Hierarchical Clustering Analysis for Positioning Two Intrusion Events at Different Locations Using Dual Mach-Zehnder Interferometers
Abstract
1. Introduction
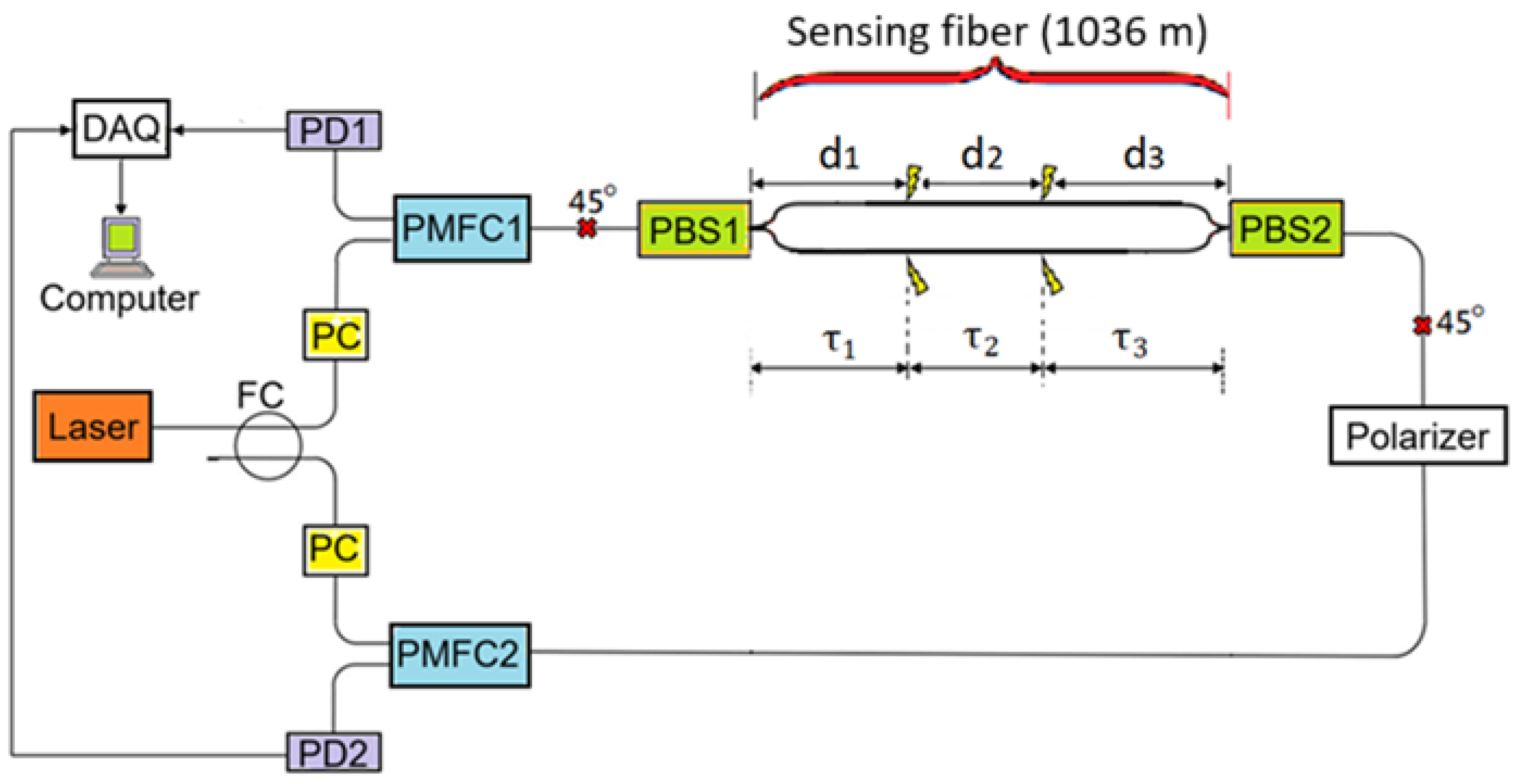
2. Outline of the Presented Measurement System
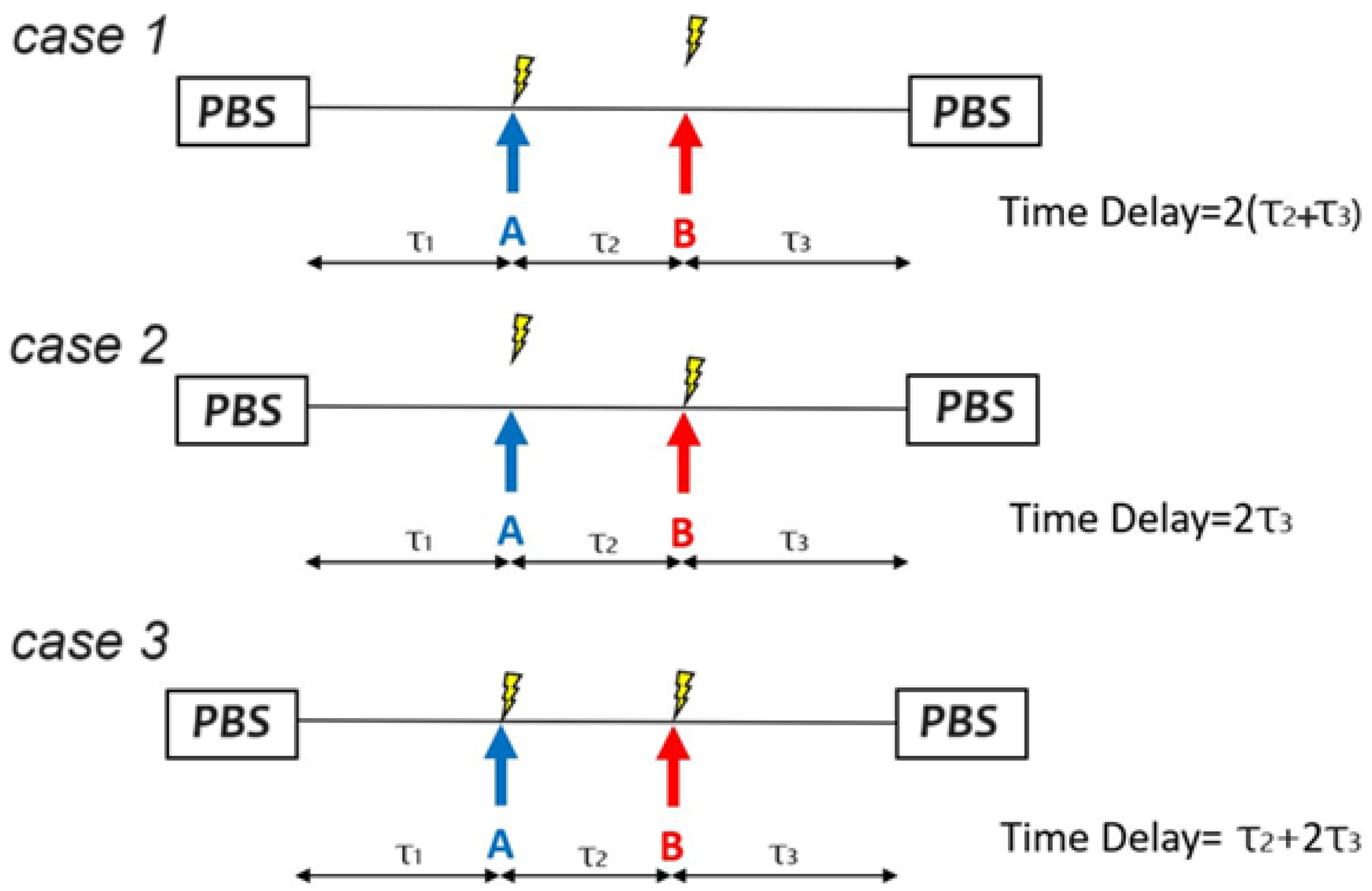
2.1. Detected Signals
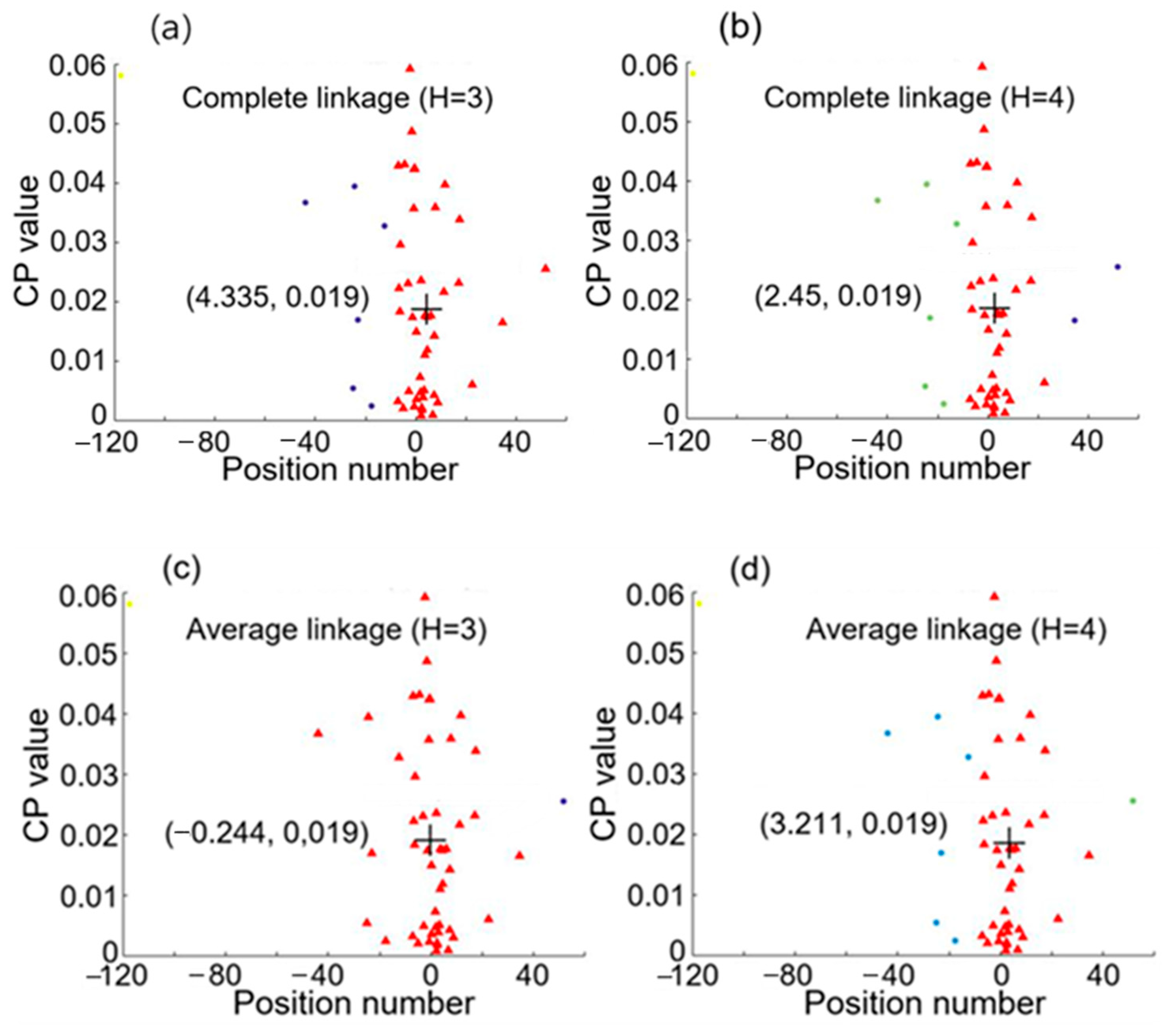
2.2. Hierarchical Clustering Analysis for Positioning
3. Experimental Results
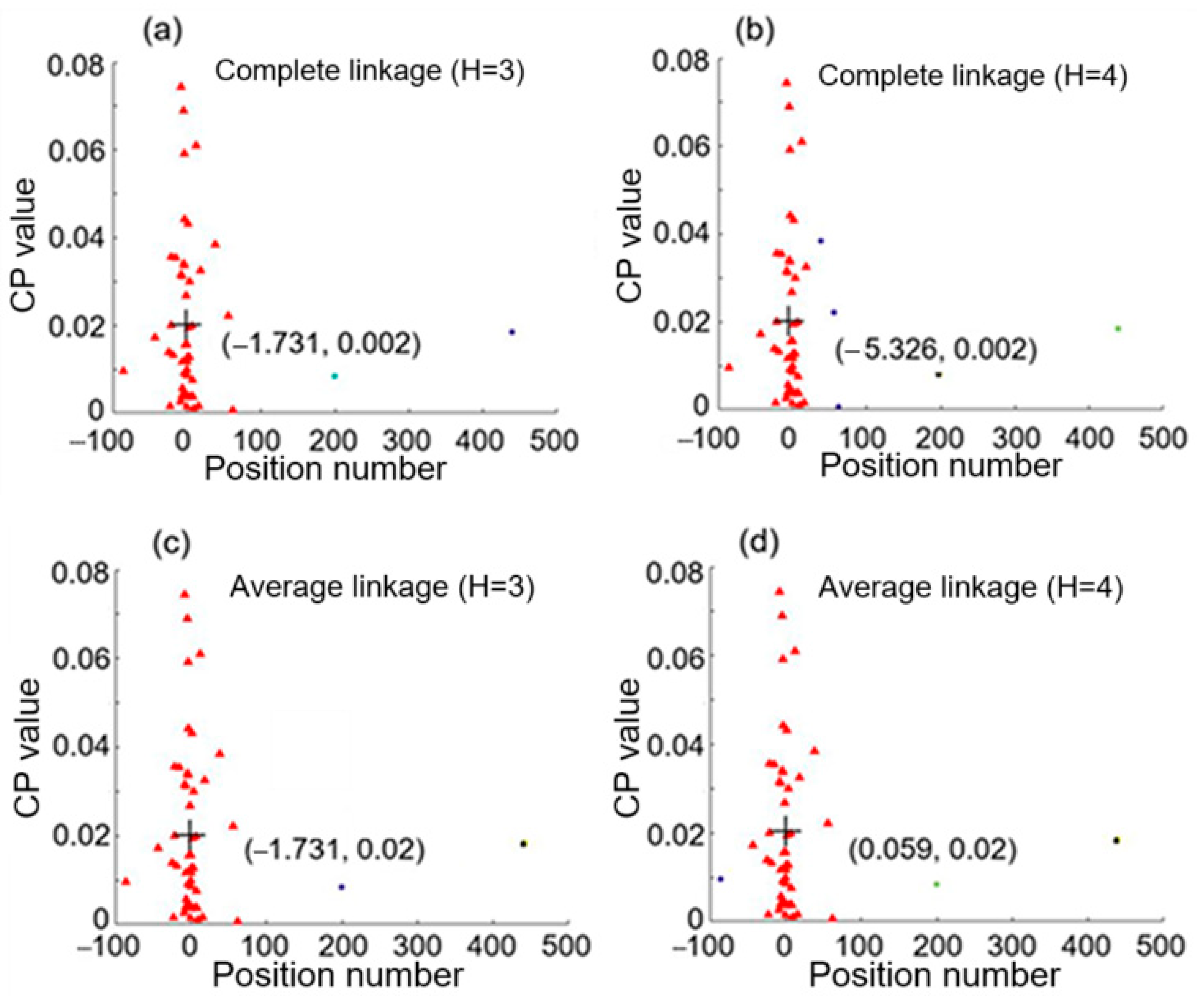
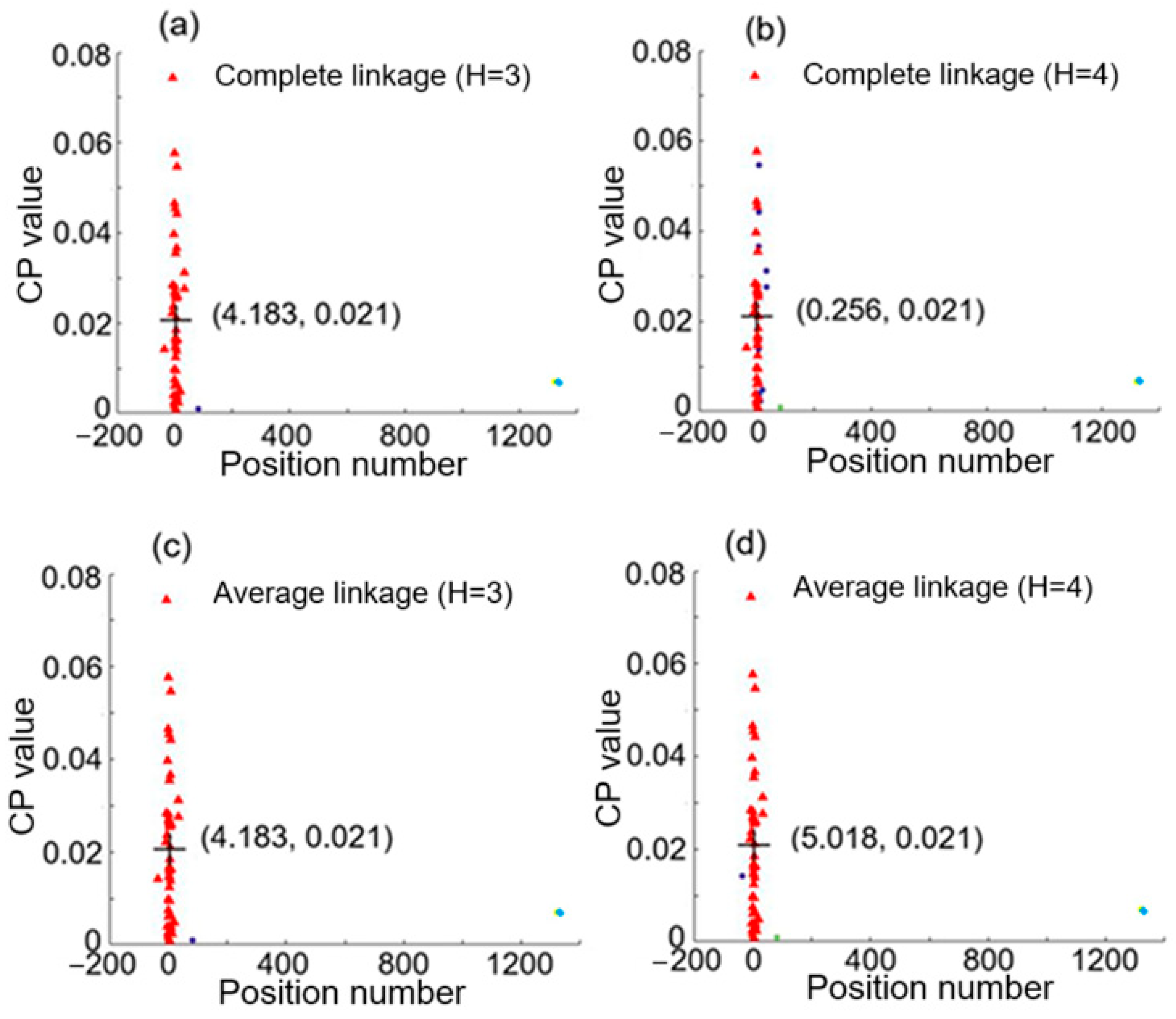
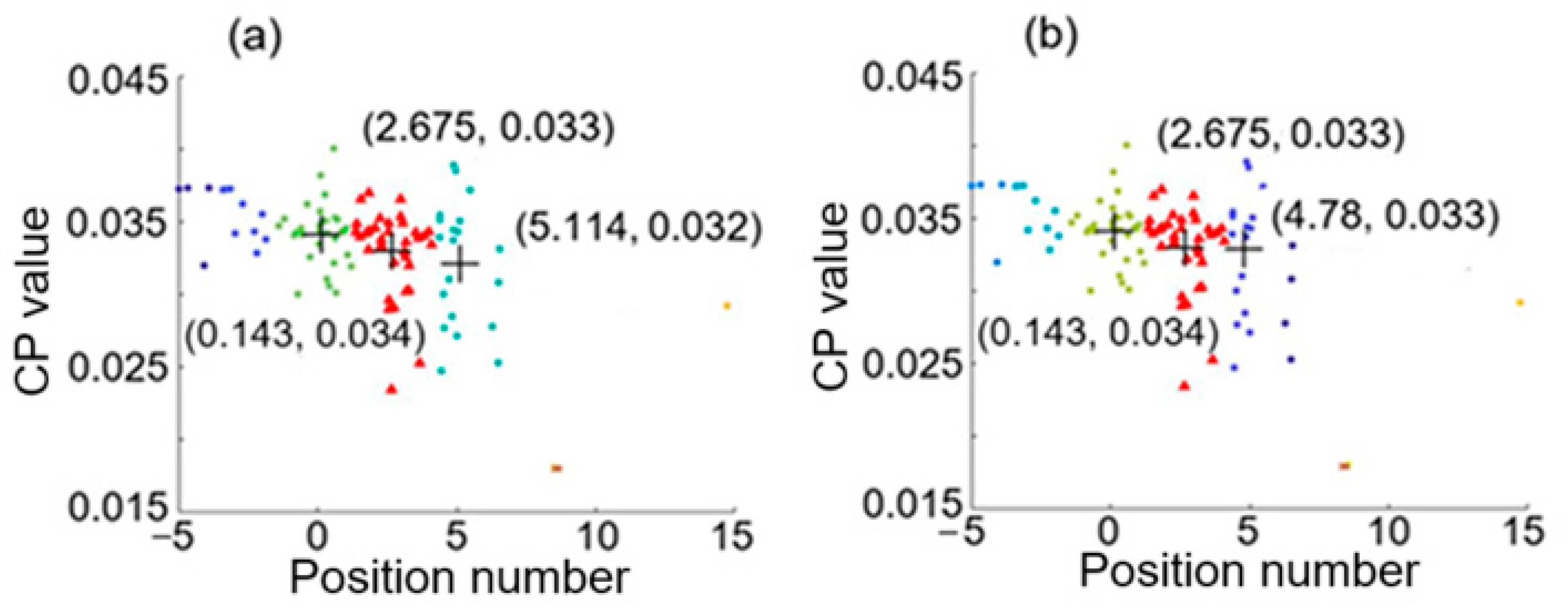
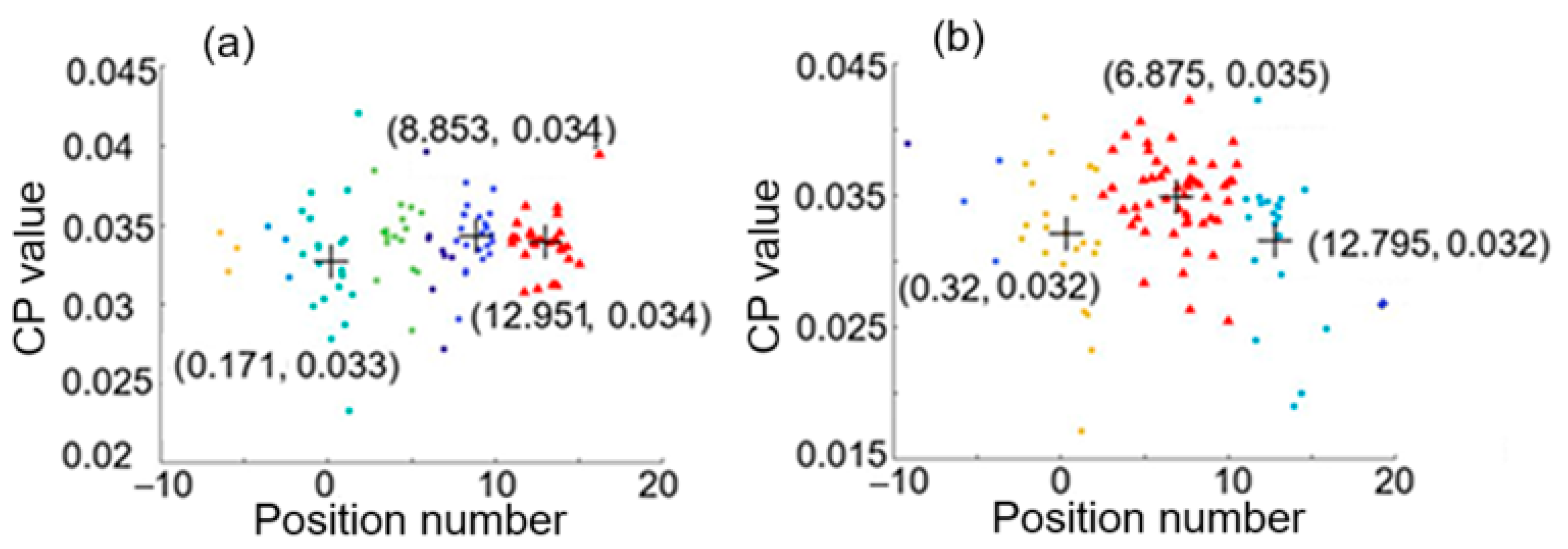
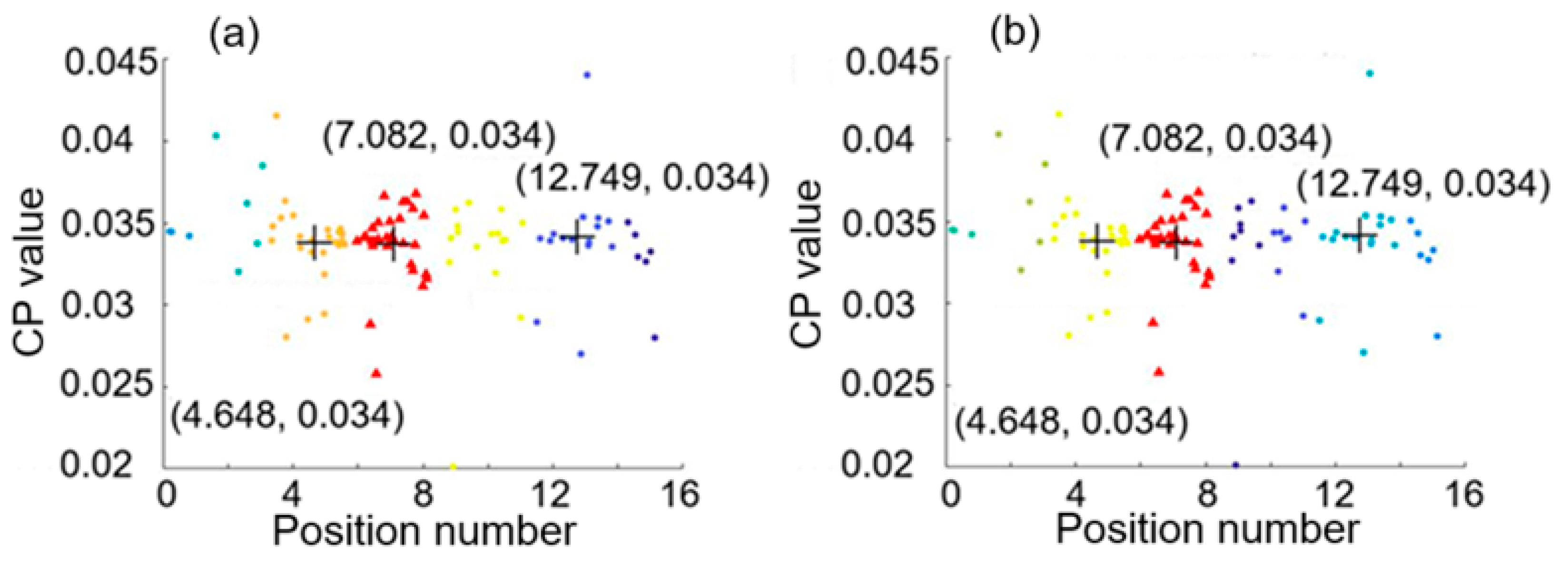
3.1. Hierarchical Clustering Results for Intrusions at 0.02 and 4.98
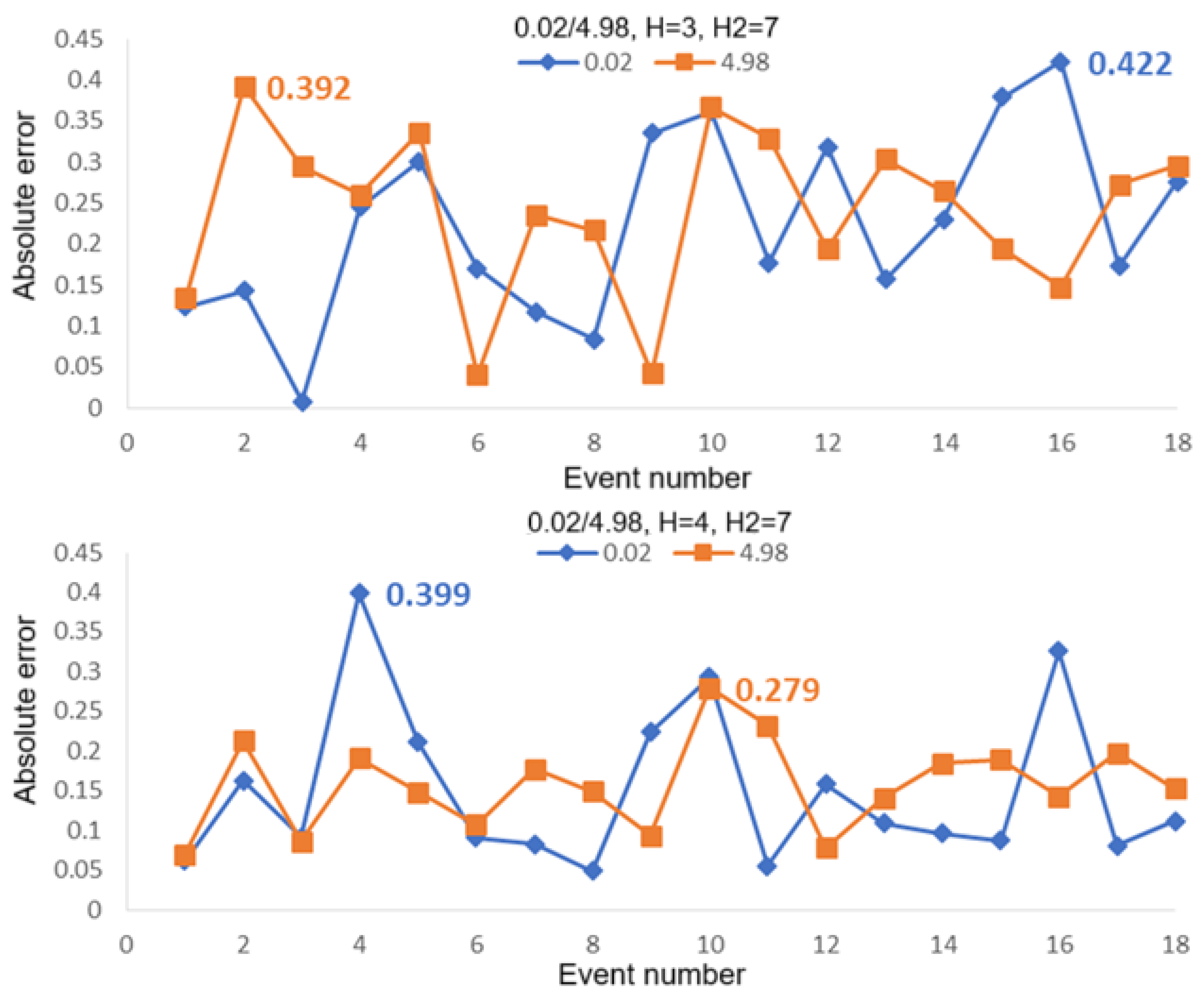
3.2. Absolute Error in Positioning of Two Intrusion Events
4. Conclusions and Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wu, H.; Rao, Y.; Tang, C.; Wu, Y.; Gong, Y. A novel FBG-based security fence enabling to detect extremely weak intrusion signals from nonequivalent sensor nodes. Sens. Actuators A Phys. 2011, 167, 548–555. [Google Scholar] [CrossRef]
