Double Image Encryption System Using a Nonlinear Joint Transform Correlator in the Fourier Domain
Abstract
1. Introduction
2. Related Works
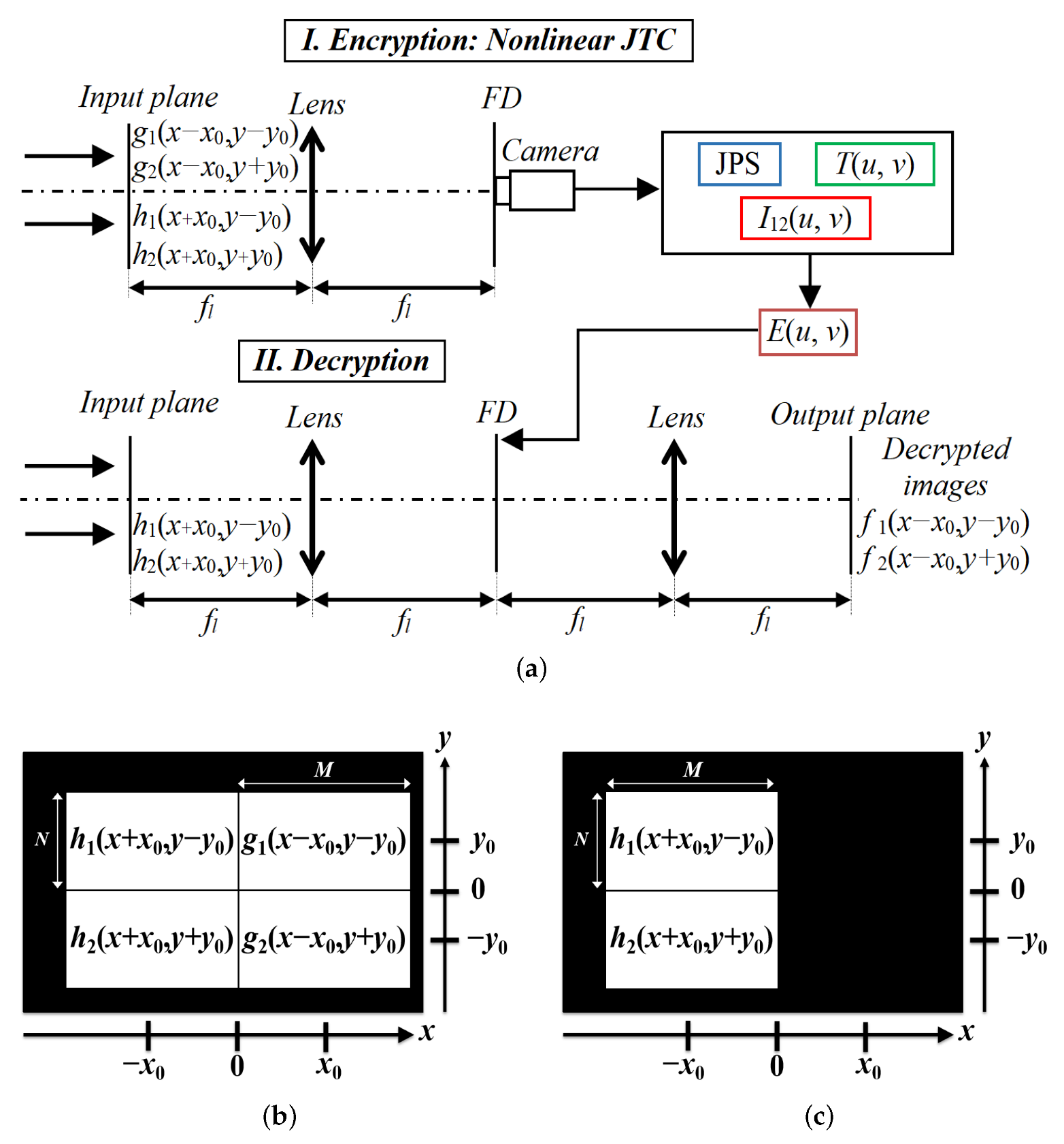
3. Encryption and Decryption Systems Based on a Nonlinear JTC Architecture in the FD
3.1. Encryption System
3.2. Decryption System
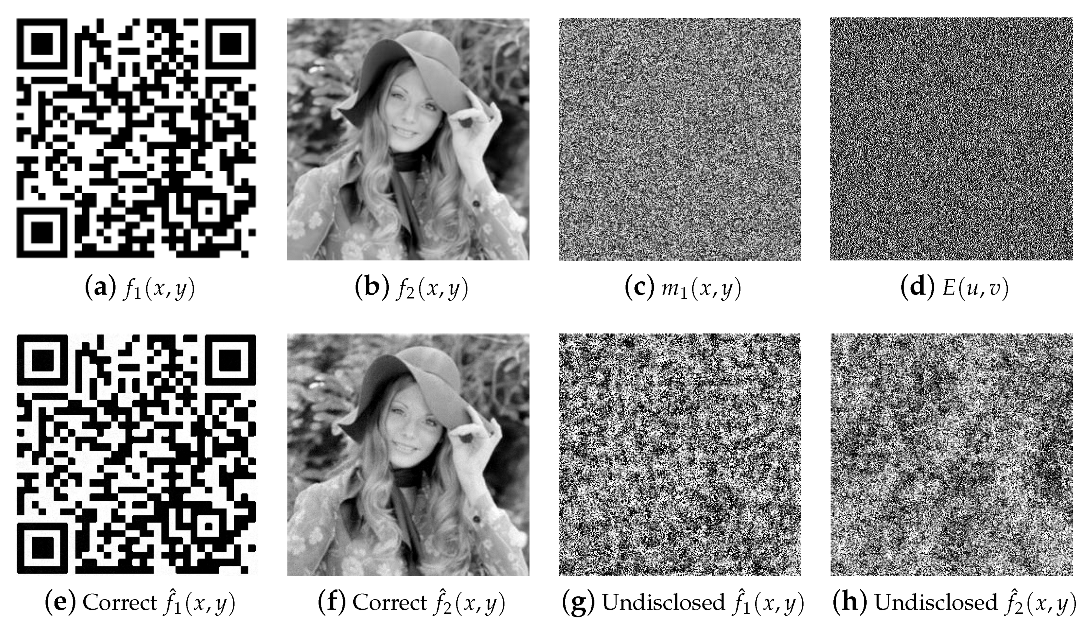
4. Simulation Results
Key Space and Robustness to Attacks
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| 2D | Two-Dimensional |
| CPA | Chosen-Plaintext Attack |
| COA | Ciphertext-Only Attack |
| DRPE | Double Random Phase Encoding |
| FFT | Fast Fourier Transform |
| FD | Fourier Domain |
| FT | Fourier Transform |
| KPA | Known-Plaintext Attack |
| JTC | Joint Transform Correlator |
| JPS | Joint Power Spectrum |
| RPMs | Random Phase Masks |
| RMSE | Root Mean Square Error |
References
- Muniraj, I.; Sheridan, J.T. Optical Encryption and Decryption, 1st ed.; SPIE Press: Bellingham, WA, USA, 2019. [Google Scholar]
- Millán, M.S.; Pérez-Cabré, E. Optical data encryption. In Optical and Digital Image Processing: Fundamentals and Applications; Cristóbal, G., Schelkens, P., Thienpont, H., Eds.; Wiley-VCH Verlag GmbH & Co.: Weinheim, Germany, 2011; pp. 739–767. [Google Scholar]
- Chen, W.; Javidi, B.; Chen, X. Advances in optical security systems. Adv. Opt. Photonics 2014, 6, 120–155. [Google Scholar] [CrossRef]
- Javidi, B.; Carnicer, A.; Yamaguchi, M.; Nomura, T.; Pérez-Cabré, E.; Millán, M.; Nishchal, N.; Torroba, R.; Barrera, J.; He, W.; et al. Roadmap on optical security. J. Opt. 2016, 18, 083001. [Google Scholar] [CrossRef]
- Millán, M.S.; Pérez-Cabré, E.; Vilardy, J.M. Nonlinear techniques for secure optical encryption and multifactor authentication. In Advanced Secure Optical Image Processing for Communications; Al Falou, A., Ed.; IOP Publishing: Bristol, UK, 2018; pp. 8-1–8-33. [Google Scholar]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Experimental optical encryption scheme for the double random phase encoding using a nonlinear joint transform correlator. Optik 2020, 217, 164653. [Google Scholar] [CrossRef]
- Réfrégier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef]
- Goodman, J.W. Introduction to Fourier Optics, 3rd ed.; Roberts & Company Publishers: Englewood, CO, USA, 2005. [Google Scholar]
