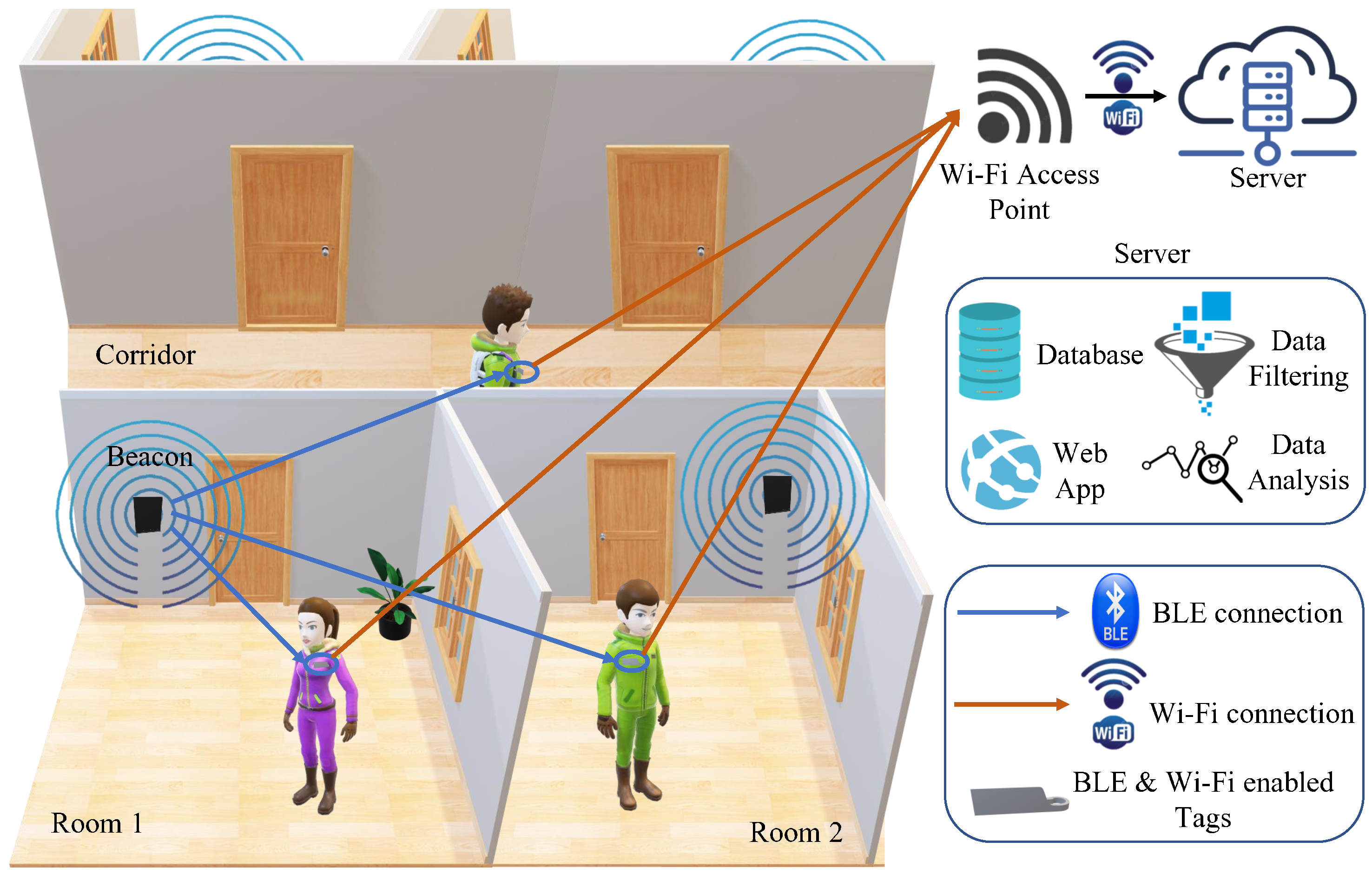
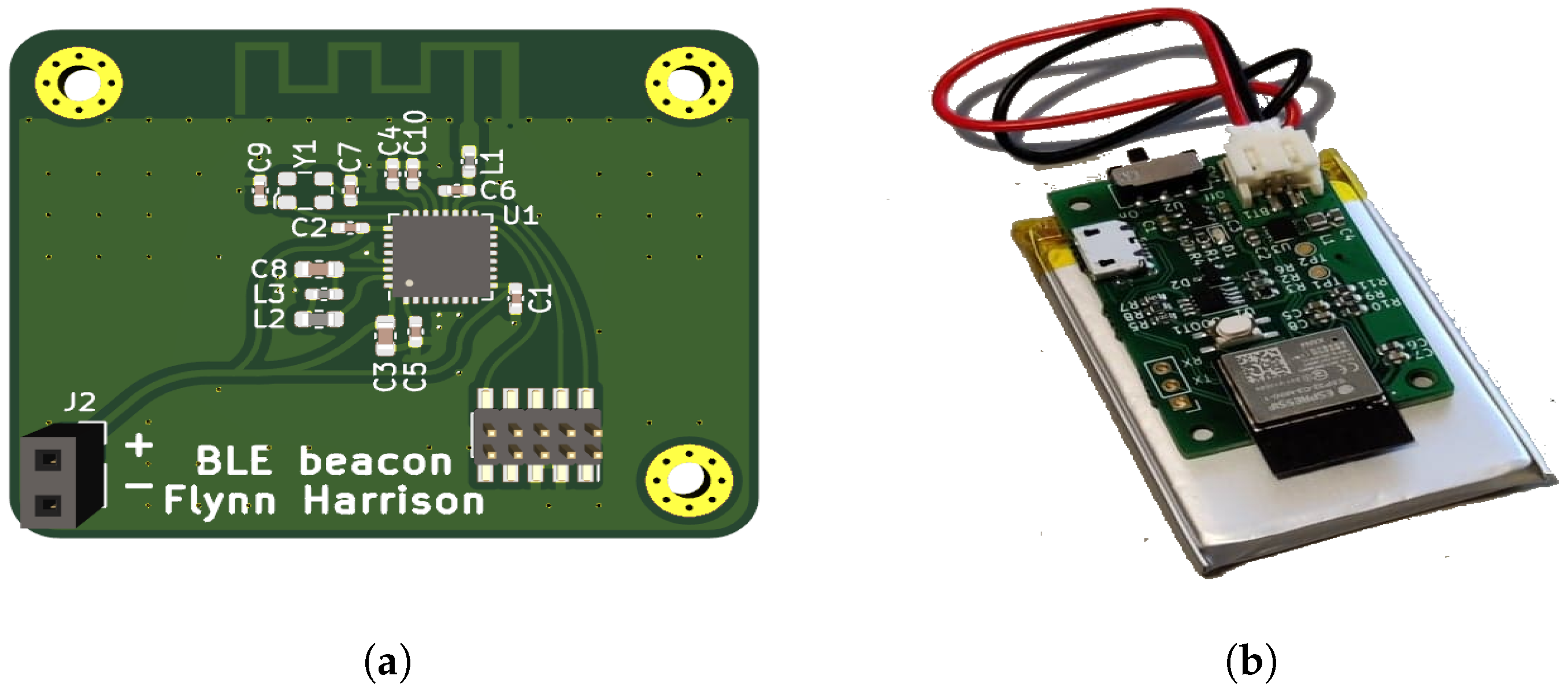
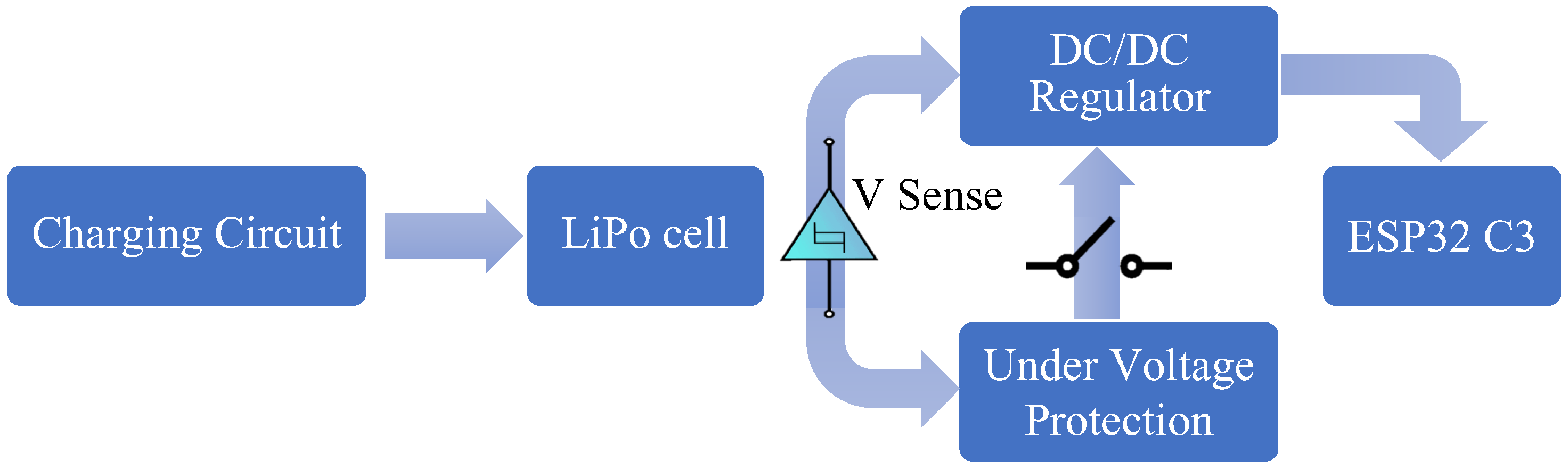
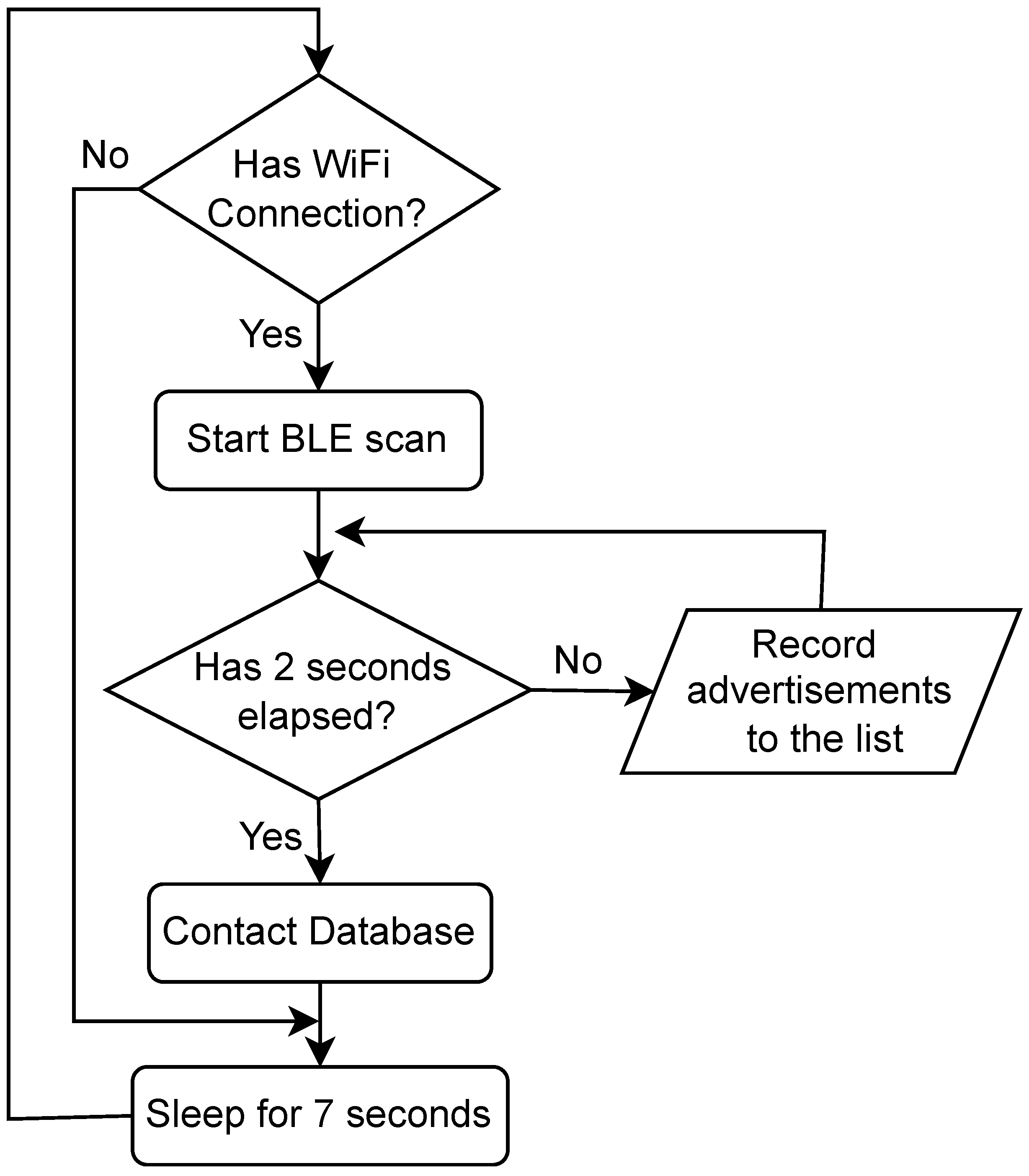
1. Introduction
Starting in 2020, the world has been witnessing the COVID-19 pandemic that has affected people’s economic [
1], physical [
2], psychological [
3], mental [
4], and social [
5] life aspects [
6]. Many countries have taken rigorous measures: cities began locking down, international travelling was completely banned, and there was an urgent direction and tendency to contain the virus using currently available technologies. One efficient method of containing the virus is through contact tracing [
7], which is—as defined by the World Health Organization (WHO)—the procedure for identifying and monitoring people who have been exposed to an infected case [
8] so they can isolate and further reduce the spread.
Contact tracing has been effectively adopted to contain historical outbreaks of Ebola, human immunodeficiency virus (HIV), and measles [
9]. However, at that time, the traditional contact tracing was done manually, which was extremely time-consuming, labour intensive, inefficient, highly prone to errors, and not scalable [
10]. In response to that, digital contact tracing, a more autonomous method, was deployed during the early stages of the COVID-19 pandemic [
11]. Many countries, such as Singapore [
12], Australia [
13], China [
14], and India [
15], adopted a range of new contact tracing technologies [
10], such as Wi-Fi [
16], Bluetooth [
17], cell tower triangulation [
18], Global Positioning System (GPS) [
19], QR codes [
20], Zigbee [
21], RFID [
9], along with IoT [
22].
IoT is an emerging concept that allows smart communication between multiple electronic devices and sensors through the Internet without requiring human interaction [
23]. Common IoT applications are for smart homes [
24], smart farming [
25], smart transport [
26], smart cities [
27], and smart security [
28]. The architecture of IoT consists generally of four main layers [
29,
