A Secure Medical Data Framework Integrating Blockchain and Edge Computing: An Attribute-Based Signcryption Approach
Abstract
1. Introduction
1.1. Background
1.2. Motivation and Contributions
- A novel framework that integrates blockchain, edge computing, and ABSC for securing and efficiently managing EHR data, designed specifically to meet the requirements of IoMT environments.
- A comprehensive evaluation that compares the proposed system with existing blockchain-based EHR solutions, showcasing its advantages in terms of security, scalability, and computational efficiency.
- A detailed analysis of the impact of edge computing on the performance of blockchain-based EHR systems, supported by real-world case studies and numerical simulations.
2. Related Work
2.1. Blockchain for Healthcare Data Security
- Data integrity and auditability: Ghadi et al. [22] demonstrated a Hyperledger Fabric-based audit system achieving 99.7% tamper detection accuracy, though limited to 150 transactions per second (TPS). This work established baseline performance metrics for medical blockchain systems but overlooked real-time processing requirements. Hussien et al. [5] innovated with smart contract-driven dynamic policy updates, representing a 40% improvement over traditional RBAC systems. However, their centralized key management architecture (single Certificate Authority) introduced new vulnerabilities.
- Decentralized access control: Mollah et al. [10] proposed a blockchain-edge hybrid model that reduced access control latency by 58% compared to pure cloud solutions. Their use of Ethereum smart contracts for policy enforcement demonstrated the feasibility of decentralized authorization. A breakthrough came from Quan et al. [13], whose 2023 framework achieved three times faster encryption throughput through edge-assisted computation offloading. Their multi-authority design mitigated single-point failures but increased signature verification overhead by 35%.
- Cross-institutional sharing: Emerging solutions like Liu et al. [19] introduced a searchable ABE for EHR systems, enabling encrypted queries with 92% precision. However, their reliance on a trusted third party for key generation remained a limitation.
2.2. Evolution of ABSC Schemes
- First-generation schemes: Wang et al. [8] pioneered CP-ABSC using elliptic curves, achieving doctor/nurse role differentiation but with signature sizes growing linearly with attributes. Their 2024 work reduced verification time by 25% through optimized pairing operations. Hu et al. [9] established foundational security proofs for multicast communications, though their scheme required four pairing operations per decryption. Belguith et al. [23] proposed a Cooperative Attribute-Based Signcryption (C-ABSC) scheme that enables secure and collaborative communication between multiple IoT entities.
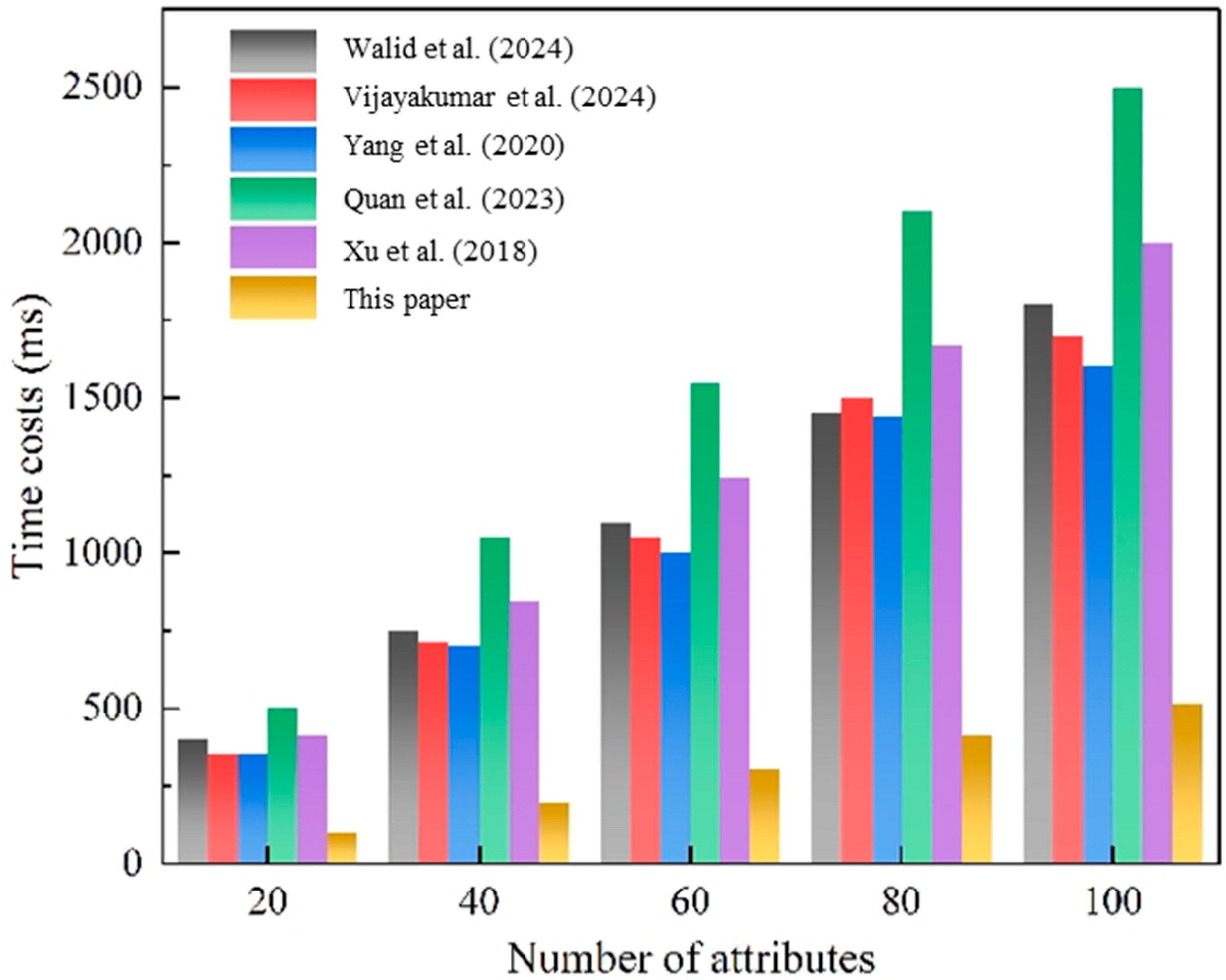
