Abstract
Secure group communication in Vehicle Ad hoc Networks (VANETs) over open channels remains a challenging task. To enable secure group communications with conditional privacy, it is necessary to establish a secure session using Authenticated Key Agreement (AKA). However, existing AKAs suffer from problems such as cross-domain dynamic group session key negotiation and heavy computational burdens on the Trusted Authority (TA) and vehicles. To address these challenges, we propose a dynamic privacy-preserving anonymous authentication scheme for condition matching in fog-cloud-based VANETs. The scheme employs general Elliptic Curve Cryptosystem (ECC) technology and fog-cloud computing methods to decrease computational overhead for On-Board Units (OBUs) and supports multiple TAs for improved service quality and robustness. Furthermore, certificateless technology alleviates TAs of key management burdens. The security analysis indicates that our solution satisfies the communication security and privacy requirements. Experimental simulations verify that our method achieves optimal overall performance with lower computational costs and smaller communication overhead compared to state-of-the-art solutions.
1. Introduction
Vehicle Ad hoc Networks (VANETs) play a crucial role in supporting intelligent transportation systems, including data sharing and collaborative processing, within modern urban traffic [1]. The popularity of electric vehicles brings more powerful sensing modules and stronger computation capabilities. VANETs, through the cooperation of On-Board Units (OBUs) and Roadside Units (RSUs), can provide high-speed data communication services between vehicles, guaranteeing the safety of vehicle travel and achieving fully intelligent traffic management. For example, in the event of a traffic accident, relevant vehicles can report the incident to nearby sections through RSUs, guiding nearby vehicles to avoid congested routes [2]. The role of VANETs in intelligent transportation has attracted attention from both industry and academia [3].
Unlike many fixed-terminal networks, VANETs must deal with rapid changes in access and are more prone to attacks like eavesdropping, user tracking, and tampering [4]. In an open VANET, ensuring communication and data security is a key concern. Traditional VANET security protection schemes generally involve a Trusted Authority (TA) that issues certificates to vehicles and RSUs, handles authentication at the access endpoints, and performs critical security algorithms [5]. However, as more vehicles join VANETs, the TA needs to manage a large number of certificates and handle a significant amount of requests, resulting in high computational and storage costs for the TA. Furthermore, due to the TA’s distance from vehicles and RSUs, higher latency is more likely, making it unable to provide real-time services.
To address the drawbacks of a single TA, multi-TA schemes have been introduced into VANETs [6]. In a multi-TA scheme, fog computing TA sub-nodes are deployed on the RSU side, and fog node TAs are managed by a central TA, forming a two-tier TA structure. Vehicles are authenticated and managed by the fog TA nodes on the RSU side, greatly improving the real-time data processing and mitigating the impact caused by DoS attacks. The VANETs architecture with multi-TA composed of fog computing can significantly enhance the service quality of the network [7].
In some previous VANET schemes, vehicles or RSUs directly report the road conditions to the TA [8]. The TA collects real-time data and responds accordingly. However, as the amount of data generated by vehicles rapidly increases, this places a significant computational burden on the TA, and the cost of storing and computing by the TA becomes extremely high. To address this issue, some scholars have combined VANETs with cloud computing [9,10], using cloud computing to store and process data in VANETs, providing VANETs with more elastic computing capabilities. For example, authenticated vehicles have the ability to upload traffic data to the remote cloud, while the TA is only responsible for secure computations such as authentication.
In VANETs, authenticated key agreement is crucial for communication security. A session security key protocol that satisfies session security can be used to construct a communication channel with dynamic members [11]. Furthermore, to provide security and privacy protection for VANETs communication, various scholars have introduced Conditional Privacy-Preserving (CPP) authentication schemes in recent years [12], where the information of vehicles is kept private from all participants except the TA. However, if a vehicle engages in malicious behavior, the TA is able to trace its real identity.
In recent years, many classic solutions have been studied for CPP authentication under VANETs. Lin et al. [13] combined blockchain technology with key derivation algorithms to manage certificates, in order to avoid vehicles storing a large number of keys, but the single TA mode is vulnerable to DoS attacks. Yu et al. [14] used ECC and certificateless aggregate signatures to reduce the computational load of OBUs, but they cannot support dynamic groups. Wang et al. [15] proposed a scheme that achieves conditional privacy protection without using pseudonyms, but it involves operations with bilinear pairs, resulting in high computational costs and unfriendly support for vehicles with low computing power.
Our Contributions
To summarize, existing schemes still have issues to address. Traditional session AKA solutions lack consideration for cross-domain scenarios and complete group session key negotiation within a single domain. Multi-TA may enhance VANET response speed and capacity but faces challenges due to increasing data volume. Our scheme addresses these issues by introducing a dynamic privacy-preserving anonymous authentication scheme tailored for fog-cloud-based VANETs. It utilizes RSUs as fog computing nodes, incorporates multi-level TAs, and integrates cloud services for storage and computing. Lightweight security algorithms are employed for group session key negotiation to ensure secure VANET communication. The contributions of our proposed scheme include:
- The introduction of an anonymous and dynamic conditional privacy-preserving scheme using basic elliptic curve algorithms and hash functions for low-computing-power OBUs.
- The implementation of certificateless and multi-TA modes to reduce the burden on TAs, improve response speed, and enhance overall VANET robustness. The use of cloud services as an outsourcing platform to expand data processing capabilities and boost VANET performance.
- Security analysis demonstrates satisfaction of VANET security requirements, achieving forward security and resisting attacks. In comprehensive performance, our proposed solution is better than existing similar conditional privacy-preserving schemes in comprehensive performance.
2. Related Work
In order to meet the security and privacy protection requirements of vehicle communication in open channels, many researchers have conducted research on conditional privacy protection for VANETs in recent years. These studies are roughly summarized as PKI-based, certificateless, fog-cloud-based, and blockchain-based.
