Hardware Acceleration-Based Privacy-Aware Authentication Scheme for Internet of Vehicles Using Physical Unclonable Function
Abstract
1. Introduction
2. Related Work
3. System Model and Design Goals
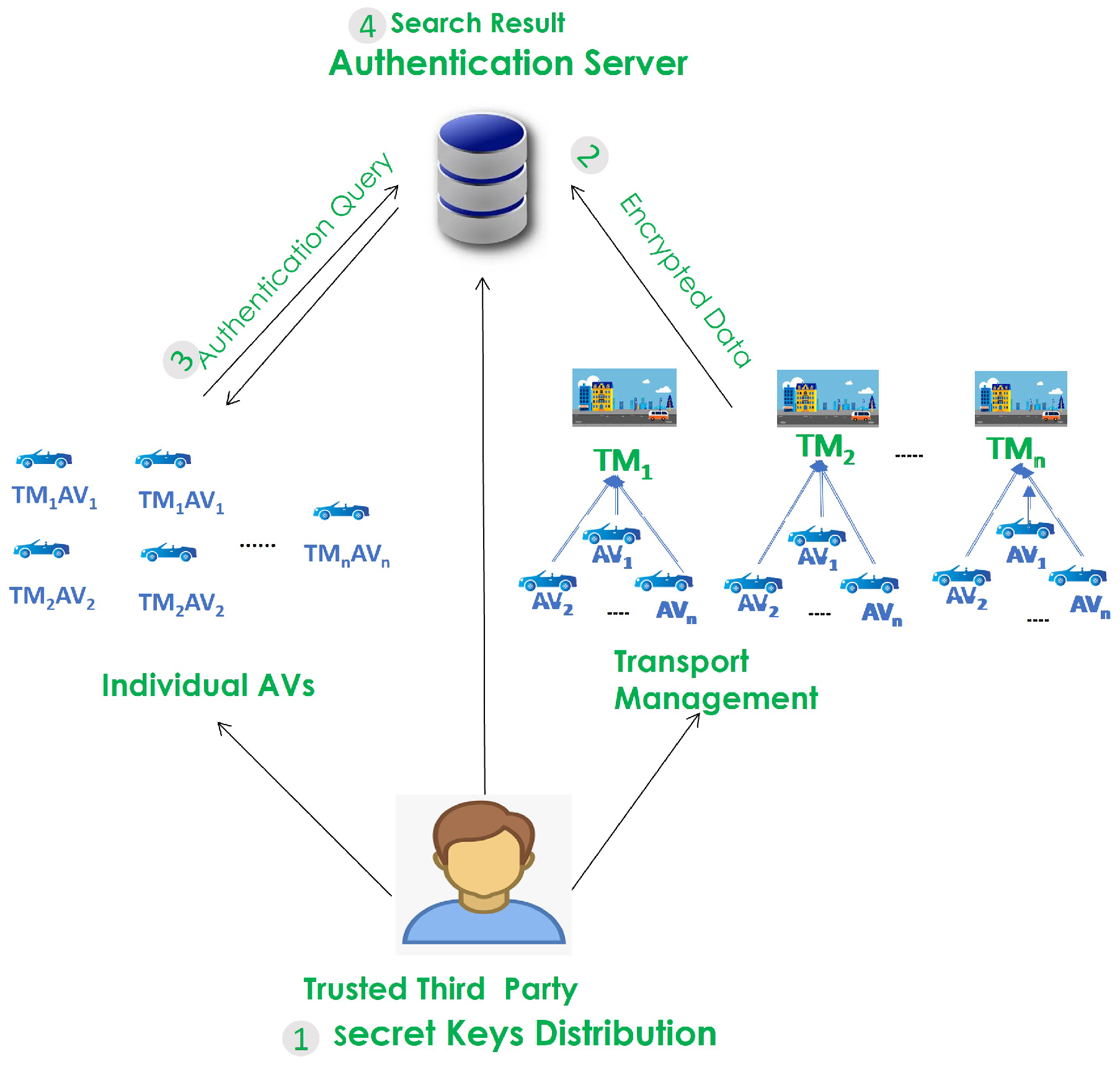
3.1. Network Model
3.2. Threat Model
3.3. Design Goals
- Scalability and efficiency: The lightweight and effective execution of encryption and search operations is crucial. This reduces energy and computational costs associated with data access and processing. Simultaneously, it allows authorized individuals to access the required information securely. Moreover, it streamlines the encryption and searching of data with varying volumes and structures, ensuring adaptability to different data sizes and scenarios.
- Authentication query search over encrypted AVs’ IDs from several TMs: Our method should be able to utilize the encrypted authentication requests from AVs to explore the encrypted ID data transmitted via various participating TMs. Each AV should use only one key to encrypt its authentication request, and it can still be matched with all indices submitted via all TMs to achieve a multi-multi searching property.
- AVs’ ID data and authentication query confidentiality: the AS must refrain from obtaining sensitive or crucial information related to the stored AV’s ID data or the authentication queries/requests.
- Authentication query unlinkability: the AS should be unable to ascertain whether two authentication requests include identical or distinct identification data.
- Distinct key generation: the TTP must be capable of generating unique keys for distribution to all scheme members, ensuring that they cannot be duplicated or repeated.
