A Comprehensive Survey of Privacy-Enhancing and Trust-Centric Cloud-Native Security Techniques Against Cyber Threats
Abstract
1. Introduction
1.1. Motivation
1.2. Contribution
- We provide a detailed survey of unique security challenges, including the dynamic nature of microservices, container vulnerabilities, and complexities in decentralized access control in cloud-native environments.
- We offer a comprehensive analysis of current security tools and techniques, including runtime protection platforms, DevSecOps pipelines, cloud-native security information and event management (SIEM), and IAM systems.
- We examine the integration of advanced technologies such as AI-driven threat detection and blockchain-based access control as innovative solutions for cloud-native security.
- We present a case study illustrating security solutions applied across multiple layers, including application, network, infrastructure, and security and compliance, highlighting how these measures ensure a consistent security posture throughout cloud-native solutions.
- Lastly, we summarize the future research directions by proposing a framework for developing adaptive security measures, advanced threat detection techniques, and robust access control mechanisms tailored to cloud-native environments.
1.3. Organization
2. Related Works
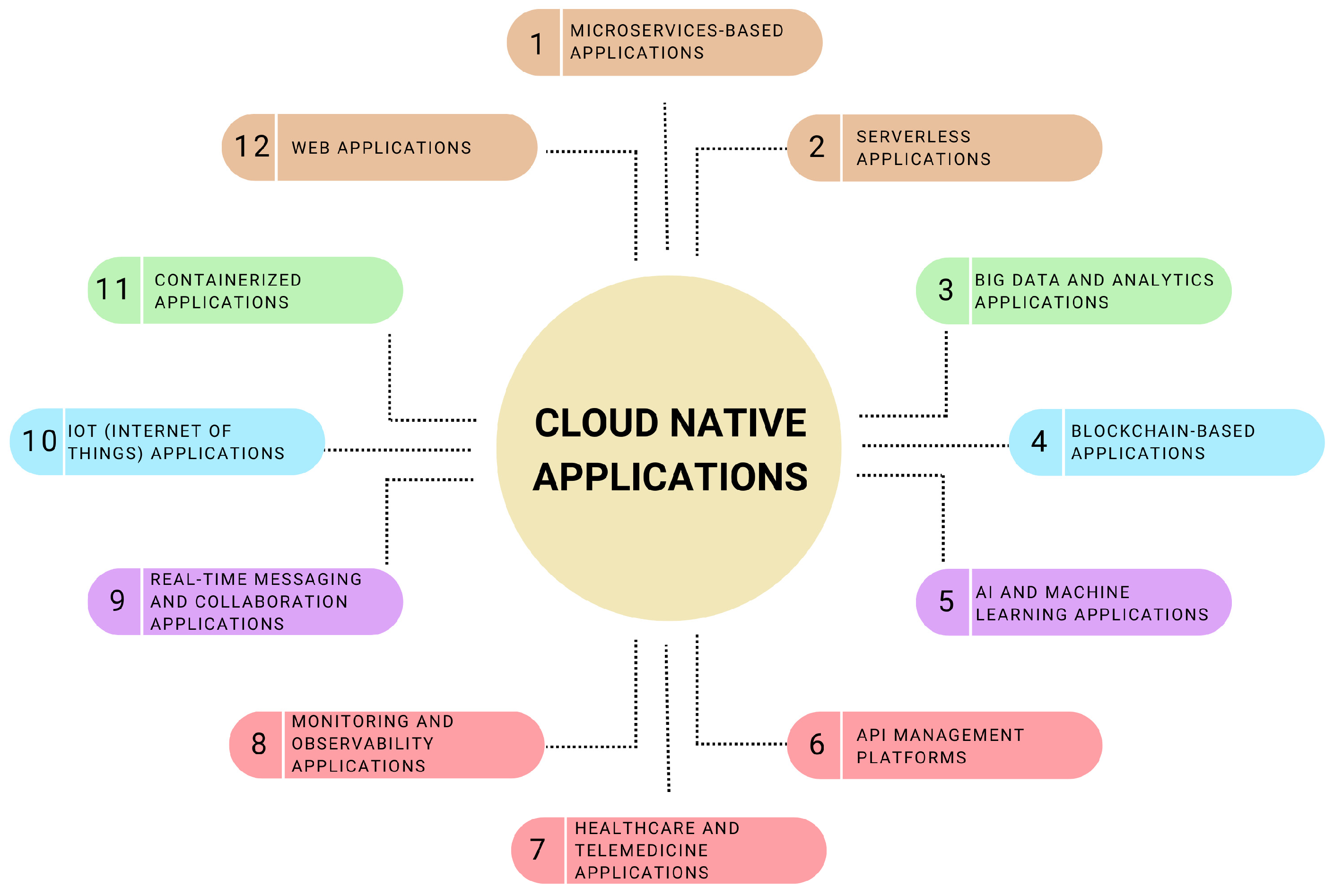
3. Cloud-Native Applications
- Microservice-based applications: Microservice architecture is a methodological advancement in software design that consists of distinct, self-contained services that communicate over well-defined Application Programming Interfaces (APIs) and carry out specialized tasks within systems. Teams may independently create, implement, and scale portions of the application with this architecture, which improves agility and shortens time-to-market. As exemplary cases, consider Netflix, Spotify, and Airbnb, where every microservice handles a different function or service, such as listing administration, user authentication, or video streaming, enabling these platforms to quickly develop and adjust to shifting consumer demands [68,69].
- Web applications: Among the most well-known and often utilized categories of cloud-native applications are web applications. These cloud-native applications provide high availability and scalability and may be accessed from any location using a web browser. Web applications developed with a cloud-native strategy can scale dynamically in response to user demand, ensuring performance and cost-effectiveness. Cloud-native web applications are best demonstrated by e-commerce sites like Amazon and eBay, which manage millions of transactions and customer interactions with ease [70]. Similar to this, cloud-native architectures are used by social media global giants like Facebook and Twitter to dynamically distribute content to billions of users globally, demonstrating the capacity to manage enormous volumes of data and user connections in real time.
- Serverless applications: With serverless computing, the cloud provider manages the execution environment, scales, and bills based on actual resource consumption, freeing developers to concentrate on building code that supports business logic. This technique works especially well with event-driven systems, in which programs react to certain occurrences, including file uploads, hypertext transfer protocol (HTTP) requests, or modifications to databases. An example of how serverless computing facilitates quick development and deployment cycles is the ability to create apps that scale automatically and economically with AWS Lambda, Azure Functions, and Google Cloud Functions [71,72].
- Containerized applications: Docker is a prime example of containerization technology that has transformed application deployment by encapsulating programs within lightweight containers. The application code, libraries, and dependencies are all included in this encapsulation, which assures consistency between various computer systems. Microservice architectures depend on containerized applications because they are cloud-native by nature and provide scalability, isolation, and simplicity of deployment. The orchestration solution for containers, Kubernetes, significantly improves containerized application administration by facilitating smooth rollouts of updates or new features, auto-scaling, and self-healing [73].
- Big data and analytics applications: Modern digital technologies need to handle and analyze massive datasets quickly and efficiently due to the proliferation of data. Cloud-native applications use cloud-based big data systems to process large amounts of data, such as Google BigQuery, Apache Spark, and Hadoop [74]. These platforms provide the scalability and flexibility needed for data ingestion, storage, processing, and visualization. By offering insights that drive innovation and decision-making, they support a broad range of applications, from genomic sequencing and scientific research to business intelligence and customer analytics.
- IoT (Internet of Things) applications: IoT applications use cloud computing to gather, handle, and evaluate data from networked sensors and devices in a variety of settings, including cities and factories as well as households. Because of the cloud’s enormous processing power and scalability, these applications frequently need real-time processing and analytics to produce actionable insights. To process and manage the massive influx of data from IoT devices and enable advanced features like maintenance forecasting and personalized user experiences, cloud-native technologies are essential to smart home systems, which include security cameras and thermostats, as well as industrial monitoring systems and connected vehicle solutions [75,76,77].
