Post-Quantum Secure Identity-Based Signature Scheme with Lattice Assumption for Internet of Things Networks
Abstract
1. Introduction
- A security model is constructed with blockchain and the PQ-IDS algorithm for IoT network applications. This model divides the IoT network into three layers: perceptual, network, and application, which help to establish a distributed and secure data-sharing mechanism for IoT network applications.
- A PQ-IDS scheme is proposed based on lattice assumption, and it inserts the IoT device’s identity into the signature scheme to achieve the traceability of IoT data sharing among the IoT network. This scheme helps to achieve anti-quantum attack security with the lattice cryptography theories.
- Security analysis and proof about the correctness, unforgeability, non-repudiation, traceability, and post-quantum security are presented. The performance evaluations of key-size data-sharing transactions are presented. These results show the efficiency and practicality of the proposed security model and PQ-IDS scheme.
2. Related Work
2.1. IoT Network Security
2.2. Signatures for IoT Networks
3. Preliminaries
3.1. Lattice Theory
3.2. Model Definitions
- (1)
- Scheme model
- Setup(): Given a security parameter n and parameters q and m, KGC derives some public parameters and the master key .
- KeyExt(): Given the public parameters and the master key , KGC generates public/private key pairs for the system user with identity .
- Sign(): The signer generates a signature e in relation to a with message with his own private key .
- Verify(): The verifier verifies the e’s legality with and , and output .
- (2)
- Security model
- Initialize: C executes the Setup algorithm to derive the system .
- Query: A queries the Hash, secret key, and signature algorithms with enough times in polynomial time, respectively.
- −
- Hash query: A queries all hash algorithms about the user or message (not the target user and message ).
- −
- Secret key query: A queries the private key about the user (not the target user ).
- −
- Signature query: AA queries the signature about the user or message (not the target user and message ).
- Forge: A generates a signature about the target user and message , and sends it to C.
- Challenge: C generates another signature about the target user and message based on the hypothesis. Then, C attempts to derive a solution for the instance by utilizing these two signatures and .
- Analyze: The lattice assumption cannot be solved with the current highest computing power. This implies that the hypothesis of the former adversary A is invalid.
4. PQ-IDS for IoT Network Applications
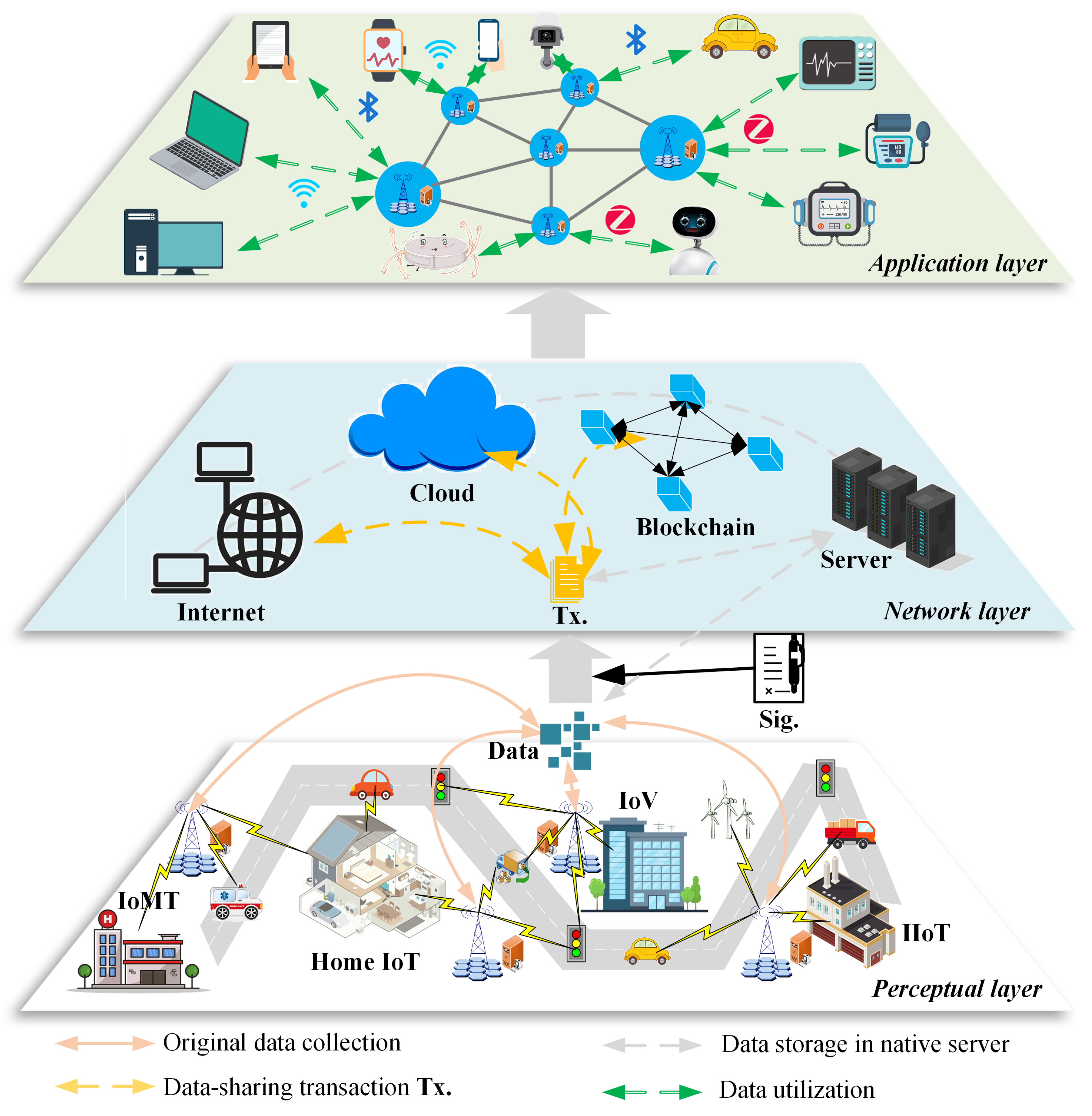
4.1. Security Model for IoT Network Application