- Chen, Y.; Zhou, L.-X.; Liu, H.-L. A fiber Bragg grating sensor perimeter intrusion localization method optimized by improved particle swarm optimization algorithm. IEEE Sens. J. 2018, 18, 1243–1249. [Google Scholar] [CrossRef]
- Juarez, J.C.; Maier, E.W.; Choi, K.N.; Taylor, H.F. Distributed fiber-optic intrusion sensor system. J. Light. Technol. 2005, 23, 2081–2087. [Google Scholar] [CrossRef]
- Masoudi, A.; Belal, M.; Newson, T.P. A distributed optical fibre dynamic strain sensor based on phase-OTDR. Meas. Sci. Technol. 2013, 24, 085204. [Google Scholar] [CrossRef]
- Peng, F.; Wu, H.; Jia, X.-H.; Rao, Y.-J.; Wang, Z.-N.; Peng, Z.-P. Ultralong high-sensitivity Φ-OTDR for high spatial resolution intrusion detection of pipelines. Opt. Exp. 2014, 22, 13804–13810. [Google Scholar] [CrossRef]
- Aktas, M.; Akgun, T.; Demircin, M.U.; Buyukaydin, D. Deep learning based multi-threat classification for phase-OTDR fiber optic distributed acoustic sensing applications. In Proceedings of the SPIE Commercial + Scientific Sensing and Imaging, Anaheim, CA, USA, 9–13 April 2017; Volume 10208, pp. 75–92. [Google Scholar]
- Hong, X.; Wu, J.; Zuo, C.; Liu, F.; Guo, H.; Xu, K. Dual Michelson interferometers for distributed vibration detection. Appl. Opt. 2011, 50, 4333–4338. [Google Scholar] [CrossRef]
- Qin, L.; Wang, H.; Li, L.; Liang, S.; Zhong, X. Fiber-optic sensor based on Michelson interferometers for distributed disturbance detection. Infr. Laser Eng. 2015, 44, 205–209. [Google Scholar]
- Russell, S.J.; Brady, K.R.C.; Dakin, J.P. Real-time location of multiple time-varying strain disturbances, acting over a 40-km fiber section, using a novel dual-Sagnac interferometer. J. Light. Technol. 2001, 19, 205–213. [Google Scholar] [CrossRef]
