, and forward and backward secrecy.
- The proposed scheme is verified using ProVerif, an official security analysis tool. In terms of performance, the proposed scheme achieves 35,436.18% computational savings compared to other recent studies, particularly on low-capacity sensor nodes.
The remainder of this paper is organized as follows: Section 2 discusses related works. Section 3 presents the system model for telemedicine and the attack model. Section 4 and Section 5 introduce Wang’s scheme and its identified vulnerabilities, respectively. Section 6 details the proposed authentication and key distribution scheme. Section 7 and Section 8 provide formal and informal security analyses, along with security and efficiency evaluations. Finally, Section 9 concludes the paper.
2. Related Work
With the advancement of IoT technology, numerous recent studies have proposed user authentication methods to ensure secure connections between IoT devices and users.
In 2018, Wazid et al. introduced the user-authenticated key management protocol (UAKMP), a secure and lightweight three-factor remote user authentication scheme for hierarchical IoT networks comprising various nodes, such as gateway nodes, cluster head nodes, and sensing nodes [13]. UAKMP provides password update functionality, ensures anonymity, and supports offline sensing node registration. However, according to Wang et al. [12], it does not satisfy clock synchronization and fails to guarantee forward secrecy.
Several authentication schemes have also been proposed for industrial IoT (IIoT) environments [14,15]. In 2020, Srinivas et al. introduced a user authentication scheme enabling remote users to analyze data in IIoT environments [15]. Their scheme employs biometric information, smart cards, and passwords for authentication, supporting password updates and smart card revocation in cases of loss or theft. However, according to Wang et al. [12], it does not ensure user anonymity. Similarly, in 2020, Yang et al. proposed a dynamic authentication credential framework for IIoT environments [14]. Their scheme achieved faster computation by avoiding public-key cryptography; however, according to Wang et al. [12], it does not guarantee forward secrecy.
Furthermore, in 2020, Wazid et al. proposed a user authentication scheme for smart-home environments [16]. Their scheme achieved high computational efficiency by utilizing only symmetric encryption and decryption. However, according to Wang et al. [12], it fails to ensure forward secrecy.
Recently, authentication schemes targeting a broader range of service environments have been proposed. In 2022, Dai et al. [17] proposed an authentication scheme for multigateway sensor networks. The scheme in [17] reduces communication requirements between gateways by registering two frequently visited gateway nodes and improves authentication efficiency using ECC. In the same year, Hu et al. [18] proposed a cloud-assisted authentication scheme based on Chebyshev polynomial encryption for IIoT environments. The scheme in [18] leverages cloud-computing technology with unlimited computing resources to reduce IoT device computation time. Additionally, in [19,20], cloud-computing technology has been utilized for authentication and key sharing in vehicle networks.
In 2023, Wang et al. [12] proposed a user authentication scheme for IoT using cloud centers. However, ref. [12] is vulnerable to stolen mobile devices and user-impersonation attacks, which may result in illegal session key exchanges. Our proposed scheme addresses the limitations of [12] and proposes a lightweight and efficient authentication and key distribution protocol.
3. Preliminaries
In this section, we introduce the system and attack models of the proposed scheme, along with the definitions and properties of the techniques used.
3.1. System Model
The proposed scheme targets a telemedicine system model, as shown in Figure 1, and consists of four entities: the user, cloud center, gateway, and IoT device. In this model, a doctor and their mobile device within a hospital are defined as the user, while a medical device that collects patient health information is classified as an IoT device. The gateway transmits data from the IoT device to the cloud center, which serves as a trusted hub for collecting, monitoring, managing, and processing patient information before transmitting it to the user. Each participant is described in detail below.
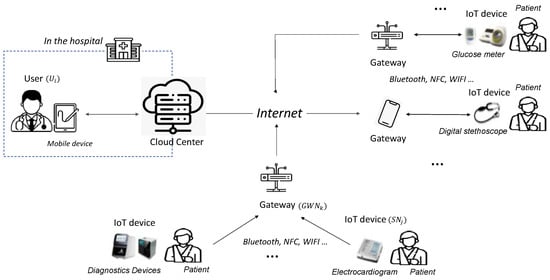
Figure 1.
System model for telemedicine.
- User (): The user is a legitimate entity with access to the IoT device. In this scheme, is a doctor who remotely monitors a patient’s health through an IoT device attached to the patient. As the system is designed for telemedicine, accesses the IoT device through the . Communication with the occurs via a smart device such as a smartphone or tablet.
- IoT Device (): The IoT device collects medical and health information from the patient and transmits it to through the gateway and the . is typically a low-power medical device placed in or on the patient’s body, such as a glucose meter or digital stethoscope. Therefore, it is assumed that cannot perform complex, resource-intensive operations. To enhance security, the proposed method uses physically unclonable function () technology in .
- Gateway (): The gateway is a trusted entity responsible for transmitting information collected from to the . While has greater computing power than , it faces limitations in handling large volumes of data transmitted by numerous IoT devices in a telemedicine environment. mainly communicates with using Bluetooth, NFC, or Wi-Fi and connects to the via the Internet.
- Cloud Center (): The is a trusted entity responsible for processing, managing, storing, and distributing patient information collected from multiple gateways to users. It plays a critical role in telemedicine services, requiring substantial computing resources to handle vast amounts of data from remotely located IoT devices. In the proposed scheme, the cloud center facilitates authentication and key distribution by securely sharing secret parameters during the registration process of , , and . It is assumed that the is securely managed and protected from attackers. In the cloud-assisted IoT for telemedicine services proposed in this paper, the cloud center does not play the role of a simple gateway that supports mutual authentication between users and IoT devices but is proposed as a centralized scheme to perform monitoring and analysis of patient information collected from IoT devices using the computing resources of the cloud center. In particular, in telemedicine services, patients (IoT devices) are often assigned to a doctor in advance, and the doctor has to manage a large number of patients, so a centralized scheme is a more realistic service model than a decentralized or peer-to-peer scheme.