- Perceptual layer: This layer is a data collection process. From different smart IoT devices, many types of data are selected. These data mainly appear in text, figure, and video forms. As in the IoMT environment, the medical data generally contain health data collected from wearable smart devices, diagnosis data created by patients and doctors, testing data generated by medical devices, and other related data about health insurance, banking, etc. In the Home IoT environment, the data are collected from smart home devices, such as door locks, cameras, refrigerators, washing machines, sweepers, smart speakers, air purifiers, etc. As in the IoV environment, the data are collected from smart vehicles, road detection, cameras, traffic lights, etc. In the IIoT environment, the data are collected from logistics trucks, wind-generating sets, and other related industrial devices. These collected data are signed with the signatures of IoT devices or device owners. The identities inserted in these signatures guarantee the data verifiability and traceability by utilizing the PQ-IDS scheme.
- Network layer: This layer is a data transmission process. The selected data are transmitted through the public network, such as the Internet, cloud, or blockchain. Under the help of communication protocol, these data are transmitted into the transaction , and they also contain the signatures of IoT devices or device owners. Through those public networks, these transactions go to the node that needs them. Meanwhile, it needs a server with enough storage space for data storage and management. The Internet and cloud networks are generally public, which cannot provide a strong security guarantee for cross-domain data sharing. Blockchain technology changes the traditional centralized form to a distributed form, which improves data-sharing transparency and cross-institution data-sharing ability. As in blockchain-based IoT networks, the system transaction verification also can be executed by the PQ-IDS to achieve network-wide consistency. Some security issues of data tampering, malicious theft, and other network attacks generally occur in this layer.
- Application layer: This is a data-utilizing process. A number of IoT devices are included in the IoT network, which continuously performs data exchange and processing. The collection, storage, calculation, and analysis of massive data support different IoT application purposes for people’s daily lives. For example, IoV data can solve some complex problems in traffic. On the one hand, the data can help understand the traffic flow situation, and improve the driving route for the vehicle owner; On the other hand, the data can also provide decision making for the traffic department in the aspects of road planning, real-time scheduling of signal lights, and vehicle diversion. More importantly, the PQ-IDS scheme plays an essential role in guaranteeing data credibility. This is because the operations throughout the life cycle of the data are recorded, and the identity information of all operators can be traced through signature verification.
