Highlights
What are the main findings?
- Efficient Drone-to-Drone communication protocol fusion with a blockchain network for the purpose of secure and efficient Unmanned Aerial Vehicle Traffic Management is presented.
What is the implication of the main finding?
- Superior performance compared to state of the art.
- Lower computational and storage costs.
Abstract
Unmanned Aerial Vehicles (UAVs) face collision risks due to Beyond Visual Line of Sight operations. Therefore, UAV Traffic Management (UTM) systems are used to manage and monitor UAV flight paths. However, centralized UTM systems are susceptible to various security attacks and are inefficient in managing flight data from different service providers. It further fails to provide low-latency communication required for UAV real-time operations. Thus, this paper proposes to integrate Drone-to-Drone (D2D) communication protocol into a secure public blockchain-based UTM system to enable direct communication between UAVs for efficient collision avoidance. The D2D protocol is designed using SHA256 hash function and bitwise XOR operations. A proof of concept has been built to verify that the UTM system is secure by enabling authorized service providers to view sensitive flight data only using legitimate secret keys. The security of the protocol has been analyzed and has been proven to be secure from key disclosure, adversary-in-the-middle, replay, and tracking attacks. Its performance has been evaluated and is proven to outperform existing studies by having the lowest computation cost of 0.01 ms and storage costs of 544–800 bits.
1. Introduction
Beyond Visual Line of Sight (BVLOS) operation of Unmanned Aerial Vehicles (UAVs), i.e., operation conducted outside of the direct visual range of the pilot, significantly enhances the capabilities of UAVs by allowing them to operate and perform tasks well beyond the direct line of sight of the operator. This, however, introduces additional challenges. BVLOS flights pose collision risks due to the lack of direct visual guidance and increased vulnerability to environmental factors such as adverse weather, rogue drones, birds, etc. To address these risks, researchers have integrated high-speed cameras [1], LiDAR [2], radar systems [3], and radio frequency-based methods [4] for detecting obstacles and potentially malicious drones. However, effective UAV traffic monitoring goes beyond local sensing and requires coordinated tracking and information sharing among UAVs.
To enable safe and efficient UAV operations, a robust UAV Traffic Management (UTM) system is essential. Remote Identification (RID) plays a crucial role in this framework by enabling authorities and the public to identify UAVs and access flight data in real-time. While RID improves transparency, it also introduces serious privacy and security risks by making UAV identities and locations publicly visible [4,5]. Furthermore, current UTMs are typically centralized, making them susceptible to single points of failure, data tampering, and unauthorized access. These systems are unable to ensure secure and efficient interactions between service providers and end-users.
As a solution, researchers have proposed integrating blockchain technology into UTMs [6,7,8,9]. The decentralized and immutable nature of blockchain makes it a promising solution for enhancing security and trust in UAV ecosystems. Smart contracts can further automate critical tasks related to traffic monitoring, flight planning, and authorization. However, while blockchain enhances transparency, it also poses privacy risks, as sensitive flight data becomes permanently visible on the public ledger. Additionally, blockchain platforms such as Ethereum suffer from transaction latency (e.g., 6–45 s) [10], which limits their ability to support real-time UAV coordination, particularly in collision avoidance scenarios.
Therefore, Drone-to-Drone (D2D) communication emerges as a vital mechanism for real-time data exchange and coordination in low-altitude airspace [11]. D2D communication enables UAVs to autonomously negotiate flight paths and avoid collisions without relying on centralized infrastructure. Various technologies have been employed for D2D communication, including short-range wireless options such as Wi-Fi, Zigbee, and Bluetooth, as well as long-range alternatives like cellular and satellite links [12,13]. Among these, LoRa stands out due to its long transmission range, low power consumption, and operation in unlicensed Industrial, Scientific, and Medical (ISM) bands, making it suitable for energy-constrained UAVs operating in wide-area BVLOS missions [14].
LoRa and the MAVLink protocol have been widely adopted for telemetry and communication in UAV systems, where MAVLink structures the data and LoRa transmits it over long distances with minimal power consumption. However, MAVLink lacks built-in encryption mechanisms [15], leaving UAVs vulnerable to spoofing, interception, and other security attacks. Therefore, there is a need for a secure, low-latency D2D communication protocol tailored for UAVs operating in blockchain-based UTM environments.
Currently, no existing protocol enables UAVs from different service providers to perform D2D communication securely within a public blockchain-based UTM. To address this gap, this research proposes a lightweight LoRa-based D2D communication protocol that leverages a public blockchain to enable efficient flight management across multiple service providers, thereby minimizing latency and complexity in data exchange between UAVs. LoRa is adopted not only for its low power and wide range technical advantages, but also to support infrastructure independence for blockchain-based UTM systems.
This work focuses on the design of the communication protocol and its robustness against four common security threats frequently observed in Internet of Things (IoT) systems: key disclosure, adversary-in-the-middle, replay, and tracking attacks [16]. Specifically, the protocol utilizes session-based keys to protect against key disclosure, employs mutual authentication steps to counter adversary-in-the-middle attacks, incorporates timestamps and random number mechanisms to prevent replay attacks, and implements dynamic identity protection to mitigate tracking threats. It is essential to note that this paper does not address broader performance evaluation of LoRa, such as its susceptibility to noise interference, energy consumption, and transmission reliability. The contributions of this paper are as follows:
- A lightweight protocol designed to enable secure D2D LoRa-based communication for secure public blockchain-based traffic management to avoid collisions.
- This protocol enables UAVs to authenticate nearby UAVs from different service providers that are registered with the UTM system.
- The protocol protects sensitive flight data of UAVs stored on the public blockchain-based UTM from attackers.
- The proposed protocol has been analyzed to ensure it is secure from key disclosure, adversary-in-the-middle, replay, and tracking attacks.
The remainder of this paper is structured as follows: Section 2 reviews related work on improving the UTM systems using blockchain technologies, and the security of LoRa in UAV communication. Section 3 describes a secure LoRa D2D communication protocol for public blockchain-based traffic management systems. Section 4 presents a proof of concept for the proposed LoRa D2D communication protocol, utilizing a public blockchain-based UTM. Section 5 demonstrates the security of the proposed protocol, and Section 6 presents a comparative performance analysis. Section 7 describes the limitations of the system and how it can be addressed in future work. Section 8 concludes this paper.
2. Related Works
Blockchain has been successfully integrated with UAV networks to secure UAV communication and enable data protection (e.g., data integrity and identity authentication). It was further utilized with UTM systems, as demonstrated by Allouch et al., where a lightweight, permissioned blockchain-based UTM was employed to provide secure and immutable traffic data for UAV stakeholders, including UAV service providers, UAV operators, and end-users [7]. UAV data were stored in the InterPlanetary File System (IPFS), and the hashes generated from the data were stored on the HyperLedger Fabric blockchain. Rahman et al. proposed a blockchain-based policy enforcement mechanism in drone-based delivery service systems [6]. The mechanism establishes policies to allocate predefined flight paths for different drones at different times, thereby avoiding collisions and ensuring the privacy of citizens by restricting their access to unauthorized areas. The blockchain enforced policies to monitor compliance with drone flights and identify non-compliant drone services, penalizing the corresponding service providers.
Although blockchain is able to improve UAV network security, messages transmitted using communication channels such as Wi-Fi, cellular, and LoRa are vulnerable to security attacks. LoRaWAN, acting as a MAC layer for LoRa communication, offers robust security features. However, LoRaWAN can experience increased data latency and a higher rate of packet collision in densely populated networks due to its ALOHA-based access scheme [17]. One of the key contributors to latency in LoRaWAN is the Time on Air (ToA), which refers to the duration a packet occupies the wireless channel during transmission, determined by the Spreading Factor (SF) parameter. LoRaWAN with a lower SF (e.g., SF7 and SF8) has shorter airtime, typically below 700 ms; however, this rises to above one second for long-distance transmission using higher SFs (e.g., SF9–SF12) [18]. To address latency concerns, particularly for time-critical transmissions, Downlink Control Packets (DCPs) have been used where gateways periodically transmit DCPs to synchronize end devices, enabling them to schedule uplink transmissions [19]. Since high data latency and packet collision rates can affect the reliability of D2D communication, LoRa has been used in UAVs due to its low power consumption and lower latency compared to LoRaWAN [20]. Consequently, standard LoRaWAN is excluded from our comparative analysis as its architecture does not meet the real-time requirements of direct D2D communication among UAVs.
Despite its popularity, LoRa lacks security features, making it necessary to implement additional protection when utilizing it for communication. In contrast, the MAVLink protocol has been widely used in UAV networks due to its security features and lightweight structure, which is supported by different types of transport layers. With MAVLink signing capability, transmitted messages can be authenticated, ensuring their integrity and origin. This added security measure helps protect against tampering and unauthorized access, making the combination of MAVLink and LoRa a more secure choice for UAV communication [14]. However, MAVLink itself is susceptible to security attacks, such as adversary-in-the-middle and tracking attacks, because it does not support encryption [15]. Therefore, encryption techniques such as symmetric encryption algorithms have been widely employed to enhance the security of the MAVLink protocol [21,22]. Khan et al. utilized the Caesar cipher to encrypt MAVLink messages [15]. However, this cipher has been proven to be vulnerable to security attacks [23].
