BFL-SDWANTrust: Blockchain Federated-Learning-Enabled Trust Framework for Secure East–West Communication in Multi-Controller SD-WANs
Abstract
1. Introduction
- A BFL-SDWANTrust model is proposed that ensures reliable and privacy-preserving distributed local model training across multiple SDN controllers while utilizing the capabilities of Convolution Neural Networks (CNN) and SVM classifiers.
- A distributed blockchain network is used to remove dependence on centralized authorities and efficiently solve various issues such as single points of failure, performance bottlenecks, and operational overheads in controller-to-controller communication.
- CNN and SVM are integrated to extract spatial-temporal patterns and perform robust classification of east–west traffic behaviors. This hybrid technique not only enhances anomaly detection accuracy but also the controller trust prediction in heterogeneous and dynamic SD-WAN environments.
2. Related Work
3. Proposed BFL-Model
3.1. Sensing Layer in East–West Interface Monitoring
| Algorithm 1 Sensing layer algorithm for east–west interface trust evaluation |
|
3.2. Blockchain Layer for Secure East–West Interface Communication
| Algorithm 2 Blockchain layer algorithm for secure east–west communication |
|
3.3. Fog Layer in Multi-Controller SD-WAN
| Algorithm 3 Local model training at fog layer |
|
3.4. Cloud Aggregation Layer in SD-WAN Controller Plane
| Algorithm 4 Cloud aggregation layer algorithm for global trust model aggregation |
|
4. Experimental Results and Analysis
4.1. Dataset Details
4.2. Experimental Results
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, J.; Chen, C.; Li, Y.; Sun, L.; Song, Y.; Zhou, J.; Jing, B.; Dou, D. Enhancing trust and privacy in distributed networks: A comprehensive survey on blockchain-based federated learning. Knowl. Inf. Syst. 2024, 66, 4377–4403. [Google Scholar] [CrossRef]
- Lakhlef, H.; Lerner, T.; Kebir, A.; El Atia, N.; Du, X.; Ingardin, V. Blockchain-Enabled SDN Solutions for IoT: Advancements, Discussions and Strategic Insights. In Proceedings of the 2024 IEEE Symposium on Computers and Communications (ISCC), Paris, France, 26–29 June 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Solis, W.V.; Parra-Ullauri, J.M.; Kertesz, A. Exploring the synergy of fog computing, blockchain and federated learning for IoT applications: A systematic literature review. IEEE Access 2024, 12, 68015–68060. [Google Scholar] [CrossRef]
- Hallaji, E.; Razavi-Far, R.; Saif, M.; Wang, B.; Yang, Q. Decentralized federated learning: A survey on security and privacy. IEEE Trans. Big Data 2024, 10, 194–213. [Google Scholar] [CrossRef]
- Ahmad, J.; Zia, M.U.; Naqvi, I.H.; Chattha, J.N.; Butt, F.A.; Huang, T.; Xiang, W. Machine learning and blockchain technologies for cybersecurity in connected vehicles. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2024, 14, e1515. [Google Scholar] [CrossRef]
- Cai, Z.; Chen, J.; Fan, Y.; Zheng, Z.; Li, K. Blockchain-empowered federated learning: Benefits, challenges and solutions. IEEE Trans. Big Data 2025, 1–20. [Google Scholar] [CrossRef]
- Hirsi, A.; Audah, L.; Salh, A.; Alhartomi, M.A.; Ahmed, S. Detecting DDoS threats using supervised machine learning for traffic classification in software defined networking. IEEE Access 2024, 12, 166675–166702. [Google Scholar] [CrossRef]
- Gali, M.; Mahamkali, A. Deep Learning Based Attack Detection and QoS Aware Secure Routing Protocol for SDN-IoT Network. Concurr. Comput. Pract. Exp. 2025, 37, e70045. [Google Scholar] [CrossRef]
- Huang, W.; Li, T.; Cao, Y.; Lyu, Z.; Liang, Y.; Yu, L.; Li, Y. Safe-NORA: Safe Reinforcement Learning-Based Mobile Network Resource Allocation for Diverse User Demands. In Proceedings of the 32nd ACM International Conference on Information and Knowledge Management (CIKM ’23), Birmingham, UK, 21–25 October 2023. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Mod. Econ. 2008, 6, 1–9. [Google Scholar]
- Luo, H.; Zhang, Q.; Sun, G.; Yu, H.; Niyato, D. Symbiotic Blockchain Consensus: Cognitive Backscatter Communications-Enabled Wireless Blockchain Consensus. IEEE/ACM Trans. Netw. 2024, 32, 5372–5387. [Google Scholar] [CrossRef]
- Luo, H.; Sun, G.; Chi, C.; Yu, H.; Guizani, M. Convergence of Symbiotic Communications and Blockchain for Sustainable and Trustworthy 6G Wireless Networks. IEEE Wirel. Commun. 2025, 32, 18–25. [Google Scholar] [CrossRef]
- Yang, J.; Yang, K.; Xiao, Z.; Jiang, H.; Xu, S.; Dustdar, S. Improving Commute Experience for Private Car Users via Blockchain-Enabled Multitask Learning. IEEE Internet Things J. 2023, 10, 21656–21669. [Google Scholar] [CrossRef]
- Farah, M.B.; Ahmed, Y.; Mahmoud, H.; Shah, S.A.; Al-Kadri, M.O.; Taramonli, S.; Bellekens, X.; Abozariba, R.; Idrissi, M.; Aneiba, A. A survey on blockchain technology in the maritime industry: Challenges and future perspectives. Future Gener. Comput. Syst. 2024, 157, 618–637. [Google Scholar] [CrossRef]
- Dai, M.; Sun, G.; Yu, H.; Wang, S.; Niyato, D. User Association and Channel Allocation in 5G Mobile Asymmetric Multi-Band Heterogeneous Networks. IEEE Trans. Mob. Comput. 2025, 24, 3092–3109. [Google Scholar] [CrossRef]
- Zhou, W.; Xia, C.; Wang, T.; Liang, X.; Lin, W.; Li, X.; Zhang, S. HIDIM: A Novel Framework of Network Intrusion Detection for Hierarchical Dependency and Class Imbalance. Comput. Secur. 2025, 148, 104155. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Zhang, H.; Qiao, S.; Huang, F.; Tian, Q.; Peng, Y. GCCNet: A Novel Network Leveraging Gated Cross-Correlation for Multi-View Classification. IEEE Trans. Multimed. 2025, 27, 1086–1099. [Google Scholar] [CrossRef]
- Heo, J.W.; Ramachandran, G.S.; Dorri, A.; Jurdak, R. Blockchain data storage optimisations: A comprehensive survey. ACM Comput. Surv. 2024, 56, 1–27. [Google Scholar] [CrossRef]
- Rebello, G.A.F.; Camilo, G.F.; de Souza, L.A.C.; Potop-Butucaru, M.; de Amorim, M.D.; Campista, M.E.M.; Costa, L.H.M. A survey on blockchain scalability: From hardware to layer-two protocols. IEEE Commun. Surv. Tutor. 2024, 26, 2411–2458. [Google Scholar] [CrossRef]
- Rani, P.; Sharma, P.; Gupta, I. Toward a greener future: A survey on sustainable blockchain applications and impact. J. Environ. Manag. 2024, 354, 120273. [Google Scholar] [CrossRef]
- Ressi, D.; Romanello, R.; Piazza, C.; Rossi, S. AI-enhanced blockchain technology: A review of advancements and opportunities. J. Netw. Comput. Appl. 2024, 225, 103858. [Google Scholar] [CrossRef]
- Söğüt, E.; Tekerek, A.; Erdem, O.A. Machine Learning-Based DDoS Attack Detection on SDN-Based SCADA Systems. Gazi MüHendislik Bilim. Derg. 2024, 9, 596–611. [Google Scholar] [CrossRef]
- Alotaibi, J. A hybrid software-defined networking approach for enhancing IoT cybersecurity with deep learning and blockchain in smart cities. Peer-to-Peer Netw. Appl. 2025, 18, 123. [Google Scholar] [CrossRef]
- Xu, G.; Lei, L.; Mao, Y.; Li, Z.; Chen, X.; Zhang, K. CBRFL: A Framework for Committee-Based Byzantine-Resilient Federated Learning. J. Netw. Comput. Appl. 2025, 238, 104165. [Google Scholar] [CrossRef]