4.2. Details of PQ-IDS
| Algorithm 1 Setup |
Input: Security parameter κ, a prime number q, a positive integer m Output: Public parameter pp and master key msk
|
| Algorithm 2 KeyExt |
Input: , , and system user’s identity Output: Key pairs
|
| Algorithm 3 Sign |
Input: Message , system public key A, signer’s private key Output: Signature e
|
| Algorithm 4 Verify |
Input: , , and Output: Reject or accept
|
4.3. Example Application
- Data collection: Through smart medical devices, the daily health data and hospital test data are collected and uploaded to the IoMT system. To establish a traceability mechanism, the medical data are labeled with the signatures of related IoMT devices or operators.
- Data storage: In the blockchain-based IoMT system, the real data are stored in the native server. The storage address, operation records, and other related lightweight information are uploaded into the blockchain ledger.
- Transaction request: When one patient wants to authorize the doctor to view their health data, they execute a transaction request. This situation is a process of seeing a doctor or scientific research as one user attempts to share data with the other system user. This transaction only sends authorization for these data and the target user must pass this authentication before they can access control on the real medical data.
- Transaction signature: Based on the former proposed PQ-IDS scheme, this patient signs the transaction with their private key . This signature is a proof that other users confirm the data’s validity by opening it. Meanwhile, this patient cannot deny this signature when some medical disputes occur.
- Transaction verification: This is the process of verifying the consistency of blockchain transactions across the network. The packaged transactions are sent to the verification nodes who check the legality of the transactions and sign them. The verification process is according to the consensus protocol proof of work (PoW) or proof of stake (PoS).
- Transaction Broadcast: The verified transactions will be broadcast to all the nodes in the IoMT network. This process mainly synchronizes the ledger across the network, but it also needs to obtain the access control rights of the real data before the target user can view the original data.
- Transaction storage: These transaction data belong to lightweight information, which is recorded in the blockchain ledger. This blockchain ledger is public and immutable, guaranteeing the transaction data’s security and traceability.
- Signature verification: The target user (doctor) first verifies the signature of the transaction originator.
- Data utilization: These medical data can be used for disease diagnosis, drug discovery, medical research, and medical device development.
5. Security Analysis
5.1. Correctness
5.2. Unforgeability
- Initialize: C performs the Setup algorithm to derive .
- Query: A queries the Hash, secret key, and signature algorithms with enough times in polynomial time, respectively.
- −
- query: A queries the hash function about the user’s identity . Next, C keeps a list to store these query results. When they obtain the queries from A, C first checks the list whether the result pair exists or not. If yes, they send to A as the response of ’s query about . If no, they compute , send to A, and record in the list . Here, A can execute this query with enough times about different identities .
- −
- query: A queries the hash function about the message (is not the target message ). Next, C keeps a list to store these query results. When they obtain the queries from A, C first checks the list whether the result pair exists or not. If yes, they send to A as the response of ’s query about . If no, they randomly choose , compute , send to A, and record in the list . Here, A can execute this query with enough times about different messages .
- −
- Private key query: A queries the private key of the user (is not the target user ). Next, C keeps a list to store these query results. When they obtain the queries from A, C first checks the list whether the result pair exists or not. If yes, they send to A as the response of a private key query about . If no, they compute , sends to A, and records in the list . Here, A can execute this query with enough times about different identities .
- −
- Signature query: A queries the signature of the user about the message (is not the target message and user ). Next, C keeps a list to store these query results. When they obtain the queries from A, C first checks the list whether the result pair exists or not. If yes, they send to A as the response of a private key query about . If no, they execute the Hash algorithm to obtain , compute , send to A, and record in the list . Here, A can execute this query with enough times about different identities and different messages .
- Forge: A utilizes the former received information to generate a valid signature about the target user and message . Then, they send this forged signature to C.