In addition to improving MAVLink security, several researchers have proposed secure protocols to enable reliable D2D communication [8,24,25,26]. However, existing research in the field lacks a specific focus on enhancing secure message transmission using LoRa-based D2D communication for secure public blockchain-based traffic management. Therefore, this paper aims to address this research gap.
3. Secure LoRa Drone-to-Drone Communication Using Public Blockchain-Based Traffic Management System
The proposed LoRa D2D communication protocol aims to support all UAVs offered by different service providers. Hence, in order to be compatible with all of them, this protocol must consider all available UAV flight times, including those of professional, consumer, toy, and military type drones. To date, the MQ-C Gray Eagle, a military drone, has the longest flight time of 25 h [27]. Thus, it is crucial to have efficient key management that all UAVs can support throughout their flight navigation.
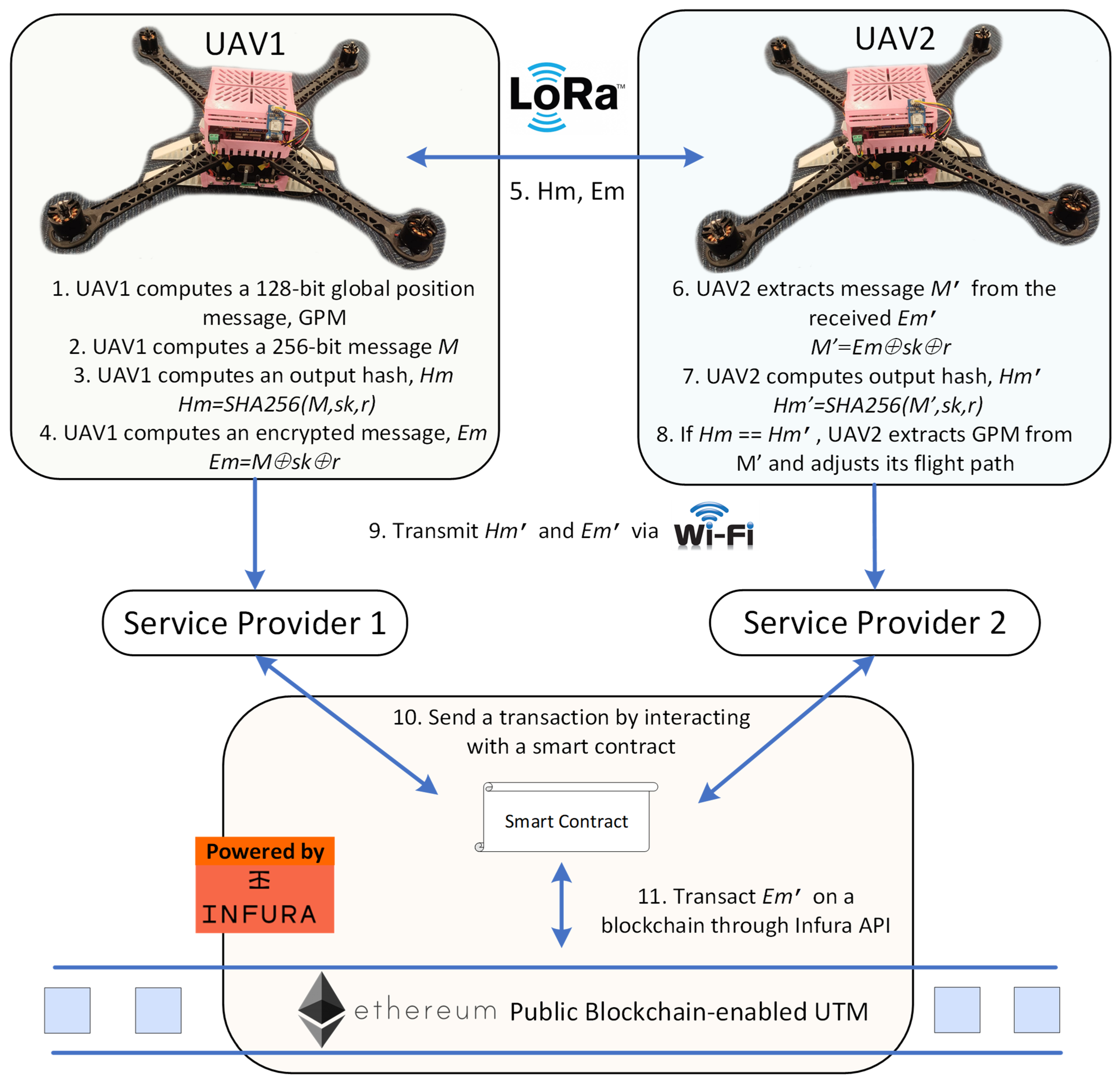
The proposed protocol consists of two phases: the initial phase and the authentication phase. Notations used in the protocol are listed in Table 1, and the infographic is depicted in Figure 1. The proposed protocol integrates a public blockchain to enhance transparency in the UTM system without relying on a central authority. The data stored on the public blockchain is immutable due to its decentralized ledger architecture, where each block is cryptographically linked to the previous one, ensuring tamper resistance and data integrity. The proposed protocol utilizes the SHA256 hash function to ensure the integrity of flight data by generating a unique and irreversible digest for each message, preventing any tampering. Additionally, the protocol uses bitwise XOR operations with a unique session key to encrypt flight data, protecting against security attacks while maintaining low computational overhead due to its lightweight nature.

Table 1.
Notation Used in The Proposed Protocol.
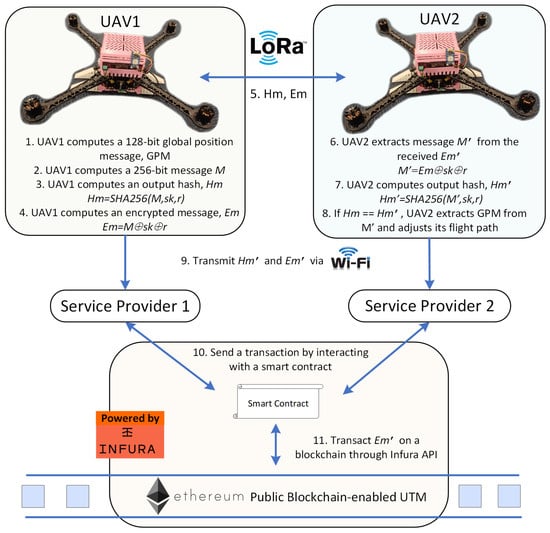
Figure 1.
LoRa D2D Communication Protocol Using Public Blockchain-based UTM.
3.1. Initial Phase
The initial phase consists of steps to be performed before the authentication phase, including session key generation. These steps are as follows:
- 1.
- Each service provider registers with a public blockchain-based UTM to obtain a pair of public and private keys, which can be used to make flight operation transactions on the Ethereum blockchain.
- 2.
- The UTM generates two random numbers, namely and , which will be returned to service providers.
- 3.
- The service providers generate two session keys, each being valid for a 24 h period in sequence to support flight operations that span more than one day (e.g., is valid from 00:01 to 24:00 on the first day and is valid from 00:01 to 24:00 on the second day). This session key, , or both session keys ( and ) as well as the random number, , will be stored on the UAVs depending on their registered flight time.where is the Unix timestamp of the start of the first day and is the Unix timestamp of the start of the second day, as illustrated in Table 2.
 Table 2. Example of Unix Timestamp Used in Session Key Generation.
Table 2. Example of Unix Timestamp Used in Session Key Generation. - 4.
- The UAV operators register their UAVs with a service provider and obtain unique UAV IDs.
- 5.
- The UAV operators submit UAVs flight plans to service providers.
- 6.
- The service providers provide flight activities of UAVs to UTM, including the intended flight destination, flight path, and speed, by making transactions on the Ethereum public blockchain.
3.2. Authentication Phase
The authentication phase is initiated only when a received LoRa signal exceeds a predefined Received Signal Strength Indicator (RSSI) threshold (i.e., >−91 dBm). This threshold corresponds approximately to a distance of 1 km under line-of-sight conditions, indicating that the transmitting UAV is within proximity [28]. This mechanism significantly reduces the overall number of transmissions by ensuring UAVs only attempt authentication when they are in close proximity. Additionally, the transmission payload is limited to just 512 bits, which significantly reduces the ToA. For instance, using a 125 kHz bandwidth and a coding rate of 4/5, the ToA for a 512-bit payload is approximately 131 ms [29], well below the 400 ms of regional dwell-time restrictions defined in the AS923 band [30]. While LoRaWAN-specific limitations do not bind the proposed solution, it remains compliant with the underlying regional regulatory limits for the ISM band, including 1% duty cycle constraints [31], which permit up to 36 s of transmission time per hour. This equates to approximately 227 packets of 512 bits per hour. By reducing transmission frequency through proximity-based triggering and minimizing airtime with short payloads, the proposed solution ensures compliance with temporal occupancy regulations in the ISM band. Although the authentication phase is described using a two-UAV scenario, as shown in Figure 1, the proposed protocol is inherently scalable to multi-UAV environments. The proximity-based mechanism helps manage communication efficiently and reduce channel contention in densely populated networks. The following describes the steps needed for two UAVs, namely UAV1 and UAV2, to conduct the authentication phase during D2D communication, which are as follows:
- 1.