4. Proposed Authentication Scheme
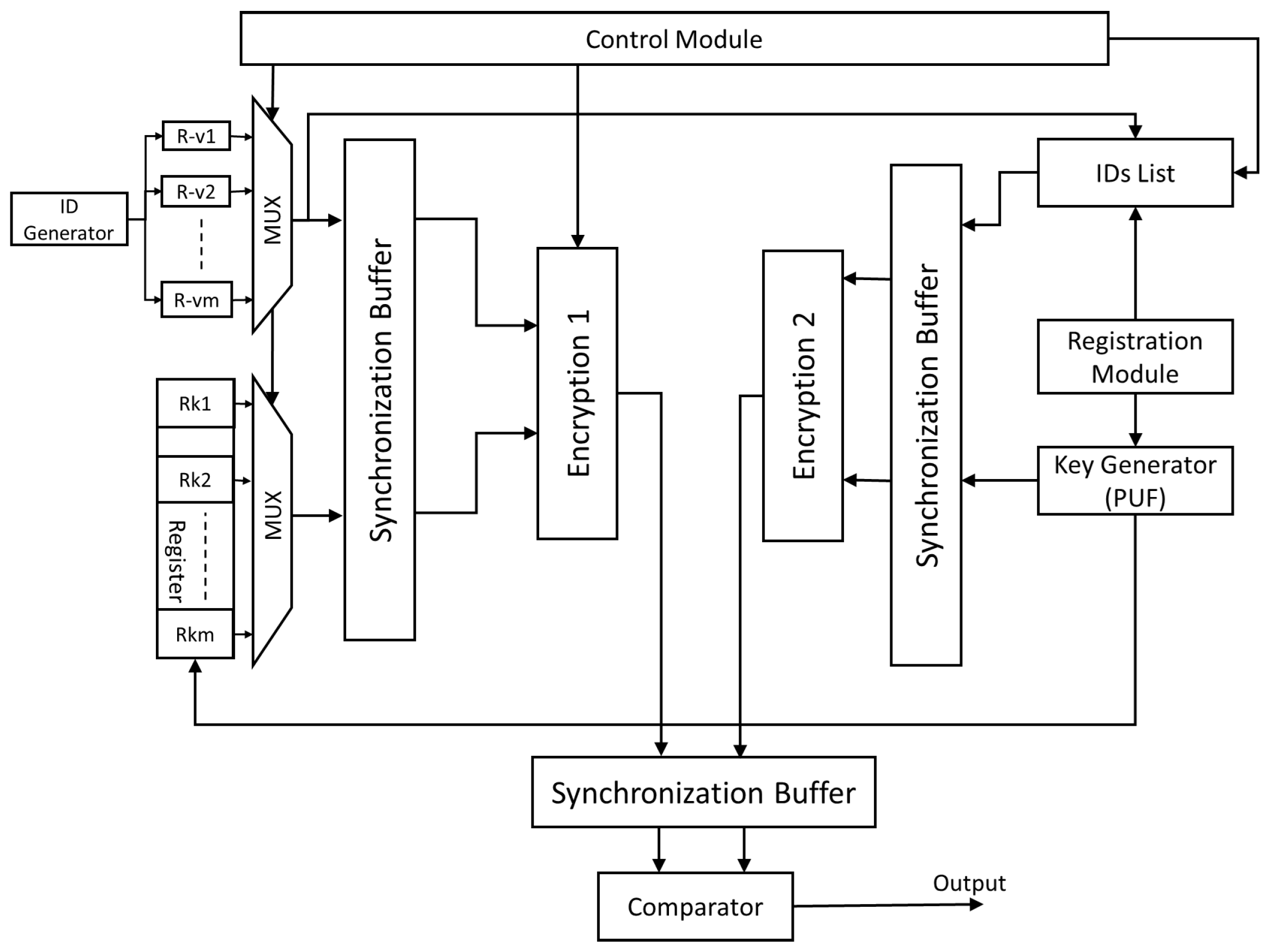
4.1. Key Generation
4.2. Key Distribution
- System Setup: The system setup algorithm takes the security parameter as an input and outputs the TTP secret key (TTPK), where TTPK = {B, , , , …, and }, B is a random binary vector of size n, and , , , , and are n*n invertible random matrices, and n is the size of the AV identification size.
- KeyGenCloud: The TTP creates the authentication server secret key (ASK), where ASK = A, A is an invertible random matrix .
- KeyGenTM: For transport management i with ID (), the TTP creates its secret key () as = {B, , , , , , , , }, where {, , , and } are random matrices , such that + = , and + = .
- KeyGenAV: For autonomous vehicle x with ID (), the TTP creates its secret key () as ={B, , , , , , , , }, where {, , , and } are random matrices , such that + = , and + = .
4.3. Encrypting an AV’s ID Data
4.4. Submitting Authentication Query
4.5. Matching Encrypted Data
5. Security and Privacy Analysis
- Scalability and efficiency. The proposed method efficiently searches encrypted IDs from multiple sources and promptly responds to requests from the AVs. This is achieved through a dot product operation using the relevant encrypted IDs and leveraging hardware acceleration. Additionally, the computational burden in our technique is relatively manageable.
- Authentication query search over encrypted AVs’ IDs from several TMs. The proposed method utilizes encrypted authentication queries sent from an AV to the AS to perform searches on encrypted ID data from various participating TM entities. Our approach eliminates the need for AVs to share a key with each TM for searching its encrypted AVs’ identification data. The AVs can efficiently use the same key obtained from the TTP to search all ID data from all the involved TMs.
- AVs’ ID data and authentication query confidentiality. The AS is barred from accessing any potentially sensitive or valuable information regarding stored ID data or issued authentication queries. This is accomplished through encryption via both the AV and TMs. This encryption ensures the confidentiality of IDs and authentication queries, preventing data transmission to the AS in plaintext. Data privacy is heightened, as the server does not decrypt the data, and the AS only conducts searches within the encrypted data.