- Challenge: C utilizes the forking lemma to generate the other valid signature about the target user and message . Here, C utilizes the same selected . Then, it hasWith the same Hash function and message , it hasIt also hasBecause of , it has with overwhelming probability. Hence, it can derive a solution for instance as shown in the following Equation (9).
- Analyze: In the common sense, the lattice assumption is not solved with the current highest computing power. This implies that the hypothesis of the former adversary A is invalid. Meanwhile, from the former query processes, A can create a valid signature with the probability . With the query times , , , and increasing, this probability will decrease to 0.
5.3. Non-Repudiation and Traceability
- Non-repudiation 1: The data-sharing transactions are all signed by related workers from the collection to processing and storage. These signatures are signed with the workers’ private keys , and they can be verified by anyone with their public keys . So, the workers cannot deny when the signatures pass the verification.
- Non-repudiation 2: The private key is generated by , and the user’s public key is generated by where the is the personal identity, such as identity number, email address, phone number, etc. The personal information guarantees that the signature cannot be denied.
- Traceability 1: This identity signature mechanism guarantees the traceability of IoT data exchange processes as the related workers will be traced by opening the corresponding signature when some security incidents occur.
- Traceability 2: The blockchain technology provides an immutable public ledger for the records of IoT data storage and operational processes, which guarantees traceability for data sharing in different IoT networks. Once some disputes occur, it can find all the operation records and related operators by opening the signatures.
5.4. Post-Quantum Security
6. Comparison and Performance
6.1. Efficiency Comparison
6.2. Performance Evaluation
- (1)
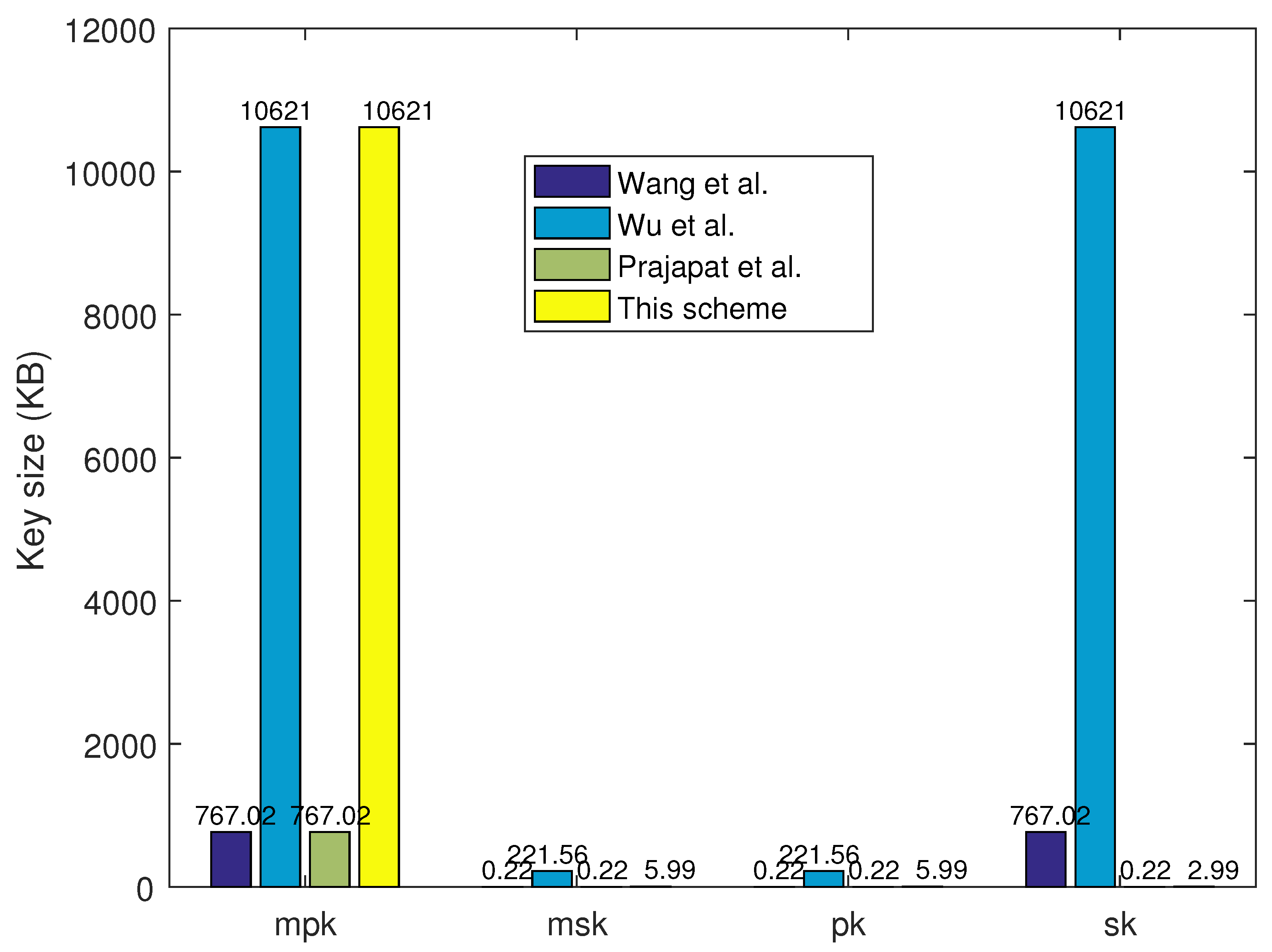
- Key size evaluation
- (2)
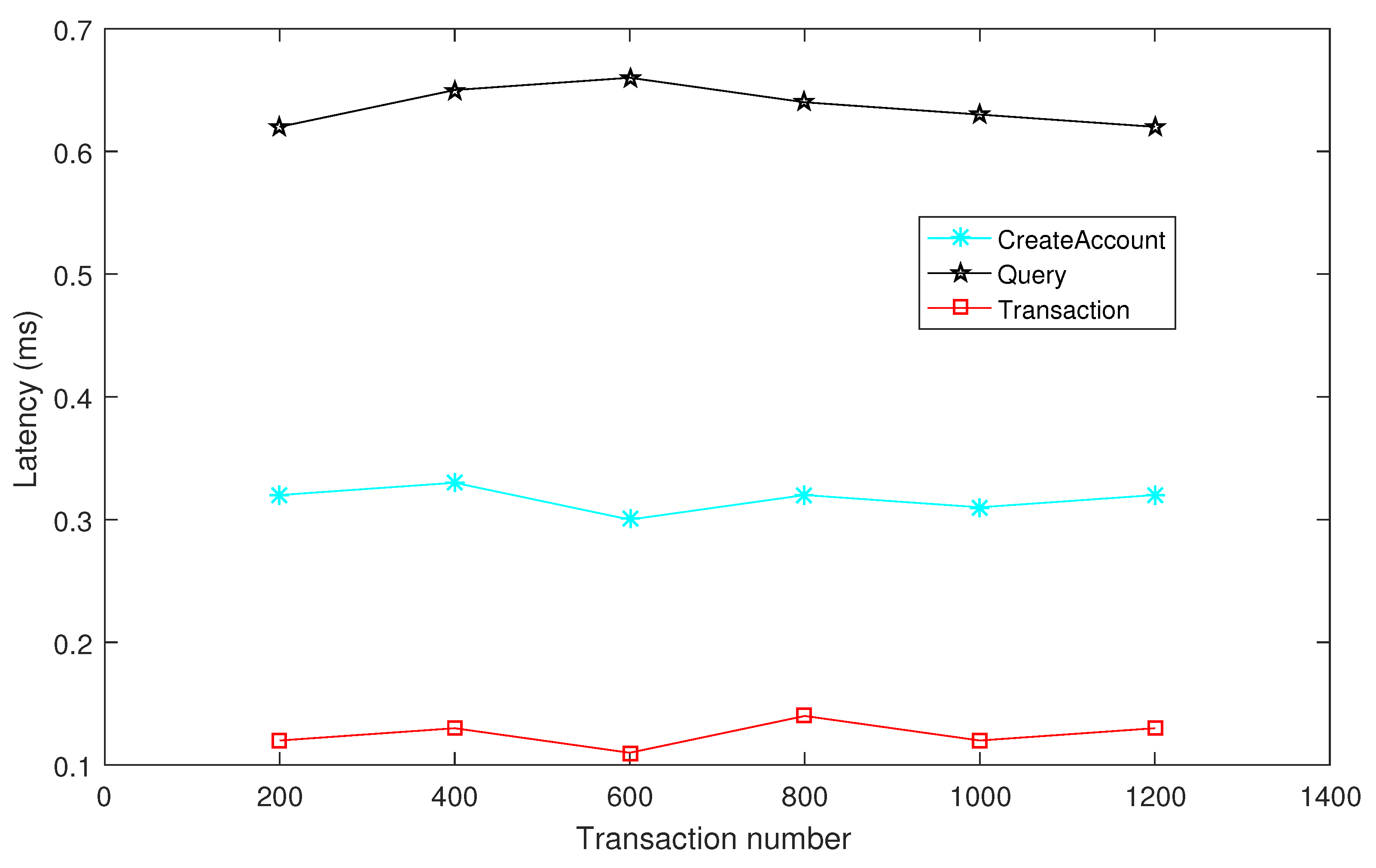
- Transaction performance for IoT data sharing
