B-SAFE: Blockchain-Enabled Security Architecture for Connected Vehicle Fog Environment †
Abstract
1. Introduction
- Firstly, blockchain security and vehicular fog networking are introduced as preliminaries of the security framework.
- Secondly, a three-layered architecture of B-SAFE is presented, focusing on vehicular communication, blockchain operations at fog nodes, and the cloud as a trust and reward management for vehicles.
- Thirdly, details of the phase-wise blockchain implementation at the fog nodes are presented, along with a flowchart and algorithm.
- Finally, the performance of the evaluation of the proposed framework B-SAFE attests to the benefits of its use in terms of trust factor, reward points, and threshold calculation.
2. Related Work
3. Preliminary and Proposed Solution
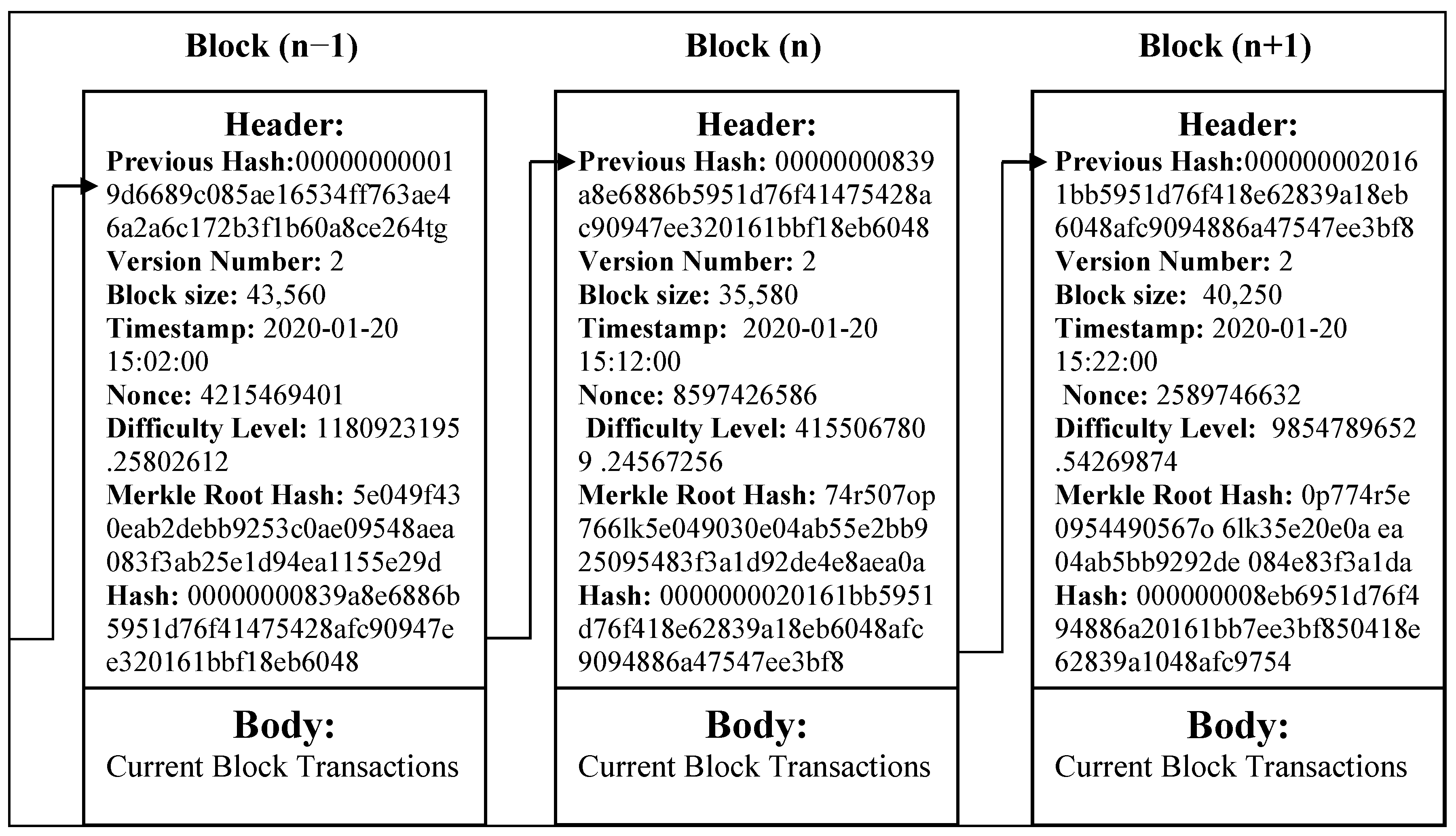
3.1. Block Data Elements—Header and Body
3.2. Features of Blockchain
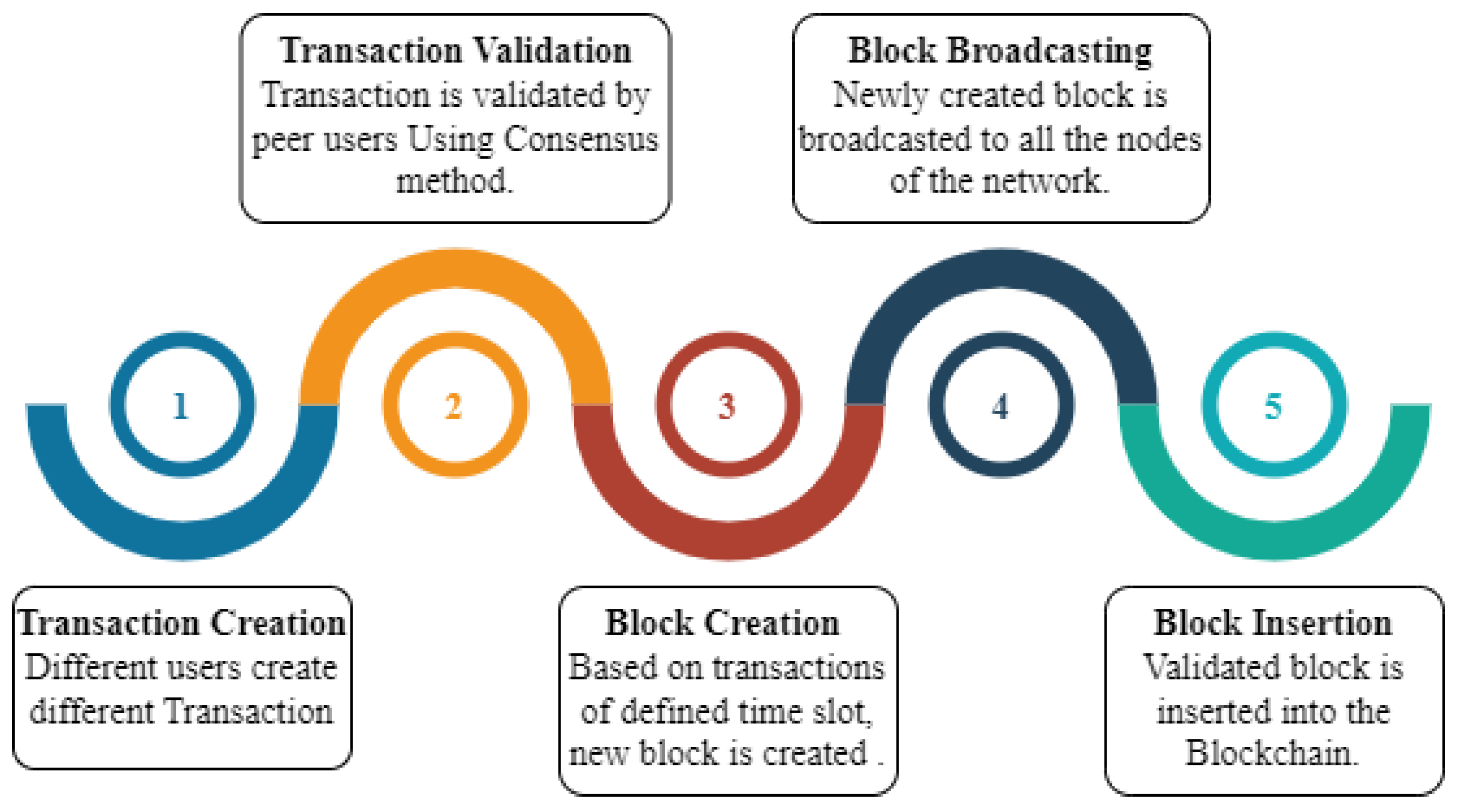
3.3. Operations in Blockchain
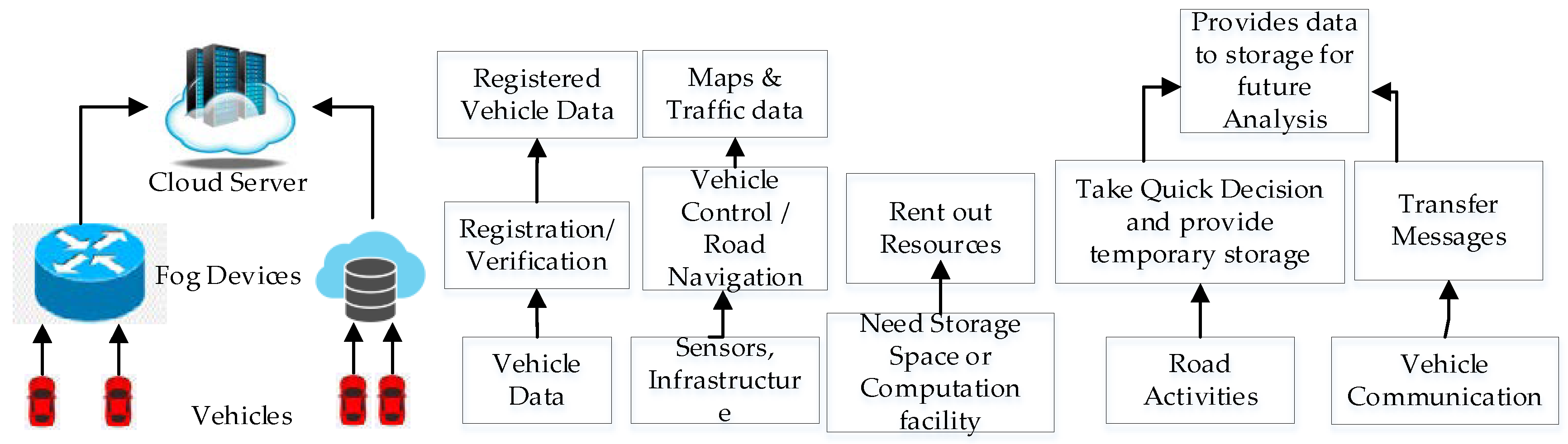
3.4. Vehicular Fog Networking
3.5. Proposed Solution
- Firstly, in order to guard against data manipulation and preserve data integrity, this system integrates a blockchain-based data storage approach. The transmission of vehicle data leads to the creation of a blockchain transaction, which is subsequently included in a block. The utilization of the transaction address facilitates the authentication of the vehicle’s identity, hence obviating the necessity for a signature and enhancing the dependability of the network. Furthermore, this serves to protect Vehicular Ad Hoc Networks (VANETs) from potential privacy breaches and authentication threats.
- Secondly, an additional challenge within VANET lies in the reliance on vehicles to blindly accept reported events without verifying their accuracy. To enhance the precision of shared data pertaining to incidents, the system incorporates nearby vehicles in the vicinity of the event to assess the validity of the provided event data. By involving proximate vehicles in making judgments regarding event correctness, this approach aims to bolster the reliability of information shared among vehicles in the network.
- Thirdly, VANET is integrated with fog computing to extend cloud-like features to the network edge for enhanced speed and efficiency, whereas traditional cloud systems suffer from drawbacks such as latency and dependency on centralized servers.
