Empowering Privacy Through Peer-Supervised Self-Sovereign Identity: Integrating Zero-Knowledge Proofs, Blockchain Oversight, and Peer Review Mechanism
Abstract
1. Introduction
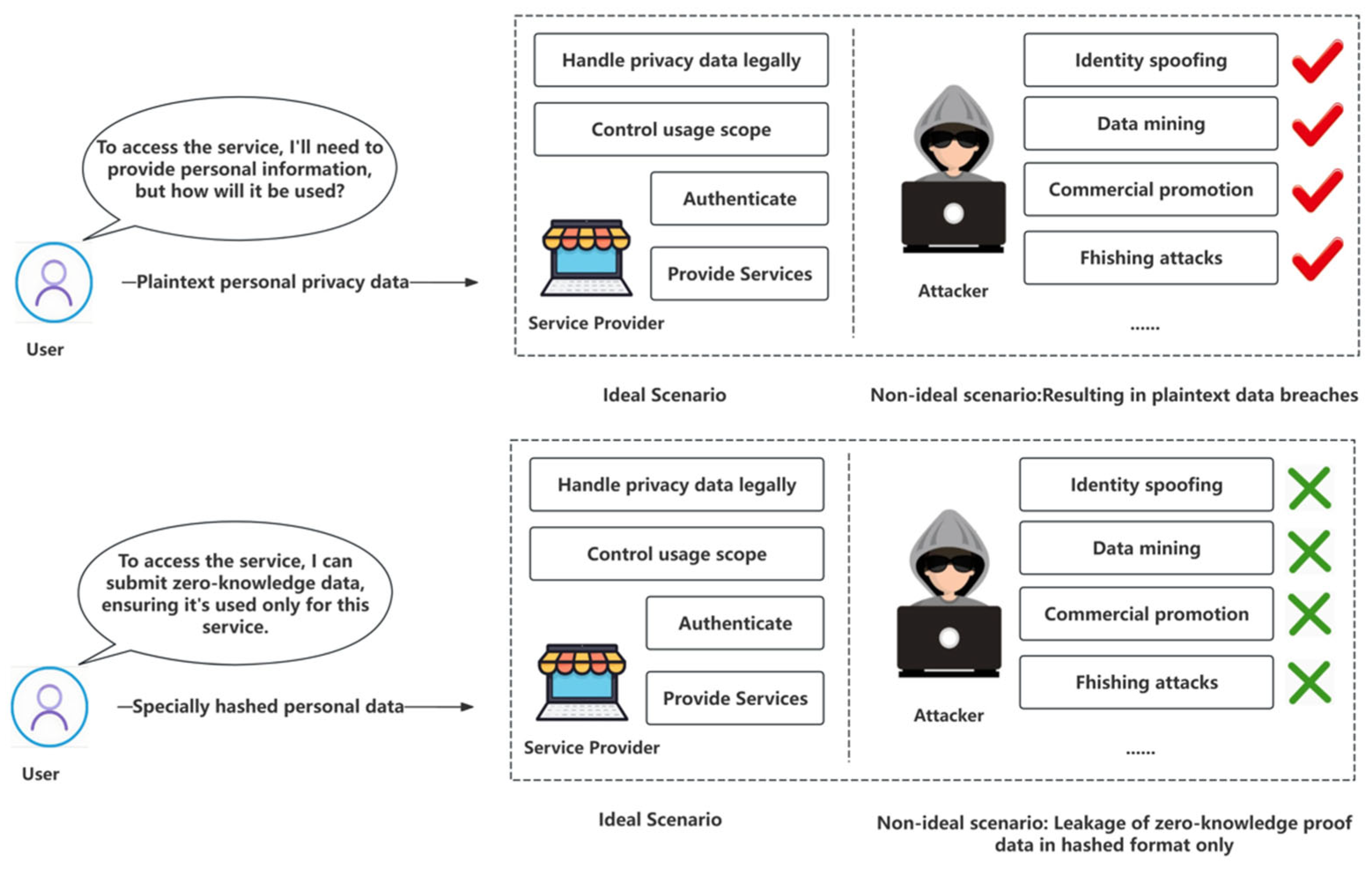
- User Data Breaches: Service providers often tend to store user data in plain text, making each provider a potential single point of failure.
- User Data Misuse: Users lack control over the data collected by service providers, which increases the risk of unauthorized use of these data.
- Excessive Data Collection: Service providers often collect more user data than necessary, heightening the risks of data breaches and misuse.
- Insufficient Regulation: Regulatory measures are typically reactive and lack stringent constraints on the behaviors of both users and service providers.
- User Control Over Personal Data: Users should have greater control over their data.
- Encryption of User Data: Storing and using user data in an encrypted format rather than plain text can significantly reduce risks.
- Unified User Authentication and Data Sharing: Implementing a standardized method for user authentication and data sharing would allow service providers to share data across domains, reducing the need for separate storage.
- Peer Review Mechanism: Introducing an effective peer review mechanism can ensure that no single service provider collects more user data than necessary for the industry, addressing the issue of excessive data collection.
- Enhanced Regulatory Measures: Strengthening regulatory methods to ensure mutual monitoring among all interaction parties can address the lack of regulation.
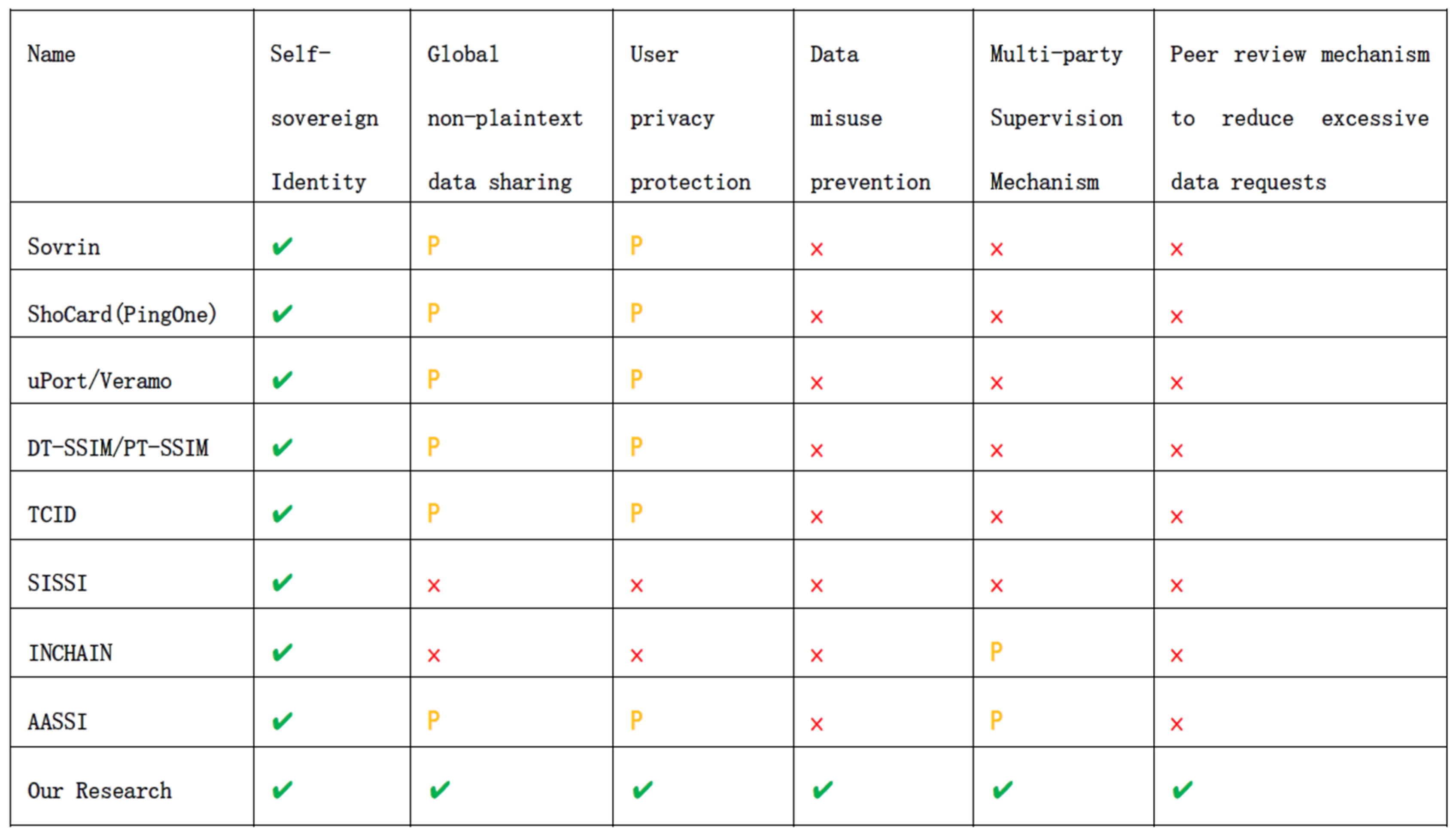
- Incorporating zero-knowledge proofs (ZKPs) for privacy protection in SSI mechanisms: ZKPs enhance the perpetual privacy of information during multiparty computations, ensuring that information remains “usable but invisible” during its flow and usage. Our approach uniquely brings ZKP, safeguarding user data in scenarios where plain text interaction is unnecessary.