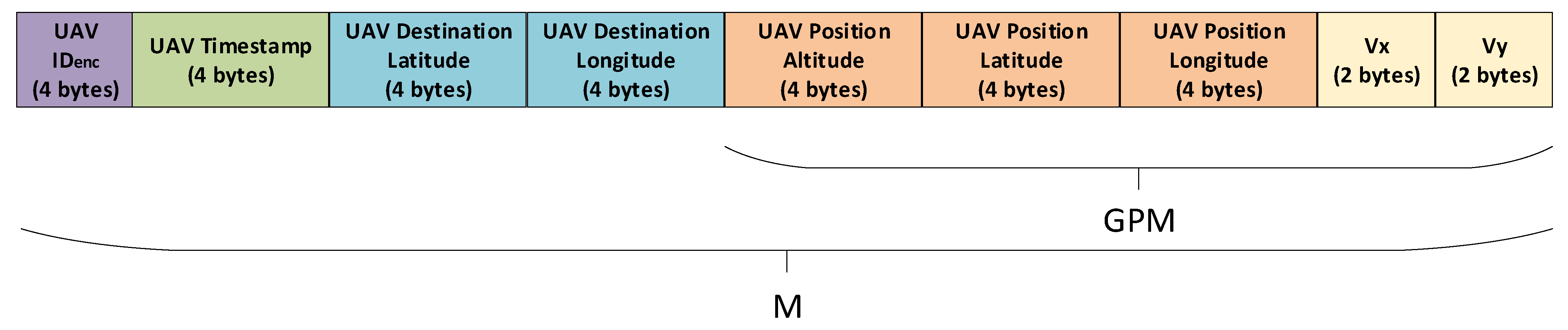
- UAV1 determines its global position via installed sensors, as shown in Table 3. It measures its velocity (i.e., vx and vy) by using an Inertial Measurement Unit (IMU). Velocity of vz is not included in the computed message , since it is needed for take-off and landing and is not as vital as vx and vy, which are critical for navigation and maintaining UAV flights. It also obtains its longitude, latitude, and altitude using the Global Positioning System (GPS). These data will be concatenated to a 128-bit global position message, , as described in Table 3.
 Table 3. Global Position Message Detail.
Table 3. Global Position Message Detail. - 2.
- UAV1 then encrypts the 32-bit UAV by XOR-ing it with the 32-bit Unix timestamp, where . It then concatenates the 32-bit UAV , current 32-bit Unix timestamp, , a 64-bit UAV flight destination, and the 128-bit global position message, to construct a 256-bit concatenated message, , as presented in Figure 2.
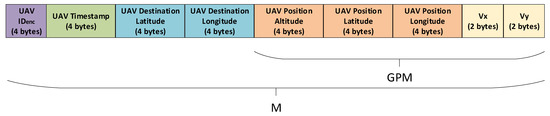 Figure 2. Structure of message M.
Figure 2. Structure of message M. - 3.
- UAV1 then computes an output hash, by hashing M with the session key, , where . This output hash is used for data integrity protection purposes.
- 4.
- UAV1 computes an encrypted message, by bitwise XOR-ing with and , where .
- 5.
- UAV1 broadcasts the output hash, and the encrypted message, to nearby UAVs through LoRa peer-to-peer communication to update its global position.
- 6.
- UAV2 receives the and values from UAV1. The UAV2 then extracts the concatenated message, from the by XOR-ing with its stored and , where .
- 7.
- UAV2 proceeds to compute an output hash, by performing hashing of and using the SHA256 hash function, where .
- 8.
- UAV2 authenticates the messages sent from UAV1 if the computed output hash, , is equal to the received output hash, . UAV2 then extracts the global position data from the concatenated message, , and adjusts its flight path if there is a potential collision with the nearby UAV1. Otherwise, the UAV2 terminates the session and deletes the received message, .
- 9.
- UAVs transmit the output hash, and the encrypted to service providers when they are covered by Wi-Fi. The authentication of the UAVs will be verified, and the message, , will be decrypted by the service providers using their stored and .
- 10.
- The service providers update the global position of UAVs by making transactions of encrypted on the Ethereum public blockchain. The UAVs flight activities can only be decrypted and viewed by authorized service providers.
The same steps apply to the communication initiated by UAV2 with UAV1 and other nearby UAVs.
4. Proof of Concept
4.1. Development of UAVs with an Onboard LoRa Communication Module
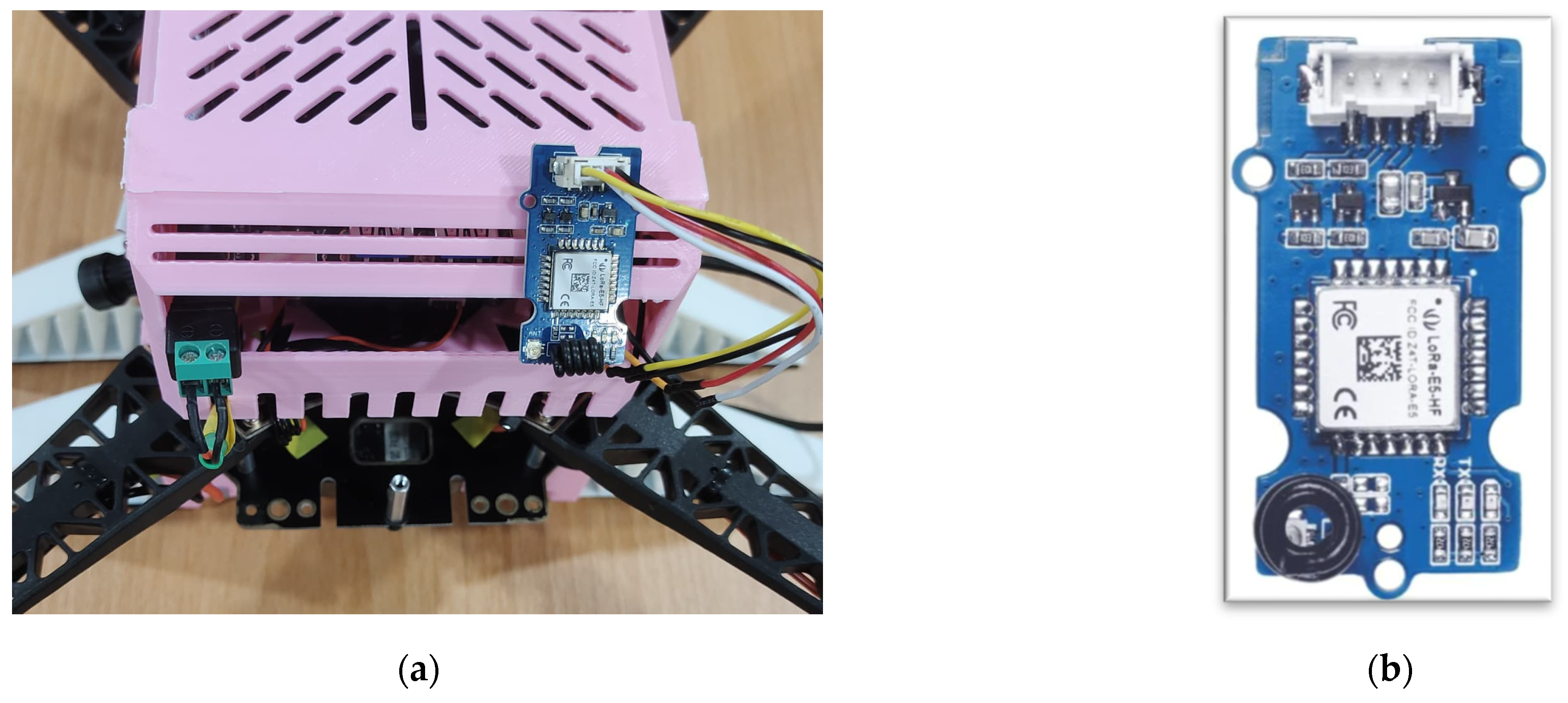
An in-house UAV equipped with a Grove LoRa-E5 module (Seeed Studio, Shenzhen, China) was used for the proof of concept, as shown in Figure 3. The module supports LoRa communication and has an integrated ARM Cortex-M4 (ARM Holdings, Cambridge, UK) ultra-low-power Microcontroller Unit (MCU), specifically the STM32WLE5JC (STMicroelectronics, Geneva, Switzerland). The integrated LoRa SX126x transceiver (Semtech, Camarillo, CA, USA) is configured to operate at 923 MHz. The UAV is built using the S500 Quadrotor kit (Holybro, Shenzhen, China) and features an onboard Jetson Orin Nano computer (Seeed Studio, Shenzhen, China) for real-time processing of deep learning and computer-vision tasks. It also features a Pixhawk 6C Mini flight controller (Holybro, Shenzhen, China) with a custom firmware based on the PX4 v1.15 version.
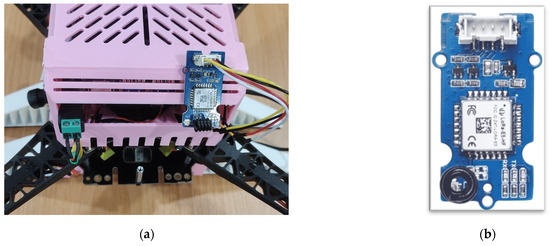
Figure 3.
