ML-Based Detection of DDoS Attacks Using Evolutionary Algorithms Optimization
Abstract
1. Introduction
2. Related Works
3. Materials and Methods
3.1. Datasets and Source
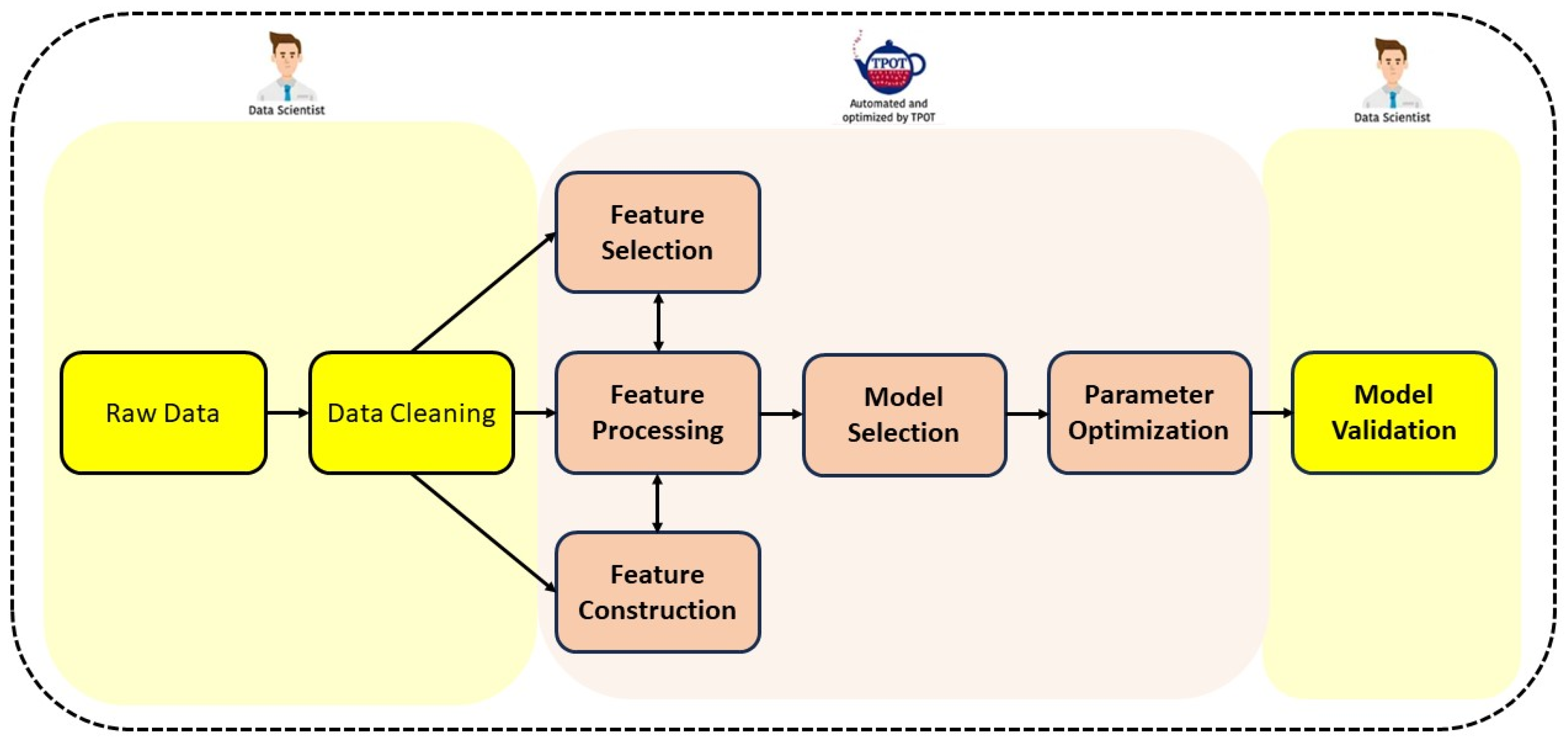
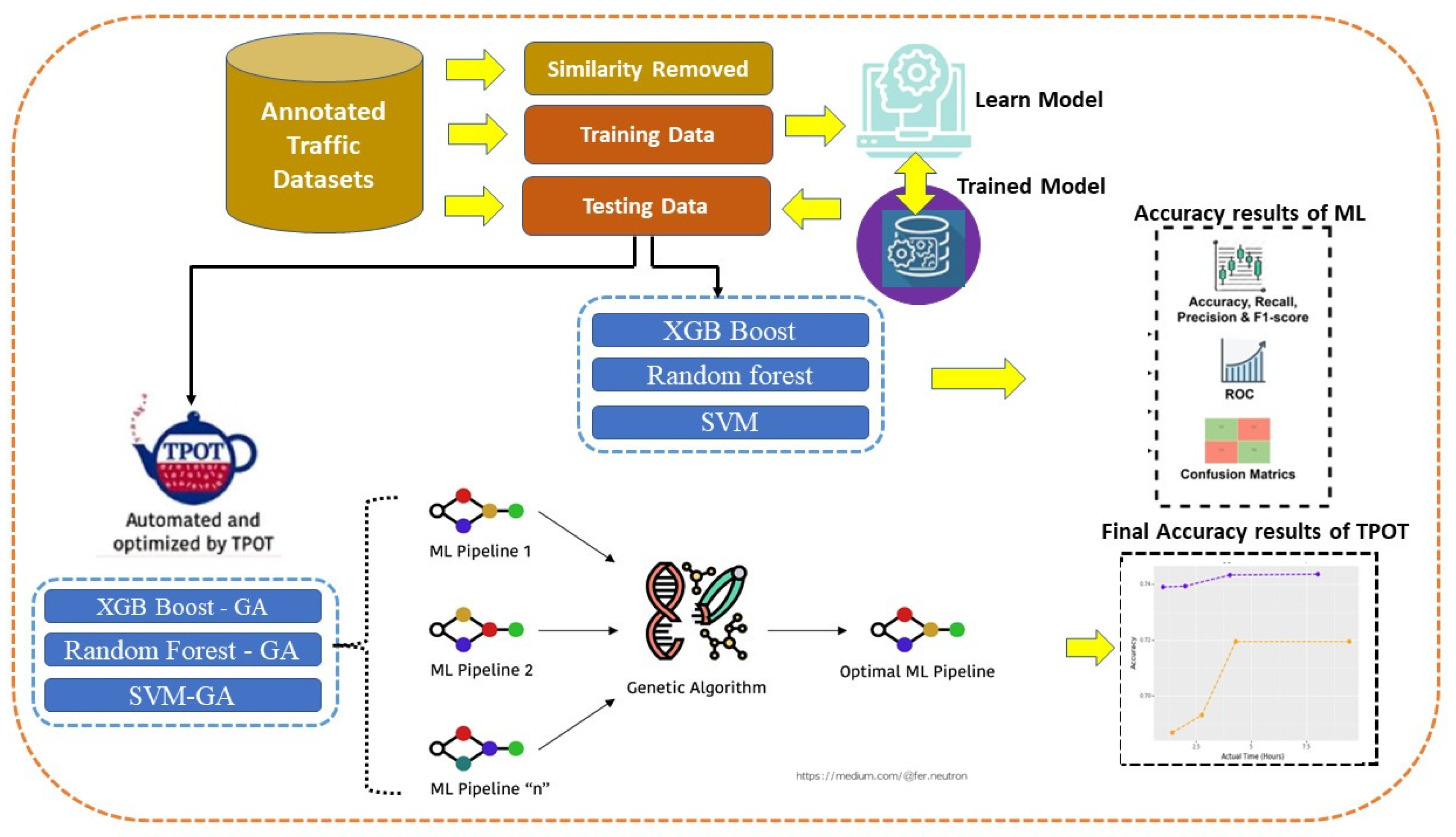
3.2. Proposed Novel Hybrid Method for DDoS Attack Detection Using Tree-Based Pipelines Optimization Tool (TPOT) with Genetics Algorithm
3.3. Three Machine Learning Algorithm Integration with Genetics Algorithms
3.4. The Framework of the Proposed DDoS Diagnosis Procedure
4. Evaluation Metrics
- True Positive, TP: When both the model’s forecast and the actual values in the dataset are positive, we say that a value is a true positive, or TP, meaning the classifier accurately differentiates between good and bad traffic.