30]. The first is the perception layer for dealing with all the electronic devices and sensors. The next is the transport layer, which allows physical devices to communicate with the network in various ways, such as using the TCP/IP stack, via gateways or wirelessly through Wi-Fi/3G/4G. The third layer is the processing layer for processing the incoming data. The final layer is the application layer that helps visualize the processed data to help answer business questions.
Using IoT in contact tracing can enhance its scalability and automation and can handle the ever-increasing number of contact tracing tasks [
31]. Generally, there are two common contact tracing architectures: centralized and decentralized [
32]. In a centralized architecture, users share their anonymous assigned IDs with a central server where contact tracing and risk analysis are done. In decentralized architecture, however, the users download the database from the server and perform the risk analysis on their devices [
33].
RFID and BLE are among the most common wireless sensing technologies used in contact tracing. Developments in RFID chip production are making it viable for new applications and contexts [
34]. Usually, an RFID system consists of a tag, a reader, and middleware. Based on the operating frequency (low frequency, high frequency, ultra-high frequency, microwave, or ultra-wide band), the system’s performance, operating range, and power requirements will differ [
35]. Despite the advancements of RFID technology, some technical issues still appear due to environmental factors; for example, noise may interfere with the reader, causing it to miss some tags, which negatively affects the read rate (It represents the number of tags that can be scanned in a specific amount of time whether it is the same tag or multiple tags.) [
34]. In addition, the prices for RFID systems remain relatively expensive compared to other available technologies [
34]. Regarding the healthcare industry, the adoption of RFID technology is relatively recent compared to other fields such as education (libraries), retail, supply chain production, and logistics [
36].