- Fourthly, a vehicle may lack the desire to take an active role in the confirmation of an incident that occurred earlier on the road. Thus, to motivate vehicles to be involved in giving information regarding event occurrence or giving judgment for validating that event data, incentives are provided to these vehicles in the form of reward points.
- Lastly, the VANET system does not even maintain the details of each vehicle, nor does it assess its reliability. In the proposed architecture, the trustworthiness of each vehicle is also evaluated and stored in the system, which analyzes the required number of vehicles for judgment. This factor is crucial for computational complexity and response time.
4. Blockchain-Enabled Security for Vehicular Fog Network
4.1. Overview of B-SAFE
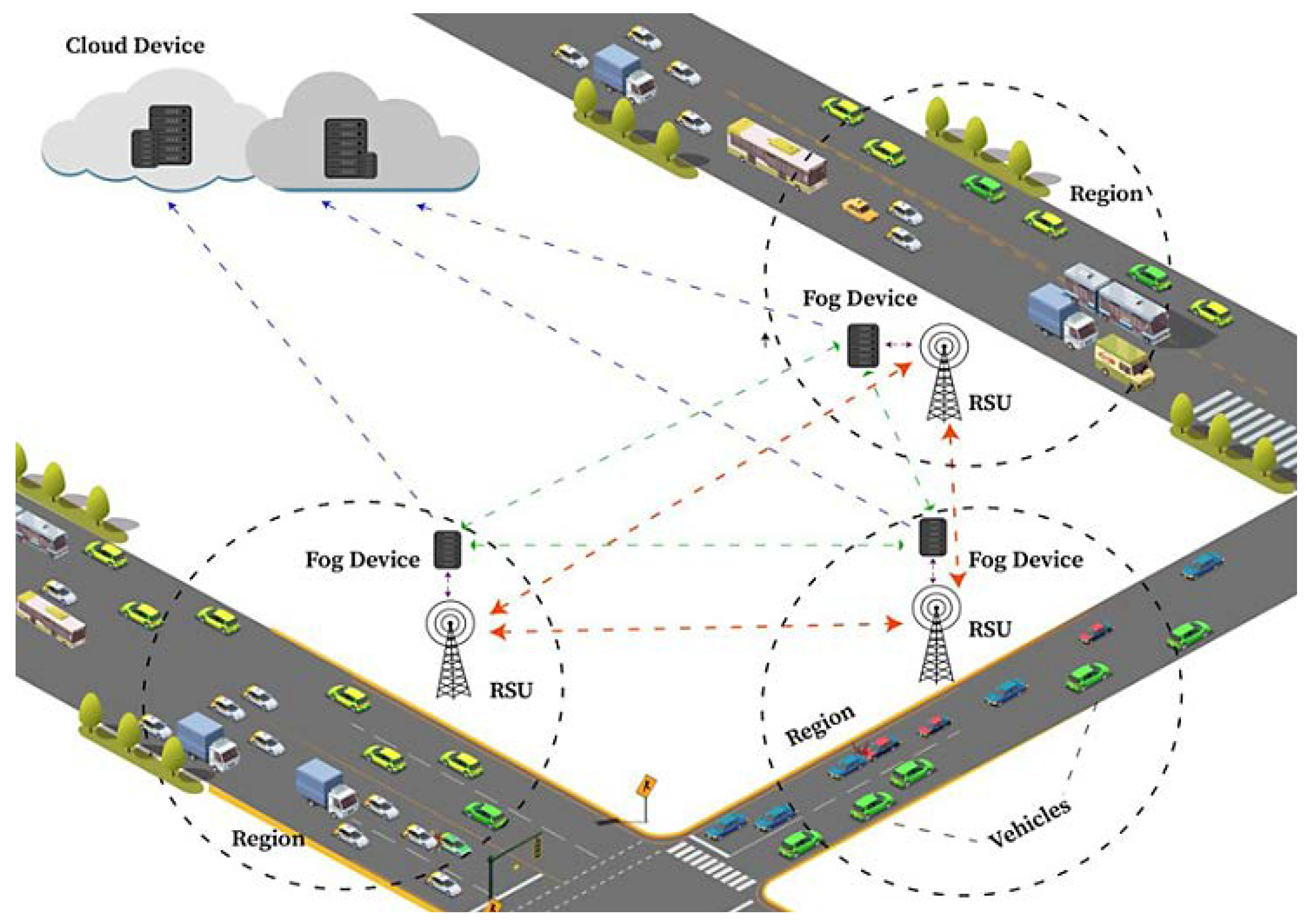
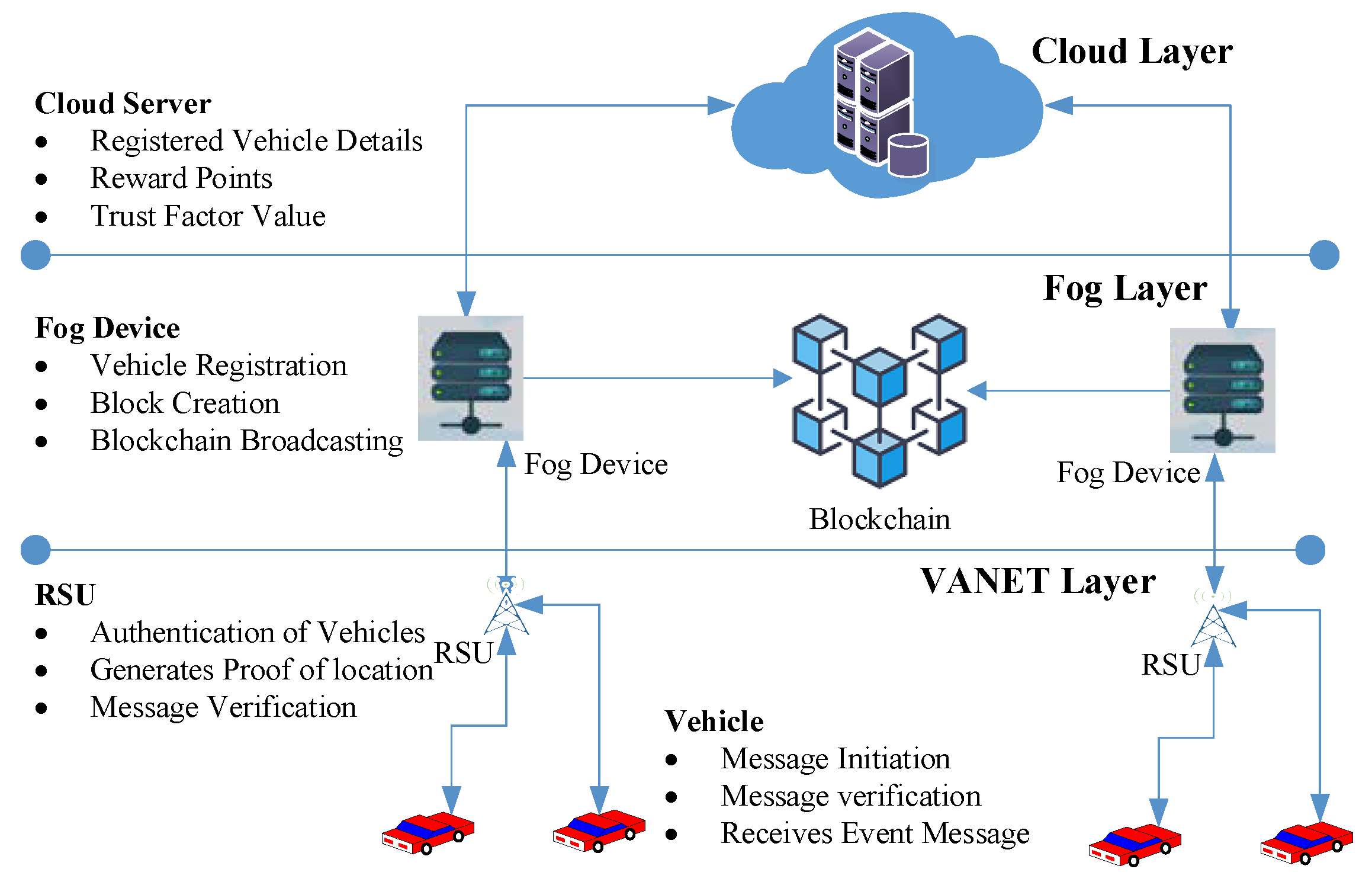
4.2. Network Architecture of B-SAFE
4.2.1. VANET Layer
4.2.2. Fog Layer
4.2.3. Cloud Layer
4.3. Phases of B-SAFE
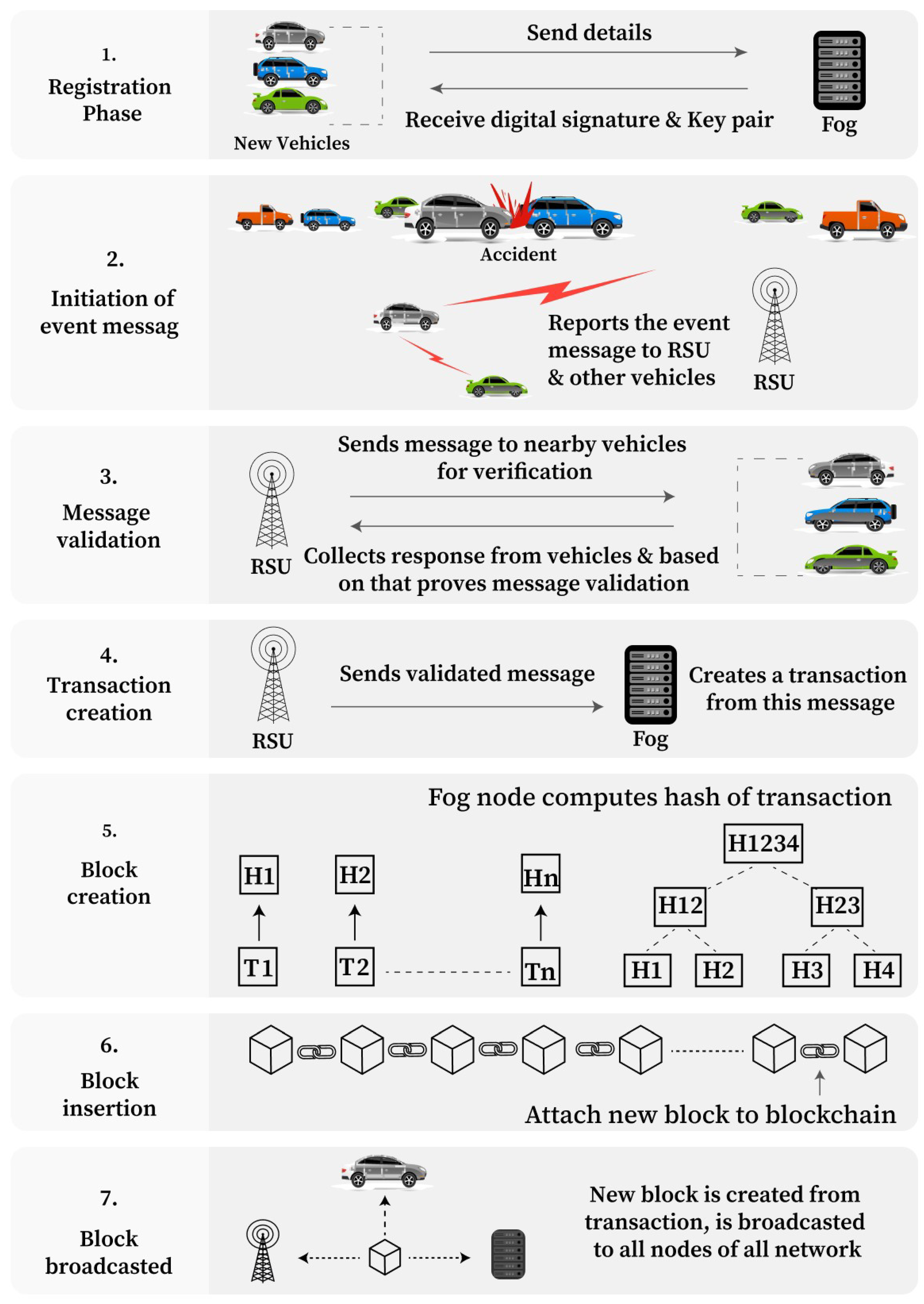
4.3.1. Registration Phase
4.3.2. Initiation of the Event Message
4.3.3. Message Validation
4.3.4. Transaction Creation
4.3.5. Block Creation
4.3.6. Block Insertion
4.3.7. Block Broadcasting
4.3.8. Algorithm and Its Description for B-SAFE
| Algorithm 1: Message Verification Process |
| Input: Lv, Le Output: LC(IV), Rp, Tf Process:
|
5. Performance Evaluation
5.1. Reward Points
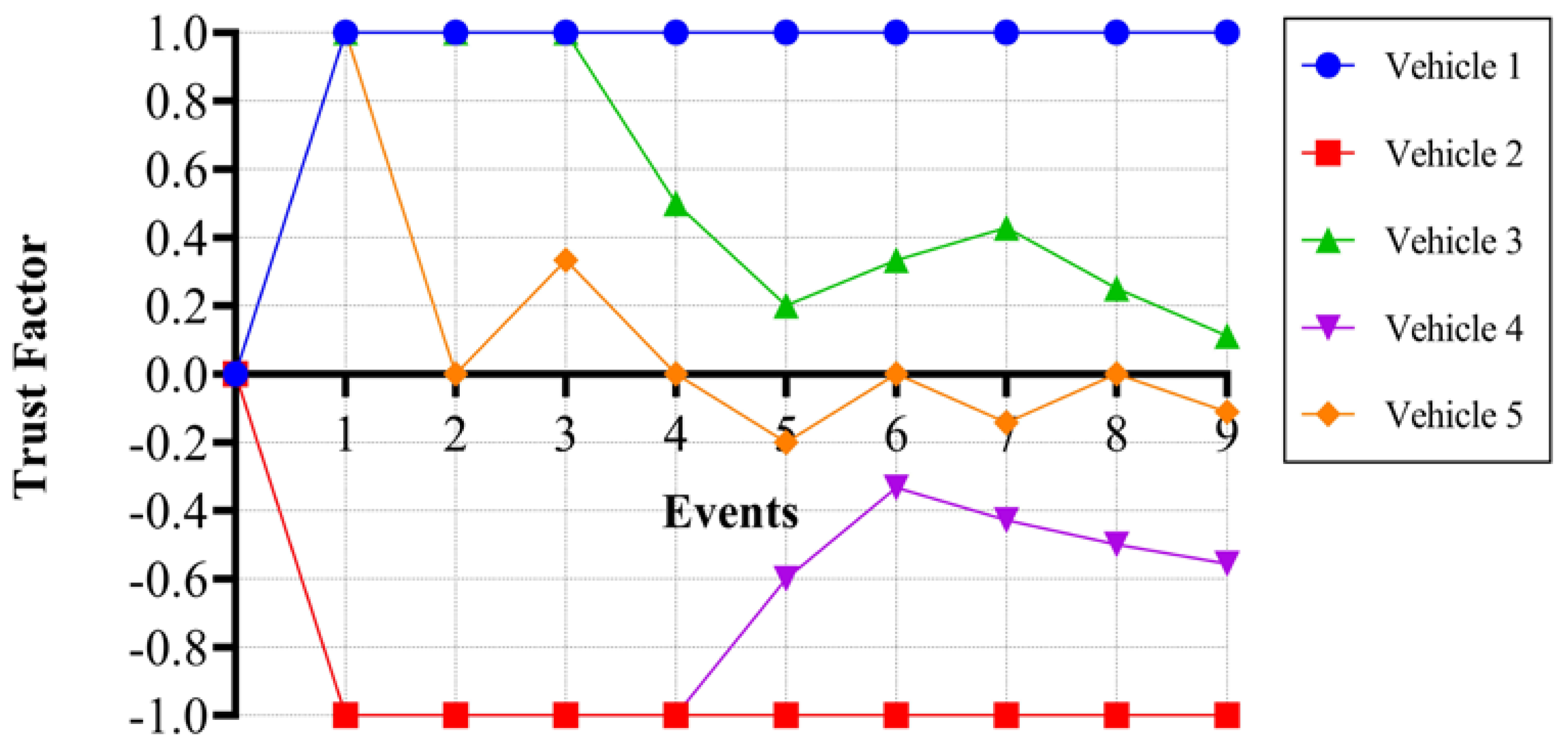
5.2. Trust Factor
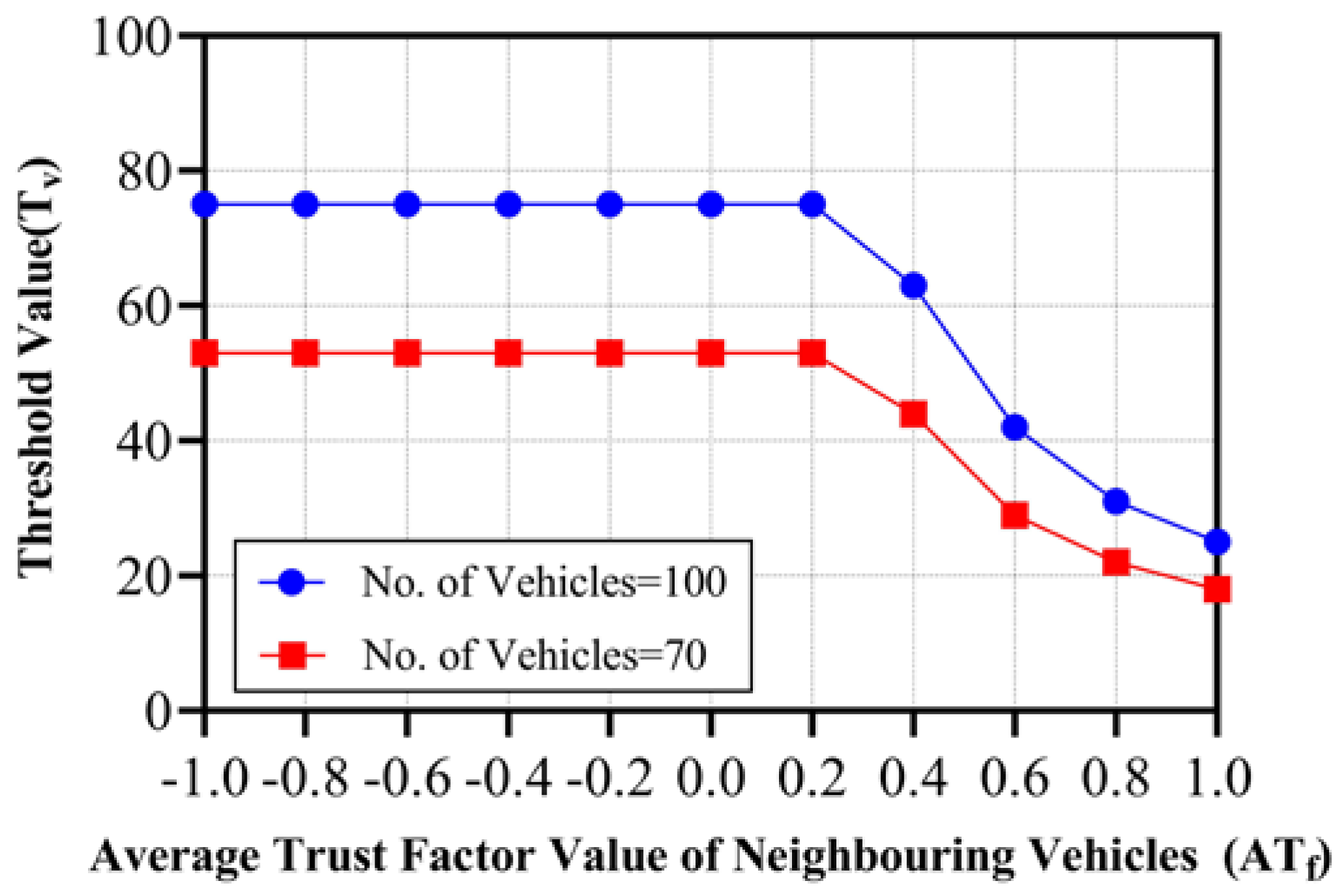
5.3. Information Gain
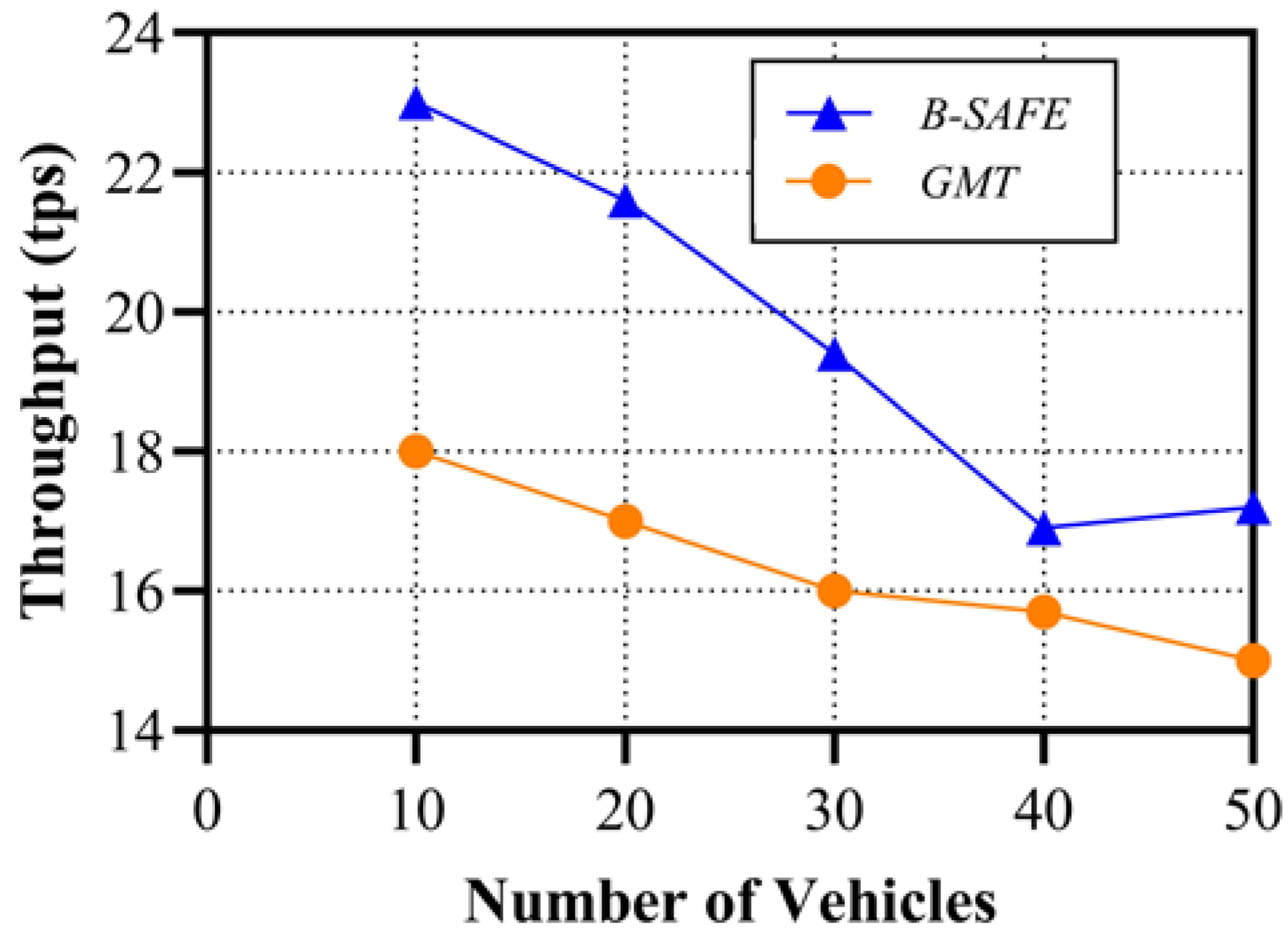
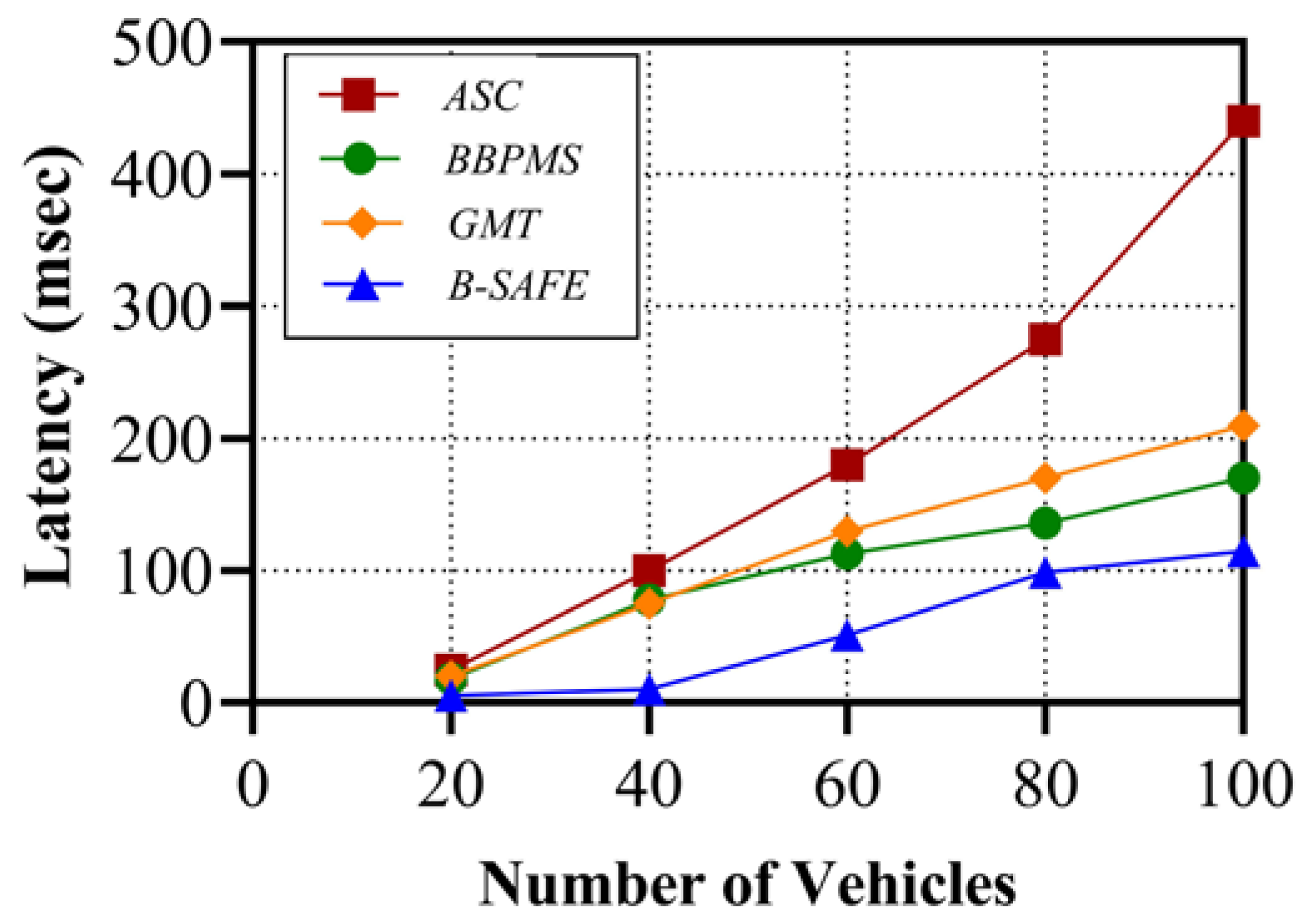
6. Comparative Result Analysis with Implementation Details
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kaiwartya, O.; Abdullah, A.; Cao, Y.; Altameem Prasad, M.; Lin, C.T.; Liu, X. Internet of vehicles: Motivation, layered architecture, network model, challenges, and future aspects. IEEE Access 2016, 4, 5356–5373. [Google Scholar] [CrossRef]
- The IDC Report, Worldwide Connected Vehicle Forecast, 2019–2023 (IDC #US45050319). Available online: https://www.idc.com/getdoc.jsp?containerId=prUS45092819 (accessed on 12 December 2023).
- Siegel, J.E.; Erb, D.C.; Sarma, S.E. A survey of the connected vehicle landscape—Architectures, enabling technologies, applications, and development areas. IEEE Trans. Intell. Transp. Syst. 2017, 19, 2391–2406. [Google Scholar] [CrossRef]