- True negative TN: When both the model’s forecast and the actual values in the dataset are negative, we say that the value is a true negative TN, i.e., it is the circumstance where the traffic is accurately categorized as malicious.
- False Positive, FP: False positive is the error category where the model prediction is positive but the actual value in the dataset is negative, i.e., it is the circumstance where the traffic is wrongly classed as innocuous.
- False Negative FN: A false negative is a form of error in which the actual values in the dataset contradict the prediction of the model, i.e., it is the circumstance where the traffic is wrongly categorized as harmful.
- As a performance metric, accuracy may be written as a fraction with the sum of correct answers (positive and negative) in the numerator and the sum of incorrect answers (positive and negative) in the denominator.
5. Results
5.1. Three Machine Learning Classification Results
5.2. SVM
5.3. Random Forest (RF)
5.4. XGBoost
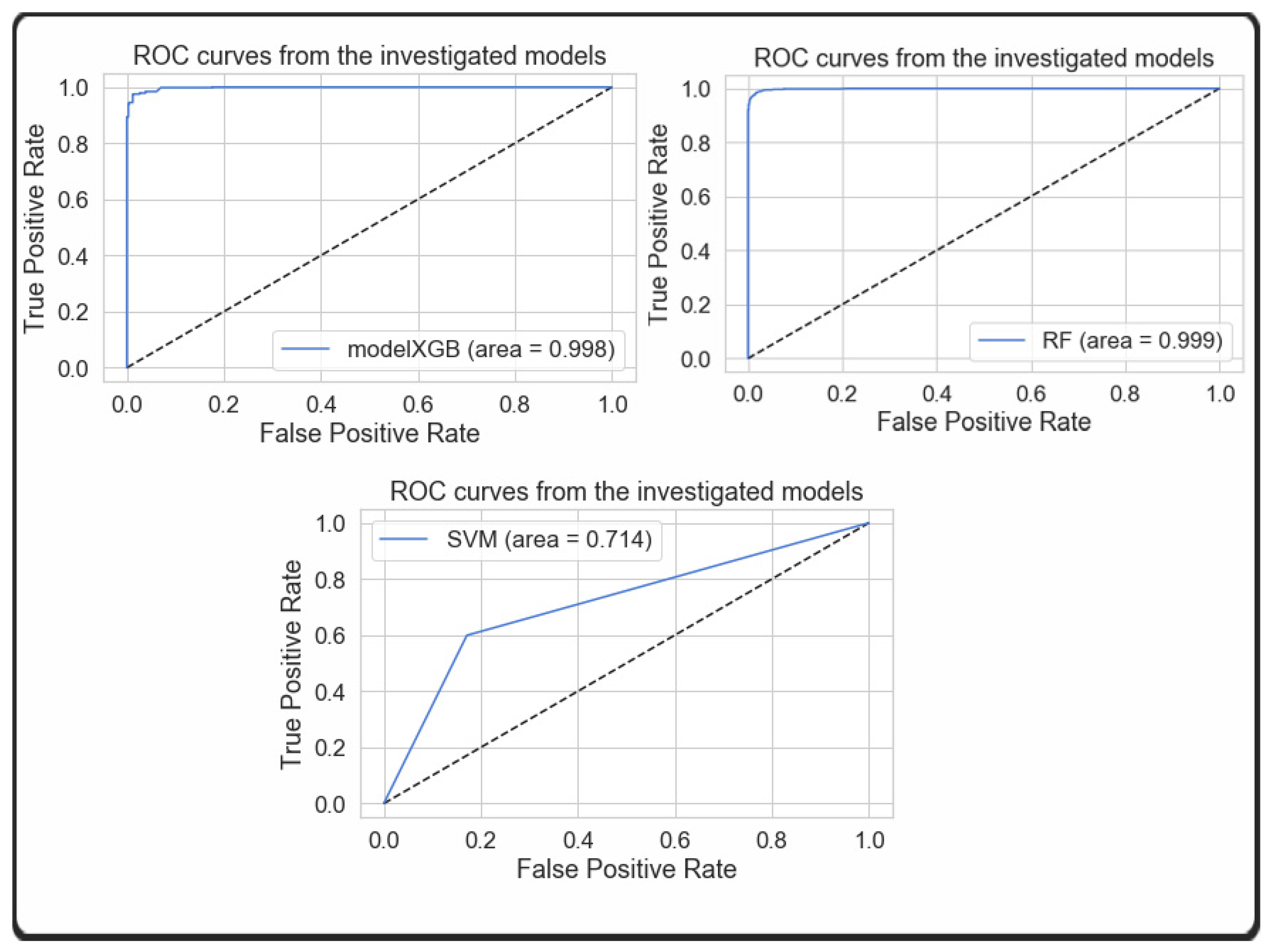
5.5. Receiver Operating Characteristic ROC (AUC) Training Performance
5.6. Performing Accuracy Tests Using a Variety of Methodologies for Fivefold Cross Validation
6. Three Machine Learning Algorithm Optimizations with Genetic Algorithms Results
6.1. RF-GA Optimization with Genetic Algorithms Results
6.2. SVM-GA Optimization with Genetic Algorithms Results
6.3. Proposed Three TPOT-Classifiers with Other Seven GA Optimization Models Results
7. Comparative Analysis with Existing Results
8. Discussion
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Fraser, A.S. Simulation of genetic systems by automatic digital computers. II: Effects of linkage on rates under selection. Austral. J. Biol. Sci. 1957, 10, 492–499. [Google Scholar] [CrossRef]
- Bremermann, H.J. The evolution of intelligence. In The Nervous System as a Model of Its Environment; Technical Report No. 1; Department of Mathematics, University of Washington: Seattle, WA, USA, 1958. [Google Scholar]
- Holland, J.H. Adaptation in Natural and Artificial Systems; University of Michigan Press: Ann Arbor, MI, USA, 1975. [Google Scholar]
