Widening Blockchain Technology toward Access Control for Service Provisioning in Cellular Networks
Abstract
1. Introduction
2. Background
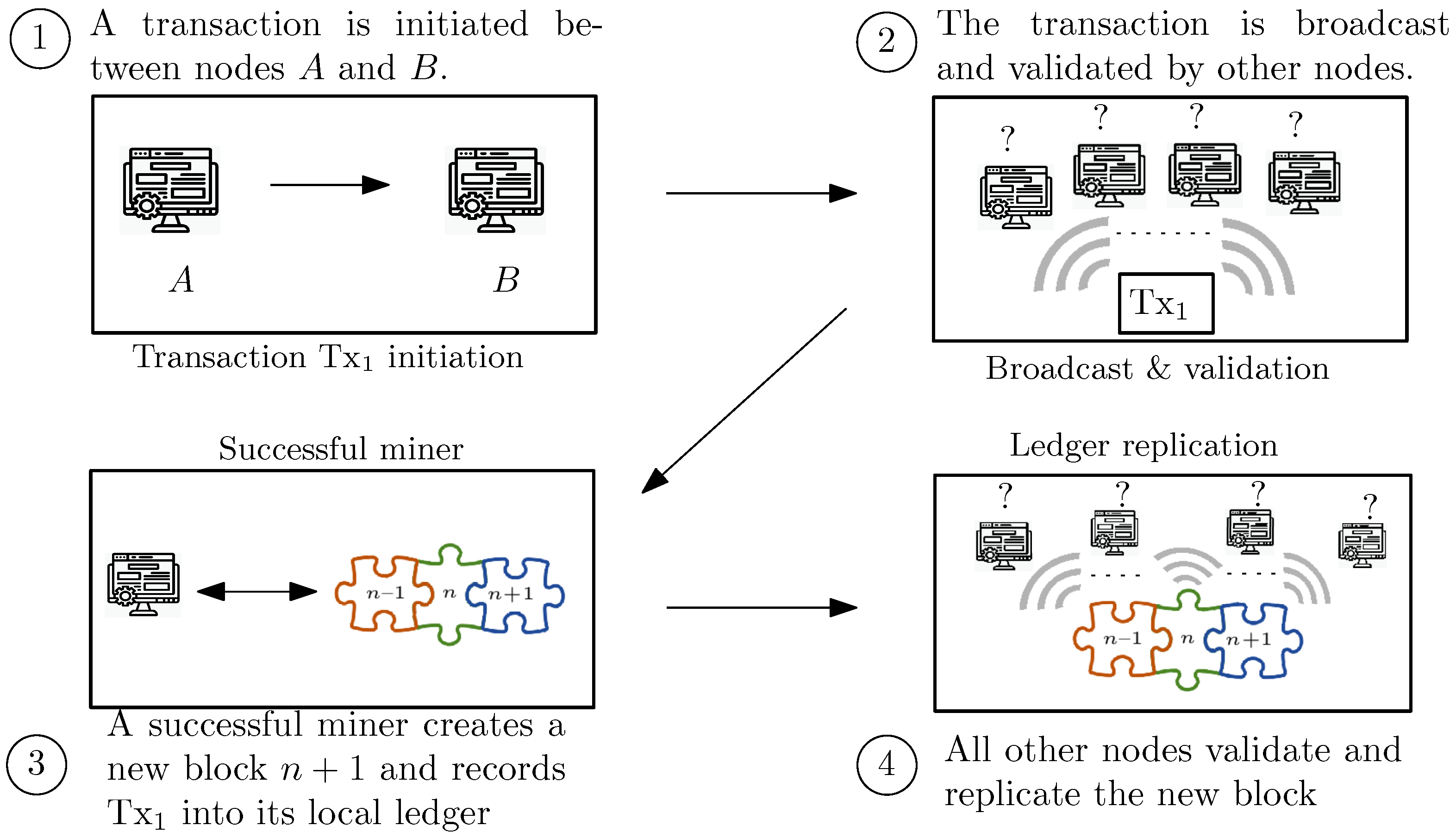
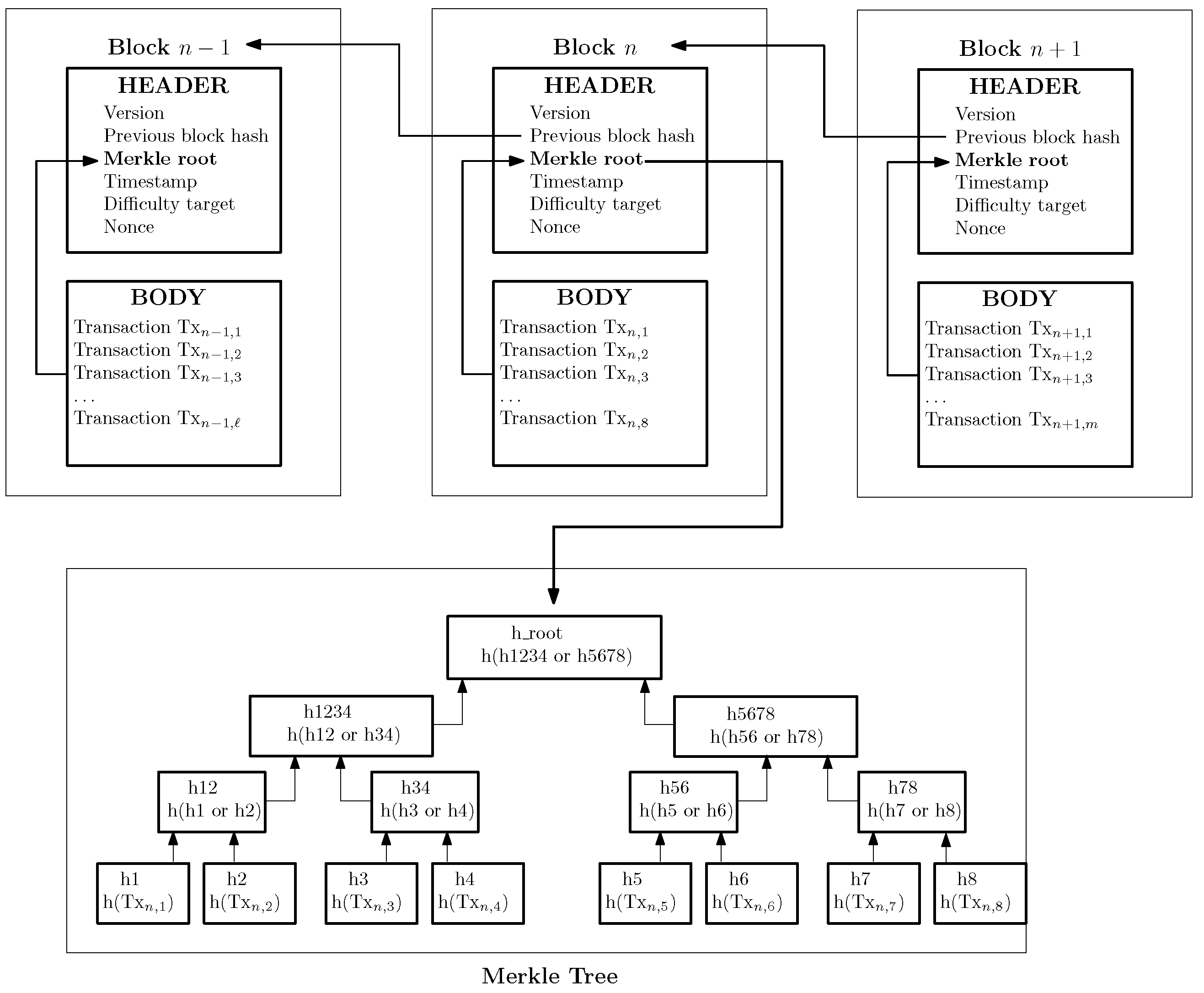
2.1. Blockchain and Distributed Ledger Technologies
2.2. Smart Contracts Enabled by BCT
2.3. Access Control Models
2.4. Private Cellular Networks
3. BCT-Based Access Control for Service Provisioning in Cellular Networks
- The user registers in the provided DApp by sending a request to a dedicated smart contract through a transaction in the Blockchain.