- Ahmed, S.H.; Ben-Othman, J.; Lloret, J.; Khokhar, A.; Beyah, R.; Sanchez, A.; Guibene, W. Emerging Technologies for Connected and Smart Vehicles. IEEE Commun. Mag. 2018, 56, 20–21. [Google Scholar] [CrossRef]
- Miller, C. Lessons learned from hacking a car. IEEE Des. Test 2019, 36, 7–9. [Google Scholar] [CrossRef]
- Eiza, M.H.; Ni, Q. Driving with sharks: Rethinking connected vehicles with vehicle cybersecurity. IEEE Veh. Technol. Mag. 2017, 12, 45–51. [Google Scholar] [CrossRef]
- Gilad, Y.; Herzberg, A.; Shulman, H. Off-path hacking: The illusion of challenge-response authentication. IEEE Secur. Priv. 2013, 12, 68–77. [Google Scholar] [CrossRef]
- Berghel, H. Vehicle telematics: The good, bad and ugly. Computer 2019, 52, 66–70. [Google Scholar] [CrossRef]
- Luo, Q.; Liu, J. Wireless telematics systems in emerging intelligent and connected vehicles: Threats and solutions. IEEE Wirel. Commun. 2018, 25, 113–119. [Google Scholar] [CrossRef]
- Biswas, S.; Mišić, J. A cross-layer approach to privacy-preserving authentication in WAVE-enabled VANETs. IEEE Trans. Veh. Technol. 2013, 62, 2182–2192. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M. Toward a secure batch verification with group testing for VANET. Wirel. Netw. 2013, 19, 1441–1449. [Google Scholar] [CrossRef]
- Liu, J.K.; Yuen, T.H.; Au, M.H.; Susilo, W. Improvements on an authentication scheme for vehicular sensor networks. Expert Syst. Appl. 2014, 41, 2559–2564. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Sheet, D.K.; Kaiwartya, O.; Abdullah, A.H.; Cao, Y.; Hassan, A.N.; Kumar, S. Location information verification using transferable belief model for geographic routing in vehicular ad hoc networks. IET Intell. Transp. Syst. 2016, 11, 53–60. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Trustworthy event-information dissemination in vehicular ad hoc networks. Mob. Inf. Syst. 2017, 2017, 9050787. [Google Scholar] [CrossRef]
- Chuprov, S.; Viksnin, I.; Kim, I.; Marinenkov, E.; Usova, M.; Lazarev, E.; Melnikov, T.; Zakoldaev, D. Reputation and Trust Approach for Security and Safety Assurance in Intersection Management System. Energies 2019, 12, 4527. [Google Scholar] [CrossRef]