- Sharif, D.M.; Beitollahi, H. Detection of Application-layer DDoS Attacks using Machine Learning and Genetic Algorithms. Comput. Secur. 2023, 135, 103511. [Google Scholar] [CrossRef]
- Jazi, H.H.; Gonzalez, H.; Stakhanova, N.; Ghorbani, A.A. Detecting HTTP-based application layer DoS attacks on web servers in the presence of sampling. Comput. Netw. 2017, 121, 25–36. [Google Scholar] [CrossRef]
- Kaur, S.; Kumar, K.; Aggarwal, N.; Singh, G. A comprehensive survey of DDoS defense solutions in SDN: Taxonomy, research challenges, and future directions. Comput. Secur. 2021, 110, 102423. [Google Scholar] [CrossRef]
- Mohammadi, S.; Babagoli, M. A Hybrid Modified Grasshopper Optimization Algorithm and Genetic Algorithm to Detect and Prevent DDoS Attacks. Int. J. Eng. 2021, 34, 811–824. [Google Scholar]
- Chaudhary, A.; Shrimal, G. Intrusion detection system based on genetic algorithm for detection of distribution denial of service attacks in MANETs. In Proceedings of the International Conference on Sustainable Computing in Science, Technology and Management (SUSCOM), Amity University Rajasthan, Jaipur, India, 26–28 February 2019. [Google Scholar]
- Lee, J.H.; Kim, D.S.; Lee, S.M.; Park, J.S. DDoS attacks detection using GA based optimized traffic matrix. In Proceedings of the Fifth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Seoul, Republic of Korea, 30 June–2 July 2011. [Google Scholar]
- Paliwal, S.; Gupta, R. Denial-of-service, probing & remote to user (R2L) attack detection using genetic algorithm. Int. J. Comput. Appl. 2012, 60, 57–62. [Google Scholar]
- Dwivedi, S.; Vardhan, M.; Tripathi, S. Defense against distributed DoS attack detection by using intelligent evolutionary algorithm. Int. J. Comput. Appl. 2022, 44, 219–229. [Google Scholar] [CrossRef]
- Al Bataineh, A.; Manacek, S. MLP-PSO Hybrid Algorithm for Heart Disease Prediction. J. Pers. Med. 2022, 12, 1208. [Google Scholar] [CrossRef] [PubMed]
- Samieinasab, M.; Torabzadeh, S.A.; Behnam, A.; Aghsami, A.; Jolai, F. Meta-Health Stack: A new approach for breast cancer prediction. Healthc. Anal. 2022, 2, 100010. [Google Scholar] [CrossRef]
- Jiao, B.; Guo, Y.; Yang, S.; Pu, J.; Gong, D. Reduced-space Multistream Classification based on Multi-objective Evolutionary Optimization. IEEE Trans. Evol. Comput. 2022, 27, 764–777. [Google Scholar] [CrossRef]