- Liu, Z.; Jiang, G.; Wu, Y.; Wang, T.; Liu, S.; Ouyang, Z. K-Coverage Estimation for Irregular Targets in Wireless Visual Sensor Networks Deployed in Complex Region of Interest. IEEE Sens. J. 2025, 25, 18370–18383. [Google Scholar] [CrossRef]
- Li, T.; Kouyoumdjieva, S.T.; Karlsson, G.; Hui, P. Data collection and node counting by opportunistic communication. In Proceedings of the 2019 IFIP Networking Conference (IFIP Networking), Warsaw, Poland, 20–22 May 2019. [Google Scholar] [CrossRef]
- Xiao, Z.; Li, T.; Cheng, W.; Wang, D. Apollonius Circles Based Outbound Handover in Macro-Small Wireless Cellular Networks. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016. [Google Scholar] [CrossRef]
- Liu, B.; Lv, N.; Guo, Y.; Li, Y. Recent advances on federated learning: A systematic survey. Neurocomputing 2024, 597, 128019. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, Y.; Huang, Z. A Survey of Deep Transfer Learning in Automatic Modulation Classification. IEEE Trans. Cogn. Commun. Netw. 2025, 11, 1357–1381. [Google Scholar] [CrossRef]
- Huang, W.; Ye, M.; Shi, Z.; Wan, G.; Li, H.; Du, B.; Yang, Q. Federated learning for generalization, robustness, fairness: A survey and benchmark. IEEE TRansactions Pattern Anal. Mach. Intell. 2024, 46, 9387–9406. [Google Scholar] [CrossRef]
- Ali, S.; Li, Q.; Yousafzai, A. Blockchain and federated learning-based intrusion detection approaches for edge-enabled industrial IoT networks: A survey. Ad Hoc Netw. 2024, 152, 103320. [Google Scholar] [CrossRef]
- Chen, J.; Yan, H.; Liu, Z.; Zhang, M.; Xiong, H.; Yu, S. When federated learning meets privacy-preserving computation. ACM Comput. Surv. 2024, 56, 1–36. [Google Scholar] [CrossRef]
- Manikumar, S.L.; Savitha, K. Design and Implementation of Secure DataTransmission Using SDN and Advanced Cryptographic Techniques. Int. J. Adv. Netw. Appl. 2025, 16, 6670–6676. [Google Scholar]
- Alrashede, H.; Eassa, F.; Ali, A.M.; Albalwy, F.; Aljihani, H. A Blockchain-Based Security Framework for East-West Interface of SDN. Electronics 2024, 13, 3799. [Google Scholar] [CrossRef]
- Zhang, J.; Sui, H.; Sun, X.; Ge, C.; Zhou, L.; Susilo, W. GrabPhisher: Phishing Scams Detection in Ethereum via Temporally Evolving GNNs. IEEE Trans. Serv. Comput. 2024, 17, 3727–3741. [Google Scholar] [CrossRef]
- Hsu, M.H.; Liu, C.C. A Decentralized Framework for the Detection and Prevention of Distributed Denial of Service Attacks Using Federated Learning and Blockchain Technology. Eng. Proc. 2025, 92, 48. [Google Scholar] [CrossRef]
- Shahraki, A.S.; Rudolph, C.; Alavizadeh, H.; Kayes, A.S.M.; Rahayu, W.; Tari, Z. Securing cross-domain data access with decentralized attribute-based access control. Ad Hoc Netw. 2025, 173, 103807. [Google Scholar] [CrossRef]
- Derhab, A.; Guerroumi, M.; Belaoued, M.; Cheikhrouhou, O. BMC-SDN: Blockchain-Based Multicontroller Architecture for Secure Software-Defined Networks. Wirel. Commun. Mob. Comput. 2021, 2021, 9984666. [Google Scholar] [CrossRef]
- Rahman, A.; Khan, M.S.I.; Montieri, A.; Islam, M.J.; Karim, M.R.; Hasan, M.; Kundu, D.; Nasir, M.K.; Pescapè, A. BlockSD-5GNet: Enhancing security of 5G network through blockchain-SDN with ML-based bandwidth prediction. Trans. Emerg. Telecommun. Technol. 2024, 35, e4965. [Google Scholar] [CrossRef]
- Ajithraj, R.A.; Rajagopalan, N. A method of preventing endpoint exploits in healthcare with block-chain token authorization implementation in SDN stack. AIP Conf. Proc. 2024, 3031, 020013. [Google Scholar] [CrossRef]
- Bajpai, N.; Dhingra, M.; Chaurasia, N. A Review on Internet of Things (IoT) Environment Using Software-Defined Networking (SDN) Based on Different. In Advances in Artificial Intelligence and Machine Learning: Select Proceedings of ICAAAIML 2023, Volume 1; Springer: Singapore, 2025; Volume 1264, p. 471. [Google Scholar] [CrossRef]
- Indrason, N.; Saha, G. Exploring Blockchain-driven security in SDN-based IoT networks. J. Netw. Comput. Appl. 2024, 224, 103838. [Google Scholar] [CrossRef]
- Haritha, K.; Vellela, S.S.; Vuyyuru, L.R.; Malathi, N.; Dalavai, L. Distributed Blockchain-SDN Models for Robust Data Security in Cloud-Integrated IoT Networks. In Proceedings of the 2024 3rd International Conference on Automation, Computing and Renewable Systems (ICACRS), Pudukkottai, India, 4–6 December 2024; pp. 623–629. [Google Scholar] [CrossRef]
- Rahman, A.; Wadud, M.A.H.; Islam, M.J.; Kundu, D.; Bhuiyan, T.A.U.H.; Muhammad, G.; Ali, Z. Internet of medical things and blockchain-enabled patient-centric agent through SDN for remote patient monitoring in 5G network. Sci. Rep. 2024, 14, 5297. [Google Scholar] [CrossRef]
- Wijesekara, P.A.D.S.N. Intrusion Detection Using Blockchain in Software-Defined Networking: A Literature Review. J. Eng. Sci. Technol. Rev. 2025, 18, 57–79. [Google Scholar] [CrossRef]
- Ohri, P.; Daniel, A.; Guha Neogi, S.; Muttoo, S.K. Blockchain-based security framework for mitigating network attacks in multi-SDN controller environment. Int. J. Inf. Technol. 2024, 1–13. [Google Scholar] [CrossRef]
- Hakiri, A.; Sellami, B.; Ben Yahia, S. Joint energy efficiency and network optimization for integrated blockchain-SDN-based internet of things networks. Future Gener. Comput. Syst. 2025, 163, 107519. [Google Scholar] [CrossRef]
- Zhao, D.; Zhang, D.; Pei, Q.; Liu, L.; Yue, P. Blockchain-Based Security Deployment and Resource Allocation in SDN-Enabled MEC System. IEEE Internet Things J. 2024, 11, 40417–40430. [Google Scholar] [CrossRef]
- Okon, A.A.; Sallam, K.; Hossain, M.F.; Jagannath, N.; Jamalipour, A.; Munasinghe, K.S. Enhancing Multi-Operator Network Handovers with Blockchain-Enabled SDN Architectures. IEEE Access 2024, 12, 82848–82866. [Google Scholar] [CrossRef]
- Karakus, M. GATE-BC: Genetic algorithm-powered QoS-aware cross-network traffic engineering in blockchain-enabled SDN. IEEE Access 2024, 12, 36523–36545. [Google Scholar] [CrossRef]
- Mateus, J.; Lusilao Zodi, G.A.; Bagula, A. Federated Learning-Based Solution for DDoS Detection in SDN. In Proceedings of the 2024 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 19–22 February 2024; pp. 875–880. [Google Scholar]
- Ma, J.; Su, W. Collaborative DDoS defense for SDN-based AIoT with autoencoder-enhanced federated learning. Inf. Fusion 2025, 117, 102820. [Google Scholar] [CrossRef]
- Mahmod, A.; Pace, P.; Iera, A. SDN-Assisted Client Selection to Enhance the Quality of Federated Learning Processes. In Proceedings of the 2024 IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024; pp. 1–6. [Google Scholar]
- Raza, M.; Saeed, M.; Riaz, M.; Sattar, M. Federated learning for privacy preserving intrusion detection in software defined networks. IEEE Access 2024, 12, 69551–69567. [Google Scholar] [CrossRef]
- Tran, H.A.; Tran, D. FL4SDN: A Fast-Convergent Federated Learning for Distributed and Heterogeneous SDN. IEEE Intell. Syst. 2024, 40, 68–79. [Google Scholar] [CrossRef]
- Javaid, M.U. InSDN Dataset 2020. 2023. Available online: https://www.kaggle.com/datasets/muhammadumarjavaid/insdn-dataset-2020 (accessed on 30 June 2025).

