From IOTA Tangle 2.0 to Rebased: A Comparative Analysis of Decentralization, Scalability, and Suitability for IoT Applications
Abstract
1. Introduction
2. Evolution of the IOTA Tangle
2.1. The Tangle
2.2. Network Protocol Updates
3. IOTA 2.0: Promises and Challenges
3.1. Core Concepts
3.1.1. Leaderless Full Decentralization
3.1.2. Consensus Mechanism
3.1.3. Reputation and Resource Management
- Stored Mana: Linked to token outputs and transferable, this type of Mana gradually decays over time to encourage continuous participation.
- Block Issuance Credits (BIC): Non-transferable credits enabling users to issue blocks, with usage dynamically adjusted based on network congestion, deterring spam and misuse.
3.1.4. Smart Contracts
3.1.5. Security Enhancements
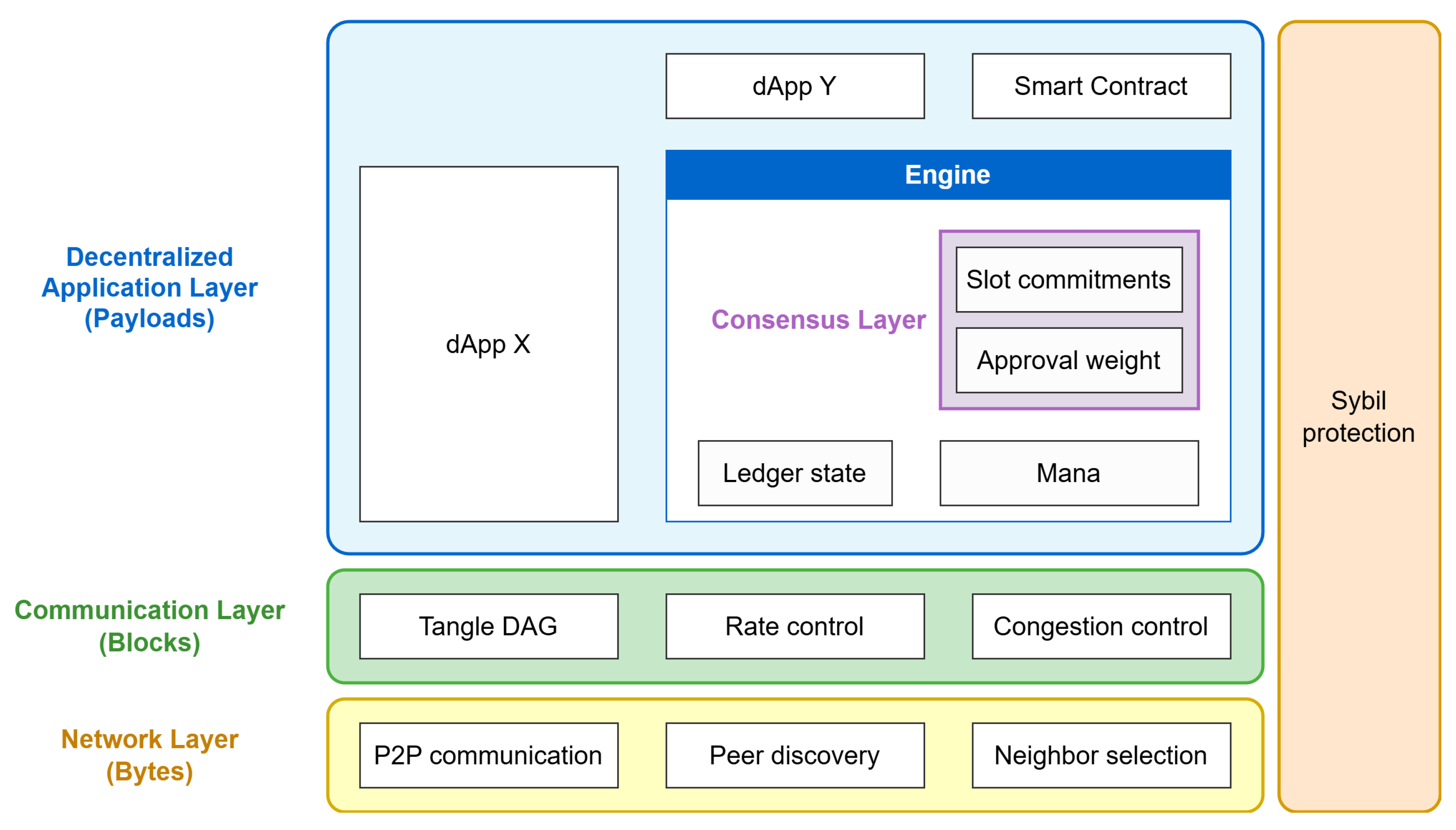
3.2. Protocol Layers