- Hameed, B.Z.; Prerepa, G.; Patil, V.; Shekhar, P.; Zahid Raza, S.; Karimi, H.; Paul, R.; Naik, N.; Modi, S.; Vigneswaran, G.; et al. Engineering and clinical use of artificial intelligence (AI) with machine learning and data science advancements: Radiology leading the way for future. Ther. Adv. Urol. 2021, 13, 17562872211044880. [Google Scholar] [CrossRef]
- Tuli, S.; Ilager, S.; Ramamohanarao, K.; Buyya, R. Dynamic Scheduling for Stochastic Edge-Cloud Computing Environments Using A3C Learning and Residual Recurrent Neural Networks. IEEE Trans. Mob. Comput. 2020, 21, 940–954. [Google Scholar] [CrossRef]
- Hu, C.; Zeng, S.; Li, C. An Uncertainty Measure for Prediction of Non-Gaussian Process Surrogates. Evol. Comput. 2023, 31, 53–71. [Google Scholar] [CrossRef]
- Zelinka, I. A survey on evolutionary algorithms dynamics and its complexity—Mutual relations, past, present and future. Swarm Evol. Comput. 2015, 25, 2–14. [Google Scholar] [CrossRef]
- Casalino, L.; Masseni, F.; Pastrone, D. Robust Design Approaches for Hybrid Rocket Upper Stage. J. Aerosp. Eng. 2019, 32, 04019087. [Google Scholar] [CrossRef]
- Jatoi, W.M.; Korejo, I.A.; Chandio, A.A.; Brohi, K.; Koondhar, Y.M. Meta-heuristic algorithms with immigrant techniques for nurse duty roster in public hospitals in Sindh, Pakistan. Int. J. Comput. Intell. Control 2020, 13, 187–197. [Google Scholar]
- Dong, D.; Ye, Z.; Cao, Y.; Xie, S.; Wang, F.; Ming, W. An improved association rule mining algorithm based on ant lion optimizer algorithm and FP-growth. In Proceedings of the 2019 10th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Metz, France, 18–21 September 2019; Volume 1, pp. 458–463. [Google Scholar]
- Ahmad, A.S.; Hassan, M.Y.; Abdullah, M.P.; Rahman, H.A.; Hussin, F.; Abdullah, H.; Saidur, R. A review on applications of ANN and SVM for building electrical energy consumption forecasting. Renew. Sustain. Energy Rev. 2014, 33, 102–109. [Google Scholar] [CrossRef]
- Madni, S.H.H.; Latiff, M.S.A.; Coulibaly, Y.; Abdulhamid, S.M. Recent advancements in resource allocation techniques for cloud computing environment: A systematic review. Clust. Comput. 2017, 20, 2489–2533. [Google Scholar] [CrossRef]
