Abstract
Low-Altitude and Slow-Speed Small (LSS) targets pose significant challenges to air defense systems due to their low detectability and complex maneuverability. To enhance defense capabilities against low-altitude targets and assist in formulating interception decisions, this study proposes a new threat assessment algorithm based on multisource data fusion under visible-light detection conditions. Firstly, threat assessment indicators and their membership functions are defined to characterize LSS targets, and a comprehensive evaluation system is established. To reduce the impact of uncertainties in weight allocation on the threat assessment results, a combined weighting method based on bias coefficients is proposed. The proposed weighting method integrates the analytic hierarchy process (AHP), entropy weighting, and CRITIC methods to optimize the fusion of subjective and objective weights. Subsequently, Technique for Order Preference by Similarity to an Ideal Solution (TOPSIS) and Dempster–Shafer (D-S) evidence theory are used to calculate and rank the target threat levels so as to reduce conflicts and uncertainties from heterogeneous data sources. Finally, the effectiveness and reliability of the two methods are verified through simulation experiments and measured data. The experimental results show that the TOPSIS method can significantly discriminate threat values, making it suitable for environments requiring rapid distinction between high- and low-threat targets. The D-S evidence theory, on the other hand, has strong anti-interference capability, making it suitable for environments requiring a balance between subjective and objective uncertainties. Both methods can improve the reliability of threat assessment in complex environments, providing valuable support for air defense command and control systems.
1. Introduction
Low-altitude airspace holds immense potential for military, agricultural, medical, and transportation applications [1,2]. Advancements in unmanned aerial vehicle technology have further highlighted its value [3,4]. While opening low-altitude airspace benefits economic development, global security conditions remain concerning or, in some cases, critical [5]. In recent years, rapid technological progress has diversified low-altitude airborne objects; however, illegal activities involving LSS targets have surged annually [6,7]. Rapid and accurate threat assessment of low-altitude targets can provide crucial auxiliary support for tasks such as air combat defense, firepower allocation, and strategy optimization. Monitoring LSS targets and providing early warnings have thus become an important research direction for modern defense systems.
LSS targets are defined as low-altitude objects flying below 1000 m at speeds under 200 km/h, with radar cross-sections (RCSs) smaller than 2 m2. Their covert operations and low detectability pose substantial threats to important protected target territories. Timely identification of incoming targets is vital for low-altitude air defense. In low-altitude airspace over urban areas and battlefields, accurate recognition and handling of LSS targets present major challenges for surveillance activities linked to defense operations and early warning systems [5,8,9]. Visible-light cameras are now a common means of LSS target identification and surveillance. Therefore, there is a growing need to build threat assessment algorithms for LSS targets based on visible camera detection techniques [10,11]. Currently, threat assessment relies on analyzing trajectories obtained through detection and tracking [12,13]. The general threat assessment process mainly consists of threat modeling for incoming targets, metric assignment using multi-attribute decision theory, and ranking, along with other activities [14]. The construction of a target threat assessment model usually involves two key aspects: first, reasonably selecting target threat assessment factors to form quantitative evaluation indicators; second, determining the weight of each evaluation factor [15].
The first key component can be distilled into effectively inferring target intent based on specific features extracted from images. The target type and its motion characteristics are the most intuitive, effective, and widely used attributes in threat assessment [16,17,18]. Threat level evaluation aims to quantitatively describe hostile intent [19]. Existing methods, such as multi-attribute decision-making (MADM) algorithms [20,21] and Bayesian networks [22,23], have made valuable contributions to threat identification strategies, but they also have certain limitations. The second key component, the weights of evaluation factors, can be determined using numerous methods. Depending on the data sources used for weight determination, these methods are categorized as subjective, objective, and combined weighting. Subjective weighting methods are among the earliest proposed and most maturely applied approaches. Techniques such as the Delphi Method, Best–Worst Method, AHP, and Analytic Network Process (ANP) have been widely adopted across various fields. Faizi et al. [24] refined the BWM by proposing a Linear Best–Worst Method and a Euclidean Best–Worst Method. Rehman et al. [25] constructed decision matrices based on the AHP with consistent fuzzy preference relations, both achieving enhanced expert decision quality in multi-criteria decision-making. Fei et al. [26] integrated D-number theory into the ANP to better accommodate uncertainty in expert judgments. Lin [27] introduced a Bayesian cosine maximization method to modify comparison matrices, enabling more accurate priority vector estimation. Despite challenges such as rank reversal, comparison scale inconsistency, and priority derivation limitations, the AHP remains the most efficient and practical decision-making method [28]. Luo et al. [29] introduced a target threat assessment model that combines the AHP and information entropy to determine the weights of targets’ subjective and objective threat factors.
Unlike conventional aerial targets, LSS targets pose detection challenges such as incomplete information acquisition [30]. In addition, some types of LSS targets also have flexible maneuverability and dynamic task planning capabilities, making it difficult to accurately assign weights to each threat factor using a single weighting method. Therefore, extracting complete, comprehensive feature information with strong discriminative ability from images and comprehensively utilizing these features to improve the performance of spatial target recognition is of great significance [31]. The subjective weighting approaches commonly used in target threat assessment require extensive auxiliary systems and prior knowledge bases. However, research on LSS targets is still in its infancy, and obtaining accurate assessment results based on the AHP method is difficult. The entropy method [32] and CRITIC method [11,13] can update weights when threat factors change, with high feasibility. This study attempts to introduce the AHP, entropy, and CRITIC methods into the threat assessment of LSS targets to establish an optimization model. The weights determined by the three methods are fused to obtain more reliable evaluation weights. Theoretically available multi-information fusion methods include the weighted average method [33], Kalman filtering method [34], Bayesian estimation method [22], D-S evidence theory [35], etc.
Prior research has proven that Bayesian estimation can be used to address information uncertainty [36]. However, the probability values calculated with this method are based on existing data, which is not applicable to the currently limited LSS target data. The TOPSIS (Technique for Order of Preference by Similarity to Ideal Solution) method is renowned for its effectiveness and robustness in managing attribute conflicts and generating exhaustive rankings. This is achieved through comparative analysis of alternatives against the positive ideal solution (PIS) and negative ideal solution (NIS) [37]. The key focus of the TOPSIS method is on weight determination. Weight assignments range from subjective (based on expert judgment) to objective (derived from data analysis). While subjective methods, such as Delphi and the analytic hierarchy process, can become complex as the number of criteria increases, objective strategies, such as Criteria Importance Through CRITIC and information entropy theory, provide statistical weights that reduce subjectivity [38]. D-S evidence theory is a typical mathematical tool for information fusion. It fuses uncertain information without prior knowledge or conditional probabilities and uses basic probability assignments to represent probabilities in uncertain problems [39]. D-S evidence theory is more advantageous when dealing with the diversity, incompleteness, inaccuracy, or uncertainty of knowledge and information in the military field [40]. Consequently, D-S evidence theory has been applied across intelligent decision-making domains, including surveillance systems [41], decision analysis [42], fault diagnosis [43], and target tracking [44]. Leveraging its unique strengths, D-S evidence theory reduces uncertainties during data fusion and holds significant potential in threat assessment [19]. The generalized D-S evidence theory has been proposed to address the issues of fusing potentially incomplete and conflicting information caused by an incomplete recognition framework, and it has been validated in practical fuzzy applications [45]. Therefore, this study considers modeling with the generalized D-S evidence theory to fuse incomplete information in LSS target threat assessment situations and compares the target threat evaluation results with those of multiple fusion algorithms to verify the effectiveness of this algorithm. The main contributions of this paper are as follows:
(1) A threat assessment system for LSS targets is established. Starting from aspects such as LSS target characteristics, flight attributes, and protected objects, an LSS threat index evaluation system is constructed by comprehensively considering target intentions and environmental attributes. Finally, the threat membership function is established for each attribute.
(2) By combining subjective and objective weighting methods with multi-attribute decision-making theory, the fuzziness inherent in visible-light camera data acquisition errors or subjective judgments is retained, and the dynamic characteristics of objective weights in target threat assessment are integrated. To effectively integrate information on the target’s combat intention, a combined weighting method based on deviation coefficients is proposed.
(3) Based on the weight values, the TOPSIS method and D-S evidence theory are used to rank the threats of different targets. The TOPSIS method comprehensively considers the membership degree of each attribute and uses a weighted scoring mechanism to improve the robustness of decision-making. D-S evidence theory is introduced to perform data fusion on the uncertain information of different LSS targets so as to rank the threat values of different targets. The effectiveness and accuracy of the TOPSIS method and D-S evidence theory are verified through testing and evaluation using different spatial LSS target data, and the two methods are compared with other fusion algorithms.
The structure of this article is as follows. In Section 2, we first describe the process of the LSS target threat assessment model and select the LSS target threat assessment factors and their membership functions. Section 3 elaborates on the models of the AHP, entropy weighting, CRITIC objective weighting, and combined weighting methods based on deviation coefficients. It also introduces the threat assessment system based on the TOPSIS method and D-S evidence theory. Section 4 verifies the method developed in this study through simulation and measured data and analyzes and discusses the experimental data. In Section 5, we summarize the research results and highlight future development directions.
2. LSS Target Threat Assessment Model and Quantification of Factors
2.1. Research on LSS Target Threat Assessment Methodology
Target threat assessment is a high-level information fusion process and generally involves three steps: (1) determining evaluation indicators; (2) formulating methods for calculating target threat levels; (3) ranking the calculated threat levels. Current research in the field of target threat assessment has relied on multiple theoretical frameworks, covering methods such as evidence theory, fuzzy reasoning, Bayesian networks, multi-attribute decision-making theory, cloud model theory, and neural networks. While these methods differ in their specific application objectives, their core principles generally make them extremely adaptable. When applied to LSS target threat assessment scenarios, each method, based on its unique theoretical basis, presents distinctive assessment characteristics. The application characteristics of each method are listed in Table 1.

Table 1.
Evaluation of target threat assessment methods.
In actual low-altitude defense environments, accurate assessment of target threat levels requires integrating multiple factors for comprehensive analysis and judgment. Although algorithms have significant advantages in rapid data processing, commanders’ experience and judgment still play an irreplaceable and crucial role in dynamic decision-making environments. Therefore, an algorithm’s capabilities must be synergistically integrated with the domain knowledge and professional experience of military professionals. When dealing with multi-target attributes and highly dynamic environments, multi-attribute decision-making theory has superior advantages in human–machine collaboration compared to other threat assessment methods.
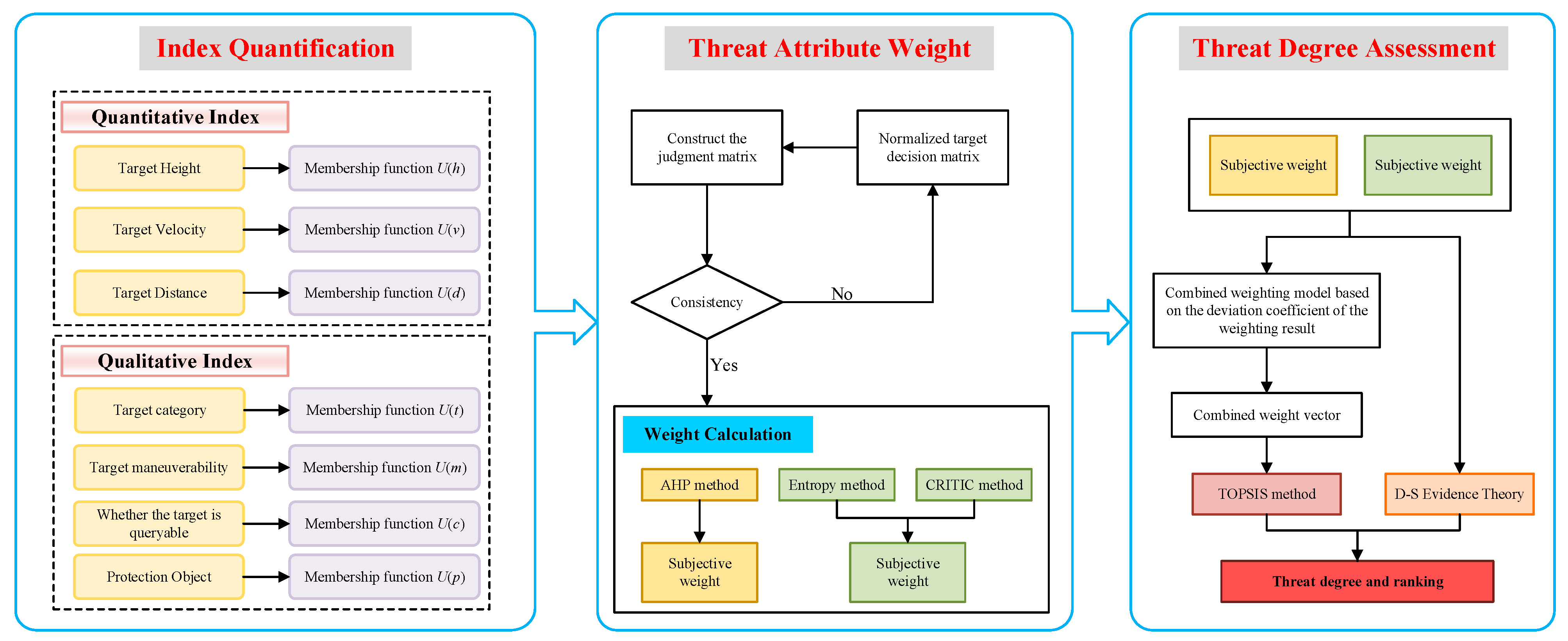
LSS target recognition is also a key focus of target detection. Target recognition mainly achieves identification by collecting LSS images through imaging technologies, conducting comparative analysis, and extracting features. The maximum recognition distance based on visible-light imaging is approximately 1 km [50]. When conducting threat assessment for LSS targets detected by visible-light cameras, regarding each incoming target as a decision object transforms an aerial target threat assessment into an MADM problem. Decision criteria are grounded in the level of threat posed by targets to ground-based air defense systems. From the basic knowledge of multi-attribute decision theory, a threat assessment model is established, as shown in Figure 1. This threat assessment model first preprocesses target situational data and establishes different affiliation functions. Subsequently, the AHP, entropy weighting, and CRITIC methods are applied to calculate weight vectors. Spearman’s rank correlation coefficient is then utilized to compute combined weights. Finally, using TOPSIS and D-S evidence theory, the threat level for the target is comprehensively evaluated.
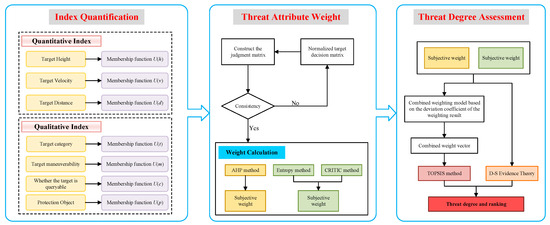
Figure 1.
Flowchart of target threat assessment model.
2.2. Selection and Quantification of Indicators for LSS Target Threat Assessment
To promote the development of low-altitude airspace resources and standardize the operation and management of these airspaces within urban areas, several laws, regulations, and key technical indicators applicable to LSS targets in urban areas have been implemented [51]. This provides an important reference for assessing the threat level of LSS targets. The threat assessment indicators for LSS targets are selected and quantified based on current detection technologies and their ability to reflect threat levels. Based on the nature and rationality of their membership functions, these indicators are divided into two categories: objective membership functions and subjective membership functions.
2.2.1. Objective Membership Functions
Both the forms and parameters of objective membership functions are derived from physical principles, mathematical relationships, or statistical analysis of sensor data. They describe a clear and interpretable functional relationship between measurable physical quantities and the perceived threat levels.
(1) Target height
The target’s flight altitude impacts the success rate of surprise defense. The lower the altitude, the easier it is for targets to evade detection and defense. At the same time, low-altitude targets can reach our position faster. Conversely, targets at excessively high altitudes struggle to directly execute planned missions—i.e., the threat level increases as the target altitude decreases. Currently, the flight airspace for LSS targets worldwide is generally restricted to 60–300 m [51]. Based on an extensive data review, the detection capabilities of three mainstream detection methods (radar, infrared, and visible-light cameras) for LSS targets [29,30,50] are listed in Table 2.