In 2007, Raya et al. [16] introduced the first PKI-based conditional privacy protection authentication system, aiming to enhance the security of vehicle communication through the utilization of anonymous certificates. However, this scheme necessitates the involvement of a Certification Authority (CA) to handle a substantial volume of certificates. Xiong et al. [17] introduced a authentication framework ensuring conditional privacy with support for dynamic members using the Chinese Remainder Theorem. This protocol supports both forward and backward security, but it also faces the problem of certificate management by a single TA. In response to the security update challenges related to Tamper-Proof Device (TPD) keys, Wei et al. [18] introduced a secure updateable conditional privacy protection authentication scheme. This scheme is built upon Shamir’s secret sharing and secure pseudo-random functions to ensure the robustness of the security updates for TPD keys. By using ECC signatures, this scheme improves the transmission speed of messages in emergency situations. To tackle the security challenges associated with heterogeneous vehicle communication in VANETs, Ali et al. [19] introduced an privacy hybrid signcryption scheme with high efficiency. This scheme relies on bilinear pairings to enhance the security of communication among diverse vehicles. They also reduced decryption time by using batch decryption. To address the risk of private key leakage in VANETs, Xiong et al. [20] constructed a dual insurance conditional privacy authentication scheme using ECC. Even if the master key or one of the vehicle keys is leaked, this scheme ensures that valid authentication messages cannot be forged. To provide traceability and credibility of malicious senders, Luo et al. [21] designed a conditional privacy protection authentication protocol using ring signatures and ring signcryption. This protocol provides publicly verifiable algorithms for exposing the real identity of malicious users, but it requires the support of a third-party TA. To address the privacy concerns introduced by the open channels in VANETs, Cai et al. [22] proposed a conditional privacy protection scheme for VANETs using identity-based encryption and ring signatures. They proved the security properties of anonymity, traceability, confidentiality, and unforgeability of the scheme. However, Du et al. [23] pointed out issues in [22] such as the lack of anonymous protection for honest senders. They improved the scheme to achieve sender anonymity and malicious user traceability, as well as resistance to response attacks. Additionally, Zhou et al. [24] proposed a multi-key outsourcing computation scheme for VANETs, which designed an efficient privacy protection information filtering system location-based service. This system eliminates useless encrypted information before authentication, optimizing the computation and communication workload. Based on PKI, the CPP solution can achieve complex functions, but it also faces challenges such as high computational costs for certain cryptographic primitives.
To avoid the burden of managing certificates and keys, many researchers have started to consider certificateless schemes in VANETs. In order to enhance computational speed, Chen et al. [25] proposed a certificateless fully aggregated signature scheme in 2021, which does not increase the length of signatures with the number of vehicles, reducing communication and processing costs. This scheme uses general ECC and hash computations, reducing the computational burden. Ali et al. [26] considered the limited computation power of OBUs and designed a certificate-free conditional privacy authentication scheme without bilinear pairings and mapping to points. They used ECC and ordinary hash functions instead and improved overall efficiency through batch signature verification. Building on the scheme proposed by [26], Zhou et al. [27] proposed a certificateless privacy-preserving authentication scheme which was both secure and lightweight. This solution can resist signature forgery attacks and has fast computational efficiency compared to [26]. Certificateless solutions effectively reduce the pressure of certificate and key management and lower the risk of key leakage. However, TA requires responsibility for participating in the generation of all keys and certificates, which can be a significant burden.
To address the issue of a high workload on a single CA, several fog-cloud-based VANET solutions have been proposed. Goudarzi et al. [28] proposed a fog-based VANET privacy protection authentication protocol, which utilizes Quotient Filter to solve node authentication, and uses fog nodes to reduce system latency and improve system throughput. Zhong et al. [29] proposed a fog computing-based CPP scheme, which supports mobility, low latency, and location awareness through fog computing, and reduces expenses by generating pseudonyms using two hash chains. Navdeti et al. [30] proposed a fog-based VANET privacy protection and secure data sharing scheme. By outsourcing the data to cloud servers and implementing fine-grained access control, data forwarding is reduced, and bandwidth requirements are lowered through fog computing. Wang et al. [31] designed a road condition monitoring scheme based on cloud that incorporates a hierarchical structure with a root authority (RA) and sub-authorities. This method improves response speed by using multiple sub-authorities and reduces the pressure on the root authority. The cloud server can quickly verify the validity of ciphertexts and categorize traffic condition reports based on equivalence classes to achieve batch processing of tasks. In order to resist DoS attacks and improve communication efficiency, Wei et al. [32] introduced a multi-TA scheme designed for privacy protection under specific conditions, employing fog computing to enhance communication efficiency and facilitate the revocation of identities of illegal vehicles. Yang et al. [33] proposed an anonymous certificateless aggregated signature encryption system for conditional privacy protection. This scheme aggregates the signed messages from neighboring vehicles into aggregate ciphertexts using fog nodes, and batch verifies them. This scheme avoids key escrow and pseudonym management. Fog-cloud-based VANETs can enhance system computing capacity and communication efficiency, and reduce pressure on TA. However, few schemes combine clouds and fog, forming a more scalable cloud-fog architecture.
In terms of combining with blockchain, Liu et al. [34] implemented conditional privacy protection using identity-based group signatures and managed vehicle reputation values using blockchain to identify the reliability of messages. In order to improve the efficiency of blockchain-based conditional privacy protection authentication schemes, Zhou et al. [35] proposed the use of knowledge signatures for identity verification to improve efficiency and eliminate the need for secure channels for key distribution. Yang et al. [36] proposed an access control scheme for partial data privacy in VANETs using function encryption. This scheme divides data access into offline and online stages to reduce online computation costs and improve efficiency. The blockchain is used to guarantee identity records and prevent data tampering. To meet the requirements of high mobility and real-time performance in VANETs, Lin et al. [37] used a one-time public key generation mechanism to generate anonymous public keys and used knowledge signatures for authentication. The anonymous public keys for data sharing can be generated and published on the blockchain in advance, improving the overall performance of the protocol. However, none of the above schemes consider the requirements of vehicle social networking, which motivated us to propose a dynamic privacy-preserving anonymous authentication scheme for condition-matching in fog-cloud-based VANETs.
3. Preliminary
3.1. Elliptic Curve Cryptosystem
The definition of an elliptic curve over the finite field with prime order p is , where the condition is satisfied. The group representation on the elliptic curve is defined as , where is called the point at infinity [38].
3.2. Related Complexity Assumptions
The security of the proposed scheme relies on the following complexity assumptions.
- Computational Discrete Logarithm (DL) Assumption: For a given generator P of group G and a point , there exists no polynomial-time algorithm capable of determining the integer .
- Decisional Computational Diffie-Hellman (CDH) Assumption: When provided with the tuple in group G, where are unknown, no polynomial-time algorithm can distinguish whether or represents a random element in G.
4. Scheme Formulation
4.1. System Model
The system model is illustrated in Figure 1, and the key entities are introduced below.
- Trusted Authority (TA): Responsible for global initialization and creating the main key pair of the system. Also, help to generate public and private key pairs for fog nodes to avoid key escrow issues. TA acts as the root TA and is not directly responsible for vehicle registration.
- Fog Node (FN): Acts as a subordinate TA and registers with TA. Responsible for managing vehicle registration on the road segment. Adopts a certificateless approach to avoid vehicle key escrow issues.