3.2. Attacker Model
We assume that the cryptographic primitives used in the proposed scheme are secure and the attacker has the following capabilities:
- According to the Dolev–Yao model [21,22,23,24,25], the attacker can eavesdrop and intercept the messages transmitted over the public communication channel. Also, the attacker can delete, modify, and reply to any message transmitted over the public channel.
- The attacker can physically capture the user’s smart device, gateway, or IoT device and obtain all stored information, including certain security parameters.
- The attacker cannot access information stored in the Cloud Center.
- The Cloud Center and Gateway each securely hold their long-term secrets, and an attacker cannot obtain them.
3.3. Elliptic Curve Cryptography
ECC is a public-key cryptosystem that utilizes the mathematical properties of elliptic curves to achieve secure encryption [26,27,28]. It provides strong security with a smaller key size compared to traditional public-key cryptosystems such as RSA, offering improved performance. The proposed scheme is based on the elliptic curve discrete logarithm problem (ECDLP), which states that given a point P and a base point G () on an elliptic curve , it is computationally difficult to determine an integer d such that .
3.4. Fuzzy Extractor
A fuzzy extractor is a cryptographic technique designed to generate a stable and secure cryptographic key from biometric data or other noisy inputs [28,29]. As biometric measurements [30], such as fingerprints, may exhibit slight variations between scans, a fuzzy extractor ensures that the same cryptographic key is consistently derived despite these minor differences. It consists of two main procedures: a probabilistic generation procedure () and a deterministic reproduction procedure (), characterized as follows:
- takes a biometric input and generates a random string along with an auxiliary string , .
- takes as input , a similar , and the auxiliary string generated by , and reconstructs the random string , .
3.5. Physically Unclonable Function,
A PUF is a hardware-based security primitive that leverages inherent physical variations in semiconductor manufacturing to generate a unique, unclonable cryptographic key [31,32]. These unpredictable manufacturing variations produce distinct responses for each chip, making replication or cloning infeasible. A PUF operates based on the challenge–response pair (CRP) model, where an input challenge generates a unique response based on the physical characteristics of the hardware. When the same challenge is applied to the same chip, it consistently produces the same response, whereas different chips generate entirely different responses.
In this study, we adopt PUFs to achieve both lightweight operation and strong security for sensor nodes. PUFs generate random values based on intrinsic physical characteristics without requiring additional storage or heavy computation, unlike hardware security modules such as TPMs or symmetric key cryptographic approaches. Moreover, compared to HMAC-based schemes or traditional symmetric-key methods, PUFs offer stronger resistance against hardware cloning attacks. Due to these properties, PUFs are particularly suitable for resource-constrained medical IoT environments where computational capability and power consumption are critical concerns. PUFs are assumed to satisfy the following conditions:
- PUFs are physically unclonable: PUFs are inherently resistant to cloning and modification. They are also highly resistant to environmental factors and aging. An identical device cannot be reproduced by cloning a PUF, and any attempt to change a device containing a PUF will modify its functionality or render it unusable.
- PUFs exhibit one-way function properties: Given a response from a specific PUF, it is computationally infeasible to derive the corresponding challenge .
- Different PUFs generate different responses: For the same challenge , two different PUFs (PUF1 and PUF2) will produce distinct responses and .
- A PUF produces a consistent response for the same challenge: A given PUF always outputs the same response when presented with the same challenge .
- Low probability of response collision among multiple PUFs: The likelihood of two different PUFs generating identical responses is extremely low. This property enables PUFs to serve as unique identifiers for distinguishing a large number of IoT devices.
The proposed scheme applies to the IoT device . Using properties, uses during the registration phase with the and , as well as during the authentication and session key distribution phase with .
4. Review of Wang et al.’s Scheme
In this section, the scheme introduced by Wang et al. [12] is described. The scheme consists of four participants: the user, cloud center, gateway, and IoT device (sensor node). The user and IoT device perform mutual authentication to share a session key using the cloud center. The scheme is divided into four phases: gateway and IoT device registration, user registration, login, and authentication. The details are as follows:
4.1. Gateway and IoT Device Registration Phase
This phase comprises the registration of the gateway and IoT device with the cloud center. The details are as follows:
4.1.1. Gateway Registration
To register with the cloud center , the gateway follows these steps:
- sends a registration request to with .
- computes using its secret key x and sends the message to .
- stores .
4.1.2. IoT Device Registration
To register with , the IoT device follows these steps:
- sends a registration request to with .
- validates . If it is valid, computes , using ’s secret key . then sends to .
- keeps as its private key.
4.2. User Registration Phase
- inputs their identity , password , and biometric information into their smart mobile device. The device selects a random number , and computes , . The registration request is then sent to .
- selects a timestamp and a random number , then computes , = . The stores in its database and sends to .
- Upon receiving , the smart device selects a new random number a and calculates the following values. Finally, the smart device stores , , , , as .
4.3. Login Phase
If wants to access an IoT device, it initiates a login request to as follows:
- enters into the smart device, which then computes , , , . The device then compares with to verify the authenticity of . If is not equal to , the login request is rejected.