- Development of a blockchain-based content-sharing oversight mechanism: Existing SSI generation mechanisms often lack regulatory frameworks to mitigate malicious behavior by users and service providers. Our research introduces an innovative three-party supervisory mechanism, empowering regulatory bodies to effectively trace and monitor all behaviors of parties involved in information sharing on the blockchain. This comprehensive oversight system ensures no blind spots in regulatory coverage and holds all interacting parties accountable, including the regulatory bodies.
- Introduction of a peer review mechanism to prevent excessive data requests: Current solutions often overlook the risk of service providers excessively requesting user data. Our research introduces a peer review mechanism that evaluates the necessity of service providers’ requests for data. This mechanism, supported by regulatory authorities, ensures that any additional data requests undergo scrutiny by industry peers, thereby mitigating the risk of data misuse.
2. Related Work
2.1. Centralized Identity
2.2. Federated Identity
2.3. User-Centric Identity
2.4. Self-Sovereign Identity
3. Methodology
3.1. Stage 1: Digital Identity Registration Stage
{Add(PriIC(UID, Hash(PubSC(PIV_id), PIN_id, m), Ts), PubSC(PIV_id), PIN_id, m) … Add(PriIC(UID, Hash(PubSC(PIV_n), PIN_n, m), Ts), PubSC(PIV_n), PIN_n, m)}
3.2. Stage 2: Digital Identity Usage Stage
3.2.1. Scenario 1: Sharing UID Only
{PubRA(UID, PriU(SPID, Success/Fail, NULL, Ts2))}
{PubRA(SPID, PriSP(UID, Success/Fail, NULL, Ts3))}
3.2.2. Scenario 2: Sharing UID and Specific Personal Identity Category Information
{PubRA(SPID, PriSP(UID, Success/Fail, PIN_id, Ts5))}
{PubRA(UID, PriU(SPID, Success/Fail, PIN_id, Ts6))}
3.3. Stage 3: Digital Identity Update Stage
3.3.1. Scenario 1: Service Provider Requests User to Add a Specific Category of Personal Identity Information
{Request(PriSP2(UID, Reason, PIN_x, Ts1))}
{Vote(PubSC(PriSPn(SPnID, UID, Ts2)))}
{PriSC(PubU(LIST, Reason, PIN_x, SP2ID, Ts3))}
{SamplingVerification(PriRA(PubSC(UID, PIN_x, Reason, LIST, SP2ID, Ts1)))}
{PubSPn(UID, PIN_x, Reason, SP2ID, Ts1)}
{PriRA(UID, LIST, PIN_x, SP2ID, Ts4)}
3.3.2. Scenario 2: Specific Category Personal Information Validation Count m Has Decremented to 1
3.4. Stage 4: Digital Identity Deletion Stage
4. Experiments and Analysis
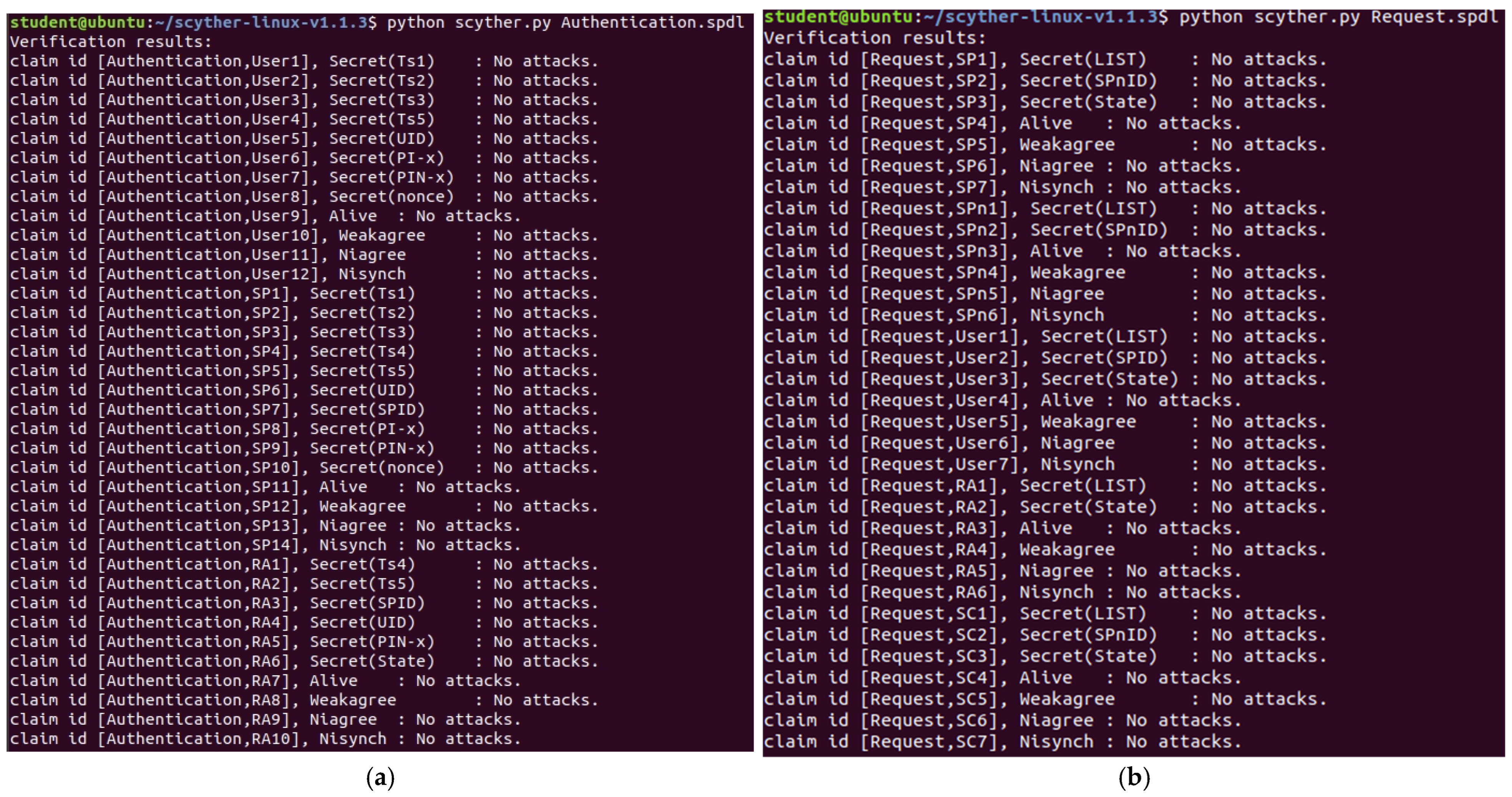
4.1. Formal Security Verification of Protocols Based on Scyther
- ✓ Confidentiality
- ✓ Aliveness
- ✓ Weak Agreement
- ✓ Non-injective Agreement (Niagree)
- ✓ Non-synchronization (Nisynch)
- ✓ State Consistency
4.2. The Analysis of Correctness and Interpretation of Experimental Results
4.2.1. Concerns from the Perspective of Honest Users
- Identity Theft or Substitution: Users worry that attackers might steal or replace their authentication credentials, leading to unauthorized access or impersonation.