3.3. Unmet Goals and Challenges of IOTA 2.0
3.3.1. Consensus Mechanism Complexities
3.3.2. Finalization Process Complexity
3.3.3. Protracted Development Cycle
3.3.4. Architectural Refinements and Optimizations
3.3.5. Smart Contracts Functionality Implementation
3.3.6. Competition from Other Blockchains
3.3.7. Hardware and Resource Constraints
4. IOTA Rebased: A Technical Overview
4.1. Technical Foundation
4.1.1. Object-Based DAG Ledger
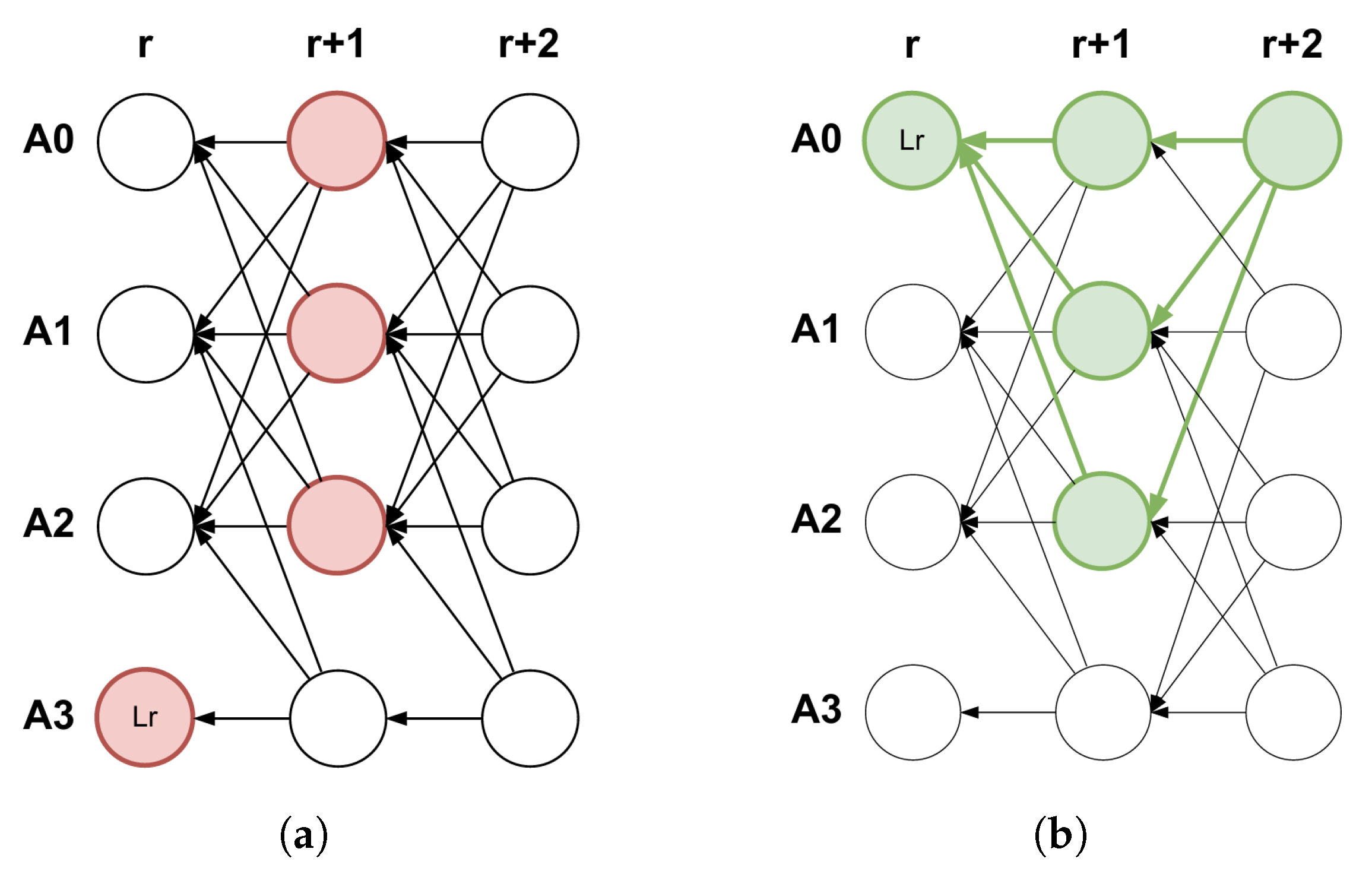
4.1.2. Mysticeti Consensus Protocol
- The skip pattern (Figure 4a) is identified at round when at least blocks do not support a specific block . Regardless of the number of proposals for the slot (including none), the skip pattern is identified if, across all proposals, we observe subsequent blocks that either do not support it or support no proposal at all.
