Security at the Edge for Resource-Limited IoT Devices
Abstract
1. Introduction
- introducing a modular platform for protecting resource-limited IoT devices;
- introducing a transparent security approach for IoT devices (and end-system users);
- introducing an authentication approach based on machine learning techniques (i.e., the oblivious authentication) with no additional computational overhead for the IoT devices.
2. Related Work
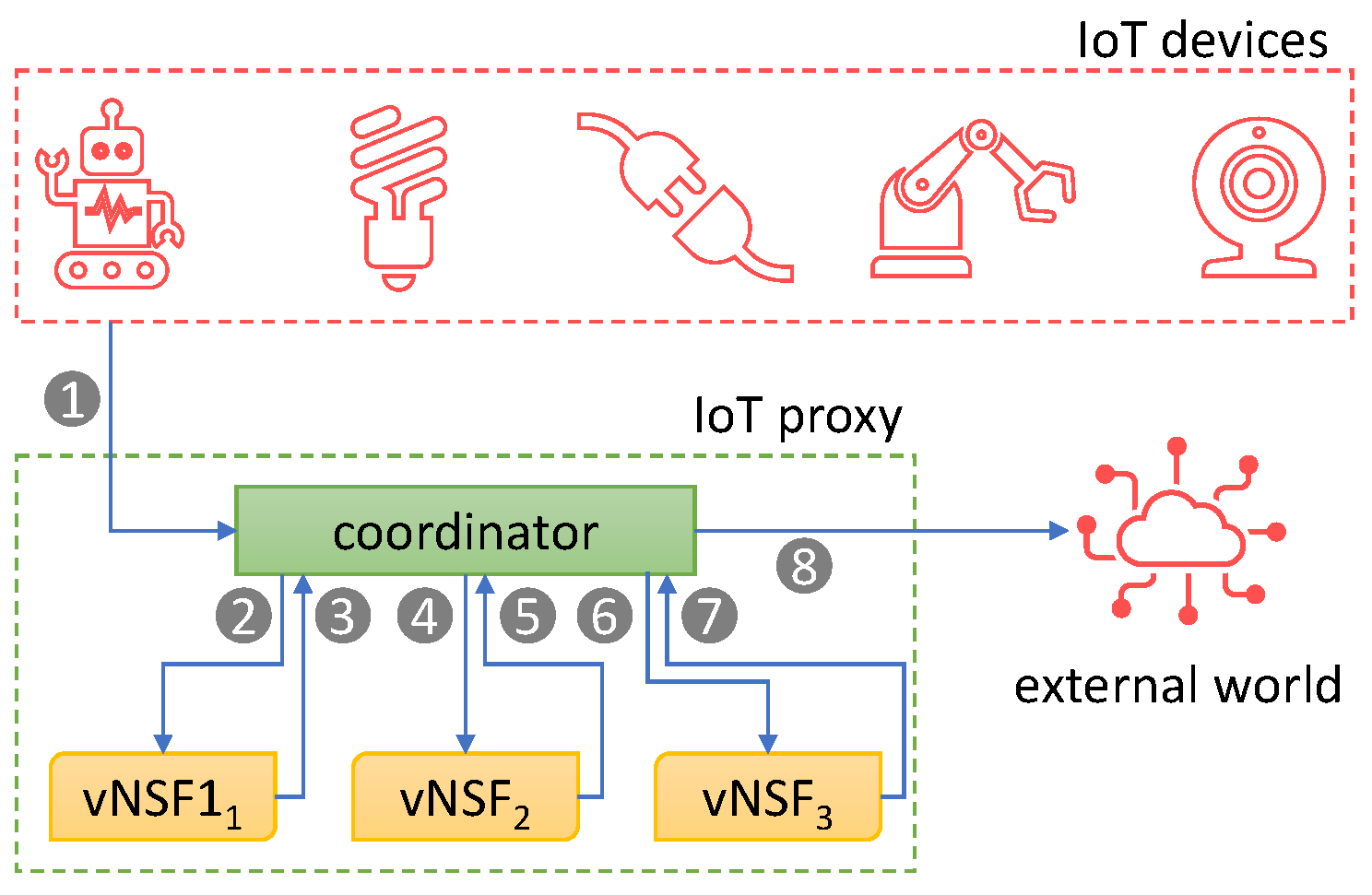
3. Proposed Approach
3.1. VPN vNSF
3.2. IDS/IPS vNSF
- network attack identification, where we detect attacks targeting an IoT device;
- oblivious authentication, where we can spot an IoT device mismatch (e.g., a thermal sensor behaving as a webcam).