Table 2.
Analysis of LSS target detection capabilities.
From the above analysis, it can be seen that the effective detection range and recognition rate of visible-light cameras for ultra-low-altitude targets in complex urban backgrounds decrease significantly. When the flight altitude is 50 m, which is close to or lower than the height of typical urban high-rise building groups, targets can easily use terrain masking, increasing the difficulty of detection and interception. This is the critical threshold height for air defense systems. Therefore, this study sets the threat level to 1 when the altitude is below 50 m and uses a piecewise function as the height membership function U(h), where h in Equation (1) is the height of the LSS target:
The quadratic function form is chosen to reflect the nonlinear accelerated growth in the threat level as altitude decreases, especially when approaching the 50 m critical height, where the threat increases sharply. The coefficient 10−3 is used to adjust the value range of the function within the domain h ∈ [50, 1000], ensuring that it falls within the interval [0, 1].
(2) Target velocity
The target’s flight velocity vector U(v) is related to both the speed magnitude v and the velocity direction. First, the target’s relative entry angle θ is calculated using Equation (2):
In the equation, α represents the target’s heading angle—the angle between its flight direction and north; β represents the target’s azimuth angle—the angle between the line connecting the target to the air defense center and north.
A higher target speed implies stronger maneuverability and a shorter flight time to reach our defense position, thus increasing the threat level. After determining the LSS target’s relative entry angle, its velocity component relative to the air defense center is calculated. The flight speed ranges of various LSS targets in low-altitude airspace are listed in Table 3. The median value of the speed range is selected as a reference, with the flight speed of LSS targets set to 40 m/s as the benchmark value. The membership function U(v) is shown in Equation (3):

Table 3.
Speed ranges of different LSS targets in low-altitude airspace.
In the equation, v denotes the speed of the LSS target, and θ denotes its relative approach angle.
(3) Target distance
The closer the target is to our position, the easier it is to carry out direct action and the shorter the response time for the defense system. Smaller detected target distance indicators imply a higher likelihood of endangering air defense positions and a greater threat posed by the target. With reference to the analysis of target detection capabilities in Table 2, the minimum distance of the target is set to 100 m [29]. This value has practical significance in low-altitude defense scenarios, usually indicating that the target has entered the effective kill zone of short-range defense systems or poses a direct collision threat. This distance indicator should meet the response time requirements of the defense system. The affiliation function for distance U(d) is expressed by Equation (4):
The distance threat membership function U(d) adopts a quadratic form to simulate the nonlinear accelerated increase in the threat level as the distance decreases. The coefficient 10−4 ensures that the function values fall within the interval [0, 1] within the domain d ∈ [100, +∞).
2.2.2. Subjective Membership Functions
Factors such as target type, maneuverability, query availability, and protected objects are subjective factors. The forms and parameters of these functions are mainly derived from the knowledge and tactical experience of domain experts. To enhance objectivity and consensus, this study invited 10 experts in related fields—3 personnel from air defense forces, 3 professors in the field of target detection systems, 3 UAV technicians, and 1 professor of military operations research. In the form of questionnaires, experts were asked to independently score and rank the threat levels of various targets, assign threat values corresponding to strong, medium, and weak maneuverability, identify threat differences between queryable and non-queryable targets, and provide relative threat values of typical protected objects. Scores were on a 0–1 scale, with 1 representing the maximum threat, and results were retained to one significant figure. The mean and median of each score were calculated, and the obtained values were compared with the research findings in references [29,51]. Finally, the membership values for factors such as target type, maneuverability, query availability, and protected objects were determined.
(1) Target type
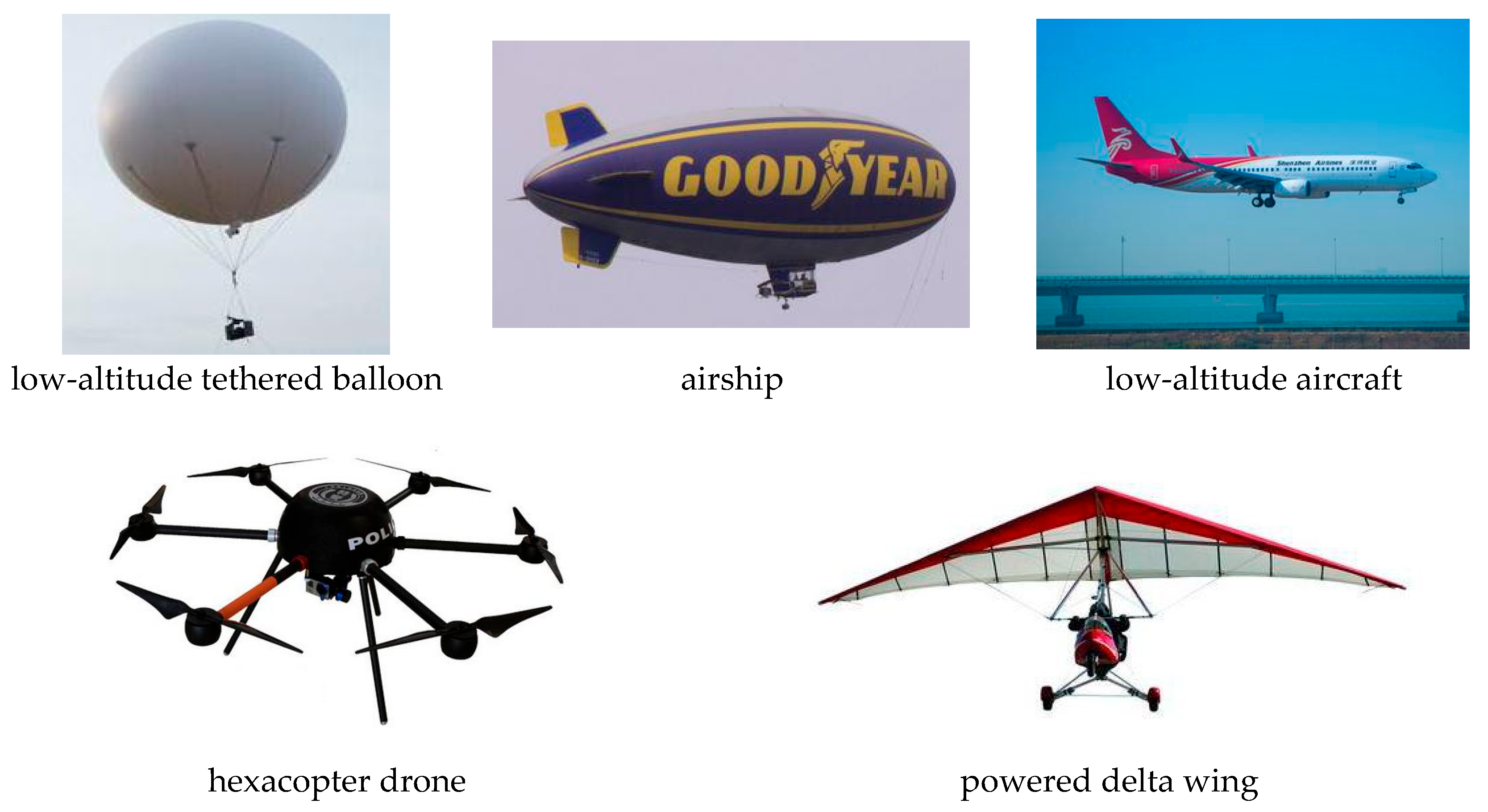
In recent years, various types of aircraft have emerged in the market, such as paragliders, light helicopters, and gyroplanes. The LSS targets in this study are grouped into five categories: powered delta wings, hexacopter unmanned aerial vehicles (UAVs), airships, low-altitude airplanes, and low-altitude tethered balloons. Their classification is shown in Figure 2.

Figure 2.
LSS target types.
Based on expert opinions [51], the above LSS targets are ranked by threat level from highest to lowest as follows: hexacopter UAVs, powered delta wings, airships, low-altitude aerial photography balloons, and low-altitude airplanes. The affiliation function value U(t) is shown in Equation (5):
(2) Target’s mobility performance
Maneuverability serves as a static indicator of target characteristics. Once the target type is identified, its corresponding maneuverability can be obtained. For air defense systems, targets with poorer maneuverability are easier to intercept. The mobility levels of the LSS target types under study are set to be strong, medium, and weak, and the affiliation function values U(m) corresponding to these three levels are shown in Equation (6):
(3) Whether the target is searchable
When targets can respond to ground communication signals, their threat level decreases. When targets fail to respond and are unqueryable, the threat level increases. Their affiliation function values U(c) are shown in Equation (7):
(4) Protected object
The threat that an incoming LSS target poses to a protected site varies depending on the type of protected site. Here, the threat degree is set to 0.8, 0.6, or 0.5, and the specific discrete affiliation function values U(p) are shown in Equation (8):
3. LSS Target Threat Assessment Model
The aim of the threat assessment model for LSS targets is to scientifically and reliably quantify the threat levels of targets; its core consists of two parts: weighted optimization of threat factors and fusion-based assessment of target threat levels. The process of assigning weights focuses on determining the relative importance of each threat assessment index. By integrating the advantages of subjective and objective weighting methods, their respective limitations can be overcome, and more reliable combined weights can be obtained. Based on the obtained comprehensive weights, multi-attribute decision-making and information fusion techniques can be used to comprehensively calculate and rank the overall threat level of a target, effectively handle the uncertain and conflicting data in the assessment process, and finally output reliable results of target threat level assessment.
3.1. Methods of Improvement
The core challenges in weight allocation for evaluating LSS target threat indicators are mainly as follows: the lack of sufficient historical data, leading to incomplete information; high uncertainty caused by the complex kinematic characteristics of target types and their vulnerability to countermeasures; and the need to integrate dynamic real-time data with static expert knowledge. A single weight-setting method cannot fully encompass such complexity. Therefore, a hybrid weighting scheme is proposed, which integrates three complementary methods, each addressing specific aspects of the LSS target problem.
The analytic hierarchy process (AHP) can tackle issues of incomplete information and a lack of statistical data. This method incorporates domain experts’ knowledge and experience, which is crucial for quantifying intangible attributes and providing an a priori understanding of threat dynamics. A consistency construction approach is adopted to meet the needs of rapid assessment in low-level security defense scenarios.
The entropy weight method is suitable for processing dynamic real-time data. It can allocate weights based on the degree of data dispersion among different targets. Indicators with high variability contribute more to distinguishing threat levels among current LSS targets, enabling the assessment to adapt to immediate situations.
The CRITIC method can reflect the relationships between indicators. It considers both the comparative intensity between indicators and their conflict characteristics, providing a more comprehensive objective measurement standard, which is vital for LSS target evaluation.
The aim of integrating the above three methods is to establish a robust weight foundation that is supported by professional knowledge, is responsive to data, and accounts for interactions between different criteria. This is essential for an environment full of uncertainties and evolving low-frequency sudden threats.
3.1.1. Consistency-Based Analytic Hierarchy Process (AHP) Subjective Weights
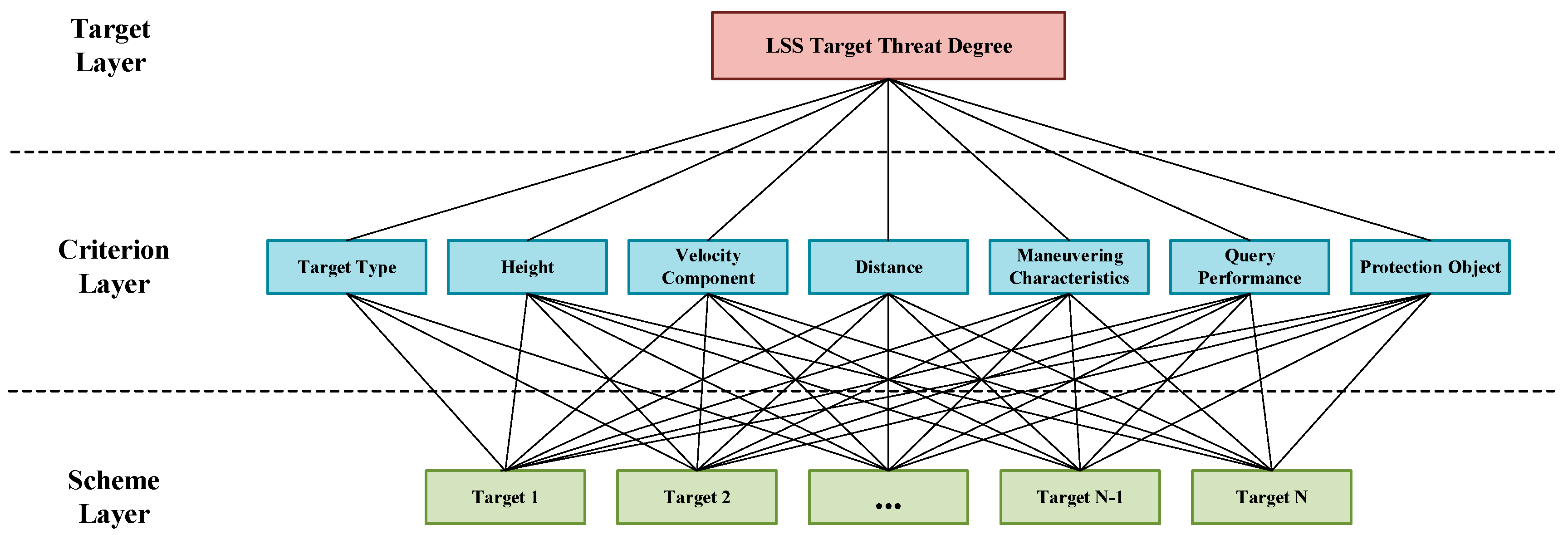
The AHP is a multi-objective decision analysis method integrating qualitative and quantitative approaches. It uses expert experience to compare the importance of participating factors, constructs a comparison matrix to determine the relative importance of each factor in the hierarchy, and forms a judgment matrix to quantitatively determine the weights of threat factors [52]. In the threat assessment model, the AHP is converted into a problem of finding the threat degree of the attacking target; in this version, the target layer is the threat degree for the current attacking LSS target, the criterion layer comprises the threat attributes for the target type, altitude, and speed, and the program layer is the current attacking batch LSS target. The hierarchical model is shown in Figure 3.
Figure 3.
Hierarchical analysis model diagram.
The following steps are typically used when determining indicator weights using this method [53]:
Step 1: Forming a judgment matrix. To establish an AHP model for the threat assessment system, experts, based on experience, rank each target threat attribute to characterize its degree of importance. Values from 1 to 9 quantitatively represent the importance level for each threat element, as shown in Table 4. The judgment matrix A = (Aij)n×n, aij, is formed to compare targets based on various threat attributes.