- Data Leakage During Transmission: Users are concerned that personal data transmitted over the network could be intercepted or disclosed, leading to privacy breaches.
- Infringement of Data Sovereignty: Users fear losing control over their data through unauthorized access or service providers exerting undue control without consent, such as using personal data on the blockchain without authorization or attempting to use data categories declared as deleted.
- Engagement in Malicious Activities: Users worry about unintentionally engaging in malicious activities while using the service, potentially causing harm to others or the system.
- Denial of Malicious Behavior: There is concern that dishonest users may deny engaging in malicious activities, making it difficult to hold them accountable for misconduct or security breaches.
4.2.2. Security Analysis of the System for the Users’ Concerns
- Identity Theft or Substitution.
- 2.
- Data Leakage During Transmission.
- 3.
- Infringement of Data Sovereignty.
- 4.
- Engagement in Malicious Activities.
{PubRA(UID, PriU(SPID, Success/Fail, NULL, Ts2))}
SP → User Behavior Chain:
{PubRA(SPID, PriSP(UID, Success/Fail, NULL, Ts3))}
- 5.
- Denial of Malicious Behavior.
4.2.3. Concerns from the Perspective of Service Providers
- Identity theft or substitution: service providers are worried about unauthorized access to user accounts due to identity theft or substitution, leading to security breaches and misuse of user data.
- Fabricated personal data: there is concern that users may submit false personal information, compromising data accuracy and service quality.
- Excessive data collection: service providers are cautious about over-collecting user data, potentially infringing privacy rights and violating regulations.
- Abuse of user data: service providers fear misuse of collected data, such as unauthorized sales to third parties or usage for purposes unrelated to the service, leading to privacy violations and loss of trust.
- Identity fraud: there is a risk of malicious actors impersonating legitimate service providers to access user data or deceive users into providing sensitive information.
- Denial of malicious behavior: service providers may deny involvement in malicious activities or responsibility for data breaches, undermining trust and accountability.
4.2.4. Security Analysis of the System for the Providers’ Concerns
- Identity Theft or Substitution.
- 2.
- Fabricated Personal Data.
- 3.
- Excessive Data Collection.
- 4.
- Abuse of User Data.
- 5.
- Identity Fraud.
SP → User Behavior Chain:
{PubRA(SPID, PriSP(UID, Success/Fail, PIN_id, Ts5))}
- 6.
- Denial of Malicious Behavior.
4.2.5. Concerns from the Regulatory Authority’s Perspective
- Inability to monitor malicious behavior: regulatory authorities may struggle to effectively monitor and detect malicious activities from both users and service providers, including fraudulent and deceptive practices.
- Peer review mechanism failures: concerns arise when service providers collude to manipulate the peer review process, rendering it ineffective in identifying and penalizing unethical behavior.
- Fabrication of peer review results: service providers falsifying peer review outcomes can undermine the credibility and reliability of the peer review process, affecting trust in industry self-regulation.
- Sensitive data leaks: Regulatory authorities must ensure the confidentiality and security of sensitive information exchanged during communications with users and service providers. Breaches could lead to identity theft, financial fraud, or reputational damage.
- Tampering with regulatory data: unauthorized alteration or manipulation of regulatory data can undermine its accuracy and reliability, leading to incorrect regulatory decisions or enforcement actions.
- Leakage of regulatory data: If regulatory data contains sensitive information, there is a risk of compromising user or service provider privacy, potentially harming their rights and interests.
- Internal malicious behavior: Regulatory authorities must guard against internal misconduct or corruption, as failure to detect such behavior can erode public trust and undermine the authority’s effectiveness.
4.2.6. Security Analysis of the System for the Regulator’s Concerns
- Inability to Monitor Malicious Behavior.
- 2.
- Peer Review Mechanism Failures.
- 3.
- Fabrication of Peer Review Results.
- 4.
- Sensitive Data Leaks.
- 5.
- Tampering with Regulatory Data.
- 6.
- Leakage of Regulatory Data.
- 7.
- Internal Malicious Behavior.
4.3. Simulation Analysis of Computational Efficiency
- Operating System: Debian 5.5.17-1kali1 (21 April 2020) x86_64 GNU/Linux
- CPU: AMD Ryzen R5 5600H (configured to four cores and four threads via VMware to simulate limited resources) (Advanced Micro Devices (AMD) based in Santa Clara, CA, USA)
- Memory: DDR4 4 GB 2666
5. Conclusions
6. Patents
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, Y.; Xiao, D. The Data Breach Notification Obligation in Australia and its Enlightenment in China. J. Inf. Resour. Manag. 2021, 11, 40–49. [Google Scholar]
- Rodrigues, G.A.P.; Serrano, A.L.M.; Vergara, G.F.; Albuquerque, R.D.O.; Nze, G.D.A. Impact, Compliance, and Countermeasures in Relation to Data Breaches in Publicly Traded US Companies. Future Internet 2024, 16, 201. [Google Scholar] [CrossRef]
- Pimenta Rodrigues, G.A.; Marques Serrano, A.L.; Lopes Espiñeira Lemos, A.N.; Canedo, E.D.; Mendonça, F.L.L.D.; de Oliveira Albuquerque, R.; García Villalba, L.J. Understanding Data Breach from a Global Perspective: Incident Visualization and Data Protection Law Review. Data 2024, 9, 27. [Google Scholar] [CrossRef]
- Ayyagari, R. An exploratory analysis of data breaches from 2005–2011: Trends and insights. J. Inf. Priv. Secur. 2012, 8, 33–56. [Google Scholar] [CrossRef]
- Gal-Or, E. Information sharing in oligopoly. Econom. J. Econom. Soc. 1985, 53, 329–343. [Google Scholar] [CrossRef]
- Rannenberg, K. ISO/IEC 24760-1: A Framework for Identity Management—Part 1: Terminology and Concepts; International Organization for Standardization: Geneva, Switzerland, 2019. [Google Scholar]
- Techopedia. What is a Digital Identity? Available online: https://www.techopedia.com/definition/23915/digital-identity (accessed on 17 December 2024).
- Fang, J.; Yan, C.; Yan, C. Centralized Identity Authentication Research Based on Management Application Platform. In Proceedings of the 2009 First International Conference on Information Science and Engineering, Nanjing, China, 26–28 December 2009. [Google Scholar]
- Microsoft Passport: Streamlining Commerce and Communication on the Web. Available online: https://news.microsoft.com/1999/10/11/microsoft-passport-streamlining-commerce-and-communication-on-the-web/ (accessed on 17 December 2024).
- Shim, S.; Bhalla, G.; Pendyala, V. Federated identity management. Computer 2005, 38, 120–122. [Google Scholar] [CrossRef]
- Jøsang, A.; Pope, S. User Centric Identity Management. In Proceedings of the AusCERT Asia Pacific Information Technology Security Conference, Gold Coast, Australia, 22–26 May 2005. [Google Scholar]
- Recordon, D.; Fitzpatrick, B. OpenID Authentication 1.1. 2006. Available online: https://openid.net/specs/openid-authentication-1_1.html (accessed on 17 December 2024).