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Laghari, A.A.; Wu, K.; Laghari, R.A.; Ali, M.; Khan, A.A. A review and state of art of Internet of Things (IoT). Arch. Comput. Methods Eng. 2021, 29, 1395–1413. [Google Scholar] [CrossRef]
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Arshad, H. The Internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Zolanvari, M.; Unal, D.; Al-Ali, A.; Jain, R. Recent advances in the internet-of-medical-things (IoMT) systems security. IEEE Internet Things J. 2020, 8, 8707–8718. [Google Scholar] [CrossRef]
- Philip, N.Y.; Rodrigues, J.J.; Wang, H.; Fong, S.J.; Chen, J. Internet of Things for in-home health monitoring systems: Current advances, challenges and future directions. IEEE J. Sel. Areas Commun. 2022, 39, 300–310. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Din, S.; Jeon, G.; Piccialli, F. Internet of vehicles: Key technologies, network model, solutions and challenges with future aspects. IEEE Trans. Intell. Transp. Syst. 2020, 22, 1777–1786. [Google Scholar] [CrossRef]
- Serror, M.; Hack, S.; Henze, M.; Schuba, M.; Wehrle, K. Challenges and opportunities in securing the industrial Internet of things. IEEE Trans. Ind. Inform. 2020, 17, 2985–2996. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24 October 2016; pp. 3–16. [Google Scholar]
- Saleh, F. Blockchain without waste: Proof-of-stake. Rev. Financ. Stud. 2021, 34, 1156–1190. [Google Scholar] [CrossRef]
- Nechvatal, J.; Barker, E.; Bassham, L.; Burr, W.; Dworkin, M.; Foti, J.; Roback, E. Report on the development of the Advanced Encryption Standard (AES). J. Res. Natl. Inst. Stand. Technol. 2001, 106, 511. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A. Elliptic curve cryptography. In Encyclopedia of Cryptography, Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2021; pp. 1–2. [Google Scholar]
- Hellman, M.E. An overview of public key cryptography. IEEE Commun. Mag. 2002, 40, 42–49. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef]
- Micciancio, D.; Regev, O. Lattice-based cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 147–191. [Google Scholar]