- Blockchain-based applications: Blockchain technology leverages cloud infrastructure’s scalability, security, and dependability to host decentralized apps (DApps). Utilizing the immutable and transparent properties of blockchain technology within a cloud-native framework, these applications, which range from cryptocurrency exchanges to supply chain tracking systems and decentralized finance (DeFi) platforms, offer new methods for managing data, decentralized from centralized control, and conducting transactions [78].
- Real-time messaging and collaboration applications: Real-time communication and collaboration tools, which need to be highly available, scalable, and latency-free to offer flawless user experiences, are best supported by cloud-native architecture. Cloud-native applications can facilitate immediate global communication and collaboration, revolutionizing the way people work and interact [79,80]. Examples of such applications include messaging apps such as WhatsApp, videoconferencing applications like Zoom, and collaborative document editing tools like Google Docs.
- AI and machine learning applications: Cloud-native technologies are being used in a novel way by AI and machine learning applications, which make it possible to handle large datasets at scale and perform intricate computations. Large datasets require a lot of resources and time in order to train machine learning models. Cloud platforms provide specialized equipment, like GPUs and TPUs, for this purpose [81]. Cloud scalability is used by cloud-native AI applications, like Netflix and Amazon’s personalized recommendation engines, image and speech recognition services, and predictive analytics for business intelligence, to adjust to changing workloads and data volumes. This allows for the quick development and implementation of AI models.
- Monitoring and observability applications: Monitoring and observability are essential for assuring application performance and reliability in the complex environment of cloud-native apps. Tools that offer the insights required to identify and fix problems in distributed systems include Grafana for visualization, Prometheus for monitoring, and Elasticsearch for logging and tracing. By gathering and examining metrics, logs, and traces from different areas of a cloud-native application, these programs help developers and operators better comprehend system behavior, maximize performance, and preserve system integrity [82,83,84].
- API management platforms: The fundamental components of digital transformation are APIs, which allow software programs to exchange information and interact. Apigee, API Gateway, and Kong are examples of cloud-native API management programs that offer a scalable environment for API creation, management, and security [85]. These platforms provide developer interfaces for API discovery and collaboration along with the ability to monitor API usage, enforce access controls, and manage API traffic. These platforms facilitate innovation and integration across digital ecosystems by enabling enterprises to speed the creation of applications and services by exploiting cloud-native capabilities.
- Healthcare and telemedicine applications: Cloud-native apps, such as electronic health records (EHR), telemedicine, and remote patient monitoring, are revolutionizing patient care in the healthcare industry [86]. Strong compliance with health data laws, such as HIPAA, is necessary for these applications, which make use of the cloud’s capacity to handle and securely store sensitive data, enable real-time patient-provider communication, and support advanced analytics for diagnostic imaging and personalized medicine. Concisely, Table 2 provides a comprehensive analysis of these applications, techniques of implementation, and their effects on cloud-native amenities in the various sectors discussed in this section.
4. Techniques for Securing Cloud-Native Applications
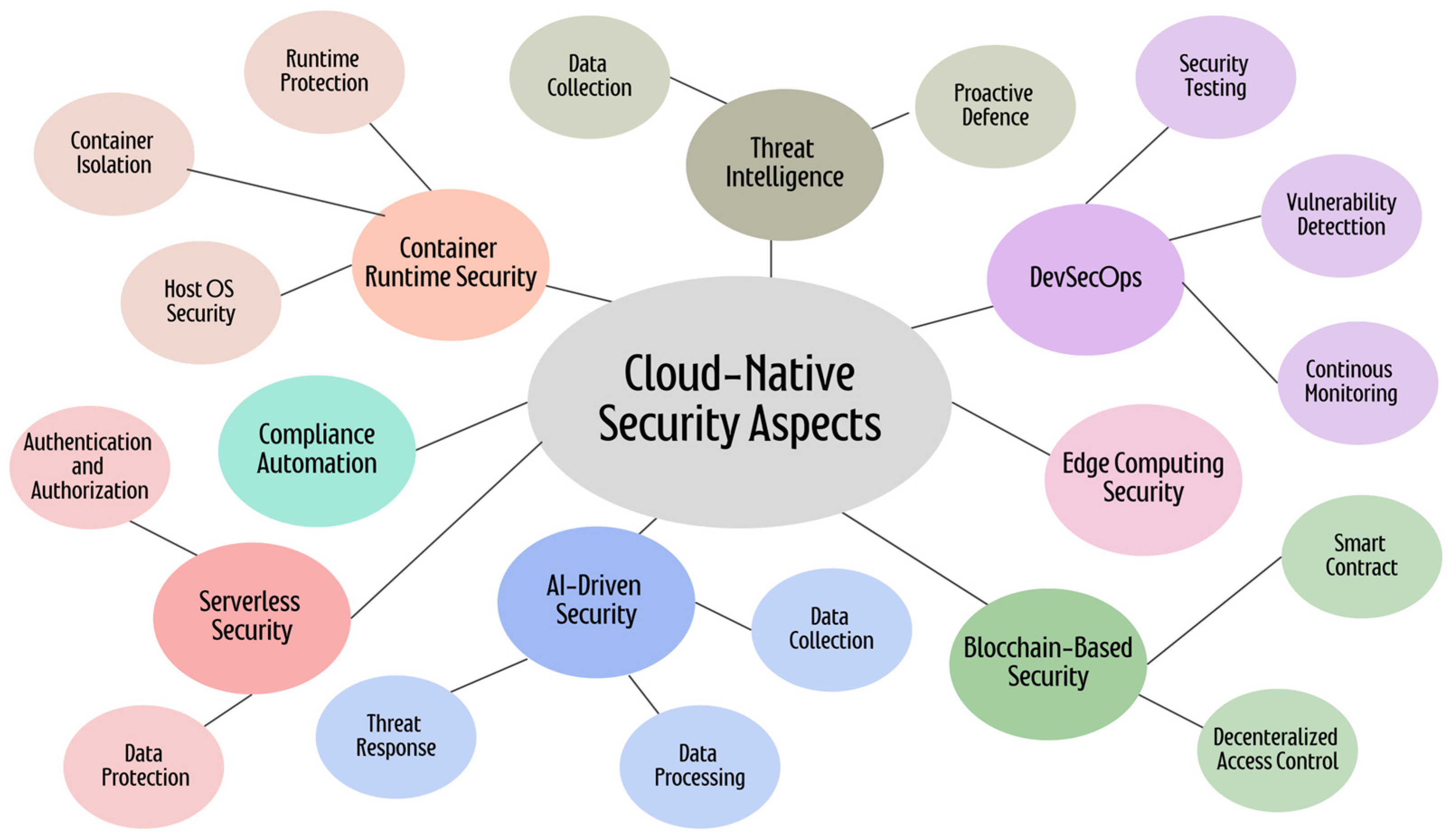
4.1. Overview of Security Techniques for Cloud-Native Applications
4.1.1. Service Mesh
4.1.2. Runtime Application Self-Protection (RASP)
4.1.3. Serverless Security
4.1.4. Security and Compliance Management
4.1.5. Immutable Infrastructure
4.1.6. DevSecOps Pipelines
4.1.7. Cloud-Native Identity and Access Management (IAM)
4.1.8. Container Image Scanning
4.1.9. Cloud-Native Encryption
4.1.10. Runtime Protection Platforms
4.1.11. Cloud-Native Endpoint Security
4.1.12. Cloud-Native Zero-Trust Security
4.1.13. Cloud-Native Security Information and Event Management (SIEM)
4.1.14. Cloud-Native Threat Intelligence Platforms
4.2. Comparative Analysis of Cloud-Native Security Techniques
4.3. Theoretical Justification of Security Techniques in Cloud-Native Environments
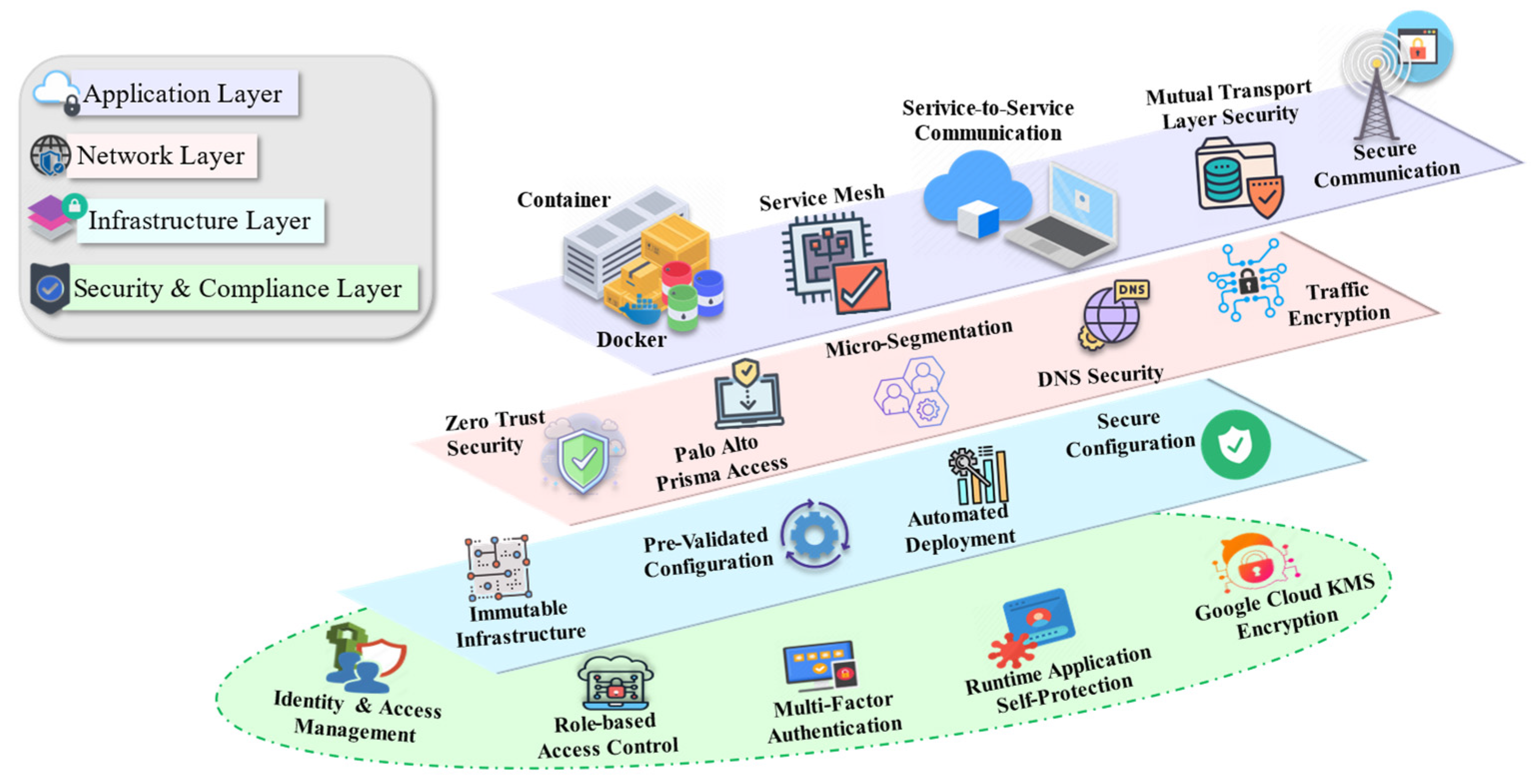
5. Case Scenario: Ensuring Security in Cloud-Native Applications
5.1. Application Layer
5.2. Network Layer
5.3. Infrastructure Layer
5.4. Security and Compliance Layer
6. Challenges and Solutions
6.1. Dynamic Nature of Cloud-Native Environments
6.2. Malware Detection
6.3. Unauthorized Access and Data Breaches
6.4. Decentralized Access Control
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mustyala, A. Migrating Legacy Systems to Cloud-Native Architectures for Enhanced Fraud Detection in Fintech. EPH-Int. J. Sci. Eng. 2023, 9, 16–26. [Google Scholar]