- Nomura, T.; Javidi, B. Optical encryption using a joint transform correlator architecture. Opt. Eng. 2000, 39, 2031–2035. [Google Scholar]
- Rueda, E.; Barrera, J.F.; Henao, R.; Torroba, R. Optical encryption with a reference wave in a joint transform correlator architecture. Opt. Commun. 2009, 282, 3243–3249. [Google Scholar] [CrossRef]
- Barrera, J.F.; Vélez, A.; Torroba, R. Experimental multiplexing protocol to encrypt messages of any length. J. Opt. 2013, 15, 055404. [Google Scholar] [CrossRef]
- Cai, J.; Shen, X.; Fan, C.; Zhou, B. Security-enhanced optical encryption based on JTC architecture with confused ciphertext. Optik 2020, 206, 163742. [Google Scholar] [CrossRef]
- Zhong, Y.; Chen, L.; Gan, W.; Liu, Y. Image Encryption System Based on Joint Transformation Correlation and Ptychography. IEEE Photonics J. 2020, 12, 1–10. [Google Scholar] [CrossRef]
- Chen, Q.; Shen, X.; Cheng, Y.; Lin, C.; Liu, Y.; Zhou, B. A security-enhanced joint transform correlator optical encryption system with cropping operation. Optik 2021, 245, 167654. [Google Scholar] [CrossRef]
- Barrera, J.F.; Vargas, C.; Tebaldi, M.; Torroba, R. Chosen-plaintext attack on a joint transform correlator encrypting system. Opt. Commun. 2010, 283, 3917–3921. [Google Scholar] [CrossRef]
- Barrera, J.F.; Vargas, C.; Tebaldi, M.; Torroba, R.; Bolognini, N. Known-plaintext attack on a joint transform correlator encrypting system. Opt. Lett. 2010, 35, 3553–3555. [Google Scholar] [CrossRef]
- Dou, S.; Shen, X.; Zhou, B.; Lin, C.; Huang, F.; Lin, Y. Known-plaintext attack on JTC-based linear cryptosystem. Optik 2019, 198, 163274. [Google Scholar] [CrossRef]
- Zhang, C.; Liao, M.; He, W.; Peng, X. Ciphertext-only attack on a joint transform correlator encryption system. Opt. Express 2013, 21, 28523–28530. [Google Scholar] [CrossRef] [PubMed]
- Hai, H.; Pan, S.; Liao, M.; Lu, D.; He, W.; Peng, X. Cryptanalysis of random-phase-encoding-based optical cryptosystem via deep learning. Opt. Express 2019, 27, 21204–21213. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Improved decryption quality and security of a joint transform correlator-based encryption system. J. Opt. 2013, 15, 025401. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Nonlinear optical security system based on a joint transform correlator in the Fresnel domain. Appl. Opt. 2014, 53, 1674–1682. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Joint transform correlator-based encryption system using the Fresnel transform and nonlinear filtering. Proc. SPIE 2013, 8785, 87853J. [Google Scholar]