- Peikert, C. Public-key cryptosystems from the worst-case shortest vector problem. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Washington, DC, USA, 31 May–2 June 2009; pp. 333–342. [Google Scholar]
- Nguyen, P.Q.; Regev, O. Learning a parallelepiped: Cryptanalysis of GGH and NTRU signatures. J. Cryptol. 2009, 22, 139–160. [Google Scholar] [CrossRef]
- Brakerski, Z.; Langlois, A.; Peikert, C.; Regev, O.; Stehlé, D. Classical hardness of learning with errors. In Proceedings of the Forty-Fifth Annual ACM Symposium on Theory of Computing, Palo Alto, CA, USA, 1–4 June 2013; pp. 575–584. [Google Scholar]
- Rehman, Z.; Gondal, I.; Ge, M.; Dong, H.; Gregory, M.; Tari, Z. Proactive defense mechanism: Enhancing IoT security through diversity-based moving target defense and cyber deception. Comput. Secur. 2024, 139, 103685. [Google Scholar] [CrossRef]
- Xu, G.; Zhou, Z.; Dong, J.; Zhang, L.; Song, X. A blockchain-based federated learning scheme for data sharing in industrial internet of things. IEEE Internet Things J. 2023, 10, 21467–21478. [Google Scholar] [CrossRef]
- Singh, R.; Dwivedi, A.D.; Srivastava, G.; Chatterjee, P.; Lin, J.C.W. A privacy preserving Internet of things smart healthcare financial system. IEEE Internet Things J. 2023, 10, 18452–18460. [Google Scholar] [CrossRef]
- Zhang, X.; Hao, L.; Gui, G.; Wang, Y.; Adebisi, B.; Sari, H. An automatic and efficient malware traffic classification method for secure Internet of Things. IEEE Internet Things J. 2023, 11, 8448–8458. [Google Scholar] [CrossRef]
- Li, T.; Zhang, J.; Shen, Y.; Ma, J. Hierarchical and multi-group data sharing for cloud-assisted industrial internet of things. IEEE Trans. Serv. Comput. 2023, 16, 3425–3438. [Google Scholar] [CrossRef]
- Malik, M.; Dutta, M. Feature engineering and machine learning framework for DDoS attack detection in the standardized Internet of things. IEEE Internet Things J. 2023, 10, 8658–8669. [Google Scholar]
- Khanday, S.A.; Fatima, H.; Rakesh, N. Implementation of intrusion detection model for DDoS attacks in Lightweight IoT Networks. Expert Syst. Appl. 2023, 215, 119330. [Google Scholar] [CrossRef]