Table 4.
Quantitative values for relative importance.
Step 2: Hierarchical ordering. Using matrix theory, the equation Aw = λmaxw is solved to obtain the eigenvector w and the maximum eigenvalue λmax. The threat level weight vector for the indicator system is w = (w1, w2, …, wn)T.
Step 3: Conducting consistency tests. Expert evaluations are mainly subjective and do not follow mathematical formulas, making it difficult to meet the consistency requirements. Therefore, a consistency check of the calculated threat weight vector w is necessary.
Step 4: Hierarchical total ordering. When dealing with multiple hierarchical structures, if the weight vector of indices at the (k − 1)-th level is 1 and the weight vector of the k-th level relative to the (k − 1)-th level is H, then the weight vector of the k-th level relative to the target layer is w = (w1, w2, …, wn)T = l · H.
Since the consistency test increases modeling complexity, it is improved, and the steps of the improved AHP method are as follows:
Step 1: Based on the 1–9 ranking scale shown in Table 1, a judgment matrix q is generated through pairwise comparison of each target threat attribute element in the evaluation index set, as shown in Equation (9). When constructing the first row, the 1–9 scale is used as the criterion; for other rows, judgments are formed using qij = qik × qkj, and the complete judgment matrix q is finally established.
Step 2: Using matrix theory, the equation qw = λmaxw is solved to obtain the eigenvector w and the maximum eigenvalue λmax of matrix q. The resulting vector w = (w1, w2, …, wn)T represents the threat weight vector of the indicator system.
3.1.2. Entropy Method for Determining Objective Weights
After determining subjective weights based on expert experience, information entropy theory is introduced into the process of determining target attribute weights for LSS target threat assessment. This approach makes weight determination more objective and better reflects the impact of each attribute on threat assessment. With the entropy weight method, weights are assigned by analyzing the deviation of information entropy values, thereby deriving indicator weights with correct and reliable results. The entropy weight method is defined as follows.
If an object has n states, and the probability of each state is (p1, p2, …, pn), then the information entropy value of the object is defined as
The steps for determining objective weights using the entropy method are as follows:
Step 1: Calculate the entropy value for the indicator Ej. Construct a decision matrix B = (bij)m × n based on threat assessment indicators, where m represents the number of LSS targets and n represents the number of threat attributes. Here, bij denotes the attribute value of the i-th target under the j-th threat indicator. Normalize the decision matrix B to obtain the normalized matrix , in which
where is a value normalized to the attribute.
Then, the information entropy Ej for the j-th threat assessment indicator is
Step 2: Calculate the weighting system for each indicator. Based on the principles of the entropy weight method, the objective weight woj for the j-th threat assessment indicator can be obtained as
Then, the information entropy-based target weight value wo is
In this formula, wo1, wo2, wo3, wo4, wo5, wo6, and wo7 represent the calculated weights for the following threat factors: target category, target altitude, velocity component relative to the air defense center, target distance, target armament performance, whether the target is queryable, and the protected object, respectively.
3.1.3. CRITIC Calculation of Objectively Assigned Weights
The CRITIC method, proposed by DIAKOULAKI, is an objective weighting method that assigns weights by quantifying the information volume of each indicator based on two key principles: comparative intensity (variability) and conflict (correlation) among indicators. Below are the specific calculation steps and an example application in threat assessment.
Step 1: The original situational data matrix dij, formed by j threat assessment indicators of i targets, first undergoes normalization processing.
For positive indicators (the higher the value, the higher the threat, e.g., speed),
For negative indicators (the smaller the value, the higher the threat, e.g., distance),
Step 2: The comparative strength for the indicator Sj is determined:
The conflictual correlation coefficient rij is
Step 3: Conflictiveness is measured by the correlation coefficient between indicators: the higher the conflictiveness (the lower the correlation coefficient), the greater the weight. The formula for calculating conflictability is
Step 4: The comprehensive information volume Gj is determined for each threat indicator:
Step 5: The weight coefficients, denoted by w, for each threat indicator are determined from the combined information of the indicators:
3.1.4. Combined Assignment Method Based on Deviation Coefficients
In the threat assessment of LSS targets, the results of subjective and objective weighting methods often differ, reflecting uncertainties from different perspectives. Simple fixed-proportion fusion (such as equal-weight averaging) cannot fully utilize the consistency information between the results of these methods. The ideal fusion assigns greater weights to methods with more consistent results. To this end, this study proposes a dynamic fusion mechanism based on the weight deviation similarity index rlk. Methods with highly consistent weighting results can more truly reflect the weight relationships and should dominate the fusion; methods with large result differences should contribute less. Compared with fixed fusion or complex optimization methods, this consistency-based dynamic weighting strategy provides a more intuitive, transparent, and efficient approach to handling uncertainties in weight allocation, enhancing the robustness of fusion results.
Due to the limitations of uncertainties in various evaluation indicators and data collection conditions, existing evaluation schemes often only consider expert experience or original situational data. To make up for the drawbacks of subjective and objective weighting, this study, on the basis of the obtained subjective and objective weight vectors, determines their weighting coefficients in the weight combination based on the deviation coefficients from the subjective and objective weighting results mentioned above; then, the relevant models are established, and the combined weights are calculated.
The numerical deviation representing the differences between the results of different weighting methods is called the weight deviation similarity index rlk. The smaller the difference, the greater the consistency between the weighting methods, and the larger the rlk value. The value of rlk is always less than or equal to 1 and non-negative. The consistency coefficient rlk of the weighting results is defined as the deviation correlation coefficient between the l-th and k-th weighting methods:
The specific solution steps for model construction are as follows.
Let the indicator number for the original evaluation program be i, i = 1, 2, …, n, the assignment method used be j, j = 1, 2, …, n, and the weight of each indicator for each assignment method be w = (w1, w2, …, wn).
Step 1: By minimizing the sum of squared deviations, solve for the optimal combined weights. The calculation model is
Formulate it as the Lagrangian function L(l, wi):
This leads to the unique optimal solution wi:
Step 2: Using the concept of correlation coefficients, establish a relevant model to calculate the weight coefficients for the three weighting results. Let rlk denote the correlation coefficient between the l-th and k-th weighting methods, and obtain the correlation coefficient matrix r corresponding to q weighting results:
From the definition of rik, it is known that rll = 1 (l = 1, 2, …, q), rlk = rkl (l, k = 1, 2, …, q). According to the symmetric matrix, calculate the correlation degree rj between the j-th weighting method and all other weighting methods. The calculation formula is
Through normalization, obtain the weight coefficients lj for each weighting method in the combined weighting:
Substitute the above formula into Equation (25) to obtain the combined weights v of each indicator calculated based on three weighting methods:
3.2. Target Threat Level Assessment
3.2.1. Target Threat Level Assessment Based on TOPSIS Method
The TOPSIS method is a commonly used multi-attribute decision analysis approach. Its basic principle involves ranking alternatives by calculating their distances to both the ideal solution (the best possible scenario, where all attributes achieve optimal values) and the negative ideal solution (the worst possible scenario, where all attributes achieve suboptimal values). A better alternative is simultaneously closer to the positive ideal solution and farther from the negative ideal solution. After obtaining the combined weights v for target threat indicators, as described in the preceding section, we analyze and rank the threat levels of each target using the decision matrix and weight information.
The standardized attribute matrix H = [hij]m×n is constructed using the comprehensive weights v = [v1, v2, …, vn] for target attributes, calculated using the combined weighting method based on deviation coefficients and based on the threat indicators of each target.
Step 1: Calculate the weighted normalized matrix V:
Step 2: Determine the ideal solution vj+ and negative ideal solution vj−:
Step 3: Calculate the distance di+, di− from each target threat indicator attribute value series to the ideal and negative ideal solutions:
Step 4: Calculate the closeness coefficient Ci for each target, representing its proximity to the ideal solution:
3.2.2. Target Threat Level Assessment Based on D-S Evidence Theory
D-S evidence theory was proposed and improved by Dempster and Shafer. It can handle incomplete, uncertain, and unclear information in multisource evidence, reducing the interference of conflicting weights in decision-making. This enables the fusion of multisource information.
D-S evidence theory first defines a finite non-empty set of hypotheses as the Frame of Discernment (FoD). This set contains U mutually exclusive and exhaustive hypotheses.
where U is the number of hypotheses in the system, and Hi (i = 1, 2, …, M) represents the i-th hypothesis reflecting the i-th possible identification result. According to the definition of FoD, the power set can be denoted by 2ϴ.
where Φ is the empty set, and H ⊆ ϴ, H ∈ 2ϴ.
To describe the support for the hypotheses, a basic probability assignment (BPA), also known as a basic belief assignment (BBA), is introduced into the power set 2Θ. The mass function m: 2Θ→[0, 1] must satisfy the following conditions:
where H is a proposition in 2Θ containing one or more hypotheses, and m(H) denotes the initial support for H.
Equations (36) and (37) reflect the non-negativity and normalization of the mass function. Without further information, m(H) cannot be further subdivided into any proper subsets of H. When m(H) > 0, H is called a focal set, and all focal sets are collectively referred to as the core of the mass function.
The belief function Bel and plausibility function Pl in the power set 2Θ are defined by the following formulas:
where H and A are both propositions in the power set 2Θ.
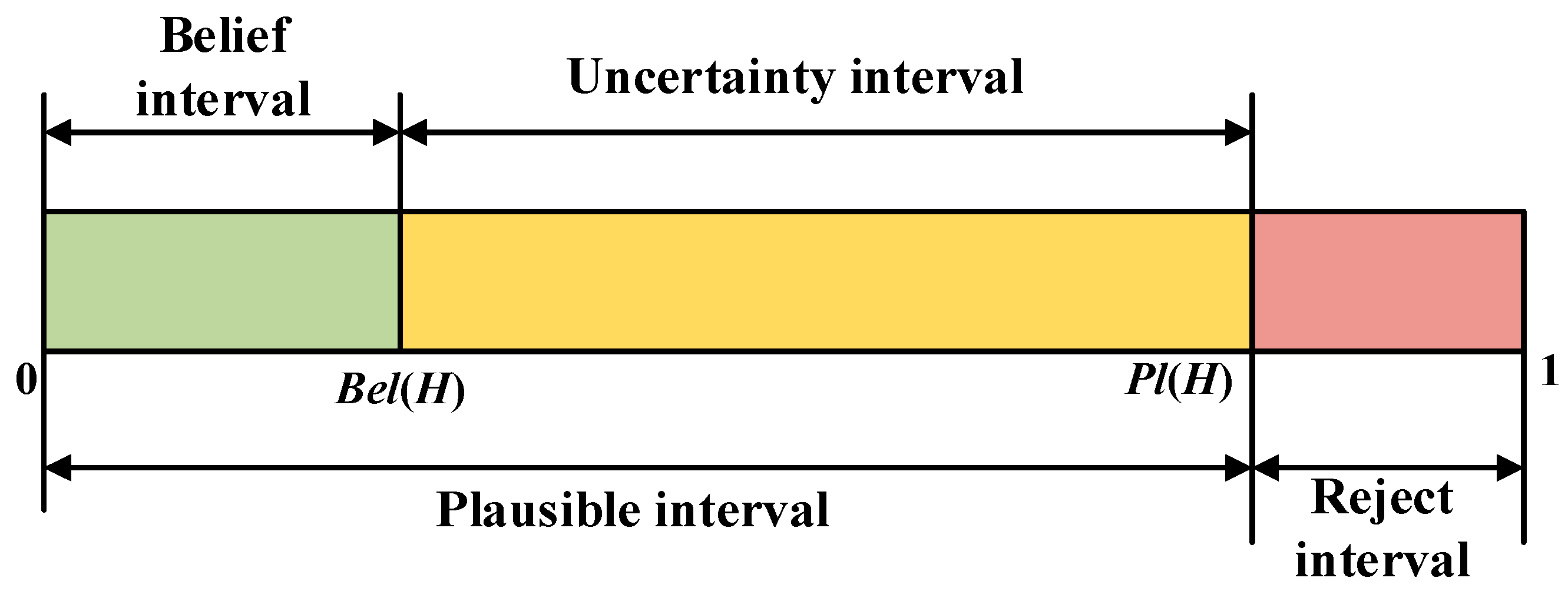
From Equation (38), Bel(H) is defined as the degree of belief in proposition H, which is the sum of basic probabilities of all subsets of H, representing the total belief in H. Therefore, it can also be considered the lower-bound function of H. Pl(H) is defined as the plausibility function of H, representing the degree of non-false belief in proposition H; thus, it is also known as the upper-bound function of H. The relationship between Bel(H) and Pl(H) can be understood from Figure 4.
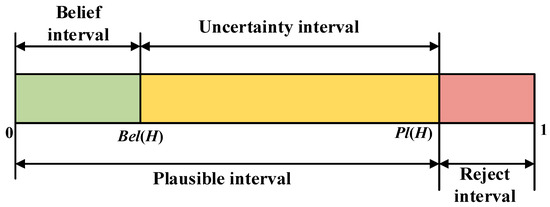
Figure 4.
Relationship between Bel(H) and Pl(H).
The uncertainty description reveals that D-S evidence theory can reflect probabilistic uncertainty, so it can be seen as an uncertainty reasoning theory, showing its applicability to multisource data information fusion. As Figure 4 shows, the logical relationship between Bel(H) and Pl(H) is as follows:
where is the complement of H.
The interval [Bel(H), Pl(H)] is called the confidence interval or uncertainty interval, representing the uncertainty and imprecision in D-S evidence theory. Suppose that m1, m2, …, mN are N independent BPAs obtained by N different sensors for the same target. D-S evidence theory’s combination rule (orthogonal sum rule) can be expressed as
Thus, the combination rule for different mi, mj (I, j = 1, 2, …, N) can be defined as
where k is the total conflict factor, which represents the total conflict between mi and mj.
The value of k represents the degree of conflict between two pieces of evidence, with 1/(1 − k) serving as the normalization factor. This ensures that the combined evidence m in Equation (45) is non-negative and normalized.
D-S evidence theory’s combination rule satisfies commutative and associative laws during computation, defined as, respectively,
4. Results and Discussion
The purpose of this section is to verify the effectiveness of multi-dimensional feature fusion and the performance of the proposed algorithm through simulation calculations based on existing data and the analysis of measured data. Firstly, the quantitative values of LSS target attributes and flight scenario parameters in the existing data are introduced. Based on the aforementioned subjective and objective weighting methods and the combined weighting method, the index weights of LSS targets are established. Subsequently, the TOPSIS method and D-S evidence theory are used to complete the threat assessment of LSS targets, and comparisons are made with various threat assessment algorithms to verify the feasibility of the fusion method proposed in this paper. On this basis, the measured data are used to calculate the target threat level, and the performance of the proposed algorithm is analyzed and compared with that of other algorithms, the results of which verify the superiority of the method in this paper.
4.1. Simulation Example
4.1.1. Data Preprocessing
A set of LSS target detection images were collected in an air defense area, and their original situational data were obtained by integrating various sensor inputs. Using the collected LSS target data, case simulations were conducted to evaluate and rank target threat levels using the proposed method. Table 5 presents the sampled LSS target situational data.

Table 5.
LSS target attribute values.
Membership functions for the threat attributes of each target indicator were quantified using the calculation methods described in Section 2.2. Thus, the attribute values in Table 5 were converted into a target attribute decision matrix, listed in Table 6.

Table 6.
Target attribute decision matrix.
4.1.2. Combined Weighting Results
Using the improved AHP method described in Section 3.1.1 and integrating expert opinions, the seven indicators are ranked by importance for target threat assessment in descending order: target distance, target type, velocity component, target altitude, maneuverability, query performance, and protected object. Their relative importance scores are shown in Table 7.

Table 7.
Relative importance scores.
Thus, the weight vector for each indicator can be derived. Table 8 presents the weight calculation results for each indicator using the improved AHP method, with the weight values denoted as W1:

Table 8.
Summary of calculation results of improved AHP method.
After normalizing the attribute matrix, the weight vectors of each index of the entropy weight method are obtained. Table 9 summarizes the weight calculation results from the entropy weight method, with the calculated weights denoted as W2:

Table 9.
Summary of calculation results of weight calculation by entropy method.
CRITIC calculates the weight vector of each index. Table 10 summarizes the weight calculation results from the CRITIC method, with the calculated weights denoted as W3:

Table 10.
Summary of CRITIC weight calculation results.
The combined weight vector v of each index is obtained by substituting the above weighting calculation results of the improved AHP, entropy, and CRITIC methods into Equation (29):
4.1.3. Analysis of Threat Assessment Results
The TOPSIS method ranks the threat levels of eight LSS targets based on the criterion that a closer proximity to the positive ideal solution corresponds to a larger closeness coefficient and a higher threat level. Threat levels are then ordered sequentially based on this coefficient. Table 11 lists the positive/negative ideal solutions for the seven evaluation indicators, and Table 12 presents the threat level calculation results and rankings for the eight LSS targets.

Table 11.
Positive and negative ideal solutions for evaluation indicators.