Bluetooth has also been used by many countries designing automated contact tracing [
37]. Bluetooth low energy (BLE) is a low power standard introduced to the Bluetooth 4.0 standard in 2009 that uses the unlicensed 2.4 GHz band for communication [
10]. BLE only sends short messages either as broadcasting advertisements or data packets between the transmitter and receiver. These packets are sent on three advertising channels (37, 38, 39) in order to not interfere with standard Wi-Fi channels, which makes it suitable for indoor environments [
38]. Technically, the device transmits broadcast packets to these three channels throughout each of its advertisement spans. The scanning mode is used by recipients to listen for such advertisement packets. During each scanning window, they record communications, either actively or passively. The former allows the scanning gadget to request further information from the advertiser. In contrast, gadgets in passive mode do not communicate with one another; instead, they only collect information from broadcast messages. A common method for performing localization with BLE beacons is to use the receiver signal strength indicator (RSSI) to measure the distance between the receiver and transmitter with a propagation model [
9]. This method can also be done with multiple beacons to perform triangulation obtaining a relative location as well as used for room level localization [
39,
40]. Another typical solution is to take advantage of the smartphone Bluetooth radio, which is a ubiquitous feature, by having the population install an application on their smart phones. These applications will then periodically send out BLE advertisements that contain some information about the user,. When another phone detects the packet, it will determine the distance from the first device using the RSSI. After this exchange, the close contacts get notified depending on the applications architecture as previously noted [
9]. Examples of some countries and their apps are Brazil (SUS) [
41], Vietnam (Blue zone), Singapore (TraceTogether), South Korea (Corona 100 m), Australia (COVIDSafe), India (Aarogya Setu), and USA (Safe Paths) [
42]. However, many researchers have pointed out for the impracticability for hospital and offices staff to continuously carry their mobile devices and, more importantly, these devices could be potential carriers for infection within indoor environments [
43,
44].
The success of any system must follow three critical success factors levels as defined in [
45]. The first is the strategic level, which involves developing a clear strategy; the second is the tactical/management level, which includes integrating the system infrastructure and proper staff usage. Finally, there is the operational level, which addresses avoiding major process changes, integrating the data collected, and using cost-effectiveness components.
This research presents autonomous, low-cost, long-battery-life IoT solutions for contact tracing that follow the three success factors levels. These solutions function without an end user dependency in hospital/office setting environments to protect the staff from indoor virus transmission. This is done by measuring the proximity between staff and tracking their presence as well as duration in commonly used indoor areas. This was based on the practicality and success of Bluetooth and RFID radio frequencies used in IoT devices for localization. Through this study, two implemented proposed contact tracing devices are described, compared, and tested, starting from concepts through final product examination.
The article is divided into seven sections.
Section 2 reviews the related work for BLE and RFID technologies in contact tracing.
Section 3 thoroughly describes the BLE-based system,
Section 4 explains the RFID-base systems, and
Section 5 displays the tests and results. Finally, our work is discussed in
Section 6 and concluded in
Section 7.
2. Related Work
Regarding using RFID and Bluetooth in automated contact tracing for pandemic outbreak management, some trials were conducted employing each technology. For tracking the severe acute respiratory syndrome (SARS) pandemic, Singapore deployed an RFID system created by Singapore’s Department of Defence, Science, and Technology in collaboration with ST Engineering [
46]. In Taiwan [
47], the Industrial Technology Research Institute built another system. These two systems shared numerous commonalities: both systems were used in hospitals and employed active RFID tags that communicated with readers through ultra high frequency (UHF) bands. The only difference between the two is who was tagged: RFID tags were provided to all hospital employees, patients, and visitors in Singapore; however, only medical personnel in Taiwan were issued RFID tags. These systems showed major challenges, including integrating the data collected and the costs of the installed systems. Another trial used ultra high frequency for accurate indoor localization [
48]. This system introduced a new concept of semi-passive RFID tags; it can sense the location of this semi-passive tag using the backscatter signals from normal passive RFID tags. The drawback of this system is its practicality; it needs a large number of fixed passive tags to detect one semi-passive tag. A trial in proposed an IoT RFID based automated tracing and tracking method, which used RFID tags and the near field communication (NFC) protocol-based mobile application as a reader. This study asked people to install a specific application on their smartphones and leave it open in the background, which made the study dependent on human interaction. Another study [
49] used the RFID together with GPS in a wearable contact tracing wristband; however, many people raised privacy concerns about using GPS in contact tracing.
On the other hand, many countries and trials used Bluetooth for contact tracing. Some approaches for positioning and proximity detection (especially indoors) were presented in [
50,
51,
52,
53,
54,
55,
56]. These works use the RSSI to measure distance between receiver and transmitter. One study [
57] demonstrated that Bluetooth 2.0 can be utilised for localisation with an inaccuracy of less than 45 cm. However, Bluetooth has the disadvantage of being an active protocol that requires two parties to establish a connection before any payload can be sent. Because of the extra complexity of the connection formation, this may impede effective message exchange. Furthermore, because devices advertise themselves, they alert potential attackers to the location of an engaged interface.
In the same manner that distance measurements for conventional Bluetooth are used, RSSI is used to determine the distance between transmitter and receiver in BLE. Various signal propagation models could be utilised to achieve this goal (e.g., the exponential or the polynomial model). BLE is more suitable than Bluetooth for co-location detection and distance measurements due to its passive advertising/broadcasting and lower energy consumption. As a result, BLE became widely employed as a contact tracing technology as developed in [
58,
59,
60]. However, these studies used people’s personal devices, such as smartphones, smart watches, or fitness trackers, which are distinctively different in their transmission power as well as their antennas gain/radiation patterns. RSSI readings must be calibrated to the appropriate instruments. Moreover, some wearables were introduced for the sake of contact tracing, such as Easy band [
61] and Abeeway [
62], which used BLE and Wi-Fi. These wearables give optical, acoustical, or mechanical alerts to maintain social distancing. These wearables have some limitations, such as limited accessibility and the trade-off between user comfort and device complexity.
BLE has also some limitations, including that distance measurements can be inaccurate due to multi-path and shadowing effects produced by signal reflection, walls, and objects that obstruct wireless signal propagation. Furthermore, an advertisement packet’s payload is limited to 31 bytes. Approaches that use passive scanning can save significant amounts of energy as compared to systems that use active message exchanges. BLE, like Bluetooth, contains vulnerabilities that allow attackers to exploit it when it is turned on. Moreover, this method is bound to produce false-positives and false-negatives, which affect the system performance and efficiency [
42]. The authors in [
63] were able to correctly detect 100% of risky contacts in 15 min at a distance of 2 m while accepting a 30% false-positive rate.
In this study, we offer two fully constructed IoT wireless sensor systems for contact tracing and monitoring infection spread. Most trials in literature sacrificed one aspect over another, such as power consumption, cost, simplicity, performance, or design. We claim that we solved the previously mentioned problems without sacrificing any aspects, based on our results, design, and hardware. First, our systems do not rely on people’s smart devices or wearables, which avoids concerns such as virus transmission carried by these devices, privacy violations, impracticability, technical variations between devices, and power consumption payload off individuals’ personal gadgets [
61,
62]. In addition, our systems are completely independent from human interaction; no actions such as installing applications, granting them permissions [
9,
41,
42], code scanning [
20], or tag taping [
64] are required; to improve simplicity and performance, our system will not be prone to human errors. Furthermore, in the implementation of our RFID system, we give special care to guarantee that the beacon is in the best location to minimize any partial gaps in contact tracing that might result in missing personnel interaction, as noted in some former studies [
65,
66,
67]. Although some studies have shown that RFID tags are unable to directly convey the extent of an exposure, we used the RSSI values in our system to overcome this limitation. Moreover, unlike some RFID systems discussed in the literature [
48], our RFID system does not require large numbers of tags to identify the individuals; each individual needs only one tag to be sensed, which reduces expenses and system complexity. Additionally, our systems are cost effective as compared to some trials, such as the BLE application COVIDSafe, which had predicted development and operational expenditures of AUD 6.75 million through early 2021, with additional monthly maintenance costs of around AUD 100,000 [
13]. In contrast, our systems used low-cost and power efficient off-the-shelf sensors. In relation to privacy preserving purposes, our system is able to successfully track hospital/office staff inside the premises only where beacons/readers are installed, as opposed to other systems using geo-localisation [
68,
69].