- Raw, R.S. The Amalgamation of Blockchain with Smart and Connected Vehicles: Requirements, Attacks, and Possible Solution. In Proceedings of the 2020 2nd International Conference on Advances in Computing, Communication Control and Networking, ICACCCN 2020, Greater Noida, India, 18–19 December 2020; pp. 896–902. [Google Scholar] [CrossRef]
- Iqbal, R.; Butt, T.A.; Afzaal, M.; Salah, K. Trust management in social Internet of vehicles: Factors, challenges, blockchain, and fog solutions. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719825820. [Google Scholar] [CrossRef]
- Sookhak, M.; Yu, F.R.; He, Y.; Talebian, H.; Safa, N.S.; Zhao, N.; Khan, M.K.; Kumar, N. Fog vehicular computing: Augmentation of fog computing using vehicular cloud computing. IEEE Veh. Technol. Mag. 2017, 12, 55–64. [Google Scholar] [CrossRef]
- Huang, C.; Lu, R.; Choo, K.K.R. Vehicular fog computing: Architecture, use case, and security and forensic challenges. IEEE Commun. Mag. 2017, 55, 105–111. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, A.; Lin, X.; Shen, X.S. Security, Privacy, and Fairness in Fog-Based Vehicular Crowdsensing. IEEE Commun. Mag. 2017, 55, 146–152. [Google Scholar] [CrossRef]
- Ali, N.A.; Taha, A.E.M.; Barka, E. Integrating Blockchain and IoT/ITS for Safer Roads. IEEE Netw. 2020, 34, 32–37. [Google Scholar] [CrossRef]
- Zhang, L.; Luo, M.; Li, J.; Au, M.H.; Choo, K.K.R.; Chen, T.; Tian, S. Blockchain based secure data sharing system for Internet of vehicles: A position paper. Veh. Commun. 2019, 16, 85–93. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Misic, J.; Misic, V.B.; Li, L. BLA: Blockchain-assisted lightweight anonymous authentication for distributed vehicular fog services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.P.; Nam, S.Y. A new type of blockchain for secure message exchange in VANET. Digit. Commun. Netw. 2019, 6, 177–186. [Google Scholar] [CrossRef]
- Li, L.; Liu, J.; Cheng, L.; Qiu, S.; Wang, W.; Zhang, X.; Zhang, Z. CreditCoin: A Privacy-Preserving Blockchain-Based Incentive Announcement Network for Communications of Smart Vehicles. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2204–2220. [Google Scholar] [CrossRef]
- Malik, N.; Nanda, P.; He, X.; Liu, R.P. Vehicular networks with security and trust management solutions: Proposed secured message exchange via blockchain technology. Wirel. Netw. 2020, 26, 4207–4226. [Google Scholar] [CrossRef]