Table 12.
Calculation results and ranking of target threat levels.
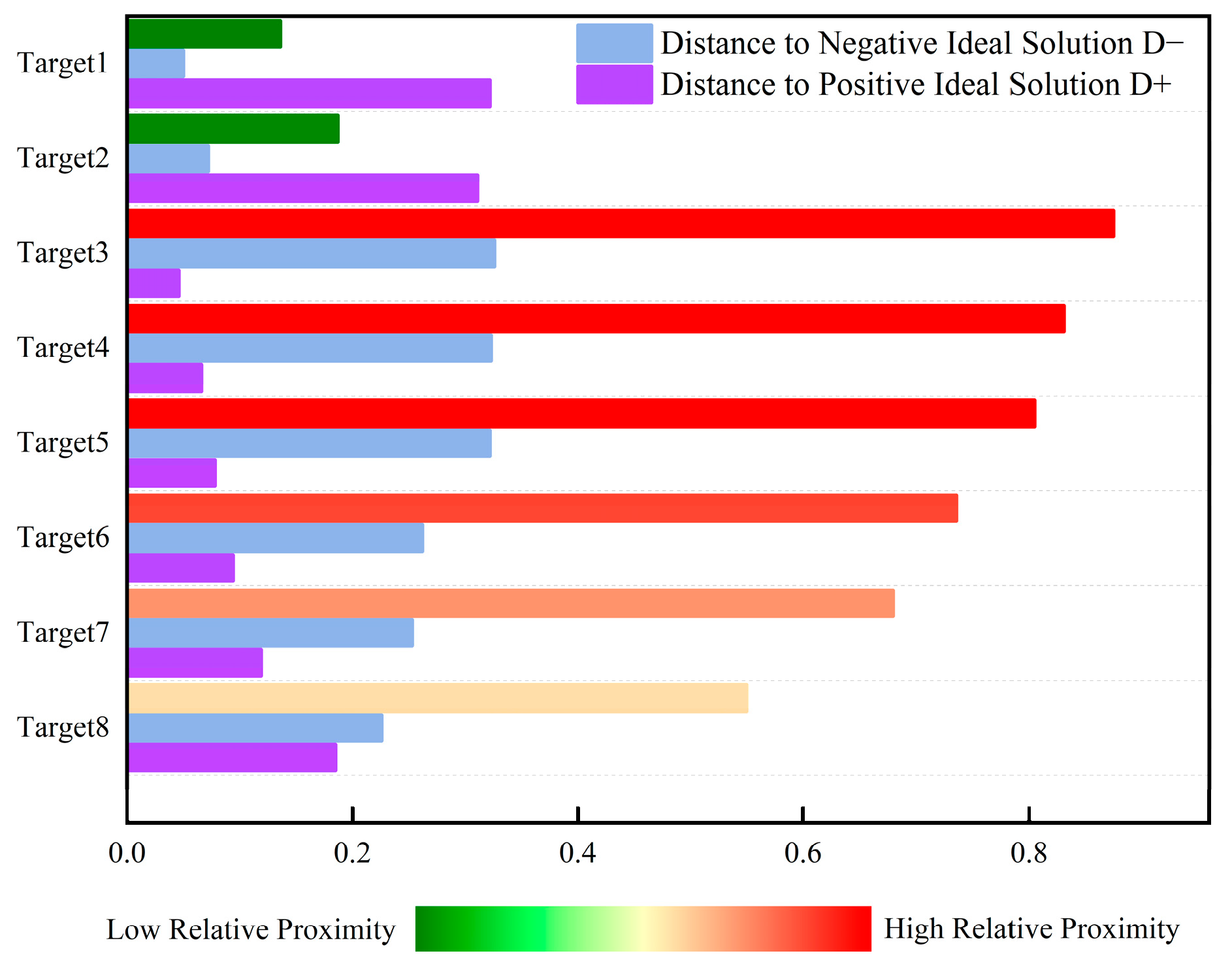
Figure 5 shows the numerical comparison of positive and negative ideal solutions and the relative closeness degrees of the seven evaluation indicators for the eight LSS targets. This ranking histogram displays the distribution of multi-target threat levels for intuitive understanding. As an auxiliary tool for dynamic perception, it can effectively help decision-makers make accurate judgments and decisions based on real-time state changes. Target 3 has a closeness coefficient of 0.875; target 4, 0.831; target 5, 0.805; target 6, 0.736; target 7, 0.680; target 8, 0.550; target 2, 0.187; and target 1, 0.136. Thus, the threat level ranking of airborne LSS targets is target 3 > target 4 > target 5 > target 6 > target 7 > target 8 > target 2 > target 1.
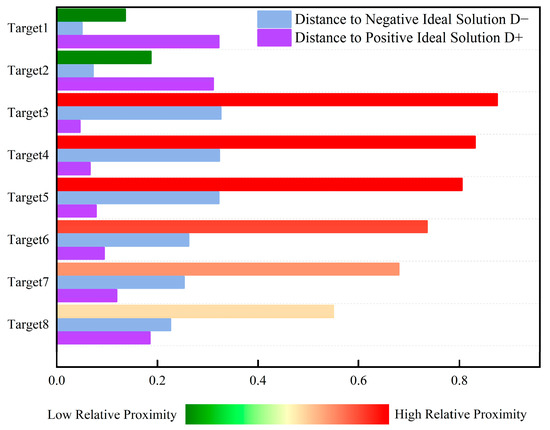
Figure 5.
Histogram of target threat level ranking based on TOPSIS evaluation.
The FoD is defined as the set of all threat assessment indicators, i.e., Θ = {target distance, target type, velocity component, target altitude, maneuverability, query performance, protected object}. The results from the improved AHP, entropy weight, and CRITIC weighting methods are treated as BPA functions in D-S evidence theory, such that m1(Hj) = W1(Hj), m2(Hj) = W2(Hj), m3(Hj) = W3(Hj). Pairwise fusion evidence is then calculated using Equations (43)–(48). The weighted conversion matrix vDS is then obtained:
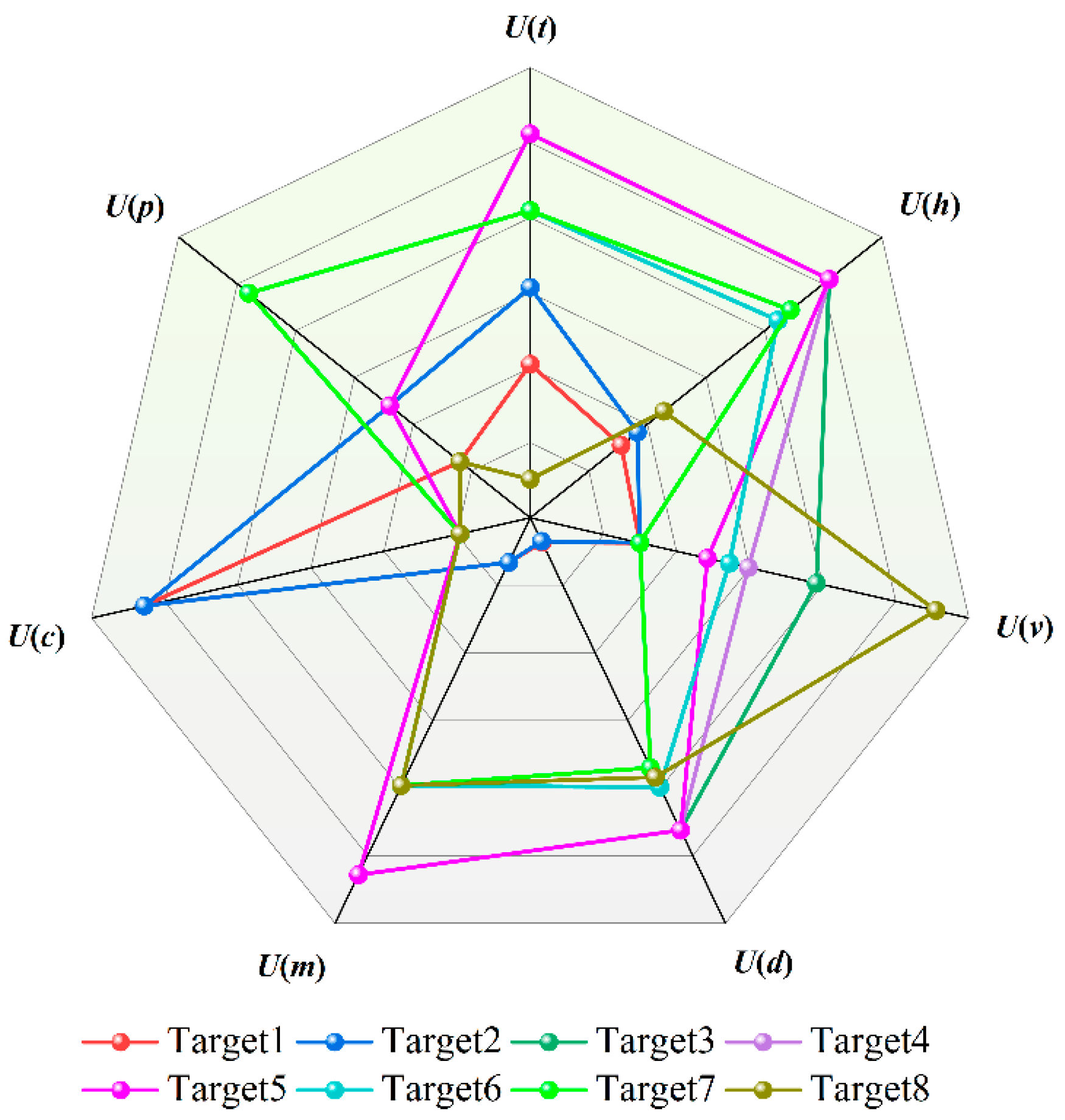
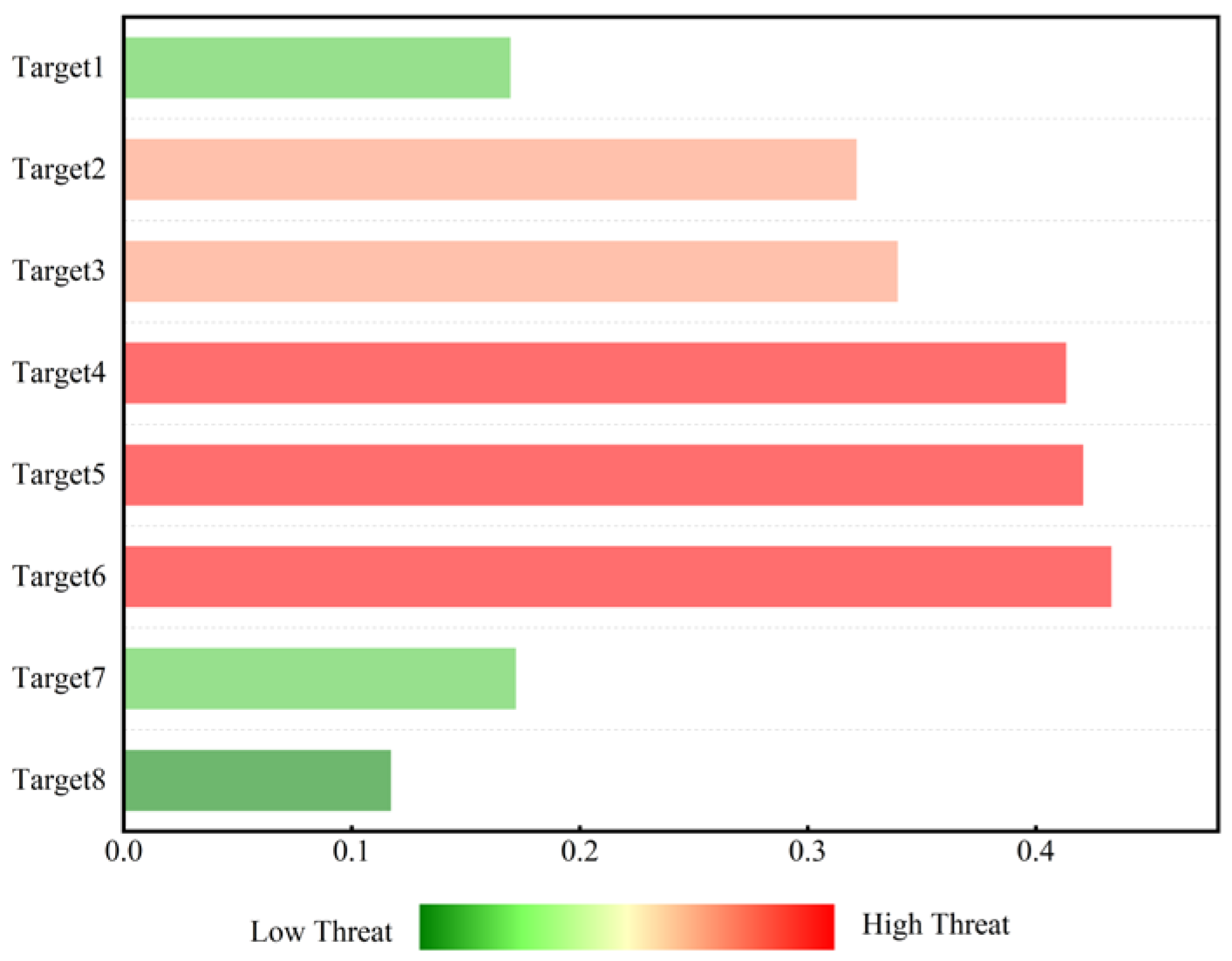
Table 13 lists the normalized values of the threat assessment indicators for LSS targets and the calculated threat levels (weighted sums). Displaying the evaluation indicators of LSS targets in the form of a radar chart (as shown in Figure 6) allows for an intuitive observation of the high-dimensional information of target threats. It can be intuitively seen from Figure 6 that when evaluating target threat levels, the deviation in results is mainly reflected in objective factors, such as target altitude and target speed. The histogram of LSS target threat level ranking can be dynamically updated, driven by real-time data. The changing trend in target threat levels can be easily displayed through the threat value scale and color temperature. It can be intuitively seen from Figure 7 that the threat values for Targets 4, 5, and 6 place them in a dangerous state, while Target 8 is in a safe state. The ranking of LSS targets by threat level is Target 3 > Target 4 > Target 5 > Target 6 > Target 7 > Target 2 > Target 8 > Target 1. Targets 3, 4, and 5—all hexacopter UAVs—are classified as high-threat targets due to their low altitude, short distance, and high speed.