- If is equal to , the smart device selects a random number and computes , , , , , and . The device then sends to .
- ,
4.4. Authentication Phase
- To verify the , computes , . It then retrieves using . If is equal to , computes , , . It then verifies via . If is equal to , accepts the authenticity of .
- inserts into if there are fewer than 10 items. If the exceeds 10, ’s account is suspended until re-registration. then determines the gateway to which belongs, selects a random number r, and computes , , , and as shown below and sends to the gateway node .
- computes , , , and then verifies whether . If is equal to , computes , , as shown below, and sends .
- (where is a random number chosen by )
- The IoT device computes , , and compares the values of and . If is equal to , chooses a random number , calculates , , , , and responds to the gateway .
- computes and compares with to verify the identity of . If is equal to , calculates and sends to .
- computes to test the identity of . If is equal to , computes , and then returns to .
- Having obtained ’s reply , the smart mobile device computes . If is equal to , accepts as his session key shared with , and the authentication process finishes successfully.
5. Limitations of Wang et al.’s Scheme
We identified several critical limitations in Wang et al. [12]’s scheme. A detailed analysis of these vulnerabilities is provided below.
5.1. Stolen Mobile Device Attack
In Wang et al. [12]’s scheme, only legitimate users are allowed to log in using and during the user login phase. However, after user logs in, the messages , , , , and , which authenticate the user to , contain only information stored in the smart device. Although Wang et al. [12]’s scheme includes as a credential known only to the user, in general, user IDs in various Internet protocols are publicly accessible for identification, or they can often be computed in polynomial time by an attacker. This implies that if an attacker gains access to the user’s smart device and retrieves its stored information, they can successfully authenticate with without requiring the login phase. The following is a detailed attack scenario.
- {In step 2 of Section 4.3 Login Phase, the attacker computes using the information and stored in the stolen mobile device, and generates a random number . In addition, the attacker can find the of the legitimate user in polynomial time.
- The attacker then generates the following message using the previously calculated , , and to impersonate the legitimate user, and sends it to :
- –
- (where Y is ECC public key of )
- –
- (where P is ECC base point of )
- –
- –
- –
- In step 2 of Section 4.4 Authentication Phase, verifies using its private key y. If is equal to , then it finds through .
- The attacker can be authenticated as a legitimate user because all subsequent steps use the information stored inside regarding to perform subsequent authentication procedures.
5.2. Illegitimate Session Key Exchange
If the attacker knows and obtains from a captured IoT device, they can manipulate the session key exchange, as shown below.
- In step 4 of Section 4.4 Authentication Phase, the attacker chooses a random number and calculates , using the transmitted message as follows.
- –
- –
- (where P is the ECC base point of )
- The attacker uses the previously computed , , and the transmitted message to generate an illegitimate session key . The attacker also generates additional information so that the gateway and user can generate the same session key, and sends to .
- –
- –
- (where is a random number generated by the gateway in step 3 of Section 4.4 Authentication Phase, and is . And is the long-term secret of .)
- In step 5 of Section 4.4 Authentication Phase, checks if is equal to ‖ using and sent by the attacker and the information , , , and that it knows, where is . If it is equal, computes and sends to .
- In step 6 of Section 4.4 Authentication Phase, checks whether is equal to using and sent from and the information , , r, and that it knows, where is , and x is the secret long-term key of . If it is equal, computes and sends
- In step 7 of Section 4.4 Authentication Phase, uses and sent by and the information , , , , , and , knowing to check whether matches . If it matches, the user generates a session key as follows.
- –
- (where, )
Through this process, the illegally generated session key is exchanged between and by the attacker.
5.3. Inefficiency
A key contribution of Wang et al.’s scheme is the use of cloud-computing technology to overcome the computational and storage limitations of gateways and IoT devices. Reducing the computational load on the gateway or IoT devices significantly impacts the overall efficiency of the authentication scheme. However, in Wang et al.’s scheme, both the gateway and IoT devices perform computationally intensive ECC operations. Therefore, it is unclear whether the scheme effectively reduces the computational load on these resource-constrained devices compared to other authentication schemes that rely on symmetric key algorithms, despite the incorporation of cloud-computing technology.
6. Proposed Scheme
In this section, we propose a secure and efficient authentication and key distribution scheme to establish a secure telemedicine environment by addressing the vulnerabilities in Wang et al.’s scheme [12] described in Section 5 and integrating a cloud-assisted IoT framework into the medical domain.
The proposed scheme is applied to the system model shown in Figure 2. In this model, a doctor in a hospital serves as the user (), while a medical IoT device (sensor node, ) attached to or carried by the patient monitors the patient’s condition outside the hospital. The patient’s health data are transmitted from the IoT device to the cloud center through a gateway (), enabling the user to access the transmitted information, assess the patient’s condition, and provide appropriate prescriptions remotely.
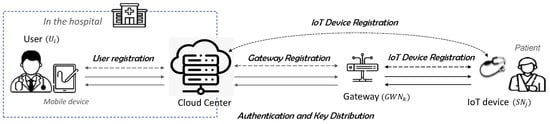
Figure 2.
Proposed authentication scheme.
To use the telemedicine service, the patient must first register the user , who is the doctor in charge, along with the medical IoT device , and the gateway with the . Therefore, in our proposed scheme, it is assumed that the cloud center is aware of the user and gateway based on the IoT device before the registration phase. In addition, in the proposed scheme, the user establishes a session key with the , while and share their respective session keys with the through mutual authentication. Consequently, direct authentication between , , and is not required. The notation used in the proposed scheme is provided in Table 1.