- a coarse-grained classifier that distinguishes various attack categories (e.g., brute force, DDoS, DoS, spoofing) and device categories (i.e., audio, camera, home automation, power outlet), for a total of 15 classes;
- a fine-grained classifier that pinpoints the exact attack (e.g., SYN flood, SQL injection) or device (e.g., Amazon Alexa Echo Dot, Wemo Smart Plug), totaling 80 classes.
4. Experimental Results
4.1. Machine Learning Model Performance
4.1.1. Dataset
- lightning and power outlet connections are the longest ones since these devices are usually online for several minutes or hours;
- recon attacks send very few bytes per connection, and this behavior is consistent with how port and network scanning works;
- Mirai attacks [6] send vast quantities of bytes per connection since they are used to flood devices;
- DoS attacks send many TCP SYN packets since many of these attacks try to open as many channels as possible;
- DDoS attacks have a long PIAT since many of these attacks try to cause congestion by deliberately opening slow connections.
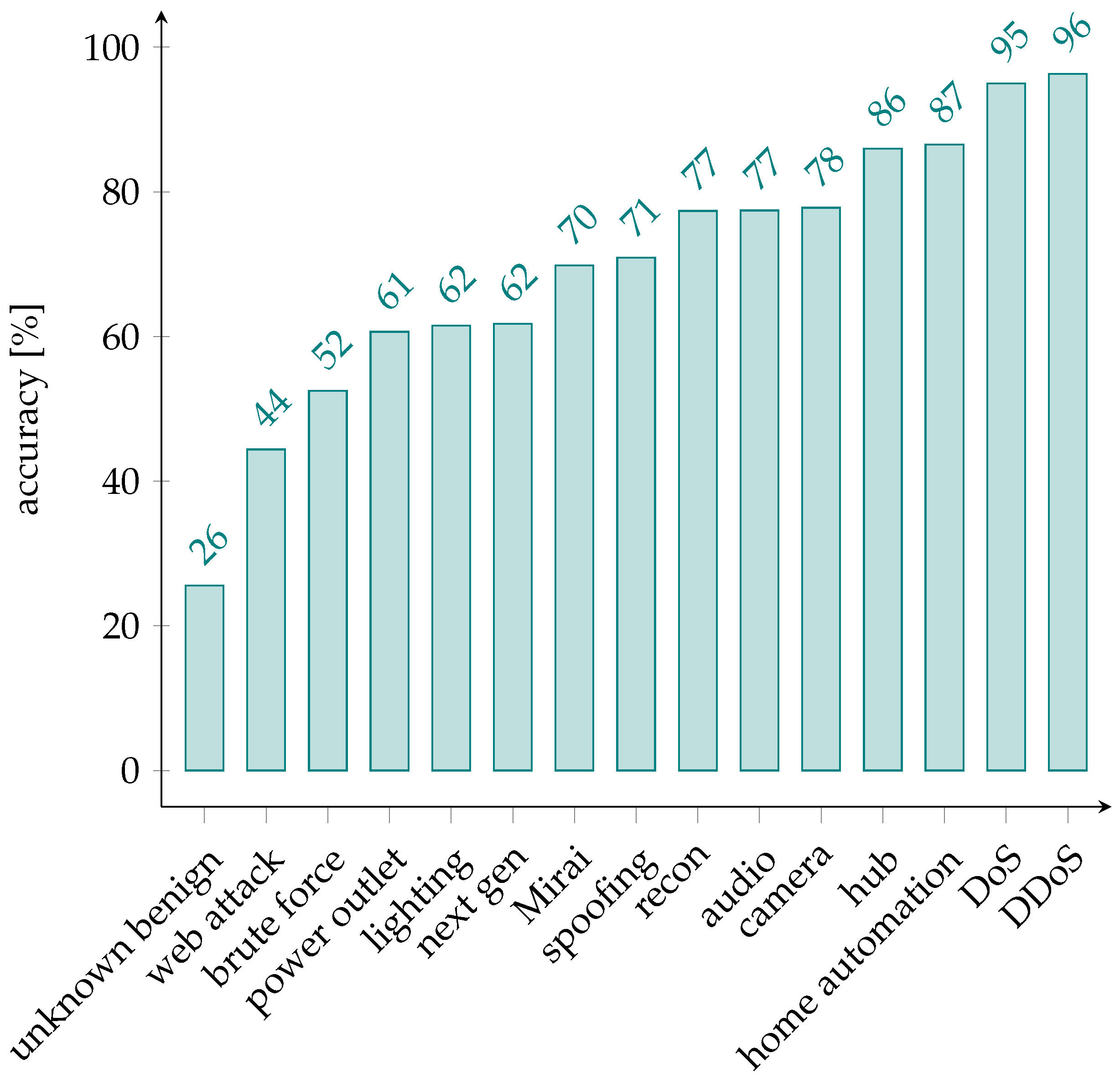
4.1.2. Coarse-Grained Classifier
4.1.3. Fine-Grained Classifier
4.2. Overhead
5. Conclusions
Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AUC | Area Under the Curve |
| CIC | Canadian Institute for Cybersecurity |
| CIoT | Consumer Internet of Things |
| DDoS | Distributed Denial of Service |
| DoS | Denial of Service |
| DPI | Deep Packet Inspection |
| GA | Genetic Algorithm |
| HTTP | Hypertext Transfer Protocol |
| HTTPS | Hypertext Transfer Protocol Secure |
| ICMP | Internet Control Message Protocol |
| IDS | Intrusion Detection System |
| IIoT | Industrial Internet of Things |
| IKE | Internet Key Exchange |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IPsec | Internet Protocol Security |
| IPS | Intrusion Prevention System |
| LSTM | Long Short-Term Memory |
| MAC | Media Access Control |
| NIDS | Network-based Intrusion Detection System |