- Atieh, A.T. The next Generation Cloud Technologies: A Review on Distributed Cloud, Fog and Edge Computing and Their Opportunities and Challenges. Res. Rev. Sci. Technol. 2021, 1, 1–15. [Google Scholar]
- Russo, E.; Longo, G.; Guerar, M.; Merlo, A. Cloud-Native Application Security Training and Testing with Cyber Ranges. Lect. Notes Netw. Syst. 2023, 841, 205–216. [Google Scholar] [CrossRef]
- Alka, T.A.; Sreenivasan, A.; Suresh, M. Entrepreneurial Strategies for Sustainable Growth: A Deep Dive into Cloud-Native Technology and Its Applications. Futur. Bus. J. 2025, 11, 14. [Google Scholar] [CrossRef]
- Surianarayanan, C.; Chelliah, P.R. Demystifying the Cloud-Native Computing Paradigm. In International Conference on Ubiquitous Computing and Ambient Intelligence; Springer: Cham, Switzerland, 2023; pp. 321–345. [Google Scholar] [CrossRef]
- Chippagiri, S.; Ravula, P. Cloud-Native Development: Review of Best Practices and Frameworks for Scalable and Resilient Web Applications. Int. J. New Media Studie 2021, 8, 13–21. [Google Scholar]
- Vaño, R.; Lacalle, I.; Sowiński, P.; S-Julián, R.; Palau, C.E. Cloud-Native Workload Orchestration at the Edge: A Deployment Review and Future Directions. Sensors 2023, 23, 2215. [Google Scholar] [CrossRef]
- Perducat, C.; Mazur, D.C.; Mukai, W.; Sandler, S.N.; Anthony, M.J.; Mills, J.A. Evolution and Trends of Cloud on Industrial OT Networks. IEEE Open J. Ind. Appl. 2023, 4, 291–303. [Google Scholar]
- Khalel, M.M.; Pugazhendhi, M.A.; Raj, G.R. Enhanced Load Balancing in Kubernetes Cluster by Minikube. In Proceedings of the 2022 International Conference on Smart Technologies and Systems for Next Generation Computing (ICSTSN), Villupuram, India, 25–26 March 2022. [Google Scholar]
- Shan, C.; Xia, Y.; Zhan, Y.; Zhang, J. KubeAdaptor: A Docking Framework for Workflow Containerization on Kubernetes. Future Gener. Comput. Syst. 2023, 148, 584–599. [Google Scholar] [CrossRef]
- Nguyen, N.T.; Kim, Y. A Design of Resource Allocation Structure for Multi-Tenant Services in Kubernetes Cluster. In Proceedings of the 2022 27th Asia Pacific Conference on Communications (APCC), Jeju Island, Republic of Korea, 19–21 October 2022. [Google Scholar]
- Li, W. Algorithm Design for Kubernetes Load Saturation Scheduling in Deep Learning. In Proceedings of the 2023 IEEE 6th International Conference on Automation, Electronics and Electrical Engineering (AUTEEE), Shenyang, China, 15–17 December 2023. [Google Scholar]
- Giommi, L.; Spiga, D.; Paladino, M.; Kuznetsov, V.; Bonacorsi, D. Developments on the “Machine Learning as a Service for High Energy Physics” Framework and Related Cloud Native Solution. IEEE Trans. Cloud Comput. 2025, 13, 429–440. [Google Scholar]
- Roca, M.; Lee, C.B.; Pertiwi, A.P.; Blume, A.; Caballero, I.; Navarro, G.; Traganos, D.; Lee, B. Subtidal Seagrass and Blue Carbon Mapping at the Regional Scale: A Cloud-Native Multi-Temporal Earth Observation Approach. GIScience Remote Sens. 2024, 62, 2438838. [Google Scholar] [CrossRef]
- Xiong, K.; Wu, Z.; Jia, X. DeepContainer: A Deep Learning-Based Framework for Real-Time Anomaly Detection in Cloud-Native Container Environments. J. Adv. Comput. Syst. 2025, 5, 1–17. [Google Scholar] [CrossRef]
- Shin, D.; Kim, J.; Pawana, I.W.A.J.; You, I. Enhancing Cloud-Native DevSecOps: A Zero Trust Approach for the Financial Sector. Comput. Stand. Interfaces 2025, 93, 103975. [Google Scholar]
- Bharadwaj, D.; Premananda, B.S. Transition of Cloud Computing from Traditional Applications to the Cloud Native Approach. In Proceedings of the 2022 IEEE North Karnataka Subsection Flagship International Conference (NKCon), Vijaypur, India, 20–21 November 2022. [Google Scholar]
- Manavadariya, B.; Mangukiya, D. Cloud-Native System Administration: Principles, Practices, Challenges. Pract. Challenges 2024, 5, 2399–2412. [Google Scholar]
- Jiao, Q.; Xu, B.; Fan, Y. Design of Cloud Native Application Architecture Based on Kubernetes. In Proceedings of the 2021 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Calgary, AB, Canada, 25–28 October 2021. [Google Scholar]
- Shitta-Bey, A.; Adewole, M. Security Concerns of Cloud Migration and Its Implications on Cloud-Enabled Business Transformation. Ph.D. Thesis, Università della Svizzera Italiana, Lugano, Switzerland, 2023. [Google Scholar]
- Ahmadi, S. Zero Trust Architecture in Cloud Networks: Application, Challenges and Future Opportunities. J. Eng. Res. Rep. 2024, 26, 215–228. [Google Scholar] [CrossRef]
- Boudi, A.; Bagaa, M.; Poyhonen, P.; Taleb, T.; Flinck, H. AI-Based Resource Management in beyond 5G Cloud Native Environment. IEEE Netw. 2021, 35, 128–135. [Google Scholar] [CrossRef]
- Chen, C.; Ma, W.; Gao, C.; Zhang, W.; Zeng, K.; Ye, T.; Chen, Y.; Du, X. GaussDB-AISQL: A Composable Cloud-Native SQL System with AI Capabilities. Front. Comput. Sci. 2025, 19, 199608. [Google Scholar] [CrossRef]
- Taleb, T.; Benzaïd, C.; Addad, R.A.; Samdanis, K. AI/ML for beyond 5G Systems: Concepts, Technology Enablers & Solutions. Comput. Networks 2023, 237, 110044. [Google Scholar]
- Oyeniran, O.C.; Modupe, O.T.; Otitoola, A.A.; Abiona, O.O.; Adewusi, A.O.; Oladapo, O.J. A Comprehensive Review of Leveraging Cloud-Native Technologies for Scalability and Resilience in Software Development. Int. J. Sci. Res. Arch. 2024, 11, 330–337. [Google Scholar]
- Aris, A.; Levi, A.; Oz, H.; Selcuk, A.; Aris, A.; Uluagac, A.S.; Levi, A. A Survey on Ransomware: Evolution, Taxonomy, and Defense Solutions. ACM Comput. Surv. 2022, 54, 1–37. [Google Scholar] [CrossRef]