- The certificate pattern (Figure 4b) is identified at round when at least blocks support a block . In this case, block B is considered certified, guaranteeing its availability and that no other certified block may exist for the same spot . Any subsequent block (like one at round ) that includes this pattern within its history is called a certificate for block B.
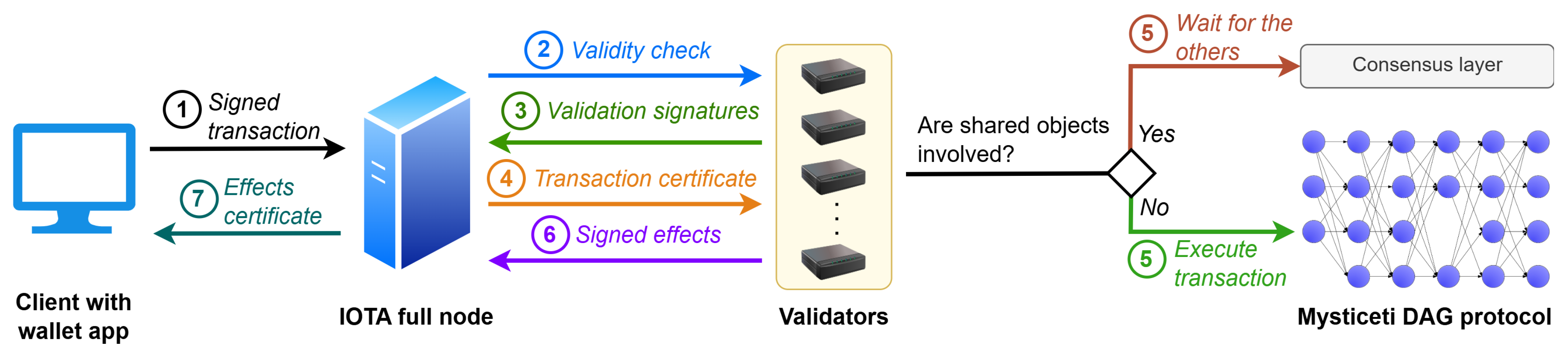
4.1.3. Transactions Life Cycle
4.1.4. Smart Contracts Virtualization
4.2. Tokenomics
4.2.1. Fee Model
4.2.2. Stacking and Inflation
5. Comparative Analysis of IOTA 2.0 with Rebased
5.1. Consensus Mechanism
5.2. Transaction Economics
5.3. Scalability
5.4. Security Considerations
5.5. Implications for IoT Applications
6. Challenges and Recommendations for Adopting IOTA Rebased in IoT
6.1. Key Challenges
6.1.1. Reintroduction of Transaction Fees
6.1.2. Staking and Validator Participation
6.1.3. Technical Complexity and Integration
6.1.4. Security and Network Scalability
6.2. Strategic Recommendations
6.2.1. Subsidization and Tiered Fee Structures
6.2.2. Lightweight Client Protocols and Proxies
6.2.3. Batch Transactions
6.2.4. Adaptive Transaction Scheduling
6.3. Use Cases Analysis
6.3.1. Smart Energy Grids and Peer-to-Peer Energy Trading
6.3.2. Supply Chain Tracking and Provenance
6.3.3. Vehicle Communication Systems
6.3.4. Healthcare Remote Monitoring
7. Potential Research Directions
7.1. Adaptive Indexing and QUERY Optimization for DAGs
7.2. Lightweight Privacy-Preserving Mechanisms
7.3. Scalability Under Extreme IoT Loads
7.4. Energy-Efficient Participation
7.5. Convergence with Other Emerging Technologies
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| DLTs | Distributed Ledger Technologies |
| DAG | Directed Acyclic Graph |
| PoW | Proof-of-Work |
| PoA | Proof-of-Authority |
| UTXO | Unspent Transaction Output |
| EdDSA | Edwards-curve Digital Signature Algorithm |
| ISC | IOTA Smart Contracts |
| BFT | Byzantine Fault Tolerant |
| EVM | Ethereum Virtual Machine |
| TPS | Transactions Per Second |
| NFTs | Non-Fungible Tokens |
| MEV | Maximal Extractable Value |
| FCOB | Fast Confirmation of On-the-Heavy Branch |
| FPC | Fast Probabilistic Consensus |
| dRNG | distributed Random Number Generation |
| BIC | Block Issuance Credits |
| DoS | Denial of Service |
| CPS | Cyber-Physical Systems |
| P2P | Peer-to-Peer |
| dApps | Decentralized Applications |
| DPoS | Delegated Proof-of-Stake |
| ECD | Encoded Cordial Dissemination |
| DAC | Data Availability Certificate |
| ORAM | Oblivious RAM |
References
- Zhu, Q.; Loke, S.W.; Trujillo-Rasua, R.; Jiang, F.; Xiang, Y. Applications of Distributed Ledger Technologies to the Internet of Things: A Survey. ACM Comput. Surv. 2019, 52, 120. [Google Scholar] [CrossRef]
