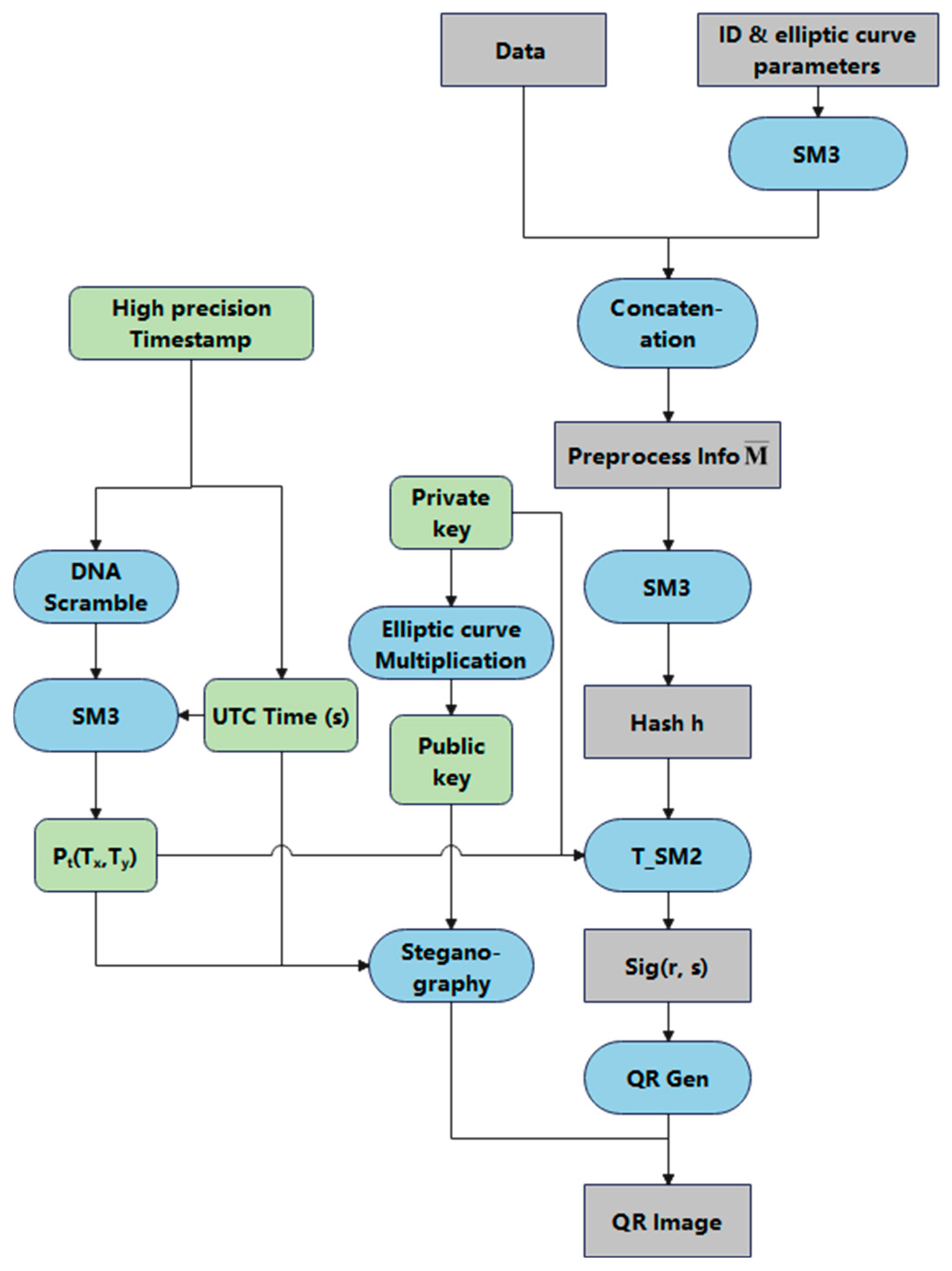
5.2.1. Comparison and Analysis of Signature Algorithms
As shown in
Table 5, the T_SM2 algorithm, like ECDSA and SM2, is based on the ECDLP. Compared to RSA, which relies on the integer factorization problem, T_SM2 offers a significant advantage in terms of key length: to achieve the same level of security, T_SM2 requires only a 256-bit key, whereas RSA requires a 3072-bit key. This results in improved computational efficiency and resource utilization.
In the process of generating digital signatures, most algorithms utilize hash functions to produce fixed-length message digests. This not only significantly reduces the computational load of the signing process but also ensures data integrity and resistance to tampering. Therefore, the collision resistance and computational performance of the hash function are critical considerations. To address these requirements, the T_SM2 algorithm adopts the Chinese national cryptographic hash function SM3, which offers collision resistance and computational performance comparable to the widely used SHA-256, thereby ensuring strong security and good compatibility
In the subsequent stages, T_SM2 further supports user identity binding and timestamp authentication, and it reduces reliance on random number generation. These features further enhance its security and applicability in scenarios requiring high identity assurance and strict time sensitivity.
5.2.2. Attack Resistance Analysis
In elliptic curve-based digital signature algorithms, the random number used during the signing process is a critical parameter that directly determines both the uniqueness and security of the signature. If the same random number is reused, it can lead to serious risks of private key leakage. Both ECDSA and the standard SM2 are susceptible to private key recovery attacks. Taking ECDSA as an example, its signature consists of a pair of values (
r,
s), where:
If the same random nonce
k is used to sign two different messages, the resulting signatures will share the same
r value, forming two signature pairs (
r,
s1) and (
r,
s2). By subtracting
s2 from
s1, the random nonce
k can be derived (Equation (8)):
Once the nonce
k is recovered by an attacker, it can be substituted into the signature equation to solve for the private key
d.