- Lightweight innovations: Vijayakumar et al. [24] revolutionized the field with fog-assisted ABSC, cutting encryption latency from 380 ms to 120 ms (100 attributes) through computational task partitioning. Their 2024 PLOS One study demonstrated 98% reliability in ICU monitoring scenarios. Xiao et al. [25] achieved 40% bandwidth reduction via attribute-based forwarding, though at the cost of 15% higher CPU utilization on fog nodes. Sai Varshith et al. [17] leveraged kernel-level attribute enforcement to support dynamic policy updates in secure healthcare environments. Kibiwott et al. [26] addressed secure access control in large-scale IoMT systems through a verifiable and scalable ABSC architecture.
- Dynamic attribute management: He et al. [4] introduced real-time revocation using timestamp attributes, reducing privilege escalation attacks by 60% but increasing storage overhead by 20%. Yang et al. [18] developed a mobile-optimized scheme with constant-size signatures, enabling secure sharing on smartphones with <100 ms latency. Xu et al. [14] proposed a secure data sharing scheme that integrates chaotic maps and blockchain, offering enhanced access control mechanisms similar to ABSC. Ma et al. [16] tackled dynamic access revocation via blockchain and ZK-Rollup, reducing user privilege escalation risks.
2.3. Real-Time Processing Frameworks
- Real-time processing frameworks: Xu et al. [21] achieved 80% faster emergency response times through fog-based pre-processing, though their multi-authority design increased key management complexity. Yang et al. [27] combined blockchain and ABSC to support real-time, consent-driven healthcare data sharing.
- Federated learning integration: Liu et al. [30] made groundbreaking progress with BC-SABE, combining blockchain with searchable ABE to enable encrypted AI model training across hospitals while maintaining 92% diagnostic accuracy.
3. Materials and Methods
3.1. Preliminaries
3.1.1. Bilinear Pairing
- Bilinearity: for all , we have , where is the integer modulo prime .
- Efficient computation: for all , there exists an efficient algorithm to compute .
- Non-degeneracy: the generators and must satisfy .
3.1.2. Access Control Structure
3.1.3. Access Tree Structure
- Root node: The root node is the top-level node in the access tree, representing the secret information to be protected (e.g., a key). Only users who meet specific conditions are allowed to access the data represented by this node.
- Non-leaf nodes: These nodes are also called “threshold nodes” and function similarly to logic gates, such as “AND” or “OR”. Each non-leaf node has a threshold value. Permissions are granted only when the number of child nodes that meet the conditions reaches or exceeds the threshold.
- Leaf nodes: These are the bottom-level nodes of the access tree. Each leaf node represents a specific attribute (e.g., “doctor”, “researcher”, or “age over 50”). Users must meet these attribute conditions to decrypt the corresponding data.