- Barrera, J.F.; Jaramillo, A.; Vélez, A.; Torroba, R. Experimental analysis of a joint free space cryptosystem. Opt. Lasers Eng. 2016, 83, 126–130. [Google Scholar]
- Dou, S.; Shen, X.; Zhou, B.; Wang, L.; Lin, C. Experimental research on optical image encryption system based on joint Fresnel transform correlator. Opt. Laser Technol. 2019, 112, 56–64. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Torres, Y.; Millán, M.S.; Pérez-Cabré, E. Generalized formulation of an encryption system based on a joint transform correlator and fractional Fourier transform. J. Opt. 2014, 16, 125405. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Images encryption system based on a fractional joint transform correlator and nonlinear filtering. Opt. Pura Apl. 2014, 47, 35–41. [Google Scholar] [CrossRef]
- Jaramillo, A.; Barrera, J.F.; Vélez, A.; Torroba, R. Fractional optical cryptographic protocol for data containers in a noise-free multiuser environment. Opt. Lasers Eng. 2018, 102, 119–125. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Nonlinear image encryption using a fully phase nonzero-order joint transform correlator in the Gyrator domain. Opt. Lasers Eng. 2017, 89, 88–94. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Perez, R.A.; Torres, C.O. Optical image encryption using a nonlinear joint transform correlator and the Collins diffraction transform. Photonics 2019, 6, 115. [Google Scholar] [CrossRef]
- Guo, C.; Liu, S.; Sheridan, J.T. Iterative phase retrieval algorithms. Part II: Attacking optical encryption systems. Appl. Opt. 2015, 54, 4709–4719. [Google Scholar] [CrossRef] [PubMed]
- Vilardy, J.M.; Torres, C.O.; Jimenez, C.J. Double image encryption method using the Arnold transform in the fractional Hartley domain. Proc. SPIE 2013, 8785, 87851R. [Google Scholar]
- Li, J.; Zheng, T.; Liu, Q.Z.; Li, R. Double-image encryption on joint transform correlator using two-step-only quadrature phase-shifting digital holography. Opt. Commun. 2012, 285, 1704–1709. [Google Scholar] [CrossRef]
- Shi, X.; Zhao, D.; Huang, Y. Double images hiding by using joint transform correlator architecture adopting two-step phase-shifting digital holography. Opt. Commun. 2013, 297, 32–37. [Google Scholar] [CrossRef]