- Wang, L. Machine availability monitoring and machining process planning towards Cloud manufacturing. CIRP J. Manuf. Sci. Technol. 2013, 6, 263–273. [Google Scholar] [CrossRef]
- Løken, E. Use of multicriteria decision analysis methods for energy planning problems. Renew. Sustain. Energy Rev. 2007, 11, 1584–1595. [Google Scholar] [CrossRef]
- Xia, W.; Wu, Z. An effective hybrid optimization approach for multi-objective flexible job-shop scheduling problems. Comput. Ind. Eng. 2005, 48, 409–425. [Google Scholar] [CrossRef]
- Aslanpour, M.S.; Ghobaei-Arani, M.; Toosi, A.N. Auto-scaling web applications in clouds: A cost-aware approach. J. Netw. Comput. Appl. 2017, 95, 26–41. [Google Scholar] [CrossRef]
- Buyya, R.; Broberg, J.; Goscinski, A.M. (Eds.) Cloud Computing: Principles and Paradigms; John Wiley & Sons: Hoboken, NJ, USA, 2010. [Google Scholar]
- Khalaf, B.A.; Mostafa, S.A.; Mustapha, A.; Mohammed, M.A.; Abduallah, W.M. Comprehensive Review of Artificial Intelligence and Statistical Approaches in Distributed Denial of Service Attack and Defense Methods. IEEE Access 2019, 7, 51691–51713. [Google Scholar] [CrossRef]
- Dixit, P.; Silakari, S. Deep Learning Algorithms for Cybersecurity Applications: A Technological and Status Review. Comput. Sci. Rev. 2021, 39, 100317. [Google Scholar] [CrossRef]
- Basit, A.; Zafar, M.; Liu, X.; Javed, A.R.; Jalil, Z.; Kifayat, K. A comprehensive survey of AI-enabled phishing attacks detection techniques. Telecommun. Syst. 2021, 76, 139–154. [Google Scholar] [CrossRef] [PubMed]
- Mohammed, M.A.; Gunasekaran, S.S.; Mostafa, S.A.; Mustafa, A.; Abd Ghani, M.K. Implementing an agent-based multi-natural language anti-spam model. In Proceedings of the 2018 International Symposium on Agent, Multi-Agent Systems and Robotics (ISAMSR), Putrajaya, Malaysia, 27–28 August 2018; pp. 1–5. [Google Scholar]
- Aburomman, A.A.; Reaz, M.B.I. A survey of intrusion detection systems based on ensemble and hybrid classifiers. Comput. Secur. 2017, 65, 135–152. [Google Scholar] [CrossRef]
- Ahuja, N. SDN Dataset. 2020. Available online: https://data.mendeley.com/datasets/jxpfjc64kr/1 (accessed on 27 September 2020).