Table 1.
Notation.
6.1. User Registration Phase
In this phase, enters a user ID , password , and biometric information on the mobile device to initiate a legitimate login and register validation information with the for authentication. The details are illustrated in Figure 3.
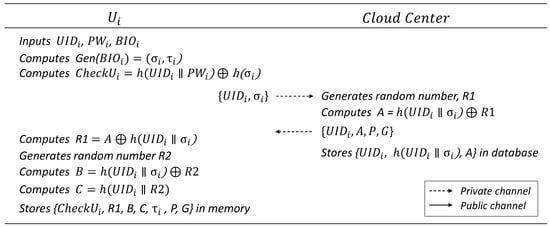
Figure 3.
User registration phase.
- inputs , , and into the mobile device, computes , and generates as additional validation information to prove legitimacy. then sends to the through a secure private channel.
- The generates a random number and computes . It then sends to , where G is the base point of the shared ECC algorithm, and P is the public key of the . After registering , the stores in its database.
- computes and generates a random number . It then computes , and stores in the mobile device’s memory.
6.2. Gateway Registration Phase
In this phase, and the complete the registration process using their respective long-term secrets, and , which are securely held by and , respectively. It is assumed that the is already aware of and , through prior offline registration. The details are illustrated in Figure 4.
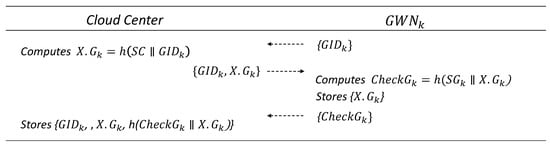
Figure 4.
Gateway registration phase.
- sends a registration request message containing to .
- computes and sends to .
- computes and sends it to the cloud center. It then stores in memory.
- stores in its database.
6.3. IoT Device Registration Phase
In this phase, registers with and , respectively. The details are illustrated in Figure 5.
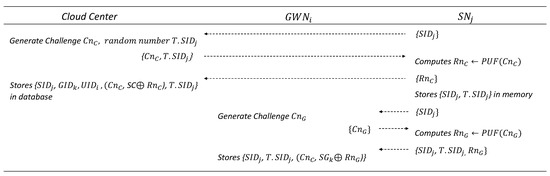
Figure 5.
IoT device (sensor) registration phase.
6.3.1. IoT Device Registration to Cloud Center
- sends a registration request message containing to .
- identifies using and generates a challenge along with a random number , where is a randomly generated temporary ID for . The then sends to .
- generates a response for and sends it to the . After sending the response, stores .
6.3.2. IoT Device Registration to Gateway
- sends a registration request message containing to .
- generates a challenge and sends it to .
- computes the response and sends to .
- stores in its database.
6.4. Authentication and Key Distribution Phase
In the proposed scheme, authentication and key distribution among the four participants are managed centrally by the . User does not communicate directly with or ; instead, all authentication and key exchange processes are facilitated through the cloud center. The details are illustrated in Figure 6 and Figure 7.

Figure 6.
Authentication and key distribution phase (Steps 1–3).
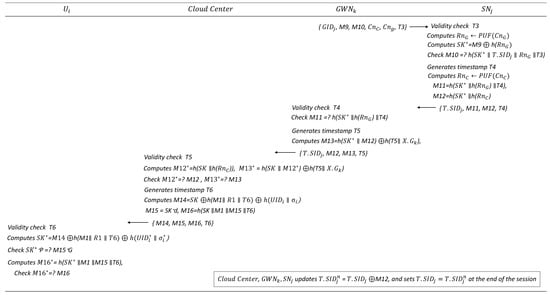
Figure 7.
Authentication and key distribution phase (Steps 4–7).
- User begins the authentication process by entering , , and on the mobile device, which then computes . The device verifies whether is equal to stored on it. If the check passes, the device computes and further verifies whether is equal to C. If successful, is logged into the mobile device. The device then generates a random number and timestamp , computing and as follows:
- , ,
Finally, sends to . - Upon receiving the message, the first verifies the validity of the timestamp . If it is invalid, the protocol terminates; otherwise, the retrieves and its associated information from its database. It then computes , , checking whether matches . If this condition is met, the computes and verifies whether it matches . To authenticate , it further checks whether matches . If successful, the user authentication is complete. Then sends the messages to . The then identifies the target gateway , generates a random session key , and a timestamp , and computes the following: , , and .Finally, the sends to .
- Upon receiving the message from the , first verifies the validity of timestamp . If invalid, the protocol terminates; otherwise, computes , and verifies whether matches . If successful, generates timestamp , and computes , , and as follows:then sends to .
- Upon receiving the message, verifies the validity of timestamp . If invalid, the protocol terminates; otherwise, computes , and verifies whether matches . If successful, generates timestamp and computes , , and as follows:then sends the message to .
- verifies the validity of timestamp and verifies whether matches M11. If valid, generates timestamp and computes , then sends to the .
- Upon receiving the message, the verifies the validity of timestamp . If valid, it retrieves , , and from the database regarding and computes , . The then verifies whether and match and , respectively. If successful, it generates timestamp and computes , , and as follows:The sends the message to .
- verifies the validity of timestamp . If valid, computes and confirms the integrity of the shared by performing the following steps:
- Computing .
- Verifying matches .
- Calculating and checking whether it is equal to .
If all conditions hold, the session key is securely shared among the participants. - Finally, at the end of the session, the , , and update as follows:
6.5. Password Update Phase
At the end of the session, inputs , , and into the smart device to initiate the password update process. The device computes and verifies whether matches the stored . If the values match, inputs as the new password and computes . Finally, the password update is completed when updates to and stores it in the device’s memory.