- Malik, V.; Khanna, A.; Sharma, N. Trends in Ransomware Attacks: Analysis and Future Predictions. Int. J. Glob. Innov. Solut. (IJGIS) 2024. [Google Scholar] [CrossRef]
- Lang, M.; Connolly, L.Y.; Taylor, P.; Corner, P.J. The Evolving Menace of Ransomware: A Comparative Analysis of Pre-Pandemic and Mid-Pandemic Attacks. Digit. Threat. Res. Pract. 2023, 4, 1–22. [Google Scholar] [CrossRef]
- Bundela, R.; Dhanda, N.; Gupta, K.K. Identification and Analysis of Security Issues in Cloud Computing. In Proceedings of the 2024 2nd International Conference on Disruptive Technologies (ICDT), Greater Noida, India, 15–16 March 2024. [Google Scholar]
- Theodoropoulos, T.; Rosa, L.; Benzaid, C.; Gray, P.; Marin, E.; Makris, A.; Cordeiro, L.; Diego, F.; Sorokin, P.; Girolamo, M.D.; et al. Security in Cloud-Native Services: A Survey. J. Cybersecur. Priv. 2023, 3, 758–793. [Google Scholar] [CrossRef]
- Rahaman, S.; Islam, A.; Cerny, T.; Hutton, S. Static-Analysis-Based Solutions to Security Challenges in Cloud-Native Systems: Systematic Mapping Study. Sensors 2023, 23, 1755. [Google Scholar] [CrossRef] [PubMed]
- Tatineni, S. AI-Infused Threat Detection and Incident Response in Cloud Security. Int. J. Sci. Research 2023, 12, 998–1004. [Google Scholar] [CrossRef]
- Barabanov, A.; Makrushin, D. Authentication and Authorization in Microservice-Based Systems: Survey of Architecture Patterns. arXiv 2020, arXiv:2009.02114. [Google Scholar] [CrossRef]
- Prakash, C. Zero-Trust Architecture Approach to Secure Microservices for the Healthcare Insurance Industry. Ph.D. Thesis, University of the Cumberlands, Williamsburg, KY, USA, 2024. [Google Scholar]
- Rangnau, T.; Buijtenen, R.V.; Fransen, F.; Turkmen, F. Continuous Security Testing: A Case Study on Integrating Dynamic Security Testing Tools in Ci/Cd Pipelines. In Proceedings of the 2020 IEEE 24th International Enterprise Distributed Object Computing Conference (EDOC), Eindhoven, The Netherlands, 5–8 October 2020; pp. 145–154. [Google Scholar] [CrossRef]
- Tatineni, S. Compliance and Audit Challenges in DevOps: A Security Perspective. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 5, 1306–1316. [Google Scholar]
- Continuous, F.; Klooster, T.; Turkmen, F.; Broenink, G.; Ten Hove, R.; Bohme, M. Continuous Fuzzing: A Study of the Effectiveness and Scalability of Fuzzing in CI/CD Pipelines. In Proceedings of the 2023 IEEE/ACM International Workshop on Search-Based and Fuzz Testing (SBFT), Melbourne, Australia, 14 May 2023; pp. 25–32. [Google Scholar] [CrossRef]
- Rangaraju, S.; Ness, S.; Dharmalingam, R. Incorporating Ai-Driven Strategies in Devsecops for Robust Cloud Security. Int. J. Innov. Sci. Res. Technol. 2023, 8, 2359–2365. [Google Scholar]
- Abiona, O.O.; Oladapo, O.J.; Modupe, O.T.; Oyeniran, O.C.; Adewusi, A.O.; Komolafe, A.M. The Emergence and Importance of DevSecOps: Integrating and Reviewing Security Practices Within the DevOps Pipeline. World J. Adv. Eng. Technol. Sci. 2024, 11, 127–133. [Google Scholar]
- Ugale, S.; Potgantwar, A. Container Security in Cloud Environments: A Comprehensive Analysis and Future Directions for DevSecOps. Eng. Proc. 2023, 59, 57. [Google Scholar] [CrossRef]
- Li, Y.; Hu, H.; Liu, W.; Yang, X. An Optimal Active Defensive Security Framework for the Container-Based Cloud with Deep Reinforcement Learning. Electronics 2023, 12, 1598. [Google Scholar] [CrossRef]
- Abbadini, M.; Beretta, M.; Facchinetti, D.; Oldani, G.; Rossi, M.; Paraboschi, S. Lightweight Cloud Application Sandboxing. In Proceedings of the 2023 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Naples, Italy, 4–6 December 2023. [Google Scholar]
- Beauchaine, A.; Shue, C.A. Toward a (Secure) Path of Least Resistance: An Examination of Usability Challenges in Secure Sandbox Systems. In Proceedings of the 2023 5th IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Atlanta, GA, USA, 1–4 November 2023. [Google Scholar]
- Shen, W.; Wu, Y.; Yang, Y.; Liu, Q.; Yang, N.; Li, J.; Lu, K.; Ma, J. Towards Understanding and Defeating Abstract Resource Attacks for Container Platforms. IEEE Trans. Dependable Secur. Comput. 2024, 22, 474–490. [Google Scholar]
- Nakata, Y.; Suzuki, S.; Matsubara, K. Reducing Attack Surface with Container Transplantation for Lightweight Sandboxing. In Proceedings of the 14th ACM SIGOPS Asia-Pacific Workshop on Systems, New York, NY, USA, 24–25 August 2023; pp. 58–64. [Google Scholar] [CrossRef]
- Ang’Udi, J.J. Security Challenges in Cloud Computing: A Comprehensive Analysis. World J. Adv. Eng. Technol. Sci. 2023, 10, 155–181. [Google Scholar] [CrossRef]
- Igwenagu, U.; Salami, A.A.; Arigbabu, A.S.; Esambe, M.C.; Oladoyinbo, T.O.; Olaniyi, O.O. Securing the Digital Frontier: Strategies for Cloud Computing Security, Database Protection, and Comprehensive Penetration Testing. Database Prot. Compr. Penetration Test. 2024. [Google Scholar] [CrossRef]
- Georgescu, T.M. A Study on How the Pandemic Changed the Cybersecurity Landscape. Inform. Econ. 2021, 25, 42–60. [Google Scholar]
- Yang, N.; Shen, W.; Li, J.; Liu, X.; Guo, X.; Ma, J. Take over the Whole Cluster: Attacking Kubernetes via Excessive Permissions of Third-Party Applications. In Proceedings of the CCS’23: Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 26–30 November 2023; pp. 3048–3062. [Google Scholar] [CrossRef]
- Cloud Native Computing Foundation. Available online: https://www.cncf.io/ (accessed on 26 March 2025).