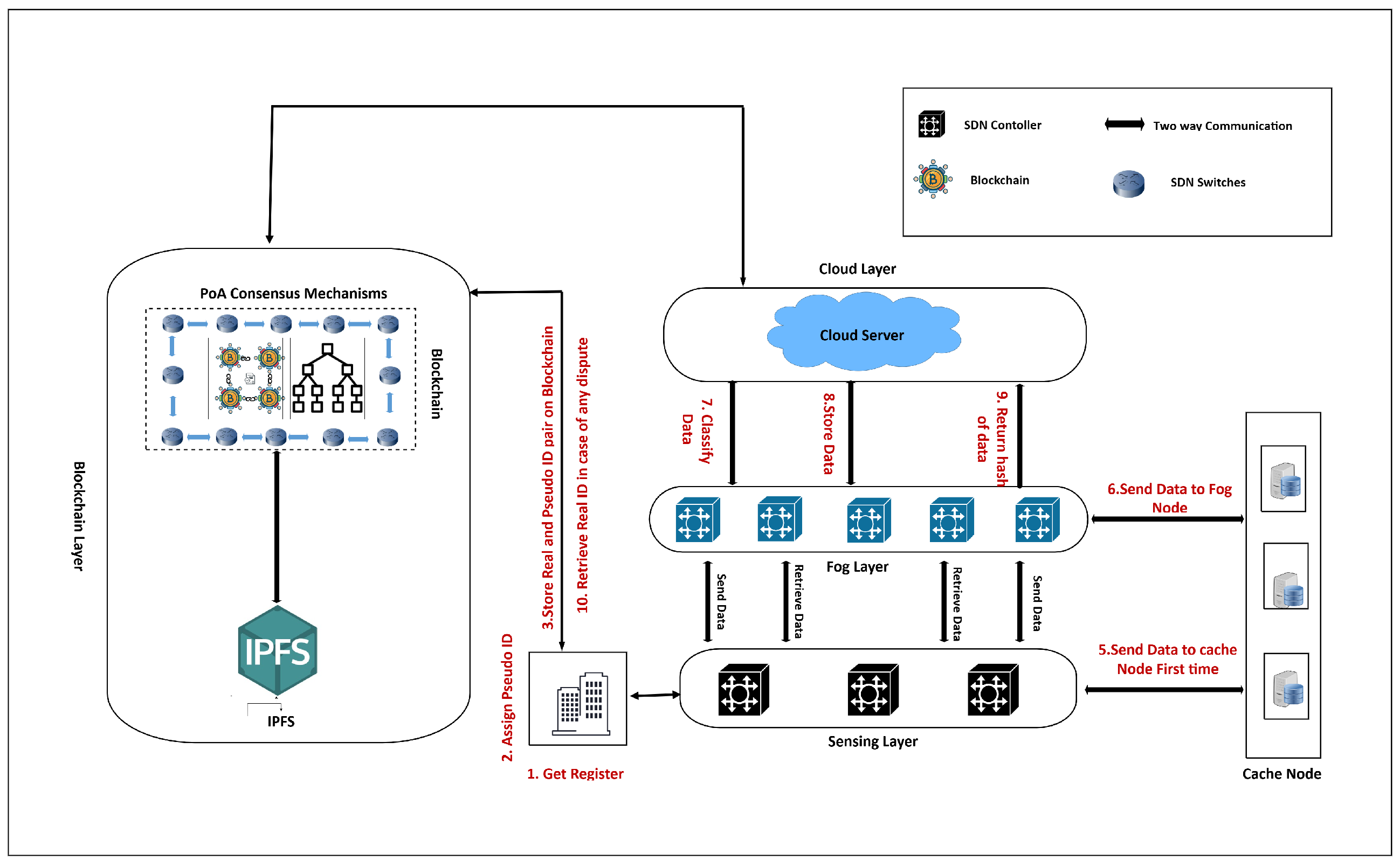



| Abbreviation | Description |
|---|---|
| AUC | Area Under the Curve |
| CNN | Convolutional Neural Network |
| FL | Federated Learning |
| IPFS | InterPlanetary File System |
| PDR | Packet Delivery Ratio |
| PK | Public Key |
| PoA | Proof of Authority |
| SDN | Software-Defined Network |
| SD-WAN | Software-Defined Wide-Area Network |
| SK | Secret Key |
| SVM | Support Vector Machine |
| TLS | Transport Layer Security |
| VM | Virtual Machine |
| Existing Model | Addressed Limitations | Performance Parameters | Research Gaps |
|---|---|---|---|
| A blockchain-based distributed mechanism is proposed that ensures distributed credential-based access control and encrypted security of data while utilizing the capabilities of the Ethereum network and customized blockchain protocols [34]. | Existing techniques are not able to secure the east–west interface and communication between SDN nodes, which compromises the security of the overall network. | Authentication time, decentralization, scalability, authentication, system latency, authentication latency, registration latency, throughput, and access control. | The proposed model is highly dependent on the Ethereum network, which leads to large network overhead, such as increased latency and operational costs due to blockchain processing overhead. |