In the following sections, we describe the comprehensive system architecture of the two proposed autonomous IoT contact tracing platforms, discussing briefly the hardware, software, and web interfaces of each system.
4. RFID Based Contact Tracing System
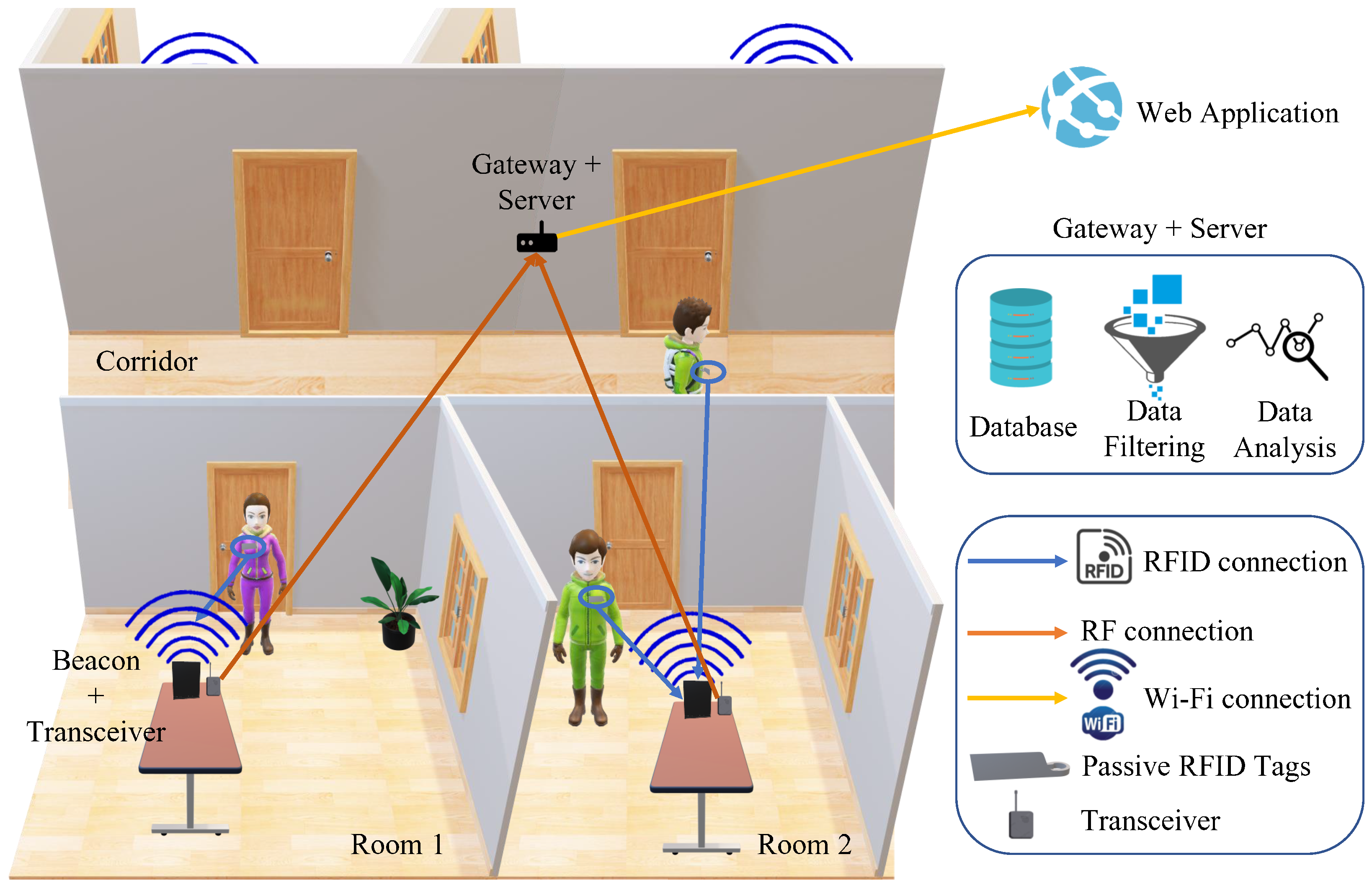
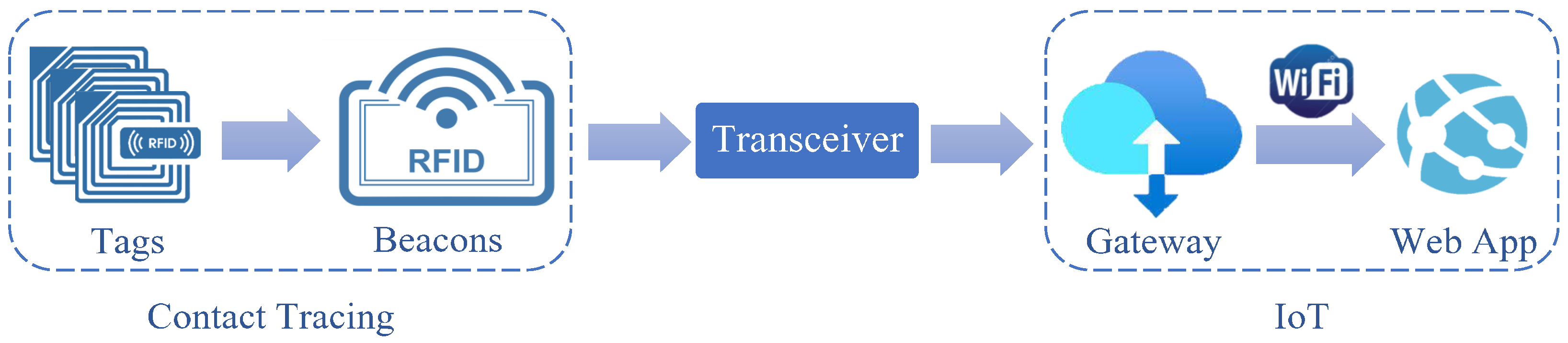
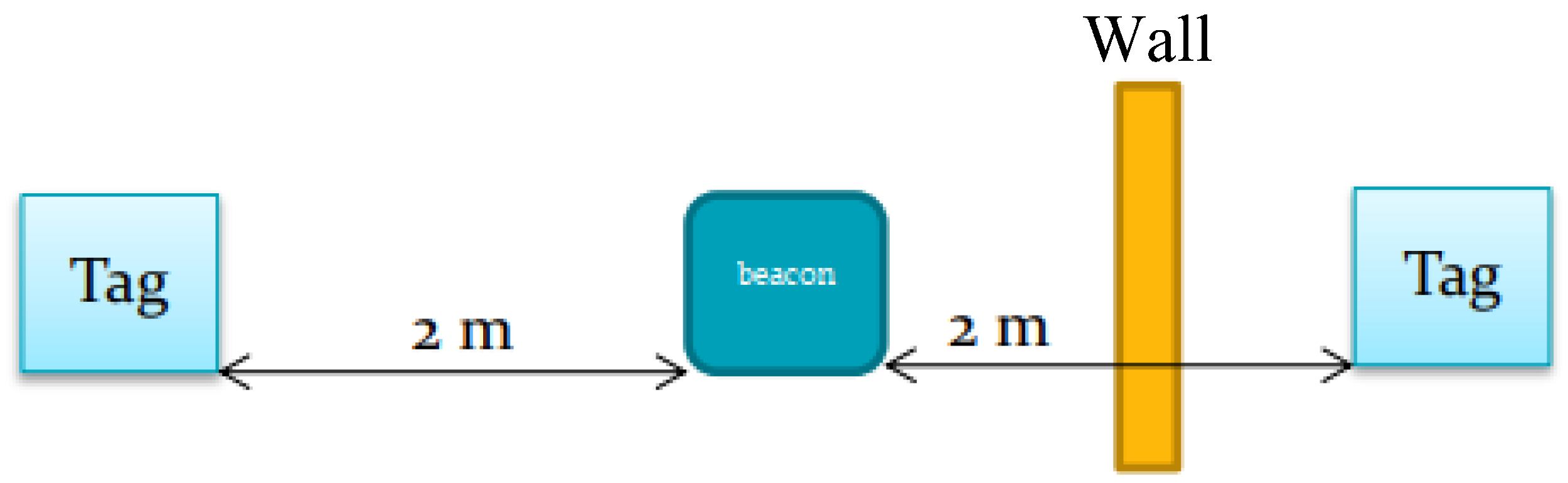
This study investigates the use of high frequency (HF) and ultra high frequency RFID systems (UHF) in a low-cost contact tracing application. The overall system overview can be seen in
Figure 9. It consists of an RFID reader, tags, and a gateway. It captures details such as name and contact details from the tags; it also tracks the rooms the tags have been in and gives indications of human-to-human proximity.