- Silvano, W.F.; Marcelino, R. Iota Tangle: A cryptocurrency to communicate Internet-of-Things data. Future Gener. Comput. Syst. 2020, 112, 307–319. [Google Scholar] [CrossRef]
- Vigneri, L.; Welz, W. On the Fairness of Distributed Ledger Technologies for the Internet of Things. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020; pp. 1–3. [Google Scholar] [CrossRef]
- Popov, S. The Tangle. In White Paper; 2018. Available online: https://cryptoverze.s3.us-east-2.amazonaws.com/wp-content/uploads/2018/11/10012054/IOTA-MIOTA-Whitepaper.pdf (accessed on 9 April 2025).
- Soltani, R.; Zaman, M.; Joshi, R.; Sampalli, S. Distributed Ledger Technologies and Their Applications: A Review. Appl. Sci. 2022, 12, 7898. [Google Scholar] [CrossRef]
- Akhtar, M.M.; Rizvi, D.R.; Ahad, M.A.; Kanhere, S.S.; Amjad, M.; Coviello, G. Efficient Data Communication Using Distributed Ledger Technology and IOTA-Enabled Internet of Things for a Future Machine-to-Machine Economy. Sensors 2021, 21, 4354. [Google Scholar] [CrossRef] [PubMed]
- Popov, S.; Moog, H.; Camargo, D.; Capossele, A.; Dimitrov, V.; Gal, A.; Greve, A.; Kusmierz, B.; Mueller, S.; Penzkofer, A.; et al. The Coordicide. In White Paper; 2020. Available online: https://files.iota.org/papers/20200120_Coordicide_WP.pdf (accessed on 9 April 2025).
- Fartitchou, M.; Boussouf, J.; Makkaoui, K.E.; Maleh, Y.; Allali, Z.E. IOTA Tangle 2.0: An Overview. Edpacs 2023, 68, 15–26. [Google Scholar] [CrossRef]
- IOTA Foundation. IOTA Rebased. Technical View. Available online: https://blog.iota.org/iota-rebased-technical-view (accessed on 9 April 2025).
- Babel, K.; Chursin, A.; Danezis, G.; Kichidis, A.; Kokoris-Kogias, L.; Koshy, A.; Sonnino, A.; Tian, M. Mysticeti: Reaching the limits of latency with uncertified dags. arXiv 2023, arXiv:2310.14821. [Google Scholar] [CrossRef]
- Kahmann, F.; Honecker, F.; Dreyer, J.; Fischer, M.; Tönjes, R. Performance Comparison of Directed Acyclic Graph-Based Distributed Ledgers and Blockchain Platforms. Computers 2023, 12, 257. [Google Scholar] [CrossRef]
- Fan, C.; Ghaemi, S.; Khazaei, H.; Chen, Y.; Musilek, P. Performance Analysis of the IOTA DAG-Based Distributed Ledger. ACM Trans. Model. Perform. Eval. Comput. Syst. 2021, 6, 10. [Google Scholar] [CrossRef]
- Sedi Nzakuna, P.; Paciello, V.; Lay-Ekuakille, A.; Kuti Lusala, A.; Iacono, S.D. Empirical Analysis of the IOTA Tangle Ledger in the Stardust Stage. In Proceedings of the 2024 IEEE International Symposium on Measurements & Networking (M&N), Rome, Italy, 2–5 July 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Staines, A.S. Concurrency and Petri Net Models. Science 2022, 18, 19. [Google Scholar] [CrossRef]
- Drąsutis, E. IOTA Smart Contracts. In White Paper; 2021. Available online: https://files.iota.org/papers/ISC_WP_Nov_10_2021.pdf (accessed on 9 April 2025).