| A blockchain and federated-learning-enabled security protocol is proposed that efficiently detects denial of services, distributed denial of services, and replay attacks and prevents the network from them [36]. | The traditional techniques are not able to efficiently detect and safeguard the network against these attacks. SDN networks are vulnerable to several attacks due to the rapid increase in IoT devices. | Data flow rate, accuracy, true positive rate, recall, true negative rate, and velocity updates. | The proposed model is vulnerable to the issues of performance degradation, as the proposed model has a large computational overhead of federated learning. |
| A decentralized attribute-based access control mechanism is proposed that removes centralized entities from the network and ensures effective and reliable cross-domain access control [37]. | Existing attribute-based access control mechanisms are not able to efficiently ensure security of cross-domain networks due to the involvement of a centralized attribute evaluation party. | Number of predicates, number of attributes, model performance, and execution time. | The proposed model is vulnerable to the issue of performance bottlenecks due to the large computational overhead of group signature schemes, especially when handling many attributes or predicates. |
| A blockchain-enabled adaptive fading reputation mechanism is proposed | SDN networks are vulnerable to various attacks, such as false data injection attacks | Detection rate, execution time, number of switches, number of hosts | The operations of the proposed model are highly dependent on a master controller of a respective domain. |
| effective and optimal detection of malicious nodes in the network [38]. | SDN networks are vulnerable to various attacks, such as false data injection attacks, denial of service, and distributed denial of service. Due to these attacks, the SDN networks are facing the issue of topology inconsistency among network controllers. | detection time, reputation, and number of observation intervals. | It causes the issue of a single point of failure within each domain, which compromises the decentralization objective of the proposed model. |
| A machine learning and blockchain-enabled SDN is proposed that ensures network security while simultaneously preserving the privacy of entities and the flexibility of the network [39]. | Fifth-generation networks are vulnerable to various issues such as low data protection, entity privacy leakage, and data loss. | Topology, bandwidth, throughput, node failure rate, computational delay, and bandwidth prediction. | The proposed model has a large computational overhead and network latency due to the training of LSTM and MLP classifiers, especially in real-time high-speed fifth-generation networks. |
| Parameter Name | Values |
|---|---|
| Dataset Used | InSDN Dataset (2020) |
| Number of Network Flows | Over 2 million labeled telemetry records |
| Network Environment | Multi-controller SD-WAN with east–west communication |
| Data Features | Telemetry metrics, flow statistics, device logs, network metadata |
| Data Preprocessing | Normalization, feature encoding, imputation, dimensionality reduction |
| Federated Learning Setup | 10 ONOS SDN controllers as distributed clients |
