Composite Vulnerabilities and Hybrid Threats for Smart Sensors and Field Busses in Building Automation: A Review
Abstract
1. Introduction
- A comprehensive review of field bus systems, protocols and standards used for data transport from sensors in building automation.
- An overview of practical examples of threats to building security that have not yet been covered in the literature, especially with regard to sensor technology in usually unprotected areas.
- A thorough analysis of whether literature from the field of warfare or composite vulnerabilities has been previously applied to the field of CPSs and specifically to BASs.
- An overview of the methods that can be employed to counteract the mentioned composite vulnerabilities and hybrid threats for the benefit of researchers and practitioners in the field.
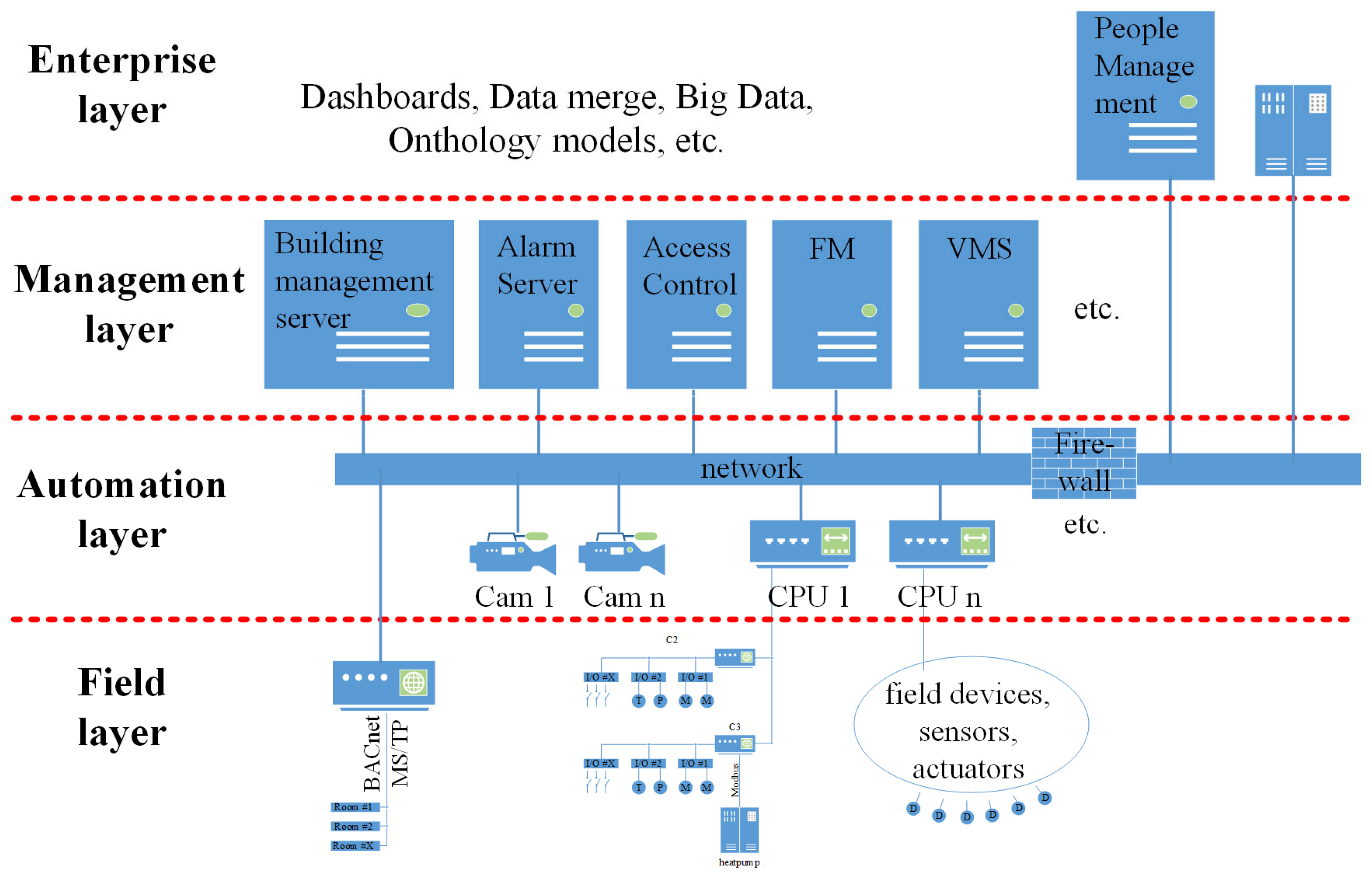
2. Building Automation and Its Communication Mechanisms
2.1. The Multi-Layered Communication in Building Automation
2.2. Cross-Level and Cross-Trade Vulnerabilities
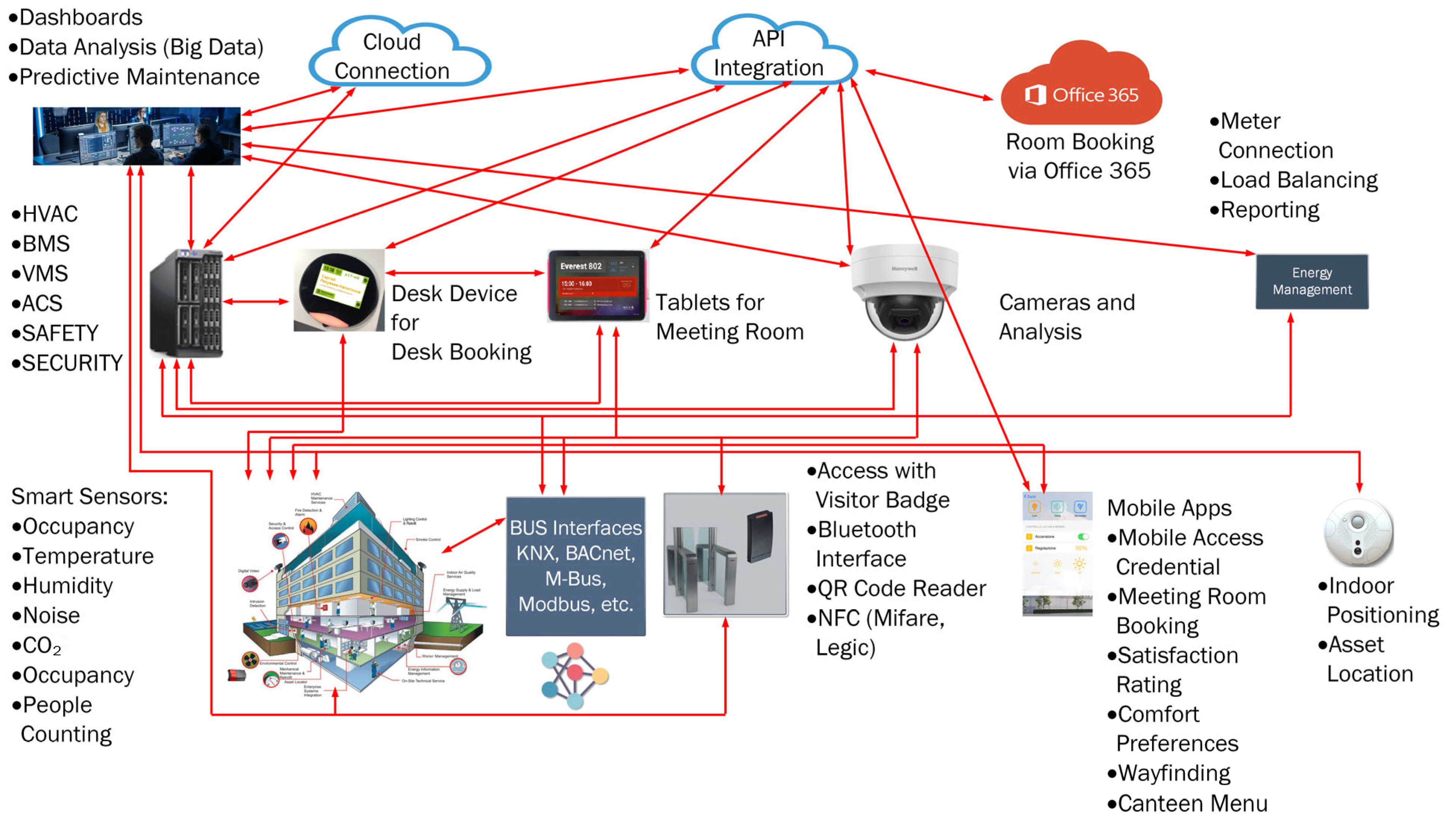
3. Practical Examples of Hybrid and Composite Vulnerabilities
- Help to understand the concept and criticality of composite vulnerabilities and hybrid threats to building automation.
- Provision of illustrative examples that have not been previously addressed in the extant literature.