- Muntaha, S.T.; Ahmed, Q.Z.; Khan, F.A.; Zaharis, Z.D.; Lazaridis, P.I. Hybrid Blockchain-Based Multi-Operator Resource Sharing and SLA Management. IEEE Open J. Commun. Soc. 2025, 6, 362–377. [Google Scholar] [CrossRef]
- IOTA Foundation. Shimmer’s Roadmap and Evolution. Available online: https://blog.shimmer.network/shimmers-roadmap-and-evolution (accessed on 14 April 2025).
- IOTA Foundation. IOTA’s EVM Mainnet Unleashed. Available online: https://blog.iota.org/iotas-evm-mainnet-launch (accessed on 14 April 2025).
- Sealey, N.; Aijaz, A.; Holden, B. IOTA Tangle 2.0: Toward a Scalable, Decentralized, Smart, and Autonomous IoT Ecosystem. In Proceedings of the 2022 International Conference on Smart Applications, Communications and Networking (SmartNets), Palapye, Botswana, 29 November–1 December 2022; pp. 1–8. [Google Scholar] [CrossRef]
- IOTA Foundation. IOTA 2.0 Research Specifications. Available online: https://github.com/iotaledger/IOTA-2.0-Research-Specifications (accessed on 13 April 2025).
- Müller, S.; Penzkofer, A.; Kuśmierz, B.; Camargo, D.; Buchanan, W.J. Fast Probabilistic Consensus with Weighted Votes. In Proceedings of the Future Technologies Conference (FTC) 2020, Volume 2; Arai, K., Kapoor, S., Bhatia, R., Eds.; Springer: Cham, Switzerland, 2021; pp. 360–378. [Google Scholar] [CrossRef]
- Müller, S.; Penzkofer, A.; Polyanskii, N.; Theis, J.; Sanders, W.; Moog, H. Tangle 2.0 Leaderless Nakamoto Consensus on the Heaviest DAG. IEEE Access 2022, 10, 105807–105842. [Google Scholar] [CrossRef]
- IOTA Foundation. A New Consensus Model: Nakamoto Consensus on a DAG. Available online: https://blog.iota.org/a-new-consensus-model-iota20 (accessed on 13 April 2025).
- Popov, S.; Buchanan, W.J. FPC-BI: Fast Probabilistic Consensus within Byzantine Infrastructures. J. Parallel Distrib. Comput. 2021, 147, 77–86. [Google Scholar] [CrossRef]
- IOTA Foundation. IOTA 2.0 Tokenomics: Mana, Accounts, Staking and Delegation. Available online: https://wiki.iota.org/learn/protocols/iota2.0/core-concepts/mana (accessed on 13 April 2025).
- Fartitchou, M.; Lamaakal, I.; Maleh, Y.; El Makkaoui, K.; El Allali, Z.; Pławiak, P.; Alblehai, F.; A. Abd El-Latif, A. IOTASDN: IOTA 2.0 Smart Contracts for Securing Software-Defined Networking Ecosystem. Sensors 2024, 24, 5716. [Google Scholar] [CrossRef]
- Yu, Z.; Gao, H.; Cong, X.; Wu, N.; Song, H.H. A Survey on Cyber–Physical Systems Security. IEEE Internet Things J. 2023, 10, 21670–21686. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- IOTA Foundation. IOTA 2.0 Data Flow. Available online: https://wiki.iota.org/learn/protocols/iota2.0/core-concepts/data-flow (accessed on 13 April 2025).
- IOTA Foundation. Finality Explained: How Nodes Sync the Ledger. Available online: https://blog.iota.org/finality-explained-iota20 (accessed on 13 April 2025).
- IOTA Foundation. IOTA 2.0: Introducing Pollen, Nectar and Honey. Available online: https://blog.iota.org/iota-2-0-introducing-pollen-nectar-and-honey-de7b9c4c8199 (accessed on 15 April 2025).