| Communication Rounds | 150 federated training rounds |
| Model Architecture | BFL-SDWANTrust: CNN + SVM with Blockchain-based Federated Learning |
| Optimizer | Adam optimizer (learning rate = 0.001) for CNN; Grid search for SVM |
| Loss Function | Cross-Entropy Loss (CNN); Hinge Loss (SVM) |
| Evaluation Metrics | Accuracy, Precision, Recall, F1-Score, AUC, Transaction Latency, Training Time, Testing Time, Packet-Drop Ratio |
| Accuracy Achieved | 99.8% (on test data) |
| Precision | 98.0% |
| Recall | 97.0% |
| F1-Score | 97.5% |
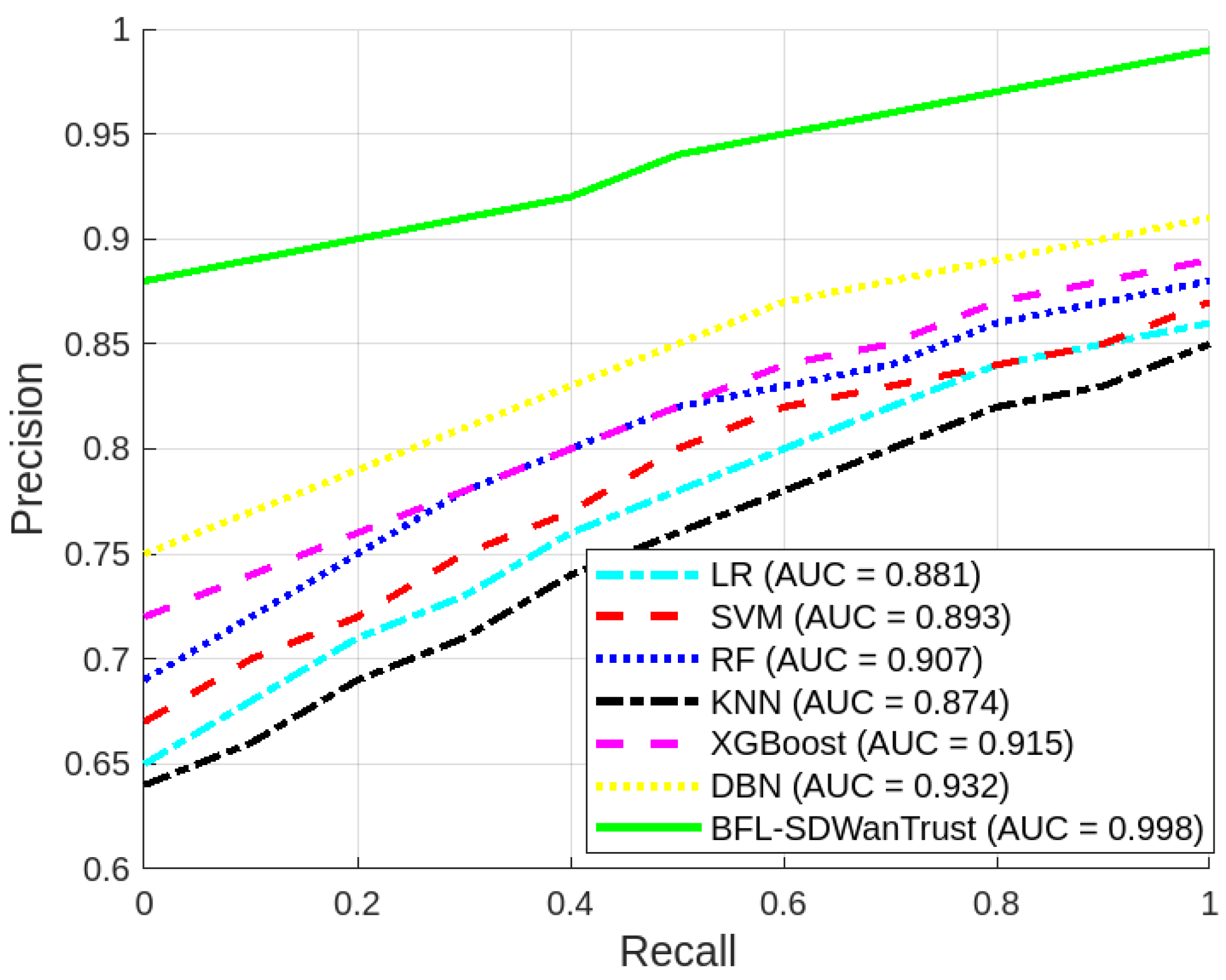
| AUC Score | 0.998 |
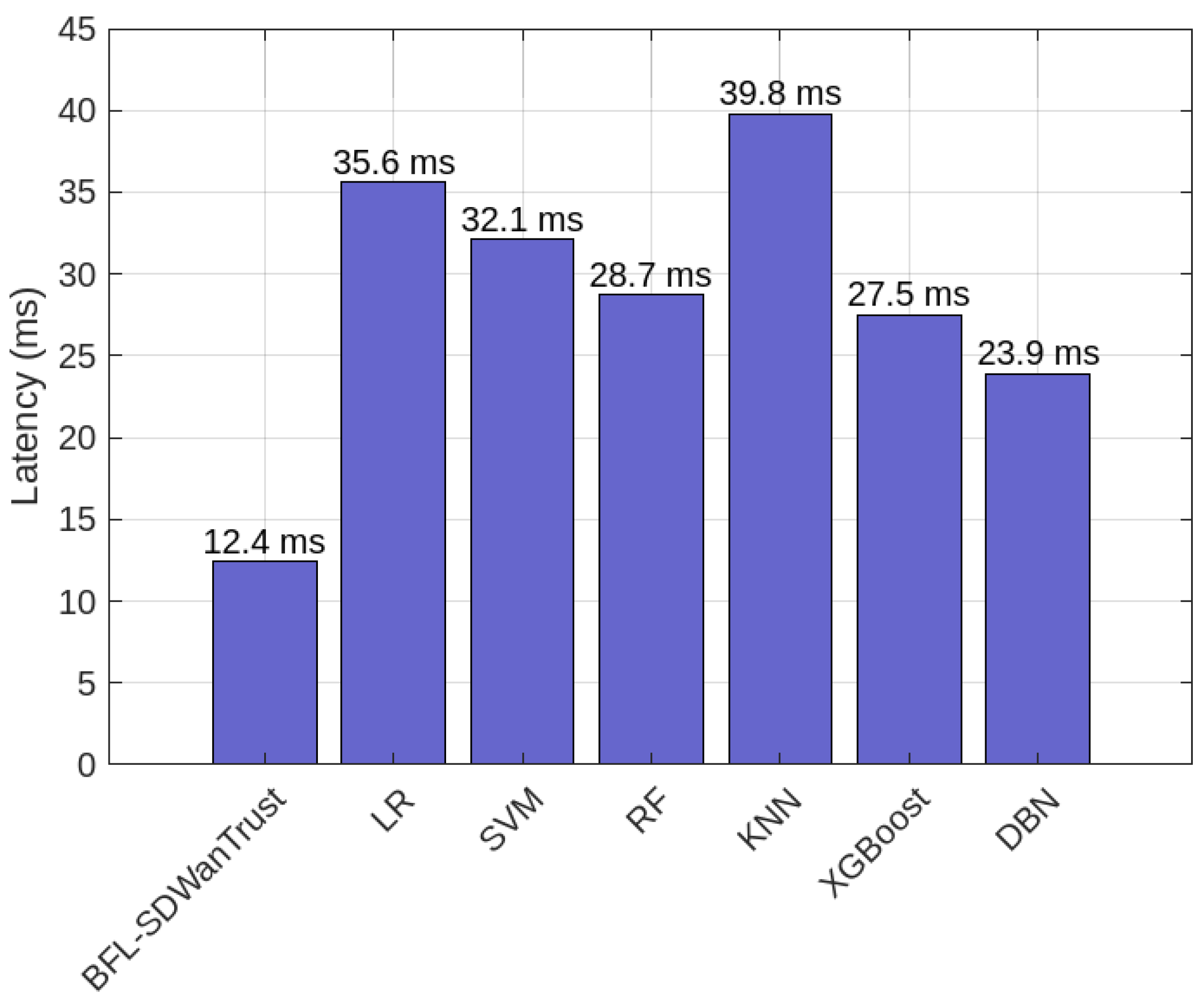
| Transaction Latency | 13.6 ms (lowest among all compared models) |
| Training Time | 12.0 s (lowest) |
| Testing Time | 3.1 s (lowest) |
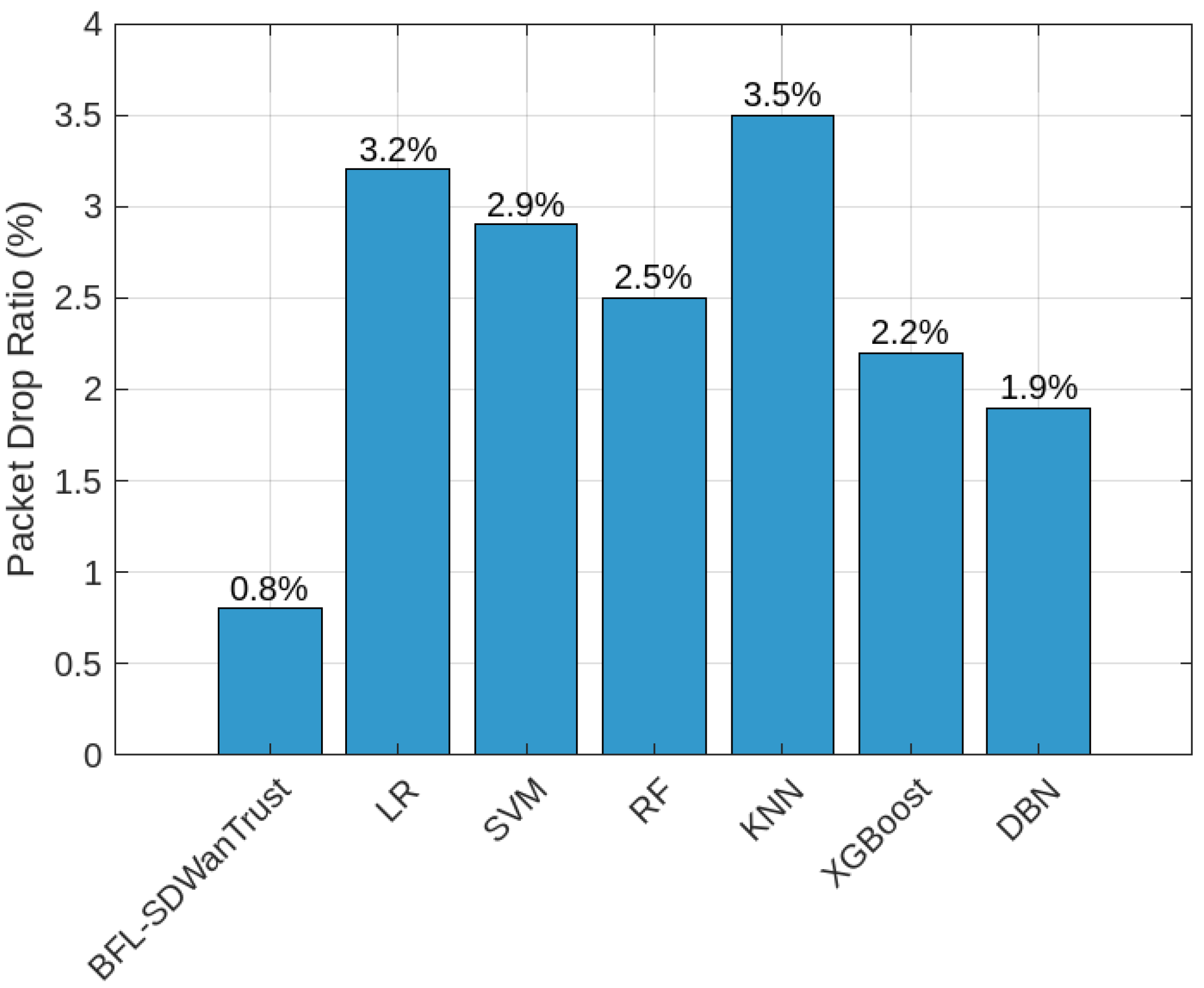
| Packet-Drop Ratio | 0.8% (lowest) |
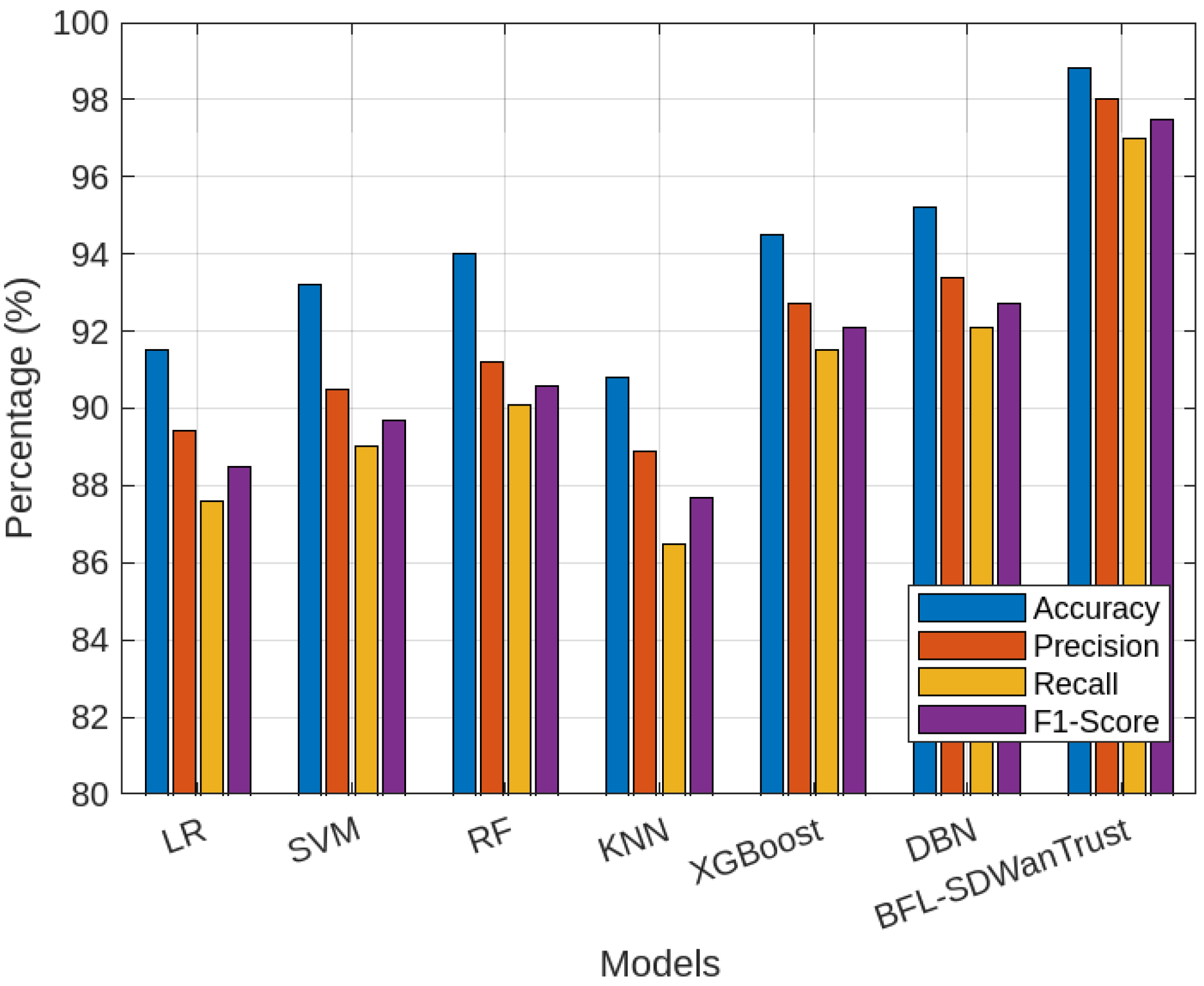
| Comparison Models | LR (91.5%), SVM (93.2%), RF (94.0%), KNN (90.8%), XGBoost (94.5%), DBN (95.2%), BFL-SDWANTrust (99.8%) |
| Privacy Preservation | Blockchain-integrated model aggregation with smart contract enforcement |
| Hardware Used | NVIDIA RTX 4090, 128 GB RAM |
| Model | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| LR | 91.5 | 89.4 | 87.6 | 88.5 |
| SVM | 93.2 | 90.5 | 89.0 | 89.7 |
| RF | 94.0 | 91.2 | 90.1 | 90.6 |
| KNN | 90.8 | 88.9 | 86.5 | 87.7 |
| XGBoost | 94.5 | 92.7 | 91.5 | 92.1 |
| DBN | 95.2 | 93.4 | 92.1 | 92.7 |
| BFL-SDWANTrust | 98.8 | 98.0 | 97.0 | 97.5 |