3.2. The System
3.2.1. System Settings
3.2.2. Algorithms
- : the setup algorithm takes a security parameter λ as input and produces public parameters along with a master key .
- ): with the public parameter , a master key , and a set of attributes as inputs, this algorithm generates a secret key , a signing key , and a verification key as outputs.
- : given the public parameters , the plain-text , the access tree , and the signing key , the algorithm generates a signed ciphertext for the plain text according to the access tree .
- : using the signed ciphertext , the secret key , and the set of attributes , the algorithm returns the plain text if the attribute set satisfies the access tree . Otherwise, it returns the error symbol ⊥.
3.3. Scheme of the System
3.3.1. System Setup
3.3.2. Entity Registration
3.3.3. Data Collection and Uploading
3.3.4. Data Query
4. Results
4.1. Implementation Environment
4.2. Theoretical Analysis
4.3. Numerical Simulations
5. Discussion
5.1. Security Model
- Data confidentiality: The ciphertext-policy ABSC ensures that only devices possessing the correct attribute sets and corresponding private keys can decrypt the data. This prevents unauthorized access to sensitive medical data.
- Data integrity: The system uses cryptographic signatures to ensure that the data have not been tampered with during storage or transmission. Any modifications to the data can be detected through signature verification.
- Message authenticity: The system guarantees that data access and transmission requests come from verified users. The proposed cryptographic mechanism is implemented through publicly accessible encryption keys issued by trusted authorities (TAs), which concurrently establish an authentication framework for both data requesters (DRs) and their associated smart devices (SDs).
- Access control: The system provides fine-grained access control through an attribute set, ensuring that only authorized users can access the encrypted data. Each data access request is validated based on the user’s attributes, ensuring precise data retrieval permissions.
5.2. Threat Model
- Identity forgery: An attacker could try to impersonate a legitimate user to gain access to the system. To prevent this, the system relies on the authentication provided by the trusted authorities (TAs), which ensure that only legitimate users receive private keys and are granted access to the system. The blockchain records every access request, which can be used for auditing and detecting any fraudulent activity.
- Unauthorized access: Attackers may attempt to gain unauthorized access to medical data. However, this threat is mitigated by the ABSC mechanism, which enforces fine-grained access control based on user attributes. Only users who possess the correct attributes are allowed to decrypt and access the data. Additionally, the use of blockchain ensures that any unauthorized attempts to modify or access data will be easily detectable.
- Data integrity attacks: Attackers may attempt to alter or tamper with data stored in the system. The use of blockchain ensures that any changes to the data are impossible without detection, as every change is recorded in an immutable ledger. In addition, the cryptographic signatures used in the ABSC scheme guarantee that the data remains unchanged during storage and transmission.
- Availability attacks: The decentralized nature of the blockchain mitigates the risk of Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attacks, as there is no single point of failure in the system. Additionally, the edge computing infrastructure offloads data processing, reducing the burden on any single node and improving the system’s resilience against availability attacks.
- Eavesdropping and data leakage: Even if an attacker intercepts communication, they cannot read the data without possessing the correct decryption keys. The encryption provided by ABSC ensures that the data are protected during transmission. Furthermore, the use of blockchain ensures the confidentiality of the encryption keys, making it difficult for attackers to obtain them.
- Replay attacks: The system ensures protection against replay attacks by utilizing secure, time-stamped messages and access control protocols that verify each transaction’s authenticity before processing it.