- IOTA Foundation. IOTA Rebased Governance Proposal. Available online: https://govern.iota.org/t/iota-rebased-governance-proposal/1768 (accessed on 15 April 2025).
- IOTA Foundation. IOTA Rebased Fast Forward. Available online: https://blog.iota.org/iota-rebased-fast-forward (accessed on 15 April 2025).
- IOTA Foundation. IOTA 2.0 Details on Current Status and Next Steps. Available online: https://iota-news.com/iota-2-0-details-on-current-status-and-next-steps (accessed on 15 April 2025).
- Welc, A.; Blackshear, S. Sui Move: Modern Blockchain Programming with Objects. In Proceedings of the SPLASH 2023: Companion Proceedings of the 2023 ACM SIGPLAN International Conference on Systems, Programming, Languages, and Applications: Software for Humanity, New York, NY, USA, 22–27 October 2023; pp. 53–55. [Google Scholar] [CrossRef]
- Yakovenko, A. Solana: A New Architecture for a High Performance Blockchain v0. 8.13. In White Paper; 2018. Available online: https://solana.com/solana-whitepaper.pdf (accessed on 9 April 2025).
- The MystenLabs Team. The Sui Smart Contracts Platform. In White Paper; 2022. Available online: https://docs.sui.io/paper/sui.pdf (accessed on 9 April 2025).
- IOTA Foundation. Consensus on IOTA. Available online: https://docs.iota.org/about-iota/iota-architecture/consensus (accessed on 15 April 2025).
- Cong, X.; Yu, Z.; Fanti, M.P.; Mangini, A.M.; Li, Z. Predictability Verification of Fault Patterns in Labeled Petri Nets. IEEE Trans. Autom. Control 2025, 70, 1973–1980. [Google Scholar] [CrossRef]
- Polyanskii, N.; Mueller, S.; Vorobyev, I. Starfish: A high throughput BFT protocol on uncertified DAG with linear amortized communication complexity. Cryptol. ePrint Arch. 2025. preprint. [Google Scholar]
- IOTA Foundation. Transaction Life Cycle. Available online: https://docs.iota.org/about-iota/iota-architecture/transaction-lifecycle (accessed on 16 April 2025).
- IOTA Foundation. Q1 2025 Progress Report. Available online: https://blog.iota.org/q12025-progress-report (accessed on 15 April 2025).
- IOTA Foundation. FAQ - IOTA Documentation. Available online: https://docs.iota.org/about-iota/FAQ (accessed on 17 April 2025).
- Chen, E.; Xiao, Z.; Liang, J.; Chen, D.; Hung, P.; Chalkias, K.K. Buck You: Designing Easy-to-Onboard Blockchain Applications with Zero-Knowledge Login and Sponsored Transactions on Sui. arXiv 2024, arXiv:2404.03845. [Google Scholar] [CrossRef]
- Oktian, Y.E.; Lee, S.G.; Lee, H.J. Hierarchical Multi-Blockchain Architecture for Scalable Internet of Things Environment. Electronics 2020, 9, 1050. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-based batch authentication protocol for Internet of Vehicles. J. Syst. Archit. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Lee, H.; Yoon, C.; Bae, S.; Lee, S.; Lee, K.; Kang, S.; Sung, K.; Min, S. Multi-Batch Scheduling for Improving Performance of Hyperledger Fabric Based IoT Applications. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Mišić, J.; Mišić, V.B.; Chang, X.; Qushtom, H. Adapting PBFT for Use with Blockchain-Enabled IoT Systems. IEEE Trans. Veh. Technol. 2021, 70, 33–48. [Google Scholar] [CrossRef]
- Qiu, X.; Chen, W.; Tang, B.; Liang, J.; Dai, H.N.; Zheng, Z. A Distributed and Privacy-Aware High-Throughput Transaction Scheduling Approach for Scaling Blockchain. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4372–4386. [Google Scholar] [CrossRef]