- Olson, R.S.; Moore, J.H. TPOT: A tree-based pipeline optimization tool for automating machine learning. In Proceedings of the Workshop on Automatic Machine Learning, New York, NY, USA, 24 June 2016; pp. 66–74. [Google Scholar]
- Santos-Neto, M.J.; Bordim, J.L.; Alchieri, E.A.P.; Ishikawa, E. DDoS attack detection in SDN: Enhancing entropy-based detection with machine learning. Concurr. Comput. Pract. Exp. 2024, 23, e8021. [Google Scholar] [CrossRef]
- Kumar, P.A.R.; Selvakumar, S. Detection of distributed denial of service attacks using an ensemble of adaptive and hybrid neuro-fuzzy systems. Comput. Commun. 2013, 36, 303–319. [Google Scholar] [CrossRef]
- Da Silva, A.S.; Wickboldt, J.A.; Granville, L.Z.; Schaeffer-Filho, A. Atlantic: A framework for anomaly traffi detection, classifiation, and mitigation in sdn. In Proceedings of the NOMS IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 27–35. [Google Scholar]
- Perez-Diaz, J.A.; Valdovinos, I.A.; Choo, K.-K.R.; Zhu, D. A Flexible SDN-Based Architecture for Identifying and Mitigating Low-Rate DDoS Attacks Using Machine Learning. IEEE Access 2020, 8, 155859–155872. [Google Scholar] [CrossRef]
- Ye, J.; Cheng, X.; Zhu, J.; Feng, L.; Song, L. A DDoS attack detection method based on SVM in software defined network. Secur. Commun. Netw. 2018, 2018, 9804061. [Google Scholar] [CrossRef]
- Ko, I.; Chambers, D.; Barrett, E. Self-supervised network traffic management for DDoS mitigation within the ISP domain. Future Gener. Comput. Syst. 2020, 112, 524–533. [Google Scholar] [CrossRef]
- Han, B.; Yang, X.; Sun, Z.; Huang, J.; Su, J. OverWatch: A Cross-Plane DDoS Attack Defense Framework with Collaborative Intelligence in SDN. Secur. Commun. Netw. 2018, 2018, 9649643. [Google Scholar] [CrossRef]
- Oo, M.M.; Kamolphiwong, S.; Kamolphiwong, T.; Vasupongayya, S. Advanced Support Vector Machine- (ASVM-) Based Detection for Distributed Denial of Service (DDoS) Attack on Software Defined Networking (SDN). J. Comput. Netw. Commun. 2019, 2019, 8012568. [Google Scholar]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D.; Kumar, N. Automated DDOS attack detection in software defined networking. J. Netw. Comput. Appl. 2021, 187, 103108. [Google Scholar] [CrossRef]
- Ahuja, N.; Mukhopadhyay, D.; Singal, G. DDoS attack traffic classification in SDN using deep learning. Pers. Ubiquitous Comput. 2024, 2024, 1–13. [Google Scholar] [CrossRef]

| Traffic Class | Benign | Malicious |
|---|---|---|
| ICMP | 24,957 | 16,364 |
| TCP | 18,897 | 10,539 |
| UDP | 22,772 | 10,816 |
| Algorithms | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| SVM | 72.00% | 71.99% | 83.99% | 76.99% |
| Random forest | 98.00% | 98.85% | 99.45% | 98.01% |
| XGBoost | 98.08% | 99.78% | 99.89% | 98.99% |
| Classifiers | Precision | Recall | F1-Score | Accuracy |
|---|---|---|---|---|
| Gradient Boost | 1.00 | 1.00 | 1.00 | 99.99% |
| 1.00 | 1.00 | 1.00 |
| Classifiers | GA Generations | Best Internal CV Score | GA Optimization Best Accuracy Score |
|---|---|---|---|
| Gradient Boost | Generation 1 | Current best internal CV score: | 99.99% |
| Generation 2 | Current best internal CV score: | 1.0 | |
| Generation 3 | Current best internal CV score: | 1.0 | |
| Generation 4 | Current best internal CV score: | 1.0 | |