- Malicious insider attacks: Insiders, such as compromised edge devices or service providers, could attempt to access or tamper with the data. However, the use of blockchain ensures full transparency and auditability of all actions, enabling the detection of any malicious activities. Additionally, the ABSC mechanism ensures that only authorized users can access the data, and any unauthorized access will be flagged.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| SD | Smart devices |
| ED | Edge devices |
| TA | Trusted authorities |
| SP | Services providers |
| DO | Data owners |
| DR | Data eequesters |
| ABSC | Attribute-Based Signcryption |
| IoMT | Internet of Medical Things |
| CP-ABSC | ciphertext-policy Attribute-Based Signcryption |
| ABE | Attribute-Based Encryption |
| IoT | Internet of Things |
| EHR | Electronic Health Record |
| ECC | Elliptic Curve Cryptography |
References
- Nyangaresi, V.O.; Huang, Y.; Teng, T.; Li, Y.; Zhang, M. Attribute encryption access control method of high dimensional medical data based on fuzzy algorithm. PLoS ONE 2025, 20, e0317119. [Google Scholar]
- Li, D.; Zhang, E.; Lei, M.; Song, C. Zero trust in edge computing environment: A blockchain based practical scheme. Math. Biosci. Eng. 2022, 19, 4196–4216. [Google Scholar] [CrossRef] [PubMed]
- Walid, R.; Joshi, K.P.; Choi, S.G. Comparison of attribute-based encryption schemes in securing healthcare systems. Sci. Rep. 2024, 14, 7147. [Google Scholar] [CrossRef] [PubMed]
- He, Z.; Chen, Y.; Luo, Y.; Zhang, L.; Tang, Y. Revocable and Traceable Undeniable Attribute-Based Encryption in Cloud-Enabled E-Health Systems. Entropy 2023, 26, 45. [Google Scholar] [CrossRef]
- Hussien, H.; Yasin, S.; Udzir, N.; Ninggal, M. Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage. Sensors 2021, 21, 2462. [Google Scholar] [CrossRef]