- The registration smart contract deploys a unique smart contract for the user (only for the first time).
- User chooses their desired service from the list of available services for registration.
- To access the service, the user sends an access transaction to the dedicated smart contract in the system.
- The access manager smart contract authorizes the user regarding the stored policies of the requested service.
- According to the pricing model of the service, the access manager smart contract blocks an amount of money.
- After termination of the service usage, the access manager smart contract pays the MNO, SP, and (if it is required) the user, according to the pricing model.
3.1. System Design
3.1.1. Reference Contract
3.1.2. Database Contracts
- The User List contract (), MNO List contract (), and Service Provider List contract () store the list of registered users, network providers, and service providers, mapped with the following structures, respectively:
- User contract (), which is a unique smart contract for a particular user which stores, at least, the user’s balance and all their registered services in the following structure:where is the user’s current balance in their wallet, is a list of the user’s application-layer services or specific subscribed services, is the expiration time of the user’s access to that specific service (if it is not applicable, it can be set to 0), and the user’s available storage if the service is related to storage.
- MNO contract (), which is a unique smart contract for a particular MNO, which stores, at least, their balance and all the services (or service providers) that the related MNO supports.
- Service Provider contract (), which is a unique smart contract for a particular service provider, which stores, at least, their balance in the system, all their provided services, and the list of applicable policies for each service.
- Policy List contract (), which stores the address of the policy smart contract, with a mapping to their code, as shown inwhere is the policy’s pre-defined code in the system, and is the related smart contract that defines that policy.
3.1.3. Manager Contracts
- A Registration Manager contract (), which manages the user, network provider, and service provider registration procedure in the platform. The main functions of this smart contract are:
- –
- registerServiceProvider() that registers new service providers in the platform.
- –
- registerNewUser() that registers a new user in the system and deploys the user’s smart contract for the first time.
- –
- registerNewMNO() that registers new network providers in the platform. This registration needs the consensus of all other registered network providers.
- –
- registerToServicePrepaid() that registers the user in a prepaid service.
- –
- registerToServicePAYG() that registers the user in a PAYG service.
- Access Control Manager contract (), which manages the user’s access control by validating the request against applicable policies for the requested service. Moreover, after the termination of the service usage, this contract handles the payment procedure. The main functions of this smart contract are:
- –
- userValidation() to validate the user’s eligibility to access the service regarding different policies and payment methods. Moreover, it blocks a specific amount of money inside the contract, as a distributed trusted party for the user, SP and the MNO, using the user’s address as the indicator, to manage the payment procedure after termination.
- –
- terminationAndPayment() manages the payment to the SP, the user, and the MNO.
3.1.4. Policy Definition Contracts
- Subject attribute validation, which includes a series of policies to validate the user’s registration, as follows:
- –