Table 13.
Calculation results of threat degree using D-S evidence theory.
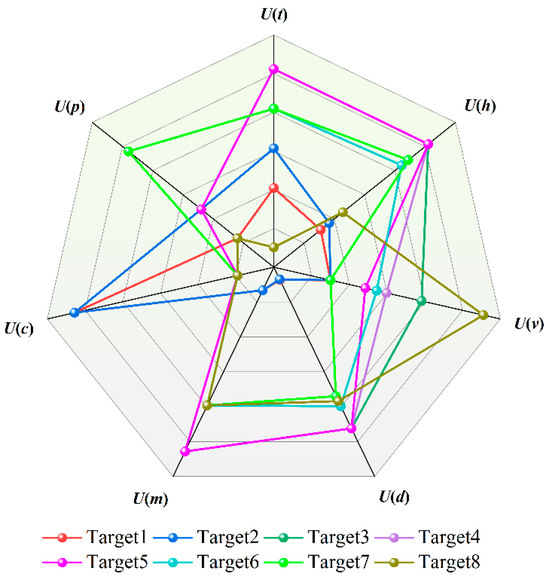
Figure 6.
LSS Target threat assessment radar chart.
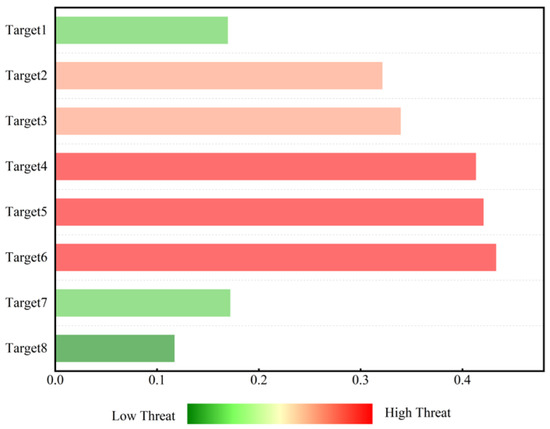
Figure 7.
Histogram of threat level ranking evaluated by D-S evidence theory.
A comparison of the threat assessment sequences derived from D-S evidence theory and the TOPSIS method shows that the main difference between the two approaches lies in the assessment of Target 2 (airship) and Target 8 (unmanned aerial vehicle), with their ranking positions swapped, while the ranking order of the other targets remains entirely consistent between methods. Specifically, the assessment consistency of the two methods reaches 75%.
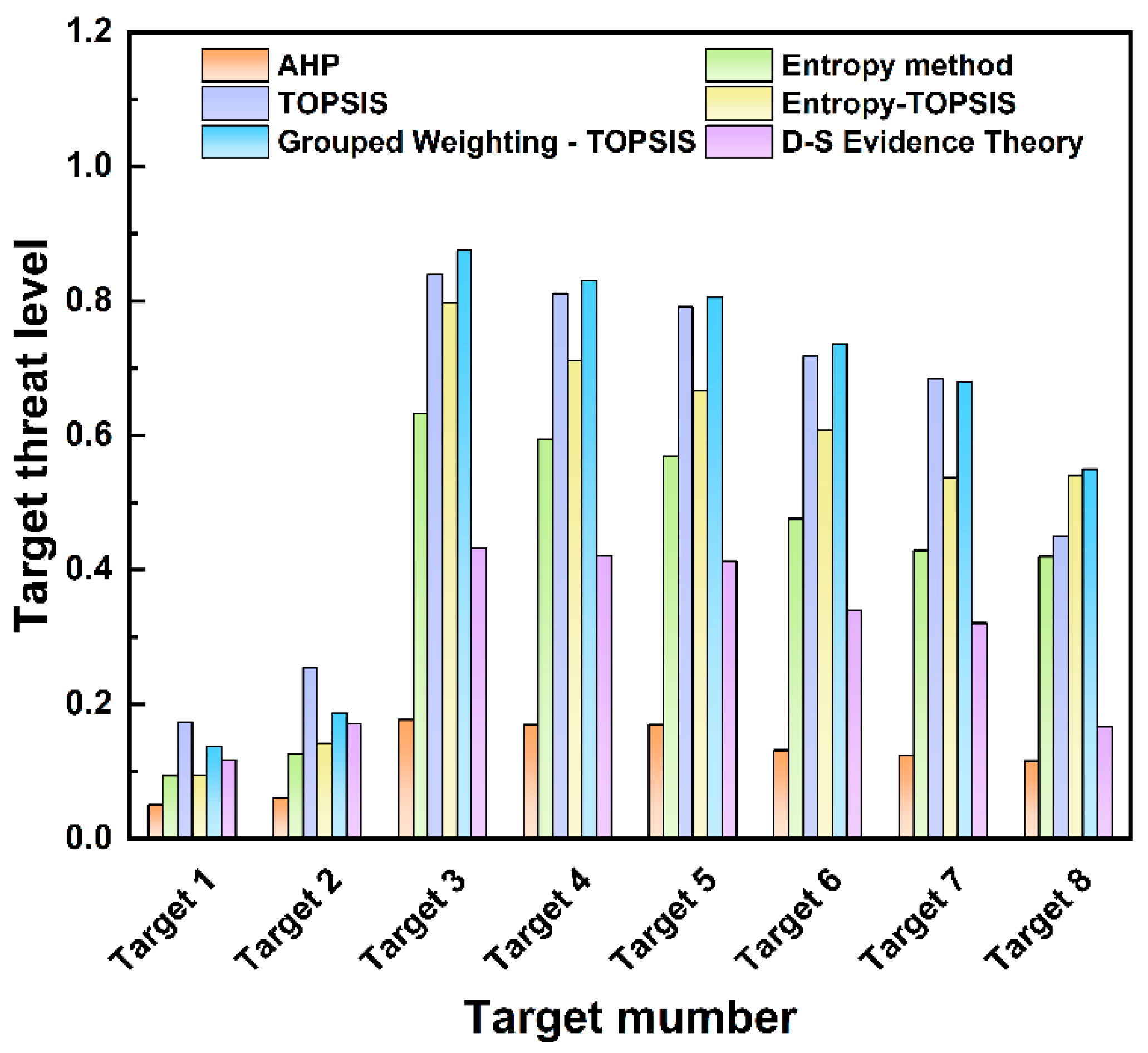
The reasons for the discrepancy are as follows: Based on combined weights, the TOPSIS method amplifies the contribution of dominant indicators (for example, the weight of target distance accounts for 24.6%), leading to the threat values of high-threat targets being significantly higher than those of other targets. D-S evidence theory, on the other hand, regards the three types of weights as independent evidence sources and dynamically adjusts the weights through conflict coefficients and orthogonal sum rules. The normalization factor weakens the impact of conflicting evidence, resulting in more balanced outcomes. Secondly, in the TOPSIS method, the inherent characteristics of the target have a substantial influence on the evaluation of the threat value; for instance, the weight of the target type reaches 24.6%, which significantly affects the final calculation of the threat value. D-S evidence theory reduces the dominance of a single indicator through fusion and increases the proportion of dynamic indicators (such as speed and distance). Finally, the TOPSIS method relies on preset weights and has low fault tolerance for data uncertainty. D-S evidence theory quantifies uncertainty through the Bel(H) and Pl(H) intervals, thereby reducing the impact of extreme values. The threat assessment results of the proposed TOPSIS method based on combined weighting and D-S evidence theory are compared with those of the traditional TOPSIS, entropy-weighted TOPSIS, entropy weight, and AHP methods. The results of the comparison are shown in Figure 8, with detailed threat level data listed in Table 14.
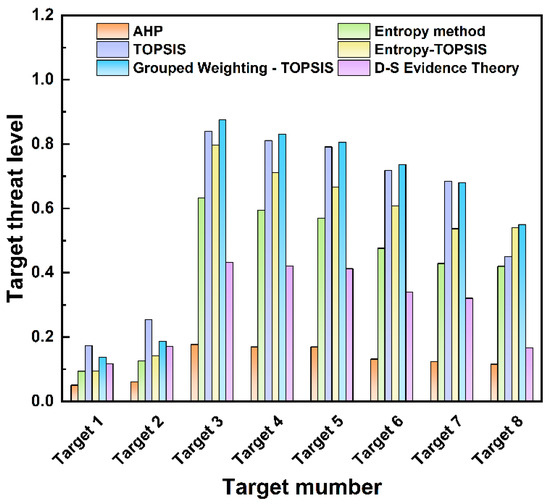
Figure 8.
Comparison of threat assessment results of different methods.

Table 14.
Threat degrees calculated by different methods.
Analysis of Figure 8 and Table 14 reveals that when measuring threat levels using the AHP method, different targets have relatively close threat levels—for example, Targets 4 and 5 both have a threat level of 0.170. The entropy weight method shows a significant gap between low- and high-threat targets, though differences among targets with the same threat level are less pronounced (e.g., Target 1 has an extremely low threat level of 0.094). The simulation results indicate consistent outcomes across methods. Notably, the results from D-S evidence theory are more neutral, effectively integrating reasonable components from each weighting method while avoiding large deviations caused by uncertainties in individual approaches. This illustrates that both proposed methods can accurately identify the threat level of hexacopter UAVs in the threat assessment of LSS targets, which verifies the model’s ability to capture key threat features and demonstrates its rationality and credibility. The above analysis indicates that the TOPSIS method provides a significant degree of discrimination in threat values, making it suitable for environments where rapid distinction between high- and low-threat targets is required. In contrast, D-S evidence theory has strong anti-interference ability, which makes it applicable to environments where a balance between subjective and objective uncertainties is needed.
4.1.4. Parameter Sensitivity Analysis
To verify the rationality of the membership function parameters, we conducted a comprehensive sensitivity analysis to evaluate the robustness of the final threat level ranking when the most critical parameters are changed. The One-Factor-At-a-Time (OFAT) method was used to analyze the simulation data in 4.1. Two objective membership functions (target altitude and target distance) and two subjective membership functions (target type and target maneuverability) from Section 2.2 were selected as the targets for sensitivity analysis. Each parameter was varied based on its defined baseline value (50 m, 100 m, 1.0, and 0.8, respectively), while all other parameters remained unchanged. The entire evaluation workflow was executed for each perturbed value, and the new threat levels were recorded.
The sensitivity verification results were quantitatively analyzed through three methods: (1) the Average Rank Change (ARC) of all targets; (2) Spearman’s rank correlation coefficient (ρ) between perturbed and baseline rankings; (3) stability of the top three high-threat targets.
Using the data in Table 6 as the baseline input, 2–5 values were selected for each parameter to be analyzed within its fluctuation range. Subsequently, a complete threat assessment model was run for each parameter value, obtaining the threat level rankings of all eight targets, which were finally compared and analyzed with the results in Table 12. The quantitative results of each parameter’s sensitivity are shown in Table 15.

Table 15.
Sensitivity analysis of membership function parameters.
This analysis indicates that the proposed threat assessment model is highly stable against perturbations of key parameters in objective membership functions. The Average Rank Change (ARC) values are small (ARC < 0.5), and within the test range, Spearman’s rank correlation coefficient ρ remains within the ideal range (ρ > 0.97). The top three most threatening targets remained consistent.
In contrast, the threat value of the hexacopter UAV within the subjective membership functions showed higher sensitivity. However, even with a 10% reduction in threat value, only the rankings of Targets 4 and 5 were changed, without affecting the identification of the target posing the most severe threat. This sensitivity analysis demonstrates that the membership function parameters determined in this study are not arbitrarily selected but possess a certain degree of stability within a reasonable value range. This conclusion lays the foundation for the subsequent validation of the model’s effectiveness and reliability.
4.2. Threat Level Assessment and Analysis of Measured Data
4.2.1. Pretreatment of Measured Data
To validate the effectiveness of the two proposed methods, a threat assessment was conducted on experimentally collected data. All data in this experiment were derived from hexacopter UAV targets, as shown in Figure 9, so all static indicators are identical. Here, no analytical modeling was performed for static indicators of hexacopter UAVs—only dynamic indicators were analyzed and modeled. After target recognition of UAV visible-light images, a model for target dynamic threat indices was developed based on measured experimental data. Table 16 lists the measured target data.

Figure 9.
Image acquired by hexarotor UAV.

Table 16.
Attribute situation values of hexarotor UAVs.
It is acknowledged that the measured data used in this study have certain limitations. The experimental data were collected for only one LSS target type—hexacopter UAVs; thus, the measured data only included dynamic threat indicators (i.e., target distance, altitude, and projected area). Static or discrete attributes such as target type, query capability, and protected objects were not detected in the measured data. This limitation mainly stems from the challenges in acquiring comprehensive, real-time multi-attribute data covering various LSS target types in practical operational environments. Although the measured data failed to effectively demonstrate the validity of static or discrete attributes in threat level assessment, such attributes are mostly subjective factors, whose accuracy mainly relies on the knowledge and experience-based judgments of domain experts. Therefore, the measured data on threat level ranking results for specific LSS targets (hexacopter UAVs), combined with reasonable subjective experience, are sufficient to verify the model’s effectiveness in evaluating high-priority dynamic characteristics.
The attribute values in Table 16 are quantified to obtain the target attribute decision matrix shown in Table 17.

Table 17.
Experimental target attribute decision matrix.
4.2.2. Threat Level Assessment Results
Analysis shows that the importance of the three indicators relative to each other is as shown in Table 18.

Table 18.
Relative importance of indicators.
Using Equations (17)–(30), the combined weight vector v for each indicator is calculated:
Based on the obtained combined weight vector v, the TOPSIS method is used to calculate and rank the threat levels of the seven hexacopter UAV targets. The results are listed in Table 19 and Table 20.

Table 19.
Positive and negative ideal solutions.

Table 20.
Target threat ranking results.
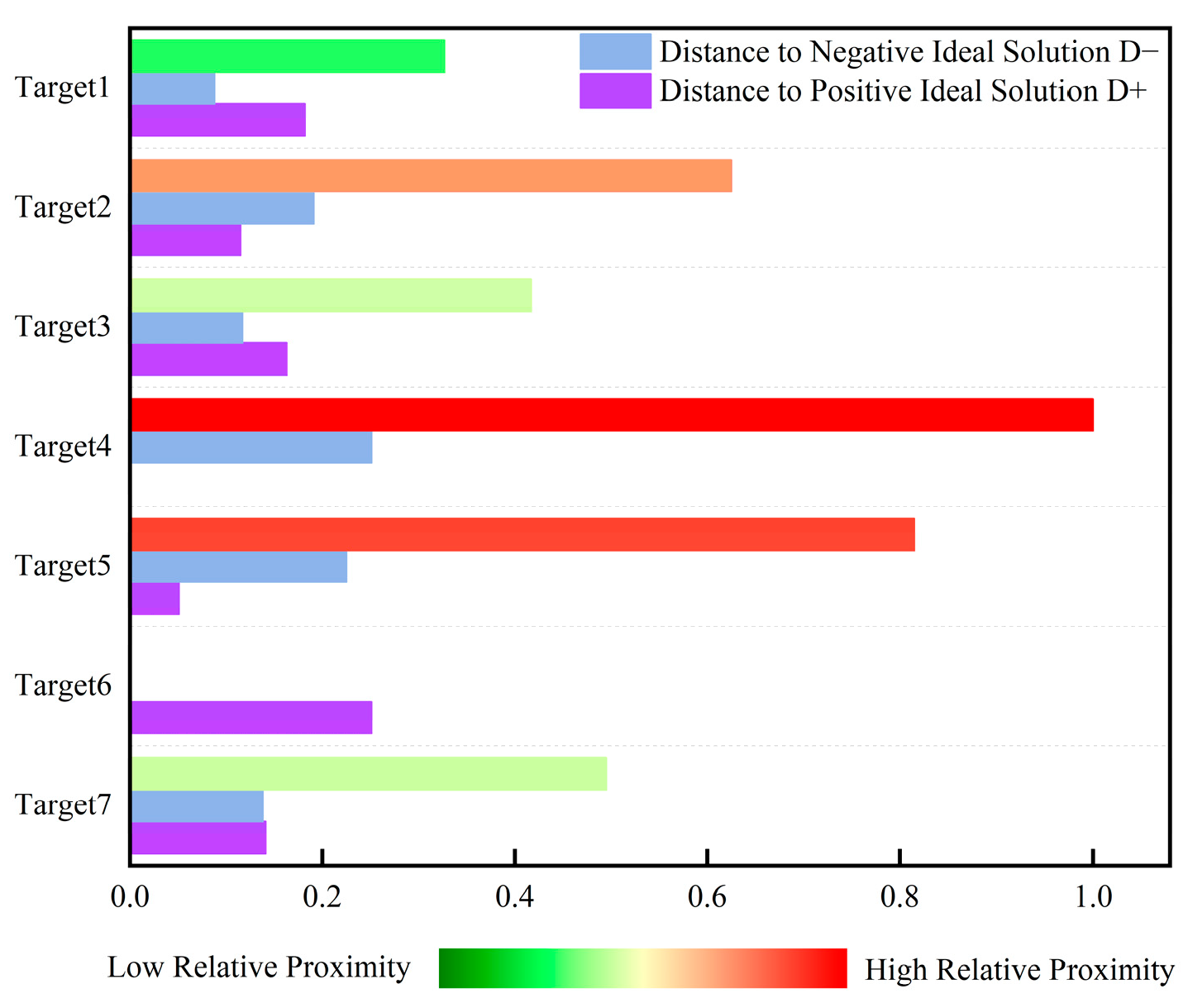
It can be seen from Figure 10 that the closeness degree of Target 4 is 1, Target 5 is 0.815, Target 2 is 0.625, Target 7 is 0.495, Target 3 is 0.417, Target 1 is 0.327, and Target 6 is 0.251. Thus, the threat levels of the seven incoming targets are ranked as follows: Target 4 > Target 5 > Target 2 > Target 7 > Target 3 > Target 1 > Target 6. Taking Target 4 as an example, its closeness degree of 1 indicates that it poses the greatest threat among all targets. Analysis of situational data reveals that Target 4 has a minimal vertical altitude and horizontal distance to the visible-light detection platform, and its imaging area in the detectors is the largest. These characteristics justify the maximum threat level for Target 4, consistent with the simulation results.
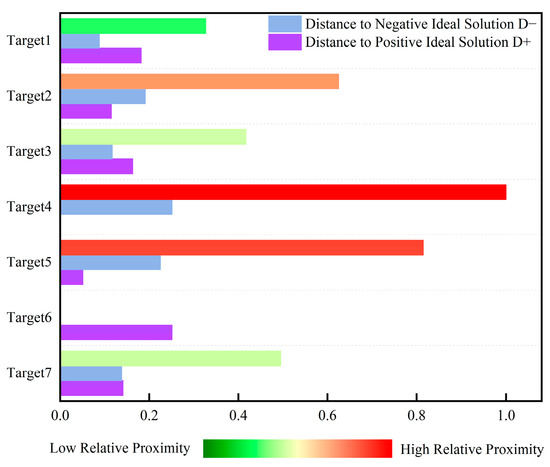
Figure 10.
Histogram of TOPSIS evaluation target threat level ranking based on actual measurement data.
Using D-S evidence theory, each BPA is first defined as m1(Hj) = W1, m2(Hj) = W2, and m3(Hj) = W3. Then, applying the orthogonal sum rule, we first calculate k123 and m123:
Finally, the threat level calculation results for each target are listed in Table 21.