- Vehicle (VH): Participant in traffic. Vehicles register with fog nodes to obtain public-private key pairs. Vehicles can autonomously establish cross-domain groups based on traffic conditions and securely communicate within the group using negotiated secure keys.
- Cloud Server (CS): Serves as the system’s data storage hub and message distribution center. Stores encrypted messages from vehicles and broadcasts them to other group members. Facilitates efficient communication and message retrieval.
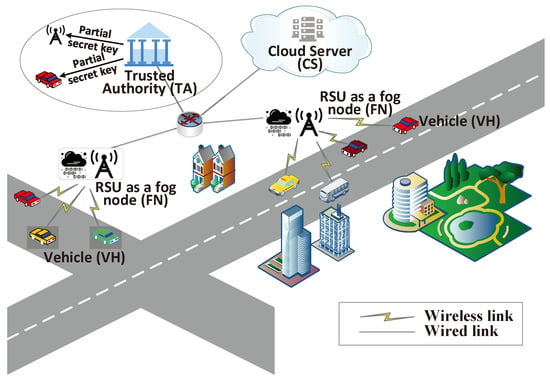
Figure 1.
System architecture.
Next, we will explain the system workflow in detail.
- performs global initialization of the privacy-preserving vehicular communication system, creating the main key pair and other public parameters. securely stores the master key locally and publicly exposes the public parameters to other entities in the system.
- The fog node () registers with . chooses a random secret value and generates partial keys to send to along with its identity information. If is verified as legitimate, computes another partial key for and generates pseudonyms. combines its self-created partial key with the partial key generated by to form its final key pair.
- The vehicle () registers with . chooses a random secret value and generates partial keys to send to along with its identity information. If the information sent by is verified as legitimate, incorporates traffic conditions and a valid time period to generate partial keys and pseudonyms for . By combining its self-generated partial key with the partial key generated by , obtains a complete key pair.
- When a group of vehicles (crossing fog nodes) wishes to establish a condition-based session group, they first use an anonymous authenticated key agreement to generate a group session key. Subsequently, the key obtained through negotiation is used to encrypt the sessions within the group.
- During the communication phase, the message-sending vehicle transmits the message to the CS, which stores it and broadcasts it to other vehicles. Vehicles within the group can retrieve the complete encrypted message from the CS at any time.
- When a vehicle applies to leave the existing group or a new vehicle joins the new group, the system recomputes and updates the group’s session key.
Remark 1.
Crossing fog nodes refers to a vehicle registered at one RSU wishing to communicate with other vehicles registered at another RSU, which may be in a different city and crossing different fog nodes, in order to form a group.
4.2. Security Requirements
The system needs to have the following functions and can provide a series of security protections.
- Mutual authentication: We select as the vehicle with higher computational power, while () represents vehicles with relatively weaker computational power. For the security of the group sessions based on traffic condition matching, mutual authentication between group members and becomes very important.
- Fog node anonymity: In order to eliminate some malicious users from obtaining the location information of vehicles through fog nodes, the scheme must generate pseudonyms for each fog node, and entities other than TA cannot obtain the real identity of fog nodes.
- Vehicle anonymity: In a socially attribute-enabled VANET, protecting the identity privacy of vehicles is crucial. A secure group session authentication key protocol should ensure the anonymity of vehicles, and entities other than TA cannot recover the real identity of vehicles from pseudonyms.
- Fog node traceability: When a malicious event involving a fog node () is received, can obtain the real identity of from pseudonyms to achieve fog node traceability.
- Vehicle traceability: When malicious behavior of a vehicle () is discovered, can use pseudonyms to obtain the real identity of to achieve vehicle traceability.
- Session key establishment: The communication key negotiation within the group is achieved through mutual authentication of all members in the group, creating a session key used to encrypt communication messages among vehicles in the group.
- Cross-domain authenticated key agreement: This scheme must allow the creation of groups between vehicles based on road conditions in different RSUs domains. Cross-domain vehicle groups are crucial for vehicle-based social topics.
- Traffic condition matching: Sharing VANETs-related traffic information is achieved by establishing groups based on traffic condition matching. Only vehicles encountering the same traffic conditions can negotiate a group session key. This traffic condition is invisible to potential attackers.
- Time-limited keys: The establishment of VANETs groups has temporary and spontaneous characteristics, so a time-limited key mechanism can ensure that vehicle keys automatically expire, improving security.
- Perfect forward secrecy: The scheme must have forward secrecy to ensure the confidentiality of intra-group communication in VANETs. Even if a malicious user gains knowledge of the group vehicles, they cannot derive the original group session key.
- Resistance against replay attacks: This scheme should be able to avoid the harm caused by replay attacks, where attackers repetitively send valid messages to vehicles, fog nodes, or TA.
- Resistance against impersonation attacks: The scheme should be able to resist impersonation attacks, where attackers pretend to be one of the entities involved in the scheme and send misleading information to the other communicating party.
- Resistance against tampering attacks: Prevent tampering attacks, where attackers secretly modify transmitted information in VANET communication without the knowledge of the communicating party.
4.3. Security Model
In this scheme, we will establish two categories of adversaries [39,40].
Adversary I: This category of adversary is represented as . is unable to obtain the master key of TA, but can query the public keys of fog nodes and vehicles, and has the ability to replace the public keys with forged ones. can freely query partial private keys and the secret values generated by and , or attempt to disrupt partial private keys and the secret values of and . The constraints for are: (1) cannot disrupt the challenger vehicles, (2) if the public keys of and are replaced, is not allowed to query the partial private keys of and or disrupt and . effectively simulates a malicious vehicle in the system.
Adversary II: This category of adversary is represented as , which has access to the master key of TA. However, does not replace the permissions of the VANETs vehicle public key. With the knowledge of TA’s master key , can compute the partial private keys of all vehicles. The constraint for is not to disrupt the challenger vehicles. can be conceptualized as a simulation of eavesdropping on .
Defined by an interactive game consisting of an adversary and a challenger , the security model of this scheme is established.
Initialization: In this phase, the challenger first creates the system’s public parameters and master public key, then exposes it to the adversary . If the adversary belongs to type , keeps the master key secret. If is of type , reveals the master key to but restricts adversaries from making substitution key requests in subsequent games.
Query Phase: During this phase, the adversary can initiate various queries beyond constraints.
- Hash Query: A hash function and a message are specified by the adversary to query the challenger . The corresponding hash value is generated by the challenger and returned to .
- Symmetric Encryption Query: The adversary initiates a symmetric encryption query using a symmetric key and a message . The challenger responds by providing the ciphertext .