- Adeniyi, J.K.; Ajagbe, S.A.; Adeniyi, A.E.; Adeyanju, K.I.; Afolorunso, A.A.; Adigun, M.O.; Ogene, I. A Blockchain-based Smart Healthcare System for Data Protection. iScience 2025, 25, 112109. [Google Scholar] [CrossRef] [PubMed]
- Yan, L.; Wang, G.; Feng, H.; Liu, P.; Gao, H.; Zhang, W.; Hu, H.; Pan, F. Efficient and accountable anti-leakage attribute-based encryption scheme for cloud storage. Heliyon 2024, 10, e32404. [Google Scholar] [CrossRef]
- Wang, H.; Ma, R.; Du, L. Efficient attribute-based strong designated verifier signature scheme based on elliptic curve cryptography. PLoS ONE 2024, 19, e0300153. [Google Scholar]
- Hu, C.; Cheng, X.; Tian, Z.; Yu, J.; Sun, L. An Attribute-Based Signcryption Scheme to Secure Attribute-Defined Multicast Communications. In Security and Privacy in Communication Networks: 11th EAI International Conference, SecureComm 2015, Dallas, TX, USA, 26–29 October 2015; Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar]
- Mollah, M.B.; Azad, M.A.K.; Zhang, Y. Secure Targeted Message Dissemination in IoT Using Blockchain Enabled Edge Computing. IEEE Trans. Consum. Electron. 2024, 70, 5389–5400. [Google Scholar] [CrossRef]
- Yang, X.; Xi, W.; Chen, A.; Wang, C. An environmental monitoring data sharing scheme based on attribute encryption in cloud-fog computing. PLoS ONE 2021, 16, e0258062. [Google Scholar] [CrossRef]
- Sun, J.; Wang, X.; Wang, S.; Ren, L.; Mehmood, R. A searchable personal health records framework with fine-grained access control in cloud-fog computing. PLoS ONE 2018, 13, e0207543. [Google Scholar] [CrossRef] [PubMed]
- Quan, G.; Yao, Z.; Chen, L.; Fang, Y.; Zhu, W.; Si, X.; Li, M. A trusted medical data sharing framework for edge computing leveraging blockchain and outsourced computation. Heliyon 2023, 9, e22542. [Google Scholar] [CrossRef] [PubMed]
- Xu, Z.; Zheng, E.; Han, H.; Dong, X.; Dang, X.; Wang, Z. A secure healthcare data sharing scheme based on two-dimensional chaotic mapping and blockchain. Sci. Rep. 2024, 14, 23470. [Google Scholar] [CrossRef] [PubMed]