7. Security Analysis of Proposed Scheme
In this section, we present both formal and informal security analyses. The details are as follows:
7.1. Formal Security Analysis
In this paper, the ProVerif tool is used to formally analyze the security of the proposed authentication protocol [33,34,35,36,37]. ProVerif, developed by Blanchet et al. [38], is widely used for verifying security properties such as confidentiality and authentication in cryptographic protocols. The proposed protocol is modeled in Applied Pi-Calculus, and its resistance to attacks is evaluated under the Dolev–Yao model [21].
The details of each code are presented in Table 2, Table 3, Table 4, Table 5, Table 6, Table 7 and Table 8. Table 2 describes the variables, events, channels, and function declarations in the ProVerif code. Table 3 presents the user registration and authentication phases. Table 4 illustrates the operation process of the cloud center, while Table 5 outlines the gateway’s operation process. Table 6 describes the operation process of the sensor node. Table 7 lists the queries used to verify the overall operation, and Table 8 presents the results obtained when the queries from Table 7 were executed.

Table 2.
Definitions of channels, variables, and other related parameters.

Table 3.
User process.

Table 4.
CloudCenter process.

Table 5.
Gateway process.

Table 6.
SensorNode process.

Table 7.
Queries and main process.

Table 8.
Result.
This study conducted an automated formal verification using the ProVerif tool to evaluate the security and safety of the designed protocol.
The ProVerif queries were configured as follows:
- query inj-event(endUser(idi)) ==> inj-event(startUser(idi)) verifies that the user’s authentication completion event occurs only if the authentication initiation event has occurred (mutual authentication for users).
- query inj-event(endCloudCenter()) ==> inj-event(startCloudCenter()) verifies the correct execution of the cloud center’s authentication process.
- query inj-event(endGateway(gwi)) ==> inj-event(startGateway(gwi)) checks the correctness of the gateway’s authentication.
- query inj-event(endSensorNode(snj)) ==> inj-event(startSensorNode(snj)) checks the correctness of the sensor node’s authentication.
- query attacker(SharedKey) verifies the confidentiality of the session key, ensuring it is not accessible to the attacker.
The verification results show that all authentication and confidentiality queries returned true. This indicates that the proposed protocol successfully guarantees mutual authentication among the user, cloud center, gateway, and sensor node, and that the session key remains confidential against potential attackers. The analysis results obtained from ProVerif show that all specified security queries were proven to be true, confirming that the protocol successfully meets its intended security requirements. Specifically, the verification demonstrated that a user’s termination event always occurs after the corresponding initiation event, clearly ensuring user authentication. Additionally, the termination event at the cloud center was verified to occur strictly following its initiation event, thereby validating the reliability of the system’s communication flow. Furthermore, the gateway and sensor nodes were also confirmed to maintain correct sequential consistency between their respective initiation and termination events, securing the integrity of message exchanges. Moreover, the analysis mathematically verified that an attacker could not access or compromise the primary shared keys, highlighting the strong confidentiality provided by the protocol. Based on these comprehensive results, it can be concluded that the proposed protocol effectively fulfills critical security requirements such as authentication, confidentiality, and integrity.
7.2. Informal Security Analysis
The proposed scheme satisfies nine critical security requirements, including protection against user-impersonation attacks, stolen-device attacks, session key disclosure attacks, anonymity and untraceability, mutual authentication, replay attacks, forward secrecy attacks, man-in-the-middle attacks, and PUF modeling attacks [39,40,41,42]. A comparison of the latest studies and their corresponding security properties is summarized in Table 9. The detailed security properties of the proposed scheme are as follows:

Table 9.
Comparison of security features.
7.2.1. A1: Resistance to User-Impersonation Attack
The proposed scheme effectively resists user-impersonation attacks because even if an attacker intercepts the authentication messages sent to the cloud center, they cannot generate , which is a critical parameter for authentication. As the cloud center must calculate to verify the user, the inability of the attacker to reconstruct prevents further progress in the authentication process. The scheme is also resistant to stolen-device attacks.
7.2.2. A2: Resistance to Stolen-Device Attack
Even if an attacker physically steals a user’s smart device and obtains stored information , they cannot generate the valid biometric information required for login or authentication. Furthermore, for IoT devices, even if an attacker gains access to and intercepts messages transmitted over public channels, they cannot generate the response used for authentication, owing to the nature of the PUF. The scheme is also resistant to stolen-device attacks.
7.2.3. A3: Resistance to Session Key Disclosure Attack
Messages and , which contain session key information, are transmitted over a public channel. However, an attacker cannot compute from these messages because they cannot access and , both of which are essential for deriving . The scheme ensures security against session key exposure attacks.
7.2.4. A4: Resistance to Replay Attack
During the authentication and key distribution phase, each transmitted message includes a timestamp, and the recipient first verifies its validity. If the timestamp is invalid, the session is immediately terminated. Therefore, the proposed scheme is resistant to replay attacks.
7.2.5. A5: Resistance to Man-in-the-Middle Attack
In the proposed scheme, secret information that can only be generated by each participant is used for mutual authentication between , , , and during the authentication and key distribution phases. For instance, even if an attacker intercepts all messages transmitted over the public channel, they may attempt to change and in a message from to to impersonate the legitimate . However, the attacker cannot generate , which is uniquely generated by . Therefore, the request message sent by the attacker cannot successfully authenticate as the legitimate user. In this manner, the proposed scheme is resistant to man-in-the-middle attacks, as the authentication value is generated using secret information known only to the legitimate participants, making it impossible for an attacker to alter or forge this value.