The reader/beacon usually consists of a transmitter and a receiver, where the transmitter broadcasts a signal searching for any tags within its range. Once an RFID tag has received this signal from the reader, the tag back-scatters the received signal [
78], sending its own signal back to the reader. The reader will then capture the back-scattered signals by its receiver, so it can locate the tag; following that, the transceiver transfers the data to the gateway. The proposed system can be divided into two parts as seen in
Figure 10. The first part is responsible for contact tracing and is done by the RFID tags and the reader along with the microcontroller unit, and the second part is the IoT part, including the gateway that hosts the database and is connected to the web app. The transceiver is the communication between the contact tracing and the IoT component of the project.
4.1. Hardware
The system hardware consists of beacons, tags, transceivers, and the gateway. Two RFID beacons were implemented (one for each frequency band); however, the transceiver modules and gateway were shared between the HF and UHF systems as the performance for these two components does not differ between the systems. Beacons:
HF RFID: The microcontroller chosen for the HF RFID system was the ATmega328P Arduino Uno board; it was chosen over other microcontrollers, such as ARM cortex-M7, due to its wide availability, relatively cheap price, and available open-sourced libraries [
79]. The HF RFID reader used was the RC522 RFID reader, as it is relatively cheap, it has a MFRC522 chip onboard for the reading/writing work, and it also comes with an inbuilt antenna that operates at 13.56 MHz. Its operating voltage is 3.3 V and it consumes 30 mA. The communication between the RC522 and the Arduino board is done via full duplex serial peripheral interface (SPI) communication protocol, as both the master (Arduino) and slave (RC522) transmit data simultaneously [
79].
UHF RFID: The microcontroller used was the ATmega2560 Arduino Mega board, it regulates the input voltage down to 5 V using LMV358LIST STMicroelectronics Operational Amplifiers and SPX1117M3-L-5-0/TR – Linear Voltage Regulator IC. The Z6334 DC/DC buck converter with output 5 V and S9V11F3S5 (3.3 V–1.5 A) step down voltage regulator were used with the design. The M6E Nano RFID reader was picked to be the UHF RFID reader for its good price to performance ratio; it operates at frequencies ranging from 859 to 920 MHz and at minimum output power of 5 dBm and a maximum of 27 dBm. For this study, the 920 MHz frequency and 20 dBm output power were used. Although the M6E nano reader comes with an inbuilt antenna, the performance was not up to standards, and the reading distance was only up to 30 cm. For this reason, an external antenna was used instead, operating at a similar frequency range as the reader and at a maximum power of 100 W with a gain of 6 dBi. The M6E nano reader consumes 0.84 W in operating mode, 15 mW in sleep mode, and 0.25 mW in shutdown mode. It is rated to read up to 200 RFID tags per second and at a reading range of 4.5 m.
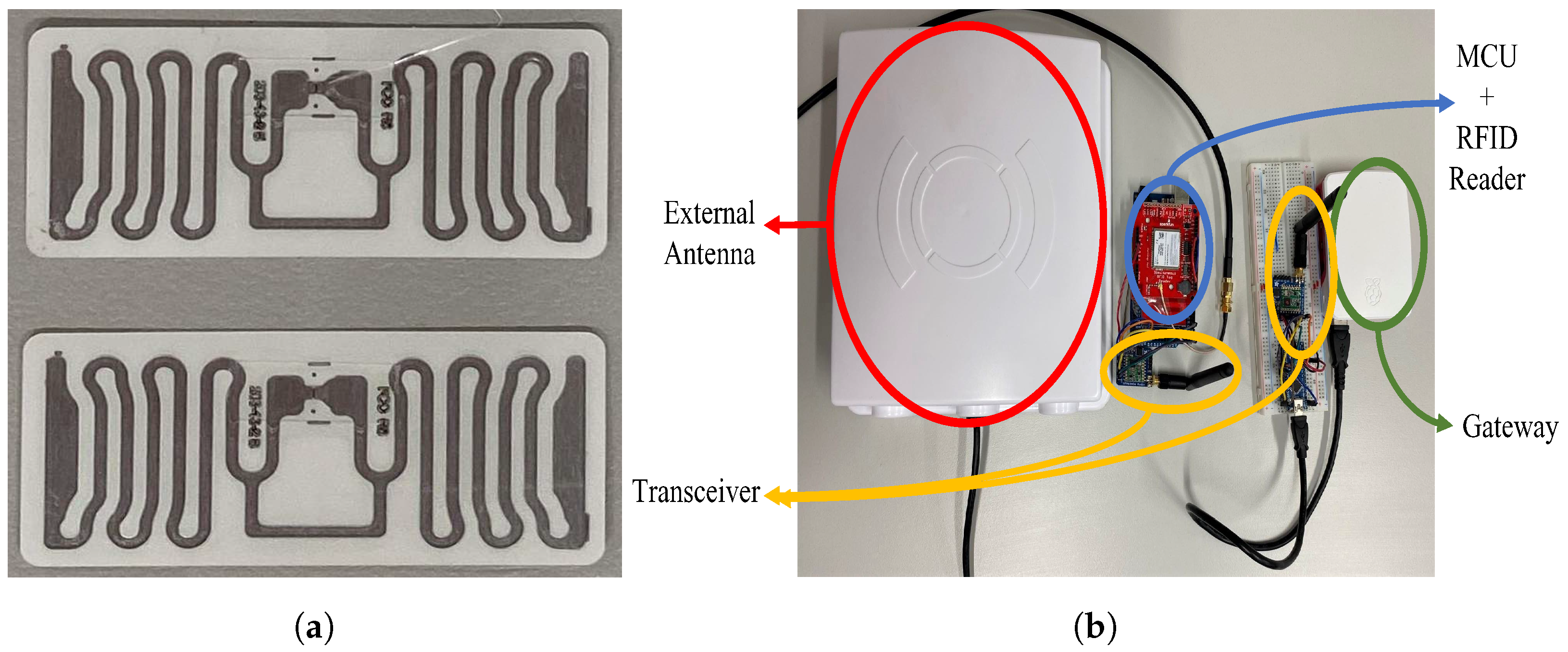
Tags: RFID tags are typically made up of an antenna and a microchip; the microchip provides the tag with computation and storage [
34]. There are two main categories of RFID tags: passive and active. Passive tags do not have any self-energy source [
38], however, when the tag comes within the range of a transmitted reader signal, its antenna is activated, creating a magnetic field and thus powering the microchip for transmitting back the tag’s unique data (a unique 32/64 bit code) to the reader. This tag has a long lifetime, but shorter reading distance. Conversely, an active RFID tag transmits its own signal to a RFID reader and requires an inbuilt battery source. These active tags have larger reading distance, but significantly higher cost. The read range of an active tag can go as far as 30 m compared to the maximum of only 6 m for a passive tag [
80,
81]. The RFID tags used in this study are passive due to price consideration and are shown in
Figure 11a.
HF RFID system: The RFID tag contains 1024 bits of memory and operates at the same 13.56 MHz frequency as the reader.
UHF RFID system: The tags are adhesive based on the Electronic Product Code global (EPCglobal) Gen2 standards containing 800 bits of memory.
Transceiver: The transceiver module used in this study is the RFM69HCW. Its radio module operates in the unlicensed ISM (industry, science and medicine) band, in either 433 MHz (used in this study for better system power consumption) or 868/915 MHz. The operating voltage ranges from 3.3 V to 5 V and draws current up to 150 mA. The RFM69HCW module does not come with an inbuilt antenna, so instead an external 2.4 GHz dipole swivel antenna was soldered to the transceiver module, operating at a gain of 2 dBi.