- Kamieniarz, K.; Mazurczyk, W. A Comparative Study on the Security of Kubernetes Deployments. In Proceedings of the 2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 27–31 May 2024. [Google Scholar]
- Zeng, Q.; Kavousi, M.; Luo, Y.; Jin, L.; Chen, Y. Full-Stack Vulnerability Analysis of the Cloud-Native Platform. Comput. Secur. 2023, 129, 103173. [Google Scholar] [CrossRef]
- Feng, M.; Zhou, J.; Tang, Y. Enhancing Cloud-Native Security Through EBPF Technology. In Proceedings of the 2024 IEEE 11th International Conference on Cyber Security and Cloud Computing (CSCloud), Shanghai, China, 28–30 June 2024. [Google Scholar]
- Arif, H.; Kumar, A.; Fahad, M.; Hussain, H.K. Future Horizons: AI-Enhanced Threat Detection in Cloud Environments: Unveiling Opportunities for Research. Int. J. Multidiscip. Sci. Arts 2024, 3, 242–251. [Google Scholar]
- Dhayanidhi, G. Research on IoT Threats & Implementation of AI/ML to Address Emerging Cybersecurity Issues in IoT with Cloud Computing. Master’s Thesis, University of Alberta, Edmonton, Canada, 2022. [Google Scholar] [CrossRef]
- Xi, N.; Liu, J.; Li, Y.; Qin, B. Decentralized Access Control for Secure Microservices Cooperation with Blockchain. ISA Trans. 2023, 141, 44–51. [Google Scholar] [CrossRef] [PubMed]
- Cheng, C.; Yan, B.; Wang, G. The Blockchain Based Access Control Scheme for the Internet of Things. Procedia Comput. Sci. 2022, 202, 342–347. [Google Scholar]
- Wang, R.; Wang, X.; Yang, W.; Yuan, S.; Guan, Z. Achieving Fine-Grained and Flexible Access Control on Blockchain-Based Data Sharing for the Internet of Things. China Commun. 2022, 9, 22–34. [Google Scholar]
- Sun, S.; Chen, S.; Du, R. Trusted and Efficient Cross-Domain Access Control System Based on Blockchain. Scientific Programming 2020, 2020, 1–13. [Google Scholar] [CrossRef]
- Yang, C.; Tan, L.; Shi, N.; Xu, B.; Cao, Y.; Yu, K. AuthPrivacyChain: A Blockchain-Based Access Control Framework with Privacy Protection in Cloud. IEEE Access 2020, 8, 70604–70615. [Google Scholar]
- Schubert, M.A.; Pagel, S.; von Korflesch, H.F.O. Success Factors in Secure Software Development of Cloud Applications in Germany: A Qualitative-Explorative Expert Study. In Proceedings of the 56th Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2023; Volume 2023, pp. 6655–6664. [Google Scholar]
- Vakhula, O.; Kurii, Y.; Opirskyy, I.; Susukailo, V. Security-as-Code Concept for Fulfilling ISO/IEC 27001:2022 Requirements. In Proceedings of the Workshop on Cybersecurity Providing in Information and Telecommunication Systems (CPITS 2024), Kyiv, Ukraine, 28 February 2024; CEUR Workshop Proceedings. Volume 3659, pp. 59–71. [Google Scholar]
- Kumar, R.; Goyal, R. Modeling Continuous Security: A Conceptual Model for Automated DevSecOps Using Open-Source Software over Cloud (ADOC). Comput. Security 2020, 97, 101967. [Google Scholar]
- Kumar, R.; Goyal, R. When Security Meets Velocity: Modeling Continuous Security for Cloud Applications Using Devsecops. Lect. Notes Data Eng. Commun. Technol. 2021, 59, 415–432. [Google Scholar] [CrossRef]
- Dasher, G.; Envid, I.; Calder, B. Architectures for Protecting Cloud Data Planes. arXiv 2022, arXiv:2201.13010. [Google Scholar]
- Jararweh, Y. Enabling Efficient and Secure Energy Cloud Using Edge Computing and 5G. J. Parallel Distrib. Computing 2020, 145, 42–49. [Google Scholar]
- Ali, B.; Gregory, M.A.; Li, S. Multi-Access Edge Computing Architecture, Data Security and Privacy: A Review. IEEE Access 2021, 9, 18706–18721. [Google Scholar]
- Telang, T. Cloud-Native Application Development. In Beginning Cloud Native Development with MicroProfile, Jakarta EE, and Kubernetes; Apress: Berkeley, CA, USA, 2023; pp. 29–54. [Google Scholar] [CrossRef]
- Peng, K.; Zhao, B.; Bilal, M.; Xu, X.; Nayyar, A. QoS-Aware Cloud-Edge Collaborative Micro-Service Scheduling in the IIoT. HCIS 2023, 13, 28. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Benson, T.A. Kubeklone: A Digital Twin for Simulating Edge and Cloud Microservices. HCIS 2022, 13, 29–35. [Google Scholar] [CrossRef]
- Malawski, M.; Gajek, A.; Zima, A.; Balis, B.; Figiela, K. Serverless Execution of Scientific Workflows: Experiments with Hyperflow, Aws Lambda and Google Cloud Functions. Future Gener. Comput. Syst. 2020, 110, 502–514. [Google Scholar]
- Venugopal, M.V.L.N.; Reddy, C.R.K. Serverless through Cloud Native Architecture. Int. J. Eng. Res. Technol. 2021, 10, 484–496. [Google Scholar]
- Mao, Y.; Fu, Y.; Gu, S.; Vhaduri, S.; Cheng, L.; Liu, Q. Resource Management Schemes for Cloud-Native Platforms with Computing Containers of Docker and Kubernetes. Int. J. Eng. Res. Technol. 2020, 10, 484–496. [Google Scholar]
- Abernathey, R.P.; Augspurger, T.; Banihirwe, A.; Blackmon-Luca, C.C.; Crone, T.J.; Gentemann, C.L.; Hamman, J.J.; Henderson, N.; Lepore, C.; McCaie, T.A.; et al. Cloud-Native Repositories for Big Scientific Data. Comput. Sci. Eng. 2021, 23, 26–35. [Google Scholar]
- Olave, D. Towards Cloud-Native Context-Aware Autonomous Robotics for IoT Applications. Master’s Thesis, Luleå University of Technology, Department of Computer Science, Electrical and Space Engineering, Luleå, Sweden, October 2023; pp. 1–158. [Google Scholar]
- Kim, T.W.; Azzaoui, A.E.; Koh, B.; Kim, J.; Park, J.H. A Secret Sharing-Based Distributed Cloud System for Privacy Protection. Hum. Centric Comput. Inf. Sci. 2022, 12, 20. [Google Scholar] [CrossRef]
- Lim, J. Versatile Cloud Resource Scheduling Based on Artificial Intelligence in Cloud-Enabled Fog Computing Environments. Hum. Centric Comput. Inf. Sci. 2023, 13, 54. [Google Scholar] [CrossRef]
- Zheng, P.; Jiang, Z.; Wu, J.; Zheng, Z. Blockchain-Based Decentralized Application: A Survey. IEEE Open J. Comput. Soc. 2023, 4, 121–133. [Google Scholar]
- Kumar, R.; Gupta, S.; Wang, H.; Kumari, C.S.; Korlam, S.S.V.P. From Efficiency to Sustainability: Exploring the Potential of 6G for a Greener Future. Sustainability 2023, 15, 16387. [Google Scholar]
- Vinod, S.; Vimal, V.R.; Selvanayaki, S. Screen Recording and Sharing over the Cloud Platform For Remote Teams And Cross-Functional Teams. In Proceedings of the 2023 International Conference on Research Methodologies in Knowledge Management, Artificial Intelligence and Telecommunication Engineering (RMKMATE), Chennai, India, 1–2 November 2023. [Google Scholar]
- Shridhar, A.; Nadig, D. Heuristic-Based Resource Allocation for Cloud-Native Machine Learning Workloads. In Proceedings of the 2022 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Gujarat, India, 18–21 December 2022. [Google Scholar]
- Kosińska, J.; Baliś, B.; Konieczny, M.; Malawski, M.; Zieliński, S. Toward the Observability of Cloud-Native Applications: The Overview of the State-of-the-Art. IEEE Access 2023, 11, 73036–73052. [Google Scholar] [CrossRef]