- Extract Secret Value of : The adversary initiates a query for the secret value of fog node . In response, the challenger discloses the secret value of to .
- Extract Partial Key of : The adversary initiates queries to extract the partial secret key associated with fog node . In response, the challenger discloses the partial secret key of to .
- Request public key of : Public keys are made accessible to adversaries. The adversary initiates queries to extract the public key associated with fog node . In response, the challenger provides the public key to .
- Replace public key of : The adversary has the capability to substitute with a carefully chosen valid public key replacement, denoted as . It is important to note that the public key of the challenged fog node cannot undergo replacement, imposing a specific restriction.
- Extract secret value from : The adversary initiates queries to obtain the secret value associated with vehicle . In response, the challenger discloses the secret value of to .
- Extract partial secret key from : The adversary initiates queries to obtain the partial secret key associated with vehicle . In response, the challenger discloses the partial secret key of to .
- Request public key of : Public keys are made accessible to adversaries. The adversary initiates queries to obtain the public key associated with vehicle . In response, the challenger provides the public key to .
- Replace public key of : The adversary possesses the capability to substitute with a carefully chosen valid public key replacement, denoted as . It is crucial to highlight that the public key of the challenged vehicle cannot undergo replacement, subject to specific restrictions.
- Execute: Upon receiving an execution request from , the challenger generates and returns the response information to .
- Reveal group authenticated key: Upon receiving a query for the group authenticated key, the challenger discloses the group authenticated key to .
- Corrupt : In response to the corruption query targeting fog node , the challenger divulges the secret key .
- Corrupt : In response to the corruption query targeting vehicle , the challenger discloses the secret key .
- Test: In the phase, a coin b is randomly tossed by the challenger from the set . If b equals 1, furnishes with the genuine authentication information among the challenged vehicles. If b equals 0, randomly selected authentication information will be provided.
Response: Finally, the adversary submits a guessed result to the challenger . Should be equal to b, the adversary wins the game, and the advantage is computed as .
Definition 1.
This scheme’s security is contingent on the polynomial-time adversary (of either type or ) being unable to win the interactive game with a non-negligible advantage. In simpler terms, any polynomial-time adversary that attains a non-negligible advantage in the game is deemed negligible.
5. The Proposed System
In Table 1, we establish the primary symbols and terms utilized throughout this document. Following this, we detail the initial configuration of the system, the registration processes for both fog nodes and vehicles, the protocols for group key agreement, and the procedures for dynamic vehicle management. The verification of the system’s operational accuracy is presented in Supplemental Material A.

Table 1.
Notations.
5.1. Initial Configuration Stage
The initiates the algorithm by taking the security parameter as an input. This process results in the derivation of system parameters along with a key pair, consisting of the system’s master public and secret keys.
(1) Opting for an elliptic curve E over a finite field p, the makes a selection, where G represents the elliptic curve group and P is its generator.
(2) randomly chooses and calculates . The system master secret key is and master public key is .
(3) For secure encryption/decryption, chooses a symmetric pair () with a key space . Additionally, chooses cryptographic hash functions and () that are resistant to collusion.
(4) Publication by includes the master public key and the system’s public parameters . The master secret key is retained in confidence by .
5.2. Fog Node Registration
In the pursuit of joining the system as the i-th fog node, initiates its registration with . Upon receiving the registration request, undertakes a validation process to ascertain the functionality of as an RSU. If the evaluation proves negative, the request is dismissed; however, in the affirmative case, and engage in mutual collaboration to establish the key pair for . It is noteworthy that this key generation process operates in a key escrow-free and certificateless manner.
(1) Set Secret Value: The fog node with identity selects and computers . Upon determining the secret value, designates and conveys the pair to through a secure channel.
(2) Partial Secret Key Extraction: This algorithm takes ’s master secret key , ’s identity and the public value as input, it outputs ’s partial secret key and pseudo identity.
- selects and computes ’s pseudo identity:
- chooses and computes
- calculates and sends the partial secret key to via secure channel.
- Upon receiving , verifies the equationThe validity of the partial secret key is contingent on the equation holding, and vice versa.
(3) Set Secret Value: The fog node , identified by the pseudo identity , assigns as its confidential secret key.
(4) Set Public Key: The fog node , associated with the pseudo identity , designates as its public key, accessible within the system.
5.3. Vehicle Reporting and Registration
A vehicle informs a fog node about a traffic condition . Subsequently, and engage in an interaction to generate the public/secret key for . Notably, this key generation procedure is designed to circumvent the key escrow problem. establishes a predefined expiration time for the key pair of each vehicle. For example, if the key’s expiration time is set to 1 December 2023, at 14:30, it is represented as “202312011430”. Other vehicles can verify whether the key of that vehicle is within its validity period based on .
(1) Set Secret Value: The vehicle with identity selects and computes . Then, sets as the secret value and securely transmits to through the secure channel.
(2) Partial Secret Key Extraction: As input, ’s secret key , ’s identity , and the public value are taken by this algorithm. In turn, ’s pseudo-identity and partial secret key are outputted.
- selects and computes ’s pseudo-identity:
- chooses and computes
- calculates and sends the partial secret key to via secure channel.
- Receiving , the vehicle verifies whether the following equation is equal:The validity of the partial secret key is contingent on the equation holding, and vice versa.
(3) Set Secret Key: The secret key is adopted by the vehicle and is confidentially stored.
(4) Set Public Key: Adopting as its public key, the vehicle makes this information public within the system.
5.4. Condition-Matching-Based Authenticated Key Agreement
Assuming the vehicles and aim to establish a secure group communication based on condition-matching, ensuring the security of their traffic discussions. The first step involves establishing a group session key. In this scenario, vehicle possesses relatively robust computational capabilities, while the vehicles within have lower computational power. The group-authenticated key agreement unfolds through the following interactive steps.
- Mutual Authentication Requests Within the Group:
The powerful vehicle sends to , and sends to .
Receiving the messages , the vehicle chooses and computes where
Then, sends to , for .
- Authentication Process for High-Computational-Power Vehicles:
When the vehicle receives messages from each vehicle , verifies whether , where
If the above equation holds true, it indicates that the identity of has been verified and encounters the same traffic condition as . Suppose the verified vehicle set be . sets .
Then, chooses and computes where
Then, sends to .
- Authentication Process for Low-Computational-Power Vehicles:
Receiving from , each vehicle computes where
If , it ensures that the identity of is authenticated and encounters the same traffic condition as . Then, computes the group session key
5.5. Vehicle Join
If a set of vehicles with lower computational power encounters the same traffic condition and desires to join the existing session group, the current group members collaboratively establish a new group authentication key as follows.