- Authentication query unlinkability. The AS cannot ascertain whether two authentication requests contain similar data. Our technique ensures the preservation of authentication query unlinkability by generating alternative ciphertexts when the same AV ID is sent out through random vector splitting during the authentication query process.
- Distinct key generation. Our scheme demonstrates that the PUF generates a unique random key during the process of creating singular keys for distribution, guaranteeing that they are non-duplicable and non-repetitive.
6. Implementation and Experimental Results
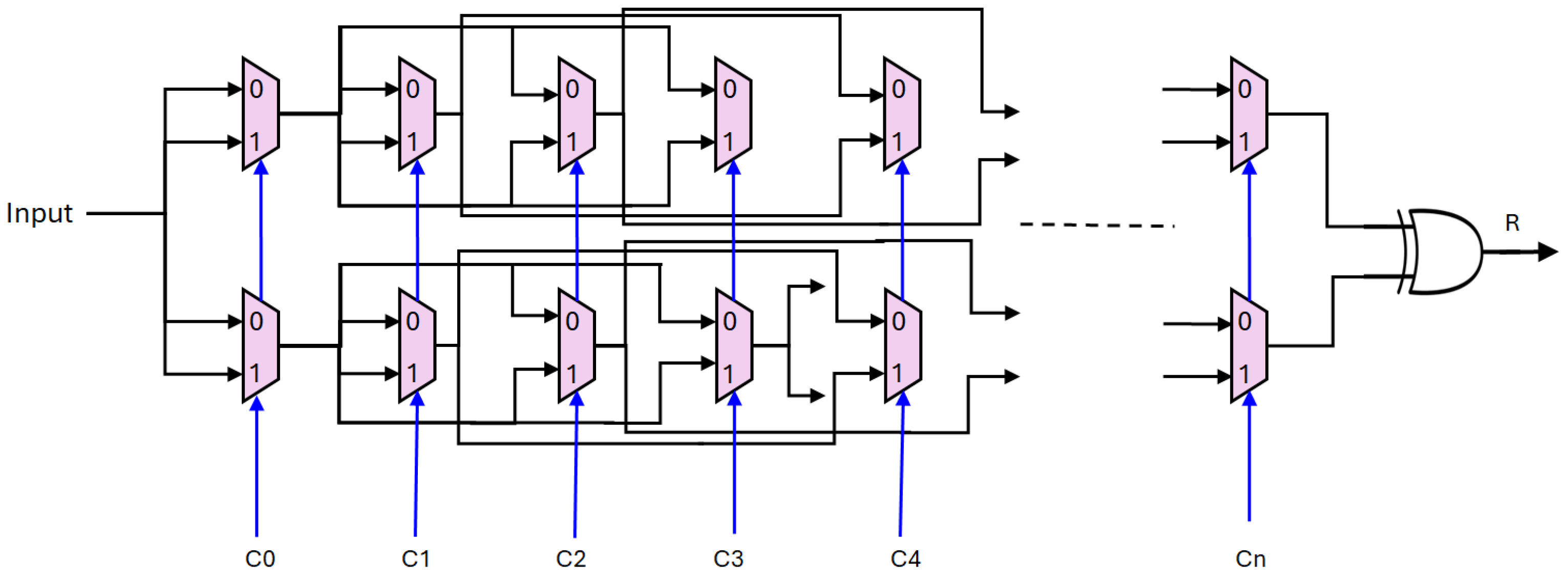
6.1. Hardware Architecture
6.2. Experimental Results
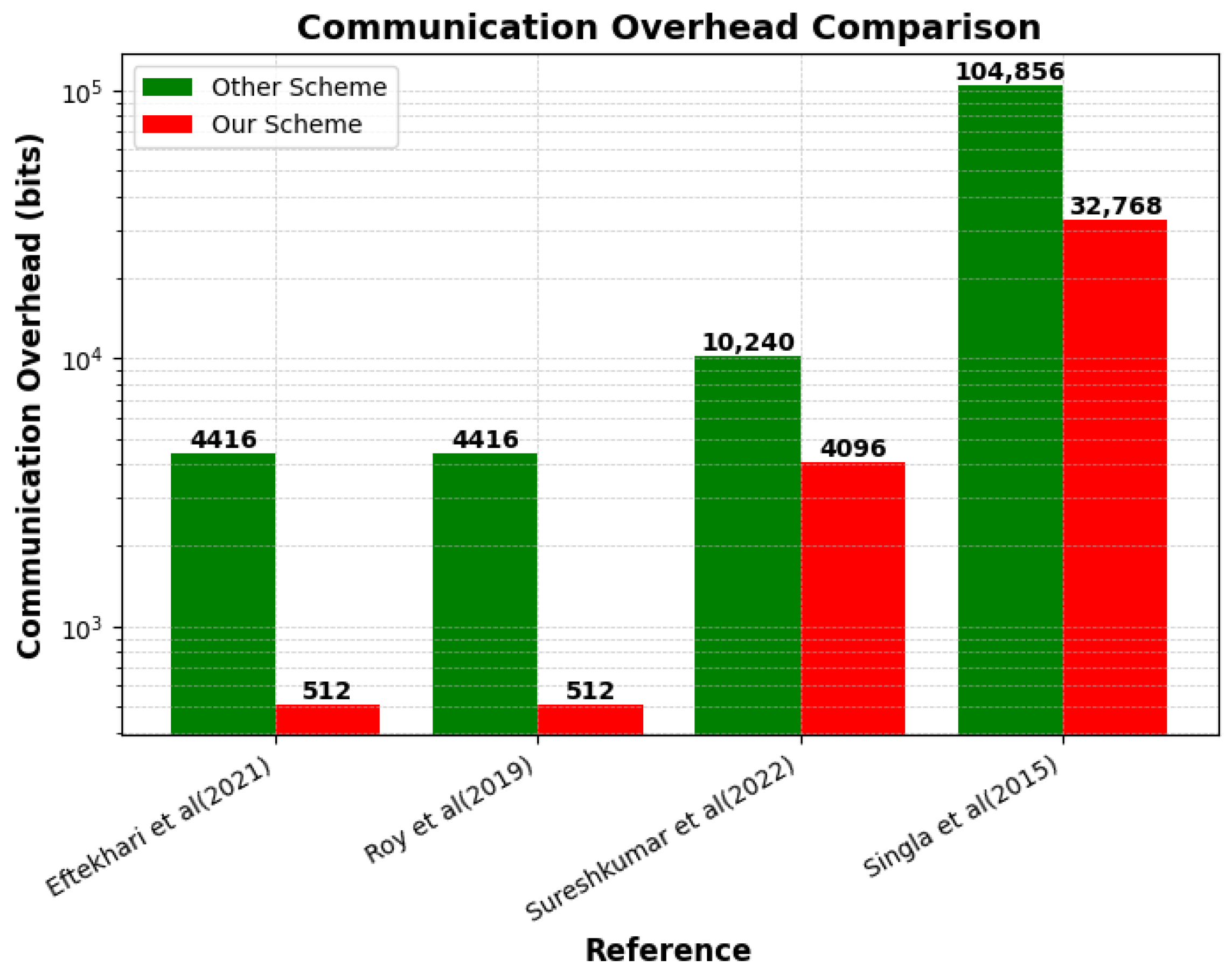
6.2.1. Communication Overhead
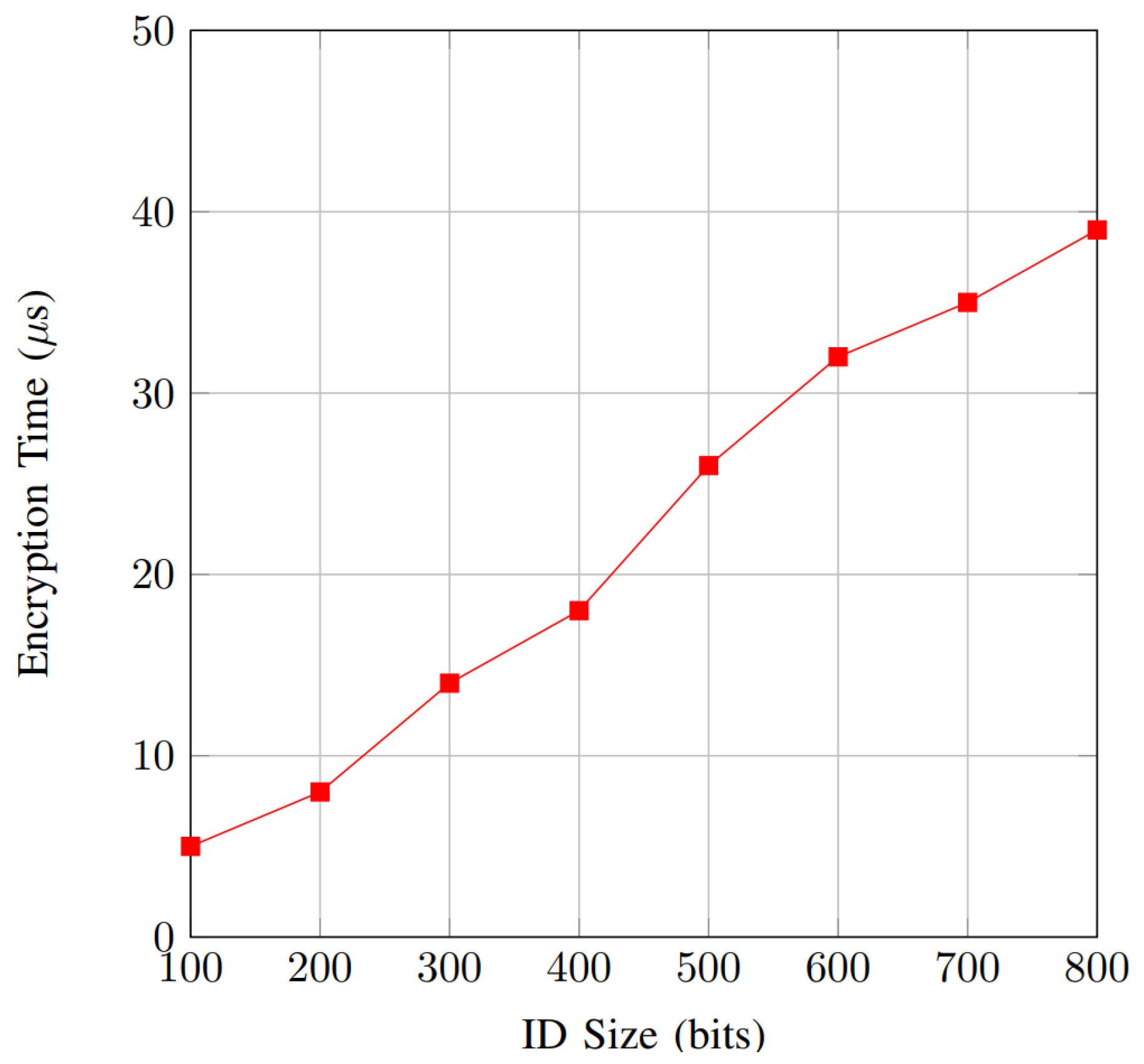
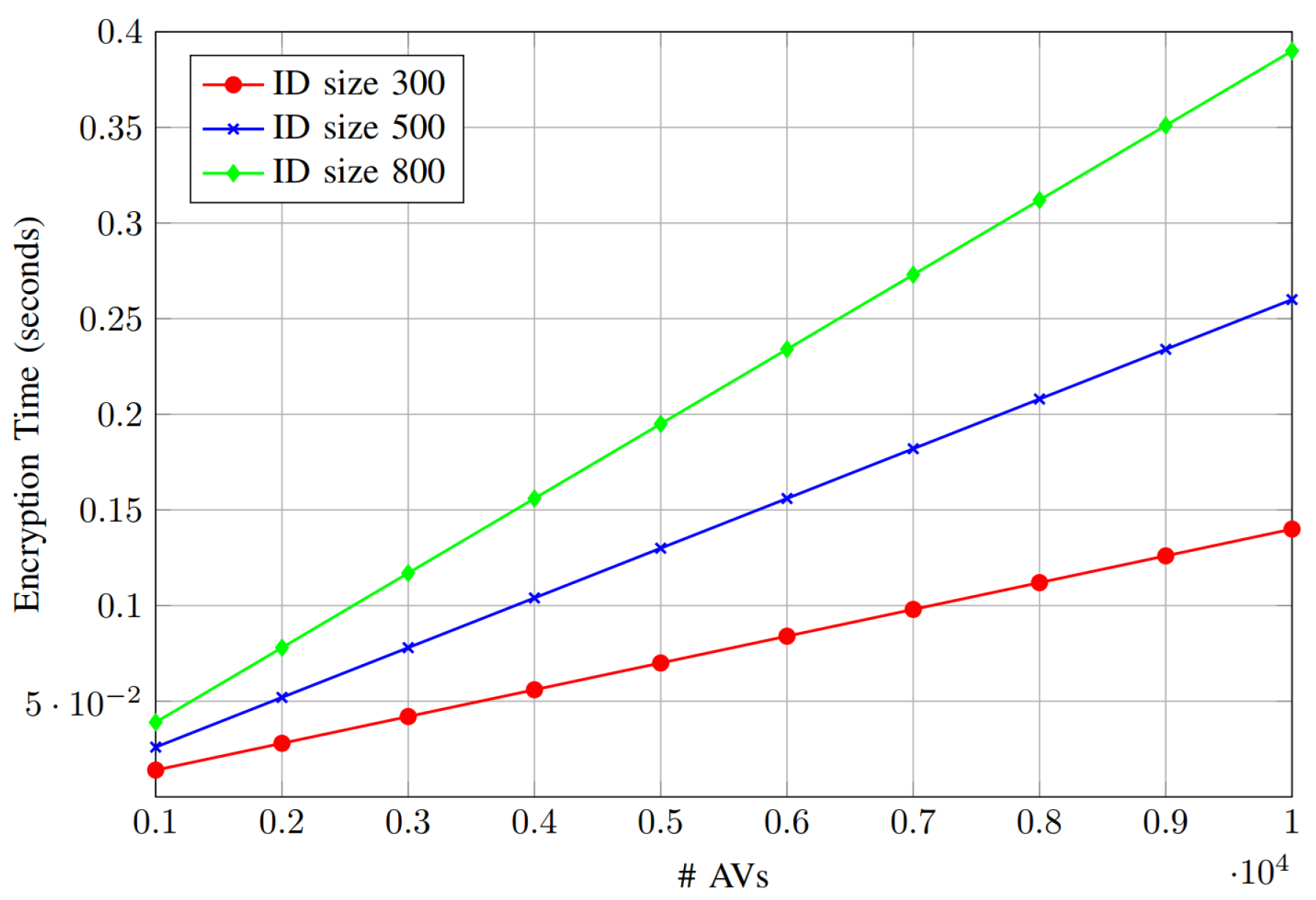
6.2.2. Computation Overhead
6.2.3. Hardware Resource Utilization
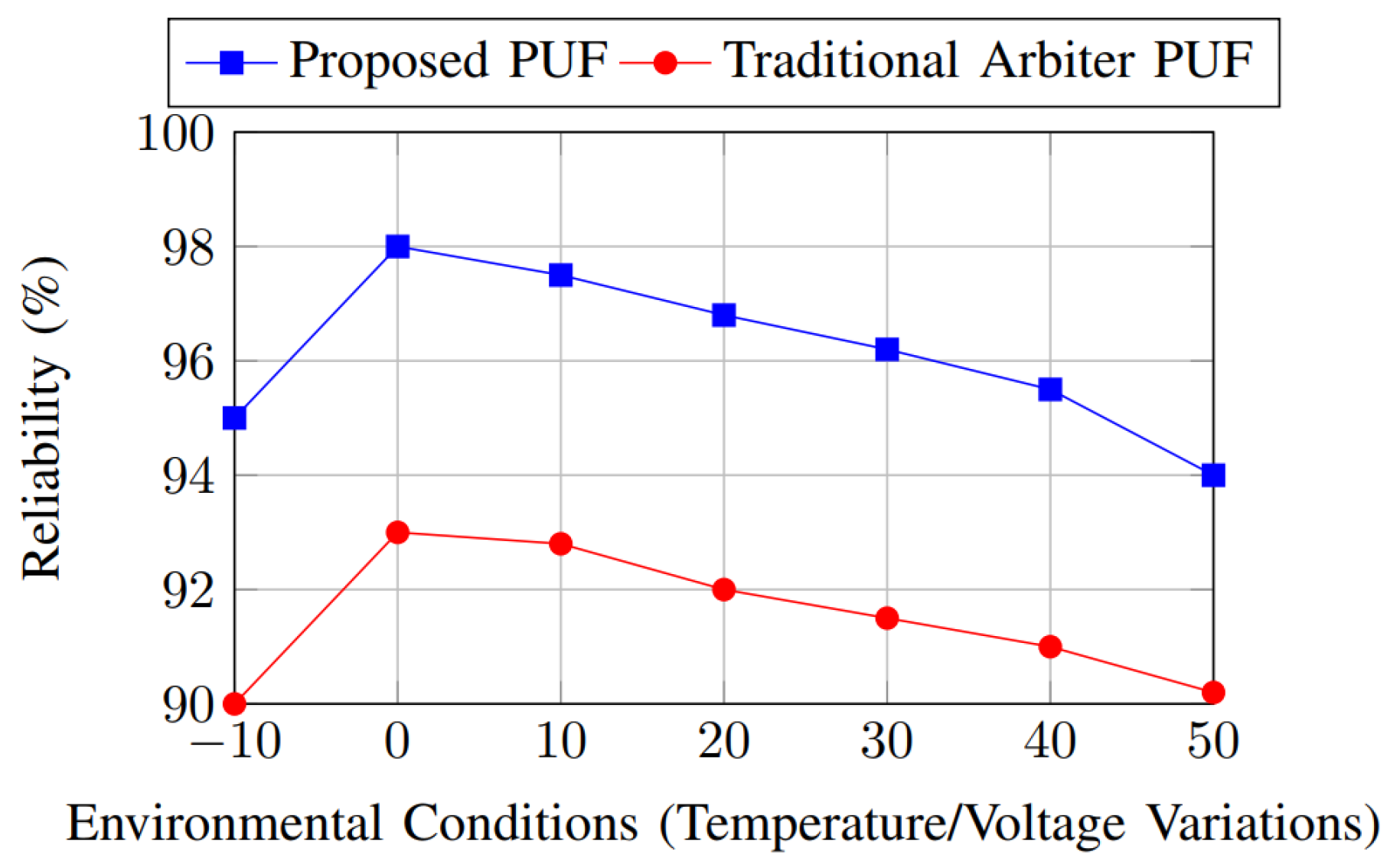
6.2.4. PUF Performance Analysis
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Rani, P.; Sharma, R. Intelligent transportation system for internet of vehicles based vehicular networks for smart cities. Comput. Electr. Eng. 2023, 105, 108543. [Google Scholar] [CrossRef]
- Xu, J.; Li, M.; He, Z.; Anwlnkom, T. Security and privacy protection communication protocol for Internet of vehicles in smart cities. Comput. Electr. Eng. 2023, 109, 108778. [Google Scholar] [CrossRef]
- Liu, Y.; Zhao, Y. A Blockchain-Enabled Framework for Vehicular Data Sensing: Enhancing Information Freshness. IEEE Trans. Veh. Technol. 2024, 73, 17416–17429. [Google Scholar] [CrossRef]
- Zhang, M.; Wei, E.; Berry, R.; Huang, J. Age-Dependent Differential Privacy. IEEE Trans. Inf. Theory 2024, 70, 1300–1319. [Google Scholar] [CrossRef]
- Gong, Y.; Yao, H.; Liu, X.; Bennis, M.; Nallanathan, A.; Han, Z. Computation and Privacy Protection for Satellite-Ground Digital Twin Networks. IEEE Trans. Commun. 2024, 72, 5532–5546. [Google Scholar] [CrossRef]
- Lan, Y.H.; Zhao, J.Y. Improving Track Performance by Combining Padé-Approximation-Based Preview Repetitive Control and Equivalent-Input-Disturbance. J. Electr. Eng. Technol. 2024, 19, 3781–3794. [Google Scholar] [CrossRef]