| PDAE | Parallel Deep Auto-Encoder |
| PIAT | Package Inter-Arrival Time |
| PKI | Public Key Infrastructure |
| QUIC | Quick UDP Internet Connections |
| RF | Random Forest |
| SPI | Shallow Packet Inspection |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| UDP | User Datagram Protocol |
| vNSF | virtual Network Security Function |
| VPN | Virtual Private Network |
References
- Bruegge, F.; Hasan, M.; Kulezak, M.; Lasse Lueth, K.; Pasqua, E.; Sinha, S.; Wegner, P.; Baviskar, K.; Taparia, A. State of IoT—Spring 2023; Technical Report; IoT Analytics GmbH: Hamburg, Germany, 2023. [Google Scholar]
- Kumar, D.; Shen, K.; Case, B.; Garg, D.; Alperovich, G.; Kuznetsov, D.; Gupta, R.; Durumeric, Z. All things considered: An analysis of IoT devices on home networks. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; USENIX Association: Berkeley, CA, USA, 2019; pp. 1169–1185. [Google Scholar]
- Langiu, A.; Boano, C.A.; Schuß, M.; Römer, K. UpKit: An Open-Source, Portable, and Lightweight Update Framework for Constrained IoT Devices. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 2101–2112. [Google Scholar] [CrossRef]
- Corno, F.; De Russis, L.; Mannella, L. Helping novice developers harness security issues in cloud-IoT systems. J. Reliab. Intell. Environ. 2022, 8, 261–283. [Google Scholar] [CrossRef]
- Corno, F.; Mannella, L. Security Evaluation of Arduino Projects Developed by Hobbyist IoT Programmers. Sensors 2023, 23, 2740. [Google Scholar] [CrossRef] [PubMed]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the Mirai Botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, USA, 16–18 August 2017; USENIX Association: Berkeley, CA, USA, 2017; pp. 1093–1110. [Google Scholar]
- ETSI, 650, Route des Lucioles, Valbonne—Sophia Antipolis, France. ETSI GS NFV 003 V1.2.1: Network Functions Virtualisation (NFV). 2014. Available online: https://www.etsi.org/deliver/etsi_gs/nfv/001_099/003/01.02.01_60/gs_nf (accessed on 4 October 2023).