- Mutual Authentication Requests Within the Group:
The vehicle with relatively robust computational capabilities sends to , and sends to .
Receiving the messages , the vehicle chooses and computes as in the Section 5.4, which is then sent to , for .
- Authentication Process for High-Computational-Power Vehicles:
Upon receiving messages from each vehicle , the vehicle verifies as outlined in Section 5.4. It is assumed that these vehicles are all authenticated to be genuine and share the same traffic condition. sets and .
Then, chooses and computes where
Then, sends to .
- Authentication Process for Low-Computational-Power Vehicles:
Receiving from , each vehicle computes where
If , it indicates that the identity of is authenticated and has encountered the same traffic condition as . Then, computes the group session key
5.6. Vehicle Leave
If a set of vehicles wishes to exit the session group, the remaining group members collaborate to create a new group authenticated key as follows.
sets and . Then, chooses and computes
Then, sends to .
Receiving from , each vehicle computes where
If , the vehicle obtains the negotiated group session key as
6. Security Proof
Theorem 1.
Assuming the decisional CDH assumption holds in the random oracle model, then the scheme we propose is secure against adversary (as defined in Section 4.3).
The formal security proof of Theorem 1 is deferred to Supplemental Material B.
Theorem 2.
In the scenario where the decisional CDH assumption is satisfied, the proposed group authenticated key agreement ensures security against adversaries in the random oracle model.
Proof.
The proof of Theorem 1 is followed with the following modification: the master key can be obtained by a attacker, but the attacker is not permitted to issue substitute public key queries. The remaining part of the proof remains unchanged. □
Theorem 3.
The proposed system satisfies mutual authentication, fog node anonymity, vehicle anonymity, vehicle traceability, cross-domain authenticated key management, group key establishment, condition-matching, time-limited keys, perfect forward secrecy, impersonation/modification/ replay attack resistance.
The proposed system meets the functional and security requirements defined in Section 4.2, which are proven in Supplemental Material C.
7. Performance Comparison and Analysis
To assess the performance of other existing conditional privacy-preserving schemes, a comparison will be made with the proposed system. Subsequently, an assessment of the computational and communication overheads of these schemes will be conducted in a real experimental environment.
7.1. Theoretical Analysis
Before conducting the comparison, we have defined certain symbols in Table 2. Our proposed system will be compared to the schemes introduced in [6,17,21]. We assume the vehicle group has a size of n.

Table 2.
The notations of performance.
7.1.1. Analysis of Computation Overhead
We conducted a theoretical analysis of the computational expenses associated with these schemes in Table 3. When analyzing the computational costs, we do not include the overhead of global initialization and server registration (such as cloud and fog servers) as they are constant and do not vary with the number of vehicles. Additionally, the computational cost of ECC scalar addition is very low, so it is also not taken into account. In the computational analysis, for ease of understanding, we consider the total computational cost of a vehicle from registration to completing verification.
- Ma et al. [6] adopts ECC algorithm design, where the initiating vehicle performs four scalar multiplications on G and five computations hashed to . Hence, the computational overhead for the initiating vehicle is . The verification task is accomplished through collaboration among the cloud server and fog nodes. Fog nodes execute four scalar multiplications on G, two computations hashed to , while the cloud server executes eight scalar multiplications on G and nine computations hashed to . Consequently, the total verification task requires .
- In Xiong et al. [17], before a group session, the TA initially constructs an instance of the Chinese Remainder Theorem and finds a root. Each joining vehicle needs to perform scalar multiplications on G and computations hashed to . Thus, the total computational overhead for the authentication initiation phase is . The verification task requires five scalar multiplications on G, totaling .
- In Luo et al. [21], the initiating vehicle performs five scalar multiplications on , four computations hashed to , and exponentiations on . Hence, the computational overhead for the initiating vehicle is . The verification task requires executing scalar multiplications on , two computations hashed to , n exponentiations on , and two bilinear pairing computations, resulting in a total verification task cost of .
- Our scheme eliminates time-consuming bilinear pairing computations. The computational overhead for the initiating vehicle is , which does not exhibit linear growth with an increase in-group members. For verification, vehicles perform seven scalar multiplications on G and nine computations hashed to , totaling to establish a group authenticated session key.

Table 3.
Comparison of computation overhead [6,17,21].
Table 3.
Comparison of computation overhead [6,17,21].
| Scheme | Registration Phase | Authentication Phase |
|---|---|---|
| Ma et al. | ||
| Xiong et al. | ||
| Luo et al. | ||
| Ours |
l: the quantity of pseudo-identities generated for a vehicle in Xiong et al. [17]. n: the number of vehicles within the group.
7.1.2. Analysis of Communication Overhead
In schemes [6,17], and our scheme, the session key is generated through negotiation, making subsequent communication processes dependent only on the length of the message itself. However, in Luo et al. [21], due to the employment of ring signatures, each communication involves additional data transmission. The communication process involves both sending and receiving parties; therefore, we uniformly consider the data quantity sent by the sender for computation. The theoretical analysis of communication overhead can be found in Table 4.
- In Ma et al. [6], utilizing offline key distribution, the communication cost for the initiating authenticated vehicle comprises three G elements and two elements. The verification process necessitates the transfer of 13 G elements and seven elements, resulting in a total communication cost of for the authentication process.
- In Xiong et al. [17], the communication cost for the initiating authenticated vehicle during the registration phase is , and during the authentication phase is . The overall communication cost sums up to .
- In Luo et al. [21], the communication cost for the initiating authenticated vehicle during the registration phase is , and during the authentication phase is . The total communication cost is .
- In our scheme, the communication cost during the registration phase for the initiating authenticated vehicle is , during the initiation of authentication is , during verification is , resulting in a total communication cost of .
In Luo et al. [21], with each communication involving the group size n, the communication cost becomes maximal. In [6,17], and our proposal, the registration and authentication times for each vehicle are not affected by other members.

Table 4.
Comparison of communication overhead [6,17,21].
Table 4.
Comparison of communication overhead [6,17,21].
| Scheme | Registration Phase | Authentication Phase |
|---|---|---|
| Ma et al. | ||
| Xiong et al. | ||
| Luo et al. | ||
| Ours |
l: the quantity of pseudo-identities generated for a vehicle in Xiong et al. [17]. n: the number of vehicles within the group.
7.1.3. Comparison of Functions and Security
We compared our solution with those in [6,17,21] in Table 5, including functionality and security aspects. In the table, ‘⊥’ denotes aspects that are not discussed or proven in the respective schemes.