- Gao, K.; Sun, C.; Wang, S.; Li, D.; Zhou, Y.; Liu, H.H.; Zhu, L.; Zhang, M.; Deng, X.; Zhou, C.; et al. Buffer-Based High-Coverage and Low-Overhead Request Event Monitoring in the Cloud. IEEE/ACM Trans. Netw. 2023, 31, 1732–1747. [Google Scholar]
- Kratzke, N. Cloud-Native Observability: The Many-Faceted Benefits of Structured and Unified Logging—A Multi-Case Study. Future Internet 2022, 14, 274. [Google Scholar]
- Sultan, M.; Rajaratnam, D.; Patel, K. Enterprise Architecture Approach to Build API Economy. In Proceedings of the 2022 International Conference on Computer Science and Software Engineering (CSASE), Duhok, Iraq, 15–17 March 2022. [Google Scholar]
- Al-Marsy, A.; Chaudhary, P.; Rodger, J.A. A Model for Examining Challenges and Opportunities in Use of Cloud Computing for Health Information Systems. Appl. Syst. Innov. 2021, 4, 15. [Google Scholar] [CrossRef]
- Cultrera, F. A Performance Analysis of Mesh Models for Cloud-Based Workflows. Master’s Thesis, University of Bologna, Bologna, Italy, 2022. [Google Scholar]
- Chernyshev, M.; Baig, Z.; Zeadally, S. Cloud-Native Application Security: Risks, Opportunities, and Challenges in Securing the Evolving Attack Surface. Computer 2021, 54, 47–57. [Google Scholar] [CrossRef]
- Christian, J.; Paulino, L.; de Sá, A.O. A Low-Cost and Cloud Native Solution for Security Orchestration, Automation, and Response. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2022; Volume 13620, pp. 115–139. [Google Scholar] [CrossRef]
- Sisto, S.P.R.; Borgogni, F.; Casciaro, L. Policy as Code, How to Automate Cloud Compliance Verification with Open-Source Tools. Ph.D. Thesis, Politecnico di Torino, Torino, Italy, 2023. [Google Scholar]
- Pandya, S.; Guha Thakurta, R. Hands-on Infrastructure as Code with Hashicorp Terraform. In Introduction to Infrastructure as Code; Apress: Berkeley, CA, USA, 2022; pp. 99–133. [Google Scholar] [CrossRef]
- Marie-Magdelaine, N. Observability and Resources Managements in Cloud-Native Environnements. Ph.D. Thesis, Université de Bordeaux, Bordeaux, France, 2021. [Google Scholar]
- Jeon, J.; Jeong, B.; Jeong, Y. PreVA: Predictive Vertical Autoscaler Using Multi Bi-GRU for Sustainable Cloud-Native Computing. Hum. Centric Comput. Inf. Sci. 2024, 14, 1–17. [Google Scholar]
- Chalishhafshejani, S.; Pham, B.; Jaatun, M. Automating Security in a Continuous Integration Pipeline. In Proceedings of the 7th International Conference on Internet of Things, Big Data and Security, Online, 22–24 April 2022. [Google Scholar] [CrossRef]
- Sankaran, A.; Datta, P.; Bates, A. Workflow Integration Alleviates Identity and Access Management in Serverless Computing. In Proceedings of the ACSAC’20: Proceedings of the 36th Annual Computer Security Applications Conference, New York, NY, USA, 7–11 December 2020; pp. 496–509. [Google Scholar] [CrossRef]
- Talluri, S. Saviynt Meets GCP: A Deep Dive into Integrated IAM for Modern Cloud Security. J. Inf. Secur. 2024, 15, 1–14. [Google Scholar] [CrossRef]
- Berkovich, S.; Kam, J.; Wurster, G. {UBCIS}: Ultimate Benchmark for Container Image Scanning. In Proceedings of the 13th USENIX Workshop on Cyber Security Experimentation and Test (CSET 20), Boston, MA, USA, 10 August 2020. [Google Scholar]
- Subramaniam, K. Cloud Network Security: A Survey on Threats, Existing Solutions and the Path Forward; School of Computing and Augmented Intelligence, Arizona State University: Tempe, AZ, USA, 2022; pp. 1–7. [Google Scholar]
- Kumar, M.; Jeni, V. Web Application Security on Top of Public Cloud. In Proceedings of the 022 Second International Conference on Interdisciplinary Cyber Physical Systems (ICPS), Chennai, India, 9–10 May 2022. [Google Scholar]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image Privacy Protection Scheme Based on High-Quality Reconstruction DCT Compression and Nonlinear Dynamics. Expert Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
- Yang, B.; Zhang, F.; Khan, S.U. An Encryption-as-a-Service Architecture on Cloud Native Platform. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021. [Google Scholar]
- German, K.; Ponomareva, O. An Overview of Container Security in a Kubernetes Cluster. In Proceedings of the 2023 IEEE Ural-Siberian Conference on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 15–17 May 2023. [Google Scholar]
- Kamruzzaman, A.; Ismat, S.; Brickley, J.C.; Liu, A.; Thakur, K. A Comprehensive Review of Endpoint Security: Threats and Defenses. In Proceedings of the 2022 International Conference on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, 7–8 December 2022. [Google Scholar]
- Kanerva, S. Lateral Movement Restriction in Advanced DevOps Environments. Master’s Thesis, Aalto University School of Business, Espoo, Finland, 2024. [Google Scholar]
- Henriques, J.; Caldeira, F.; Cruz, T.; Simões, P. A Survey on Forensics and Compliance Auditing for Critical Infrastructure Protection. IEEE Access 2024, 12, 2409–2444. [Google Scholar] [CrossRef]
- Arif, T.; Jo, B.; Kang, J.; Park, J.H. Blockchain-Enabled IDPS and Federated Learning for Enhancing CPS Security Against Advanced Persistent Threats in Zero Trust Architectures. Hum. Centric Comput. Inf. Sci. 2025, 15, 22. [Google Scholar] [CrossRef]
- Ammi, M.; Adedugbe, O.; Alharby, F.M.; Benkhelifa, E. Leveraging a Cloud-Native Architecture to Enable Semantic Interconnectedness of Data for Cyber Threat Intelligence. Clust. Comput. 2022, 25, 3629–3640. [Google Scholar] [CrossRef]
- Nour, B.; Pourzandi, M.; Debbabi, M. A Survey on Threat Hunting in Enterprise Networks. IEEE Commun. Surv. Tutorials 2023, 25, 2299–2324. [Google Scholar] [CrossRef]
| Authors | Focus Area | Issues | Description | Tools and Techniques |
|---|---|---|---|---|
| [31] | The dynamic nature of cloud-native security | Addressing swift alterations in containerized architectures | Examined how dynamic cloud-native settings affect security, with a focus on adaptable security measures. | Modular threat modeling and adaptable security measures |
| [33] | Microservice architecture’s effects on security | Reducing risks related to decentralized patterns and illegal access | Examined how microservice designs in cloud-native contexts affect security. | Decentralized access control systems with robust authentication techniques |
| [35,36] | DevSecOps pipelines | Fostering a development strategy that prioritizes security | Explored how DevSecOps pipelines may automate security testing along the software development lifecycle. | Vulnerability scanning and automated security testing |
| [38] | Leveraging threat intelligence | Overcoming obstacles in the proactive defense against cyberattacks | Investigated integrating cloud-native threat intelligence systems with pipelines for DevSecOps. | Threat data collection and evaluation |