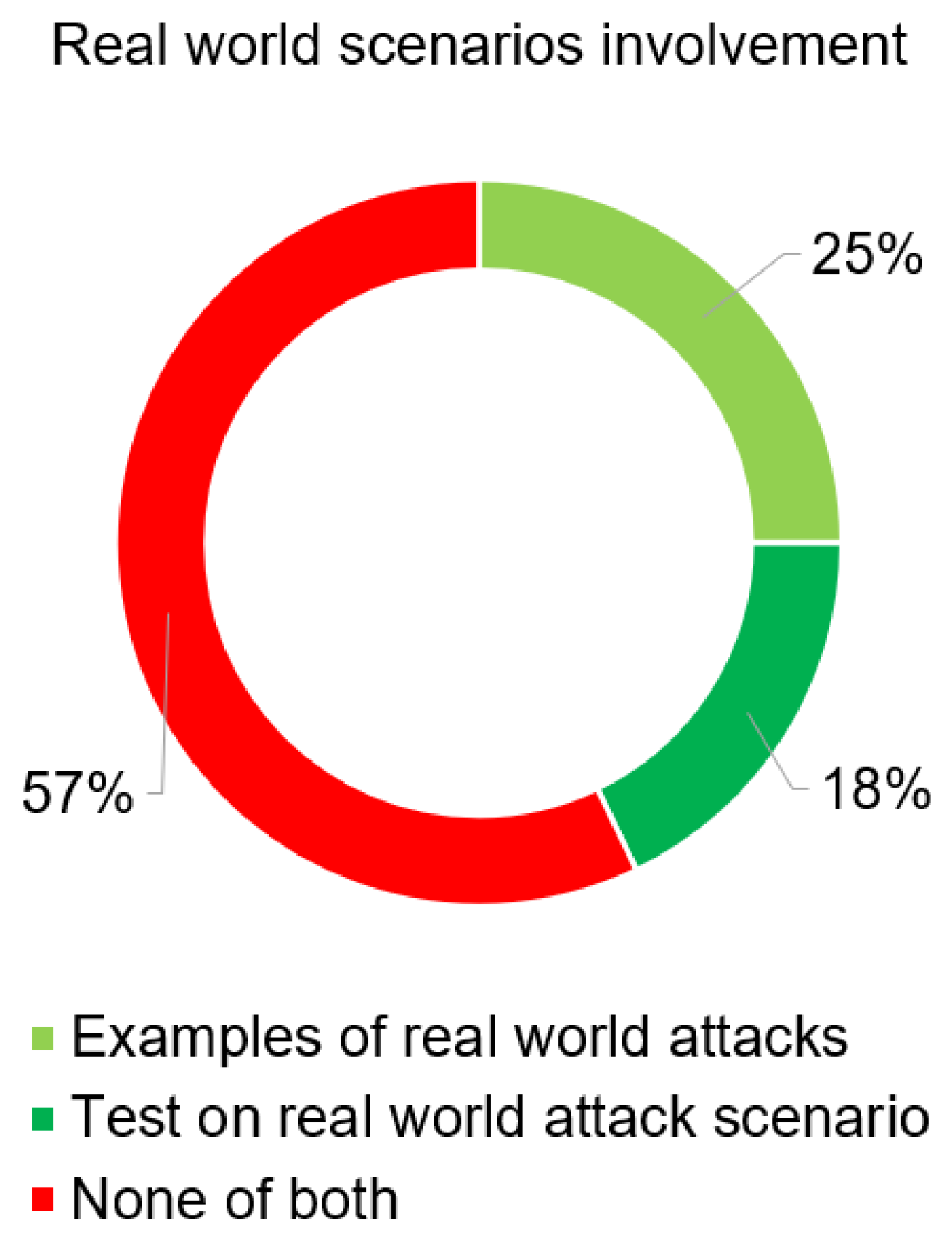
- Documentation of real-world scenarios in order to improve data management and strengthen real-time capabilities of fault detection, as these have been given very little consideration in the literature to date [30].
3.1. Example 1, Composite Vulnerabilities
3.2. Example 2, Composite Vulnerabilities
3.3. Example 3, Composite Vulnerabilities
3.4. Example 4, Hybrid Threats
4. Methodology
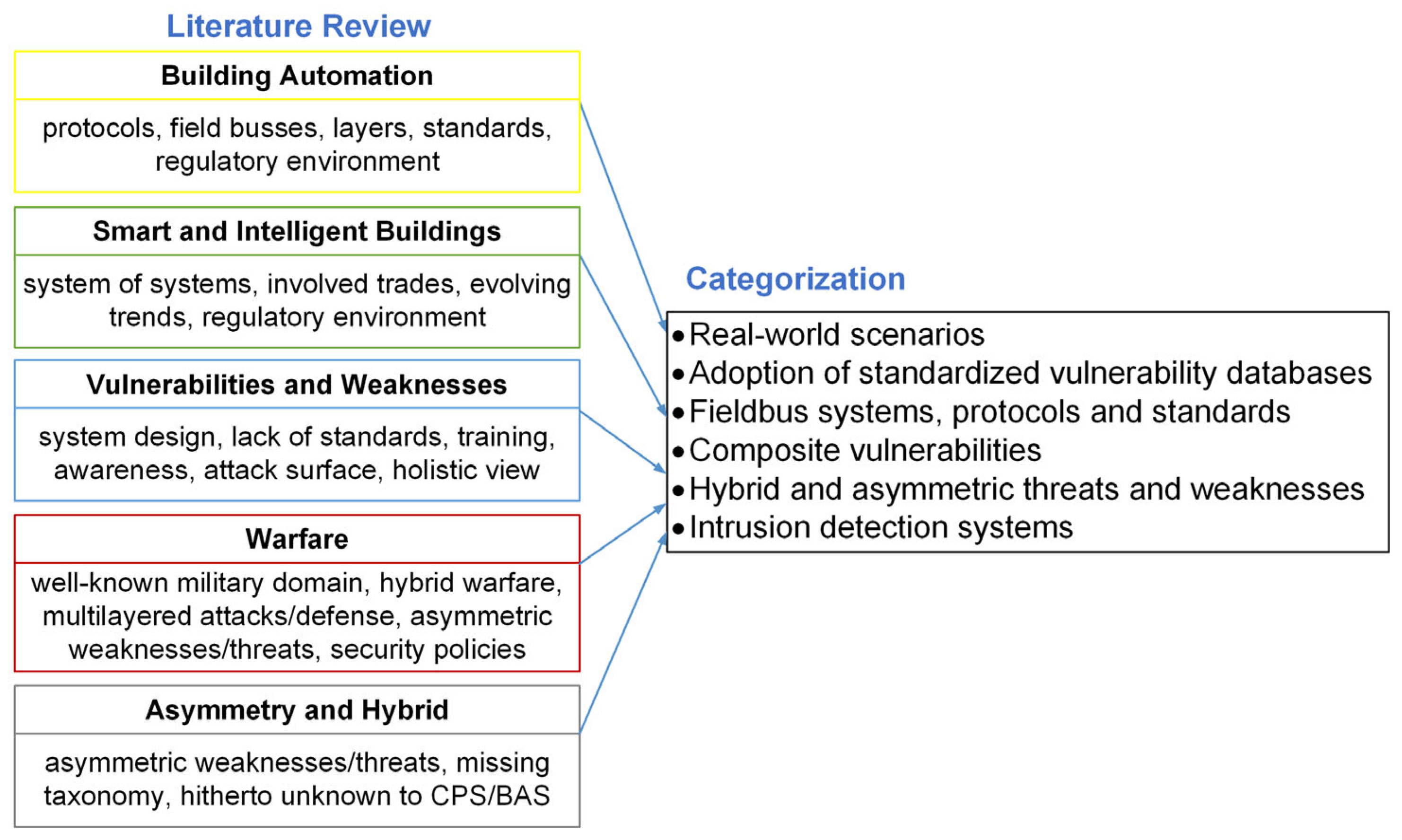
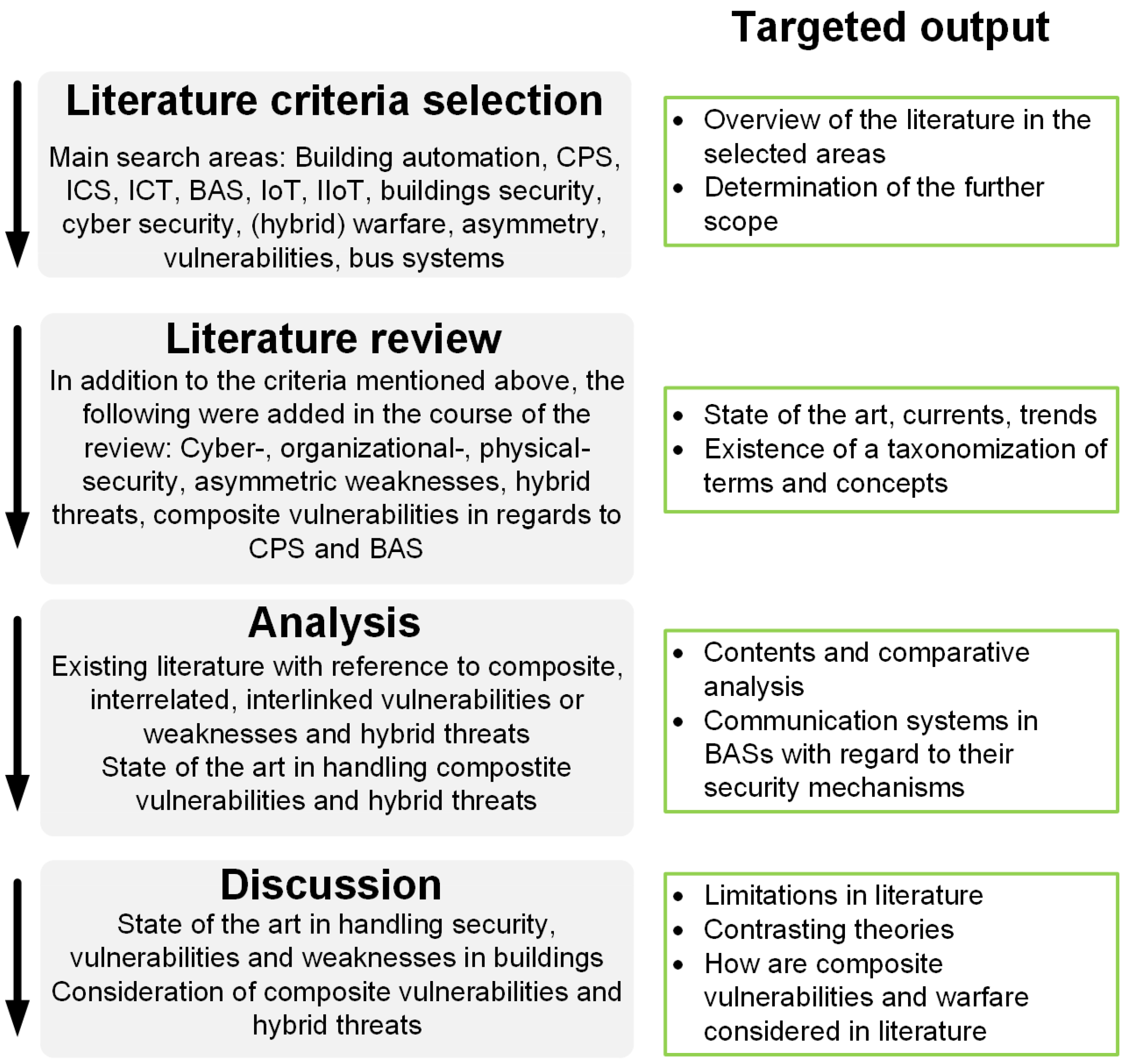
4.1. Design of the Literature Review
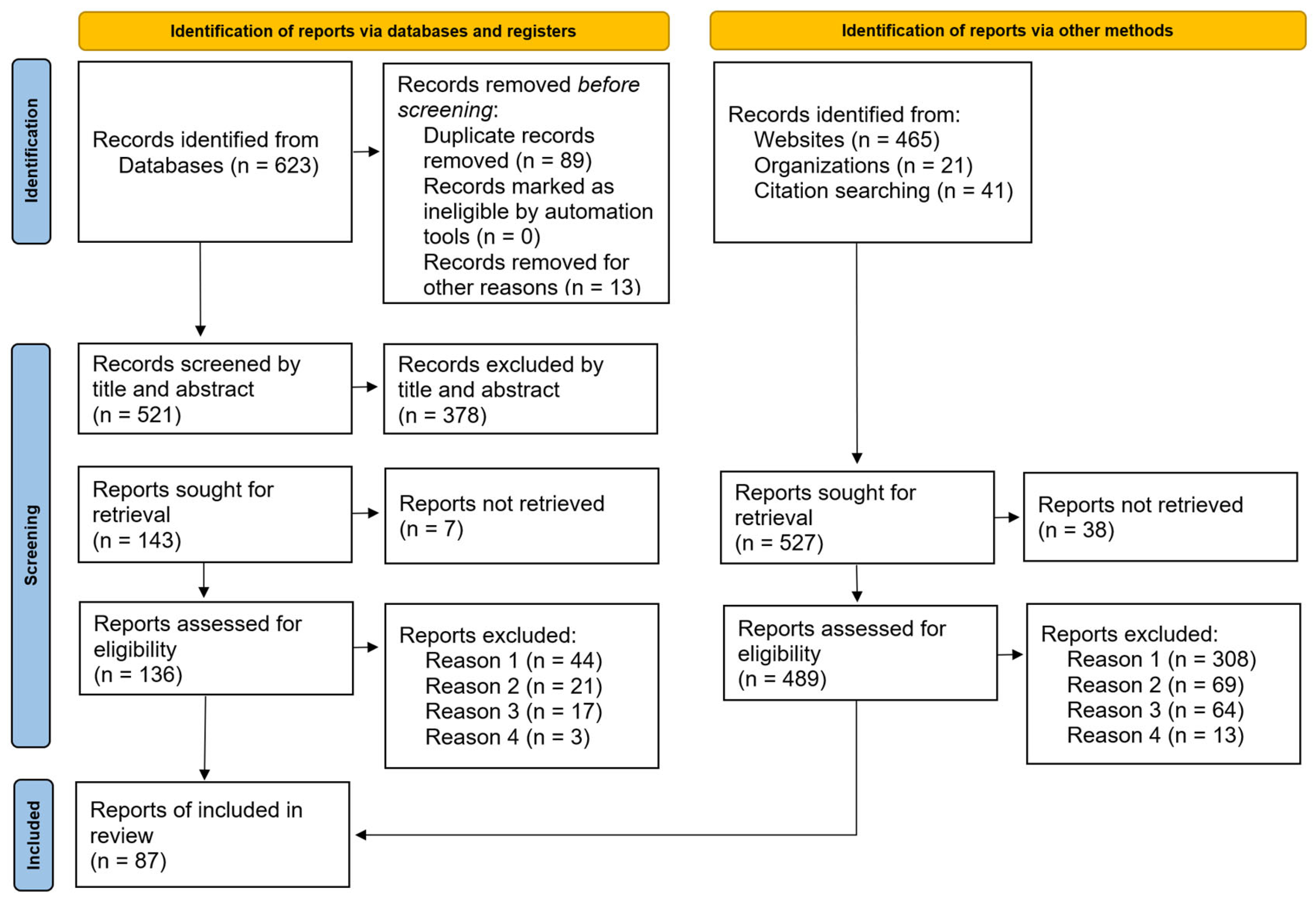
4.2. Review Method and Selection Process
4.3. Inclusion and Exclusion Criteria
4.3.1. Further Inclusion Criteria
- Literature addressing composite, interrelated, or interlinked vulnerabilities in the context of CPS, ICT, ICS, and BAS.
- Literature addressing hybrid or asymmetric threats or vulnerabilities in the context of CPS, ICT, ICS, and BAS.
- Literature related to hybrid or asymmetric warfare in connection with CPS, ICT, ICS, and BAS.
4.3.2. Further Exclusion Criteria
- Literature regarding safety, natural hazards, or events such as floods, storms, earthquakes, avalanches, and similar.
- Literature related to terrorist attacks was excluded.
- ○
- Unless it explicitly fell under the above-mentioned categories and was relevant in the context of the article being analyzed.
- Literature in the context of data privacy or GDPR (General Data Protection Regulation).
- Non-indexed government documents, journal articles, legal rules or regulations, reports, standards and preprints to assure accessibility and academic rigor.
- Only reports written in English or German were analyzed. Reports in all other languages were excluded.
4.4. Search Procedure
4.5. Data Extraction and Presentation
4.6. Quality Declaration
- Reason 1: The inclusion criteria have not been fully met.
- Reason 2: Exclusion criterion: Literature regarding safety, natural hazards, or events such as floods, storms, earthquakes, avalanches, and similar.
- Reason 3: Exclusion criterion: Literature in the context of data privacy or GDPR.
- Reason 4: Other reasons for exclusion according to the exclusion criteria.