- Jain, G.; Kumar, N.; Rigby, C. Blockchain’s Transformative Potential in Healthcare. Blockchain Healthc. Today 2024, 7, 336. [Google Scholar] [CrossRef]
- Ma, S.; Zhang, X. Integrating blockchain and ZK-ROLLUP for efficient healthcare data privacy protection system via IPFS. Sci. Rep. 2024, 14, 11746. [Google Scholar] [CrossRef]
- Varshith, H.O.S.; Sural, S.; Vaidya, J.; Atluri, V. Enabling Attribute-Based Access Control in Linux Kernel. In Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, Nagasaki, Japan, 30 May–3 June 2022; Association for Computing Machinery: Nagasaki, Japan, 2022; pp. 1237–1239. [Google Scholar]
- Yang, Y.; Liu, X.; Deng, R.H.; Li, Y. Lightweight Sharable and Traceable Secure Mobile Health System. IEEE Trans. Dependable Secur. Comput. 2020, 17, 78–91. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, Y.; Fan, Y. Searchable Attribute-Based Signcryption Scheme for Electronic Personal Health Record. IEEE Access 2018, 6, 76381–76394. [Google Scholar] [CrossRef]
- Patil, P.; Mukane, S.; Nagpure, S.; Patil, R. Maintaining Chain of Custody using Attribute Based Signcryption (ABSC). In Proceedings of the 2024 International Conference on Intelligent Computing and Emerging Communication Technologies (ICEC), Guntur, India, 23–25 November 2024. [Google Scholar]
- Xu, Q.; Tan, C.; Fan, Z.; Zhu, W.; Xiao, Y.; Cheng, F. Secure Data Access Control for Fog Computing Based on Multi-Authority Attribute-Based Signcryption with Computation Outsourcing and Attribute Revocation. Sensors 2018, 18, 1609. [Google Scholar] [CrossRef]
- Ghadi, Y.Y.; Mazhar, T.; Shahzad, T.; Amir khan, M.; Abd-Alrazaq, A.; Ahmed, A.; Hamam, H. The role of blockchain to secure internet of medical things. Sci. Rep. 2024, 14, 18422. [Google Scholar] [CrossRef]