- Registration in Platform contract (): validates if the user is registered in the platform.
- –
- Registration in Service contract (): validates if the user is registered in the specific requested service of the particular service provider.
- Environment attribute validation, which includes another series of policies to validate if the user is eligible to use the service, as follows:
- –
- MNO Support contract (): validates if the user’s MNO supports the user’s demanded service.
- –
- Time Control contract (): validates if the service’s expiration time is not passed for that specific user.
- –
- Balance Control contract (): validates if the user has enough balance to register and access the service in the following scenarios:
- –
- For the prepaid services, the user’s balance needs to be checked in the registration step.
- –
- For the prepaid services, the service provider’s balance needs to be checked in the access control step.
- –
- For the PAYG services, the user’s balance needs to be checked in the access control step.
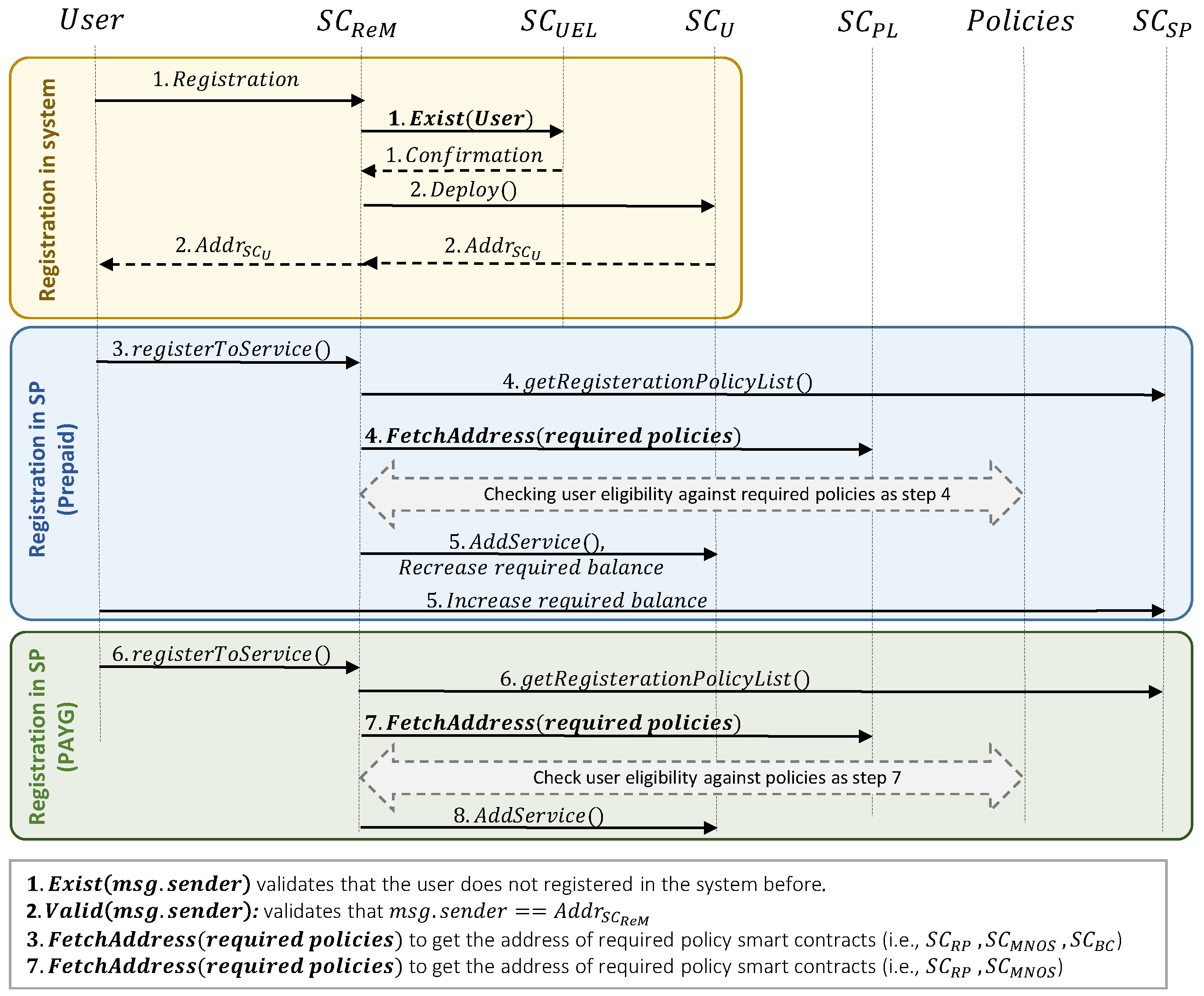
3.2. Registration Step
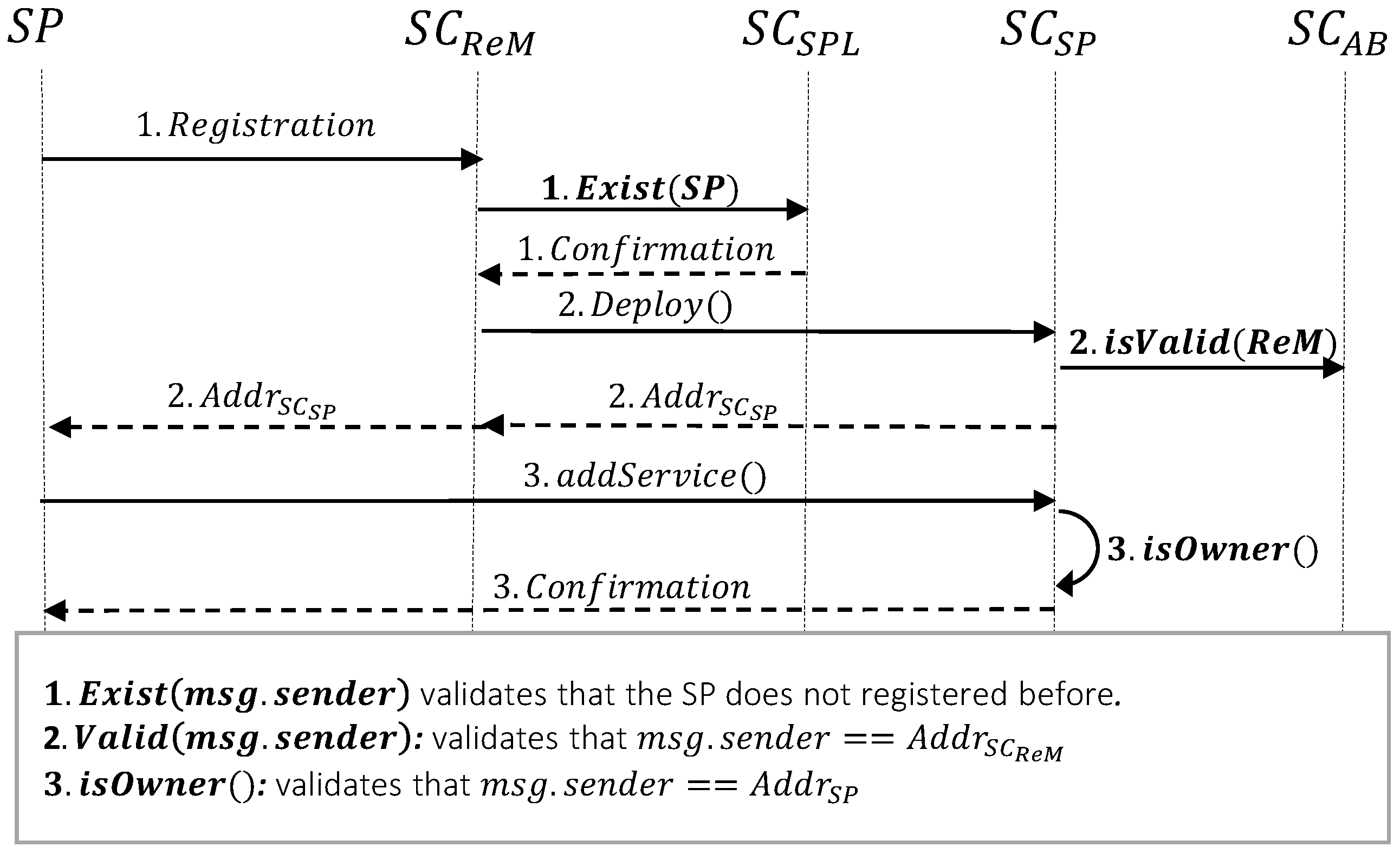
3.2.1. Service Provider Registration
- First, sends the registration request to . Since each service provider can register only one time, needs to verify that the is not registered beforehand. To do so, it calls the isExist() function of and sends the address of the caller as its argument. Note that here the caller is , so sends the in isExist() function. Since msg.sender in Solidity language is the address of the caller or the creator of the transaction, in the rest of the paper we use msg.sender to indicate the caller of the function.
- After receiving confirmation from , deploys the service provider’s unique smart contract (i.e., ). Note that the deployment of smart contracts for all entities in the system is only can be done by . Therefore, the constructor() of verifies that msg.sender is equal to . It is important to mention that in the proposed system, the only fixed and hard-coded address is , to be able to use this smart contract as a reference point. After the deployment of , its address is sent to .
- Finally, as the owner of the smart contract can add its preferred services into . These services would be advertised to the network providers and the users for further registration. While inserting the services into , the service provider defines the costs for prepaid and PAYG scenarios (note that the service providers can choose one of these payment solutions based on their preference). The following costs will be added to for each advertised service (cf. Figure 3, ):
- : defines the prepaid cost that the user needs to pay for registering in this service for a predefined time/data usage.
- : defines the fee that will pay to on behalf of the user, after user access termination.
- : defines the fee that the user needs to pay per hour/MB while using a PAYG service.
- : defines the minimum required tokens in the user’s wallet to give access to a PAYG service. Note that the user’s real usage may be more than this amount, so, the user will be charged after access termination for the remaining part. or, if the real cost is less than this amount, the user’s wallet would be refunded.
- : defines the ’s share in percentage from the user’s real usage of service. So, the cost of the user’s real usage will be between and based on this value.
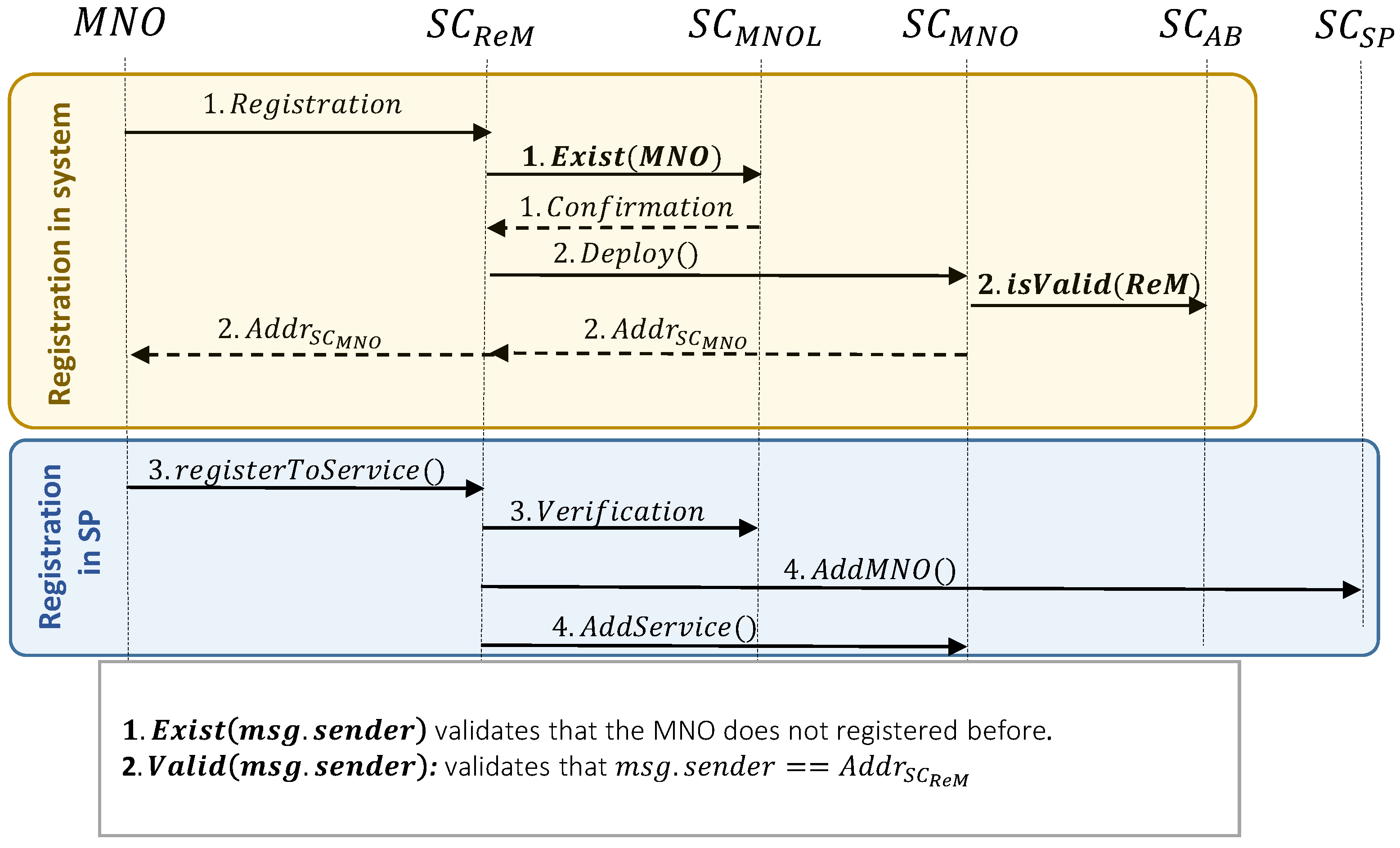
3.2.2. MNO Registration
- MNO registration in the system:
- sends the registration request to . Similar to the service provider registration procedure, each MNO can register only one time to the system. So, verifies that the is not registered beforehand (i.e., by using the isExist() function of and sending the MNO address, msg.sender, as its argument).