- Mehmood, M.; Amin, R.; Muslam, M.M.; Xie, J.; Aldabbas, H. Privilege escalation attack detection and mitigation in cloud using machine learning. IEEE Access 2023, 11, 46561–46576. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Cui, M.; Li, K.C.; Souri, A.; Shojafar, M. IdenMultiSig: Identity-based decentralized multi-signature in Internet of things. IEEE Trans. Comput. Soc. Syst. 2023, 10, 1711–1721. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Liu, Q.; Choo, K.K.R. An efficient provably-secure certificateless signature scheme for Internet-of-Things deployment. Ad Hoc Networks 2018, 71, 78–87. [Google Scholar] [CrossRef]
- Du, H.; Wen, Q.; Zhang, S.; Gao, M. A new provably secure certificateless signature scheme for Internet of Things. Ad Hoc Networks 2020, 100, 102074. [Google Scholar] [CrossRef]
- Li, T.; Wang, H.; He, D.; Yu, J. Permissioned blockchain-based anonymous and traceable aggregate signature scheme for industrial internet of things. IEEE Internet Things J. 2020, 8, 8387–8398. [Google Scholar] [CrossRef]
- Bao, Z.; He, D.; Khan, M.K.; Luo, M.; Xie, Q. PBidm: Privacy-Preserving Blockchain-Based Identity Management System for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 19, 1524–1534. [Google Scholar] [CrossRef]
- Cheng, C.; Lu, R.; Petzoldt, A.; Takagi, T. Securing the Internet of things in a quantum world. IEEE Commun. Mag. 2017, 55, 116–120. [Google Scholar] [CrossRef]
- Srivastava, V.; Debnath, S.K.; Bera, B.; Das, A.K.; Park, Y.; Lorenz, P. Blockchain-envisioned provably secure multivariate identity-based multi-signature scheme for Internet of Vehicles environment. IEEE Trans. Veh. Technol. 2022, 71, 9853–9867. [Google Scholar] [CrossRef]
- Wang, L.; Huang, C.; Cheng, H. Novel proxy signature from lattice for the post-quantum Internet of Things. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 9939–9946. [Google Scholar] [CrossRef]
- Wu, F.; Zhou, B.; Zhang, X. Identity-based proxy signature with message recovery over NTRU lattice. Entropy 2023, 25, 454. [Google Scholar] [CrossRef]
- Prajapat, S.; Gautam, D.; Kumar, P.; Jangirala, S.; Das, A.K.; Park, Y.; Lorenz, P. Secure lattice-based aggregate signature scheme for vehicular Ad Hoc networks. IEEE Trans. Veh. Technol. 2024. Available online: https://ieeexplore.ieee.org/abstract/document/10487896 (accessed on 25 June 2024).