- Aman, M.N.; Javaid, U.; Sikdar, B. Security Function Virtualization for IoT Applications in 6G Networks. IEEE Commun. Stand. Mag. 2021, 5, 90–95. [Google Scholar] [CrossRef]
- Coker, G.; Guttman, J.; Loscocco, P.; Herzog, A.; Millen, J.; O’Hanlon, B.; Ramsdell, J.; Segall, A.; Sheehy, J.; Sniffen, B. Principles of remote attestation. Int. J. Inf. Secur. 2011, 10, 63–81. [Google Scholar] [CrossRef]
- Zolotukhin, M.; Hämäläinen, T. On Artificial Intelligent Malware Tolerant Networking for IoT. In Proceedings of the 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Verona, Italy, 27–29 November 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Ortiz, S. Software-defined networking: On the verge of a breakthrough? Computer 2013, 46, 10–12. [Google Scholar] [CrossRef]
- ETSI, 650, Route des Lucioles, Valbonne—Sophia Antipolis, France. NFV Whitepaper: Network Function Virtualization, Issue 1. 2012. Available online: https://portal.etsi.org/nfv/nfv_white_paper.pdf (accessed on 4 October 2023).
- Guizani, N.; Ghafoor, A. A Network Function Virtualization System for Detecting Malware in Large IoT Based Networks. IEEE J. Sel. Areas Commun. 2020, 38, 1218–1228. [Google Scholar] [CrossRef]
- Graves, A. Long Short-Term Memory. In Supervised Sequence Labelling with Recurrent Neural Networks; Springer: Berlin/Heidelberg, Germany, 2012; pp. 37–45. [Google Scholar] [CrossRef]
- Kasongo, S.M. An Advanced Intrusion Detection System for IIoT Based on GA and Tree Based Algorithms. IEEE Access 2021, 9, 113199–113212. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, Opportunities, and Directions. IEEE Trans. Ind. Informatics 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Srinivas, M.; Patnaik, L.M. Genetic algorithms: A survey. Computer 1994, 27, 17–26. [Google Scholar] [CrossRef]
- Kumar, A.; Abhishek, K.; Ghalib, M.; Shankar, A.; Cheng, X. Intrusion detection and prevention system for an IoT environment. Digit. Commun. Networks 2022, 8, 540–551. [Google Scholar] [CrossRef]
- Chen, S.; Zhang, T.; Shi, W. Fog Computing. IEEE Internet Comput. 2017, 21, 4–6. [Google Scholar] [CrossRef]
- Mirkovic, J.; Reiher, P. A Taxonomy of DDoS Attack and DDoS Defense Mechanisms. Acm Sigcomm Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Sunyaev, A. Distributed Ledger Technology. In Internet Computing: Principles of Distributed Systems and Emerging Internet-Based Technologies; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; pp. 265–299. [Google Scholar] [CrossRef]
- Basati, A.; Faghih, M.M. PDAE: Efficient network intrusion detection in IoT using parallel deep auto-encoders. Inf. Sci. 2022, 598, 57–74. [Google Scholar] [CrossRef]
- Khan, W.Z.; Ahmed, E.; Hakak, S.; Yaqoob, I.; Ahmed, A. Edge computing: A survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar] [CrossRef]
- Sharma, R.K.; Pippal, R.S. Malicious Attack and Intrusion Prevention in IoT Network using Blockchain based Security Analysis. In Proceedings of the 2020 12th International Conference on Computational Intelligence and Communication Networks (CICN), Bhimtal, India, 25–26 September 2020; pp. 380–385. [Google Scholar] [CrossRef]