- Xu, W.; Zhang, C.; Liang, S.; Li, L.; Lin, W.; Yang, Y. Fiber-optic distributed sensor based on a Sagnac interferometer with a time delay loop for detecting time-varying disturbance. Microw. Opt. Technol. Lett. 2009, 51, 2564–2567. [Google Scholar] [CrossRef]
- Chen, Q.; Jin, C.; Bao, Y.; Li, Z.; Li, J.; Lu, C.; Yang, L.; Li, G. A distributed fiber vibration sensor utilizing dispersion induced walk-off effect in a unidirectional Mach-Zehnder interferometer. Opt. Express 2014, 22, 2167–2173. [Google Scholar] [CrossRef]
- Liu, X.; Wang, Y.; Zhang, J.; Wang, D.; Lv, Y.; Zhang, M.; Jin, B.; Wang, Y. Pulse-modulated Mach–Zehnder interferometer for vibration location. Opt. Comm. 2019, 437, 27–32. [Google Scholar] [CrossRef]
- Spammer, S.; Swart, P.; Chtcherbakov, A. Merged Sagnac-Michelson interferometer for distributed disturbance detection. J. Light. Technol. 1997, 15, 972–976. [Google Scholar] [CrossRef]
- Chtcherbakov, A.A.; Swart, P.L.; Spammer, S.J. Mach–Zehnder and modified Sagnac-distributed fiber-optic impact sensor. Appl. Opt. 1998, 37, 3432–3437. [Google Scholar] [CrossRef] [PubMed]