- Belguith, S.; Kaaniche, N.; Mohamed, M.; Russello, G. C-ABSC: Cooperative Attribute Based SignCryption Scheme for Internet of Things Applications. In Proceedings of the 2018 IEEE International Conference on Services Computing (SCC), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Vijayakumar, P.; Sun, Y.; Du, X.; Niu, S.; Zhou, S. A lightweight attribute-based signcryption scheme based on cloud-fog assisted in smart healthcare. PLoS ONE 2024, 19, e0297002. [Google Scholar]
- Xiao, J.; Chang, C.; Wu, P.; Ma, Y. Attribute identification based IoT fog data security control and forwarding. PeerJ Comput. Sci. 2023, 9, e1747. [Google Scholar] [CrossRef] [PubMed]
- Kibiwott, K.P.; Zhao, Y.; Kogo, J.; Zhang, F. Verifiable fully outsourced attribute-based signcryption system for IoT eHealth big data in cloud computing. Math. Biosci. Eng. 2019, 16, 3561–3594. [Google Scholar] [CrossRef] [PubMed]
- Yang, X.; Li, T.; Xi, W.; Chen, A.; Wang, C. A Blockchain-Assisted Verifiable Outsourced Attribute-Based Signcryption Scheme for EHRs Sharing in the Cloud. IEEE Access 2020, 8, 170713–170731. [Google Scholar] [CrossRef]
- Yu, J.; Liu, S.; Wang, S.; Xiao, Y.; Yan, B. LH-ABSC: A Lightweight Hybrid Attribute-Based Signcryption Scheme for Cloud-Fog-Assisted IoT. IEEE Internet Things J. 2020, 7, 7949–7966. [Google Scholar] [CrossRef]
- Hong, H.; Sun, Z. An efficient and secure attribute based signcryption scheme with LSSS access structure. SpringerPlus 2016, 5, 644. [Google Scholar] [CrossRef]
- Liu, S.; Yu, J.; Xiao, Y.; Wan, Z.; Yan, B. BC-SABE: Blockchain-aided Searchable Attribute-based Encryption for Cloud-IoT. IEEE Internet Things J. 2020, 7, 7851–7867. [Google Scholar] [CrossRef]
- Ming, Y.; Zhang, T. Efficient Privacy-Preserving Access Control Scheme in Electronic Health Records System. Sensors 2018, 18, 3520. [Google Scholar] [CrossRef]
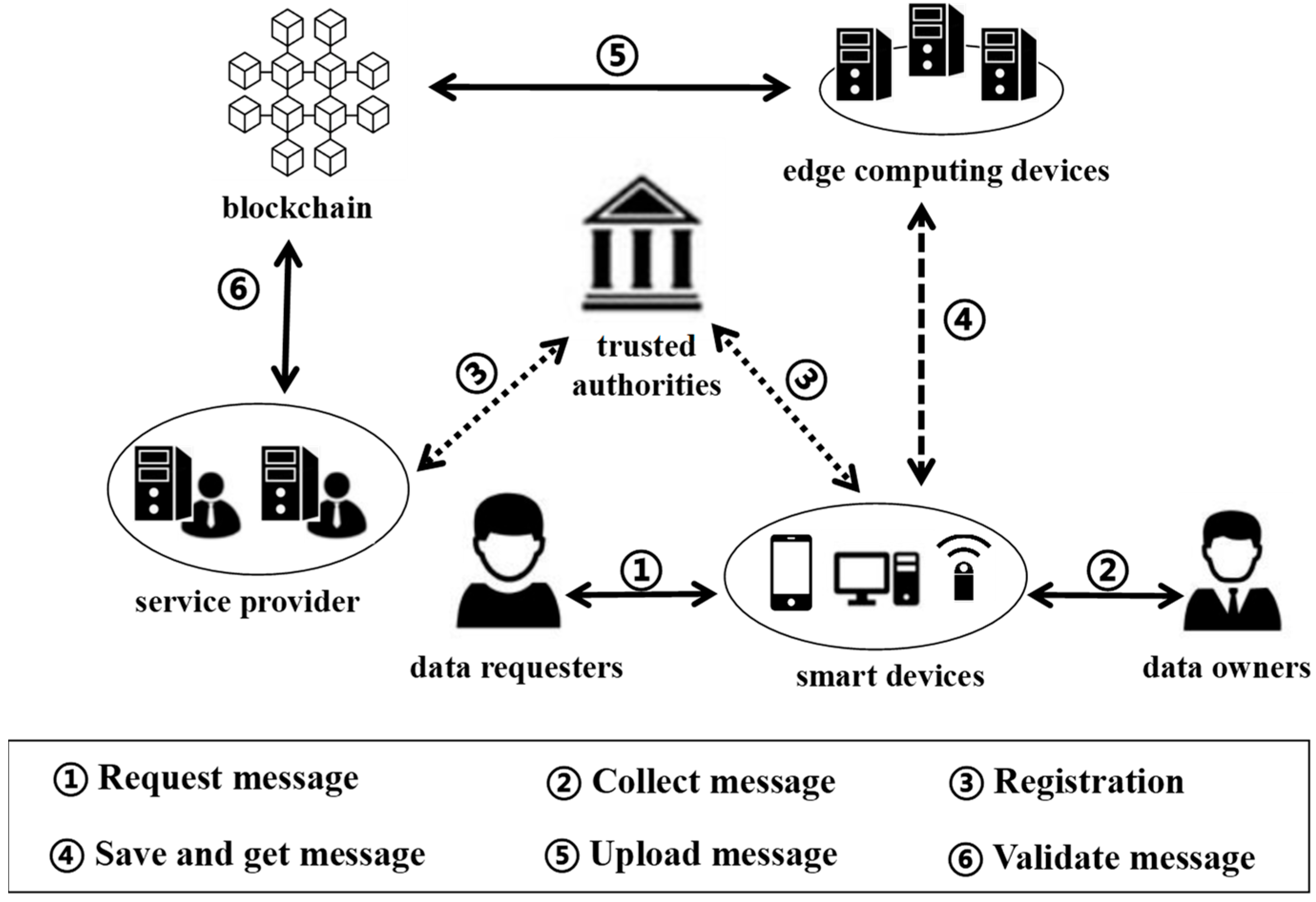

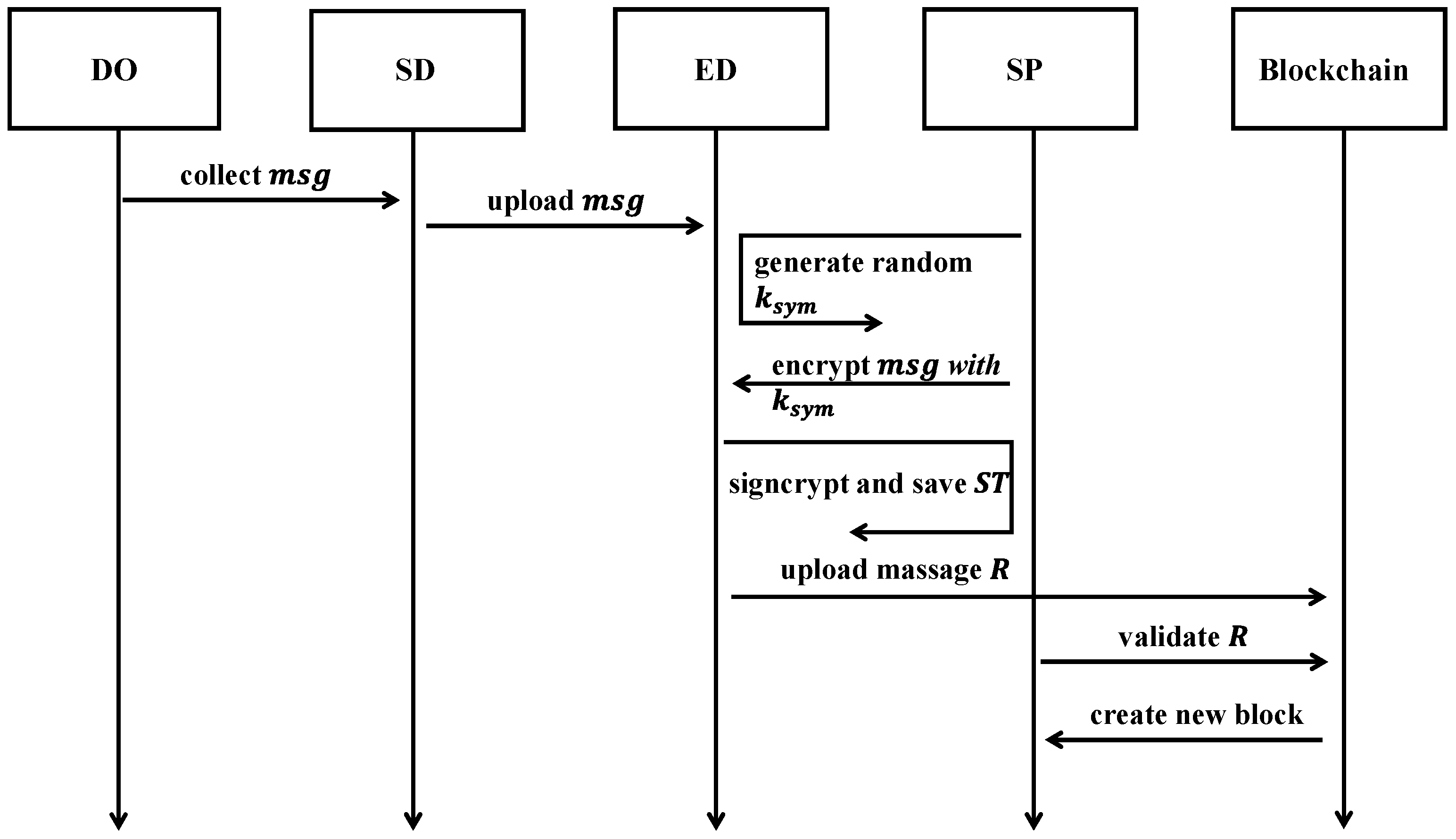
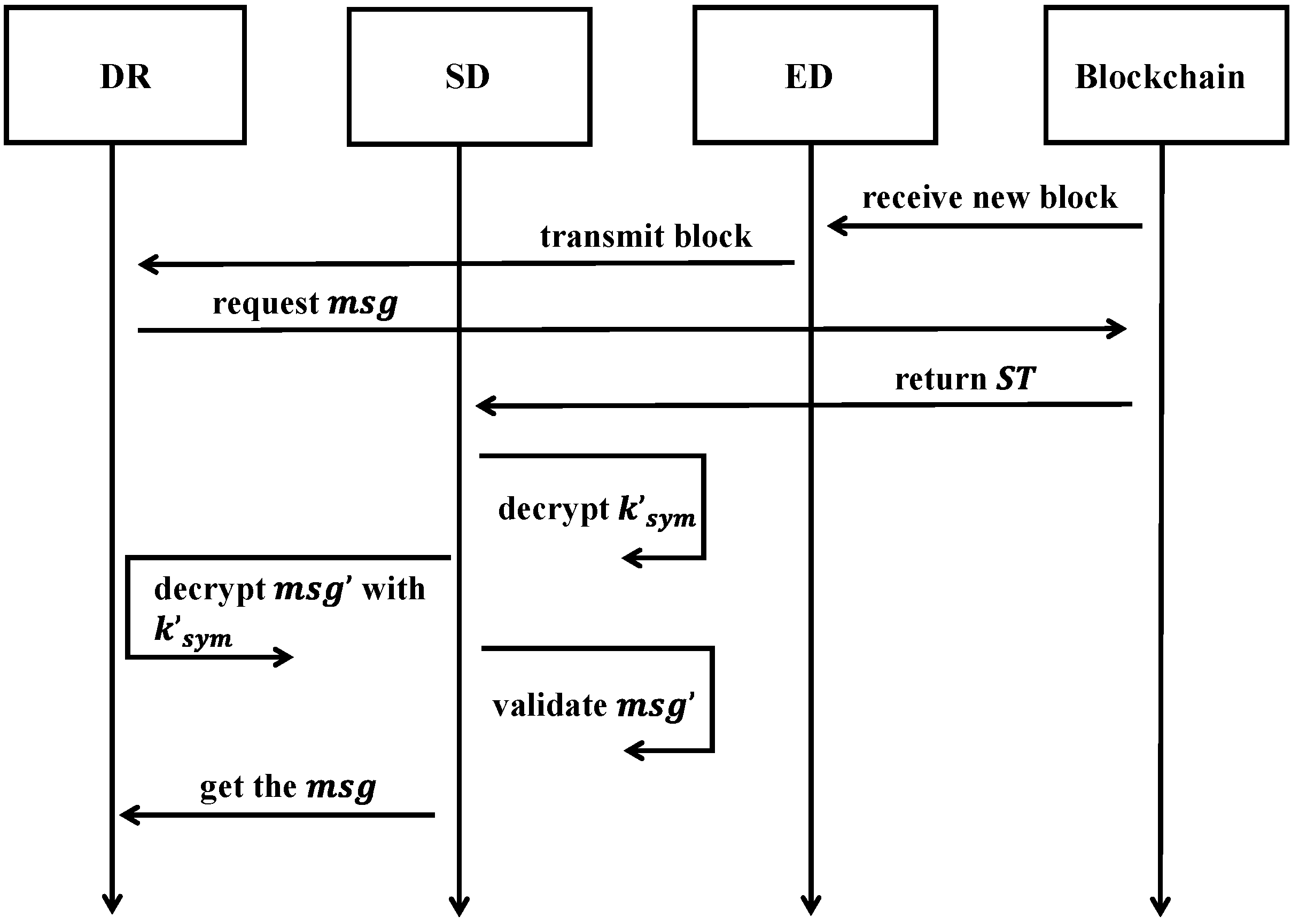

| Component | Primary Role | Key Responsibilities |
|---|---|---|
| Smart device (SD) | Data collection | -Collects physiological data -Performs lightweight encryption |