| Generation 5 | Current best internal CV score: | 1.0 | |
| Best pipeline test accuracy: | 1.000 | ||
| Accuracy: | 99.99% |
| Classifiers | MAE | MSE | R2 |
|---|---|---|---|
| Gradient Boost | 4.7917 | 4.7917 | 0.9997 |
| ML-GA Classifiers | 5 Iterations/5-Fold CV | Best Pipeline Test Accuracy Score |
|---|---|---|
| Extra Trees Classifier | Internal cv score | 0.8123 |
| K-Neighbors Classifier | Internal cv score | 0.8158 |
| Bernoulli NB | Internal cv score | 0.7322 |
| GBoosting Classifier | Internal cv score | 0.9910 |
| SGD Classifier | Internal cv score | 0.5283 |
| Multinomial NB | Internal cv score | 0.5307 |
| Logistic Regression | Internal cv score | 0.7151 |
| SVM-GA Optimization | Internal cv score | 0.9940 |
| Best pipeline test accuracy | Internal cv score | 0.9960 |
| RF-GA Optimization | Internal cv score | 0.9988 |
| Best pipeline test accuracy | Internal cv score | 0.9950 |
| Proposed XGB-GA | Accuracy: | 0.9999 |
| Best pipeline test accuracy: | 1.000 |
| Classifiers | GA Generations | Best internal CV Score | Best Pipeline Test Accuracy Score |
|---|---|---|---|
| RF-GA | Generation 1 | Current best internal CV score: | 0.9981 |
| Generation 2 | Current best internal CV score: | 0.9988 | |
| Generation 3 | Current best internal CV score: | 0.9983 | |
| Generation 4 | Current best internal CV score: | 0.9988 | |
| Generation 5 | Current best internal CV score: | 0.9988 | |
| Best pipeline test accuracy: | 0.9988 | ||
| Classifiers | GA Generations | Best Internal CV Score | Best Pipeline Test Accuracy Score |
|---|---|---|---|
| SVM-GA | Generation 1 | Current Pareto front scores: | 0.9739 |
| Generation 2 | Current Pareto front scores: | 0.9835 | |
| SVM-GA | Generation 3 | Current Pareto front scores: | 0.9925 |
| Generation 4 | Current Pareto front scores: | 0.9925 | |
| Generation 5 | Current Pareto front scores: | 0.9940 | |
| Best pipeline test accuracy: | 0.9960 | ||
| S. No | Authors | Testing Accuracy |
|---|---|---|
| 1 | Meti et al., 2017 [37] | 80% |
| 2 | Da Silva et al., 2016 [38] | 88.7% |
| 3 | Perez-Díaz et al. [39] | 95% |
| 4 | Ye et al., 2018 [40] | 95.24% |
| 5 | Ko et al. [41] | 96% |
| 6 | Han et al., 2018 [42] | 96% |
| 7 | Myint Oo et al., 2019 [43] | 97% |
| 8 | Auhoja, 2021 [44] | 98.8% |
| 9 | Proposed XGB-GA Optimization | 99.00% |
| 10 | Proposed TPOT Best pipeline test accuracy: | 1.000% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Talpur, F.; Korejo, I.A.; Chandio, A.A.; Ghulam, A.; Talpur, M.S.H. ML-Based Detection of DDoS Attacks Using Evolutionary Algorithms Optimization. Sensors 2024, 24, 1672. https://doi.org/10.3390/s24051672
Talpur F, Korejo IA, Chandio AA, Ghulam A, Talpur MSH. ML-Based Detection of DDoS Attacks Using Evolutionary Algorithms Optimization. Sensors. 2024; 24(5):1672. https://doi.org/10.3390/s24051672
Chicago/Turabian StyleTalpur, Fauzia, Imtiaz Ali Korejo, Aftab Ahmed Chandio, Ali Ghulam, and Mir. Sajjad Hussain Talpur. 2024. "ML-Based Detection of DDoS Attacks Using Evolutionary Algorithms Optimization" Sensors 24, no. 5: 1672. https://doi.org/10.3390/s24051672
APA StyleTalpur, F., Korejo, I. A., Chandio, A. A., Ghulam, A., & Talpur, M. S. H. (2024). ML-Based Detection of DDoS Attacks Using Evolutionary Algorithms Optimization. Sensors, 24(5), 1672. https://doi.org/10.3390/s24051672