7.2.6. A6: Resistance to PUF Modeling Attack
Finally, the scheme is resistant to PUF modeling attacks, which involve collecting a large number of PUF challenge–response pairs and using machine learning techniques to predict legitimate responses. In the proposed scheme, two PUF challenge–response pairs, and , are transmitted over a private channel during the IoT device registration phase. However, during the authentication and key-sharing phases, only the PUF challenges and are transmitted over a public channel, while the responses remain private. This prevents attackers from collecting sufficient challenge–response pairs to train a predictive model, making PUF modeling attacks infeasible.
7.2.7. S1: Provide Anonymity and Untraceability
Regarding anonymity and untraceability, the proposed telemedicine system model does not require user anonymity because the doctor communicates with the cloud center rather than directly with the IoT device. However, anonymity and untraceability are necessary for the patient’s IoT device. The scheme achieves this by using , a temporary ID for , which is randomly generated for each session and updated at the end of the session to provide anonymity and untraceability.
7.2.8. S2: Provide Mutual Authentication
During the authentication and key distribution phases, , , , and undergo mutual authentication. The authenticates by verifying that and match and , respectively. authenticates the by verifying , while authenticates by verifying . If any of these values are invalid, the session is aborted, ensuring that the proposed scheme provides mutual authentication.
7.2.9. S3: Provide Forward and Backward Secrecy
The proposed scheme guarantees forward and backward secrecy by ensuring that the session key is randomly generated for each session. Although it is used to compute , it cannot be inferred owing to the one-way nature of the hash function. Therefore, even if the session key for a particular session is compromised, an attacker cannot determine the session keys for previous or future sessions. Therefore, the proposed scheme provides forward secrecy and backward secrecy.
8. Performance Analysis of Proposed Scheme
In this section, we compare the performance of the proposed scheme with recent studies [12,13,14,15,16,17,18,19], focusing on minimizing the computational overhead of IoT devices while evaluating our scheme against existing works.
For comparison, we utilized computational overhead measurements obtained from a prior study conducted in a CPU-based environment using an Intel Core i7-8700 (3.20 GHz) processor, Windows 10 (64-bit) OS, and 48 GB of memory, employing the Python cryptography library 3.13.2 [33]. The results are presented in Table 10.

Table 10.
Computation times for each operation (μs).
In the study by Wang et al. [12], the user performs 8 hash function computations, 1 fuzzy extractor operation, and 3 elliptic curve multiplications, which can be expressed as . Based on the experimental environment, this corresponds to 2129.52 s. At the cloud center, 10 hash function computations and 1 elliptic curve multiplication are performed, expressed as s. The gateway node performs 9 hash function computations, represented as s. Additionally, the sensor node executes 4 hash function computations and 2 elliptic curve multiplications, which can be expressed as s.
Wazid et al. [13] introduced an approach where the user carries out , which corresponds to 535.01 s. Their scheme does not involve a cloud center, so the gateway node handles , taking 2.03 s. On the sensor side, is performed, resulting in 1.3 s.
Yang et al. [14]’s method focuses on lightweight computation, requiring the user to compute , leading to 1.52 s. The gateway node processes , with an execution time of 2.66 s, while the sensor node performs , taking 1.33 s.
Srinivas et al. [15] proposed an approach where the user performs , consuming 542.45 s. Their method involves computations at the gateway node, where is executed, taking 1.9 s. The sensor node carries out , leading to a processing time of 8.74 s.
Wazid et al.’s scheme in [16] follows a slightly different structure. The user executes , with a computation time of 533.98 s. The gateway node computes , requiring 2.63 s, while the sensor node carries out , taking 1.6 s.
Dai et al. [17] introduced a model where the user must perform , consuming 2129.71 s. The gateway node handles , with an execution time of 534.09 s, and the sensor node processes , leading to 1064.95 s.
Hu et al. [18]’s scheme assigns computations to the user, requiring 542.45 s. Their method does not include cloud center processing, so the gateway node executes , with a computation time of 1.6 s. Meanwhile, the sensor node performs , resulting in 8.63 s.
Jiang et al. [19] designed a method where the user processes , which takes 3194.36 s. The cloud center, in their model, executes , consuming 2662.55 s, while the sensor node handles , leading to 0.76 s.
In our proposed scheme, as demonstrated in Table 11, we optimize the computational cost across all entities. The user performs , leading to 2661.71 s. Our approach eliminates unnecessary computations at the cloud center, processing , taking 1067.23 s. The gateway node handles , requiring 1.71 s, while the sensor node executes , resulting in a final processing time of 0.57 s. Our proposed scheme increases the computational load at the cloud center and user mobile devices, thereby reducing the computational burden on the sensor node. While the average computational cost at the sensor node in other schemes is 202.5563 s, our scheme reduces this to 0.57 s, making it approximately 35,436.18% more efficient. The overall efficiency of the authentication scheme is most affected by the load and cost of the sensor nodes. Relatively speaking, cloud centers and user mobile devices have relatively high computing resources compared to sensor nodes and gateways, so the increase in computation does not have a significant impact on the overall efficiency of the authentication scheme. Moreover, as demonstrated in Table 9, our proposed scheme ensures stronger security performance compared to other studies.

Table 11.
Comparisons of computational costs (s).