| Edge device (ED) | Local processing/storage | -Processes and stores encrypted data -Maintains blockchain network |
| Service provider (SP) | Data analysis intermediary | -Processes medical data -Validates blockchain transactions |
| Trusted authority (TA) | Security management | -Manages authentication |
| Data owner (DO) | Data control | -Defines access policies -Records data transactions on blockchain |
| Data requester (DR) | Data access | -Requests data access -Undergoes identity verification |
| System Initialization | Registration | Signcryption | Designcryption | Reference |
|---|---|---|---|---|
| 3 + | 2|N| + 6 + 2 | (5|N| + 6) + (2|N| + 4) | 2|N| + 3 + |N| | [31] |
| (3 + |N|) + |N| | (3 + |N|) + (|N| + 1) + 2 | (|N| + 2) + (|N| + 1) + 2 | [24] | |
| 2|N| + 6 + 2 | (5|N| + 6) + (2|N| + 4) | 2|N| + 3 + |N| | [3] | |
| 3 + | (3 + |N|) + |N| | (2|N| + 6) + (|N| + 1) + 2 | (|N|+2) + (|N| + 1) + 2 | This paper |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dou, T.; Zheng, Z.; Qiu, W.; Ge, C. A Secure Medical Data Framework Integrating Blockchain and Edge Computing: An Attribute-Based Signcryption Approach. Sensors 2025, 25, 2859. https://doi.org/10.3390/s25092859
Dou T, Zheng Z, Qiu W, Ge C. A Secure Medical Data Framework Integrating Blockchain and Edge Computing: An Attribute-Based Signcryption Approach. Sensors. 2025; 25(9):2859. https://doi.org/10.3390/s25092859
Chicago/Turabian StyleDou, Tengyue, Zhiming Zheng, Wangjie Qiu, and Chunxia Ge. 2025. "A Secure Medical Data Framework Integrating Blockchain and Edge Computing: An Attribute-Based Signcryption Approach" Sensors 25, no. 9: 2859. https://doi.org/10.3390/s25092859
APA StyleDou, T., Zheng, Z., Qiu, W., & Ge, C. (2025). A Secure Medical Data Framework Integrating Blockchain and Edge Computing: An Attribute-Based Signcryption Approach. Sensors, 25(9), 2859. https://doi.org/10.3390/s25092859