| Actual / Predicted | Normal | DDoS | Recon | Backdoor |
|---|---|---|---|---|
| Normal | 240 | 2 | 1 | 0 |
| DDoS | 3 | 230 | 4 | 1 |
| Recon | 2 | 0 | 225 | 3 |
| Backdoor | 1 | 2 | 0 | 216 |
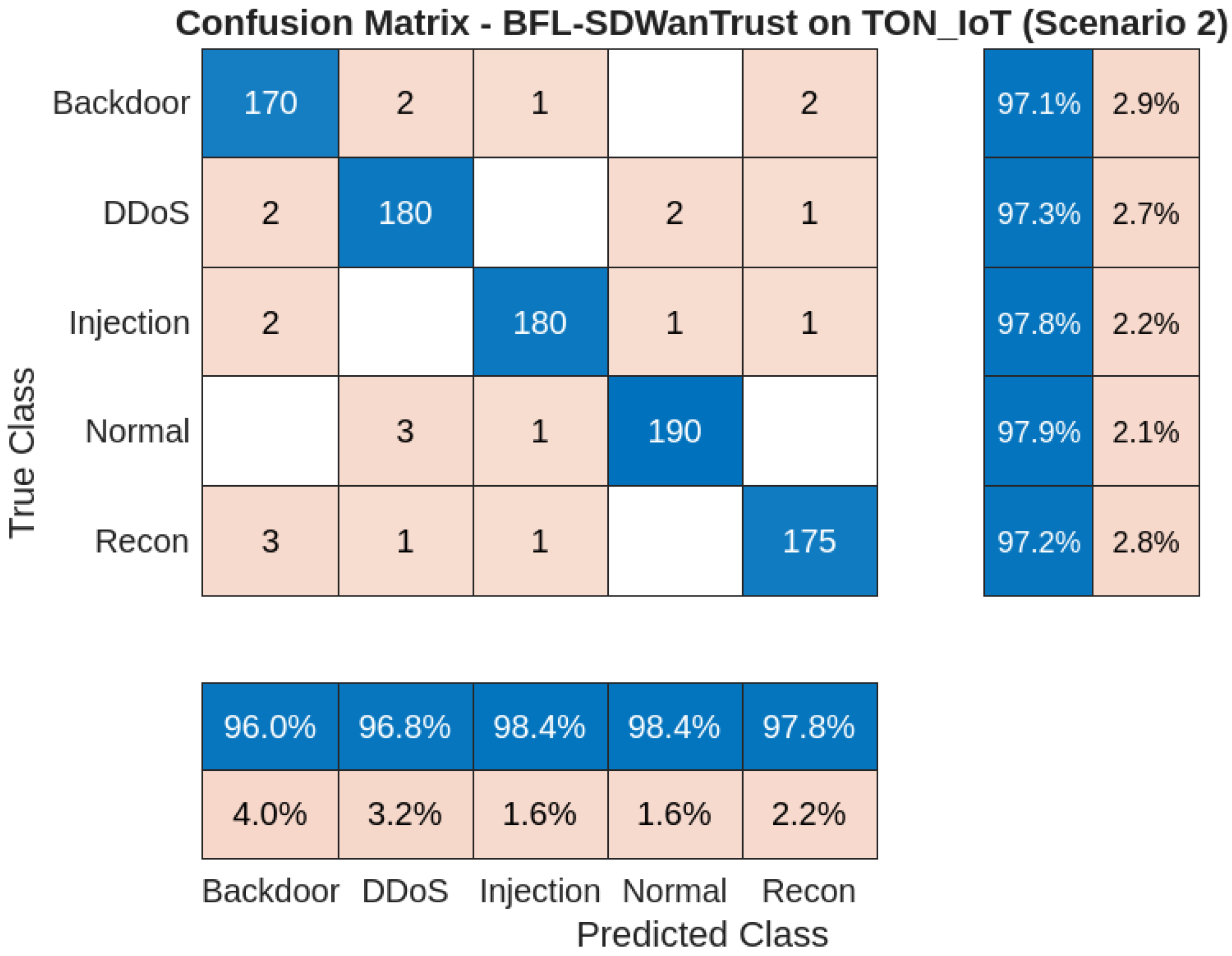
| Actual / Predicted | Normal | DDoS | Recon | Backdoor | Injection |
|---|---|---|---|---|---|
| Normal | 190 | 3 | 0 | 0 | 1 |
| DDoS | 2 | 180 | 1 | 2 | 0 |
| Recon | 0 | 1 | 175 | 3 | 1 |
| Backdoor | 0 | 2 | 2 | 170 | 1 |
| Injection | 1 | 0 | 1 | 2 | 180 |
| Model | Packet-Drop Ratio (%) |
|---|---|
| BFL-SDWANTrust | 0.8 |
| LR | 3.2 |
| SVM | 2.9 |
| RF | 2.5 |
| KNN | 3.5 |
| XGBoost | 2.2 |
| DBN | 1.9 |
| Model | Latency (ms) |
|---|---|
| BFL-SDWANTrust | 12.4 |
| LR | 35.6 |
| SVM | 32.1 |
| RF | 28.7 |
| KNN | 39.8 |
| XGBoost | 27.5 |
| DBN | 23.9 |
| Model | AUC (PR) |
|---|---|
| BFL-SDWANTrust | 0.998 |
| DBN | 0.932 |
| XGBoost | 0.915 |
| RF | 0.907 |
| SVM | 0.893 |
| LR | 0.881 |
| KNN | 0.874 |
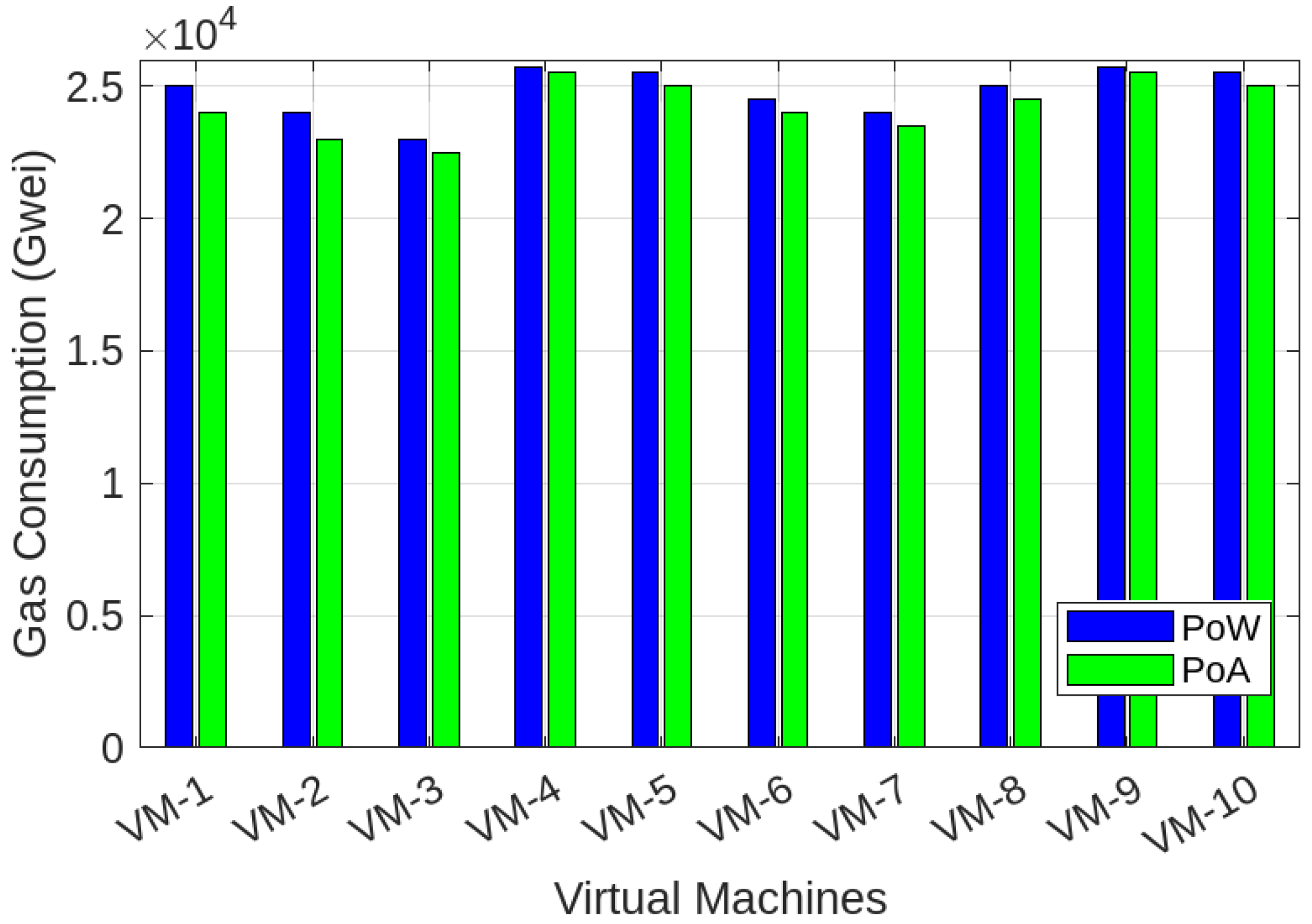
| VM Instance | PoW (Gwei) | PoA (Gwei) |
|---|---|---|
| VM-1 | 25,000 | 24,000 |
| VM-2 | 24,000 | 23,000 |
| VM-3 | 23,000 | 22,500 |
| VM-4 | 25,700 | 25,500 |
| VM-5 | 25,500 | 25,000 |
| VM-6 | 24,500 | 24,000 |
| VM-7 | 24,000 | 23,500 |
| VM-8 | 25,000 | 24,500 |
| VM-9 | 25,700 | 25,500 |
| VM-10 | 25,500 | 25,000 |
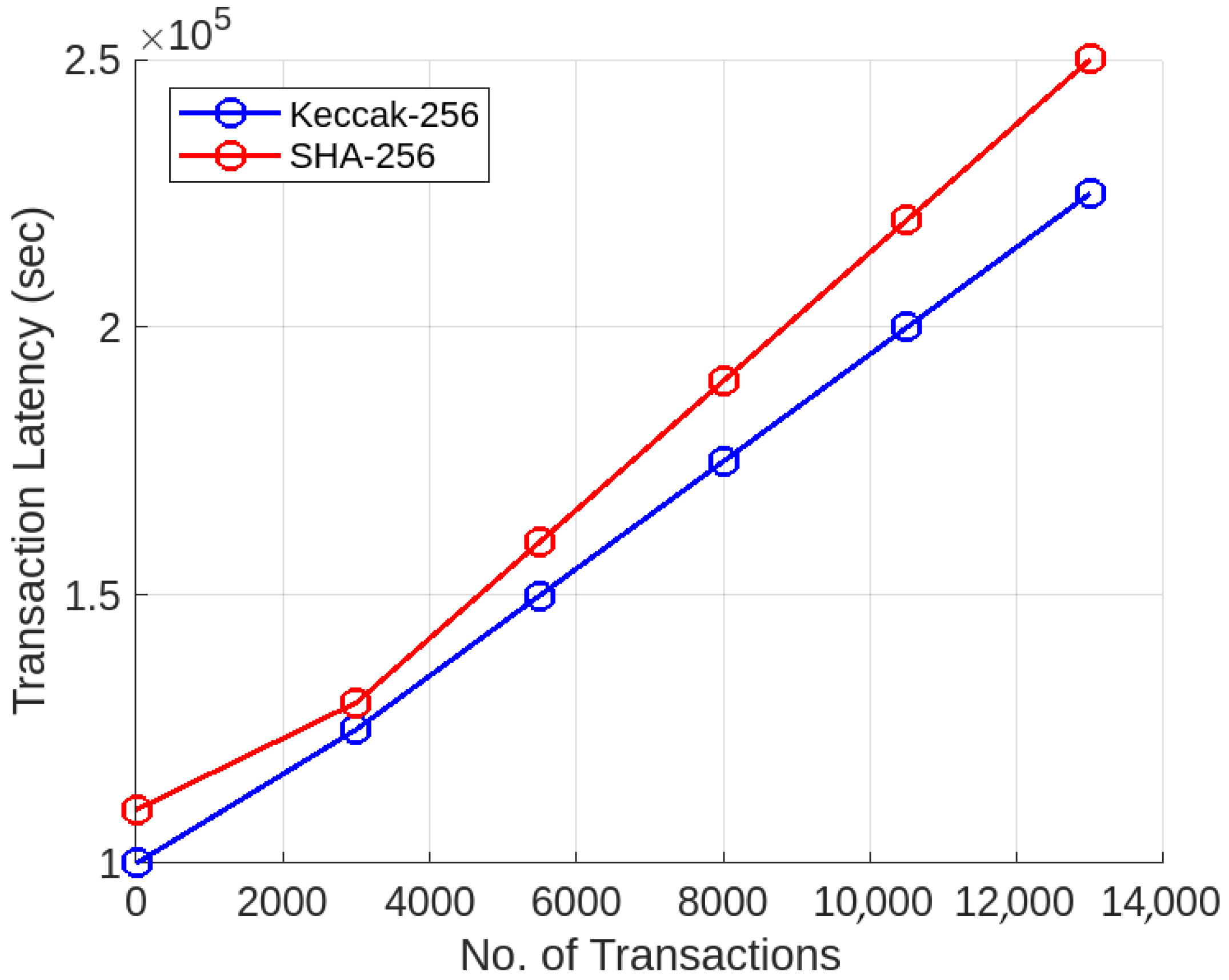
| No. of Transactions | Keccak-256 Latency (s) | SHA-256 Latency (s) |
|---|---|---|
| 1500 | 100,000 | 110,000 |
| 3000 | 125,000 | 130,000 |
| 5500 | 150,000 | 160,000 |