This vulnerability has led to severe consequences in real-world systems. For example, in 2010, Sony’s PlayStation 3 suffered an ECDSA private key leak due to the use of a fixed
k [
38]. Similarly, in 2013, a flaw in the random number generator on the Android platform caused nonce reuse in Bitcoin wallets, resulting in large-scale theft of funds [
39].
In addition, digital signature algorithms that heavily rely on random numbers may also be vulnerable to replay attacks. A replay attack refers to a scenario where an adversary intercepts a valid digital signature during communication, stores it, and subsequently resends it in a different context or at a later time. This allows the attacker to impersonate a legitimate user or execute unauthorized operations, deceiving the recipient into accepting the request as authentic and current. If the system lacks effective mechanisms to verify the uniqueness or timeliness of a signature, the attacker can repeatedly exploit the same signature, leading to unauthorized access, resource exhaustion, and other serious security threats. Therefore, the degree of reliance on randomness in a digital signature algorithm plays a critical role in determining its overall security, particularly in terms of resisting private key leakage and replay attacks.
To evaluate the security of digital signature algorithms under scenarios involving the reuse of the random number
k, this study conducts multiple signatures on the same dataset using the same private key and identical random number
k. This setup simulates scenarios in which an attacker intercepts signature communications or obtains previously signed messages and exploits the reuse of the random number
k to attempt private key recovery or perform replay attacks. Such attacks may occur in real-world applications due to improper implementation of random number generators or compromise of signature devices. A comparative analysis is then performed to assess the resilience of ECDSA, SM2, and the improved T_SM2 algorithm against such attacks. The experimental results are summarized in
Table 6.
5.2.3. Timestamp Precision Analysis
Numerous researchers have proposed various digital signature schemes based on timestamps, either to enable time-based authentication or to enhance the randomness in the signature generation process. In the T_SM2 algorithm proposed in this study, a high-precision timestamp is introduced from an external high-resolution clock. Due to limitations in the local computer hardware, a GNSS common-view receiver is employed to achieve nanosecond-level accuracy. In contrast, most related works rely on UNIX timestamps [
20,
21], obtained from standard computer hardware, which offer only second-level precision—a significant difference in terms of orders of magnitude.
This substantial improvement in timestamp precision greatly enhances the accuracy of time authentication, allowing the signature generation time to be recorded with much higher accuracy. As a result, the reliability of time validity verification is significantly improved, which is particularly beneficial in time-sensitive fields such as metrology. Furthermore, the nanosecond-level timestamp offers finer-grained temporal input, enriching the entropy of the random seed used during signature generation. This, in turn, strengthens the overall randomness of the signature and its resistance to replay attacks.
By comparison, second-level timestamps, due to their limited resolution, are more likely to cause time window overlaps, which not only reduces the accuracy of time authentication but may also weaken the cryptographic strength of the signature due to insufficient randomness.
5.2.4. Other Security Analyses
The hash function employed by T_SM2 is SM3, which is part of the national cryptographic standard system, offering robust security and compatibility. SM3 is optimized based on SHA-256, with the same output length of 256 bits. SM3 exhibits comparable security strength to SHA-256 in collision resistance, with equivalent computational efficiency. Theoretically, its collision resistance achieves a security level of
due to the birthday bound, making it suitable for high-security applications. As shown in
Table 7, even a minor change of just one bit in the input leads to a significant alteration in the generated hash value, highlighting its high sensitivity to input variations.
T_SM2 is built upon the national cryptographic standard SM2 digital signature algorithm, providing an equivalent level of key security. The private key is generated and securely stored within the cryptographic chip embedded in the user’s local device, ensuring both the authenticity and confidentiality of the key.
Furthermore, to prove that the T_SM2 signature scheme achieves existential unforgeability under adaptive chosen message attacks (EUF-CMA), this paper conducts the analysis based on the following security assumptions:
In the security proof, we introduce a game-based model involving two parties: the challenger C and the adversary A. The interaction between them is defined as follows:
The challenger C runs the key generation algorithm of T_SM2 to obtain a private key d and computes the corresponding public key P for the adversary A;
The adversary A adaptively submits a sequence of messages M1, …, Mn to C, who returns valid signature pairs for each message, following the signing procedure defined in Algorithm 1;
Finally, the adversary outputs a new message–signature pair , where , and attempts to forge a valid signature on .
If the verification algorithm returns Accept, i.e., , then the adversary is considered to have succeeded in the attack.
Next, if there exists an adversary A that can successfully forge a valid signature pair with non-negligible probability, then one can construct an algorithm to solve the ECDLP, which contradicts the assumption of its computational intractability. It is important to note that although the adversary may obtain the perturbed timestamp hash values Tx and Ty, these values primarily serve to prevent signature replay, thereby ensuring the uniqueness of each signature. The adversary cannot deduce the ephemeral value k or any other sensitive information from Tx and Ty. Therefore, without knowledge of the legitimate private key d, the adversary cannot generate a new valid signature, even with access to the timestamp hashes.
Assuming the adversary successfully forges a signature
, the signature must satisfy the following conditions:
To achieve this goal, the adversary would need to predict or invert the values of h,
, and
, which requires solving the ECDLP or finding a hash collision. As both tasks are computationally infeasible, signature forgery remains impractical.
Therefore, we conclude that the T_SM2 signature scheme is secure under the EUF-CMA model; that is, no efficient adversary can forge a new valid signature under reasonable computational constraints.