| [40] | Runtime security for containers | Preventing runtime errors in programs that are containerized | Examined the difficulties in protecting containerized applications from runtime vulnerabilities. | Isolating containers and reducing host OS vulnerabilities |
| [42] | Enhanced runtime security | Securing cloud-native environments by implementing policies into place | Investigated the application of sandboxing and sophisticated runtime security measures in cloud-native environments. | Techniques for sandboxing and runtime protection |
| [46] | Automation of compliance | Ensuring adherence to the CCPA, GDPR, and other privacy laws | Examined the difficulties in ensuring that cloud-native applications comply with privacy laws and regulations. | Access control methods and data encryption |
| [54] | AI-based security solutions | Overcoming obstacles in cloud-native environments related to cyber threat detection and mitigation | Explored the possibilities for identifying and reducing risks in cloud-native environments using AI-driven security solutions. | Security telemetry analysis and machine learning techniques |
| [55] | AI-based security solutions | Overcoming obstacles to effectively utilizing AI for threat detection and mitigation | Explored the possibilities of AI-driven security solutions, with an emphasis on threat identification and mitigation, for cloud-native IoT environments. | Threat detection and mitigation using machine learning techniques |
| [56] | Blockchain-driven security | Addressing single points of failure and preventing illegal access | A decentralized access control mechanism that uses blockchain technology in microservice architectures is proposed. | Blockchain-driven system for access control |
| [61] | Observance of legal requirements | Ensuring compliance with best practices and regulatory standards | Addressed how to match established frameworks, such as the NIST Cybersecurity Framework, with cloud-native security concepts. | Combining compliance requirements with security controls |
| [63,64] | DevSecOps procedures and culture | Addressing issues with ongoing security maintenance across the software development lifecycle | Discovered how to include security procedures in DevOps processes while valuing teamwork. | Collaboration between teams and integration of DevSecOps |
| [65] | Serverless architecture security considerations | Overcoming obstacles of putting strong authentication and data security measures in place in serverless applications | Examined serverless architecture security issues, focusing on data protection and authentication techniques. | Data protection and authentication procedures |
| [66] | Edge computing security issues | Addressing issues with data transmission and edge device security in decentralized infrastructures | Examined edge computing infrastructures’ best practices and security issues. | Security of edge devices, data transfer, and application deployment |
| [67] | Edge computing security concerns | Keeping decentralized edge infrastructures secure | Examined edge computing environments’ security problems and recommendations, with a focus on protecting edge devices and data transit. | Security of edge devices and data transfer |
| Applications | Objective | Technologies Used | Benefits |
|---|---|---|---|
| Web applications | Provide high-availability, accessible, and scalable applications via web browsers | High-availability configurations, cloud infrastructure deployment, and dynamic scaling | Improved user experience, global accessibility, and cost efficiency. |
| Microservice-based applications | Allow application components to be developed, deployed, and scaled independently | APIs for communication, decentralized architecture, and small, independent services | Enhanced fault isolation, faster time-to-market, and improved agility. |
| Containerized applications | Ensure that deployment environments are consistent and isolated | Encapsulating dependencies, Kubernetes for orchestration, and Docker for containerization | Ease of deployment, enhanced resource utilization, and consistent behavior across environments. |
| Serverless applications | Abstract server administration to enable business logic-focused development | Event-driven execution, Google Cloud Functions, AWS Lambda, and Azure Functions | Faster development cycles, costly effective, automatic scaling. |
| IoT (Internet of Things) applications | Gather, handle, and evaluate data from linked devices. | Sensor integration, cloud-based analytics frameworks, and real-time data processing | Enhanced operational efficiency, improved decision-making, and real-time insights. |
| Big data and analytics applications | Process and examine huge datasets to find insights | Cloud storage possibilities, Google BigQuery, Apache Spark, and Hadoop | Advances in scientific research, corporate intelligence, and informed decision-making. |
| Real-time messaging and collaboration applications | Facilitate immediate collaboration and communication. | Low-latency networks, cloud-native communications protocols, and real-time data synchronization | Improved user interaction, enhanced remote collaboration, and seamless communication. |
| Blockchain-based applications | Enhance security and transparency while hosting decentralized applications | Decentralized ledgers, cloud-hosted nodes, and blockchain frameworks | Improved trust, secure transactions, and decentralized control. |
| AI and machine learning applications | Enable large-scale data processing and advanced computations for AI models | Cloud-based platforms with GPUs and TPUs, machine learning frameworks, and scalable computing resources | Rapid creation of AI models, scalable computing, and customized user interfaces. |
| Monitoring and observability applications | Assure cloud-native applications reliability and efficiency | Grafana for visualization, Elasticsearch for logging, and Prometheus for monitoring | Enhanced system health, proactive issue resolution, and optimized performance. |
| Healthcare and telemedicine applications | Improving patient care and enabling remote health services | Secure data storage, real-time communication tools, and cloud-based EHR systems | Improved patient care, compliance with health laws, and remote diagnosis. |
| API management platforms | Make API design, administration, and security easier | Kong, AWS API Gateway, Apigee, and access control methods | Speedy application development, secure data transfer, and improved API governance. |
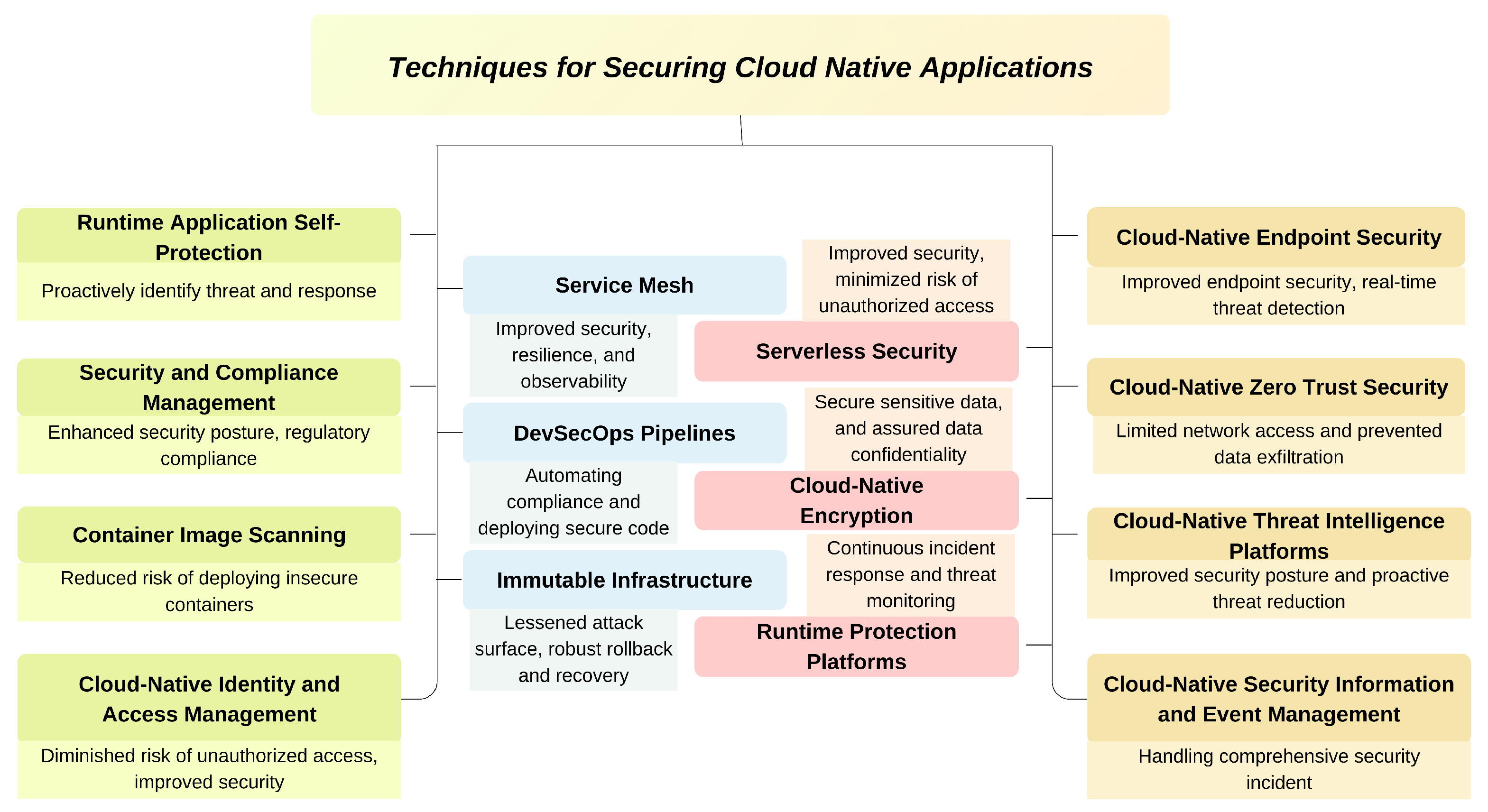
| Tool and Technique | Purpose | Key Features | Implementation Method | Impact |
|---|---|---|---|---|
| Service mesh | Handle service-to-service communication | Traffic management, observability, mTLS encryption. | Istio, Linkerd, Consul Linkerd, Istio, and Consul | Improved security, resilience, and observability |