- Ding, C.; Zhu, L.; Shen, L.; Li, Z.; Li, Y.; Liang, Q. The Intelligent Traffic Flow Control System Based on 6G and Optimized Genetic Algorithm. IEEE Trans. Intell. Transp. Syst. 2024, 1–14. [Google Scholar] [CrossRef]
- Hu, J.; Jiang, H.; Chen, S.; Zhang, Q.; Xiao, Z.; Liu, D.; Liu, J.; Li, B. WiShield: Privacy Against Wi-Fi Human Tracking. IEEE J. Sel. Areas Commun. 2024, 42, 2970–2984. [Google Scholar] [CrossRef]
- Seliem, M.; Elgazzar, K.; Khalil, K. Towards privacy preserving iot environments: A survey. Wirel. Commun. Mob. Comput. 2018, 2018, 1032761. [Google Scholar] [CrossRef]
- Akter, S.; Khalil, K.; Bayoumi, M. A Survey on Hardware Security: Current Trends and Challenges. IEEE Access 2023, 11, 77543–77565. [Google Scholar] [CrossRef]
- Akter, S.; Khalil, K.; Bayoumi, M. Hardware Security in the Internet of Things: A Survey. In Proceedings of the 2023 IEEE 36th International System-on-Chip Conference (SOCC), Santa Clara, CA, USA, 5–8 September 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Drobot, A.; Zhang, T.; Buonarosa, M.L.; Kargl, F.; Schwinke, S.; Sikdar, B. The Internet of Vehicles (IoV)—Security, Privacy, Trust, and Reputation Management for Connected Vehicles. IEEE Internet Things Mag. 2023, 6, 6–16. [Google Scholar] [CrossRef]
- Zhou, Q.; Zeng, Z.; Wang, K.; Chen, M.; Zheng, Y. Privacy Protection Scheme for the Internet of Vehicles Based on Collaborative Services. IEEE Internet Things J. 2023, 10, 13342–13353. [Google Scholar] [CrossRef]
- Madububambachu, U.; Fatima, R.; White, K.; Riley, J.; Sherif, A.; Khalil, K. Hardware-Acceleration Based Privacy-Aware Authentication Scheme for Internet of Vehicles. In Proceedings of the 2024 IEEE 3rd International Conference on Computing and Machine Intelligence (ICMI), Mt Pleasant, MI, USA, 13–14 April 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Khalil, K.; Idriss, H.; Idriss, T.; Bayoumi, M. Lightweight Hardware Security and Physically Unclonable Functions; Springer: Cham, Switzerland, 2025. [Google Scholar] [CrossRef]
- Yu, S.; Park, K. PUF-Based Robust and Anonymous Authentication and Key Establishment Scheme for V2G Networks. IEEE Internet Things J. 2024, 11, 15450–15464. [Google Scholar] [CrossRef]