- After receiving confirmation from , deploys the MNO’s unique smart contract (i.e., ), after verifying that msg.sender . After registration, as the owner of the smart contract can add its preferred services into , using the following steps.
- MNO registration in the services:
- 3.
- selects the desired services from existing options, then sends the registration request to . After receiving the request, verifies that is already registered in the system. Note that, when selects a service from existing services in the system, this means that it agrees on the prices that are related to the payment to (i.e., and ).
- 4.
- To register the is an specific service, inserts the and into . So, the service provider would have the in its customer list. Moreover, the and will be inserted in as well.
3.2.3. User Registration
- User registration in the system:
- sends the registration request to . Since each user can register only once to the system, verifies that the has not been registered beforehand (i.e., by calling the isExist() function associated with and sending the value of (msg.sender) as its argument).
- After receiving confirmation from , then deploys the unique smart contract of the user (i.e., ).
- User registration in the prepaid pricing model:
- 3.
- selects the desired services from existing options, then sends the registration request to . After receiving the request, fetches all policies that are defined for the registration of the user in the system (e.g., checking the user’s balance and verifying that ).
- 4.
- Once getting the list of policies, will retrieve the address of each smart contract in which those policies are defined (e.g., , , , , ). Then it can verify the user’s eligibility based on each policy.
- 5.
- In case of the user’s eligibility, the and will be inserted into . Moreover, the will be transferred from the user to the service provider’s wallet. Note that this transfer is based on ERC20 standards [30].
- User registration in the PAYG pricing model: Because the majority of the registration steps in this model are the same as for the prepaid one, we only summarized the main steps.
- 6.
- sends the registration request to , then it fetches all required registration policies.
- 7.
- verifies the user’s eligibility based on each policy.
- 8.
- and will be inserted into . In this pricing model, the user does not need to make any payment in the registration step.
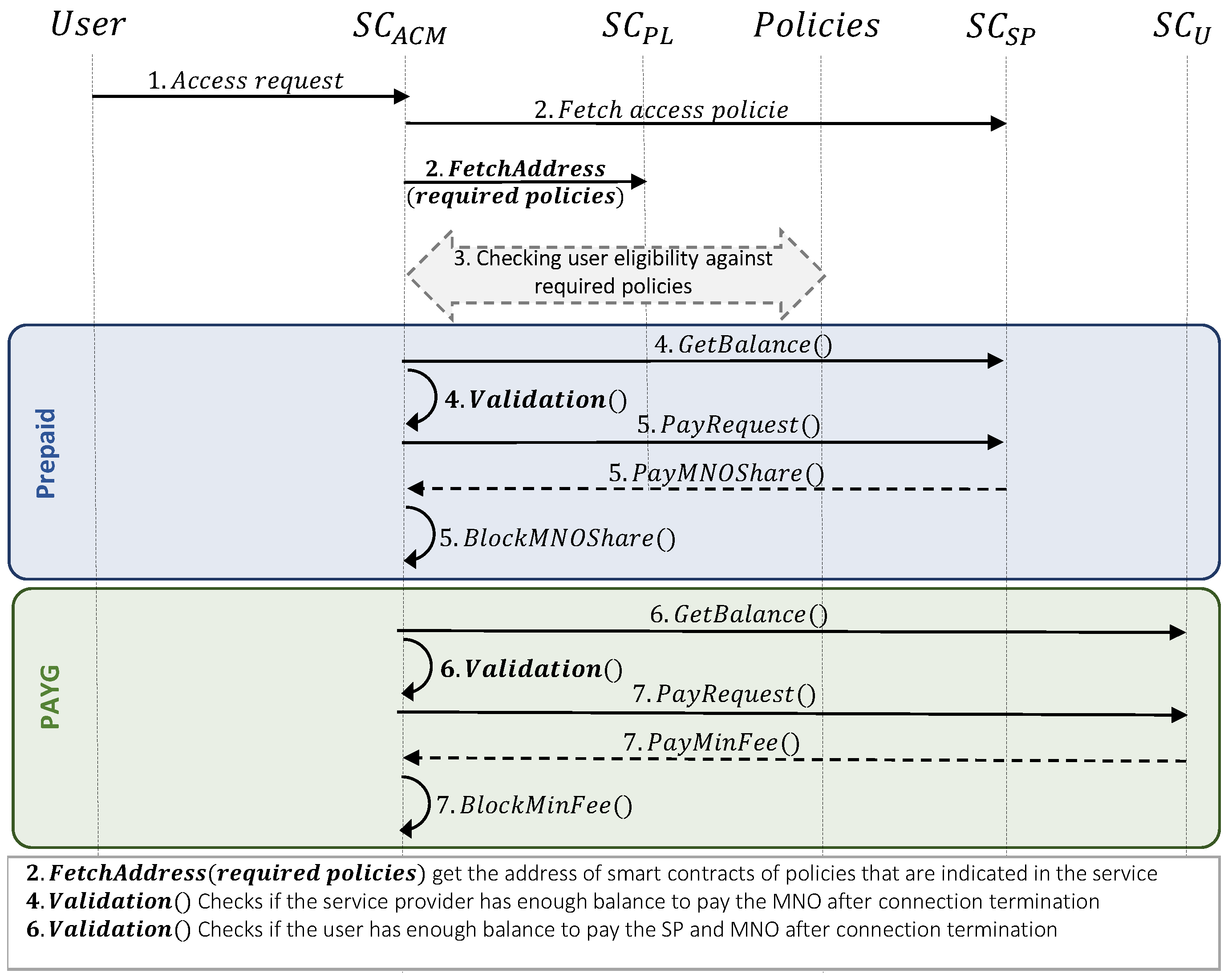
3.3. Attribute-Based Access Control
- User access verification:
- selects a service among registered services, (this selection creates an access request transaction to smart contract).
- After receiving the request, fetches all policies that are defined as prerequisites for access o the service (e.g., checking the user’s balance, checking the geographical IP, etc.).