(a) A LoRa node attached to an S500 UAV; (b) Grove LoRa E5 node.
4.2. Development of a Decentralized UAV Traffic Management Web Application Platform
A decentralized UAV traffic management web application platform was created to enable each service provider to view UAVs flight activities through a public blockchain. The Ethereum Sepolia testnet was used for this purpose. A public blockchain is transparent, which enables all users, including attackers, to view the transactions, including their inputs. Hence, it is necessary to encrypt the transaction inputs to allow authorized service providers to view the UAV flight activities.
In order to achieve this, a smart contract was designed to store encrypted flight information on the blockchain using an updateFlight() function, as described in Algorithm 1. This function is restricted to the contract owner through the use of the onlyOwner. This access control mechanism prevents unauthorized users from modifying the state of the contract, thereby preventing attackers from exploiting the function through front-running attacks.
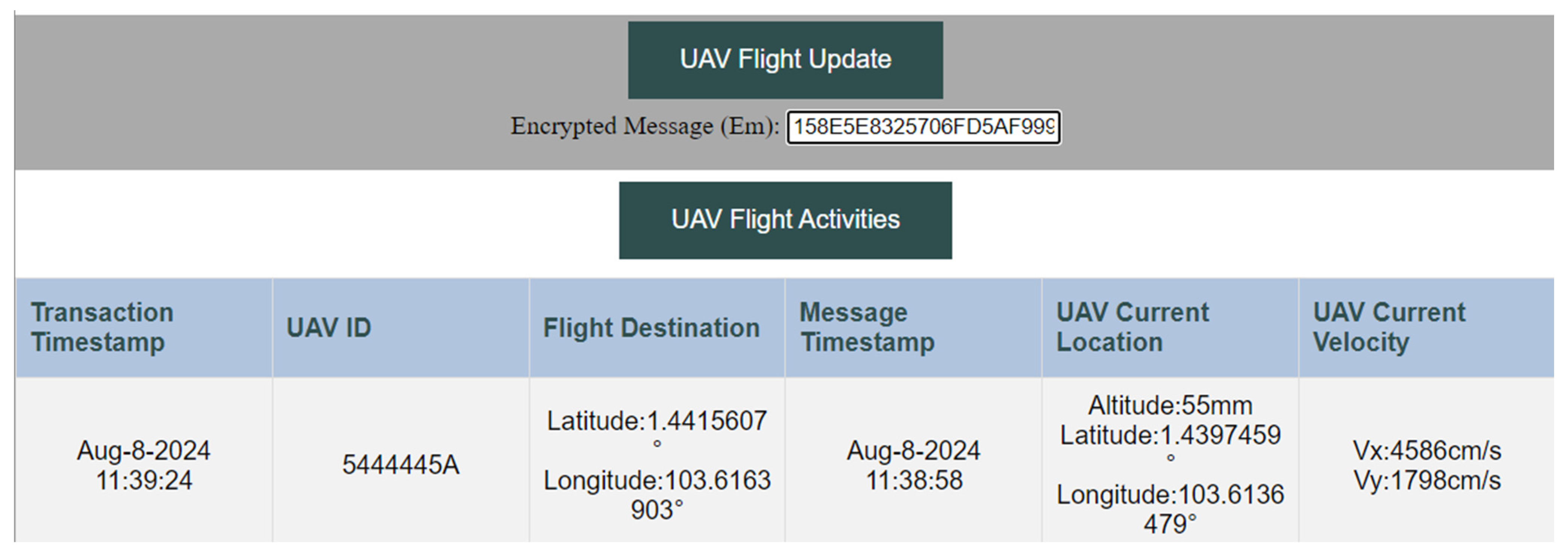
The decentralized web page was designed using HyperText Markup Language (HTML), and JavaScript was used to enable interactive content on the webpage. To interact with the Ethereum Sepolia testnet and smart contracts, the Web3.js library is used. In addition, Infura was used to interact with the testnet by accessing Ethereum remote nodes. This platform enables authorized service providers with correct and values to decrypt the transaction inputs and view the flight details, as shown in Figure 4. The UAV is obtained by XOR-ing the extracted from the message M with the extracted timestamp, . Attackers will only be able to obtain encrypted input from transactions and will be unable to decrypt to obtain the correct flight details.
| Algorithm 1: Pseudo-code of updateFlight() |
| Input: valueEm: bytes32 |
| 1. if (msg.sender == owner) 2. if (balance > transaction fee) 3. assign valueEm to storedEm 4. else 5. revert the transaction 6. end 7. else 8. revert the transaction 9. end |
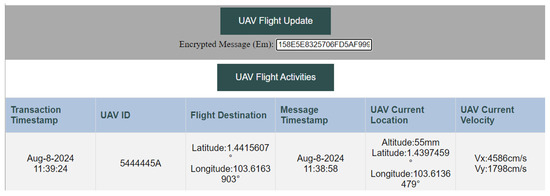
Figure 4.
Decentralized Web Application for a Public Blockchain-based UTM.
5. General Security Analysis
5.1. Secret Key Disclosure Attack
Attackers may attempt to eavesdrop on the communication and obtain transmitted messages. However, no plaintext is transmitted, only an output hash, , and an encrypted message, are broadcasted. In addition, the secret key, , is computed by hashing random numbers and , as well as a timestamp. Crucially, the random number is never disclosed to the UAVs operators or transmitted over the network. Since the SHA256 hash function is resistant to preimage attacks [32], the attackers are unable to reverse engineer the session key, even with knowledge of the timestamp, because the secret random number is used. Thus, the attackers are unable to extract the secret session key, or the underlying random numbers, and from intercepted messages.
In addition, although the blockchain stores the encrypted message, , decryption is only possible with the correct and session key . The session key, is generated using the SHA256 function, based on a secret random number , which remains undisclosed. Since the blockchain is publicly visible, attackers may attempt to scan historical data for potential decryption attempts in the long term. Nonetheless, due to the strong preimage resistance of SHA256, successful preimage attacks are not expected to be feasible for at least the next decade [33]. This preserves forward secrecy and prevents disclosure of the secret key.
5.2. Replay Attack
If attackers replay previously transmitted messages to nearby UAVs, this attack will be unsuccessful due to the inclusion of the current timestamp in the transmitted messages. UAVs receiving the transmitted message will verify the extracted timestamp with the current one. The LoRa transmission time in the worst-case scenario, with a bandwidth of 125 kHz and a Spreading Factor (SF) of 12, is 4.245 s [34]. Thus, if the timestamp difference exceeds 10 s, the authentication of legitimate D2D communication will fail, and the nearby UAVs will not further process the message. However, dynamic conditions, such as congestion and varying UAV density, may introduce transmission latency, potentially leading to false detection of replay attacks. This will be addressed in future work by implementing an adaptive time window adjustment to calibrate the allowable timestamp difference dynamically. The Receive Signal Strength Indicator (RSSI) will be used as a real-time metric for assessing network congestion.
Furthermore, this design mitigates length extension attacks, which typically allow an attacker to create a valid hash by appending data to a partially known input. This protocol generates a unique session key for each communication session using a hash of a random number , a secret random number , and the current timestamp. As explained in Section 5.1, attackers are unable to extract the session key from transmitted messages because the secret value is never transmitted or disclosed. The attackers are unable to decrypt the message and reconstruct the original plaintext without access to the session key, making it impossible to append data for a length extension attack. Additionally, these attacks will not succeed, as the protocol is resistant to replay attacks through the use of unique session keys and timestamp validation.
5.3. Adversary-in-the-Middle Attack
Attackers might attempt to eavesdrop, block, and modify transmitted messages, including and . However, these attacks will be unsuccessful because attackers cannot generate the same message, using the modified , and . Therefore, if the computed hash, differs from the received hash value, , peer UAVs will reject the modified message. Furthermore, even if attackers intercept multiple encrypted messages and know the format of , they are unable to extract the session key, , or the random numbers, and . This is because the secret random number is used in the key generation and is never disclosed or transmitted. As a result, the protocol is resistant to known plaintext attacks and remains secure under adversarial conditions.
5.4. Tracking Attack
Attackers are unable to trace transmitted messages, and as these messages vary for each communication session. Message consists of the concatenation of the encrypted UAV , timestamp, and UAV information, which vary for each session. In addition, message is encrypted with a session key, and a random number, . Thus, the attackers are unable to extract the UAV from the message, , and are unable to trace any specific UAV from the communicated messages.
6. Comparative Performance Analysis
As mentioned in Section 2, no research work was found on designing secure D2D LoRa communication for public blockchain-based UTM systems. Therefore, this section analyzes the performance of the proposed D2D LoRa communication protocol in terms of security, computation, storage, and payload size. Ethereum blockchain and SHA256 hash function security analyses are not included in this paper as they have already been proven secure [35,36].