- Lu, Z.; Liu, W.; Wang, Q.; Qu, G.; Liu, Z. A privacy-preserving trust model based on blockchain for VANETs. IEEE Access 2018, 6, 45655–45664. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2020, 6, 4660–4670. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Goudarzi, S.; Anisi, M.H.; Kama, N.; Adli Ismail, S.; Azmi, A.; Zareei, M.; Hanan Abdullah, A. A trust model using edge nodes and a cuckoo filter for securing VANET under the NLoS condition. Symmetry 2021, 12, 609. [Google Scholar] [CrossRef]
- Ahmed, A.; Abdullah, S.; Iftikhar, S.; Ahmad, I.; Ajmal, S.; Hussain, Q. A Novel Blockchain Based Secured and QoS Aware IoT Vehicular Network in Edge Cloud Computing. IEEE Access 2022, 10, 77707–77722. [Google Scholar] [CrossRef]
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain—A Disruptive Technology. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Lu, Y. Blockchain and the related issues: A review of current research topics. J. Manag. Anal. 2018, 5, 231–255. [Google Scholar] [CrossRef]
- Niranjanamurthy, M.; Nithya, B.N.; Jagannatha, S. Analysis of Blockchain technology: Pros, cons and SWOT. Clust. Comput. 2019, 22, 14743–14757. [Google Scholar] [CrossRef]
- Bernabe, J.B.; Canovas, J.L.; Hernandez-Ramos, J.L.; Moreno, R.T.; Skarmeta, A. Privacy-Preserving Solutions for Blockchain: Review and Challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Dinh, T.N.; Thai, M.T. Ai and blockchain: A disruptive integration. Computer 2018, 51, 48–53. [Google Scholar] [CrossRef]
- Gaba, P.; Raw, R.S.; Mohammed, M.A.; Nedoma, J.; Martinek, R. Impact of Block Data Components on the Performance of Blockchain-Based VANET Implemented on Hyperledger Fabric. IEEE Access 2022, 10, 71003–71018. [Google Scholar] [CrossRef]
- Knirsch, F.; Unterweger, A.; Engel, D. Implementing a blockchain from scratch: Why, how, and what we learned. EURASIP J. Inf. Secur. 2019, 2019, 2. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. 2019, 52, 51. [Google Scholar] [CrossRef]
- Kui, X.; Sun, Y.; Zhang, S.; Li, Y. Characterizing the Capability of Vehicular Fog Computing in Large-scale Urban Environment. Mob. Netw. Appl. 2018, 23, 1050–1067. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Wang, L. Offloading in Internet of Vehicles: A Fog-Enabled Real-Time Traffic Management System. IEEE Trans. Ind. Inform. 2018, 14, 4568–4578. [Google Scholar] [CrossRef]