- Khalil, K.; Idriss, H.; Idriss, T.; Bayoumi, M. Physically Unclonable Functions. In Lightweight Hardware Security and Physically Unclonable Functions: Improving Security of Constrained IoT Devices; Springer Nature: Cham, Switzerland, 2025; pp. 49–52. [Google Scholar] [CrossRef]
- Tun, N.W.; Mambo, M. Secure PUF-based authentication systems. Sensors 2024, 24, 5295. [Google Scholar] [CrossRef]
- Alahmadi, S.; Khalil, K.; Bayoumi, M. Enhancing Arbiter PUF Against Modeling Attacks Using Constant Weight Encoding. In Proceedings of the 2024 IEEE 67th International Midwest Symposium on Circuits and Systems (MWSCAS), Springfield, MA, USA, 11–14 August 2024; pp. 173–177. [Google Scholar] [CrossRef]
- Khalil, K.; Idriss, H.; Idriss, T.; Bayoumi, M. Advanced PUF Designs. In Lightweight Hardware Security and Physically Unclonable Functions: Improving Security of Constrained IoT Devices; Springer Nature: Cham, Switzerland, 2025; pp. 97–113. [Google Scholar] [CrossRef]
- Alahmadi, S.; Khalil, K.; Idriss, H.; Bayoumi, M. Fortifying Strong PUFs: A Modeling Attack-Resilient Approach Using Weak PUF for IoT Device Security. In Proceedings of the 2024 IEEE International Symposium on Circuits and Systems (ISCAS), Singapore, 19–22 May 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Dey, B.; Khalil, K.; Kumar, A.; Bayoumi, M. A Novel Design Gate based Low-Cost Configurable RO PUF using Reversible Logic. In Proceedings of the 2019 IEEE 62nd International Midwest Symposium on Circuits and Systems (MWSCAS), Dallas, TX, USA, 4–7 August 2019; pp. 211–214. [Google Scholar] [CrossRef]
- Cao, N.; Wang, C.; Li, M.; Ren, K.; Lou, W. Privacy-Preserving Multi-Keyword Ranked Search over Encrypted Cloud Data. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 222–233. [Google Scholar] [CrossRef]
- Wong, W.K.; Cheung, D.W.l.; Kao, B.; Mamoulis, N. Secure kNN computation on encrypted databases. In Proceedings of the 2009 ACM SIGMOD International Conference on Management of Data, SIGMOD ’09, New York, NY, USA, 29 June–2 July 2009; pp. 139–152. [Google Scholar] [CrossRef]
- Yang, C.; Zhang, W.; Xu, J.; Xu, J.; Yu, N. A Fast Privacy-Preserving Multi-keyword Search Scheme on Cloud Data. In Proceedings of the 2012 International Conference on Cloud and Service Computing, Shanghai, China, 22–24 November 2012; pp. 104–110. [Google Scholar] [CrossRef]