Table 21.
Calculation results of threat degree for each target.
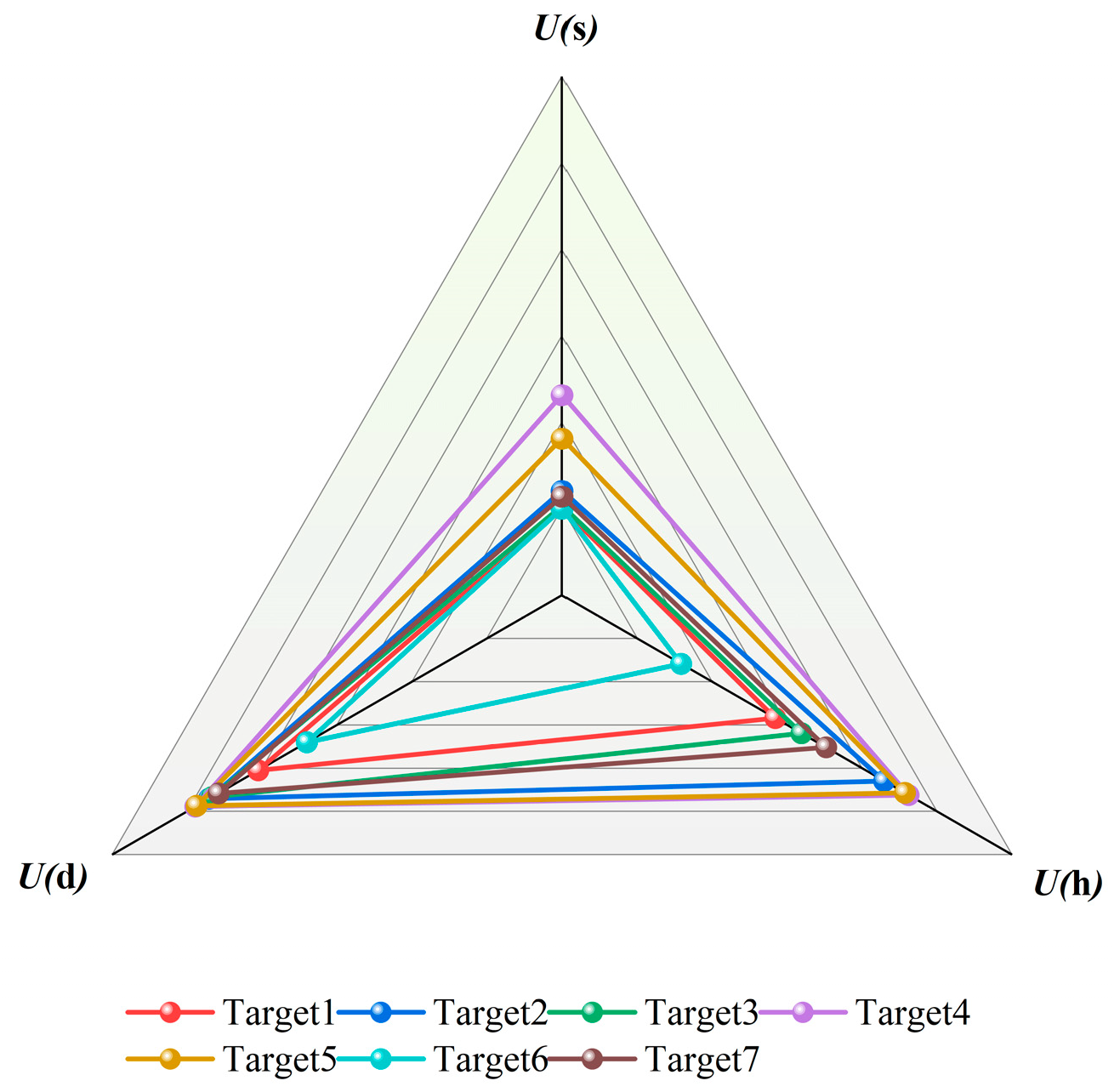
Based on the attributes and specific values of the measured data, the radar chart for evaluating the threat level of each target is shown in Figure 11. It can be seen from the figure that for hexacopter UAV targets, subjective factors such as target type and maneuverability remain fixed values. Factors affecting the target threat level are largely objective factors, such as target altitude, target distance, and target area. The target area factor is related to target speed and angle and, as shown in the radar chart, varies in a small range for targets of the same type; thus, the factors affecting the target threat level depend on changes in target altitude and target distance.
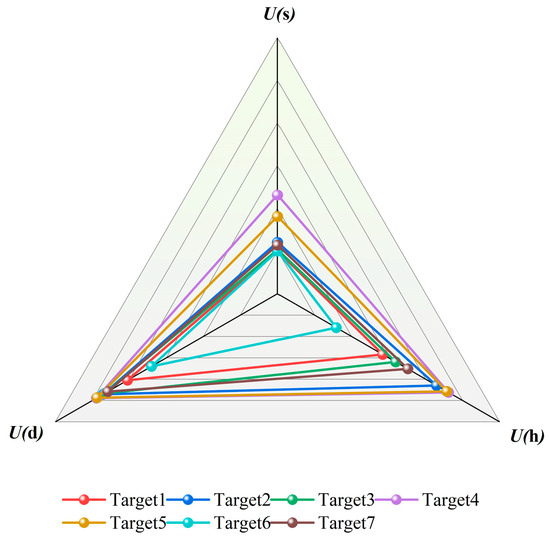
Figure 11.
Radar chart of measured target threat assessment.
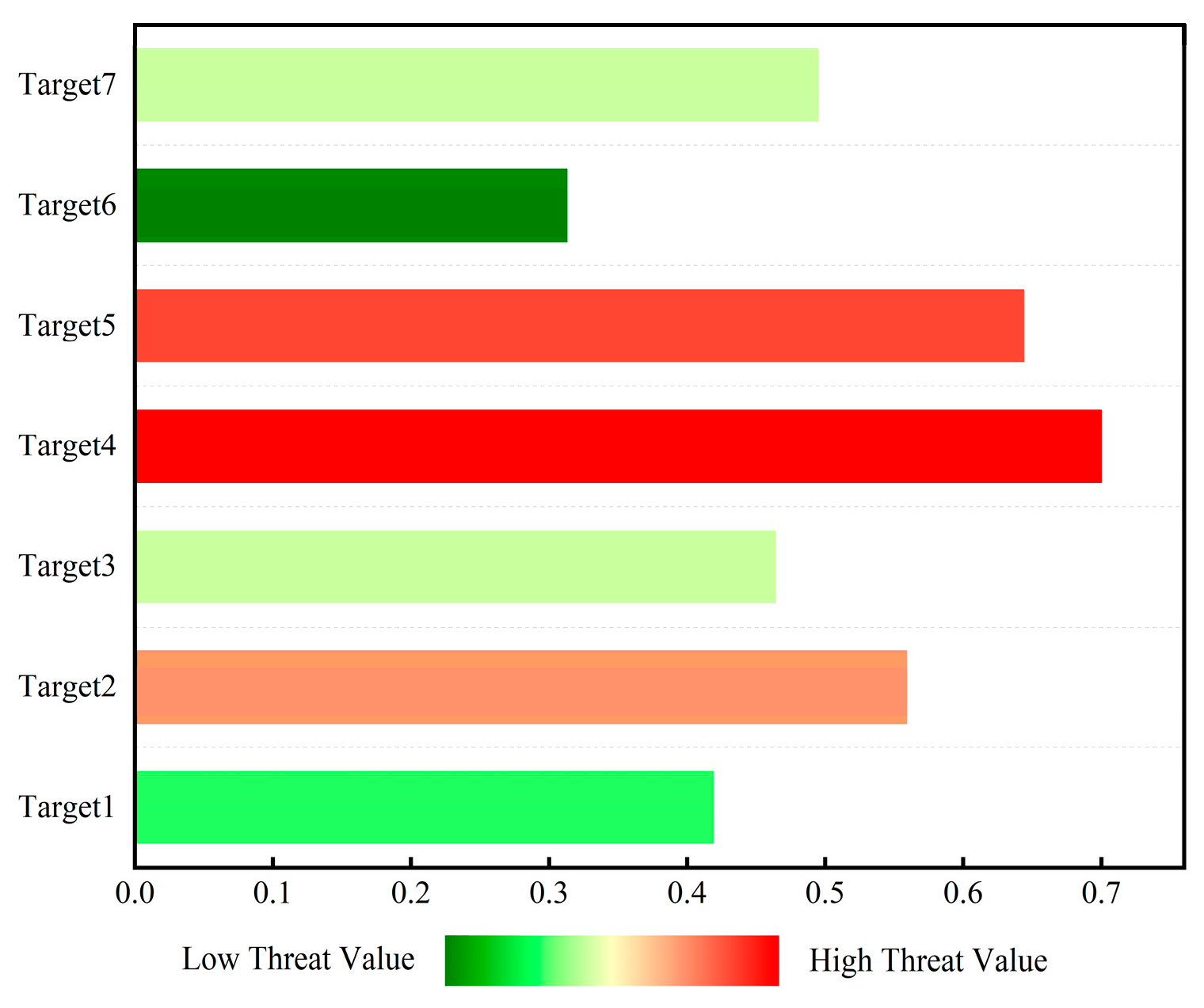
Figure 12 shows the histogram of threat level ranking evaluated by D-S evidence theory. As shown in the figure, Target 4 has a threat value of 0.7, shown in deep red, indicating the highest threat ranking. Targets 5 and 2 have threat values of 0.644 and 0.559, respectively. The red color indicates that these two targets have a lower threat ranking than Target 4 but are also in a threatening state. However, Target 6 has a threat value of 0.313, shown in deep green, indicating that its threat level is low and it is in a safe state.
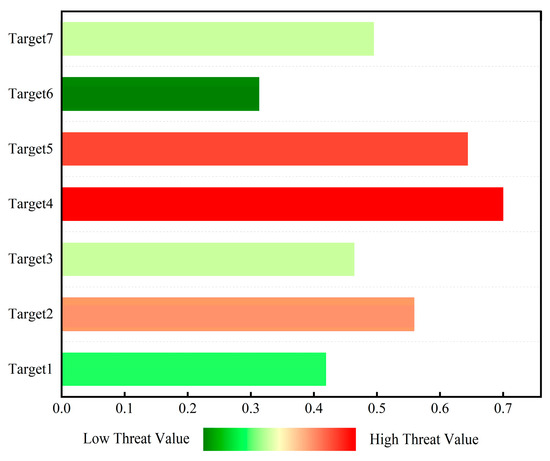
Figure 12.
Histogram of threat level ranking evaluated using D-S evidence theory based on measured data.
4.2.3. Comparative Analysis
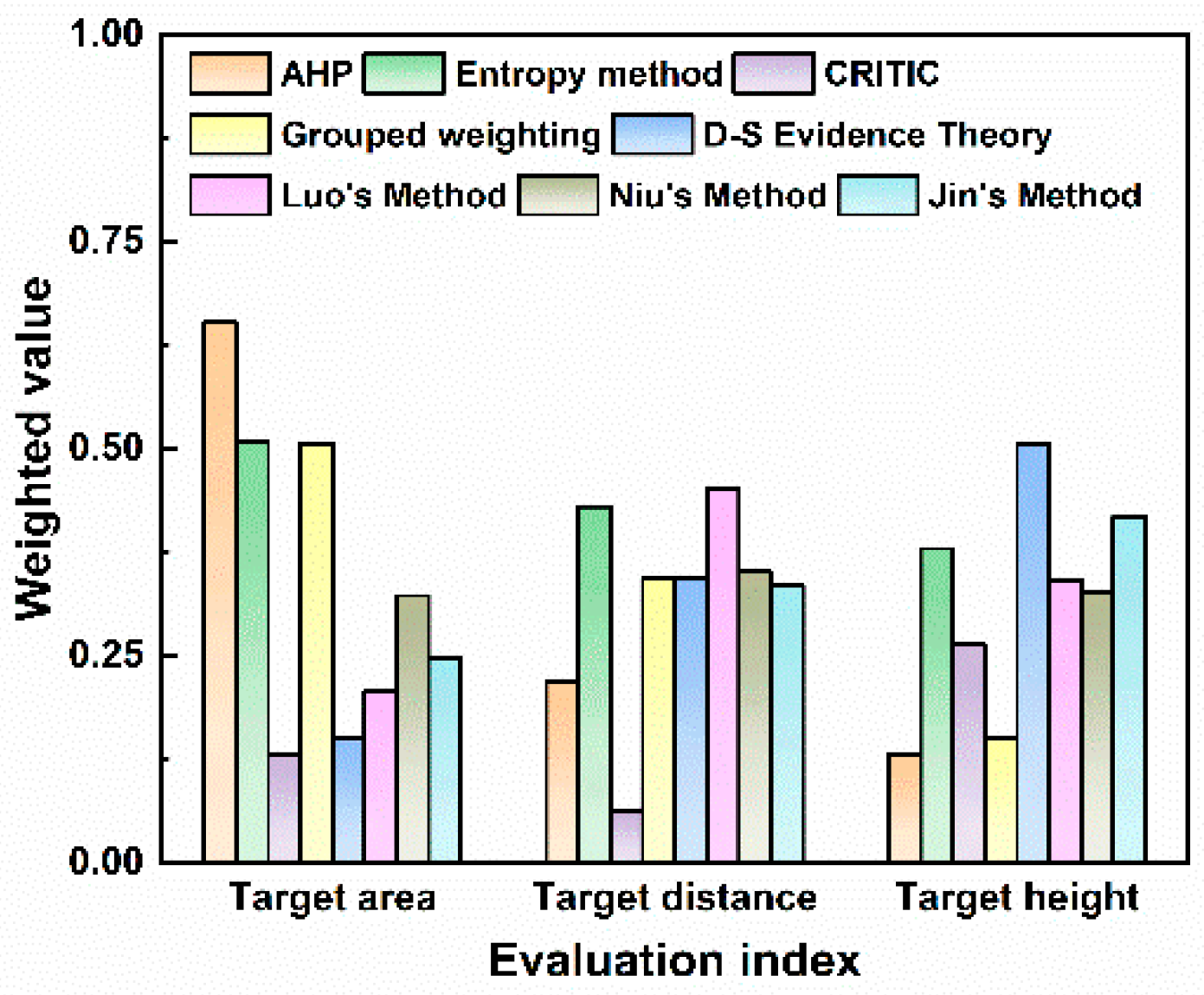
The measured environmental configuration for UAVs is similar to that in many related algorithm studies [29,53]. To further verify the effectiveness of the method proposed in this paper and consider the impacts of the individual AHP, entropy, CRITIC, and TOPSIS methods on the target threat assessment results, the measured data are taken as input, and the calculation and ranking results of the two methods for target threat assessment are compared with those reported in references [29,53]. The weight results obtained by each weighting method are shown in Figure 13.
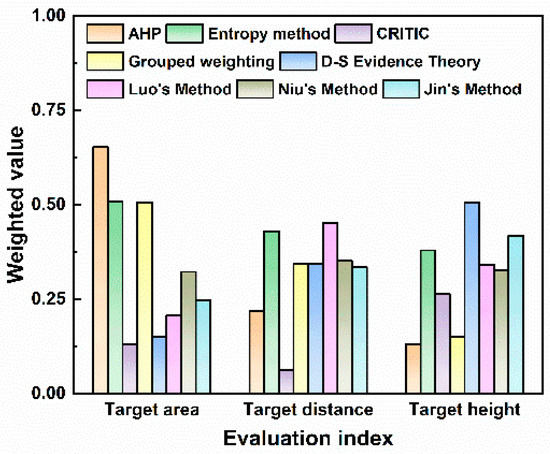
Figure 13.
Weight distribution of different methods.
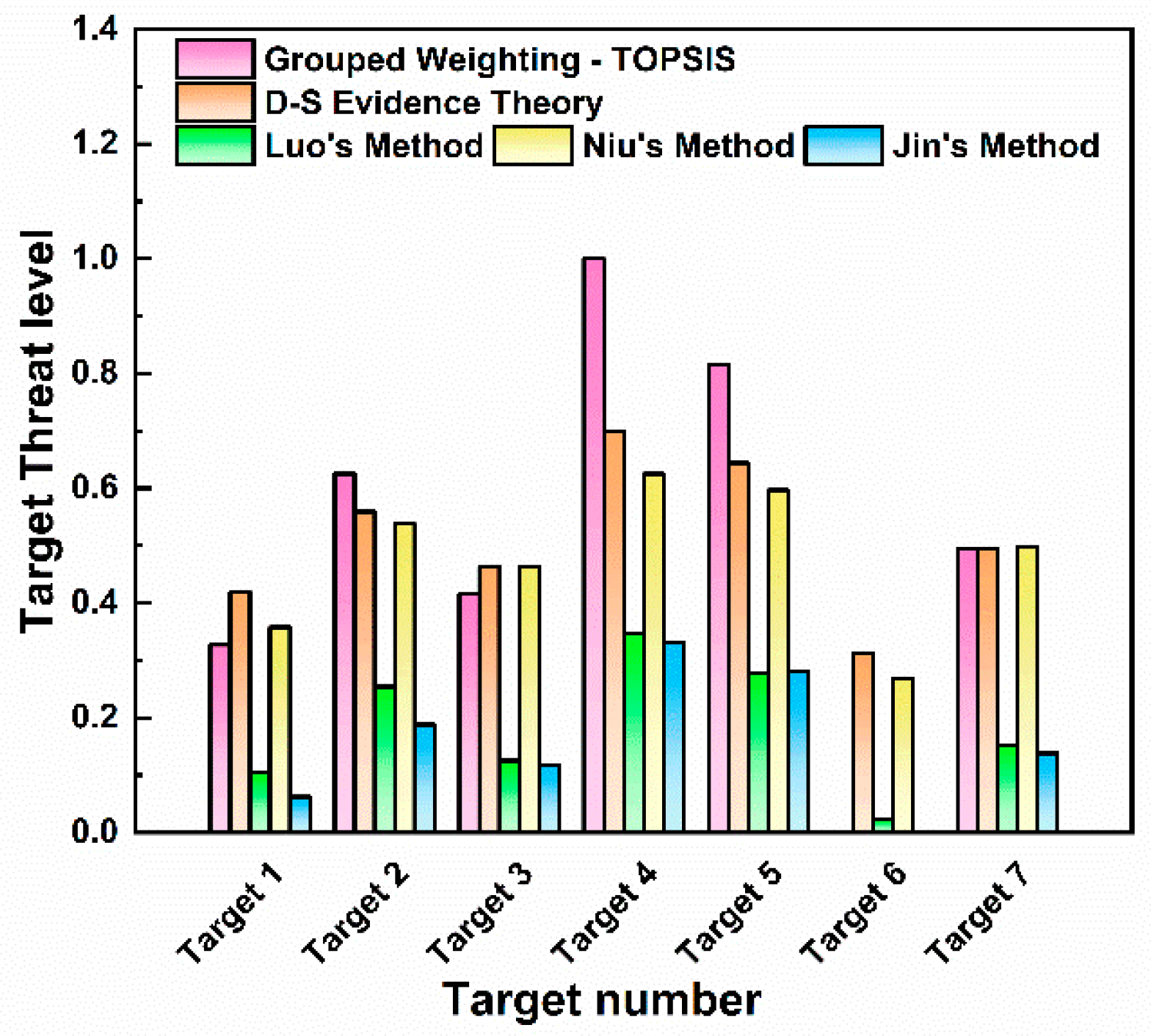
The quantitative values of weight allocation reflect the different focuses of various algorithms on multiple attributes of the target. Differences in weight allocation can significantly affect the core logic and results of threat assessment. As shown by the comparison of different algorithms, the AHP method assigns the highest weight to the target area (0.63). The target area is a comprehensive reflection of the target type and maneuverability. Its excessive focus on the target area means that the AHP can be easily disturbed by decoy targets in the process of target threat assessment, which ultimately leads to errors in the ranking of multi-target threat levels. The entropy weight method focuses on the weight of the target distance, so the algorithm provides a passive defense response and easily overlooks high-threat target types. The combined weighting method assigns a weight of 0.41 to target distance and 0.39 to target height. This indicates that the combined weighting method allocates weights in a more balanced manner among different evaluation indicators and can account for the requirements of early-warning distance and high-altitude defense. With D-S evidence theory, the highest weight is assigned to target height (0.50), making this algorithm more suitable for actively scanning low-altitude detection areas. Among the three improved algorithms in the literature, Luo’s algorithm determines the subjective and objective threat factor weights of LSS targets based on AHP and information entropy. This method relies on a complete expert knowledge base, and the reliability will decrease with incomplete expert knowledge bases. Niu’s method allocates weights of 0.322, 0.351, and 0.327 to the three evaluation indicators, respectively. The weight allocation with this method is very balanced, which makes the algorithm less sensitive to key factors. Jin’s method focuses on the measurement of dynamic indicators and allocates higher weights to target height and target distance.