- Gaba, P.; Raw, R.S. Vehicular Cloud and Fog Computing Architecture, Applications, Services, and Challenges. In IoT and Cloud Computing Advancements in Vehicular Ad-Hoc Networks; Rao, R.S., Jain, V., Kaiwartya, O., Nanhay, S., Eds.; IGI Global: Hershey, PA, USA, 2020; pp. 268–296. [Google Scholar]
- Aljeri, N.; Boukerche, A. Fog-enabled vehicular networks: A new challenge for mobility management. Internet Technol. Lett. 2020, 2019, e141. [Google Scholar] [CrossRef]
- Gaba, P.; Raw, R.S. BIVFN: Blockchain-Enabled Intelligent Vehicular Fog Networks. In Intelligent Computing and Applications: Proceedings of ICDIC 2020; Springer Nature Singapore: Singapore, 2022; pp. 19–27. [Google Scholar]
- Gaba, P.; Raw, R.S. B-VANET: A blockchain-based vehicular ad-hoc network for data validation. Peer-to-Peer Netw. Appl. 2022, 15, 2650–2669. [Google Scholar] [CrossRef]
- Kaiwartya, O.; Cao, Y.; Lloret, J.; Kumar, S.; Aslam, N.; Kharel, R.; Abdullah, A.H.; Shah, R.R. Geometry-based localization for GPS outage in vehicular cyber physical systems. IEEE Trans. Veh. Technol. 2018, 67, 3800–3812. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the 13th EuroSys Conference, EuroSys 2018, Porto, Portugal, 23–26 April 2018; Volume 2018, pp. 1–15. [Google Scholar] [CrossRef]
- Gaba, P.; Raw, R.S. Impact of Endorsement Policy on the Performance of Blockchain-based VANET. Trans. Emerg. Telecommun. Technol. 2023, 34, e4822. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Anonymous and lightweight authentication for secure vehicular networks. IEEE Trans. Veh. Technol. 2017, 66, 10626–10636. [Google Scholar] [CrossRef]
- George, S.A.; Stephen, S.M.; Jaekel, A. Blockchain-based pseudonym management scheme for vehicular communication. Electronics 2021, 10, 1584. [Google Scholar] [CrossRef]
- Ahmed, M.; Moustafa, N.; Akhter, A.S.; Razzak, I.; Surid, E.; Anwar, A.; Shah, A.S.; Zengin, A. A Blockchain-Based Emergency Message Transmission Protocol for Cooperative VANET. IEEE Trans. Intell. Transp. Syst. 2021, 23, 19624–19633. [Google Scholar] [CrossRef]




| Notation | Meaning |
|---|---|
| IV | Initiating Vehicle |
| EM | Event Message |
| Lv | Location of Initiating Vehicle |
| Le | Location of Event |
| LC | Location Certificate |
| NBV_LIST | Nearby Vehicles List |
| Rc | Response Counter |
| Cr | Response saying Correct |
| Fr | Response saying Fake |
| T | Time elapsed in the message verification process |