- After getting the list of policies, retrieves the address of each smart contract in the list (e.g., , , , , ). Then it can verify the user’s eligibility based on each policy (i.e., for the verification we defined a isEligible() function, that compares the user’s access attributes with the defined rules).
- User access control to the prepaid pricing model:
- 4.
- If the access verification is successful, validates the service provider’s balance for further user access. It is important to mention that, in the prepaid pricing model, the user is paid to the service provider while the registration step, and while using the service, the user would not pay to MNO (e.g., the user’s mobile data will not be reduced while using the service); and, the service provider is the entity that will pay to MNO on behalf of the user. So, verifies that .
- 5.
- If the balance verification is successful, the will be transferred from the service provider’s wallet to as a distributed trusted party for all entities. Note that, this transfer is based on ERC20 standard [30]. Record of this payment is added to as a mapping of the user’s address to a balance as follows:
- User access control to the PAYG pricing model:
- 6.
- If the access verification is successful, validates the user’s balance, since, in this pricing model, the user needs directly pay the service provider and MNO separately, according to the real service utilization. So, verifies that .
- 7.
- If the balance verification is successful, the will be transferred from the user’s wallet to . Note that this amount balance is only a minimum balance to guarantee the payment to the service provider and MNO. It means that the user’s real utilization will be sent to after termination, and the real price will be calculated at that time. Same as in the prepaid model, the record of this payment is added to .
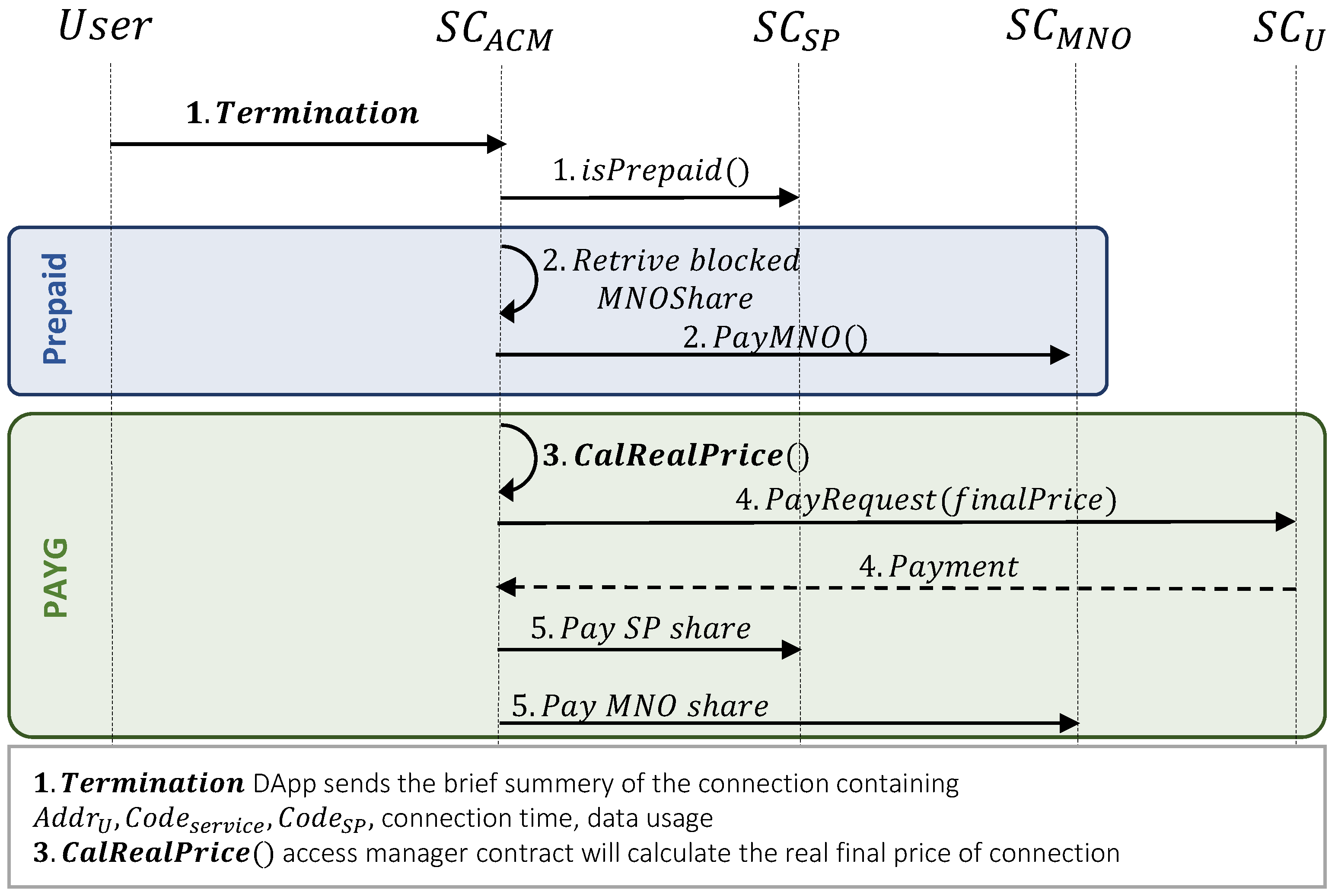
3.4. Payment
- Checking service type:
- sends the termination transaction to the smart contract. This contract checks the service type for handling the further payment procedure.
- Payment in the prepaid pricing model:
- Payment in the PAYG pricing model:
- 3.
- First, calculates the real service price as follows:Then, it calculates the amount of money that the user needs to pay or be reimbursed as follows:In this equation, if , the user needs to pay this amount, otherwise, the user will be refunded by .
- 4.
- If , payment request will be sent to user, and will receive the tokens from user’s wallet.
- 5.
- calculates the MNO and service provider’s shares from as follows, and transfer tokens to each one.
4. Evaluation
4.1. Implementation
4.1.1. Deployment of Cellular Network Testbed
- User Equipment: We utilize the Samsung Galaxy S4 smartphone with LTE network capability as our used equipment. A programmable SIM card connects the smartphone to the cellular network. The SIM card stores information such as secret keys, mobile country codes, mobile network codes, etc. This information helps in choosing the right network operator during the authentication process. We utilize a SIM card reader and pySim (https://github.com/osmocom/pysim (accessed on 21 February 2023)) software to program the SIM card and store the necessary information.
- Radio Access Network: We employ OpenAirInterface5g (https://gitlab.eurecom.fr/oai/openairinterface5g (accessed on 21 February 2023)) software to implement a softwerized RAN in COTS system. The COTS system configuration includes an Intel Core i7-6700 CPU running at 3.40 GHz, 16 GB of RAM, and Ubuntu 18.04 OS with a low latency kernel. The OAI RAN software includes the v1.1.0 git branch. We attach an USRP B210 device to the system for radio communication between the UE and RAN. All the functionalities of the USRP B210 device are handled by the USRP Hardware Driver (UHD), which is installed in the same system. In order to set up interfaces for communication with CN, OAI software provides numerous configuration files that contain data regarding PLMN and IP addresses. We utilize the configuration file named enb.band7.tm1.50PRB.usrpb210.conf to store the PLMN values, IP addresses, and network interfaces of RAN and CN.
- Core Network: We utilize OpenAirInterface LTE+ software to implement the core network in the COTS system. The COTS system configuration includes an Intel Xeon W-2102 CPU running at 2.90 GHz, 16 GB of RAM, and Ubuntu 20.04 OS. The OAI-based core network utilizes the master branch (https://github.com/OPENAIRINTERFACE/openair-epc-fed (accessed on 21 February 2023)) and the MagmaCore uses version 1.8 branch (https://github.com/magma/magma/tree/v1.8 (accessed on 21 February 2023)). All the modules of the core network are containerized using either Docker or VirtualBox. The MME functionality of CN initiates a connection with RAN and manages all requests arriving from UE via RAN. The information regarding the user, such as secret keys, is stored in the HSS database and is utilized during the authentication process.