6.1. UTM Access Management with D2D Communication Integration
Blockchain technology has been proposed for integration with UTM to enable a secure and efficient traffic monitoring system through controlled access to flight data [7,9]. Alkadi and Shoufan implemented access control modifiers for each function in smart contracts to manage the privileges and authorities of users on a permissioned public blockchain [9]. Different Ethereum addresses are used to represent various roles, such as UAV operator, public reporter, authority smart contract, and UAV service provider. However, this approach increases the complexity of the UTM system, as keeping track of the addresses and role assignments is challenging and creates scalability issues.
Allouch et al. proposed to use the Hyperledger Fabric, a private blockchain, for identity management and access control [7]. This approach allows nodes to control and limit access to their distributed sensitive information. UAVs must constantly update their ground control stations with flight information. The data are then sent to the cloud server, encrypted, and stored in an off-chain database (i.e., OrbitDB with IPFS). The data are subsequently hashed and stored as an immutable transaction on the blockchain. However, a private blockchain is not fully decentralized and, hence, susceptible to security attacks.
To ensure transparency and enhanced security, this paper proposes developing a UTM system using a public Ethereum blockchain, allowing users to view transactions while only authorized service providers with legitimate secret keys can view flight data. Communication latency is the main issue in [7,9] because it does not support real-time D2D communications, which is critical for adapting UAVs flight paths to avoid obstacles. The proposed solution addresses this by supporting direct D2D communication, enabling more efficient collision avoidance for UAVs. The message transmitted during D2D communication will be updated on the Ethereum blockchain in the proposed UTM system for better flight monitoring.
6.2. Computation Cost
The proposed protocol utilizes one SHA256 function to generate a 256-bit . It further uses one bitwise XOR operation to encrypt the UAVs’ , followed by two additional bitwise XOR operations to compute a 256-bit encrypted message, . The sensitive flight information in message M is encrypted to prevent security attacks. The computational cost has been analyzed and compared with related works where various IoT devices, ranging from resource-constrained IoT devices like the Arduino Uno to more powerful devices, such as the Galaxy S5 smartphone (Samsung, Suwon, Republic of Korea), have been used. The companion board used for the proof of concept is the Jetson Orin Nano, a device with 8 GB of RAM and a 1.5 GHz CPU clock speed. The average computation time for a SHA256 function and three XOR operations using the aforementioned hardware is approximately 0.01 ms.
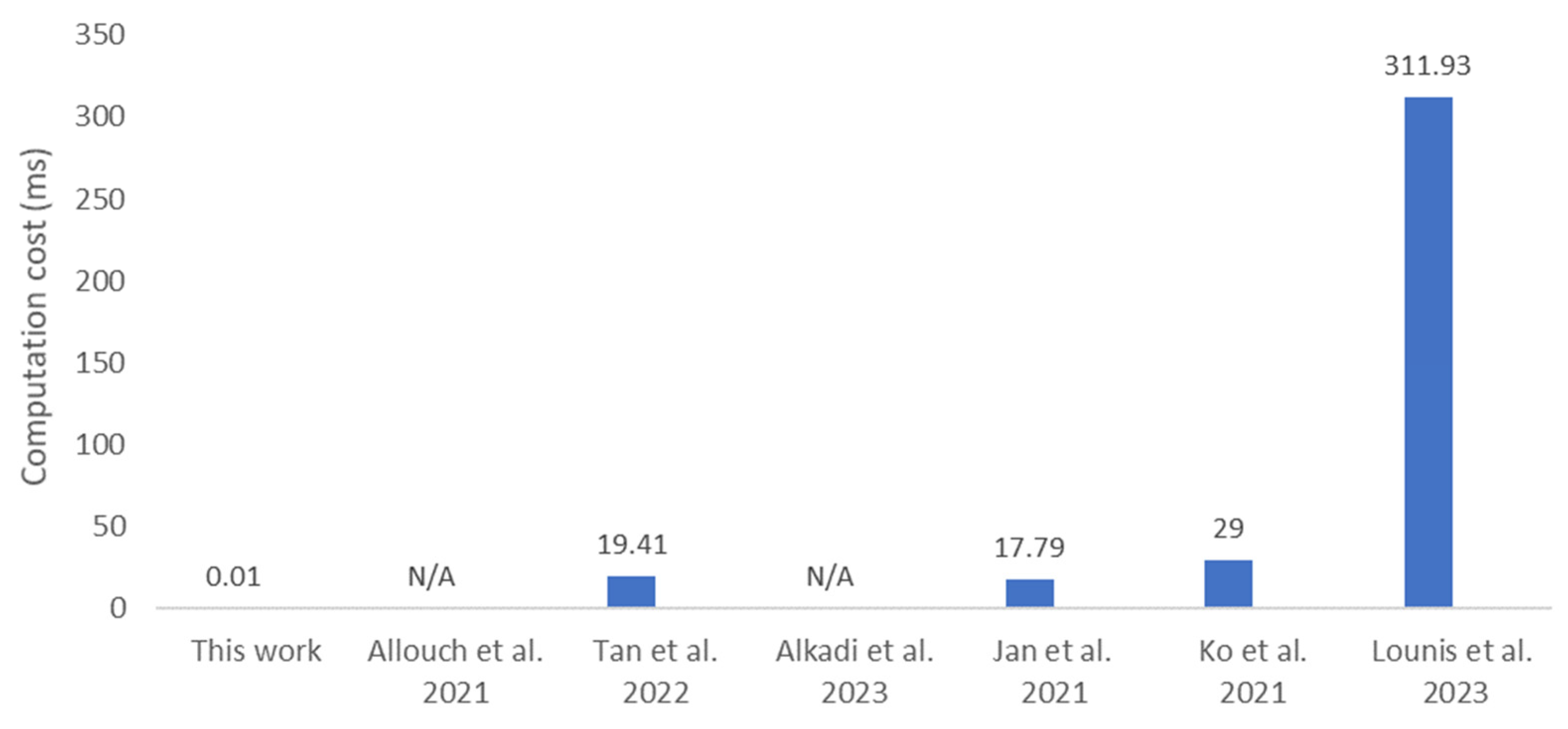
In addition to the computation cost, for a fair comparison with the related studies, the cryptography used in the protocols is analyzed. Figure 5 illustrates that the proposed protocol has the lowest computation cost compared to related works, due to its lightweight design, which requires only 1 SHA256 and 3 XOR operations. In contrast, the protocol in [25] takes 29.00 ms, as it involves performing both the Elliptic Curve Digital Signature Algorithm (ECDSA) and Hash-based Message Authentication Code (HMAC). The solution in [26] involves 16 hash function operations and 10 bitwise XOR operations, requiring a computation time of 311.93 ms. The protocol in [24] requires 17.79 ms for authentication, involves one multiplication, seven HMAC, and eight XOR operations, while [8] requires 19.41 ms to perform Elliptic Curve Cryptography (ECC). Some other related works transmit flight data as plaintext, eliminating the need for additional computation processes. According to Big-O notation, the computation cost in [9] addresses only the implementation of smart contracts, which is O(1) in complexity, as is the case in [7].
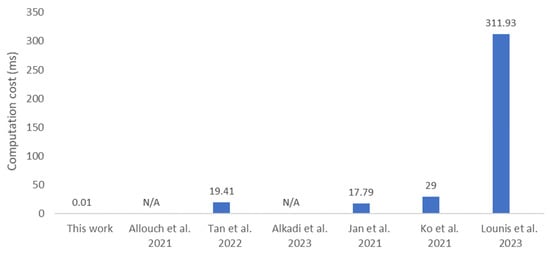
Figure 5.
Comparative computation cost [7,8,9,24,25,26].