| CRV_LIST | Correct Response Vehicle’s List |
| FRV_LIST | Fake Response Vehicle’s List |
| Tv | Threshold Value |
| Dt | Defined Allotted Time |
| VM | Verifying Message |
| VN | Verifying Node |
| Rp | Reward Points |
| CEP | Current Event Points |
| Tf | Trust Factor for Initiating/Verifying Messages |
| Cm | Total Correct message Initiated/Verified by a vehicle |
| Fm | Total Fake messages Initiated/Verified by a vehicle |
| ATf | Average Trust Factor Value of nearby vehicles |
| IM | Initiating Message |
| N | Number of nearby vehicles |
| I | Any vehicle |
| Tfi | Trust Factor for i-th vehicle |
| C | Count of messages in a block |
| M | Maximum messages allowed in a block |
| Event | Initiating Vehicle | Vehicle 1 | Vehicle 2 | Vehicle 3 | Vehicle 4 | Vehicle 5 | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Ep | Rp | Ep | Rp | Ep | Rp | Ep | Rp | Ep | Rp | ||
| 1 | Vehicle4 | 0.25 | 0.25 | −0.25 | −0.25 | 0.25 | 0.25 | −1 | −1 | 0.25 | 0.25 |
| 2 | Vehicle2 | 0.25 | 0.5 | −1 | −1.25 | 0.25 | 0.5 | −0.25 | −1.25 | −0.25 | 0 |
| 3 | Vehicle3 | 0.25 | 0.75 | −0.25 | −1.5 | 1 | 1.5 | −0.25 | −1.5 | 0.25 | 0.25 |
| 4 | Vehicle1 | 1 | 1.75 | −0.25 | −1.75 | −0.25 | 1.25 | −0.25 | −1.75 | −0.25 | 0 |
| 5 | Vehicle4 | 0.25 | 2 | −0.25 | −2 | −0.25 | 1 | 1 | −0.75 | −0.25 | −0.25 |
| 6 | Vehicle1 | 1 | 3 | −0.25 | −2.25 | 0.25 | 1.25 | 0.25 | −0.5 | 0.25 | 0 |
| 7 | Vehicle2 | 0.25 | 3.25 | −1 | −3.25 | 0.25 | 1.5 | −0.25 | −0.75 | −0.25 | −0.25 |
| 8 | Vehicle5 | 0.25 | 3.5 | −0.25 | −3.5 | −0.25 | 1.25 | −0.25 | −1 | 1 | 0.75 |
| 9 | Vehicle3 | 0.25 | 3.75 | −0.25 | −3.75 | −1 | 0.25 | −0.25 | −1.25 | −0.25 | 0.5 |
| 10 | Vehicle5 | 0.25 | 4 | −0.25 | −4 | 0.25 | 0.5 | −0.25 | −1.5 | 1 | 1.5 |
| Event | Vehicle 1 | Vehicle 2 | Vehicle 3 | Vehicle 4 | Vehicle 5 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Correct /Fake | Tf | Correct /Fake | Tf | Correct /Fake | Tf | Correct /Fake | Tf | Correct /Fake | Tf | |
| 1 | Correct | 1 | Fake | −1 | Correct | 1 | Fake | −1 | Correct | 1 |
| 2 | Correct | 1 | Fake | −1 | Correct | 1 | Fake | −1 | Fake | 0 |
| 3 | Correct | 1 | Fake | −1 | Correct | 1 | Fake | −1 | Correct | 0.33 |
| 4 | Correct | 1 | Fake | −1 | Fake | 0.50 | Fake | −1 | Fake | 0 |
| 5 | Correct | 1 | Fake | −1 | Fake | 0.20 | Correct | −0.60 | Fake | −0.20 |
| 6 | Correct | 1 | Fake | −1 | Correct | 0.33 | Correct | −0.33 | Correct | 0 |