Figure 11b shows the UHF beacon and transceiver connected together. The RFM69HCW transceiver then uses an SPI to communicate with a host microcontroller (the Arduino ATmega328P on the transmitter side and the Arduino mini on the receiver side). It features advanced encryption standard (AES) encryption to keep data private from the readers to the gateway.
Gateway: The gateway is built using Raspberry Pi 4 and the RFM69HCW transceiver module for receiving information from the MCU/RFID reader. They are connected via UART serial communication as shown in
Figure 11b. The prices for the hardware materials used for the HF and UHF RFID systems are shown in
Table 3.
4.2. Software
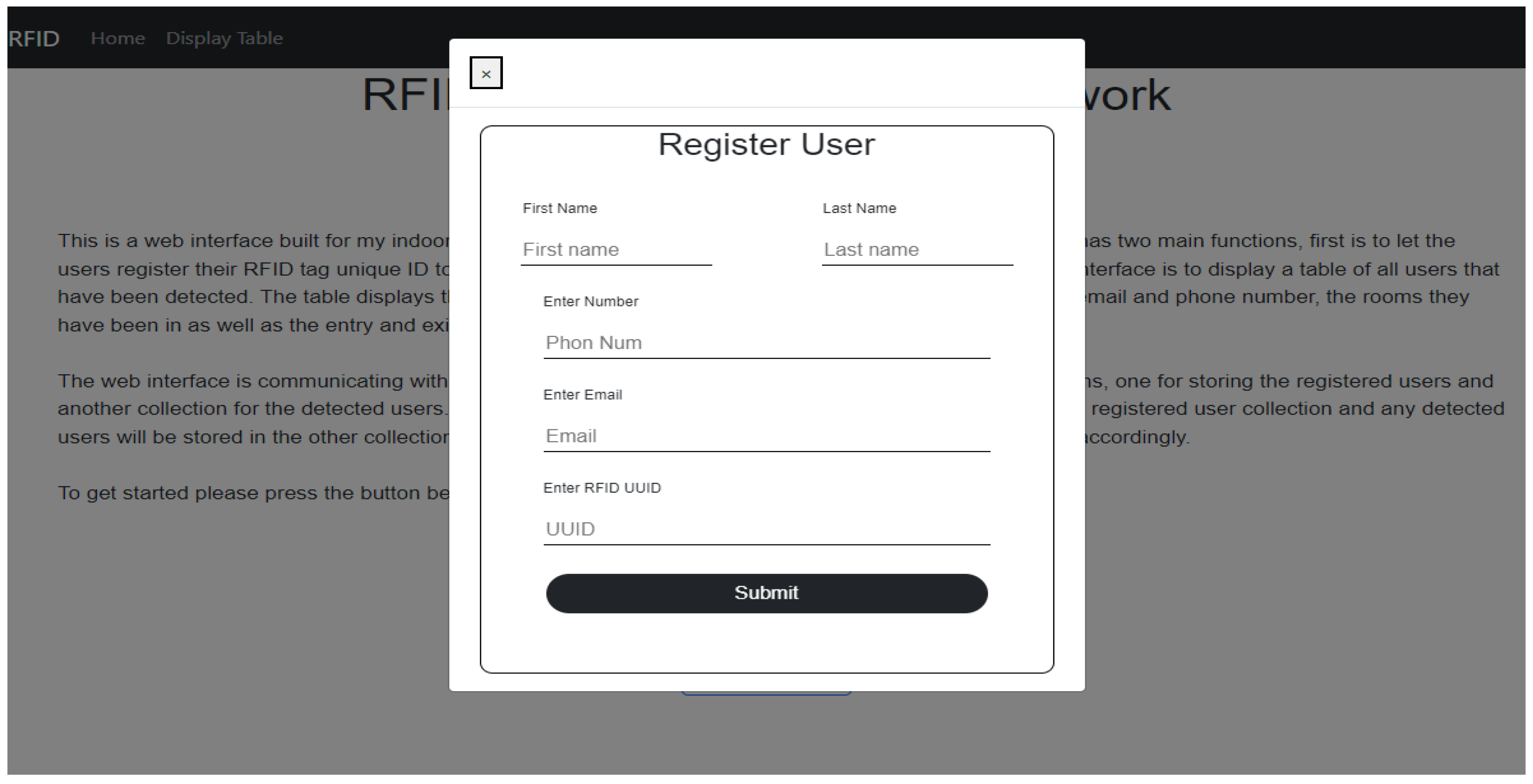
Because the RFID tags hold at most 1024 bits of memory, they would not have enough memory to hold all the relevant information needed. Therefore, first the web interface registers the unique RFID tags ID through manual registration, as shown in
Figure 12. It connects these tags to the users along with some contact details, storing them in a separate database called
registerUsers. The RFID tags instead store only their unique ID. The room number, on the other hand, was pre-programmed on the MCU, as it is assumed there is always an MCU/Reader pair in each room.
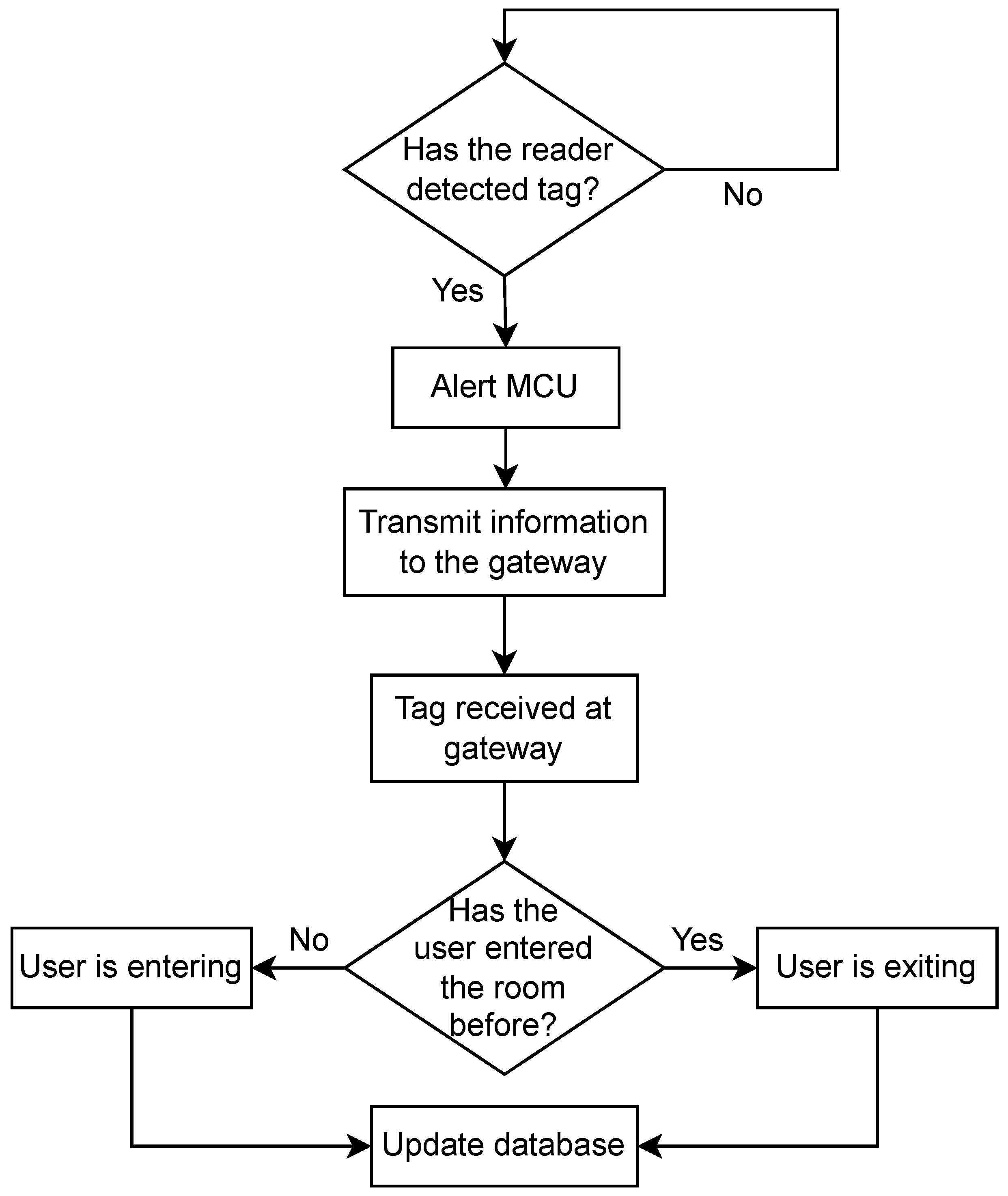
Figure 13 shows the operation flowcharts for The RFID system. The readers are continuously scanning for tags; whenever a tag is identified, the MCU retrieves the data from the tags, measures the RSSI value of the back-scattered signals, concatenates it with the pre-programmed room name, and activates the transceiver to transmit these data to the gateway. Finally, the gateway extracts the relevant information from the received message, looks up the tag based on the unique RFID ID in its private
registerUsers database, and starts inputting a detected user into the
detectedUser database, which has the following information:
The entry and exit tag detection process was tested by three different algorithms. Algorithm 1 is an RSSI gradient-based method: a positive gradient of the RSSI values was expected when entering (as the tag approaches the beacon), and a negative gradient was expected when leaving a room. However, it was found that the multi-path and interference distorted the RSSI values and the gradient was incorrectly recognized. Therefore, Algorithm 2 was implemented instead; the gateway handles current entry and exit detection, as shown in
Figure 13.