| 8000 | 175,000 | 190,000 |
| 10,500 | 200,000 | 220,000 |
| 13,000 | 225,000 | 250,000 |
| Model | Training Time (s) | Testing Time (s) |
|---|---|---|
| LR | 20.0 | 5.2 |
| SVM | 28.0 | 6.8 |
| RF | 35.0 | 7.5 |
| KNN | 25.0 | 6.1 |
| XGBoost | 42.0 | 8.0 |
| DBN | 40.0 | 7.2 |
| BFL-SDWANTrust | 12.0 | 3.1 |
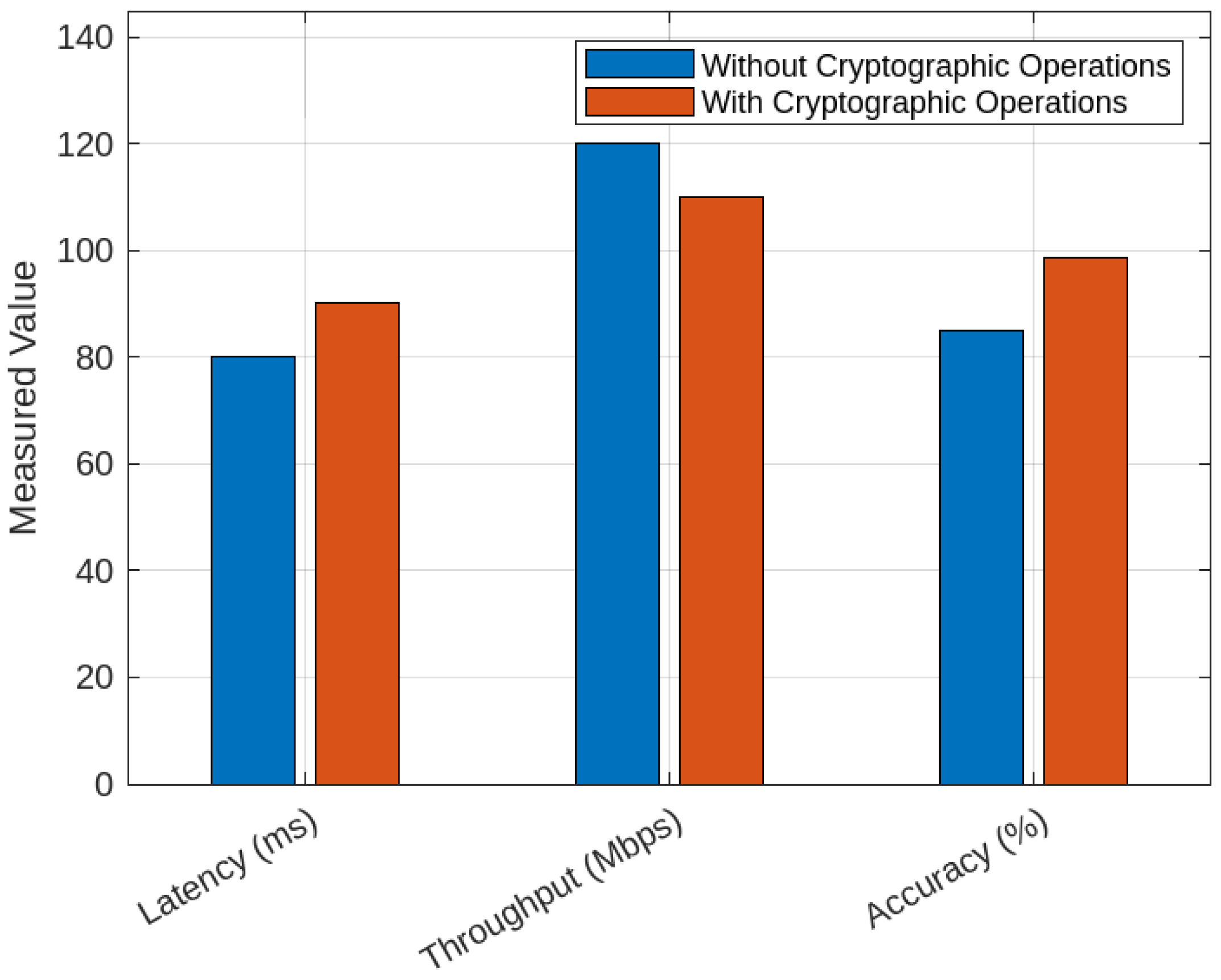
| Scenario | Latency (ms) | Throughput (Mbps) | Accuracy (%) |
|---|---|---|---|
| Without Cryptographic Operations | 80.00 | 120.00 | 85.0 |
| With Cryptographic Operations | 90.16 | 110.00 | 98.8 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mushtaq, M.; Kifayat, K. BFL-SDWANTrust: Blockchain Federated-Learning-Enabled Trust Framework for Secure East–West Communication in Multi-Controller SD-WANs. Sensors 2025, 25, 5188. https://doi.org/10.3390/s25165188
Mushtaq M, Kifayat K. BFL-SDWANTrust: Blockchain Federated-Learning-Enabled Trust Framework for Secure East–West Communication in Multi-Controller SD-WANs. Sensors. 2025; 25(16):5188. https://doi.org/10.3390/s25165188
Chicago/Turabian StyleMushtaq, Muddassar, and Kashif Kifayat. 2025. "BFL-SDWANTrust: Blockchain Federated-Learning-Enabled Trust Framework for Secure East–West Communication in Multi-Controller SD-WANs" Sensors 25, no. 16: 5188. https://doi.org/10.3390/s25165188
APA StyleMushtaq, M., & Kifayat, K. (2025). BFL-SDWANTrust: Blockchain Federated-Learning-Enabled Trust Framework for Secure East–West Communication in Multi-Controller SD-WANs. Sensors, 25(16), 5188. https://doi.org/10.3390/s25165188