- Chtcherbakov, A.A.; Swart, P.L.; Spammer, S.J.; Lacquet, B.M. Modified Sagnac/Mach-Zehnder interferometer for distributed disturbance sensing. Microw. Opt. Technol. Lett. 1999, 20, 34–36. [Google Scholar]
- Song, Q.; Zhou, P.; Peng, H.; Hu, Y.; Xiao, Q.; Wu, H.; Jia, B. Improved localization algorithm for distributed fiber-optic sensor based on merged Michelson-Sagnac interferometer. Opt. Express 2020, 28, 7207–7220. [Google Scholar] [CrossRef]
- Luo, G.; Zhang, C.; Li, L.; Ma, Z.; Lan, T.; Li, C.; Lin, W. Distributed fiber optic perturbation locating sensor based on dual Mach-Zehnder interferometer. In Proceedings of the International Symposium on Photoelectronic Detection and Imaging: Technology and Applications, Beijing, China, 9–12 September 2007; Volume 6622, pp. 66220z1–66220z7. [Google Scholar]
- Tu, D.; Xie, S.; Jiang, Z.; Zhang, M. Ultra long distance distributed fiber-optic system for intrusion detection. In Proceedings of the Advanced Sensor Systems and Applications V, Beijing, China, 5–9 November 2012; Volume 8561, pp. 354–359. [Google Scholar]