Table 5.
Comparison of functions and security [6,17,21].
- Vehicle authentication is a crucial factor in conditional privacy-preserving schemes. The schemes in Table 5 authenticate vehicles either online or offline before distributing group keys.
- Our scheme achieves cross-domain and condition-matching for vehicles. These useful functionalities favor flexible vehicle management. Regrettably, other schemes do not consider these functionalities.
- To our knowledge, our scheme is the first in the literature pertaining to VANETs which supports conditional matching and cross-domain communication under conditional privacy preservation.
- Both our approach and the one presented in Xiong et al. [17] address dynamic scenarios involving the joining and leaving of vehicles in a group. In the event of changes in-group members, the group session key will be promptly updated to maintain the confidentiality of the group session following the changes. It is worth noting that certain alternative schemes lack provisions for managing dynamic member changes.
- In schemes [6,21], vehicle keys are generated offline by the TA and sent to vehicles using smart cards, incurring high usage costs. In Luo et al. [21], all keys are entrusted to the TA, posing insecurity if the TA is compromised. In Xiong et al. [17] and our scheme, certificateless cryptography is adopted, creating a key escrow-free scheme. Each vehicle generates a secret value and transmits the corresponding public information to the TA. The TA is responsible for generating a subset of keys, which, when combined with the secret value, forms the user’s key. Hence, the TA cannot access all elements of the vehicle keys. However, in Xiong et al. [17], pre-computed secret values are sent offline to vehicles, also incurring high usage costs.
- Both our proposed scheme and the one presented in Xiong et al. [17] have been demonstrated to attain forward secrecy and resist the attacks outlined in Table 5. It is noteworthy that not all other schemes exhibit these comprehensive security attributes.
7.2. Simulation
For the simulation of group sessions under conditional privacy protection, we used the Integer and Rational Arithmetic Cryptographic Library (Miracl) [41] to test the performance of our schemes and others, as presented in [6,17,21]. The experiments were performed on a desktop computer with a 64-bit Windows 10 operating system, featuring an Intel(R) Core(TM) i7-9700 CPU @ 3.00 GHz and 16.00 GB RAM.
We selected points belonging to the elliptic curve as elements of group G. The order of group G is denoted by q. The bit length of q is 256 bits, and the bit length of elements in G is 512 bits. We chose the eta_T pairing to evaluate the scheme [21]. The lengths of elements in G, , and are 512 bits, 512 bits, and 256 bits, respectively.
7.2.1. Transmission Efficiency
The transmission costs for vehicles are shown in Table 6 and Figure 2. In our comparison, we consider the total transmission expenses for vehicles during both the registration and authentication processes. We set the group size n of vehicles to vary from 2, 5, 10 to 30. Below is the analysis of the transmission costs for vehicles:
- In Ma et al. [6], the authentication transmission cost when is 20.5 kb. As n increases from 5, 10 to 15, the transmission costs for vehicles are 51.25 kb, 102.5 kb, and 153.75 kb, respectively. When the number of vehicles reaches 30, the total transmission expense amounts to 307.5 kb.
- In Xiong et al. [17], the authentication transmission cost when is 22 kb. The communication volumes generated when n ranges from 5 to 30 are 55 kb, 110 kb, 165 kb, 220 kb, 275 kb, and 330 kb, respectively. The communication costs of this scheme are slightly higher compared to [6].
- In Luo et al. [21], due to the employment of a ring signature scheme, the transmission costs for each vehicle increase with the group size n. When , the transmission cost for authenticating a single message is 6.5 kb. The communication costs generated when n ranges from 5 to 30 are 27.5 kb, 92.5 kb, 195 kb, 335 kb, 512.5 kb, and 727.5 kb, respectively. It is noticeable that this scheme incurs significantly higher communication costs as the number of vehicles increases compared to other schemes.
- In our scheme, when , the authentication transmission cost is 9 kb. The communication costs generated when n ranges from 5 to 30 are 22.5 kb, 45 kb, 67.5 kb, 90 kb, 112.5 kb, and 135 kb, respectively. Our proposed scheme exhibits the most optimal communication costs.
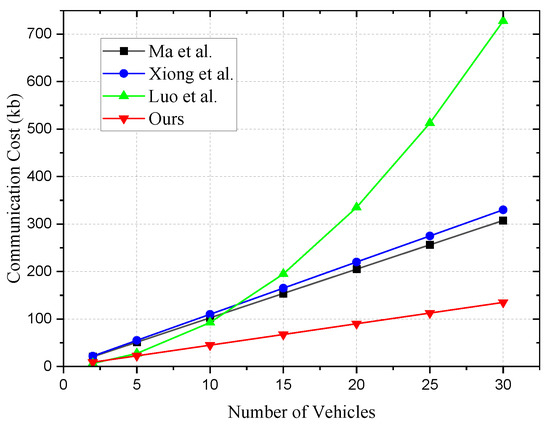
Figure 2.
Transmission cost of vehicles [6,17,21].

Table 6.
Transmission cost of vehicles (kb) [6,17,21].
Table 6.
Transmission cost of vehicles (kb) [6,17,21].
| n | 2 | 5 | 10 | 15 | 20 | 25 | 30 |
|---|---|---|---|---|---|---|---|
| Ma et al. | 20.5 | 51.25 | 102.5 | 153.75 | 205 | 256.25 | 307.5 |
| Xiong et al. | 22 | 55 | 110 | 165 | 220 | 275 | 330 |
| Luo et al. | 6.5 | 27.5 | 92.5 | 195 | 335 | 512.5 | 727.5 |
| Ours | 9 | 22.5 | 45 | 67.5 | 90 | 112.5 | 135 |
In summary, compared to schemes in [6,17,21], our proposed scheme demonstrates lower communication transmission costs.
7.2.2. Computation Efficiency
Next, we analyze computational efficiency. Bilinear pairing computations and hashing to points are particularly time-consuming, while scalar multiplications and hashing to are more efficient operations. Especially, the addition computation in G is highly efficient, which we directly ignore in our analysis. It is essential to highlight that in Xiong et al. [17], the Chinese Remainder Theorem is used, and its construction and solving are also time-consuming computations that we must consider. Schemes [6,17], and our scheme use symmetric encryption for communication, which introduces encryption time considerations during communication. Table 7 and Figure 3 compare the computational costs for vehicles.

Table 7.
Computational cost of vehicles (ms) [6,17,21].