5. Results of the Literature Review
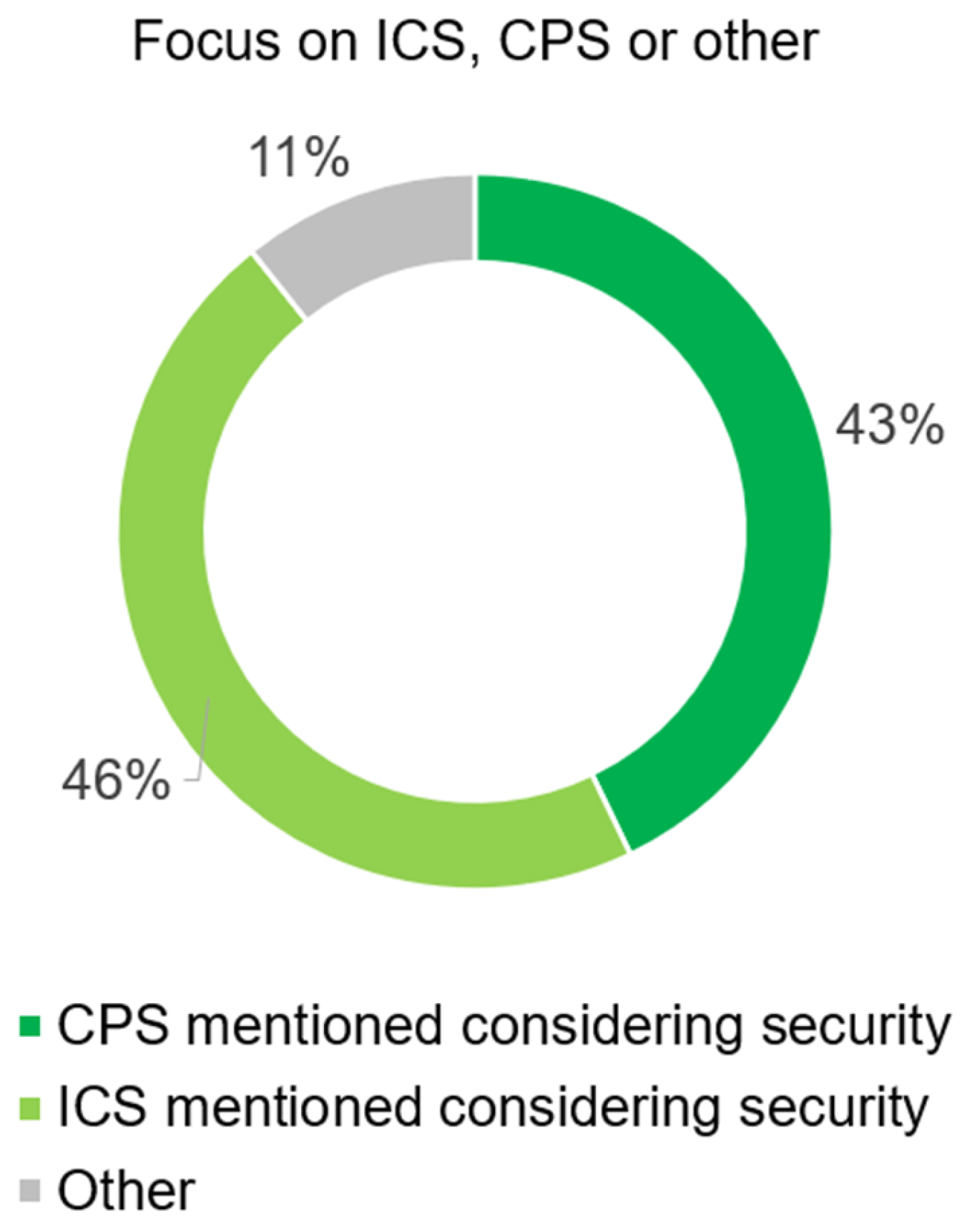
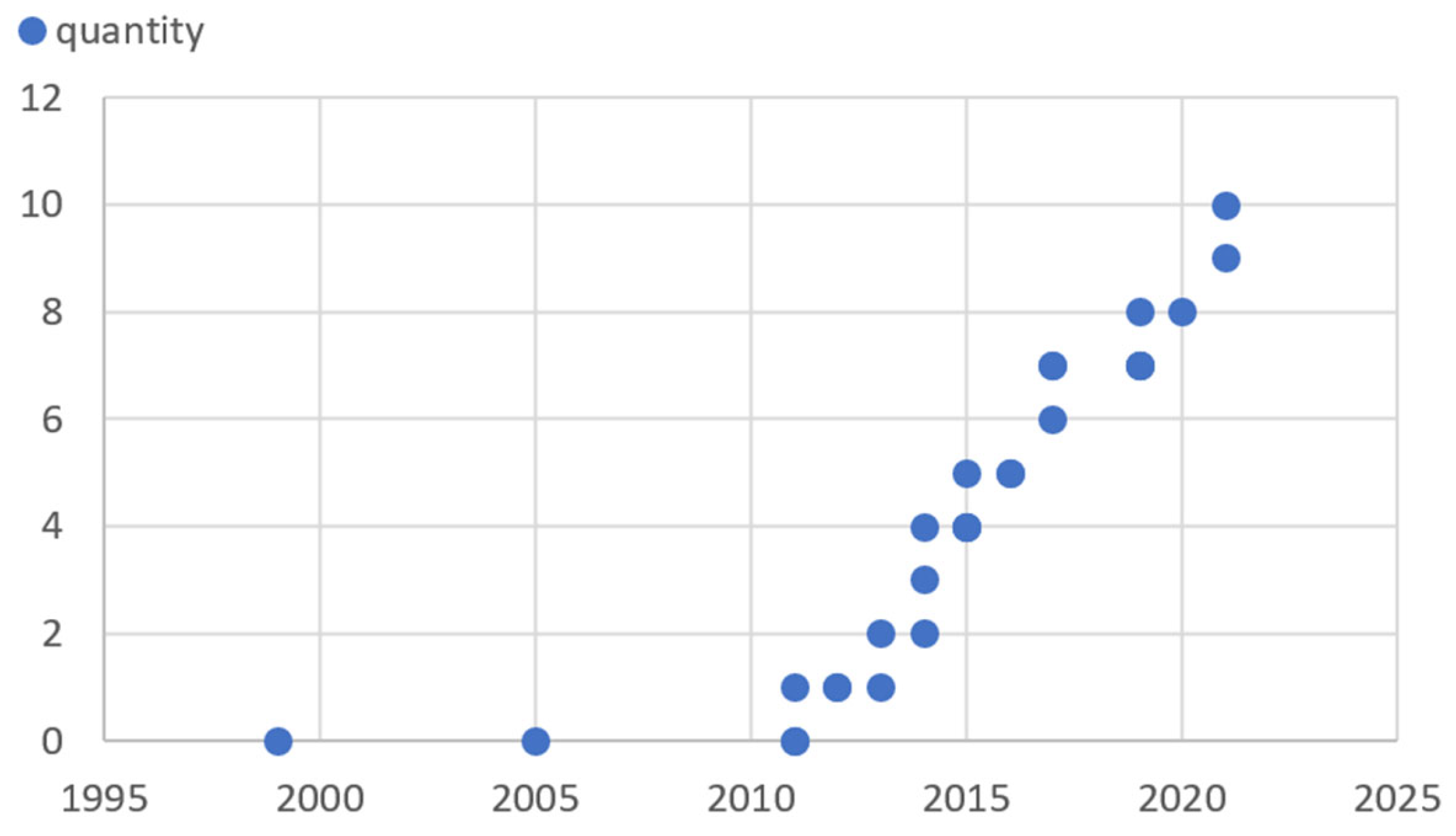
5.1. Occurrences of Real-World Scenarios in the Literature
5.2. Adoption of Standardized Vulnerability Databases for CPS and BAS
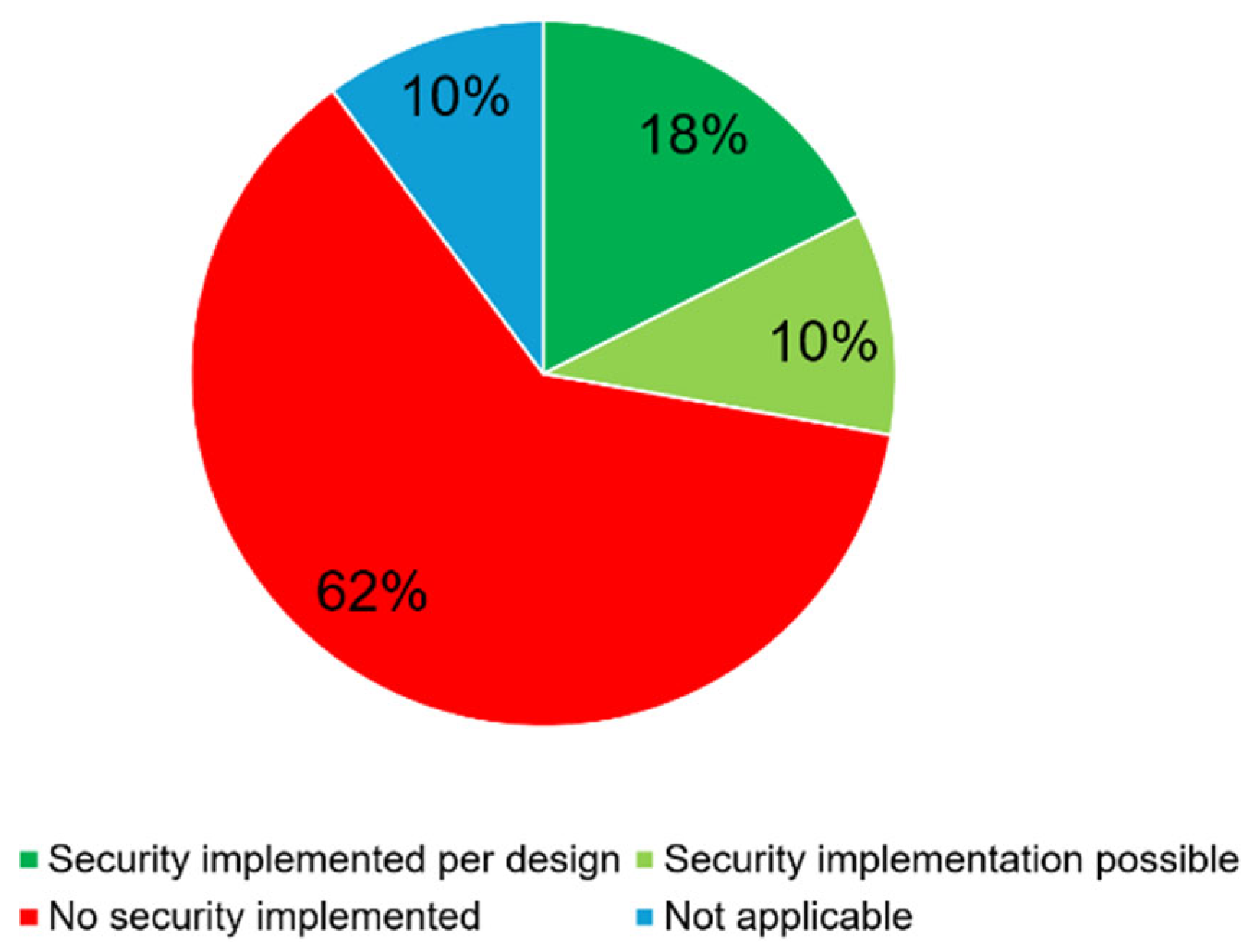
5.3. Fieldbus Systems, Protocols and Standards in BAS with Regard to Security
5.3.1. Analysis of Fieldbus Systems Used in Relation to Their Security
5.3.2. Security Strategies at the Field- and Automation Layers
5.4. Composite Vulnerabilities in Relation to CPS, ICT, ICS, IoT, and BAS
5.4.1. Literature Around Composite Vulnerabilities in the BAS, CPS, ICT, and ICS Areas
5.4.2. Literature Around Composite Vulnerabilities in the IoT Area
5.4.3. Strategies to Mitigate Composite Vulnerabilities in BASs

5.5. Hybrid and Asymmetric Warfare Related to CPS, ICT, ICS, and BAS
5.5.1. Literature Related to Hybrid and Asymmetric Warfare in Connection with CPS, ICT, ICS, and BAS
5.5.2. Literature Related to Asymmetrical or Hybrid Weaknesses in Connection with CPS, ICT, ICS, and BAS
5.5.3. Strategies to Mitigate Hybrid or Asymmetrical Weaknesses in BASs
5.6. Intrusion Detection Systems in CPS
5.7. Discussion on the Utilization of Behavioral Models in BASs
5.8. Security Mechanisms from Other Areas
6. Discussion and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACS | Access Control System |
| AHU | Air Handling Unit |
| AI | Artificial Intelligence |
| ASHRAE | American Society of Heating, Refrigerating, and Air-Conditioning Engineers |
| BAS | Building Automation System |
| CCTV | Closed-Circuit Television |
| CPNI | Centre for Protection of National Infrastructure |
| CPS | Cyber Physical System |
| CVSS | Common Vulnerability Scoring System |
| DCS | Distributed Control System |
| DDC | Direct Digital Control |
| DOS | Denial of Service |
| DREAD | Damage, Reproducibility, Exploitability, Affected Users, Discoverability |
| EPBD | Energy Performance of Buildings Directive |