9. Conclusions
In this study, we analyzed Wang et al.’s authentication scheme and identified several limitations, including the vulnerability in illegal session key exchanges due to stored information in IoT devices and publicly transmitted data, as well as inefficiencies despite utilizing cloud centers. To overcome these issues, we incorporated technology into IoT devices to prevent unauthorized session key exchanges and improve efficiency by ensuring that public-key computations are performed exclusively in the cloud center. In addition to safeguarding patient privacy and maintaining untraceability, IoT devices utilize only a temporary during authentication and key distribution. In this study, computationally intensive operations are offloaded to the cloud to significantly reduce the computational and energy burden on sensor nodes. This approach enables stable service provision even in resource-constrained medical IoT devices. By performing all authentication and key exchange processes through the cloud center, the proposed scheme achieves lightweight operation at both sensor nodes and gateways. The system is designed under the assumption that the cloud center possesses sufficient computational power and communication resources. In practical deployments, ensuring appropriate cloud resource provisioning and adopting efficient resource management strategies will help maintain system efficiency and stability. Through this approach, the proposed authentication and key distribution scheme is expected to maintain efficiency and robustness across diverse environments. Although the proposed authentication and key distribution scheme is designed for medical IoT environments, its structure is not application-specific, allowing for flexible adaptation to other IoT domains. For instance, the lightweight sensor node design and cloud-based authentication framework can be readily applied to smart homes, industrial IoT, and smart city environments. Therefore, the proposed scheme can maintain high efficiency and stability not only in healthcare but also in a variety of large-scale IoT deployments. Finally, we compared the security and efficiency of our scheme with recent authentication schemes [12,13,14,15,16,17,18,19] and validated its security using ProVerif, a formal security analysis tool.
Author Contributions
Conceptualization: H.J.L., S.K., and K.K.; methodology: H.J.L. and J.R.; software: S.K. and K.K.; validation: H.J.L., H.L., and J.R.; formal Analysis: K.K. and J.R.; writing—original draft preparation: H.J.L., S.K., and K.K.; writing—review and editing: J.R. and Y.L.; visualization: H.J.L.; supervision: J.R. and D.W.; project administration: J.R. and D.W.; funding acquisition: D.W. All authors have read and approved the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ali, Z.; Mahmood, S.; Mansoor, K.; Daud, A.; Alharbey, R.; Bukhari, A. A lightweight and secure authentication scheme for remote monitoring of patients in IoMT. IEEE Access 2024, 12, 73004–73020. [Google Scholar] [CrossRef]
- Manickam, N.; Ponnusamy, V. A Review of Secure Healthcare Data Analytics using Federated Machine Learning and Blockchain Technology. IEIE Trans. Smart Process. Comput. 2024, 13, 254–262. [Google Scholar] [CrossRef]
- Batool, R.; Raza, G.M.; Khalid, U.; Kim, B.S. Automated Detection of COVID-19 in Chest Radiographs: Leveraging Machine Learning Approaches. IEIE Trans. Smart Process. Comput. 2024, 13, 572–578. [Google Scholar]
- Lee, H.J.; Kook, S.; Kim, K.; Ryu, J.; Lee, Y.; Won, D. LAMT: Lightweight and Anonymous Authentication Scheme for Medical Internet of Things Services. Sensors 2025, 25, 821. [Google Scholar] [CrossRef]
- Prajapat, S.; Kumar, P.; Kumar, D.; Das, A.K.; Hossain, M.S.; Rodrigues, J.J. Quantum secure authentication scheme for internet of medical things using blockchain. IEEE Internet Things J. 2024, 11, 38496–38507. [Google Scholar] [CrossRef]
- Mookherji, S.; Vanga, O.; Prasath, R.; Das, A.K. A secure authentication protocol for remote patient monitoring in an internet-of-medical-things environment. Secur. Priv. 2024, 7, e428. [Google Scholar] [CrossRef]
- Sachnev, V.; Suresh, M.B. An Automatic Diagnostic Tool for Autism Spectrum Disorder using Structural Magnetic Resonance Imaging and a Tailored Binary Coded Genetic Algorithm. IEIE Trans. Smart Process. Comput. 2024, 13, 236–242. [Google Scholar] [CrossRef]
- Fortune Business Insights. Available online: https://www.fortunebusinessinsights.com/press-release/telemedicine-market-9214 (accessed on 20 March 2025).