- Dang, Q. Secure Hash Standard. In Federal Information Processing Standards Publication (NIST FIPS); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [Google Scholar] [CrossRef]
- Jiang, C.; Kuang, J.; Wang, S. Home IoT Intrusion Prevention Strategy Based on Edge Computing. In Proceedings of the 2019 IEEE 2nd International Conference on Electronics and Communication Engineering (ICECE), Xi’an, China, 9–11 December 2019; pp. 94–98. [Google Scholar] [CrossRef]
- Raj, J.R.; Srinivasulu, S. Design of IoT Based VPN Gateway for Home Network. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 561–564. [Google Scholar] [CrossRef]
- Upton, E.; Halfacree, G. Raspberry Pi User Guide; John Wiley & Sons: Hoboken, NJ, USA, 2016. [Google Scholar]
- Fan, J.; Wang, Z.; Li, C. Design and Implementation of IoT Gateway Security System. In Proceedings of the 2019 International Conference on Artificial Intelligence and Advanced Manufacturing (AIAM), Dublin, Ireland, 16–18 October 2019; pp. 156–162. [Google Scholar] [CrossRef]
- Frankel, S.; Krishnan, S. IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap. RFC Editor, 2011, number 6071 in Request for Comments. [CrossRef]
- Rescorla, E. The Transport Layer Security (TLS) Protocol Version 1.3. RFC Editor, 2018, number 8446 in Request for Comments.
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Subaschandrabose, N.; Ye, Z. Secure the Internet of Things with challenge response authentication in fog computing. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017. [Google Scholar]
- Zedak, C.; Lekbich, A.; Belfqih, A.; Boukherouaa, J.; Haidi, T.; El Mariami, F. A proposed secure remote data acquisition architecture of photovoltaic systems based on the Internet of Things. In Proceedings of the 2018 6th International Conference on Multimedia Computing and Systems (ICMCS), Rabat, Morocco, 10–12 May 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Combe, T.; Martin, A.; Di Pietro, R. To Docker or Not to Docker: A Security Perspective. IEEE Cloud Comput. 2016, 3, 54–62. [Google Scholar] [CrossRef]
- Corno, F.; Mannella, L. A Gateway-based MUD Architecture to Enhance Smart Home Security. In Proceedings of the 2023 8th International Conference on Smart and Sustainable Technologies (SpliTech), Split/Bol, Croatia, 20–23 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Lear, E.; Droms, R.; Romascanu, D. Manufacturer Usage Description Specification. RFC Editor, 2019, number 8520 in Request for Comments. [CrossRef]
- Boeyen, S.; Santesson, S.; Polk, T.; Housley, R.; Farrell, S.; Cooper, D. Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. RFC Editor, 2008, number 5280 in Request for Comments. [CrossRef]
- Kaufman, C.; Hoffman, P.E.; Nir, Y.; Eronen, P.; Kivinen, T. Internet Key Exchange Protocol Version 2 (IKEv2). RFC Editor, 2014, number 7296 in Request for Comments. [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Eddy, W. Transmission Control Protocol (TCP). RFC Editor, 2022, number 9293 in Request for Comments. [CrossRef]