| FTA | Fault Tree Analysis |
| GPDR | General Data Protection Regulation |
| HAZOP | Hazard and Operability Analysis |
| HVAC | Heating Ventilation and Air Conditioning |
| IBs | Intelligent Buildings |
| ICS | Industrial Control System |
| ICT | Information and Communication Technology |
| IDS | Intrusion Detection System |
| IIoT | Industrial Internet of Things |
| IMECA | Intervention Mode Effects and Criticality Analysis |
| IoT | Internet of Things |
| IT | Information Technology |
| LAN | Local Area Network |
| LLMs | Large Language Models |
| NATO | North Atlantic Treaty Organization |
| NIST | National Institute of Standards and Technology |
| NVD | National Vulnerability Database |
| ODBC | Open Database Connectivity |
| OT | Operational Technology |
| RBD | Reliability Block Diagram |
| SBs | Smart Buildings |
| SCADA | Supervisory Control and Data Acquisition |
| SQL | Structured Query Language |
| STRIDE | Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege |
| TCP/IP | Transmission Control Protocol/Internet Protocol |
| TMM | Threat Modelling Method |
| VMS | Video Management System |
References
- Fan, C.; Xiao, F.; Yan, C. A framework for knowledge discovery in massive building automation data and its application in building diagnostics. Autom. Constr. 2015, 50, 81–90. [Google Scholar] [CrossRef]
- Bakakeu, J.; Schäfer, F.; Bauer, J.; Michl, M.; Franke, J. Building Cyber-Physical Systems—A Smart Building Use Case. In Smart Cities: Foundations, Principles, and Applications; Wiley: Hoboken, NJ, USA, 2017; pp. 605–639. [Google Scholar]
- Schmidt, M.; Åhlund, C. Smart buildings as Cyber-Physical Systems: Data-driven predictive control strategies for energy efficiency. Renew. Sustain. Energy Rev. 2018, 90, 742–756. [Google Scholar] [CrossRef]
- Perry, C. Smart Buildings: A Deeper Dive into Market Segments; American Council for an Energy-Efficient Economy: Washington, DC, USA, 2017; p. 82. Available online: https://www.aceee.org/ (accessed on 18 August 2021).