The threat level calculation and ranking results of the two methods in this paper and the three comparison algorithms are shown in Figure 14. The ranking of threat levels for the seven targets is the same for all algorithms: Target 4 > Target 5 > Target 2 > Target 7 > Target 3 > Target 1. Through the analysis of the histogram, it is found that the TOPSIS threat assessment based on combined weights results in a maximum target threat value of 1 and a minimum of 0. This leads to a large gap in threat values between multiple targets, which can easily cause judgment errors when subject to external interference. In contrast, D-S evidence theory can avoid large deviations caused by irrational factors. The threat values of each target fall within the range of 0.3–0.7, showing a relatively distinct hierarchical distribution. Luo’s method yields relatively low threat values for all targets, with the maximum being 0.346 and the minimum 0.104. This reduces the sensitivity of the algorithm in target threat assessment, as the differences in threat levels between targets are small, so its sensitivity in dynamic target monitoring needs further investigation. Niu’s method is relatively sensitive in responding to UAV threats, but it involves extensive calculation, which may pose computational challenges when dealing with large-scale data. Jin’s method uses the VIKOR model for dynamic attribute threat assessment, and its evaluation results for target motion state information are more reasonable and effective. However, for the discrete measured data in this study, its evaluation results for target threats are relatively low, with the maximum target threat value being only 0.331 and the minimum being 0. Thus, this algorithm is not suitable for the assessment of discrete target threat detection in this study.
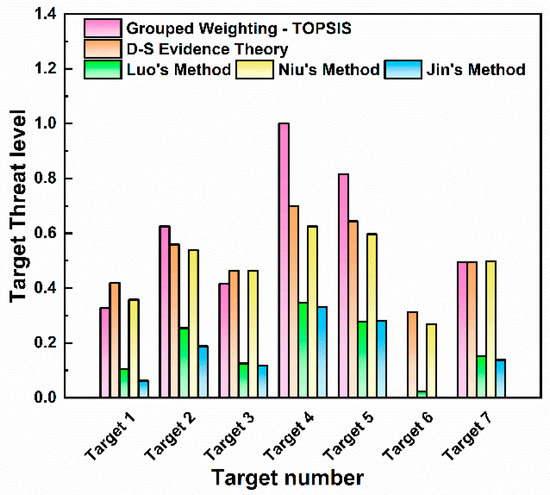
Figure 14.
Comparison of threat assessment results for each target.
4.3. Real-Time Performance Verification and Analysis
4.3.1. Experimental Setup
The interception of LSS targets requires the threat assessment system to have extremely high real-time performance. To verify the practical feasibility of the proposed fusion evaluation framework in actual combat and compare the performance of the two evaluation paths (TOPSIS and D-S evidence theory), this section presents the results of strict empirical tests and theoretical analysis of their computational efficiency.
To simulate the actual deployment environment, all experiments were performed on a portable computing platform equipped with an Intel Core (Santa Clara, CA, USA) i7-11800H @ 2.30 GHz CPU and 16 GB RAM. Core matrix operations were conducted in the Matlab environment. The test data included two parts: the eight simulated targets from Section 4.1 and the seven measured targets from Section 4.2 as benchmark data; to evaluate algorithm scalability, large-scale datasets with target scales of 20, 50, 100, and 200 were generated through simulation. The threat attribute dimension was set to 7 in all datasets. The execution time of the complete evaluation process was measured. The process was divided into two stages: weight calculation and threat assessment. To eliminate errors, each dataset was run 200 times, and the average processing time and standard deviation were recorded.
4.3.2. Analysis of Real-Time Performance Results
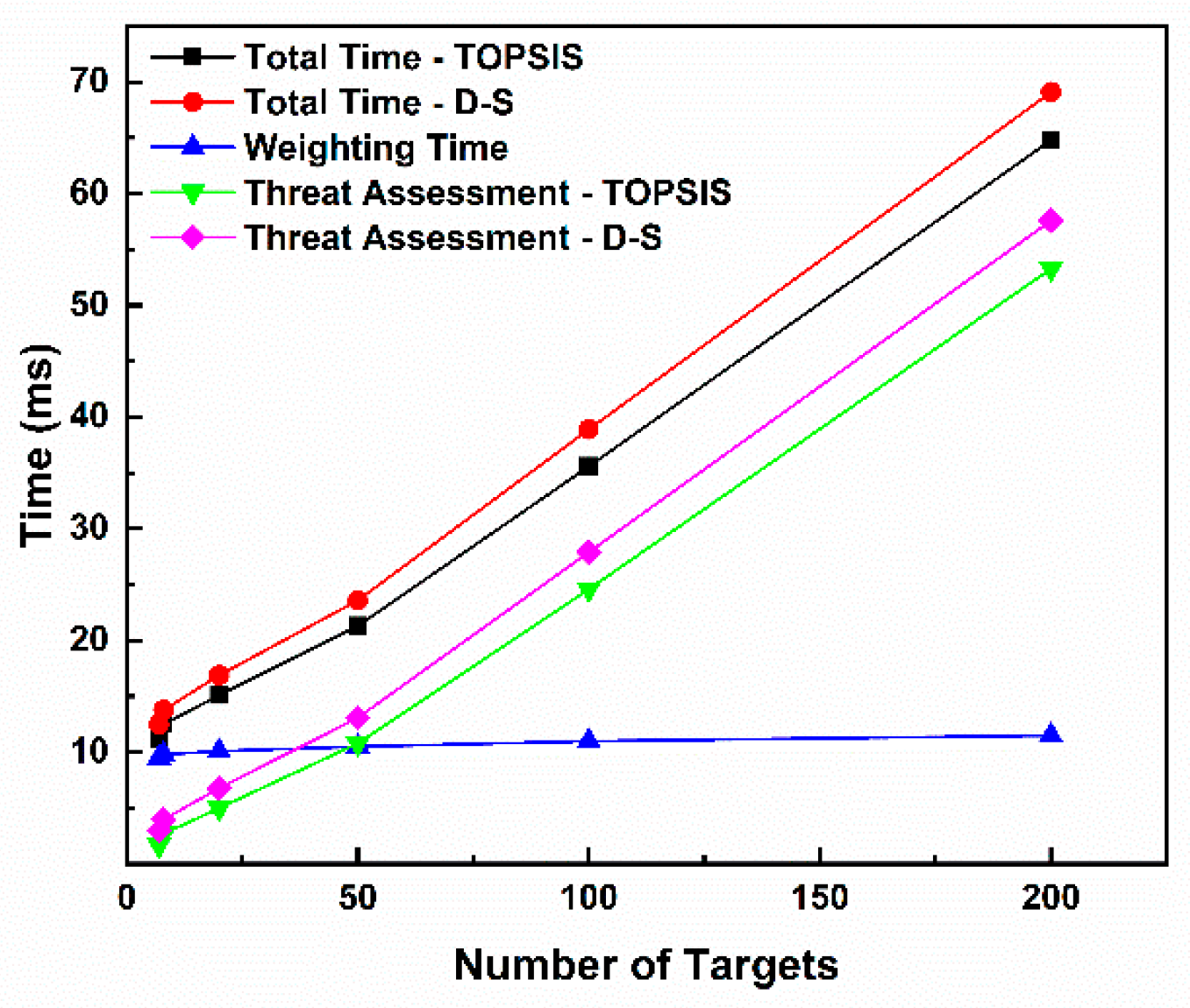
The measured processing time is shown in Table 22, and its growth trend with the number of targets is shown in Figure 15. Analysis of Figure 15 reveals that both evaluation paths exhibit millisecond-level response speeds. In the benchmark scenario with eight targets, the TOPSIS path takes 12.5 milliseconds, and the D-S path takes 13.8 milliseconds, providing extremely ample response time for the defense system. The total processing time of both paths shows a linear growth relationship with the number of targets (m). Even in large-scale swarming scenarios with up to 200 targets, the processing times of the TOPSIS and D-S paths are only 64.8 milliseconds and 69.1 milliseconds, respectively, which are still far below the typical decision cycle. The TOPSIS path is slightly faster than the D-S path in all test scenarios, with a time difference ranging from approximately 1.3ms to 4.3ms. This is because, after fusing weights, the D-S path needs to calculate the weighted sum for each target, which involves slightly more calculation steps than the distance calculation in TOPSIS. However, this minor performance gap is negligible in actual decision-making scenarios. The time consumed in the weight calculation stage (shared) is less affected by the number of targets, which is consistent with the fact that its complexity mainly depends on the fixed number of indicators (n = 7). The time consumed in the threat assessment stage (TOPSIS or D-S) increases linearly with the number of targets, being the main computational load of the algorithm.