4.1.2. Deployment of the Decentralized Application via BCT
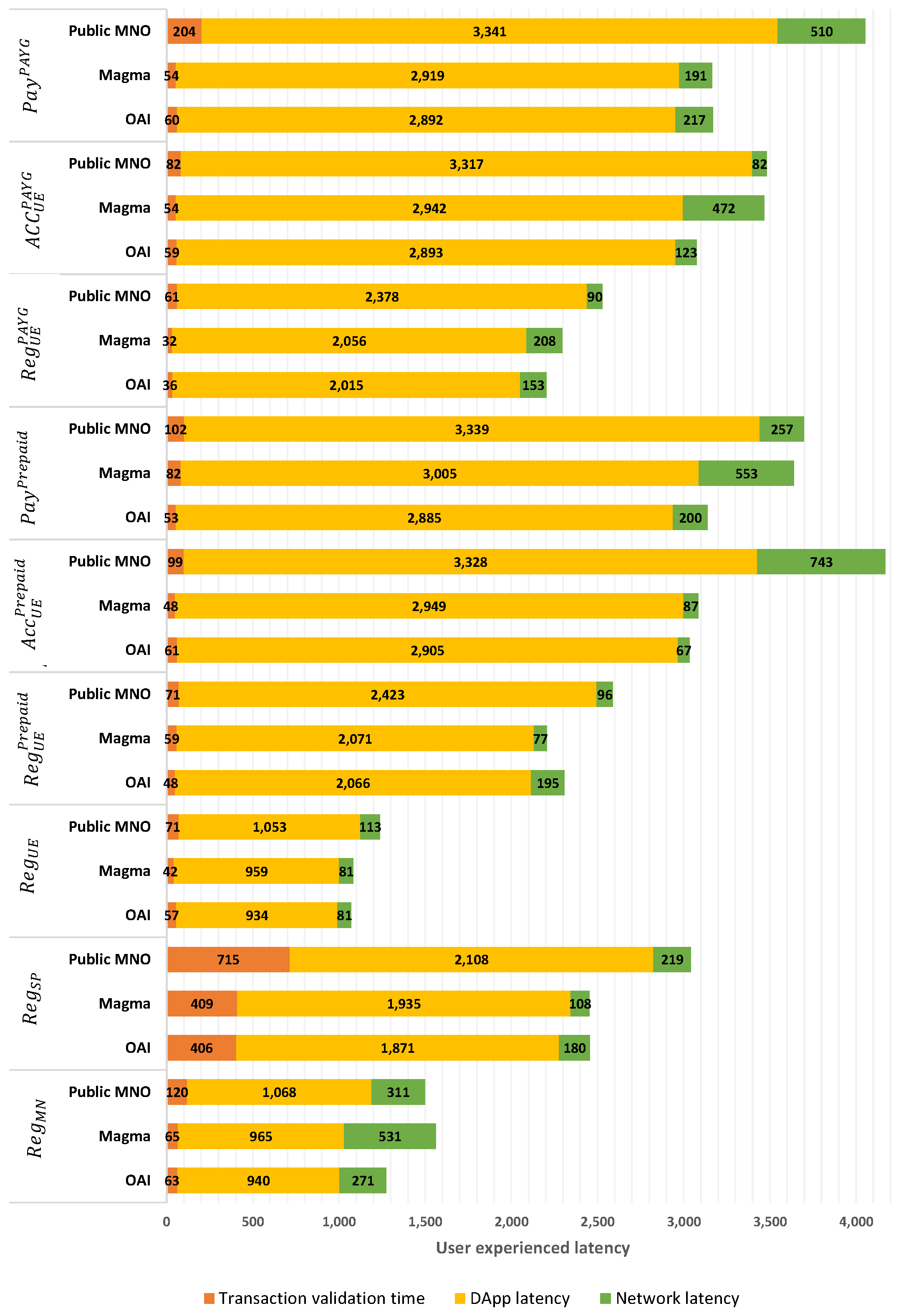
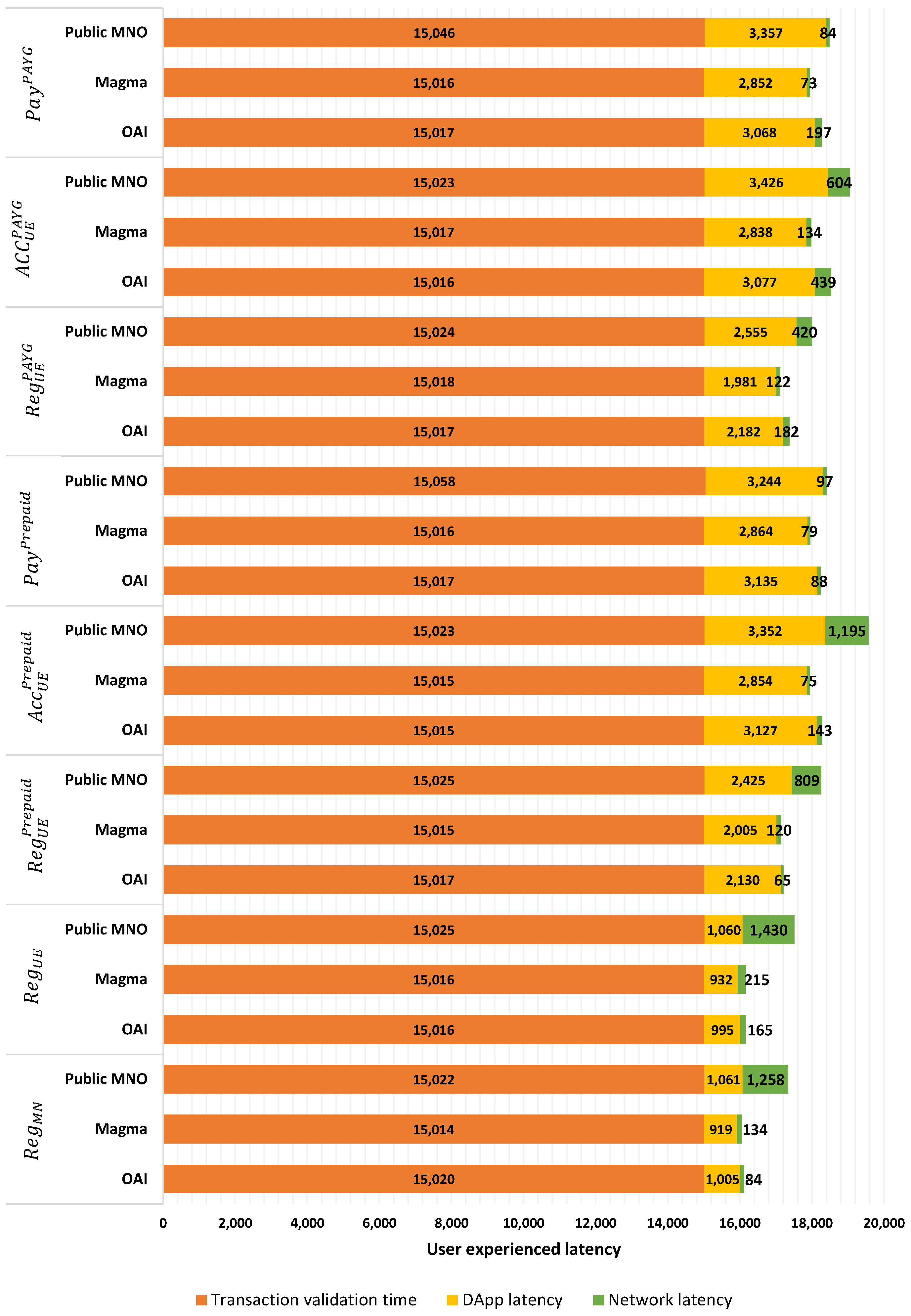
4.2. Performance Evaluation
- Connecting the COST UE to the OAI-RAN and OAI-core networks, and DApp is hosted in MNO;
- Connecting the COST UE to OAI-RAN and magma core, and DApp is hosted in MNO;
- Connecting the COST UE to a public network, and DApp is hosted in either MNO or other third-party entities (available through the internet);
- The GAS usage: GAS is the fee that must be paid by the sender to submit transactions to the Ethereum network. GAS price in the public networks is defined in (i.e., as , which is the real-time price of the Ethereum cryptocurrency). However, in the private or consortium Blockchains, this price can be modified by the actors and governors.