- Wong, J.K.W.; Li, H.; Wang, S.W. Intelligent building research: A review. Autom. Constr. 2005, 14, 143–159. [Google Scholar] [CrossRef]
- Delsing, J. Smart City Solution Engineering. Smart Cities 2021, 4, 643–661. [Google Scholar] [CrossRef]
- Tragos, E.Z.; Foti, M.; Surligas, M.; Lambropoulos, G.; Pournaras, S.; Papadakis, S.; Angelakis, V. An IoT based intelligent building management system for ambient assisted living. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 246–252. [Google Scholar]
- Nge, C.L.; Ranaweera, I.U.; Midtgård, O.-M.; Norum, L. A real-time energy management system for smart grid integrated photovoltaic generation with battery storage. Renew. Energy 2019, 130, 774–785. [Google Scholar] [CrossRef]
- Marksteiner, S.; Exposito Jimenez, V.J.; Valiant, H.; Zeiner, H. An overview of wireless IoT protocol security in the smart home domain. In Proceedings of the 2017 Internet of Things Business Models, Users, and Networks, Copenhagen, Denmark, 23–24 November 2017; pp. 1–8. [Google Scholar]
- Khan, R.; McLaughlin, K.; Laverty, D.; Sezer, S. STRIDE-based threat modeling for cyber-physical systems. In Proceedings of the 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Torino, Italy, 26–29 September 2017; pp. 1–6. [Google Scholar]
- Aghemo, C.; Virgone, J.; Fracastoro, G.V.; Pellegrino, A.; Blaso, L.; Savoyat, J.; Johannes, K. Management and monitoring of public buildings through ICT based systems: Control rules for energy saving with lighting and HVAC services. Front. Archit. Res. 2013, 2, 147–161. [Google Scholar] [CrossRef]
- European Union. DIRECTIVE (EU) 2018_844 of 30 May 2018 amending Directive 2010_31_EU on the energy performance of buildings and Directive 2012_27_EU on energy efficiency. Off. J. Eur. Union 2016, 153, 20. [Google Scholar]
- Kastner, W.; Neugschwandtner, G.; Soucek, S.; Newman, H.M. Communication systems for building automation and control. Proc. IEEE 2005, 93, 1178–1203. [Google Scholar] [CrossRef]
- Hammadi, O.A.; Hebsi, A.A.; Zemerly, M.J.; Ng, J.W.P. Indoor Localization and Guidance Using Portable Smartphones. In Proceedings of the 2012 IEEE/WIC/ACM International Conferences on Web Intelligence and Intelligent Agent Technology, Washington, DC, USA, 4–7 December 2012; pp. 337–341. [Google Scholar]
- Kiliccote, S.; Piette, M.A.; Ghatikar, G.; Hafemeister, D.; Kammen, D.; Levi, B.G.; Schwartz, P. Smart Buildings and Demand Response. AIP Conf. Proc. 2011, 1401, 328–338. [Google Scholar] [CrossRef]
- Bushby, S.T. Information Model Standard for Integrating Facilities with Smart Grid. ASHRAE J. 2011, 53, B18–B22. [Google Scholar]
- Zhukabayeva, T.; Zholshiyeva, L.; Karabayev, N.; Khan, S.; Alnazzawi, N. Cybersecurity Solutions for Industrial Internet of Things–Edge Computing Integration: Challenges, Threats, and Future Directions. Sensors 2025, 25, 213. [Google Scholar] [CrossRef]
- Mahmoud, M.S.; Xia, Y. Cyberphysical Security Methods. In Networked Control Systems; Springer: London, UK, 2019; pp. 389–456. [Google Scholar]
- Bachmann, S.-D.O.V.; Gunneriusson, H. Terrorism and Cyber Attacks as Hybrid Threats: Defining a Comprehensive Approach for Countering 21st Century Threats to Global Risk and Security. J. Terror. Secur. 2013. [Google Scholar] [CrossRef]
- Ciholas, P.; Such, J.M. Composite Vulnerabilities in Cyber Physical Systems; Security Lancaster: Lancaster, UK, 2016; pp. 4–7. [Google Scholar]
- Merz, H.; Hansemann, T.; Hübner, C. Gebäudeautomation Kommunikationssysteme Mit EIB/KNX, LON und BACnet; Fachbuchverlag Leipzig: Leipzig, Germany, 2016; Volume 3. (In German) [Google Scholar]
- Graveto, V.; Cruz, T.; Simöes, P. Security of Building Automation and Control Systems: Survey and future research directions. Comput. Secur. 2022, 112, 102527. [Google Scholar] [CrossRef]
- Sinopoli, J. Advanced Technology for Smart Buildings; Artech House: Boston, MA, USA, 2016. [Google Scholar]
- Younus, M.U.; Islam, S.u.; Ali, I.; Khan, S.; Khan, M.K. A survey on software defined networking enabled smart buildings: Architecture, challenges and use cases. J. Netw. Comput. Appl. 2019, 137, 62–77. [Google Scholar] [CrossRef]
- Butzin, B.; Golatowski, F.; Timmermann, D. A survey on information modeling and ontologies in building automation. In Proceedings of the IECON 2017—43rd Annual Conference of the IEEE Industrial Electronics Society, Beijing, China, 29 October–1 November 2017; pp. 8615–8621. [Google Scholar]
- Macaulay, T. RIoT Control. In RIoT Control: Understanding and Managing Risks and the Internet of Things; Morgan Kaufmann: Burlington, MA, USA, 2017; p. 383. [Google Scholar]
- DiMase, D.; Collier, Z.A.; Chandy, J.; Cohen, B.S.; D’Anna, G.; Dunlap, H.; Hallman, J.; Mandelbaum, J.; Ritchie, J.; Vessels, L. A Holistic Approach to Cyber Physical Systems Security and Resilience. In Proceedings of the 2020 IEEE Systems Security Symposium (SSS), Crystal City, VA, USA, 1 July–1 August 2020; pp. 1–8. [Google Scholar]
- Brooks, D.J.; Coole, M.; Haskell-Dowland, P.; Griffiths, M.; Lockhart, N. Building Automation & Control Systems An Investigation into Vulnerabilities Current Practice & Security Management Best Practice; ASIS Foundation: Alexandria, VA, USA; Security Industry Association: Silver Spring, MD, USA; Building Owners and Managers Association: Washington, DC, USA, 2017; p. 220. [Google Scholar]
- Shwartz, O.; Cohen, A.; Shabtai, A.; Oren, Y. Inner conflict: How smart device components can cause harm. Comput. Secur. 2020, 89, 101665. [Google Scholar] [CrossRef]
- Leite, D.; Andrade, E.; Rativa, D.; Maciel, A.M.A. Fault Detection and Diagnosis in Industry 4.0: A Review on Challenges and Opportunities. Sensors 2024, 25, 60. [Google Scholar] [CrossRef] [PubMed]
- Jeffrey, N.; Tan, Q.; Villar, J.R. Using Ensemble Learning for Anomaly Detection in Cyber–Physical Systems. Electronics 2024, 13, 1391. [Google Scholar] [CrossRef]
- Mundt, T.; Wickboldt, P. Security in building automation systems—A first analysis. In Proceedings of the 2016 International Conference on Cyber Security And Protection of Digital Services (Cyber Security), London, UK, 13–14 June 2016; pp. 1–8. [Google Scholar]
- Harzing, A.-W.; Alakangas, S. Google Scholar, Scopus and the Web of Science: A longitudinal and cross-disciplinary comparison. Scientometrics 2015, 106, 787–804. [Google Scholar] [CrossRef]
- Coole, M.; Evans, D.; Brooks, D. A Framework for the Analysis of Security Technology Vulnerabilities: Defeat Evaluation of an Electronic Access Control Locking System. In Proceedings of the 2022 IEEE International Carnahan Conference on Security Technology (ICCST), Valec, Czech Republic, 7–9 September 2022; pp. 1–6. [Google Scholar]
- Granzer, W.; Praus, F.; Kastner, W. Security in Building Automation Systems. IEEE Trans. Ind. Electron. 2010, 57, 3622–3630. [Google Scholar] [CrossRef]
- Common Weakness Enumeration. Common Weakness Enumeration. 2021. Available online: http://cwe.mitre.org/data/index.html (accessed on 17 August 2025).
- NIST-Resilience-Research. Resilience Research. Available online: https://www.nist.gov/resilience (accessed on 9 September 2022).
- Prisma.org. Transparent reporting or systematic reviews and meta-analysis. Prism. Checkl. 2024, 2024. [Google Scholar]
- Kshetri, N. Information and communications technologies, strategic asymmetry and national security. J. Int. Manag. 2005, 11, 563–580. [Google Scholar] [CrossRef][Green Version]
- Meyer, D.; Haase, J.; Eckert, M.; Klauer, B. New attack vectors for building automation and IoT. In Proceedings of the IECON 2017—43rd Annual Conference of the IEEE Industrial Electronics Society, Beijing, China, 29 October–1 November 2017; pp. 8126–8131. [Google Scholar]
- Kumar, S.A.; Vealey, T.; Srivastava, H. Security in Internet of Things: Challenges, Solutions and Future Directions. In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 5772–5781. [Google Scholar]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Survey of IIoT Protocols. ACM Comput. Surv. 2020, 53, 1–53. [Google Scholar] [CrossRef]
- first.org. Common Vulnerability Scoring System SIG. 2023. Available online: https://www.first.org/cvss/ (accessed on 17 August 2025).
- NIST. National Vulnerability Database (NVD). 2022. Available online: https://www.nist.gov/programs-projects/national-vulnerability-database-nvd (accessed on 17 August 2025).