- Recordon, D.; Reed, D. OpenID 2.0: A platform for user-centric identity management. In Proceedings of the Second ACM Workshop on Digital Identity Management, Alexandria, VA, USA, 3 November 2006; pp. 11–16. [Google Scholar]
- Sakimura, N.; Bradley, J. OpenID Connect Core 1.0. Available online: https://openid.net/specs/openid-connect-core-1_0-final.html (accessed on 17 December 2024).
- Leiba, B. OAuth Web Authorization Protocol. IEEE Internet Comput. 2012, 16, 74–77. [Google Scholar] [CrossRef]
- Cho, S.R.; Choi, D.S.; Jin, S.H.; Lee, H.H. Passwordless Authentication Technology-FIDO. Electron. Telecommun. Trends 2014, 29, 101–109. [Google Scholar]
- Mühle, A.; Grüner, A.; Gayvoronskaya, T.; Meinel, C. A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 2018, 30, 80–86. [Google Scholar] [CrossRef]
- Khovratovich, D.; Law, J. Sovrin: Digital Identities in the Blockchain Era. 2017. Available online: https://sovrin.org/wp-content/uploads/AnonCred-RWC.pdf (accessed on 17 December 2024).
- Naik, N.; Jenkins, P. Sovrin network for decentralized digital identity: Analysing a self-sovereign identity system based on distributed ledger technology. In Proceedings of the 2021 IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 13 September 2021–13 October 2021; pp. 1–7. [Google Scholar]
- Windley, P. How Sovrin Works; Windely.com: Hoboken, NJ, USA, 2016. [Google Scholar]
- ShoCard. Available online: https://shocard.com (accessed on 29 October 2024).
- To the Sovrin Community. Available online: https://us14.campaign-archive.com/?u=b2c2f50b93f0ad7684f55ccde&id=97dcc86838 (accessed on 29 October 2024).
- PingOne Neo. Available online: https://www.pingidentity.com/en/lp/ac/pingone-neo.html (accessed on 29 October 2024).
- Naik, N.; Jenkins, P. uPort Open-Source Identity Management System: An Assessment of Self-Sovereign Identity and User-Centric Data Platform Built on Blockchain. In Proceedings of the 2020 IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 12 October 2020–12 November 2020. [Google Scholar]
- El Haddouti, S.; El Kettani MD, E.C. Analysis of identity management systems using blockchain technology. In Proceedings of the 2019 International Conference on Advanced Communication Technologies and Networking (CommNet), Rabat, Morocco, 12–14 April 2019; pp. 1–7. [Google Scholar]
- Panait, A.E.; Olimid, R.F.; Stefanescu, A. Analysis of uPort Open, an identity management blockchain-based solution. In International Conference on Trust and Privacy in Digital Business; Springer International Publishing: Cham, Switzerland, 2020; pp. 3–13. [Google Scholar]
- Performant and Modular Apis for Verifiable Data and Ssi. Available online: https://veramo.io/ (accessed on 29 October 2024).
- Abid, A.; Cheikhrouhou, S.; Kallel, S.; Jmaiel, M. A blockchain-based self-sovereign identity approach for inter-organizational business processes. In Proceedings of the 2022 17th Conference on Computer Science and Intelligence Systems (FedCSIS), Sofia, Bulgaria, 4–7 September 2022; pp. 685–694. [Google Scholar]
- Cocco, L.; Tonelli, R.; Marchesi, M. A system proposal for information management in building sector based on BIM, SSI, IoT and blockchain. Future Internet 2022, 14, 140. [Google Scholar] [CrossRef]
- Stokkink, Q.; Ishmaev, G.; Epema, D.; Pouwelse, J. A Truly Self-Sovereign Identity System. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4–7 October 2021. [Google Scholar]
- Samir, E.; Wu, H.; Azab, M.; Xin, C.S.; Zhang, Q. DT-SSIM: A Decentralized Trustworthy Self-Sovereign Identity Management Framework. IEEE Internet Things J. 2022, 9, 7972–7988. [Google Scholar] [CrossRef]
- Fathalla, E.S.; Azab, M.; Xin, C.; Wu, H. PT-SSIM: A proactive, trustworthy self-sovereign identity management system. IEEE Internet Things J. 2023, 10, 17155–17169. [Google Scholar] [CrossRef]
- Braun, C.H.J.; Papanchev, V.; Käfer, T. SISSI: An architecture for semantic interoperable self-sovereign identity-based access control on the web. In Proceedings of the ACM Web Conference 2023, Austin, TX, USA, 30 April 2023–4 May 2023; pp. 3011–3021. [Google Scholar]