Figure 13.
RFID algorithm 2 software overview.
Figure 13.
RFID algorithm 2 software overview.
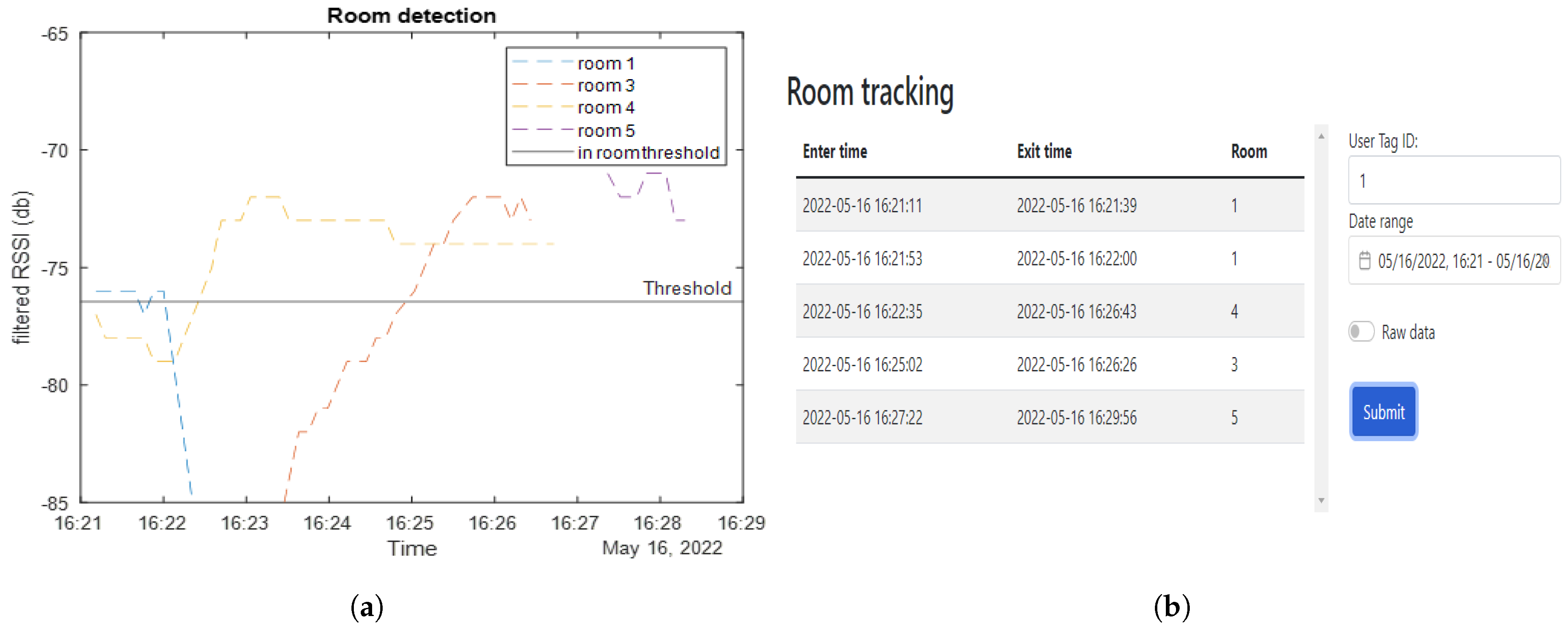
Once the data are received at the gateway, tag detection is dependent on the tags’ past history; the gateway checks the database to see whether there is any history between the associated tag and room. If there is a history, the gateway alters the state of the tag (if the last state was entry then its new state is exit, and vice versa). Once a decision is made, the database is updated with the entry/exit time.
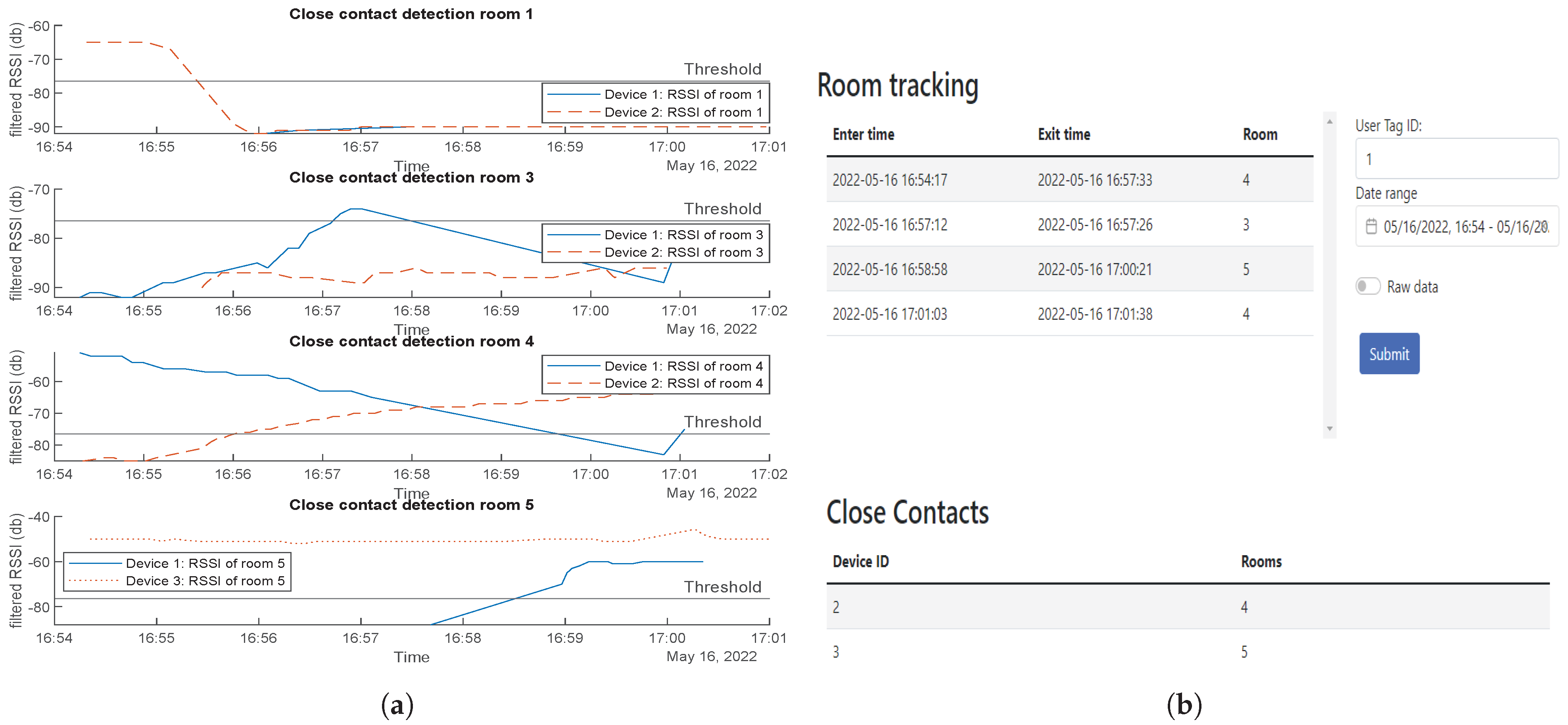