- Zhang, X.; Zhu, X.; Ali, I. Performance Analysis of IOTA Tangle and a New Consensus Algorithm for Smart Grids. IEEE Internet Things J. 2024, 11, 6396–6411. [Google Scholar] [CrossRef]
- Mullaney, C.; Aijaz, A.; Sealey, N.; Holden, B. Peer-to-Peer Energy Trading meets IOTA: Toward a Scalable, Low-Cost, and Efficient Trading System. In Proceedings of the 2022 IEEE/ACM 15th International Conference on Utility and Cloud Computing (UCC), Vancouver, WA, USA, 6–9 December 2022; pp. 399–406. [Google Scholar] [CrossRef]
- García-Hernández, J.; Marín-Collazos, L.G.; Jiménez-Estévez, G.; Mendoza-Araya, P. Distributed Ledger Technologies Based Microgrid Energy Management Using IOTA Tangle. In Proceedings of the 2021 IEEE CHILEAN Conference on Electrical, Electronics Engineering, Information and Communication Technologies (CHILECON), Valparaíso, Chile, 6–9 December 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Raman, S.E.; Venkatramaraju, D. Secured and Transparent Transactions Using IOTA Tangle Distributed Ledger Technology in Dairy Supply Chains. In Proceedings of the 2024 International Conference on E-mobility, Power Control and Smart Systems (ICEMPS), Thiruvananthapuram, India, 18–20 April 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Leivadaros, S.; Kornaros, G.; Coppola, M. Secure Asset Tracking in Manufacturing through Employing IOTA Distributed Ledger Technology. In Proceedings of the 2021 IEEE/ACM 21st International Symposium on Cluster, Cloud and Internet Computing (CCGrid), Melbourne, Australia, 10–13 May 2021; pp. 754–761. [Google Scholar] [CrossRef]
- Halgamuge, M.N. Malicious Data Traceability and Throughput Optimization Using Blockchain (IOTA Smart Contracts) for Next Generation Internet of Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 18102–18119. [Google Scholar] [CrossRef]
- Lozano Domínguez, J.M.; Mateo Sanguino, T.J. Review on V2X, I2X, and P2X Communications and Their Applications: A Comprehensive Analysis over Time. Sensors 2019, 19, 2756. [Google Scholar] [CrossRef] [PubMed]
- Abdullah, S.; Arshad, J.; Khan, M.M.; Alazab, M.; Salah, K. PRISED tangle: A privacy-aware framework for smart healthcare data sharing using IOTA tangle. Complex Intell. Syst. 2023, 9, 3023–3041. [Google Scholar] [CrossRef]
- Akbulut, S.; Semantha, F.H.; Azam, S.; Pilares, I.C.A.; Jonkman, M.; Yeo, K.C.; Shanmugam, B. Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology. Sensors 2023, 23, 5174. [Google Scholar] [CrossRef]
- Wu, H.; Tang, Y.; Shen, Z.; Tao, J.; Lin, C.; Peng, Z. TELEX: Two-Level Learned Index for Rich Queries on Enclave-based Blockchain Systems. In IEEE Transactions on Knowledge and Data Engineering; IEEE Computer Society: Washington, DC, USA, 2025; pp. 1–16. [Google Scholar] [CrossRef]
- Wei, W.; An, B.; Qiao, K.; Shen, J. A Blockchain-Based Multi-Users Oblivious Data Sharing Scheme for Digital Twin System in Industrial Internet of Things. IEEE J. Sel. Areas Commun. 2023, 41, 3318–3332. [Google Scholar] [CrossRef]
- Cao, H.; Li, R.; Tian, W.; Xu, Z.; Xiao, W. Blockchain-based accountability for multi-party oblivious RAM. J. Parallel Distrib. Comput. 2020, 137, 224–237. [Google Scholar] [CrossRef]
- Alshaikhli, M.; Al-Maadeed, S.; Saleh, M. Enhancing Scalability and Network Efficiency in IOTA Tangle Networks: A POMDP-Based Tip Selection Algorithm. Computers 2025, 14, 117. [Google Scholar] [CrossRef]
- Avalanche Foundation. How to Stake. Available online: https://github.com/ava-labs/builders-hub/blob/master/content/docs/nodes/validate/how-to-stake.mdx (accessed on 26 May 2025).