- Abualsauod, E.H. A hybrid blockchain method in internet of things for privacy and security in unmanned aerial vehicles network. Comput. Electr. Eng. 2022, 99, 107847. [Google Scholar] [CrossRef]
- Zhong, H.; Han, S.; Cui, J.; Zhang, J.; Xu, Y. Privacy-preserving authentication scheme with full aggregation in VANET. Inf. Sci. 2019, 476, 211–221. [Google Scholar] [CrossRef]
- Wang, X.; Zeng, P.; Patterson, N.; Jiang, F.; Doss, R. An Improved Authentication Scheme for Internet of Vehicles Based on Blockchain Technology. IEEE Access 2019, 7, 45061–45072. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A Privacy-Preserving and Scalable Authentication Protocol for the Internet of Vehicles. IEEE Internet Things J. 2021, 8, 1123–1139. [Google Scholar] [CrossRef]
- Liu, J.; Li, Q.; Sun, R.; Du, X.; Guizani, M. An Efficient Anonymous Authentication Scheme for Internet of Vehicles. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Shahzad, L.; Abdelmaboud, A.; Elfadil Eisa, T.A.; Alamri, B.; Javed, I.T.; Al-Dhaqm, A.; Crespi, N. A Blockchain-Based Efficient, Secure and Anonymous Conditional Privacy-Preserving and Authentication Scheme for the Internet of Vehicles. Appl. Sci. 2022, 12, 476. [Google Scholar] [CrossRef]
- Liao, M.; Yuan, J.; Huang, F.; Wang, P.; Wang, W.; Luo, S.; Yao, Y. On-Chip Silicon Optical Scattering Physical Unclonable Function Towards Hardware Security. J. Light. Technol. 2023, 41, 1487–1494. [Google Scholar] [CrossRef]
- Abdolinezhad, S.; Zimmermann, L.; Sikora, A. A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs. Electronics 2021, 10, 2597. [Google Scholar] [CrossRef]
- Assaf, T.; Al-Dweik, A.; Iraqi, Y.; Jangsher, S.; Pandey, A.; Giacalone, J.P.; Abulibdeh, E.E.; Saleh, H.; Mohammad, B. High-Rate Secret Key Generation Using Physical Layer Security and Physical Unclonable Functions. IEEE Open J. Commun. Soc. 2023, 4, 209–225. [Google Scholar] [CrossRef]
- Singla, A.; Mudgerikar, A.; Papapanagiotou, I.; Yavuz, A.A. HAA: Hardware-Accelerated Authentication for internet of things in mission critical vehicular networks. In Proceedings of the MILCOM 2015—2015 IEEE Military Communications Conference, Tampa, FL, USA, 26–28 October 2015; pp. 1298–1304. [Google Scholar] [CrossRef]