- Farao, A.; Paparis, G.; Panda, S.; Panaousis, E.; Zarras, A.; Xenakis, C. INCHAIN: A cyber insurance architecture with smart contracts and self-sovereign identity on top of blockchain. Int. J. Inf. Secur. 2024, 23, 347–371. [Google Scholar] [CrossRef]
- Gao, L.; Yu, J.; Zhang, J.; Tang, Y.; Wen, Q. AASSI: A Self-Sovereign Identity Protocol with Anonymity and Accountability; IEEE Access: Piscataway, NJ, USA, 2024. [Google Scholar]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures; Cryptology ePrint Archive: Carson, NV, USA, 1998. [Google Scholar]
- Chen, X.; Zhang, F.; Kim, K. Chameleon hashing without key exposure. In International Conference on Information Security; Springer: Berlin/Heidelberg, Germany, 2004; pp. 87–98. [Google Scholar]
- Chen, X.; Zhang, F.; Susilo, W.; Tian, H.; Li, J.; Kim, K. Identity-based chameleon hashing and signatures without key exposure. Inf. Sci. 2014, 265, 198–210. [Google Scholar] [CrossRef]
- Zhang, Q.; Zhou, X.; Zhong, H.; Cui, J.; Li, J.; He, D. Device-Side Lightweight Mutual Authentication and Key Agreement Scheme based on Chameleon Hashing for Industrial Internet of Things. In IEEE Transactions on Information Forensics and Security; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Yellick, J. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Lin, I.C.; Kuo, C.W. Trustworthy Blockchain Oracles for Smart Contracts. In 2021 International Conference on Security and Information Technologies with AI, Internet Computing and Big-data Applications; Springer International Publishing: Cham, Switzerland, 2022; pp. 379–389. [Google Scholar]
- Tian, Y.; Miyaji, A.; Matsubara, K.; Cui, H.; Li, N. Revocable policy-based chameleon hash for blockchain rewriting. Comput. J. 2023, 66, 2365–2378. [Google Scholar] [CrossRef]
- Khalili, M.; Dakhilalian, M.; Susilo, W. Efficient chameleon hash functions in the enhanced collision resistant model. Inf. Sci. 2020, 510, 155–164. [Google Scholar] [CrossRef]
- Wang, Z.; Lan, L.; Yiu, S. Chameleon Hash Based Efficiently Updatable Oblivious Key Management. In IEEE Transactions on Services Computing; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- Goldreich, O.; Oren, Y. Definitions and properties of zero-knowledge proof systems. J. Cryptol. 1994, 7, 1–32. [Google Scholar] [CrossRef]
- Feige, U.; Fiat, A.; Shamir, A. Zero-knowledge proofs of identity. J. Cryptol. 1988, 1, 77–94. [Google Scholar] [CrossRef]
- Kurmi, J.; Sodhi, A. A Survey of Zero-Knowledge Proof for Authentication. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2015, 5, 494–501. [Google Scholar]
- Zhou, L.; Diro, A.; Saini, A.; Kaisar, S.; Hiep, P.C. Leveraging zero knowledge proofs for blockchain-based identity sharing: A survey of advancements, challenges and opportunities. J. Inf. Secur. Appl. 2024, 80, 103678. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P.; Sun, Z.; Xie, W.; Peng, X. A survey on zero-knowledge proof in blockchain. IEEE Netw. 2021, 35, 198–205. [Google Scholar] [CrossRef]
- Sharma, A.K.; Mittal, S.K. Cryptography & network security hash function applications, attacks and advances: A review. In Proceedings of the 2019 Third International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 10–11 January 2019; pp. 177–188. [Google Scholar]
- Hasan, H.A.; Al-Layla, H.F.; Ibraheem, F.N. A review of hash function types and their applications. Wasit J. Comput. Math. Sci. 2022, 1, 75–88. [Google Scholar] [CrossRef]
- Mittelbach, A.; Fischlin, M. The Theory of Hash Functions and Random Oracles: An Approach to Modern Cryptography; Springer Nature: Cham, Switzerland, 2021. [Google Scholar]
- Scheffler, S.; Kulshrestha, A.; Mayer, J. Public verification for private hash matching. In Proceedings of the 2023 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–25 May 2023; pp. 253–273. [Google Scholar]
- Mishra, N.; Islam, S.H.; Zeadally, S. A comprehensive review on collision-resistant hash functions on lattices. J. Inf. Secur. Appl. 2021, 58, 102782. [Google Scholar] [CrossRef]
- Cremers, C.J.F. Scyther: Semantics and Verification of Security Protocols. Ph.D. Thesis, Technische Universiteit Eindhoven, Eindhoven, The Netherlands, 2006. [Google Scholar]