- Singh, H.; Yadav, A.K.; Vashisth, S.; Singh, K. Double phase-image encryption using gyrator transforms, and structured phase mask in the frequency plane. Opt. Lasers Eng. 2015, 67, 145–156. [Google Scholar] [CrossRef]
- Yu, N.; Xi, S.; Wang, X.; Zhang, C.; Wang, W.; Dong, Z.; Zhua, Q.; Liua, X.; Wang, H. Double images encryption in optical image subtraction/addition 4F system. Optik 2019, 178, 135–141. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Alfaro, E.; Jimenez, C.J. Correlation operation in the Fresnel domain and truncation operations applied to the simultaneous encryption of two images. J. Physics Conf. Ser. 2022, 2307, 012043. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, X.; Shan, M.; Zhong, Z.; Liu, B.; Yu, L.; Liu, L. Asymmetric double-image encryption via wavelength multiplexing. Appl. Opt. 2022, 61, 1248–1253. [Google Scholar] [CrossRef]
- Li, W.; Kim, N.; Shan, M. Experimentally implementable double-image optical encryption based on Gerchberg-Saxton algorithm. In Imaging and Applied Optics 2014; Optica Publishing Group: Washington, DC, USA, 2014; paper JTu4A.41. [Google Scholar]
- Sui, L.; Lu, H.; Ning, X.; Wang, Y. Asymmetric double-image encryption method by using iterative phase retrieval algorithm in fractional Fourier transform domain. Opt. Eng. 2014, 53, 026108. [Google Scholar] [CrossRef]
- Rajput, S.K.; Nishchal, N.K. Optical double image security using random phase fractional Fourier domain encoding and phase-retrieval algorithm. Opt. Commun. 2017, 388, 38–46. [Google Scholar] [CrossRef]
- Kumar, R.; Sheridan, J.T.; Bhaduri, B. Nonlinear double image encryption using 2D non-separable linear canonical transform and phase retrieval algorithm. Opt. Laser Technol. 2018, 107, 353–360. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, D. Double images encryption method with resistance against the specific attack based on an asymmetric algorithm. Opt. Express 2012, 20, 11994–12003. [Google Scholar] [CrossRef] [PubMed]
- Xiaopeng, D. A hybrid attack on `double images encryption method with resistance against the specific attack based on an asymmetric algorithm’. Opt. Commun. 2014, 317, 7–12. [Google Scholar] [CrossRef]
- Vilardy, J.M.; Millán, M.S.; Pérez-Cabré, E. Image encryption system based on a nonlinear joint transform correlator for the simultaneous authentication of two users. Photonics 2019, 6, 128. [Google Scholar] [CrossRef]