- Xiao, J.; Ren, Y.; Du, J.; Zhao, Y.; Kumari, S.; Alenazi, M.J.; Yu, H. CALRA: Practical conditional anonymous and leakage-resilient authentication scheme for vehicular crowdsensing communication. IEEE Trans. Intell. Transp. Syst. 2025, 26, 1273–1285. [Google Scholar] [CrossRef]
- Eftekhari, S.A.; Nikooghadam, M.; Rafighi, M. Security-enhanced three-party pairwise secret key agreement protocol for fog-based vehicular ad-hoc communications. Veh. Commun. 2021, 28, 100306. [Google Scholar] [CrossRef]
- Roy, S.S.; Turan, F.; Jarvinen, K.; Vercauteren, F.; Verbauwhede, I. FPGA-based high-performance parallel architecture for homomorphic computing on encrypted data. In Proceedings of the 2019 IEEE International Symposium on High Performance Computer Architecture (HPCA), Washington, DC, USA, 16–20 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 387–398. [Google Scholar]
- Sureshkumar, V.; Chinnaraj, P.; Saravanan, P.; Amin, R.; Rodrigues, J.J. Authenticated key agreement protocol for secure communication establishment in vehicle-to-grid environment with FPGA implementation. IEEE Trans. Veh. Technol. 2022, 71, 3470–3479. [Google Scholar] [CrossRef]
- Seshabhattar, S.; Jagannatha, S.K.; Engels, D.W. Security implementation within GEN2 protocol. In Proceedings of the 2011 IEEE International Conference on RFID-Technologies and Applications, Sitges, Spain, 15–16 September 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 402–407. [Google Scholar]




| Symbol | Description |
|---|---|
| Physical unclonable function. | |
| k-nearest neighbor encryption technique. | |
| Autonomous vehicle. | |
| Transport management entity. | |
| Authentication server. | |
| Trusted third party. | |
| n | Size of identification vectors (e.g., AV ID data). |
| B | A random binary vector of size n used as part of the key generation for scheme members. |
| Invertible random matrices of size used in the key generation of the TTP. | |
| Invertible random matrices of size that form part of the TTP secret key. | |
| TTP secret key, defined as . | |