- Cremers, C.J. The scyther tool: Verification, falsification, and analysis of security protocols: Tool paper. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Cremers, C.J.F. Scyther: Unbounded verification of security protocols. Technol. Rep./ETH Zur. Dep. Comput. Sci. 2011, 572. [Google Scholar] [CrossRef]
- Worrasangasilpa, K. Formally Verifying the Security Properties of a Proof-of-Stake Blockchain Protocol; Apollo—University of Cambridge Repository: Cambridge, UK, 2021. [Google Scholar] [CrossRef]
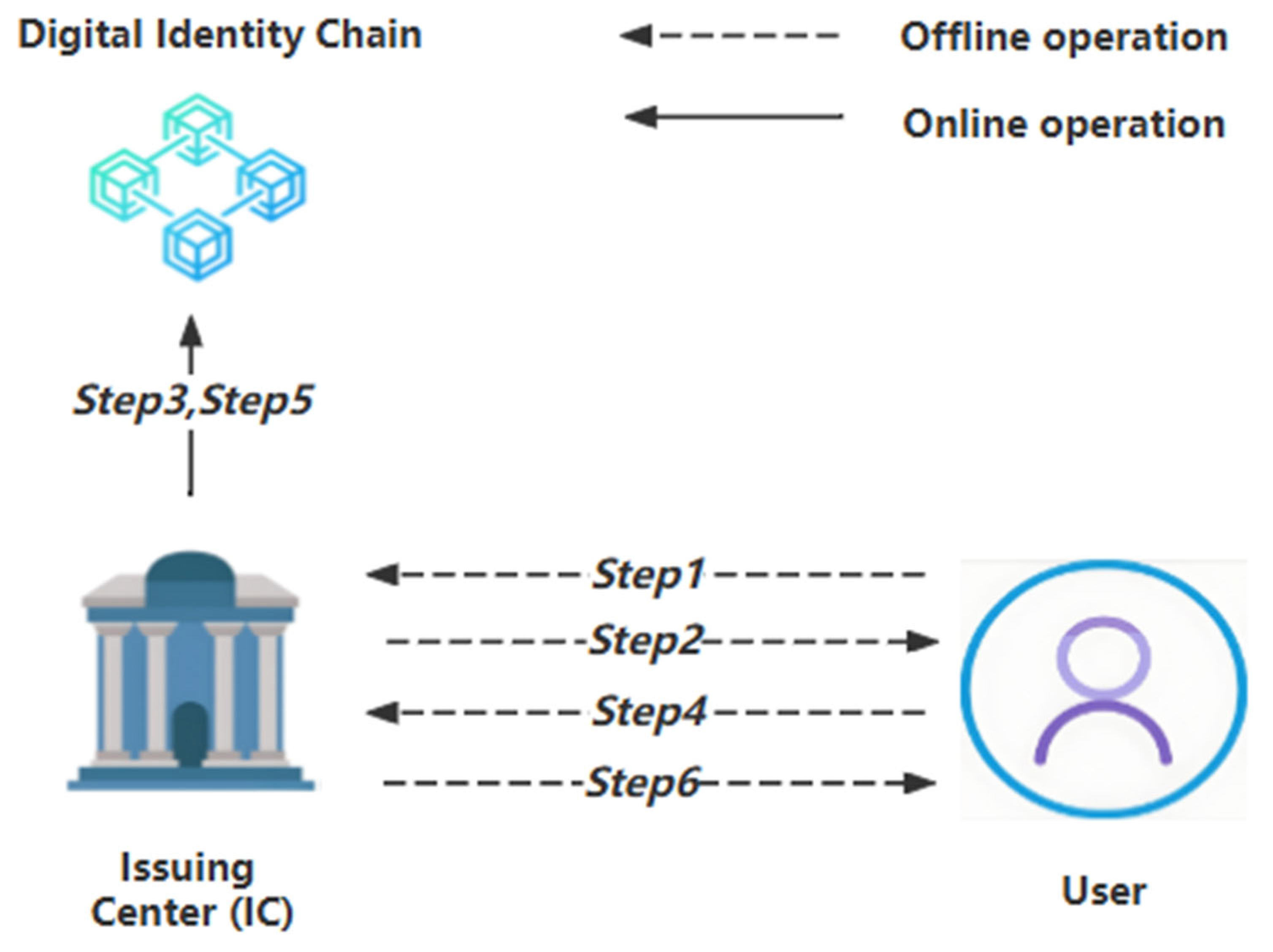

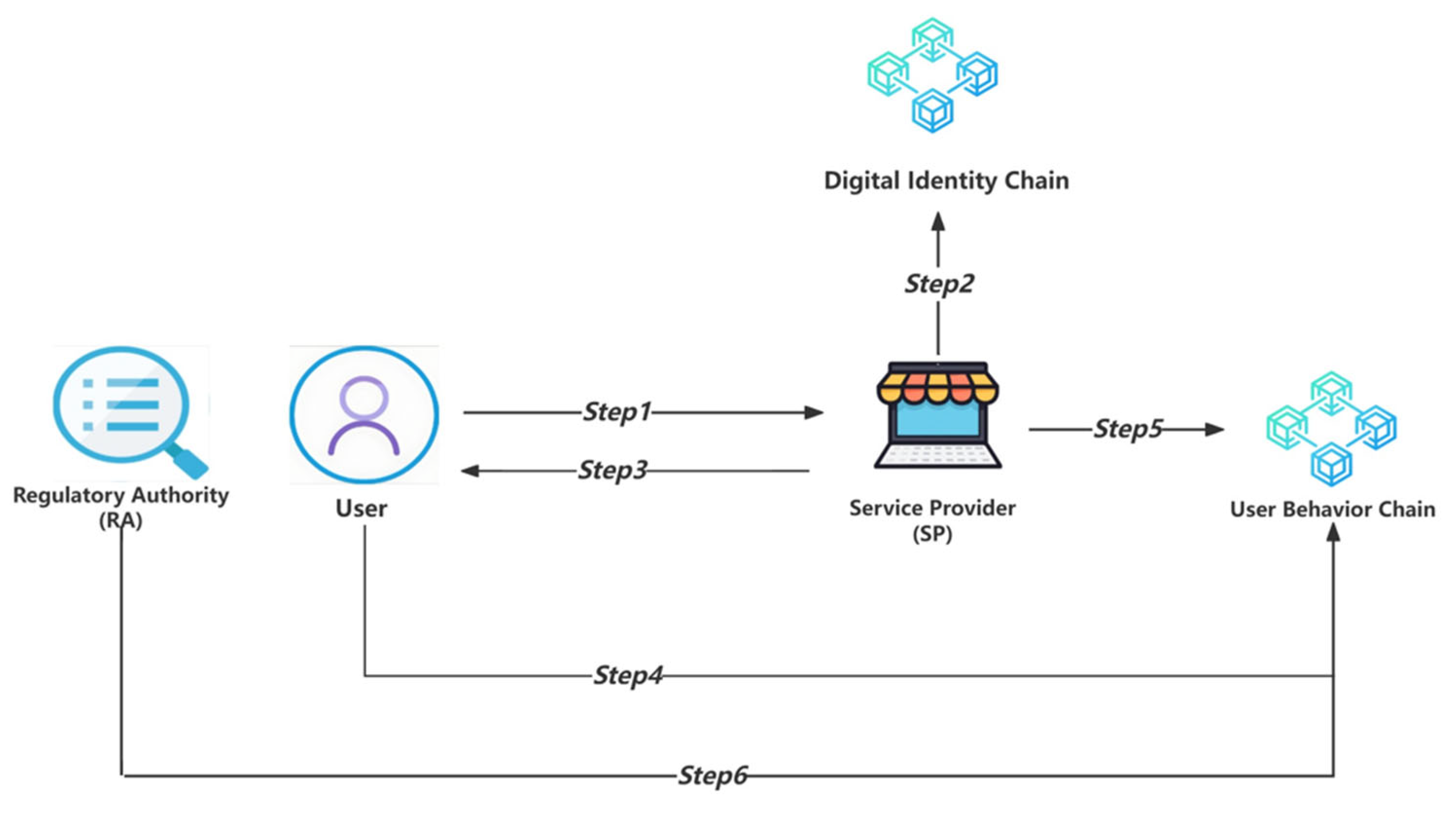
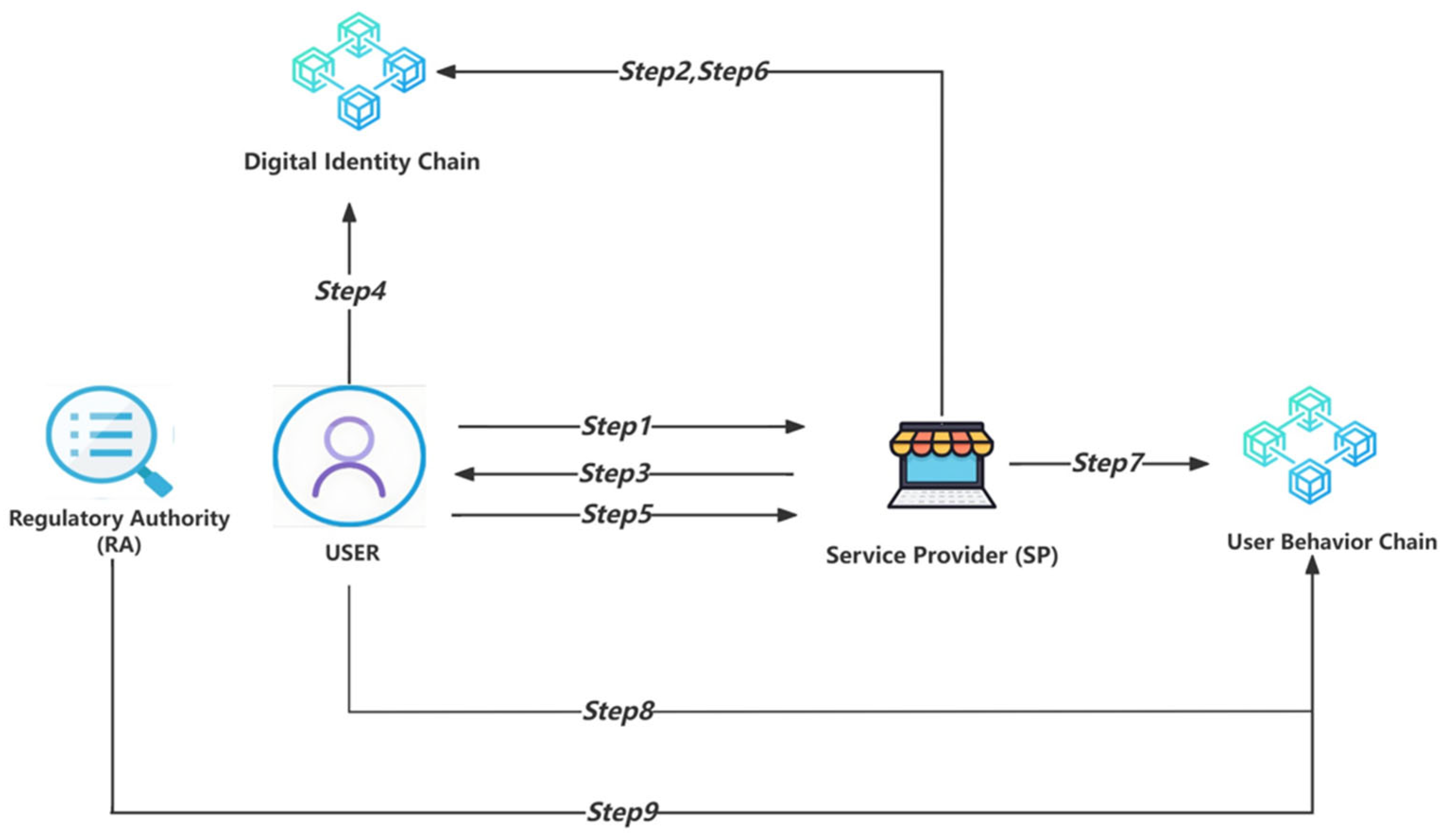
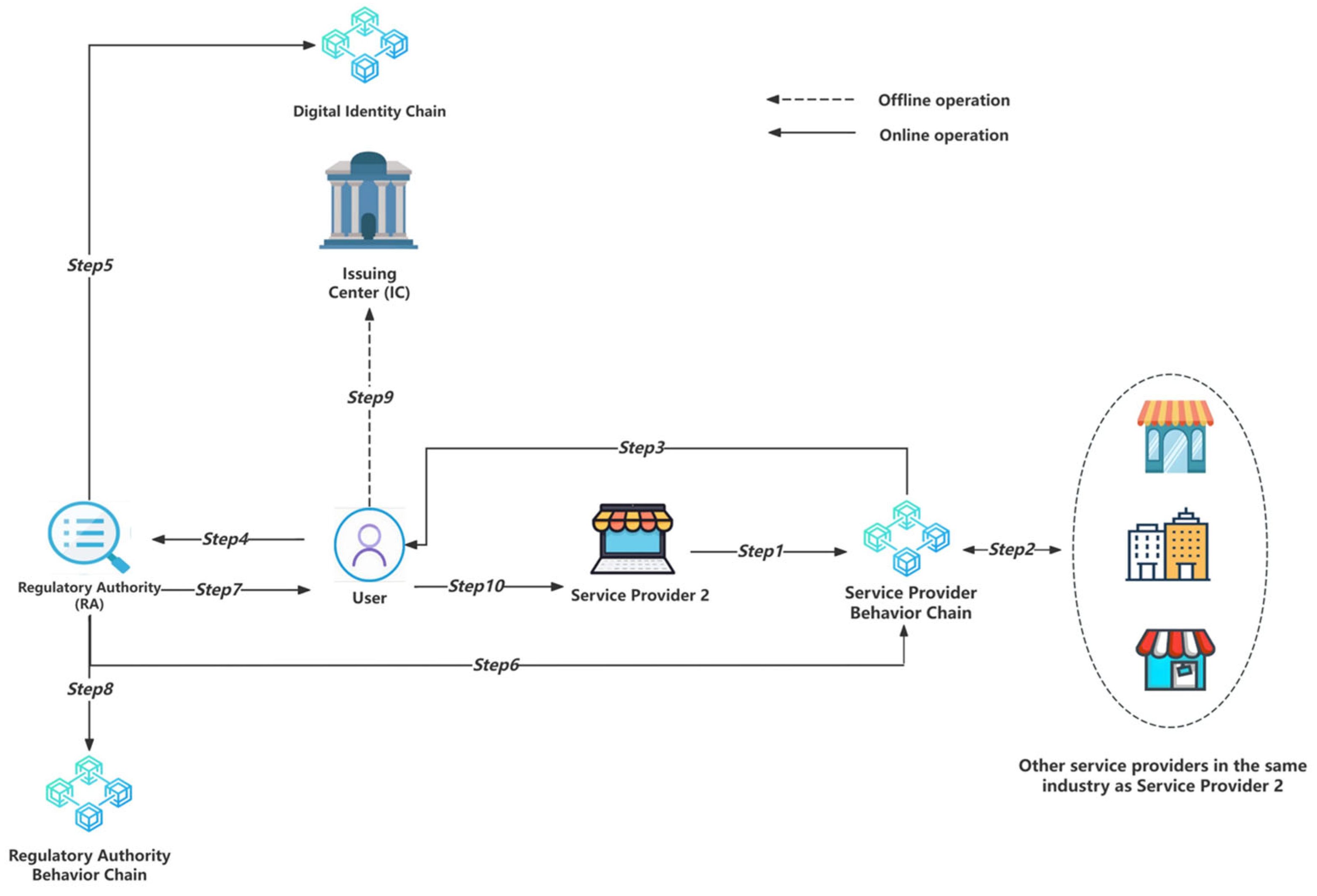


| Entity Name | Description |
|---|---|
| User | Users are physical entities who register and use digital identities. |
| Issuing Center (IC) | The Issuing Center (IC) is an entity in the digital identity registration stage that is the only entity capable of creating and updating digital identity information. In our research, the Issuing Center (IC) acts as a trusted entity, like a government institution, responsible for verifying users’ physical identities and creating their digital identities. The IC’s digital signature endorses the identity information created. However, the IC does not control any blockchain or the information on the blockchain. |
| Service Provider (SP) | The Service Provider (SP) is an entity that interacts with users for digital identity transactions. It verifies the user’s digital identity and provides specific services to the user, during which it requires user data. |
| Regulatory Authority (RA) | The Regulatory Authority (RA) regulates digital identity registration and usage, ensuring compliance and security of the digital identity system. |
| Blockchain Name | Description |
|---|---|
| Digital Identity Chain | The Digital Identity Chain records user digital identity information. In the digital identity registration stage, the user’s digital identity information is stored on the Digital Identity Chain. |
| User Behavior Chain | The User Behavior Chain records user behavior during the digital identity usage stage. |
| Regulatory Authority Behavior Chain | The Regulatory Authority Behavior Chain records the actions of the Regulatory Authority (RA) during digital identity registration and usage processes. |
| Service Provider Behavior Chain | The Service Provider Behavior Chain records SP behavior during the digital identity usage and update stage. |
| Symbol | Description |
|---|---|
| PubX | The public key of a particular entity. For example, PubU represents the user’s public key. |
| PriX | The private key of a particular entity. For example, PubU represents the user’s private key. |
| UID | Stands for User Digital Identity ID. An IC issues it and is unique. |
| SPID | Stands for Service Provider ID. It is assigned by an IC when the SP is established and is unique. |
| PI_x | PI_x represents the detailed content of a specific type of user’s personal information. For example, PI_id can represent the user’s identity ID details, and PI_phone can represent the user’s phone number information. |
| PIN_x | PIN_x denotes the name of a specific type of personal information, such as ’Identity ID’ for PIN_id and ’Phone Number’ for PIN_phone. It categorizes on-chain stored personal information, which remains non-plaintext in this study. Service providers refer to PIN_x when requesting access. |
| PIV_x | PIV_x represents Personal Information Verification data, which is the hashed personal information ultimately stored on the blockchain. This ensures privacy while supporting zero-knowledge proof sharing and verification. For example, PIV_id represents the verifiable identity ID data. Each PIV_x is a specially processed data set that allows for m instances of zero-knowledge proof verification. |
| m | The number of hashes used to create PIV_x represents the number of zero-knowledge proof verifications available on the blockchain. |
| c | c is the counter used by the smart contract’s Fetch() function, which sets up a separate counter for each type of PIV_x for every user, with each counter initialized to m. The value of c can be stored on-chain and modified using a chameleon hash [36,37,38,39] or managed as an internal counter within the smart contract’s storage. |