- Thomas, R.J.; Chothia, T. Learning from Vulnerabilities—Categorising, Understanding and Detecting Weaknesses in Industrial Control Systems. In Computer Security; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2020; pp. 100–116. [Google Scholar]
- Stouffer, K.; Pillitteri, V.; Lightman, S.; Abrams, M.; Hahn, A. Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [Google Scholar]
- Liu, Y.; Pang, Z.; Dan, G.; Lan, D.; Gong, S. A Taxonomy for the Security Assessment of IP-Based Building Automation Systems: The Case of Thread. IEEE Trans. Ind. Inform. 2018, 14, 4113–4123. [Google Scholar] [CrossRef]
- Heartfield, R.; Loukas, G.; Budimir, S.; Bezemskij, A.; Fontaine, J.R.J.; Filippoupolitis, A.; Roesch, E. A taxonomy of cyber-physical threats and impact in the smart home. Comput. Secur. 2018, 78, 398–428. [Google Scholar] [CrossRef]
- Geismann, J.; Bodden, E. A systematic literature review of model-driven security engineering for cyber–physical systems. J. Syst. Softw. 2020, 169, 110697. [Google Scholar] [CrossRef]
- Wittenberg, D.K.; Smith, J.; Gray, R.; Eakman, G. Automotive Vulnerability Detection System. In Proceedings of the 10th escar USA-The World’s Leading Automotive Cyber Security Conference, Plymouth, MI, USA, 20–22 June 2015. [Google Scholar]
- Qu, Y.; English, A.; Hannon, B. Quantifying the Impact of Vulnerabilities of the Components of an Information System towards the Composite Rise Exposure. In Proceedings of the 2021 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 15–17 December 2021; pp. 788–793. [Google Scholar]
- Ciholas, P.; Lennie, A.; Sadigova, P.; Such, J.M. The Security of Smart Buildings: A Systematic Literature Review. arXiv 2019, arXiv:1901.05837. [Google Scholar] [CrossRef]
- Ly, K.; Jin, Y. Security Challenges in CPS and IoT: From End-Node to the System. In Proceedings of the 2016 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Pittsburgh, PA, USA, 11–13 July 2016; pp. 63–68. [Google Scholar]
- Huang, B.; Chaki, D.; Bouguettaya, A.; Lam, K.-Y. A Survey on Conflict Detection in IoT-based Smart Homes. ACM Comput. Surv. 2023, 56, 1–40. [Google Scholar] [CrossRef]
- Cimino, G.; Deufemia, V. SIGFRID: Unsupervised, Platform-Agnostic Interference Detection in IoT Automation Rules. ACM Trans. Internet Things 2025, 6, 1–33. [Google Scholar] [CrossRef]
- Li, C.H.; Yuen, H.Y.; Lee, T.T.; Tang, W.F.; Lee, C.C.; Ng, C.; Mak, S.L. How to Embed AI Applications of Building Management System in Campus Management. In Intelligent Sustainable Systems; Lecture Notes in Networks and Systems; Springer: Singapore, 2024; pp. 403–411. [Google Scholar]
- BSI Federal Office for Information Security. Unternehmen und Organisationen–Standards und Zertifizierung; BSI Federal Office for Information Security: Bonn, Germany, 2022. [Google Scholar]
- Army War College Press. Unorthodox Thoughts about Asymmetric Warfare; OMB No. 0704-0188; Army War College Press: Carlisle, PA, USA, 2003; p. 16. [Google Scholar]
- Lele, A. Asymmetric Warfare: A State vs Non-State Conflict. Oasis 2014, 20, 97–111. [Google Scholar]
- Chen, A.; Sriraman, A.; Vaidya, T.; Zhang, Y.; Haeberlen, A.; Loo, B.T.; Phan, L.T.X.; Sherr, M.; Shields, C.; Zhou, W. Dispersing Asymmetric DDoS Attacks with SplitStack. In Proceedings of the 15th ACM Workshop on Hot Topics in Networks, Atlanta, GA, USA, 9–10 November 2016; pp. 197–203. [Google Scholar]
- Miles, F.B. Asymmetric Warfare: An Historical Perspective; U.S. Army War College: Carlisle, PA, USA, 1999; p. 54. [Google Scholar]
- Kshetri, N. Information and Communications Technologies, Cyberattacks, and Strategic Asymmetry. In The Global Cybercrime Industry; Springer: Berlin/Heidelberg, Germany, 2010; pp. 119–137. [Google Scholar]
- Pernin, C.G.; Axelband, E.; Drezner, J.A.; Dille, B.B.; Gordon, I.; Held, B.J.; McMahon, K.S.; Perry, W.L.; Rizzi, C.; Shah, A.R. Lessons from the Army’s Future Combat Systems Program; RAND, ARROYO CENTER: Santa Monica, CA, USA, 2012; p. 29. [Google Scholar]
- Gupta, A.; Langbort, C.; Basar, T. Dynamic Games With Asymmetric Information and Resource Constrained Players With Applications to Security of Cyberphysical Systems. IEEE Trans. Control Netw. Syst. 2017, 4, 71–81. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Jajodia, S.; Cybenko, G.; Liu, P.; Wang, C.; Wellman, M. Adversarial and Uncertain Reasoning for Adaptive Cyber Defense; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Cybenko, G.; Wellman, M.; Liu, P.; Zhu, M. Overview of Control and Game Theory in Adaptive Cyber Defenses. In Adversarial and Uncertain Reasoning for Adaptive Cyber Defense; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; pp. 1–11. [Google Scholar]
- Jones, M.G. Asymmetric Information Games and Cyber Security. Ph.D. Thesis, Georgia Institute of Technology, Giorgia Tech Library, Atlanta, GA, USA, 2013. [Google Scholar]
- Pawlick, J.; Colbert, E.; Zhu, Q. A Game-theoretic Taxonomy and Survey of Defensive Deception for Cybersecurity and Privacy. ACM Comput. Surv. 2019, 52, 1–28. [Google Scholar] [CrossRef]
- Sheikh, Z.A.; Singh, Y. A Hybrid Threat Assessment Model for Security of Cyber Physical Systems. In Proceedings of the 2022 Seventh International Conference on Parallel, Distributed and Grid Computing (PDGC), Solan, India, 25–27 November 2022; pp. 582–587. [Google Scholar]
- Siebel, N.T. Securing IT Networks for Industrial and Building Automation Systems. Int. J. Trend Res. Dev. 2018, 134–136. [Google Scholar] [CrossRef]
- Soucek, S.; Zucker, G. Current developments and challenges in building automation. Elektrotechnik Und Informationstechnik 2012, 129, 278–285. [Google Scholar] [CrossRef]
- Tenkanen, T.; Hamalainen, T. Security Assessment of a Distributed, Modbus-Based Building Automation System. In Proceedings of the 2017 IEEE International Conference on Computer and Information Technology (CIT), Helsinki, Finland, 21–23 August 2017; pp. 332–337. [Google Scholar]
- ENISA. Glossary of Threat and Risk Management. 2021. Available online: https://www.enisa.europa.eu/sites/default/files/publications/O.7.2-T2-Risk_Management_standards.pdf (accessed on 17 August 2025).
- Badawy, M.; Sherief, N.H.; Abdel-Hamid, A.A. Legacy ICS Cybersecurity Assessment Using Hybrid Threat Modeling—An Oil and Gas Sector Case Study. Appl. Sci. 2024, 14, 8398. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Beaver, J.M.; Borges-Hink, R.C.; Buckner, M.A. An Evaluation of Machine Learning Methods to Detect Malicious SCADA Communications. In Proceedings of the 2013 12th International Conference on Machine Learning and Applications, Miami, FL, USA, 4–7 December 2013; pp. 54–59. [Google Scholar]
- Zhang, F.; Kodituwakku, H.A.D.E.; Hines, J.W.; Coble, J. Multilayer Data-Driven Cyber-Attack Detection System for Industrial Control Systems Based on Network, System, and Process Data. IEEE Trans. Ind. Inform. 2019, 15, 4362–4369. [Google Scholar] [CrossRef]
- Goh, J.; Adepu, S.; Tan, M.; Lee, Z.S. Anomaly Detection in Cyber Physical Systems Using Recurrent Neural Networks. In Proceedings of the 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Singapore, 12–14 January 2017; pp. 140–145. [Google Scholar]
- Gawand, H.L.; Bhattacharjee, A.K.; Roy, K. Securing a Cyber Physical System in Nuclear Power Plants Using Least Square Approximation and Computational Geometric Approach. Nucl. Eng. Technol. 2017, 49, 484–494. [Google Scholar] [CrossRef]
- Varela-Vaca, Á.J.; Rosado, D.G.; Sánchez, L.E.; Gómez-López, M.T.; Gasca, R.M.; Fernández-Medina, E. Definition and Verification of Security Configurations of Cyber-Physical Systems. In Computer Security; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2020; pp. 135–155. [Google Scholar]
- Abdulmunem, A.-S.M.Q.; Kharchenko, V.S. Availability and Security Assessment of Smart Building Automation Systems: Combining of Attack Tree Analysis and Markov Models. In Proceedings of the 2016 Third International Conference on Mathematics and Computers in Sciences and in Industry (MCSI), Chania, Greece, 27–29 August 2016; pp. 302–307. [Google Scholar]
- Abdulmunem, A.-S.M.K.; Akhmed Valid Al-Khafadzhi, V.K. The method of IMECA-based security assessment: Case study for building automation system. Ivan Kozhedub Kharkiv Natl. Air Force Univ. (KNAFU) 2016, 1, 138–144. [Google Scholar]
- Jones, C.B.; Carter, C.; Thomas, Z. Intrusion Detection & Response using an Unsupervised Artificial Neural Network on a Single Board Computer for Building Control Resilience. In Proceedings of the 2018 Resilience Week (RWS), Denver, CO, USA, 20–23 August 2018; pp. 31–37. [Google Scholar]
- Chen, Y.; Ni, T.; Xu, W.; Gu, T. SwipePass. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2022, 6, 1–25. [Google Scholar] [CrossRef]