- The user-experienced latency (): This time is the exact period it takes from sending the user’s request through the browser to getting the answer from the network.
- The transaction validation time (smart contract function execution time) (): this time defines the period that it takes for the network to execute all function(s) related to a specific request in the network and to return a transaction receipt for that. Note that is dependent on the block time in the Blockchain network.
- The DApp latency (): this time consists of the latency in the internal functions in DApp and the non-transaction calls to the Blockchain.
- The network latency (): this time is the network latency of the user’s connection to RAN or core networks (i.e., ).
- : the registration of the MNO in the system including the deployment of ;
- : the registration of the service provider in the system, including the deployment of ad insertion of two services for each service provider, and the definition of two access policies for each service.
- : the registration of the user in the system including the deployment of ;
- : the registration of the user in one of the available services with the prepaid pricing model.
- : attribute-based access control of the user to access the registered prepaid service.
- : termination of the user’s access to the service and service provider’s payment to MNO on behalf of the user.
- : the registration of the user in one of the available services with the PAYG pricing model.
- : attribute-based access control of the user to access the registered PAYG service.
- : termination of the user’s access to the service, the user’s access time to the service, and their payment to the service provider and MNO accordingly.
5. Discussion
5.1. Real Implementation of the System
- Trustworthiness in the immutability of prices advertised by the service provider: Since the advertised prices of the service providers are stored in with the service provider’s ownership, the first concern is how the other entities can be assured that this prices will not change without their agreement. To address this concern, we propose to implement a simple voting system for the entities that will be affected by the price changes. For instance, the following scenario is implemented in the current version: when an MNO registers in the service, its address is added to the list of beneficiaries in . Updating the prices will be managed by updatePrice() function in . This function will execute a voting procedure, in which all the existing MNOs in beneficiaries list need to vote in a predefined time (the request will be sent to them as an event). Once the predefined tile is finished, or all beneficiaries voted, the decision will be based on the majority of the votes. Therefore, we can state that the prices are adaptable only in case of the agreement of all (or the majority of) the participants.
- Guaranteed payment to service providers and the MNOs after providing the service and network: Since, in this system, either the user will not pay the MNO (i.e., in prepaid services) or they pays based on their real utilization of the service (i.e., in PAYG pricing model), it is crucial for the MNOs, as well as service providers, to be sure about the payment. If the payment guarantee can not be provided in the proposed system, indeed, the service providers and MNOs will not be motivated to accept the new business model. To address this issue, we benefit from the trustworthiness of smart contracts through automatic execution in a deterministic way. In both prepaid and PAYG pricing models, we defined a fee that is blocked in the at the time of the user’s request to access the service. The following approaches are proposed for two pricing models:
- –
- In the prepaid scenario, since the user already paid the service provider, this fee (i.e., ) will be deducted from the service provider’s account and blocked in . After termination of the service usage, will transfer the blocked money to MNO. It means the service provider is guaranteed to pay the MNO on behalf of the user.
- –
- In the PAYG scenario, since the user will pay both the MNO and service provider according to their usage, a minimum fee (i.e., ) will be deducted from the user’s account and blocked in . After termination of the service usage, will transfer the blocked money to MNO and the service provider according to their share of this fee. In the current implementation of the system, if the user’s real usage is less than the blocked money, the user will be refunded, unless the remaining fee can be deducted from the user’s account. Other solutions are also possible to address this exceptional situation, provided as future directions.
5.2. Discussion on Latency and Storage Complexity
- Designing a tailor-made DLT for access control purposes can encourage the BCT community researchers to design a precise ledger with specific consensus models, block sizes, transaction fees, block times, incentives, and other specifications to make it possible to validate the higher number of transactions with high security in a given time. The main problem with this solution is that it needs lots of research and proof before application.
- Chain sharding is another novel solution that horizontally shards the chain to distribute the transaction loads among shards [33]. After the validation of transactions in the shards and generating the blocks, a smart contract would be utilized to merge the shard blocks to the main chain. This solution increases the throughput and decreases storage usage. Several sharding solutions are recently proposed that state the feasibility of this method. For instance, RapidChain [34] increased the throughput to 7380 TpS, in comparison with 15 to 20 in Ethereum, with 4000 participating nodes and 250 shards.
5.3. Discussion on Scalability
6. Related Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Disclaimer
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review 2008. p. 21260. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 12 April 2023).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of blockchains in the Internet of Things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1676–1717. [Google Scholar] [CrossRef]
- Jing, N.; Liu, Q.; Sugumaran, V. A blockchain-based code copyright management system. Inf. Process. Manag. 2021, 58, 102518. [Google Scholar] [CrossRef]
- Saari, A.; Vimpari, J.; Junnila, S. Blockchain in real estate: Recent developments and empirical applications. Land Use Policy 2022, 121, 106334. [Google Scholar] [CrossRef]
- Xi, P.; Zhang, X.; Wang, L.; Liu, W.; Peng, S. A review of Blockchain-based secure sharing of healthcare data. Appl. Sci. 2022, 12, 7912. [Google Scholar] [CrossRef]
- García-Corral, F.J.; Cordero-García, J.A.; de Pablo-Valenciano, J.; Uribe-Toril, J. A bibliometric review of cryptocurrencies: How have they grown? Financ. Innov. 2022, 8, 2. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for 5G and beyond networks: A state of the art survey. J. Netw. Comput. Appl. 2020, 166, 102693. [Google Scholar] [CrossRef]
- Agyapong, P.K.; Iwamura, M.; Staehle, D.; Kiess, W.; Benjebbour, A. Design considerations for a 5G network architecture. IEEE Commun. Mag. 2014, 52, 65–75. [Google Scholar] [CrossRef]
- Donet, J.A.; Pérez-Sola, C.; Herrera-Joancomartí, J. The bitcoin P2P network. In Financial Cryptography and Data Security: FC 2014 Workshops, BITCOIN and WAHC 2014, Christ Church, Barbados, 7 March 2014, Revised Selected Papers; Springer: Berlin, Germany, 2014; pp. 87–102. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Lande, S.; Zunino, R. SoK: Unraveling Bitcoin smart contracts. In Proceedings of the 7th International Conference on Principles of Security and Trust, Thessaloniki, Greece, 14–20 April 2018; pp. 217–242. [Google Scholar]
- Dumas, J.G.; Lafourcade, P.; Tichit, A.; Varrette, S. Les Blockchains en 50 Questions-2éd.: Comprendre le Fonctionnement de Cette Technologie; Dunod: Malakoff, France, 2022. [Google Scholar]
- Morrison, D. PATRICIA—Practical algorithm to retrieve information coded in alphanumeric. J. ACM 1968, 15, 514–534. [Google Scholar] [CrossRef]
- Ferraiolo, D.; Kuhn, D.R.; Chandramouli, R. Role-Based Access Control; Artech House: New York, NY, USA, 2003. [Google Scholar]
- Lampson, B.W. Protection. ACM SIGOPS Oper. Syst. Rev. 1974, 8, 18–24. [Google Scholar] [CrossRef]
- Levy, H.M. Capability-Based Computer Systems; Digital Press: Los Angeles, CA, USA, 2014. [Google Scholar]
- Samarati, P.; de Vimercati, S.C. Access control: Policies, models, and mechanisms. In Foundations of Security Analysis and Design: Tutorial Lectures; Springer: Berlin, Germany, 2000; pp. 137–196. [Google Scholar]
- Sandhu, R.S. Role-based access control. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 1998; Volume 46, pp. 237–286. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Orange. Mobile Private Network. Available online: https://www.orange-business.com/fr/produits/mobile-private-networks (accessed on 21 February 2023).