6.3. Storage Cost
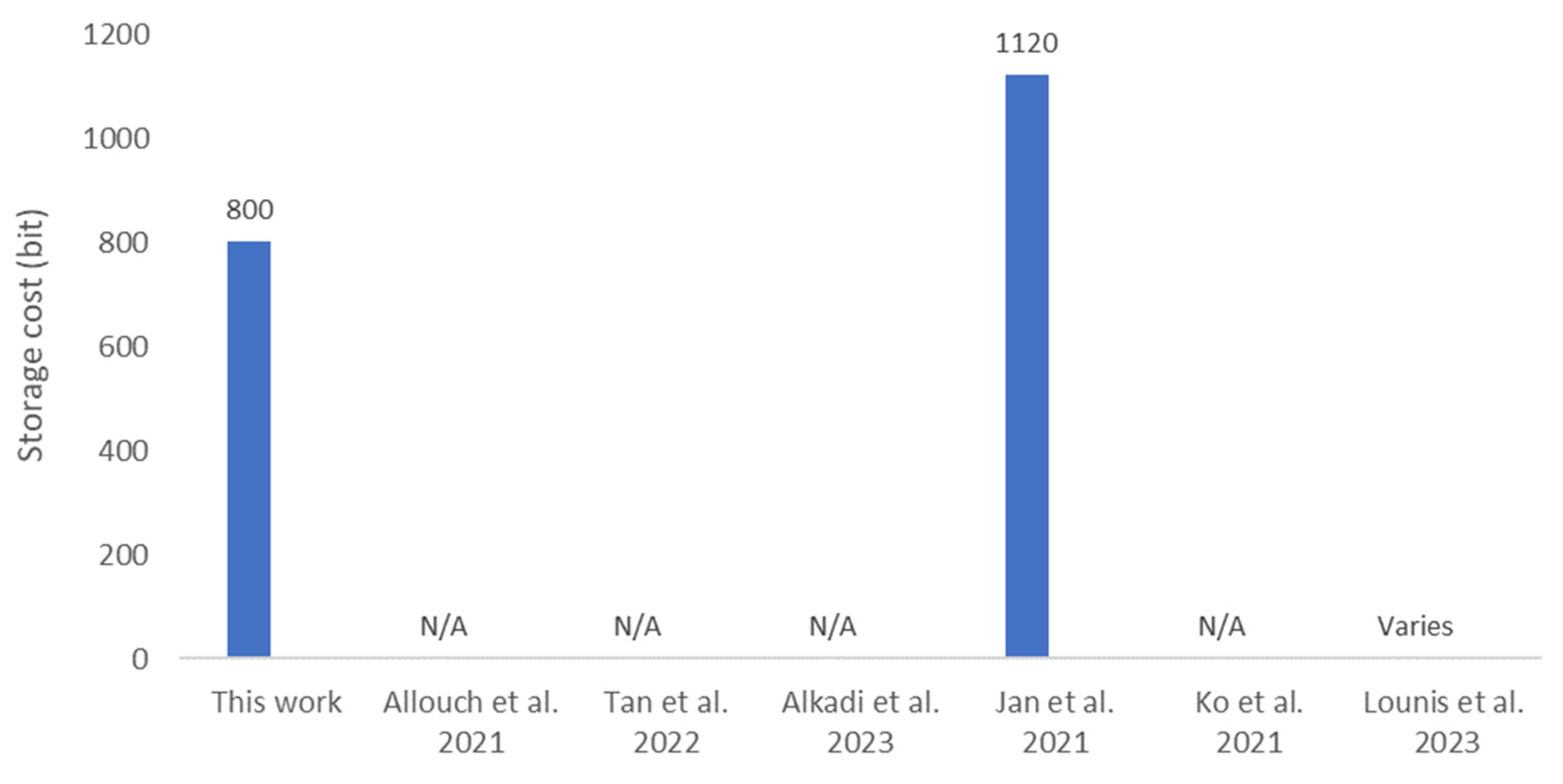
The storage cost analysis of the proposed protocol is focused solely on UAVs, as service providers and UTM systems can support more resource-intensive computations. UAVs are required to store either a 256-bit session key, , or both session keys ( and ), depending on their flight duration, as described in Section 3. Additionally, UAVs must also store a 256-bit random number, and a 32-bit . Thus, the total storage cost for UAVs ranges from 544 bits to 800 bits, based on the flight duration, which is manageable even for resource-constrained UAVs. Figure 6 shows that the storage cost for the proposed protocol is the lowest compared to related works, as [24] requires 1120 bits. Although [26] uses a Physical Unclonable Function (PUF) for credential generation, the protocol requires a storage cost that varies with the number of registered UAVs (n), specifically 2n + 3 for a 64-bit configuration. Thus, the storage cost becomes significantly high and unsupported by resource-constrained UAVs when the number of registered UAVs becomes large.
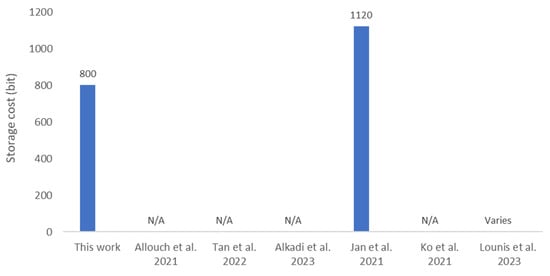
Figure 6.
Comparative storage cost [7,8,9,24,25,26]. N/A: Data Not Available at the source.
6.4. Formal Security Analysis
Formal security analysis is important in addition to the general security one, since it provides a rigorous method to prove the correctness of the proposed protocol. Although the protocol proposed in [8] has not undergone formal security analysis, other related works have been analyzed using formal methods, including modal-logic-based analysis [25] or verification tools [24,25,26].
The proposed protocol is modeled using the High-Level Protocol Specification Language (HLPSL) and analyzed with a widely used formal security verification tool, AVISPA. This security verification tool has four back-end verification engines. The On-the-Fly Model Checker (OFMC) back-end was selected for analyzing the proposed protocol because it effectively checks for security vulnerabilities that this paper aims to examine. The security flaws include adversary-in-the-middle attacks, replay attacks, tracking attacks through state space exploration, key disclosure attacks through symbolic analysis, and authentication flaws.
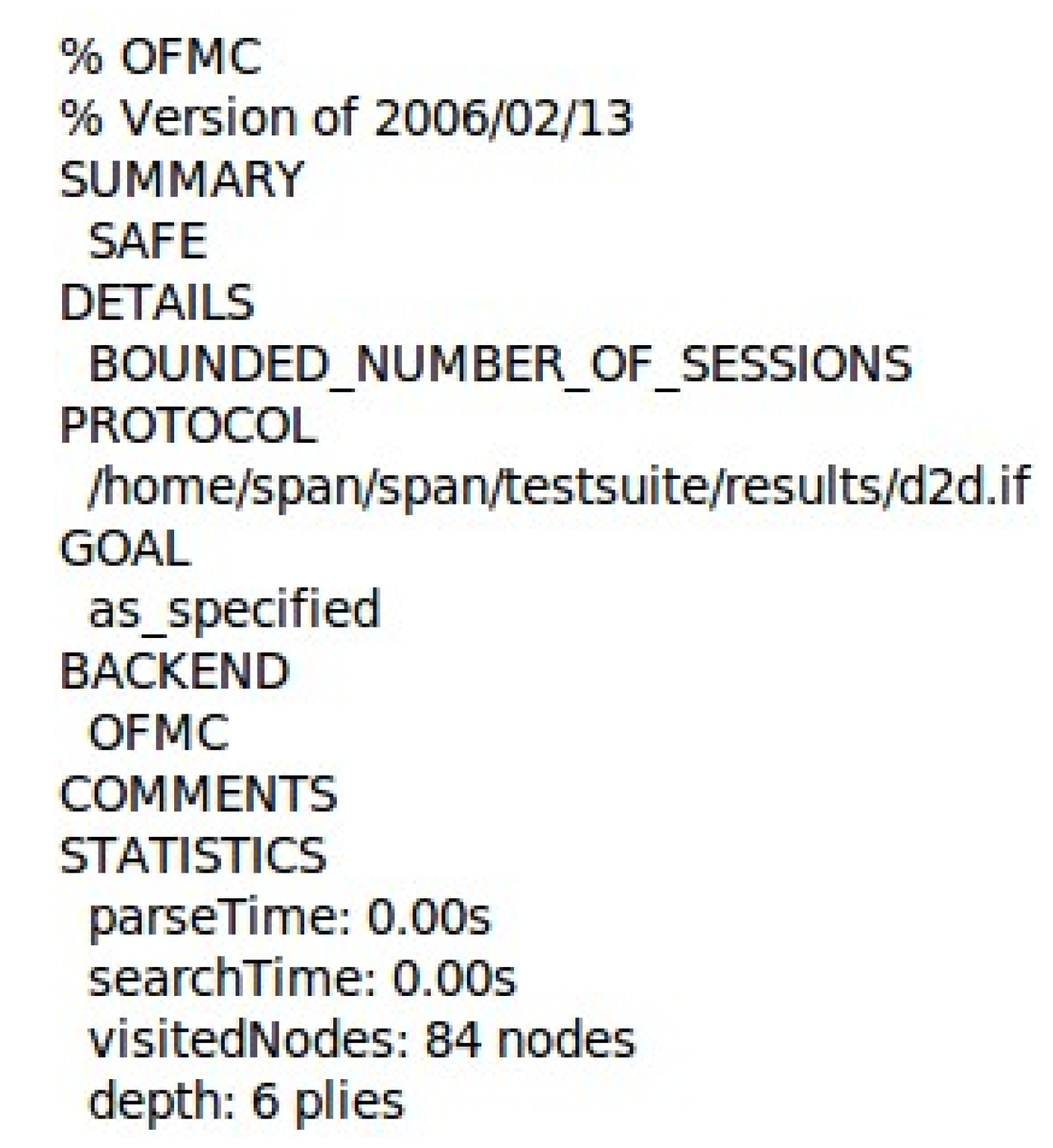
Figure 7 shows that the OFMC used an extremely small and unmeasurable amount of time (0.00 s) to read and process the input specification of the protocol. The search process of OFMC is efficient, as it took the same amount of time to explore the state space for vulnerabilities. The OFMC result shows that the proposed protocol is safe from the aforementioned attack, having been visited by 84 states and explored up to six levels of the protocol.
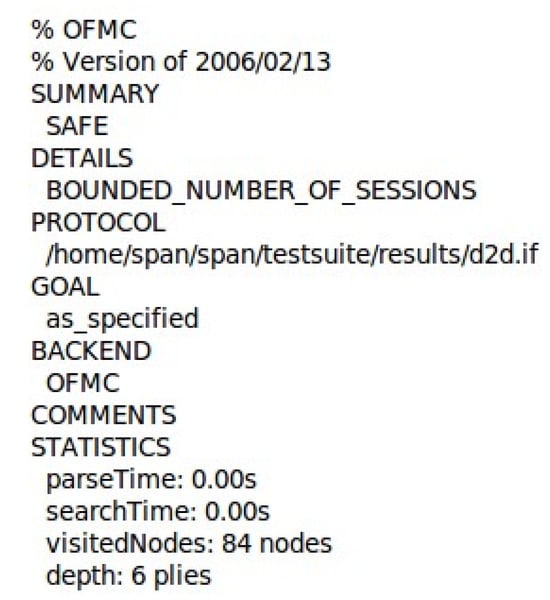
Figure 7.