Table 22.
Data processing test time.
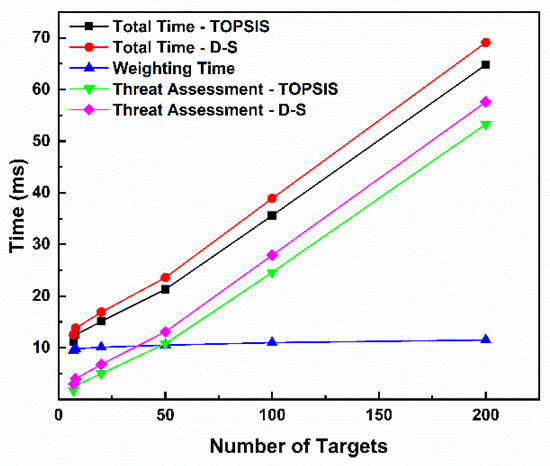
Figure 15.
Trend in response time with increasing number of targets.
A typical air defense command and control system requires the threat assessment process to be completed within 1 to 3 s. Both evaluation paths in the threat assessment framework proposed in this study possess strong real-time processing capabilities, fully meeting the timeliness requirements for rapid and large-scale interception decisions for LSS targets in actual combat environments. Path selection can be based on specific tactical needs rather than performance constraints. The comparative analysis of the TOPSIS method and D-S evidence theory provides practical insights for system deployment. The TOPSIS method, with its significant threat value differentiation capability and power-efficient computation, is particularly suitable for early warning and rapid screening scenarios. It can clearly distinguish between high-threat and low-threat targets, making it well-suited for such time-critical, high-volume screening tasks. In contrast, D-S evidence theory excels in high-risk, uncertain environments. When protecting high-value assets from complex threats that may employ electronic countermeasures, operators benefit not only from threat values but also from their associated uncertainty ranges [Bel(H), Pl(H)]. A target with a moderate threat value but a wide belief–plausibility interval indicates a high degree of information conflict; this inherent ability to quantify and reveal uncertainty makes D-S theory more advantageous in decision-making under ambiguous conditions.
5. Conclusions
Based on expert experience, the AHP can be used to subjectively evaluate target attributes. In contrast, the information entropy weight and CRITIC methods can objectively reflect the variability in target attributes, enabling rapid responses to dynamic task planning and maneuverability. Therefore, they are often used for threat estimation when target information is incomplete. This study uses two models—the combined weighting method based on deviation coefficients and D-S evidence theory—to fuse three types of subjective and objective weights, thereby obtaining more reliable evaluation results. The threat levels of LSS targets are calculated using both TOPSIS and D-S evidence theory. Finally, the reliability and effectiveness of the two models are verified through simulation analysis and measured data, providing a reference for LSS target interception decision-making. The main conclusions obtained are as follows:
(1) For the evaluation of LSS target threat levels, the threat level rankings obtained by D-S evidence theory (using basic probability assignments (BPA) and indicator weights) are completely consistent with those of TOPSIS based on the combined weighting method with deviation coefficients. This consistency demonstrates that both methods equally capture core threat features in scenarios without indicator conflicts. The dynamic adjustment of subjective–objective weight ratios via deviation coefficients essentially involves linear weighted summation, while D-S evidence theory achieves evidence fusion through Dempster’s combination rule. Although their mathematical logics differ, in scenarios where all indicators positively support threat levels and no evidence conflict exists, the weighted sum is equivalent to the D-S belief function calculation. Thus, their results align, both providing reliable bases for tactical decision-making.
(2) The combined weighting method based on deviation coefficients calculates the consistency between weighting methods through the dynamic fusion mechanism of the weight deviation similarity index rlk and allocates combination coefficients according to the degree of correlation, ensuring that the weight allocation between subjective experience and objective data is more in line with actual scenarios. In contrast, D-S evidence theory reduces the influence of contradictory evidence through the conflict coefficient k, balances differences between subjective and objective sources, and prevents dominance by a single indicator, aligning with the comprehensive judgment of multisource evidence.
(3) Simulation analysis and comparative experiments show that the two methods proposed in this paper can comprehensively consider the capabilities and intentions of multiple LSS targets and accurately provide threat assessment results based on different LSS movement state information. The proposed methods can be directly applied to real-world low-altitude airspace defense systems.
The limitations of the established expert knowledge base accordingly decrease the reliability of the evaluation. Future in-depth research on the movement laws of LSS targets will continually enrich the expert knowledge base. Future work will focus on three key areas: (1) continuously enrich and improve the expert database and incorporate new threat assessment factors; (2) establish the structure of new threat assessment factor quantification functions and optimize their parameters to improve accuracy; (3) adopt incremental computing technology to accelerate the processing of large-scale data and improve the dynamic update speed of the evaluation system.
Author Contributions
W.W.: Methodology: Software, Data curation, Writing—original draft. W.J.: Supervision, Writing—review and editing. A.L.: Supervision, Writing—review and editing. X.L.: Conceptualization, Project administration. W.L.: Visualization, Data curation. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Defense Pre-Research Foundation (Grant No. 61402060103) and the 2023 Open Project Fund of Science and Technology on Electromechanical Dynamic Control Laboratory (No. 6142601200301).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
References
- Zhou, Y. Unmanned aerial vehicles based low-altitude economy with lifecycle techno-economic-environmental analysis for sustainable and smart cities. J. Clean. Prod. 2025, 499, 145050. [Google Scholar] [CrossRef]
- Huang, C.; Fang, S.; Wu, H.; Wang, Y.; Yang, Y. Low-altitude intelligent transportation: System architecture, infrastructure, and key technologies. J. Ind. Inf. Integr. 2024, 42, 100694. [Google Scholar] [CrossRef]
- Yang, L.N.; Cao, Z.Y.; Li, Y.X. Research on UAV swarm combat composition and combat concept. Mod. Def. Technol. 2020, 48, 44–51. [Google Scholar]
- Liu, L.Z.; Zhang, J.; Zhao, Z.H. Operational conception and key technology of UAV swarm interception system. Command. Control Simul. 2021, 43, 48–54. [Google Scholar]
- Hu, J.; Fan, L.; Lei, Y.; Xu, Z.; Fu, W.; Xu, G. Reinforcement Learning-Based Low-Altitude Path Planning for UAS Swarm in Diverse Threat Environments. Drones 2023, 7, 567. [Google Scholar] [CrossRef]
- Morrison, J. Modelling and simulation of a RADAR tracking system. UNSW Canberra ADFA J. Undergrad. Eng. Res. 2018, 9, 323–327. [Google Scholar]
- Wen, N.; Zhao, L.; Su, X.; Ma, P. UAV online path planning algorithm in a low altitude dangerous environment. IEEE/CAA J. Autom. Sin. 2015, 2, 173–185. [Google Scholar] [CrossRef]
- Fang, M.; Li, L.; Zhao, C.; Guo, Y.; Qi, Z. A LSS-target detection method for urban complex environment. In Proceedings of the 2021 2nd China International SAR Symposium (CISS), Shanghai, China, 3–5 November 2021; pp. 1–5. [Google Scholar]
- Zhu, N.; Zhong, F.; Lei, X.; Niu, G.; Xie, H.; Zhang, Y. Situation Awareness and Tracking Algorithm for Countering Low-Altitude Swarm Target Threats. Remote Sens. 2025, 17, 1172. [Google Scholar] [CrossRef]
- Gao, Y.; Li, D. Consensus evaluation method of multi-ground-target threat for unmanned aerial vehicle swarm based on heterogeneous group decision making. Comput. Electr. Eng. 2019, 74, 223–232. [Google Scholar] [CrossRef]
- Gao, Y.; Lyu, N. A new multi-target three-way threat assessment method with heterogeneous information and attribute relevance. Mathematics 2024, 12, 691. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, G.; Ma, Y.; Kang, J.U.; Kwan, C. Small infrared target detection based on fast adaptive masking and scaling with iterative segmentation. IEEE Geosci. Remote Sens. Lett. 2021, 19, 700060. [Google Scholar] [CrossRef]
- Fan, Z.; Xu, Y.; Kang, Y.; Luo, D. Air combat maneuver decision method based on A3C deep reinforcement learning. Machines 2022, 10, 1033. [Google Scholar] [CrossRef]
- Lee, H.; Choi, B.J.; Kim, C.O.; Kim, J.S.; Kim, J.E. Threat evaluation of enemy air fighter via neural network-based Markov chain modeling. Knowl.-Based Syst. 2017, 116, 49–57. [Google Scholar] [CrossRef]
- Nie, X.; Yan, P.; Wang, B.; Wu, B.; Gao, C. A target threat assessment method for low-altitude aircraft. J. Phys. Conf. Ser. 2020, 1549, 052067. [Google Scholar] [CrossRef]
- Gong, H.; Yu, X.; Zhang, Y.; Liu, F. Dynamic threat assessment of air multi-target based on DBN-TOPSIS method. In Proceedings of the 2021 China Automation Congress (CAC), Beijing, China, 22–24 October 2021; pp. 6902–6907. [Google Scholar]
- Zhao, R.; Yang, F.; Ji, L.; Bai, Y. Dynamic air target threat assessment based on interval-valued intuitionistic fuzzy sets, game theory, and evidential reasoning methodology. Math. Probl. Eng. 2021, 2021, 6652706. [Google Scholar] [CrossRef]
- Zhang, H.; Wei, Z. Research on armored unit target threat assessment based on SVM. In Proceedings of the 2022 IEEE 10th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 17–19 June 2022; Volume 10, pp. 2072–2074. [Google Scholar]
- Chen, Q.; Zhao, Q.; Zou, Z.; Qian, Q.; Zhou, J.; Yuan, R. A novel air combat target threat assessment method based on three-way decision and game theory under multi-criteria decision-making environment. Expert Syst. Appl. 2025, 259, 125322. [Google Scholar] [CrossRef]
- Qu, C.; He, Y.; Ma, Q. Multiple attribute decision making method of threat assessment. Syst. Eng. Electron. 2000, 22, 26–28. [Google Scholar]
- Kong, D.; Chang, T.; Wang, Q.; Sun, H.; Dai, W. A threat assessment method of group targets based on interval-valued intuitionistic fuzzy multi-attribute group decision-making. Appl. Soft Comput. 2018, 67, 350–369. [Google Scholar] [CrossRef]
- Massignan, J.A.; London, J.B.; Bessani, M.; Maciel, C.D.; Fannucchi, R.Z.; Miranda, V. Bayesian inference approach for information fusion in distribution system state estimation. IEEE Trans. Smart Grid 2021, 13, 526–540. [Google Scholar] [CrossRef]
- Gaglione, D.; Soldi, G.; Meyer, F.; Hlawatsch, F.; Braca, P.; Farina, A.; Win, M.Z. Bayesian information fusion and multitarget tracking for maritime situational awareness. IET Radar Sonar Navig. 2020, 14, 1845–1857. [Google Scholar] [CrossRef]
- Faizi, S.; Saabun, W.; Nawaz, S.; Rehman, A.U.; Atróbski, J.W. Best-Worst method and Hamacher aggregation operations for intuitionistic 2-tuple linguistic sets. Expert Syst. Appl. 2021, 181, 115088. [Google Scholar] [CrossRef]
- Rehman, A.; Shekhovtsov, A.; Rehman, N.; Faizi, S.; Sałabun, W. On the Analytic Hierarchy Process Structure in Group Decision-Making Using Incomplete Fuzzy Information with Applications. Symmetry 2021, 13, 609. [Google Scholar] [CrossRef]
- Fei, L. D-ANP: A multiple criteria decision making method for supplier selection. Appl. Intell. 2020, 50, 2537–2554. [Google Scholar] [CrossRef]
- Lin, C.; Kou, G. A heuristic method to rank the alternatives in the AHP synthesis. Appl. Soft Comput. 2021, 100, 106916. [Google Scholar] [CrossRef]
- Jiaxin, H.; Yanwei, Z.; Huan, H.; Ming, Z.; Xi, L. AHP-Based Interactive Target Threat Level Assessment and Visualization Method. In Proceedings of the International Conference on Guidance, Navigation and Control, Harbin, China, 5–7 August 2022; pp. 456–467. [Google Scholar]
- Luo, R.; Huang, S.; Zhao, Y.; Song, Y. Threat assessment method of low altitude slow small (LSS) targets based on information entropy and AHP. Entropy 2021, 23, 1292. [Google Scholar] [CrossRef]
- Yu, X.; Wei, S.; Fang, Y.; Sheng, J.; Zhang, L. Low-altitude slow small target threat assessment algorithm by exploiting sequential multifeature with long short-term memory. IEEE Sens. J. 2023, 23, 21524–21533. [Google Scholar] [CrossRef]
- Chen, X.; Zhang, H.; Zhang, S.; Feng, J.; Xia, H.; Rao, P.; Ai, J. A space infrared dim target recognition algorithm based on improved DS theory and multi-dimensional feature decision level fusion ensemble classifier. Remote Sens. 2024, 16, 510. [Google Scholar] [CrossRef]
- Han, Q.; Pang, B.; Li, S.; Li, N.; Guo, P.-S.; Fan, C.-L.; Li, W.-M. Evaluation method and optimization strategies of resilience for air & space defense system of systems based on kill network theory and improved self-information quantity. Def. Technol. 2023, 21, 219–239. [Google Scholar] [CrossRef]
- Kamal, A.T.; Farrell, J.A.; Roy-Chowdhury, A.K. Information weighted consensus filters and their application in distributed camera networks. IEEE Trans. Autom. Control 2013, 58, 3112–3125. [Google Scholar] [CrossRef]
- Ji, H.; Lewis, F.L.; Hou, Z.; Mikulski, D. Distributed information-weighted Kalman consensus filter for sensor networks. Automatica 2017, 77, 18–30. [Google Scholar] [CrossRef]
- Li, Y.; Yao, S.; Zhang, R.; Yang, C. Analyzing host security using D-S evidence theory and multisource information fusion. Int. J. Intell. Syst. 2021, 36, 1053–1068. [Google Scholar] [CrossRef]
- Muñoz, J.; Molero-Castillo, G.; Benítez-Guerrero, E.; Bárcenas, E. Data fusion as source for the generation of useful knowledge in context-aware systems. J. Intell. Fuzzy Syst. 2018, 34, 3165–3176. [Google Scholar] [CrossRef]
- Pires, H.B.; Guimarães, L.N.F.; Rebouças, S. A Multi-Target Threat Assessment Method Based on Objective Three-Way Decision. IEEE Access. 2024, 13, 681–694. [Google Scholar] [CrossRef]
- Pires, H.B.; Guimarães, L.N.F. Dynamic Multi-Target Three-Way Threat Assessment in the Context of Air Defense. IEEE Access. 2024, 12, 141397–141413. [Google Scholar] [CrossRef]
- Liao, Z.; Wang, S.; Shi, J.; Sun, Z.; Zhang, Y.; Sial, M.B. Cooperative situational awareness of multi-UAV system based on improved DS evidence theory. Aerosp. Sci. Technol. 2023, 142, 108605. [Google Scholar] [CrossRef]
- Xu, H.; Zhao, J.; Zhang, H.; Jiang, J.; Chen, L. A Review of Target Situation Assessment Methods. In Proceedings of the International Conference on Autonomous Unmanned Systems, Shenyang, China, 19–21 September 2023; pp. 239–250. [Google Scholar]
- Deng, Y. A threat assessment model under uncertain environment. Math. Probl. Eng. 2015, 2015, 878024. [Google Scholar] [CrossRef]
- Kang, J.; Gu, Y.B.; Li, Y.B. Multi-sensor information fusion algorithm based on DS evidence theory. Chin. Inert. Technol. 2012, 20, 670–673. [Google Scholar]
- Basir, O.; Yuan, X. Engine fault diagnosis based on multi-sensor information fusion using Dempster–Shafer evidence theory. Inf. Fusion 2007, 8, 379–386. [Google Scholar] [CrossRef]
- Dong, G.; Kuang, G. Target recognition via information aggregation through Dempster–Shafer’s evidence theory. IEEE Geosci. Remote Sens. Lett. 2015, 12, 1247–1251. [Google Scholar] [CrossRef]
- Zhao, K.; Li, L.; Chen, Z.; Sun, R.; Yuan, G.; Li, J. A survey: Optimization and applications of evidence fusion algorithm based on Dempster–Shafer theory. Appl. Soft Comput. 2022, 124, 109075. [Google Scholar] [CrossRef]
- Benavoli, A.; Ristic, B.; Farina, A.; Oxenham, M.; Chisci, L. An approach to threat assessment based on evidential networks. In Proceedings of the 2007 10th International Conference on Information Fusion, Quebec, QC, Canada, 9–12 July 2007; pp. 1–8. [Google Scholar]
- Fan, C.; Fu, Q.; Song, Y.; Lu, Y.; Li, W.; Zhu, X. A new model of interval-valued intuitionistic fuzzy weighted operators and their application in dynamic fusion target threat assessment. Entropy 2022, 24, 1825. [Google Scholar] [CrossRef]
- Di, R.; Gao, X.; Guo, Z.; Wan, K. A threat assessment method for unmanned aerial vehicle based on bayesian networks under the condition of small data sets. Math. Probl. Eng. 2018, 2018, 8484358. [Google Scholar] [CrossRef]
- Qu, C.; He, Y.; Ma, Q. Threat Assessment Using Multiple Attribute Decision Making. Syst. Eng. Electron. 2000, 22, 26–29. [Google Scholar]
- Jiang, R.Q.; Bai, R.K.; Peng, Y.P. Overview of target detection technology for low slow small UAV. Winged Missile 2020, 4, 100–105. [Google Scholar]
- Guo, X. Detection and Recognition and Thread Assessment for Small Target at Low Altitude and Slow Speed; University of Chinese Academy of Sciences: Beijing, China, 2016. [Google Scholar]
- Yin, G.Y.; Zhou, X.L.; Zhang, W.J. A Threat Assessment Algorithm Based on AHP and Principal Components Analysis. Procedia Eng. 2011, 15, 4590–4596. [Google Scholar] [CrossRef][Green Version]
- Niu, Q.; Ren, S.; Gao, W.; Wang, C. A Dynamic Threat Assessment Method for Multi-Target Unmanned Aerial Vehicles at Multiple Time Points Based on Fuzzy Multi-Attribute Decision Making and Fuse Intention. Mathematics 2025, 13, 1663. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).