- Ekambaram, D.; Ponnusamy, V. AI-assisted physical therapy for post-injury rehabilitation: Current state of the art. IEIE Trans. Smart Process. Comput. 2023, 12, 234–242. [Google Scholar] [CrossRef]
- Rani, D.; Tripathi, S. Design of blockchain-based authentication and key agreement protocol for health data sharing in cooperative hospital network. J. Supercomput. 2024, 80, 2681–2717. [Google Scholar] [CrossRef]
- Yadav, N.S.; Goar, V.K. IoT in Healthcare and Telemedicine: Revolutionizing Patient Care and Medical Practices. In Scalable Modeling and Efficient Management of IoT Applications; IGI Global: Hershey, PA, USA, 2025; pp. 19–58. [Google Scholar]
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and lightweight user authentication scheme for cloud-assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Yang, Z.; He, J.; Tian, Y.; Zhou, J. Faster authenticated key agreement with perfect forward secrecy for industrial internet-of-things. IEEE Trans. Ind. Inform. 2020, 16, 6584–6596. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous lightweight chaotic map-based authenticated key agreement protocol for industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1133–1146. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2020, 17, 391–406. [Google Scholar] [CrossRef]
- Dai, C.; Xu, Z. A secure three-factor authentication scheme for multi-gateway wireless sensor networks based on elliptic curve cryptography. Ad Hoc Netw. 2022, 127, 102768. [Google Scholar] [CrossRef]
- Hu, H.; Liao, L.; Zhao, J. Secure authentication and key agreement protocol for cloud-assisted industrial internet of things. Electronics 2022, 11, 1652. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified biometric privacy preserving three-factor authentication and key agreement for cloud-assisted autonomous vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Zhao, J.; Li, Q.; Gong, Y.; Zhang, K. Computation Offloading and Resource Allocation For Cloud Assisted Mobile Edge Computing in Vehicular Networks. IEEE Trans. Veh. Technol. 2019, 68, 7944–7956. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Degefa, F.; Ryu, J.; Kim, H.; Won, D. MES-FPMIPv6: MIH-Enabled and enhanced secure Fast Proxy Mobile IPv6 handover protocol for 5G networks. PLoS ONE 2022, 17, e0262696. [Google Scholar] [CrossRef]
- Jung, J.; Lee, D.; Lee, H.; Won, D. Security enhanced anonymous user authenticated key agreement scheme using smart card. J. Electron. Sci. Technol. 2018, 16, 45–49. [Google Scholar]
- Mahmood, K.; Obaidat, M.S.; Shamshad, S.; Alenazi, M.J.; Kumar, G.; Anisi, M.H.; Conti, M. Cost-effective authenticated solution (CAS) for 6G-enabled artificial intelligence of medical things (AIoMT). IEEE Internet Things J. 2024, 11, 23977–23984. [Google Scholar] [CrossRef]
- Chen, C.M.; Xiong, Z.; Wu, T.Y.; Kumari, S.; Alenazi, M.J. Protecting Virtual Economies: A Blockchain-based Anti-Phishing Authentication Protocol for Metaverse Applications. IEEE Internet Things J. 2025; early access. [Google Scholar]
- Kapoor, V.; Abraham, V.S.; Singh, R. Elliptic curve cryptography. Ubiquity 2008, 9, 1–8. [Google Scholar] [CrossRef]
- Maarouf, A.; Sakr, R.; Elmougy, S. An offline direct authentication scheme for the internet of medical things based on elliptic curve cryptography. IEEE Access 2024, 12, 134902–134925. [Google Scholar] [CrossRef]
- Lee, H.; Kang, D.; Lee, Y.; Won, D. Secure Three-Factor Anonymous User Authentication Scheme for Cloud Computing Environment. Wirel. Commun. Mob. Comput. 2021, 2021, 2098530. [Google Scholar] [CrossRef]
- Fuller, B.; Reyzin, L.; Smith, A. When are fuzzy extractors possible? IEEE Trans. Inf. Theory 2020, 66, 5282–5298. [Google Scholar] [CrossRef]
- An, J.; Choi, S.H. End-to-end Facial Recognition Deep Learning Model Specialized for Facial Angle using Gray Image. IEIE Trans. Smart Process. Comput. 2024, 13, 534–539. [Google Scholar] [CrossRef]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Aldosary, A.; Tanveer, M. PAAF-SHS: PUF and authenticated encryption based authentication framework for the IoT-enabled smart healthcare system. Internet Things 2024, 26, 101159. [Google Scholar] [CrossRef]
- Woo, N.; Kang, T.; Ryu, J. CESA: Chebyshev-Polynomials-Based Efficient and Secure Access Authentication Scheme for Both User Equipment and Massive Machine-Type-Communication Devices Over 5G Networks. IEEE Internet Things J. 2025; early access. [Google Scholar]
- Kim, K.; Ryu, J.; Lee, H.; Lee, Y.; Won, D. Distributed and federated authentication schemes based on updatable smart contracts. Electronics 2023, 12, 1217. [Google Scholar] [CrossRef]
- Lee, H.; Ryu, J.; Won, D. Secure and anonymous authentication scheme for mobile edge computing environments. IEEE Internet Things J. 2023, 11, 5798–5815. [Google Scholar] [CrossRef]
- Ryu, J.; Lee, H.; Lee, Y.; Won, D. SMASG: Secure mobile authentication scheme for global mobility network. IEEE Access 2022, 10, 26907–26919. [Google Scholar] [CrossRef]
- Kang, T.; Woo, N.; Ryu, J. Enhanced lightweight medical sensor networks authentication scheme based on blockchain. IEEE Access 2024, 12, 35612–35629. [Google Scholar] [CrossRef]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 2.00: Automatic Cryptographic Protocol Verifier. User Man. Tutor. 2018, 16, 5–16. [Google Scholar]
- Kim, J.; Moon, J.; Jung, J.; Won, D. Security analysis and improvements of session key establishment for clustered sensor networks. J. Sens. 2016, 2016, 4393721. [Google Scholar] [CrossRef]
- Ryu, J.; Kang, D.; Won, D. Improved secure and efficient Chebyshev chaotic map-based user authentication scheme. IEEE Access 2022, 10, 15891–15910. [Google Scholar] [CrossRef]
- Kook, S.; Kim, K.; Ryu, J.; Lee, Y.; Won, D. Lightweight Hash-Based Authentication Protocol for Smart Grids. Sensors 2024, 24, 3085. [Google Scholar] [CrossRef]
- Miao, J.; Wang, Z.; Wu, Z.; Ning, X.; Tiwari, P. A blockchain-enabled privacy-preserving authentication management protocol for Internet of Medical Things. Expert Syst. Appl. 2024, 237, 121329. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).