- Sun, L.; Wang, Y.; Ren, Y.; Xia, F. Path signature-based xai-enabled network time series classification. Sci. China Inf. Sci. 2024, 1–15. [Google Scholar]
- Ducas, L.; Durmus, A.; Lepoint, T.; Lyubashevsky, V. Lattice signatures and bimodal Gaussians. In Advances in Cryptology, Proceedings of the CRYPTO 2013: Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1–41, 40–56. [Google Scholar]


| Scheme | IoT Network | Main Technology | Limitation | Anti-Quantum |
|---|---|---|---|---|
| Liu et al. [26] | IoT | ID multi-signature; Threshold Merkle tree; Consortium blockchain | Identity traceability lack | No |
| Jia et al. [27] | IoT | Certificateless signature; ECC | Identity traceability lack; Centralized management | No |
| Du et al. [28] | IoT | Certificateless signature; ECC; Security authentication technology | Identity traceability lack; Centralized management | No |
| Li et al. [29] | IIoT | Aggregate signature; Permissioned blockchain; Smart contract | Identity traceability lack; Data openness; Centralized like management | No |
| Bao et al. [30] | IIoT | Identity management; Permissioned blockchain; Smart contract | Data openness; Centralized like management | No |
| Srivastava et al. [32] | IoV | ID multi-signature; Blockchain; Cloud server network | Efficiency to be improved | No |
| Wang et al. [33] | IoT | Proxy signature; Fixed dimension lattice basis delegation; Preimage sample | Identity traceability lack; Centralized management; Efficiency to be improved | No |
| Wu et al. [34] | IoT | ID proxy signature; NTRU lattice; Message recovery; Blockchain | Efficiency to be improved | Yes |
| Prajapat et al. [35] | VANETs | ID aggregate signature; Vehicle pseudo-identities; Cloud storage | Centralized management; Efficiency to be improved | Yes |
| Sun et al. [36] | XAI network | Path signature; Time series classification | Identity traceability lack; Centralized management | No |
| This paper | General IoT | ID signature; LWE lattice; Blockchain; Gaussian distribution | Efficiency to be improved | Yes |
| Notation | Meaning |
|---|---|
| n | Security parameter |
| q | A prime number |
| m | A positive integer with |
| L | Threshold parameter |
| The standard deviation | |
| Public parameter | |
| Muster secret key | |
| User i’s identity | |
| The bimodal Gaussian distribution | |
| User’s public key | |
| User’s private key | |
| The cryptographic Hash function | |
| The message |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Y.; Tang, Y.; Li, C.; Zhang, H.; Ahmad, H. Post-Quantum Secure Identity-Based Signature Scheme with Lattice Assumption for Internet of Things Networks. Sensors 2024, 24, 4188. https://doi.org/10.3390/s24134188
Zhang Y, Tang Y, Li C, Zhang H, Ahmad H. Post-Quantum Secure Identity-Based Signature Scheme with Lattice Assumption for Internet of Things Networks. Sensors. 2024; 24(13):4188. https://doi.org/10.3390/s24134188
Chicago/Turabian StyleZhang, Yang, Yu Tang, Chaoyang Li, Hua Zhang, and Haseeb Ahmad. 2024. "Post-Quantum Secure Identity-Based Signature Scheme with Lattice Assumption for Internet of Things Networks" Sensors 24, no. 13: 4188. https://doi.org/10.3390/s24134188
APA StyleZhang, Y., Tang, Y., Li, C., Zhang, H., & Ahmad, H. (2024). Post-Quantum Secure Identity-Based Signature Scheme with Lattice Assumption for Internet of Things Networks. Sensors, 24(13), 4188. https://doi.org/10.3390/s24134188