- Ericsson. Dedicated Networks. Available online: https://www.ericsson.com/en/portfolio/enterprise-wireless-solutions/dedicated-networks (accessed on 21 February 2023).
- Samsung. Digital Transformation Powerd by Private Networks. Available online: https://www.samsung.com/global/business/networks/solutions/private-networks/ (accessed on 21 February 2023).
- Nokia. Private Cellular Networks Can Effectively and Affordably Serve the Needs of Education. Available online: https://www.nokia.com/blog/private-cellular-networks-can-effectively-and-affordably-serve-the-needs-of-education/ (accessed on 21 February 2023).
- Aryal, N.; Ghaffari, F.; Rezaei, S.; Bertin, E.; Crespi, N. Private Cellular Network Deployment: Comparison of OpenAirInterface with Magma Core. In Proceedings of the 2022 18th International Conference on Network and Service Management (CNSM), Thessaloniki, Greece, 31 October–4 November 2022; IEEE: New York, NY, USA, 2022; pp. 364–366. [Google Scholar]
- Nikaein, N.; Marina, M.K.; Manickam, S.; Dawson, A.; Knopp, R.; Bonnet, C. OpenAirInterface: A flexible platform for 5G research. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 33–38. [Google Scholar] [CrossRef]
- Magma. Implications of the Magma Architecture Interoperability, Scale and Resilience. 2022. Available online: https://magmacore.org/wp-content/uploads/sites/5/2022/10/WP_Implications_of_Magma_Architecture_092822.pdf (accessed on 21 February 2023).
- Chen, J.; Xia, X.; Lo, D.; Grundy, J.; Luo, X.; Chen, T. Defining smart contract defects on ethereum. IEEE Trans. Softw. Eng. 2020, 48, 327–345. [Google Scholar] [CrossRef]
- Wackerow, P. ERC-20 Token Standard. 2022. Available online: https://ethereum.org/en/developers/docs/standards/tokens/erc-20 (accessed on 21 February 2023).
- Aponte-Novoa, F.A.; Orozco, A.L.S.; Villanueva-Polanco, R.; Wightman, P. The 51% attack on blockchains: A mining behavior study. IEEE Access 2021, 9, 140549–140564. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, D. Exploring the attack surface of blockchain: A comprehensive survey. IEEE Commun. Surv. Tutor. 2020, 22, 1977–2008. [Google Scholar] [CrossRef]
- Kaur, G.; Gandhi, C. Scalability in blockchain: Challenges and solutions. In Handbook of Research on Blockchain Technology; Elsevier: Amsterdam, The Netherlands, 2020; pp. 373–406. [Google Scholar]
- Zamani, M.; Movahedi, M.; Raykova, M. Rapidchain: Scaling blockchain via full sharding. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 931–948. [Google Scholar]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Blendcac: A smart contract enabled decentralized capability-based access control mechanism for the IoT. Computers 2018, 7, 39. [Google Scholar] [CrossRef]
- Ali, G.; Ahmad, N.; Cao, Y.; Khan, S.; Cruickshank, H.; Qazi, E.A.; Ali, A. xDBAuth: Blockchain based cross domain authentication and authorization framework for Internet of Things. IEEE Access 2020, 8, 58800–58816. [Google Scholar] [CrossRef]
- Shafeeq, S.; Alam, M.; Khan, A. Privacy aware decentralized access control system. Future Gener. Comput. Syst. 2019, 101, 420–433. [Google Scholar] [CrossRef]
- Popov, S. The tangle. White Pap. 2018, 1, 30. [Google Scholar]
- Zhang, J.; Yang, Y.; Liu, X.; Ma, J. An efficient blockchain-based hierarchical data sharing for Healthcare Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 7139–7150. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. An access control scheme with fine-grained time constrained attributes based on smart contract and trapdoor. In Proceedings of the 26th International Conference on Telecommunications (ICT), Hanoi, Vietnam, 8–10 April 2019; IEEE: New York, NY, USA, 2019; pp. 249–253. [Google Scholar]
- Ling, X.; Wang, J.; Bouchoucha, T.; Levy, B.C.; Ding, Z. Blockchain radio access network (B-RAN): Towards decentralized secure radio access paradigm. IEEE Access 2019, 7, 9714–9723. [Google Scholar] [CrossRef]
- Ling, X.; Le, Y.; Wang, J.; Ding, Z. Hash access: Trustworthy grant-free IoT access enabled by blockchain radio access networks. IEEE Netw. 2020, 34, 54–61. [Google Scholar] [CrossRef]
- Sukhodolskiy, I.; Zapechnikov, S. A blockchain-based access control system for cloud storage. In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), St. Petersburg, Russia, 29 January–1 February 2018; IEEE: New York, NY, USA, 2018; pp. 1575–1578. [Google Scholar]
- Yu, G.; Zha, X.; Wang, X.; Ni, W.; Yu, K.; Yu, P.; Zhang, J.A.; Liu, R.P.; Guo, Y.J. Enabling attribute revocation for fine-grained access control in blockchain-IoT systems. IEEE Trans. Eng. Manag. 2020, 67, 1213–1230. [Google Scholar] [CrossRef]
- Wang, S.; Wang, X.; Zhang, Y. A secure cloud storage framework with access control based on blockchain. IEEE Access 2019, 7, 112713–112725. [Google Scholar] [CrossRef]
- Ghaffari, F.; Bertin, E.; Crespi, N.; Behrad, S.; Hatin, J. A novel access control method via smart contracts for internet-based service provisioning. IEEE Access 2021, 9, 81253–81273. [Google Scholar] [CrossRef]


| Parameter | GAS Used | Price in € |
|---|---|---|
| 320,065 | 0.47 | |
| 463,673 | 0.69 | |
| Add new service by SP | 135,841 | 0.20 |
| Add new policy for service | 51,529 | 0.07 |
| 343,685 | 0.51 | |
| 182,172 | 0.27 | |
| 95,671 | 0.14 | |
| 68,307 | 0.10 | |
| 48,331 | 0.07 | |
| 95,787 | 0.14 | |
| 75,831 | 0.11 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghaffari, F.; Aryal, N.; Bertin, E.; Crespi, N.; Garcia-Alfaro, J. Widening Blockchain Technology toward Access Control for Service Provisioning in Cellular Networks. Sensors 2023, 23, 4224. https://doi.org/10.3390/s23094224
Ghaffari F, Aryal N, Bertin E, Crespi N, Garcia-Alfaro J. Widening Blockchain Technology toward Access Control for Service Provisioning in Cellular Networks. Sensors. 2023; 23(9):4224. https://doi.org/10.3390/s23094224
Chicago/Turabian StyleGhaffari, Fariba, Nischal Aryal, Emmanuel Bertin, Noel Crespi, and Joaquin Garcia-Alfaro. 2023. "Widening Blockchain Technology toward Access Control for Service Provisioning in Cellular Networks" Sensors 23, no. 9: 4224. https://doi.org/10.3390/s23094224
APA StyleGhaffari, F., Aryal, N., Bertin, E., Crespi, N., & Garcia-Alfaro, J. (2023). Widening Blockchain Technology toward Access Control for Service Provisioning in Cellular Networks. Sensors, 23(9), 4224. https://doi.org/10.3390/s23094224