- Chen, Q.; Liu, T.; Liu, K.; Jiang, J.; Ding, Z.; Zhang, L.; Li, Y.; Pan, L.; Ma, C. An elimination method of polarization-induced phase shift and fading in dual Mach–Zehnder interferometry disturbance sensing system. J. Light. Technol. 2013, 31, 3135–3141. [Google Scholar] [CrossRef]
- Ma, C.; Liu, T.; Liu, K.; Jiang, J.; Ding, Z.; Pan, L.; Tian, M. Long-range distributed fiber vibration sensor using an asymmetric dual Mach–Zehnder interferometers. J. Light. Technol. 2016, 34, 2235–2239. [Google Scholar] [CrossRef]
- Huang, J.; Chen, Y.; Song, Q.; Peng, H.; Zhou, P.; Xiao, Q.; Jia, B. Distributed fiber-optic sensor for location based on polarization-stabilized dual-Mach-Zehnder interferometer. Opt. Express 2020, 28, 24820–24832. [Google Scholar] [CrossRef]
- Ho, H.-R.; Hsieh, C.-Y.; Hsu, Y.-C.; Wang, L. Modified dual Mach-Zehnder interferometers with new locating algorithm for intrusion detection. Opt. Express 2021, 29, 34341–34359. [Google Scholar] [CrossRef]