| Runtime application self-protection | Monitor real-time application security | Anomaly detection, vulnerability scanning, behavioral analysis. | Trivy Aqua Security, Sysdig Secure | Proactively identify threats and response |
| Serverless security | Protected serverless environments | Runtime monitoring, access control, and function isolation. | Azure Functions Proxies, AWS Lambda Layers | Improved security, minimized risk of unauthorized access |
| Security and compliance management | Centralized compliance handling and security | Threat detection, compliance reporting, and network segmentation. | Palo Alto Networks Prisma Cloud, Aqua CSPM | Enhanced security posture, regulatory compliance |
| Immutable infrastructure | Assure consistency and protected infrastructure | Automated provisioning, configuration management, IaC templates. | AWS CloudFormation, HashiCorp Terraform | Lessened attack surface, robust rollback, and recovery |
| DevSecOps pipelines | Secure the CI/CD pipeline by integration. | Compliance checks, automated security testing, vulnerability scanning. | SonarQube, GitLab Secure, and Snyk | Automating compliance and deploying secure code |
| Cloud-native IAM | Handle identities and access controls | Identity federation, MFA, and granular access control | Google Cloud IAM and AWS IAM | Diminished risk of unauthorized access, improved security |
| Container image scanning | Determine which container images are vulnerable. | Integration with CI/CD, compliance scanning, and vulnerability detection. | Anchore Engine, Clair, Docker Security Scanning | Reduced risk of deploying insecure containers |
| Cloud-native encryption | Secure data both in transit and at rest. | Key management, encryption techniques, and cloud service integration | HashiCorp Vault, Google Cloud KMS, and AWS KMS | Secure sensitive data, and assure data confidentiality |
| Runtime protection platforms | Monitor real-time security and response | Workload protection, visibility, container runtime security, and analytics | Sysdig Secure and Aqua Security | Continuous incident response and threat monitoring |
| Cloud-native endpoint security | Secure endpoints and devices | Threat hunting, advanced prevention capabilities, and EDR | Carbon Black Cloud, CrowdStrike Falcon | Improved endpoint security, real-time threat detection |
| Cloud-native zero-trust Security | Protect network traffic and communications | Traffic inspection, threat prevention, network segmentation, | Cisco Umbrella and Palo Alto Networks Prisma Access | Limited network access and prevented data exfiltration |
| Cloud-native SIEM | Centralized security incident tracking and analysis | Automation of incident response, log aggregation, and real-time event correlation. | IBM QRadar, Splunk Enterprise Security, and LogRhythm | Handling comprehensive security incident |
| Cloud-native threat intelligence platforms | Proactively protect against cyber attacks | Collaboration, threat data aggregation, threat analysis, and prioritization. | Recorded Future, Anomali, and ThreatConnect | Improved security posture and proactive threat reduction |
| Techniques | Performance Impact | Scalability | Ease of Integration | Trade-Offs |
|---|---|---|---|---|
| Service mesh (Istio, Linkerd) | Medium (proxy overhead) | High | Moderate | Great for network control but adds latency |
| Runtime protection (Sysdig) | Low | High | High | Lightweight, strong at runtime, easy to integrate |
| IAM (AWS IAM, Google IAM) | Low | Medium | High | Seamless for cloud-native, but limited across clouds |
| AI/threat detection (SIEM) | High | High | Moderate | Requires computing power and telemetry integration |
| DevSecOps pipelines | Low–medium | High | Moderate–high | High automation but setup complexity |
| Image scanning tools | Low | Medium | High | Best in CI/CD; not effective for runtime threats |
| Concerns | Restrictions and Limitations | Challenges and Issues | Solutions |
|---|---|---|---|
| Security issues | Because cloud-native settings are dynamic, it can be difficult to maintain security and stability. | Handling sensitive data, adhering to privacy rules, and scalability issues are examples of security hazards. | Creation of cutting-edge security solutions that make use of AI/ML, improved malware detection methods, and strengthened container runtime security. |
| Malware identification | Sophisticated malware created for containerized applications may be undetectable to traditional detection methods. | Cybercriminals can harm the entire system by taking advantage of flaws in the host OS kernels. | Deployment of advanced detection methods for successful threat mitigation, such as anomaly detection algorithms and behavior-based analysis. |
| Access management | Unauthorized access and data breaches can result from insufficient access control measures. | To avoid security breaches, inter-container communications must be secured. | Enhancing access control measures and creating decentralized systems to lower the possibility of unwanted access and single points of failure. |
| Examining conditions | It is difficult to build realistic testbeds for assessing security systems in environments based on microservices. | Errors in security measures could be caused by improper testing conditions. | Creation of sophisticated testing frameworks and modeling tools to precisely replicate cloud-native settings in the real world. |
| Scalability consequences | Although scalability has advantages, it also brings security risks that should be carefully considered. | Runtime vulnerabilities could arise from cloud-native environments’ dynamic nature. | To lessen the effect of DDoS assaults on cloud containers, scalable DDoS mitigation technologies, improved container runtime security, and preventive measures should be implemented. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Arif, T.; Jo, B.; Park, J.H. A Comprehensive Survey of Privacy-Enhancing and Trust-Centric Cloud-Native Security Techniques Against Cyber Threats. Sensors 2025, 25, 2350. https://doi.org/10.3390/s25082350
Arif T, Jo B, Park JH. A Comprehensive Survey of Privacy-Enhancing and Trust-Centric Cloud-Native Security Techniques Against Cyber Threats. Sensors. 2025; 25(8):2350. https://doi.org/10.3390/s25082350
Chicago/Turabian StyleArif, Tuba, Byunghyun Jo, and Jong Hyuk Park. 2025. "A Comprehensive Survey of Privacy-Enhancing and Trust-Centric Cloud-Native Security Techniques Against Cyber Threats" Sensors 25, no. 8: 2350. https://doi.org/10.3390/s25082350
APA StyleArif, T., Jo, B., & Park, J. H. (2025). A Comprehensive Survey of Privacy-Enhancing and Trust-Centric Cloud-Native Security Techniques Against Cyber Threats. Sensors, 25(8), 2350. https://doi.org/10.3390/s25082350




_Park.png)