- Iyengar, J.; Thomson, M. QUIC: A UDP-Based Multiplexed and Secure Transport. RFC 9000, 2021. [CrossRef]
- Postel, J.B. Internet Control Message Protocol. RFC Editor, 1981, number 792 in Request for Comments. [CrossRef]
- Berbecaru, D.G.; Giannuzzi, S.; Canavese, D. Autoencoder-SAD: An Autoencoder-based Model for Security Attacks Detection. In Proceedings of the 2023 IEEE Symposium on Computers and Communications (ISCC), Gammarth, Tunisia, 9–12 July 2023; pp. 758–763. [Google Scholar] [CrossRef]
- Canavese, D.; Regano, L.; Basile, C.; Ciravegna, G.; Lioy, A. Encryption-agnostic classifiers of traffic originators and their application to anomaly detection. Comput. Electr. Eng. 2022, 97, 107621. [Google Scholar] [CrossRef]
- Canavese, D.; Regano, L.; Basile, C.; Ciravegna, G.; Lioy, A. Data set and machine learning models for the classification of network traffic originators. Data Brief 2022, 41, 107968. [Google Scholar] [CrossRef] [PubMed]
- Basile, C.; Canavese, D.; Regano, L.; Pedone, I.; Lioy, A. A model of capabilities of Network Security Functions. In Proceedings of the 2022 IEEE 8th International Conference on Network Softwarization (NetSoft), Milan, Italy, 27 June–1 July 2022; pp. 474–479. [Google Scholar] [CrossRef]
| 1 | https://fishy-project.eu/, accessed on 2 October 2023. |
| 2 | https://www.eeas.europa.eu/eeas/horizon-2020_en, accessed on 2 October 2023. |
| 3 | https://www.strongswan.org/, accessed on 3 October 2023. |
| 4 | See note 3 above. |
| 5 | https://www.nfstream.org/, accessed on 6 October 2023. |
| 6 | https://scikit-learn.org/, accessed on 6 October 2023. |
| 7 | https://www.unb.ca/cic/datasets/iotdataset-2023.html, accessed on 7 October 2023. |
| 8 | The balanced accuracy of a 15-class classifier is . |
| 9 | https://iperf.fr/, accessed on 14 November 2023. |


| Description | Unit | Global | Sent | Received |
|---|---|---|---|---|
| flow duration | ms | √ | √ | √ |
| packet count | packet | √ | √ | √ |
| byte count | byte | √ | √ | √ |
| minimum packet size | byte | √ | √ | √ |
| mean packet size | byte | √ | √ | √ |
| st. deviation of packet size | byte | √ | √ | √ |
| maximum packet size | byte | √ | √ | √ |
| minimum inter-arrival time | ms | √ | √ | √ |
| mean inter-arrival time | ms | √ | √ | √ |
| st. deviation of inter-arrival time | ms | √ | √ | √ |
| maximum inter-arrival time | ms | √ | √ | √ |
| TCP packets with SYN set | packet | √ | √ | √ |
| TCP packets with CWR set | packet | √ | √ | √ |
| TCP packets with ECE set | packet | √ | √ | √ |
| TCP packets with ACK set | packet | √ | √ | √ |
| TCP packets with PSH set | packet | √ | √ | √ |
| TCP packets with RST set | packet | √ | √ | √ |
| TCP packets with FIN set | packet | √ | √ | √ |
| use of IPv4 | boolean | √ | - | - |
| use of IPv6 | boolean | √ | - | - |
| use of TCP | boolean | √ | - | - |
| use of UDP | boolean | √ | - | - |
| use of ICMP | boolean | √ | - | - |
| Protocol | IPv4 | IPv6 |
|---|---|---|
| TCP | 124,028,344 | 6 |