- Mazzocca, C.; Romandini, N.; Montanari, R.; Bellavista, P. Enabling Federated Learning at the Edge through the IOTA Tangle. Future Gener. Comput. Syst. 2024, 152, 17–29. [Google Scholar] [CrossRef]
- Javed, F.; Zeydan, E.; Mangues-Bafalluy, J.; Dev, K.; Blanco, L. Blockchain for Federated Learning in the Internet of Things: Trustworthy Adaptation, Standards, and the Road Ahead. arXiv 2025, arXiv:2503.23823. [Google Scholar] [CrossRef]


| Protocol | Release Date | Description | Main Features |
|---|---|---|---|
| IOTA 1.0 | July 2016 | The legacy version of the IOTA Tangle, using a probabilistic consensus algorithm based random walkers to select most suitable tips for approval. | Trinary data representation. |
| Chrysalis 1 (IOTA 1.5) | August 2020 | The White-Flag approach replaces the heavy probabilistic consensus algorithm, addressing the conflict spamming attack by enforcing a deterministic ordering of the Tangle. | White-Flag confirmation. |
| Chrysalis 2 (IOTA 1.5) | April 2021 | Transitioned from trinary to binary data representation, replaced the account model with the UTXO model, migrated from Winternitz One-Time Signature to EdDSA signature scheme, and implemented measures to guard against dust transactions. | Binary data representation, UTXO, EdDSA. |
| Stardust | October 2023 | Introduced support for multiple assets support, implemented byte cost-based granular dust protection through storage deposits, evolved vertices from messages to blocks, and prepared for ISC anchoring via Alias Outputs, replacement of the single Coordinator node with a validation committee. | Multiple assets, smart contracts, byte cost-based dust protection, blocks as vertices, Bench32 addresses, validation committee. |
| IOTA Rebased | May 2025 | Reimagined ledger architecture replacing the Tangle with the Mysticeti DAG, introducing transaction fees, MoveVM-based smart contracts, and a Delegated Proof-of-Stake (DPoS) consensus model via the Mysticeti protocol. | Object-oriented ledger, Mysticeti protocol, transaction fees, MoveVM integration, DPoS consensus. |
| Feature | IOTA 2.0 | IOTA Rebased |
|---|---|---|
| Ledger model | UTXO-based Tangle DAG with simpler microtransaction logic | Object-oriented ledger enabling Layer 1 smart contracts at the cost of microtransaction logic |
| Hardware requirements | Light nodes could operate on low-power IoT devices | MoveVM and Mysticeti demand higher computational resources, limiting edge devices participation |
| Consensus | Nakamoto on DAG, prioritizes decentralization | DPoS with Mysticeti, high throughput and low latency, 0.5-s finality |
| Transaction fees | Feeless, ideal for microtransactions | Minimal fees, supports economic sustainability |
| Scalability | Theoretically high TPS, scaling with network activity, potentially variable confirmation times | Over 50,000 TPS, fixed set of validators, suited for high-speed transactions |
| Security | Decentralized validation with Mana for reputation | Economic security via staking and periodic validator refresh |
| Smart contracts | Layer 2 with limited Layer 1 support | Native Layer 1 with Layer 2 solutions, MoveVM and IOTA EVM, supports complex dApps |
| Governance | Permissionless, decentralized, fully inclusive | On-chain voting, DPoS validators committee, faster but less inclusive |
| IoT suitability | Optimized for low-cost, high-frequency transactions | Economic model may hinder low-value transactions in IoT setups |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sedi Nzakuna, P.; Paciello, V.; Lay-Ekuakille, A.; Kuti Lusala, A.; Dello Iacono, S.; Pietrosanto, A. From IOTA Tangle 2.0 to Rebased: A Comparative Analysis of Decentralization, Scalability, and Suitability for IoT Applications. Sensors 2025, 25, 3408. https://doi.org/10.3390/s25113408
Sedi Nzakuna P, Paciello V, Lay-Ekuakille A, Kuti Lusala A, Dello Iacono S, Pietrosanto A. From IOTA Tangle 2.0 to Rebased: A Comparative Analysis of Decentralization, Scalability, and Suitability for IoT Applications. Sensors. 2025; 25(11):3408. https://doi.org/10.3390/s25113408
Chicago/Turabian StyleSedi Nzakuna, Pierre, Vincenzo Paciello, Aimé Lay-Ekuakille, Angelo Kuti Lusala, Salvatore Dello Iacono, and Antonio Pietrosanto. 2025. "From IOTA Tangle 2.0 to Rebased: A Comparative Analysis of Decentralization, Scalability, and Suitability for IoT Applications" Sensors 25, no. 11: 3408. https://doi.org/10.3390/s25113408
APA StyleSedi Nzakuna, P., Paciello, V., Lay-Ekuakille, A., Kuti Lusala, A., Dello Iacono, S., & Pietrosanto, A. (2025). From IOTA Tangle 2.0 to Rebased: A Comparative Analysis of Decentralization, Scalability, and Suitability for IoT Applications. Sensors, 25(11), 3408. https://doi.org/10.3390/s25113408