OFMC Security Result.
6.5. LoRa Payload Size Analysis
Most related works do not include hardware implementations of communication technologies [7,8], and some barely mention that UAV relies on wireless technologies [24,25,26]. While [9] specifically mentions the use of Wi-Fi and Bluetooth, it lacks the analysis of communication performance. This paper proposes using LoRa technology in D2D communication to achieve wider signal coverage. Although LoRaWAN communication has payload size limits for both uplink and downlink transmission through the gateway based on data rate and SF [30], these constraints do not apply in LoRa. Furthermore, while high SF allows for greater sensitivity and longer transmission range, it requires longer transmission times, directly increasing the power consumption. Therefore, SF7 to SF9 have been identified as the most suitable options for achieving balanced communication in IoT networks, optimizing both transmission range and power consumption [37].
This paper utilizes LoRa peer-to-peer communication, making it essential to determine the payload size limitation for message transmission without relying on gateways. Table 4 presents experimental results for transmitting 512-bit messages, consisting of 256 bits of and 256 bits of , across a range of SFs from 7 to 12, independent of the LoRaWAN payload size limit discussed in [30]. In addition to bypassing payload size constraints, the proposed LoRa peer-to-peer solution does not enforce LoRaWAN-specific MAC layer constraints outlined in [30], such as the join duty cycle, Receive Window 1 Data Rate Offset (RX1DROffset), dwell time restriction, and band-specific limitations. This flexibility allows for the use of a wider range of SFs, enabling the selection that provides sufficient coverage for typical D2D communication distances. Under line-of-sight conditions, LoRa performance demonstrates that SF7 can support ranges of approximately 2 km, while SF12 can extend coverage up to 14 km in open environments [38]. However, these distances may vary depending on environmental factors, especially in scenarios involving densely populated UAV networks, which will be further analyzed in future work.

Table 4.
LoRa Payload Length Limit.
6.6. Smart Contract Vulnerability Analysis
Although smart contracts have been used in works [7,8,9], only [9] analyzes smart contract vulnerability using verification tools, including SmartCheck, Oyente, Osiris, and Slither. Thus, smart contracts deployed in [7,8] may be susceptible to vulnerabilities due to the lack of thorough analysis and verification.
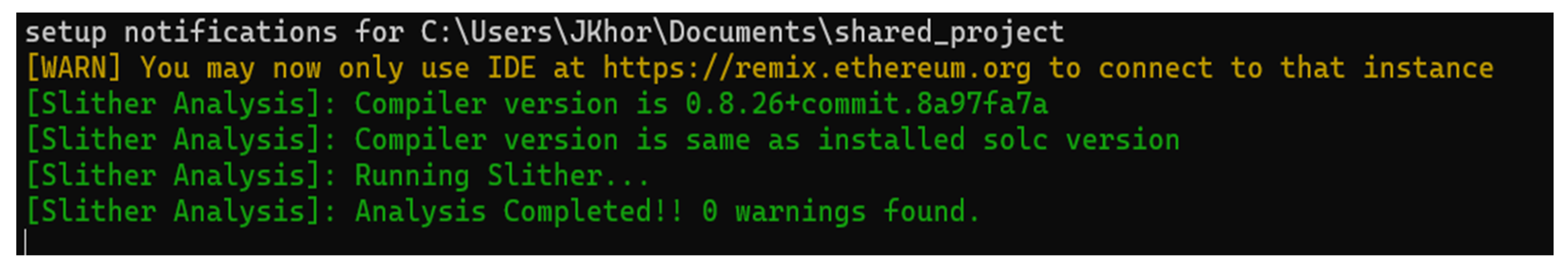
A well-accepted static code verification tool, Slither, has been used to analyze the d2d.sol for potential vulnerabilities, including shadowing, uninitialized variables, and reentrancy. Slither generates an Abstract Syntax Tree (AST) from the d2d.sol and then transforms it into an internal representation language, SlithIR, to compute various code analyses [39]. Figure 8 shows the Slither analysis result with no errors or warnings found in the d2d.sol.
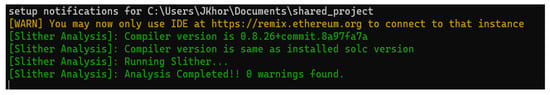
Figure 8.
Slither Analysis Result.
Table 5 provides a comparative performance summary of the proposed solution against related works. The results demonstrate that none of the existing studies have integrated D2D communication with a UTM system, a feature that is uniquely addressed by this solution. In addition, the proposed D2D protocol exhibits the lowest computation and storage costs, supported by a comprehensive general and formal security analysis, as well as a detailed performance evaluation of the overall system.

Table 5.
Comparative Performance Analysis.
7. Limitations and Future Work
A key limitation of the current system is the use of a static RSSI threshold to estimate UAV proximity. In practice, environmental factors such as interference, multipath fading, and antenna orientation may cause RSSI values to fluctuate, leading to false proximity detection or missed communication opportunities. Moreover, dynamic network conditions, such as UAV density and channel congestion, can introduce transmission latency, potentially leading to the false detection of replay attacks.
To address these limitations, future work will focus on enhancing the proximity detection mechanism by incorporating adaptive RSSI thresholds, Signal-to-Noise Ratio (SNR) values, and GPS-based distance estimation. An adaptive window calibration mechanism will also be introduced to account for latency variations. Furthermore, RSSI will be utilized as a real-time metric to assess network congestion and guide the dynamic adjustment of protocol parameters. A comprehensive scalability analysis will be conducted through simulations and testbed evaluations to quantify the protocol’s performance in terms of latency, collision rate, and throughput under different UAV densities.
8. Conclusions
This paper addresses a significant research gap in UTM studies by integrating secure direct D2D communication to avoid collisions efficiently. The proposed D2D protocol supports a wide range of UAVs, regardless of their flight duration or service provider. A public Ethereum blockchain is utilized to develop a secure UTM, ensuring that the sensitive flight data are accessible only to the authorized service providers with the appropriate secret keys. A proof of concept demonstrates the feasibility of this UTM system, and the proposed D2D protocol has been rigorously evaluated by means of a general security analysis, with its formal security properties being verified by the AVISPA tool. It has been proven to be secure against key disclosure, adversary-in-the-middle, replay, and tracking attacks. Performance evaluation shows the protocol achieves the lowest computation and storage costs, at 0.01 ms and 544–800 bits, respectively. The feasibility of using LoRa technology for D2D communication is also validated, with a successful message transmission across all SFs despite payload size limitations. Future work will focus on improving proximity detection and implementing an adaptive time window adjustment to dynamically calibrate allowable timestamp differences. The scalability of the proposed system will further be evaluated by analyzing UAV performance under varying density conditions.