- Duan, D.; Sun, Z.; Ni, T.; Li, S.; Jia, X.; Xu, W.; Li, T. F2Key: Dynamically Converting Your Face into a Private Key Based on COTS Headphones for Reliable Voice Interaction. In Proceedings of the 22nd Annual International Conference on Mobile Systems, Applications and Services, Tokyo, Japan, 3–7 June 2024; pp. 127–140. [Google Scholar]
- Ni, T.; Zhang, X.; Zhao, Q. Recovering Fingerprints from In-Display Fingerprint Sensors via Electromagnetic Side Channel. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 253–267. [Google Scholar]
| Categories | ||||||
|---|---|---|---|---|---|---|
| Real-World Scenarios | Adoption of Standardized Vulnerability Databases | Fieldbus Systems, Protocols and Standards | Composite Vulnerabilities | Hybrid and Asymmetric Threats and Weaknesses | Intrusion Detection Systems | |
| Area | CPS, ICS, IoT | BAS, CPS, ICT, IoT | BAS | CPS, ICT, IoT | CPS, ICT, IoT | CPS, ICT, IoT |
| References | [31,39,40] | [41,42,43,44,45] | [13,21,42,46] | [18,19,20,29,35,47,48,49,50,51,52,53,54,55,56,57,58,59,60] | [49,50,61,62,63,64,65,66,67,68,69,70] | [22,31,71,72,73,74,75] |
| Type of Attacks or Vulnerabilities most frequently listed | Malicious code, tampering, eavesdropping, sniffing, noise in data, gateway attacks, unauthorized access, injecting fake information, denial of service. | CVSS and NVD as very comprehensive databases that cover almost all types of attacks or vulnerabilities. | Unauthorized device discovery, denial of service, writing failure, write property, man-in-the-middle, eavesdropping, replay, spoofing, local manipulation, physical attack. | Mutual influence, inter-rule or interaction conflicts, combined vulnerabilities, man-in-the-middle, spoofing, information disclosure. | All known types of attacks or vulnerabilities. Typically divided into the cyber, physical and organizational area, physical/environ-mental damage. | Most of the known types of attacks or vulnerabilities. |
| Layers affected | Enterprise Management Automation | Enterprise Management | Field | Enterprise Management Automation Field | Enterprise Management Automation Field | Enterprise Management Automation |
| Key messages | Missing threat classification. Lack of practical examples for training deep learning algorithms and intrusion detection systems. | Focus on the field of cyber security (IT, networking). Difficult to adapt for BAS. Lack of trained personnel in the CPS area. | Due to the longevity of BAS, many old and proprietary protocols still in use. Low prevalence of BACnet Secure, KNX Secure, or other secure protocols. | Vulnerabilities that emerge from a combination of multiple components or systems, which may individually seem harmless but together lead to exploitable conditions. | Neither purely cyber, physical, or organizational nature making them challenging to detect and mitigate. Particularly in BAS, many smart sensors are located in unprotected areas, which facilitates such attacks. | IDS supports the detection of many types of threats or intrusion. Widespread use in network technology and IT. No literature available on building automation. |
| Standard-, Bus-, Protocol-Name | Full Name or Short Description | Trade Mostly Spread | Pro-Prietary or Open System | Owner or Developer | Security per Design or as a Feature Implemented | Type of Security If Applicable | Object Dis-covery Tool Available | Standards Involved/Owner Link | Long Description |
|---|---|---|---|---|---|---|---|---|---|
| BACnet | Building Automation and Control | HVAC | open | bacnet.org | no | yes | ISO 16484-5; IEEE 802.2; IEEE 802.3; EIA-485, ASHRAE/ANSI 135 | Communication protocol standard, object oriented, de facto standard in BAS | |
| C-Bus | 2-wire EIA-485 based | HVAC | proprietary | Honeywell | no | yes | honeywell.com | 2-wire fieldbus to connect controllers amongst each other and to a BMS, only for Honeywell devices, outdated | |
| DALI | Digital Addressable Lighting Interface | lighting | open | IEC and DiiA | no | yes | IEC 62386, IEC 60929 | Widely spread lighting control bus | |
| KNX | Konnex, formerly called EIB (Europäischer InstallationsBus) or InstaBus | lighting, electrical, HVAC | open | knx.org | no | yes | EN 50090-3,4; EN 13321-1,2; ISO/IEC 14543 | Fieldbus and standard especially for lighting, shading and electrical installations, de facto standard in building automation | |
| LON | Local Operating Network | HVAC, lighting, security | open | Echelon | no | yes | EN ISO/IEC 14908; ANSI/CEA-709.1-B | Framework: LonTalk, LonWorks, CEA-709; more outdated, very commonly used before BACnet | |
| M-Bus | Also called Meter-Bus | metering | open | oms-group.org | no | yes | EN13757; EN 61334-4-1; IEC 60870-5 | Most common bus for metering applications in BAS in Europe | |
| M-Bus wireless | Meter-Bus as a wireless application | metering | open | oms-group.org | no | yes | EN13757-4: 2005 | Uses frequency of 868MHz, designed primarily for remote reading, battery-supplied devices | |
| Modbus RTU/ASCII | 2-wire EIA-485 based | BMS, industrial | open | Modbus Organization | no | yes | modbus.org ANSI/TIA/EIA-485-A-98 | Communication protocol, de facto standard for basic communication between industrial devices, royalty free | |
| Modbus TCP/UDP | IP layer for Modbus | BMS, industrial | open | Modbus Organization | no | yes | modbus.org | Communication protocol, de facto standard for basic communication between industrial devices, royalty free | |
| MQTT | Message Queuing Telemetry Transport | IoT, smart home | open | OASIS | yes | TLS | yes | OASIS, ISO/IEC 20922:2016 | Lightweight message transport protocol for client/server environments |
| ONVIF | Open Network Video Interface Forum | VMS | open | onvif.org | (yes) | (TLS) | yes | onvif.org | Open industry forum that provides and promotes standardized interfaces Open industry forum that provides and promotes standardized interfaces for effective interoperability of IP-based physical security products |
| OPC | Open Platform Communications / OLE for Process Control | BMS | open | OPC Foundation | no | yes | opcfoundation.org | Specifies communication of real-time plant data between control devices from different manufacturers. Series of standards and specifications, based on the OLE, COM, and DCOM | |
| OPC DA | Open Platform Communications Data Access | BMS | open | OPC Foundation | (yes) | tunneling, COM/DCOM | yes | opcfoundation.org | Client/Server communication, cross-platform, binary protocol, and web service. Intended for Alarm&Event (A&E) and History Data Access (HDA) |
| OPC UA | Open Platform Communications Unified Architecture | BMS | open | OPC Foundation | yes | tunneling, COM/DCOM | yes | opcfoundation.org | Client/Server communication, SOA (Service-oriented architecture), cross-platform, binary protocol and web service. Intended for Alarm&Event (A&E) and History Data Access (HDA). Unified Architecture |
| SMI | Standard Motor Interface | shading | open | SMI-group | no | yes | standard-motor-interface.com | 5-wire common interface for sunblinds |
| Authors | Year | Scope | Focus Area | BAS Mentioned | Weaknesses Mentioned in the Context of Vulnerabilities | Vulnerabilities or Threat Classification | CPS/ICS System Behavior Modelling | Short Description of the Content |
|---|---|---|---|---|---|---|---|---|
| [82] | 2017 | security assessment/analysis | attack tree analysis | yes | yes | no | yes | Based on an attack tree analysis using the Markov model, the report intends to assess the BAS’s security. |
| [83] | 2016 | security assessment/analysis | BAS in general | yes | no | no | yes | Apply FTA, HAZOP, RBD, and IMECA to BAS. |
| [84] | 2018 | anomaly detection | unsupervised learning algorithm | yes | no | no | yes | Intrusion and anomaly detection via a single board computer which inspects the network traffic between the BAS nodes. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gerhalter, M.; Dahal, K. Composite Vulnerabilities and Hybrid Threats for Smart Sensors and Field Busses in Building Automation: A Review. Sensors 2025, 25, 5218. https://doi.org/10.3390/s25175218
Gerhalter M, Dahal K. Composite Vulnerabilities and Hybrid Threats for Smart Sensors and Field Busses in Building Automation: A Review. Sensors. 2025; 25(17):5218. https://doi.org/10.3390/s25175218
Chicago/Turabian StyleGerhalter, Michael, and Keshav Dahal. 2025. "Composite Vulnerabilities and Hybrid Threats for Smart Sensors and Field Busses in Building Automation: A Review" Sensors 25, no. 17: 5218. https://doi.org/10.3390/s25175218
APA StyleGerhalter, M., & Dahal, K. (2025). Composite Vulnerabilities and Hybrid Threats for Smart Sensors and Field Busses in Building Automation: A Review. Sensors, 25(17), 5218. https://doi.org/10.3390/s25175218