| A | An invertible random matrix in used to generate the authentication server secret key (ASK). |
| Random matrices in used in TM key generation, satisfying and . | |
| Secret key for transport management entity | |
| Random matrices in used in AV key generation, with and . | |
| Secret key for an autonomous vehicle. | |
| Identification data vector of an AV as managed by . | |
| Two column vectors obtained by splitting using the binary vector B. | |
| Ciphertext (encrypted index) generated by for an . | |
| Original identification vector of . | |
| Two vectors obtained by splitting using B. | |
| Trapdoor (encrypted authentication query) generated by . | |
| Modified ciphertext obtained by applying to , used in the matching process. | |
| * | Dot product operation used in matching the encrypted data. |
| Resource | Available | Used | Utilization (%) |
|---|---|---|---|
| LUTs | 63,400 | 15,400 | 24.3% |
| FFs | 126,800 | 7100 | 5.6% |
| BRAM | 135 | 30 | 22.2% |
| DSP Slices | 240 | 60 | 25% |
| IO Pins | 200 | 50 | 25% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Madububa Mbachu, U.; Fatima, R.; Sherif, A.; Dockery, E.; Mahmoud, M.; Alsabaan, M.; Khalil, K. Hardware Acceleration-Based Privacy-Aware Authentication Scheme for Internet of Vehicles Using Physical Unclonable Function. Sensors 2025, 25, 1629. https://doi.org/10.3390/s25051629
Madububa Mbachu U, Fatima R, Sherif A, Dockery E, Mahmoud M, Alsabaan M, Khalil K. Hardware Acceleration-Based Privacy-Aware Authentication Scheme for Internet of Vehicles Using Physical Unclonable Function. Sensors. 2025; 25(5):1629. https://doi.org/10.3390/s25051629
Chicago/Turabian StyleMadububa Mbachu, Ujunwa, Rabeea Fatima, Ahmed Sherif, Elbert Dockery, Mohamed Mahmoud, Maazen Alsabaan, and Kasem Khalil. 2025. "Hardware Acceleration-Based Privacy-Aware Authentication Scheme for Internet of Vehicles Using Physical Unclonable Function" Sensors 25, no. 5: 1629. https://doi.org/10.3390/s25051629
APA StyleMadububa Mbachu, U., Fatima, R., Sherif, A., Dockery, E., Mahmoud, M., Alsabaan, M., & Khalil, K. (2025). Hardware Acceleration-Based Privacy-Aware Authentication Scheme for Internet of Vehicles Using Physical Unclonable Function. Sensors, 25(5), 1629. https://doi.org/10.3390/s25051629