Author Contributions
Conceptualization, J.H.K., M.S. and M.J.Y.C.; methodology, J.H.K. and M.J.Y.C.; software, M.J.Y.C.; validation, J.H.K., M.S. and M.J.Y.C.; formal analysis, J.H.K.; investigation, M.J.Y.C.; data curation, M.S.; writing—original draft preparation, J.H.K. and M.S.; writing—review and editing, M.S.; visualization, M.S.; supervision, J.H.K.; project administration, J.H.K.; funding acquisition, J.H.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Higher Education of Malaysia through the Fundamental Research Grant Scheme (FRGS), grant number FRGS/1/2023/ICT03/USMC/02/1.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Relevant data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Dizeu, F.B.D.; Picard, M.; Drouin, M.A.; Gagné, G. Extracting Unambiguous Drone Signature Using High-Speed Camera. IEEE Access 2022, 10, 45317–45336. [Google Scholar] [CrossRef]
- Seidaliyeva, U.; Ilipbayeva, L.; Utebayeva, D.; Smailov, N.; Matson, E.T.; Tashtay, Y.; Turumbetov, M.; Sabibolda, A. LiDAR Technology for UAV Detection: From Fundamentals and Operational Principles to Advanced Detection and Classification Techniques. Sensors 2025, 25, 2757. [Google Scholar] [CrossRef]
- Bertocco, M.; Brighente, A.; Ciattaglia, G.; Gambi, E.; Peruzzi, G.; Pozzebon, A.; Spinsante, S. Malicious Drone Identification by Vibration Signature Measurement: A Radar-Based Approach. IEEE Trans. Instrum. Meas. 2025, 74, 1–15. [Google Scholar] [CrossRef]
- Aouladhadj, D.; Kpre, E.; Deniau, V.; Kharchouf, A.; Gransart, C.; Gaquière, C. Drone Detection and Tracking Using RF Identification Signals. Sensors 2023, 23, 7650. [Google Scholar] [CrossRef] [PubMed]
- Tedeschi, P.; Nuaimi, F.A.A.; Awad, A.I.; Natalizio, E. Privacy-Aware Remote Identification for Unmanned Aerial Vehicles: Current Solutions, Potential Threats, and Future Directions. IEEE Trans. Ind. Inform. 2024, 20, 1069–1080. [Google Scholar] [CrossRef]
- Rahman, M.S.; Khalil, I.; Atiquzzaman, M. Blockchain-Powered Policy Enforcement for Ensuring Flight Compliance in Drone-Based Service Systems. IEEE Netw. 2021, 35, 116–123. [Google Scholar] [CrossRef]
- Allouch, A.; Cheikhrouhou, O.; Koubâa, A.; Toumi, K.; Khalgui, M.; Nguyen Gia, T. UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones. Sensors 2021, 21, 3049. [Google Scholar] [CrossRef]
- Tan, Y.; Liu, J.; Kato, N. Blockchain-Based Lightweight Authentication for Resilient UAV Communications: Architecture, Scheme, and Future Directions. IEEE Wirel. Commun. 2022, 29, 24–31. [Google Scholar] [CrossRef]
- Alkadi, R.; Shoufan, A. Unmanned Aerial Vehicles Traffic Management Solution Using Crowd-Sensing and Blockchain. IEEE Trans. Netw. Serv. Manag. 2023, 20, 201–215. [Google Scholar] [CrossRef]
- Zhang, L.; Lee, B.; Ye, Y.; Qiao, Y. Evaluation of Ethereum End-to-end Transaction Latency. In Proceedings of the 2021 11th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 19–21 April 2021; pp. 1–5. [Google Scholar]
- Rezaee, M.R.; Hamid, N.A.W.A.; Hussin, M.; Zukarnain, Z.A. Comprehensive Review of Drones Collision Avoidance Schemes: Challenges and Open Issues. IEEE Trans. Intell. Transp. Syst. 2024, 25, 6397–6426. [Google Scholar] [CrossRef]
- Noor, F.; Khan, M.A.; Al-Zahrani, A.; Ullah, I.; Al-Dhlan, K.A. A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics. Drones 2020, 4, 65. [Google Scholar] [CrossRef]
- Fakhreddine, A.; Raffelsberger, C.; Sende, M.; Bettstetter, C. Experiments on Drone-to-Drone Communication with Wi-Fi, LTE-A, and 5G. In Proceedings of the 2022 IEEE Globecom Workshops (GC Wkshps), Rio de Janeiro, Brazil, 4–8 December 2022; pp. 904–909. [Google Scholar]
- Khor, J.H.; Sidorov, M.; Law, S.Z.; Tan, S.Y.; Woon, P.Y. Public Blockchain-Based Data Integrity Protection for Federated Learning in UAV Networks Using MAVLink Protocol. In Proceedings of the International Conference on Green Energy, Computing and Intelligent Technology, Iskandar Puteri, Malaysia, 10–12 July 2023; pp. 321–333. [Google Scholar]
- Khan, N.-A.; Jhanjhi, N.-Z.; Brohi, S.-N.; Almazroi, A.-A.; Almazroi, A.-A. A Secure Communication Protocol for Unmanned Aerial Vehicles. CMC-Comput. Mater. Contin. 2022, 70, 601–618. [Google Scholar]
- Khor, J.H.; Sidorov, M.; Zulqarnain, S.A. Scalable Lightweight Protocol for Interoperable Public Blockchain-Based Supply Chain Ownership Management. Sensors 2023, 23, 3433. [Google Scholar] [CrossRef] [PubMed]
- Tsakmakis, A.; Valkanis, A.; Beletsioti, G.; Kantelis, K.; Nicopolitidis, P.; Papadimitriou, G. An Adaptive LoRaWAN MAC Protocol for Event Detection Applications. Sensors 2022, 22, 3538. [Google Scholar] [CrossRef]
- Pötsch, A.; Hammer, F. Towards End-to-End Latency of LoRaWAN: Experimental Analysis and IIoT Applicability. In Proceedings of the 2019 15th IEEE International Workshop on Factory Communication Systems (WFCS), Sundsvall, Sweden, 27–29 May 2019; pp. 1–4. [Google Scholar]
- Tamang, D.; Pozzebon, A.; Parri, L.; Fort, A.; Abrardo, A. Designing a Reliable and Low-Latency LoRaWAN Solution for Environmental Monitoring in Factories at Major Accident Risk. Sensors 2022, 22, 2372. [Google Scholar] [CrossRef]
- Ghazali, M.H.M.; Teoh, K.; Rahiman, W. A Systematic Review of Real-Time Deployments of UAV-Based LoRa Communication Network. IEEE Access 2021, 9, 124817–124830. [Google Scholar] [CrossRef]
- Allouch, A.; Cheikhrouhou, O.; Koubâa, A.; Khalgui, M.; Abbes, T. MAVSec: Securing the MAVLink Protocol for Ardupilot/PX4 Unmanned Aerial Systems. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference, Tangier, Morocco, 24–28 June 2019; pp. 621–628. [Google Scholar]
- Morel, A.E.; Ufuktepe, D.K.; Ignatowicz, R.; Riddle, A.; Qu, C.; Calyam, P.; Palaniappan, K. Enhancing Network-edge Connectivity and Computation Security in Drone Video Analytics. In Proceedings of the IEEE Applied Imagery Pattern Recognition Workshop, Washington, DC, USA, 13–15 October 2020; pp. 1–12. [Google Scholar]
- Zahra, S.W.; Arshad, A.; Nadeem, M.; Riaz, S.; Dutta, A.K.; Alzaid, Z.; Alabdan, R.; Almutairi, B.; Almotairi, S. Development of Security Rules and Mechanisms to Protect Data from Assaults. Appl. Sci. 2022, 12, 12578. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and Analysis of Lightweight Authentication Protocol for Securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef]
- Lounis, K.; Ding, S.H.H.; Zulkernine, M. D2D-MAP: A Drone to Drone Authentication Protocol Using Physical Unclonable Functions. IEEE Trans. Veh. Technol. 2023, 72, 5079–5093. [Google Scholar] [CrossRef]
- Top 10 Drones With The Longest Flight Time in 2023. Available online: https://www.jouav.com/blog/drone-with-longest-flight-time.html#:~:text=The%20average%20flight%20time%20of,even%20fly%20for%20several%20hours (accessed on 19 January 2023).
- Elhassan, S.A.M.; Kamal, N.L.M.; Norhashim, N.; Sahwee, Z.; Shah, S.A. Unmanned aerial vehicle localisation using RSSI-based trilateration. In Proceedings of the International Conference on Green Energy, Computing and Intelligent Technology 2024 (GEn-CITy 2024), Iskandar Puteri, Malaysia, 11–13 December 2024; pp. 235–240. [Google Scholar]
- LoRa Calculator. Available online: https://www.semtech.com/design-support/lora-calculator (accessed on 7 August 2025).
- Seeed Studio. LoRa-E5: LoRa Wireless Module-Powered by STM32WLE5 (AT Command Specification); Seeed Studio: Shenzhen, China, 2020. [Google Scholar]
- MTSFB and MCMC. Short Range Devices-Specifications; MTSFB: Kuala Lumpur, Malaysia; MCMC: Cyberjaya, Malaysia, 2025. [Google Scholar]
- Allende, M.; León, D.L.; Cerón, S.; Pareja, A.; Pacheco, E.; Leal, A.; Da Silva, M.; Pardo, A.; Jones, D.; Worrall, D.J.; et al. Quantum-resistance in blockchain networks. Sci. Rep. 2023, 13, 5664. [Google Scholar] [CrossRef] [PubMed]
- Khor, J.H.; Sidorov, M.; Ong, M.T.; Chua, S.Y. Public Blockchain-based Data Integrity Verification for Low-power IoT Devices. IEEE Internet Things J. 2023, 10, 13056–13064. [Google Scholar] [CrossRef]
- LoRa Networking Guide-Transmission Modes. Available online: https://development.libelium.com/lora_networking_guide/transmission-modes (accessed on 1 July 2024).
- Khor, J.H.; Sidorov, M.; Woon, P.Y. Public Blockchains for Resource-constrained IoT Devices-A State of the Art Survey. IEEE Internet Things J. 2021, 8, 11960–11982. [Google Scholar] [CrossRef]
- Sidorov, M.; Khor, J.H.; Wong, A.C.H.; Lee, Y.Y.; Li, J. A Lightweight Authentication Scheme for LoRaWAN Nodes Represented as On-Chain Non-Fungible Tokens. IEEE Sens. J. 2024, 24, 28222–28232. [Google Scholar] [CrossRef]
- Lima, W.G.; Lopes, A.V.R.; Cardoso, C.M.M.; Araújo, J.P.L.; Neto, M.C.A.; Tostes, M.E.L.; Nascimento, A.A.; Rodriguez, M.; Barros, F.J.B. LoRa Technology Propagation Models for IoT Network Planning in the Amazon Regions. Sensors 2024, 24, 1621. [Google Scholar] [CrossRef]
- Choi, R.; Lee, S.; Lee, S. Reliability Improvement of LoRa with ARQ and Relay Node. Symmetry 2020, 12, 552. [Google Scholar] [CrossRef]
- Feist, J.; Grieco, G.; Groce, A. Slither: A Static Analysis Framework for Smart Contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).