| 7 | Correct | 1 | Fake | −1 | Correct | 0.43 | Fake | −0.43 | Fake | −0.14 |
| 8 | Correct | 1 | Fake | −1 | Fake | 0.25 | Fake | −0.50 | Correct | 0 |
| 9 | Correct | 1 | Fake | −1 | Fake | 0.11 | Fake | −0.56 | Fake | −0.11 |
| 10 | Correct | 1 | Fake | −1 | Correct | 0.20 | Fake | −0.60 | Correct | 0 |
| ATf | Tv | |
|---|---|---|
| Number of Vehicles = 100 | Number of Vehicles = 70 | |
| 1 | 25 | 18 |
| 0.8 | 31 | 22 |
| 0.6 | 42 | 29 |
| 0.4 | 63 | 44 |
| 0.2 | 75 | 53 |
| 0 | 75 | 53 |
| −0.2 | 75 | 53 |
| −0.4 | 75 | 53 |
| −0.6 | 75 | 53 |
| −0.8 | 75 | 53 |
| −1 | 75 | 53 |
| Operating System | Ubuntu 16.04 LTS |
|---|---|
| For Client Application |
|
| For fog nodes |
|
| For Blockchain network | Hyperledger Fabric
|
| For Blockchain performance evaluation | Hyperledger Caliper |
| ASC | BBPMS | GMT | B-SAFE | |
|---|---|---|---|---|
| Blockchain-based or not | Not based on Blockchain | Based on Blockchain | Based on Blockchain | Based on Blockchain |
| Implementation | VanetMobiSim, OPNET. | SUMO 0.32.0, OMNET++ 5.3, Veins 4.7.1 | Ethereum, Truffle framework | Hyperledger Fabric and Caliper |
| Privacy | Yes | Yes | Yes | Yes |
| Authentication | Yes | Yes | Yes | Yes |
| Anonymity | Yes | Yes | Yes | Yes |
| Immutability | No | Yes | Yes | Yes |
| Decentralization | No | Yes | Yes | Yes |
| Non-repudiation and traceable | No | Yes | Yes | Yes |
| Data validation | Yes | No | No | Yes |
| Incentive Mechanism | No | No | No | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gaba, P.; Raw, R.S.; Kaiwartya, O.; Aljaidi, M. B-SAFE: Blockchain-Enabled Security Architecture for Connected Vehicle Fog Environment. Sensors 2024, 24, 1515. https://doi.org/10.3390/s24051515
Gaba P, Raw RS, Kaiwartya O, Aljaidi M. B-SAFE: Blockchain-Enabled Security Architecture for Connected Vehicle Fog Environment. Sensors. 2024; 24(5):1515. https://doi.org/10.3390/s24051515
Chicago/Turabian StyleGaba, Priyanka, Ram Shringar Raw, Omprakash Kaiwartya, and Mohammad Aljaidi. 2024. "B-SAFE: Blockchain-Enabled Security Architecture for Connected Vehicle Fog Environment" Sensors 24, no. 5: 1515. https://doi.org/10.3390/s24051515
APA StyleGaba, P., Raw, R. S., Kaiwartya, O., & Aljaidi, M. (2024). B-SAFE: Blockchain-Enabled Security Architecture for Connected Vehicle Fog Environment. Sensors, 24(5), 1515. https://doi.org/10.3390/s24051515