- Zhao, H.; Zhong, Z.; Fang, W.; Xie, H.; Zhang, Y.; Shan, M. Double-image encryption using chaotic maps and nonlinear non-DC joint fractional Fourier transform correlator. Opt. Eng. 2016, 55, 093109. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, Y.; Li, S.; Liu, W.; Liu, W.; Wang, Y.; Liu, S. Double image encryption scheme by using random phase encoding and pixel exchanging in the gyrator transform domains. Opt. Laser Technol. 2013, 47, 152–158. [Google Scholar] [CrossRef]
- Liansheng, S.; Cong, D.; Xiao, Z.; Ailing, T.; Anand, A. Double-image encryption based on interference and logistic map under the framework of double random phase encoding. Opt. Lasers Eng. 2019, 122, 113–122. [Google Scholar] [CrossRef]
- Su, Y.; Xue, X.; Deng, R.; Wang, Y.; Zhao, Q.; Li, T.; Li, Y.; Liu, S.; Zhao, J. Asymmetric double-image encryption based on chaotic random phase encoding. Appl. Opt. 2022, 61, 7608–7617. [Google Scholar] [CrossRef] [PubMed]
- Li, C.T.; Yin, S.; Yu, F.T.S. Nonzero-order joint transform correlator. Opt. Eng. 1998, 37, 58–65. [Google Scholar] [CrossRef]
- Frauel, Y.; Castro, A.; Naughton, T.J.; Javidi, B. Resistance of the double random phase encryption against various attacks. Opt. Express 2007, 15, 10253–10265. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Perez, R.A.; Pérez-Cabré, E.; Vilardy, J.M.; Millán, M.S.; Torres, C.O. Double Image Encryption System Using a Nonlinear Joint Transform Correlator in the Fourier Domain. Sensors 2023, 23, 1641. https://doi.org/10.3390/s23031641
Perez RA, Pérez-Cabré E, Vilardy JM, Millán MS, Torres CO. Double Image Encryption System Using a Nonlinear Joint Transform Correlator in the Fourier Domain. Sensors. 2023; 23(3):1641. https://doi.org/10.3390/s23031641
Chicago/Turabian StylePerez, Ronal A., Elisabet Pérez-Cabré, Juan M. Vilardy, María S. Millán, and Cesar O. Torres. 2023. "Double Image Encryption System Using a Nonlinear Joint Transform Correlator in the Fourier Domain" Sensors 23, no. 3: 1641. https://doi.org/10.3390/s23031641
APA StylePerez, R. A., Pérez-Cabré, E., Vilardy, J. M., Millán, M. S., & Torres, C. O. (2023). Double Image Encryption System Using a Nonlinear Joint Transform Correlator in the Fourier Domain. Sensors, 23(3), 1641. https://doi.org/10.3390/s23031641