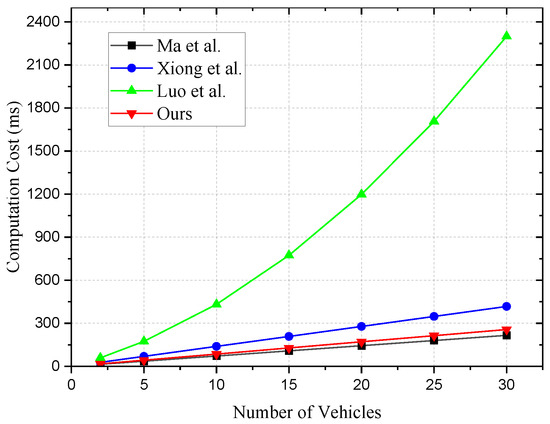
Figure 3.
Computational cost of vehicles [6,17,21].
- In Ma et al. [6], the computation time for the authentication phase is . In our simulation test, the computation time for is 14.42 ms. As the communication quantity n increases from 5 to 30, the time increases from 36.05 ms to 216.3 ms. Hence, the computational time for the [6] scheme appears stable in Table 7.
- In Table 3, we analyzed the computational costs of each scheme with theory. In Xiong et al. [17], the computation costs for registration and authentication are . The computation time for is 27.834 ms. As the number of vehicles n increases from 5 to 30, the time increases from 69.585 ms to 417.51 ms.
- In Luo et al. [21], the computation costs for vehicle registration and authentication processes are . The computation time for is 59.386 ms. This scheme employs a ring encryption method, hence the encryption algorithm’s computational load is substantial. As the number of vehicles n increases from 5 to 30, the time increases from 174.175 ms to 2299.05 ms.
- In our scheme, the computation cost for the authentication phase is . The computation time for is 17.11 ms. As the number of vehicles n increases from 5 to 30, the time increases from 42.775 ms to 256.65 ms.
Overall, in our proposed system, the computational costs for authentication and total communication remain at a lower level compared to all the compared schemes.
8. Conclusions
In this paper, we propose a dynamic privacy-preserving anonymous authentication scheme for condition-matching in fog-cloud-based VANETs. The approach addresses the challenge of computational limitations in OBUs by using general ECC to optimize computational efficiency. By leveraging fog computing, the scheme implements a multi-TA mode to enhance system robustness and meet the real-time requirements of VANETs. Our scheme employs a certificateless approach, eliminating the need for TA-managed certificates and enabling cross-domain group session key agreement. This improves the social aspects of VANETs and expands their potential applications in the era of intelligent vehicles. Integrating VANETs with cloud services enhances scalability and provides essential storage and computational support for diverse VANET-based applications. Our scheme satisfies the security requirements for conditional privacy protection in VANETs through security proofs. Additionally, performance analysis shows that it outperforms similar relevant schemes comprehensively. For future research, we consider designing authenticated key agreement based on lattices to achieve resistance against quantum attacks, and adopting outsourcing computing to reduce the computational requirements for vehicles.
Supplementary Materials
The following supporting information can be downloaded at: https://www.mdpi.com/article/10.3390/s24061773/s1.
Author Contributions
Conceptualization, Y.Z.; methodology, Y.Z.; software, Y.Z. and W.X.; validation, Y.Z., W.X. and R.S.; formal analysis, Y.Z., Y.H. and W.X.; investigation, Y.Z.; resources, X.Z. and Y.H.; data curation, Y.Z.; writing—original draft preparation, Y.Z. and W.X.; writing—review and editing, Y.Z., R.S., Y.H. and X.Z.; visualization, Y.Z.; supervision, Y.Z. and X.Z.; project administration, Y.Z. and X.Z.; funding acquisition, X.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by National Natural Science Foundation of China under Grant No. 61872091; National Defense Basic Research Program of China under Grant JCKY20 19102C001; National Natural Science Foundation of China (No. 62372110); Fujian Provincial Natural Science of Foundation (No. 2023J02008); Key-Area Research and Development Program of Guangdong Province (No. 2020B0101090005); The specific research fund of The Innovation Platform for Academician of Hainan Province (No. YSPTZX202145); Major Special Project for Industrial Science and Technology in Fujian Province (2022HZ022022); Industrial Guiding Project in Fujian (2022H0012); Special Project of Central Finance Guiding Local Development (2022L3003).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Al-shareeda, M.A.; Alazzawi, M.A.; Anbar, M.; Manickam, S.; Al-Ani, A.K. A comprehensive survey on vehicular ad hoc networks (vanets). In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021; pp. 156–160. [Google Scholar]
- Rabieh, K.; Mahmoud, M.M.; Younis, M. Privacy-preserving route reporting scheme for traffic management in VANETs. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7286–7291. [Google Scholar]
- Jeong, H.H.; Shen, Y.C.; Jeong, J.P.; Oh, T.T. A comprehensive survey on vehicular networking for safe and efficient driving in smart transportation: A focus on systems, protocols, and applications. Veh. Commun. 2021, 31, 100349. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Xu, Y.; Liu, L. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs. IEEE Trans. Mob. Comput. 2021, 21, 3280–3297. [Google Scholar] [CrossRef]
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A security and privacy review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An efficient and provably secure authenticated key agreement protocol for fog-based vehicular ad-hoc networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Truong, N.B.; Lee, G.M.; Ghamri-Doudane, Y. Software defined networking-based vehicular adhoc network with fog computing. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 1202–1207. [Google Scholar]
- Chen, L.; Ng, S.L.; Wang, G. Threshold anonymous announcement in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 605–615. [Google Scholar] [CrossRef]
- Guerrero-Ibanez, J.A.; Zeadally, S.; Contreras-Castillo, J. Integration challenges of intelligent transportation systems with connected vehicle, cloud computing, and internet of things technologies. IEEE Wirel. Commun. 2015, 22, 122–128. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. Security and privacy in vehicular ad hoc network and vehicle cloud computing: A survey. Wirel. Commun. Mob. Comput. 2020, 2020, 5129620. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002: International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Kumar, N.; Choo, K.K.R. BCPPA: A blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2020, 22, 7408–7420. [Google Scholar] [CrossRef]