| Hashx | The hash operation, where x represents the number of times the hash is applied. |
| Nonce | The random value hashed with PI_x to create PIV_x is given to the user for future zero-knowledge proof verifications and to prevent replay attacks on the blockchain. |
| Ts | Timestamp |
| Success/Fail | Flag for successful or failed operation |
| Reason | The rationale submitted by the service provider in the peer review mechanism for requesting data serves as the basis for the peer review process. |
| LIST | The collection of Service Provider IDs in the peer review process who approve the current data request. |
| Smart Contract Function Name | Description |
|---|---|
| Create () Input: Accepts one parameter pair consisting of the UID and PubU, both signed using the Issuing Center’s (IC) private key. Output: Return True on success, False on failure. | Create a new user digital identity block and write UID and PriIC (UID, PubU) to the block. |
| Add() Input: Accepts four parameters: the UID and timestamp (Ts), along with the combined hash result for PubSC (PIV_x), PIN_x, and m, all signed with the Issuing Center’s (IC) private key; the PIV_x set is encrypted with the public key of the smart contract function; the digital identity name (PIN_x); and the number of verifiable attempts (m)”. Output: Return True on success, False on failure. | Upload the newly created PIV_x to the digital identity chain. |
| Smart Contract Function Name | Description |
|---|---|
| GetPubKey() Input: Accepts one parameter, which is UID. Output: Return PubU on success, Null on failure | Find the corresponding PubU on the chain based on the UID and return it as the return value. |
| Fetch() Input: Accepts three parameters, namely UID, SPID, and personal information name PIN_x. Output: If the input SPID is the same as the currently locked SPID of the GetC() function, the value of counter c is determined. If the counter c is greater than 1, PriIC(PriU(Hashc(PI_x·Nonce))) is returned. A null value is returned if c does not exist; if c equals 1, a data update prompt string is returned. Service is denied if the input SPID is different from the currently locked SPID of the GetC() function or is not locked. | This function and the GetC() function build a synchronization semaphore with each other. If the GetC() function is not called by the user in advance and locks the specific SPID, the current function will not work. To ensure the consistency of the c value each time data are shared, the user should authorize this sharing. When the SPID is acknowledged, this function uses the UID and PIN_x to locate the block containing the corresponding PIV_x data. The smart contract chain code includes counter c, private key PriSC, and corresponding decryptor. Counter c is initially set to the current m value of PIV_x. Each time the smart contract decrypts PubSC(PriIC(PriU(Hashc(PI_x·Nonce)))) and returns PriIC(PriU(Hashc(PI_x·Nonce))), the counter c decreases by 1. When the counter c decreases to 1 for the current PIV_x, it indicates that all the hash data of the current PIV_x have been used and need to be updated. The value of c can be stored on-chain and modified through decrementing using a chameleon hash [36,37,38,39], or it can be managed as an internal counter within the smart contract’s own storage. |
| GetC() Input: Accepts two parameters, which are the UID and the SPID, PIN_x, Ts combination signed using the private key PriU corresponding to the UID. Output: Returns the current remaining number of verifiable times (c) for the user’s digital identity PIN_x. At the same time, the current c value is locked, and other service providers other than the input SPID are prohibited from initiating data-sharing requests during this period until the Fetch() function confirms that the current sharing has been completed. Negative constant if PIN_x has not been registered. | GetC() confirms the current remaining number of verification times c of the user’s digital identity PIN_x based on the UID and reserves the current number of verification times c for the SPID in the user’s signature. During this period, only the current SPID can initiate a sharing request for PIN_x until Fetch() function is called and confirms that the sharing is completed. |