| UDP | 4,878,325 | 46,212 |
| ICMP | 89,958 | 0 |
| other | 14,065 | 35,330 |
| total | 129,010,692 | 81,564 |
| (a) Benign traffic. | |
| Category | Flows |
| audio | 48,717 |
| camera | 126,364 |
| home automation | 10,630 |
| hub | 20,252 |
| lighting | 1323 |
| next-gen | 173 |
| power outlet | 2140 |
| unknown | 297,238 |
| total | 507,002 |
| (b) Malicious traffic. | |
| Category | Flows |
| brute force | 6452 |
| DDoS | 118,780,042 |
| DoS | 7,978,026 |
| Mirai | 512,905 |
| recon | 1,141,540 |
| spoofing | 147,823 |
| web attack | 18,466 |
| total | 128,585,254 |
| Category | Duration [ms] | Bytes | PIAT [ms] | SYN Packets |
|---|---|---|---|---|
| audio | 79,819.59 | 7257.89 | 1481.24 | 0.55 |
| brute force | 45,737.65 | 5662.02 | 1689.59 | 0.93 |
| camera | 31,344.17 | 44,393.27 | 806.44 | 0.22 |
| DDoS | 318,543.99 | 2314.38 | 22,238.50 | 6.40 |
| DoS | 427,393.55 | 7751.54 | 8180.93 | 24.55 |
| home automation | 120,800.44 | 6186.60 | 2436.34 | 0.51 |
| hub | 67,226.78 | 3951.05 | 2446.75 | 0.41 |
| lighting | 942,282.45 | 20,572.59 | 12,207.54 | 0.37 |
| Mirai | 23,256.00 | 288,397.63 | 1785.00 | 0.93 |
| next-gen | 1878.77 | 79,213.42 | 232.80 | 0.04 |
| power outlet | 693,913.67 | 14,842.67 | 7144.68 | 0.28 |
| recon | 12,464.81 | 1447.62 | 499.59 | 0.89 |
| spoofing | 32,446.62 | 24,107.19 | 3053.01 | 0.34 |
| unknown | 50,424.88 | 22,804.24 | 1303.65 | 0.49 |
| web attack | 33,310.13 | 5133.73 | 3222.72 | 0.43 |
| Statistic | Value [%] |
|---|---|
| accuracy | 95.72817533754541 |
| balanced accuracy | 69.56422432885422 |
| AUC | 96.51575656890216 |
| F-score (macro) | 35.80059247737348 |
| recall (macro) | 69.56422432885422 |
| precision (macro) | 28.473269071998175 |
| Statistic | Value [%] |
|---|---|
| accuracy | 96.0684655558229 |
| balanced accuracy | 60.3814098614751 |
| AUC | 94.34290472146797 |
| F-score (macro) | 33.337772924857084 |
| recall (macro) | 60.3814098614751 |
| precision (macro) | 28.746583759039684 |
| Component | Version |
|---|---|
| operating system | GNU/Linux Ubuntu 20.04.1 |
| kernel | 5.15.0-72-generic |
| Python | 3.8.10 |
| Docker | 20.10.21 (build baeda1f) |
| docker-compose | 1.25.0 |
| scikit-learn | 1.1.0 |
| CPU | Intel® Core™ i7-1065G7 CPU @ 1.30GHz |
| RAM | 8 GiB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Canavese, D.; Mannella, L.; Regano, L.; Basile, C. Security at the Edge for Resource-Limited IoT Devices. Sensors 2024, 24, 590. https://doi.org/10.3390/s24020590
Canavese D, Mannella L, Regano L, Basile C. Security at the Edge for Resource-Limited IoT Devices. Sensors. 2024; 24(2):590. https://doi.org/10.3390/s24020590
Chicago/Turabian StyleCanavese, Daniele, Luca Mannella, Leonardo Regano, and Cataldo Basile. 2024. "Security at the Edge for Resource-Limited IoT Devices" Sensors 24, no. 2: 590. https://doi.org/10.3390/s24020590
APA StyleCanavese, D., Mannella, L., Regano, L., & Basile, C. (2024). Security at the Edge for Resource-Limited IoT Devices. Sensors, 24(2), 590. https://doi.org/10.3390/s24020590