- Yu, S.; Cao, Q.; Wang, C.; Xu, G.; Ma, H.; Zhu, Y.; Peng, Y.; Jia, Y. Efficient ECC-based Conditional Privacy-preserving Aggregation Signature Scheme in V2V. IEEE Trans. Veh. Technol. 2023, 72, 15028–15039. [Google Scholar] [CrossRef]
- Wang, Q.; Li, Y.; Tan, Z.; Fan, N.; Yao, G. Conditional privacy-preserving authentication scheme for V2V communication without pseudonyms. J. Inf. Secur. Appl. 2023, 78, 103616. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Xiong, H.; Chen, J.; Mei, Q.; Zhao, Y. Conditional privacy-preserving authentication protocol with dynamic membership updating for VANETs. IEEE Trans. Dependable Secur. Comput. 2020, 19, 2089–2104. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Xu, Y.; Cheng, J.; Zhong, H. Secure and lightweight conditional privacy-preserving authentication for securing traffic emergency messages in VANETs. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1681–1695. [Google Scholar] [CrossRef]
- Ali, I.; Lawrence, T.; Omala, A.A.; Li, F. An efficient hybrid signcryption scheme with conditional privacy-preservation for heterogeneous vehicular communication in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 11266–11280. [Google Scholar] [CrossRef]
- Xiong, W.; Wang, R.; Wang, Y.; Zhou, F.; Luo, X. CPPA-D: Efficient conditional privacy-preserving authentication scheme with double-insurance in VANETs. IEEE Trans. Veh. Technol. 2021, 70, 3456–3468. [Google Scholar] [CrossRef]
- Luo, M.; Zhou, Y. An efficient conditional privacy-preserving authentication protocol based on generalized ring signcryption for VANETs. IEEE Trans. Veh. Technol. 2022, 71, 10001–10015. [Google Scholar] [CrossRef]
- Cai, Y.; Zhang, H.; Fang, Y. A conditional privacy protection scheme based on ring signcryption for vehicular ad hoc networks. IEEE Internet Things J. 2020, 8, 647–656. [Google Scholar] [CrossRef]
- Du, H.; Wen, Q.; Zhang, S.; Gao, M. An Improved Conditional Privacy Protection Scheme Based on Ring Signcryption for VANETs. IEEE Internet Things J. 2023, 10, 17881–17892. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Qin, Z.; Dong, X.; Ren, K. LPPA: Lightweight privacy-preserving authentication from efficient multi-key secure outsourced computation for location-based services in VANETs. IEEE Trans. Inf. Forensics Secur. 2019, 15, 420–434. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, J. CPP-CLAS: Efficient and conditional privacy-preserving certificateless aggregate signature scheme for VANETs. IEEE Internet Things J. 2021, 9, 10354–10365. [Google Scholar] [CrossRef]
- Ali, I.; Chen, Y.; Ullah, N.; Kumar, R.; He, W. An efficient and provably secure ECC-based conditional privacy-preserving authentication for vehicle-to-vehicle communication in VANETs. IEEE Trans. Veh. Technol. 2021, 70, 1278–1291. [Google Scholar] [CrossRef]
- Zhou, X.; Luo, M.; Vijayakumar, P.; Peng, C.; He, D. Efficient certificateless conditional privacy-preserving authentication for VANETs. IEEE Trans. Veh. Technol. 2022, 71, 7863–7875. [Google Scholar] [CrossRef]
- Goudarzi, S.; Soleymani, S.A.; Anisi, M.H.; Azgomi, M.A.; Movahedi, Z.; Kama, N.; Rusli, H.M.; Khan, M.K. A privacy-preserving authentication scheme based on Elliptic Curve Cryptography and using Quotient Filter in fog-enabled VANET. Ad Hoc Netw. 2022, 128, 102782. [Google Scholar] [CrossRef]
- Zhong, H.; Chen, L.; Cui, J.; Zhang, J.; Bolodurina, I.; Liu, L. Secure and Lightweight Conditional Privacy-Preserving Authentication for Fog-Based Vehicular Ad Hoc Networks. IEEE Internet Things J. 2021, 9, 8485–8497. [Google Scholar] [CrossRef]
- Navdeti, C.P.; Banerjee, I.; Giri, C. Privacy preservation and secure data sharing scheme in fog based vehicular ad-hoc network. J. Inf. Secur. Appl. 2021, 63, 103014. [Google Scholar] [CrossRef]
- Wang, Y.; Ding, Y.; Wu, Q.; Wei, Y.; Qin, B.; Wang, H. Privacy-preserving cloud-based road condition monitoring with source authentication in VANETs. IEEE Trans. Inf. Forensics Secur. 2018, 14, 1779–1790. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Bolodurina, I.; Liu, L. A lightweight and conditional privacy-preserving authenticated key agreement scheme with multi-TA model for fog-based VANETs. IEEE Trans. Dependable Secur. Comput. 2021, 20, 422–436. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, L.; Zhao, Y.; Choo, K.K.R.; Zhang, Y. Privacy-preserving aggregation-authentication scheme for safety warning system in fog-cloud based VANET. IEEE Trans. Inf. Forensics Secur. 2022, 17, 317–331. [Google Scholar] [CrossRef]
- Liu, X.; Huang, H.; Xiao, F.; Ma, Z. A blockchain-based trust management with conditional privacy-preserving announcement scheme for VANETs. IEEE Internet Things J. 2019, 7, 4101–4112. [Google Scholar] [CrossRef]
- Zhou, X.; He, D.; Khan, M.K.; Wu, W.; Choo, K.K.R. An efficient blockchain-based conditional privacy-preserving authentication protocol for vanets. IEEE Trans. Veh. Technol. 2022, 72, 81–92. [Google Scholar] [CrossRef]
- Yang, C.; Jiang, P.; Zhu, L. Accelerating Decentralized and partial-privacy data access for VANET via online/offline functional encryption. IEEE Trans. Veh. Technol. 2022, 71, 8944–8954. [Google Scholar] [CrossRef]
- Lin, C.; Huang, X.; He, D. EBCPA: Efficient blockchain-based conditional privacy-preserving authentication for VANETs. IEEE Trans. Dependable Secur. Comput. 2022, 20, 1818–1832. [Google Scholar] [CrossRef]
- Koblitz, N.; Menezes, A.; Vanstone, S. The state of elliptic curve cryptography. Des. Codes Cryptogr. 2000, 19, 173–193. [Google Scholar] [CrossRef]
- Islam, S.K.H.; Singh, A. Provably secure one-round certificateless authenticated group key agreement protocol for secure communications. Wirel. Pers. Commun. 2015, 85, 879–898. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Wang, H.; Wang, L.; Choo, K.K.R.; Vinel, A. A provably-secure cross-domain handshake scheme with symptoms-matching for mobile healthcare social network; IEEE Trans. Dependable Secur. Comput. 2016, 15, 633–645. [Google Scholar] [CrossRef]
- MIRACL Ltd. Multiprecision Integer and Rational Arithmetic Cryptographic Library. Available online: https://github.com/miracl/MIRACL (accessed on 6 March 2024).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).