| Smart Contract Function Name | Description |
|---|---|
| Add() | As introduced in Table 4 of the digital identity registration stage |
| Request() Input: Accepts one parameter in the format PriSP(UID, Reason, PIN_x, Ts). Output: Returns True on success, False on failure. | When a service provider needs to request a user to add a new category of personal information, the Request() function is initiated on the service provider behavior chain using the specified input format. |
| Vote() Input: Accepts one parameter in the format PriSPn(PubSP(SPnID, UID, Ts)). Output: Returns True on success, False on failure. | When the smart contract function Request() is called, the Vote() smart contract function will automatically initiate a peer review process involving other peer service providers (SP1 to SPn) of the service provider that called the Request() function. For those service providers that approve the application, the Vote() function will be called using the specified input format to cast their votes. |
| SamplingVerification() Input: Accepts 1 parameter in the format PriSRA(PubSC(UID, PIN_x, Reason, LIST, SPID, Ts)) Output: A collection of verification results returned by the service provider being randomly checked. | This function is used by the regulatory agency (RA) to conduct random checks on the service providers who voted in favor of the application to verify whether they actually participated in the vote and approved the application. This function will randomly select some service providers from the LIST that approve the application and ask these service providers to confirm their actual participation in this vote by sending data in the following format: PubSPn(UID, PIN_x, Reason, SPID, Ts) |
| Smart Contract Function Name | Description |
|---|---|
| Delete() Input: Accepts two parameters: the UID and the set of personal information name PIN_x and timestamp signed by the corresponding user’s private key. Output: Returns True on success and False on failure. | This function confirms PubU based on UID and verifies the private key signature. If the verification passes and the timestamp in the signature is within the valid range, the counter c corresponding to the name PIN_x under the UID is set to 0. |
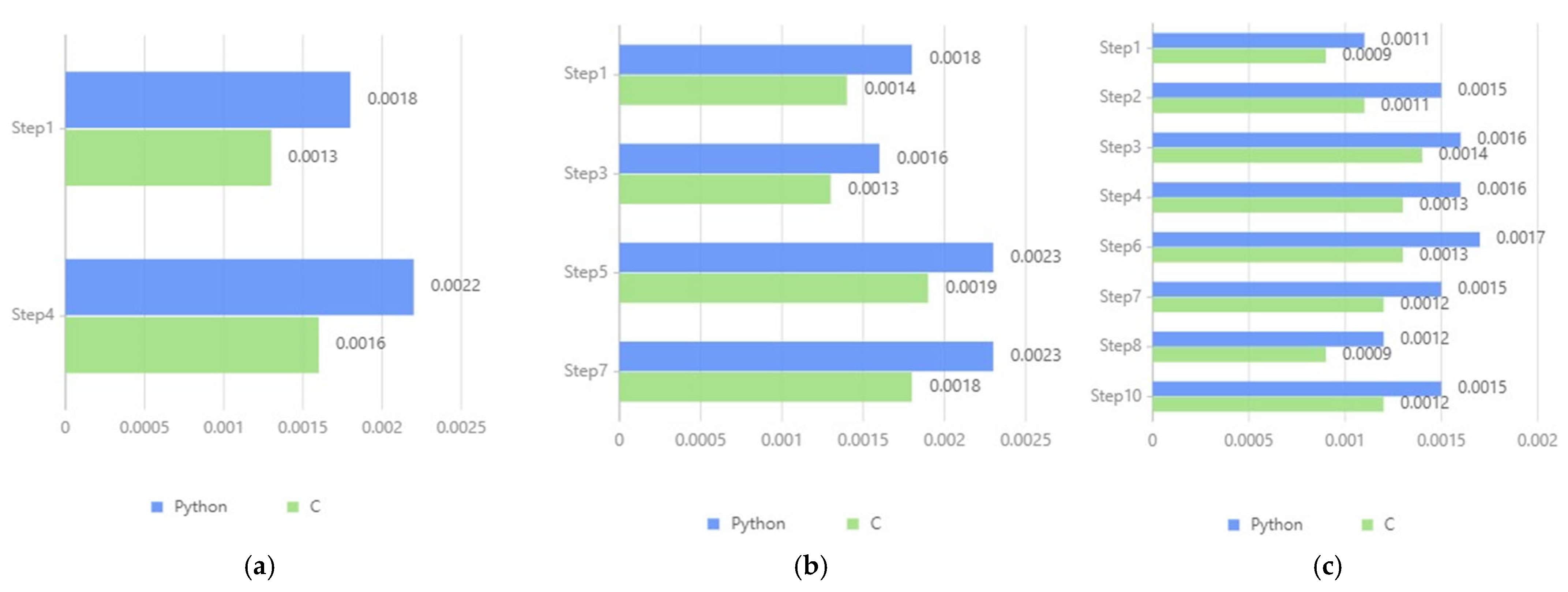
| Stage and Scenario | Steps | Number of Cryptographic Calculations |
|---|---|---|
| Scenario 1 of the Digital Identity Usage Stage | Step 1 | 1 E(2 Params) + 1 DS(1 Param) |
| Step 4 | 1 E(2 Params) + 1 DS(4 Params) | |
| Scenario 2 of the Digital Identity Usage Stage | Step 1 | 1 E(2 Params) + 1 DS(1 Param) |
| Step 3 | 1 E(3 Params) + 1 DS(1 Param) | |
| Step 5 | 1 E(3 Params) + 1 DS(2 Param) | |
| Step 7 | 1 E(2 Params) + 1 DS(4 Params) | |
| Scenario 1 of the Digital Identity Update Stage | Step 1 | 1 DS(4 Params) |
| Step 2 | 1 E(1 Param) + 1 DS(3 Params) | |
| Step 3 | 1 E(5 Params) + 1 DS(1 Param) | |
| Step 4 | 1 E(6 Params) + 1 DS(1 Param) | |
| Step 6 | 1 E(6 Params) + 1 DS(1 Param) | |
| Step 7 | 1 E(6 Params) + 1 DS(1 Param) | |
| Step 8 | 1 DS(5 Params) | |
| Step 10 | 1 E(6 Params) + 1 DS(1 Param) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, J.; Liang, Z.; Lyu, Q. Empowering Privacy Through Peer-Supervised Self-Sovereign Identity: Integrating Zero-Knowledge Proofs, Blockchain Oversight, and Peer Review Mechanism. Sensors 2024, 24, 8136. https://doi.org/10.3390/s24248136
Liu J, Liang Z, Lyu Q. Empowering Privacy Through Peer-Supervised Self-Sovereign Identity: Integrating Zero-Knowledge Proofs, Blockchain Oversight, and Peer Review Mechanism. Sensors. 2024; 24(24):8136. https://doi.org/10.3390/s24248136
Chicago/Turabian StyleLiu, Junliang, Zhiyao Liang, and Qiuyun Lyu. 2024. "Empowering Privacy Through Peer-Supervised Self-Sovereign Identity: Integrating Zero-Knowledge Proofs, Blockchain Oversight, and Peer Review Mechanism" Sensors 24, no. 24: 8136. https://doi.org/10.3390/s24248136
APA StyleLiu, J., Liang, Z., & Lyu, Q. (2024). Empowering Privacy Through Peer-Supervised Self-Sovereign Identity: Integrating Zero-Knowledge Proofs, Blockchain Oversight, and Peer Review Mechanism. Sensors, 24(24), 8136. https://doi.org/10.3390/s24248136