- Li, M.-C.; Wang, L. Dual Mach-Zehnder Interferometers with hierarchical clustering analysis method applied for positioning the intrusion. IEEE Sens. J. 2022, 23, 1179–1190. [Google Scholar] [CrossRef]
- Sun, Q.; Liu, D.; Wang, J.; Liu, H. Distributed fiber-optic vibration sensor using a ring Mach-Zehnder interferometer. Optics Comm. 2008, 281, 1538–1544. [Google Scholar] [CrossRef]
- Zhang, C.; Li, Q.; Liang, S.; Lin, W.; Li, L.; Zhong, X. Location algorithm for multi-disturbances in fiber-optic distributed disturbance sensor using a Mach-Zehnder interferometer. In Proceedings of the 9th International Conference on Optical Communications and Networks, Nanjing, China, 24–27 October 2010; pp. 102–107. [Google Scholar]
- Abouelkhir, N.-E.; Slaoui, A.; Saidi, E.H.; Laamara, R.A.; El Hadfi, H. Enhancing phase sensitivity in Mach-Zehnder interferometer with various detection schemes using SU(1,1) coherent states. J. Opt. Soc. Am. B 2025, 42, 495–508. [Google Scholar] [CrossRef]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, T.-W.; Wang, L. Hierarchical Clustering Analysis for Positioning Two Intrusion Events at Different Locations Using Dual Mach-Zehnder Interferometers. Sensors 2025, 25, 5074. https://doi.org/10.3390/s25165074
Chen T-W, Wang L. Hierarchical Clustering Analysis for Positioning Two Intrusion Events at Different Locations Using Dual Mach-Zehnder Interferometers. Sensors. 2025; 25(16):5074. https://doi.org/10.3390/s25165074
Chicago/Turabian StyleChen, Ting-Wang, and Likarn Wang. 2025. "Hierarchical Clustering Analysis for Positioning Two Intrusion Events at Different Locations Using Dual Mach-Zehnder Interferometers" Sensors 25, no. 16: 5074. https://doi.org/10.3390/s25165074
APA StyleChen, T.-W., & Wang, L. (2025). Hierarchical Clustering Analysis for Positioning Two Intrusion Events at Different Locations Using Dual Mach-Zehnder Interferometers. Sensors, 25(16), 5074. https://doi.org/10.3390/s25165074