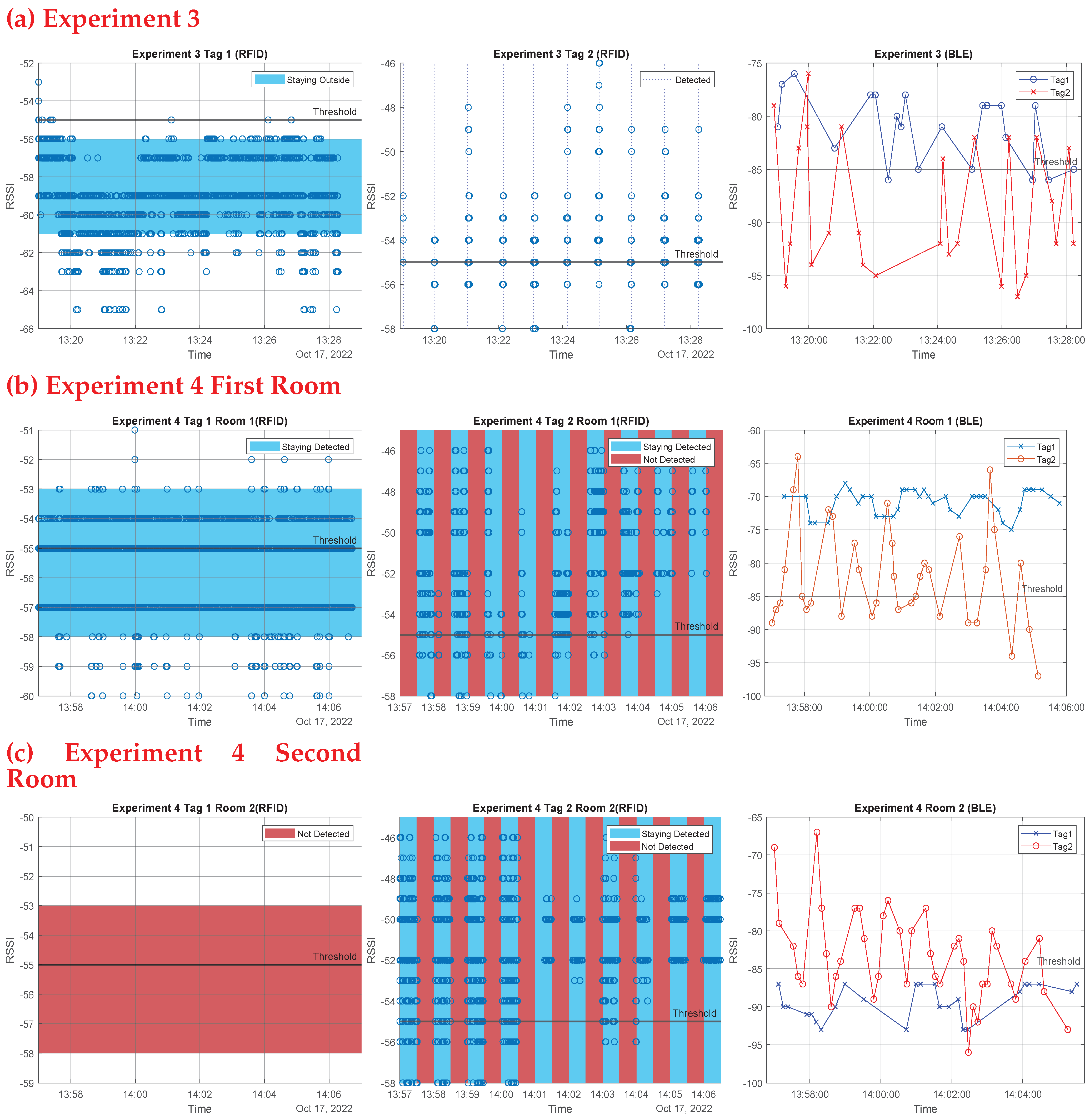
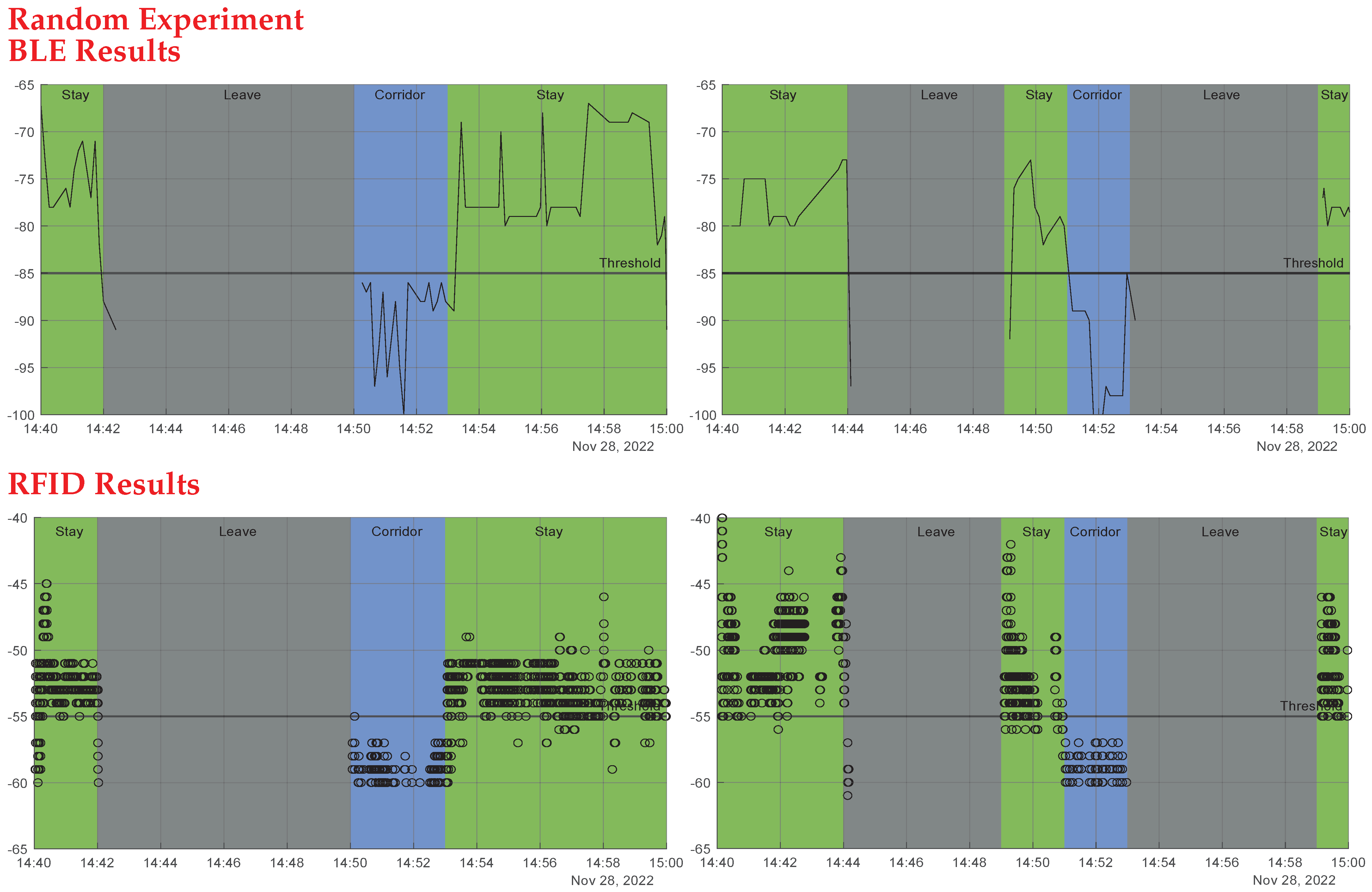
Close contact is determined when two tags are detected for entry at the same time interval in the same room. The system first captures their RSSI entry values and compares these values. If their difference is less than or equal to 3.5 (based on practical tests of tags that were 1 m apart), the system deduces that the two tags are in close proximity. Algorithm 3 uses two beacons in the same room; it was used to overcome some flaws in Algorithm 2 that will be thoroughly explained in
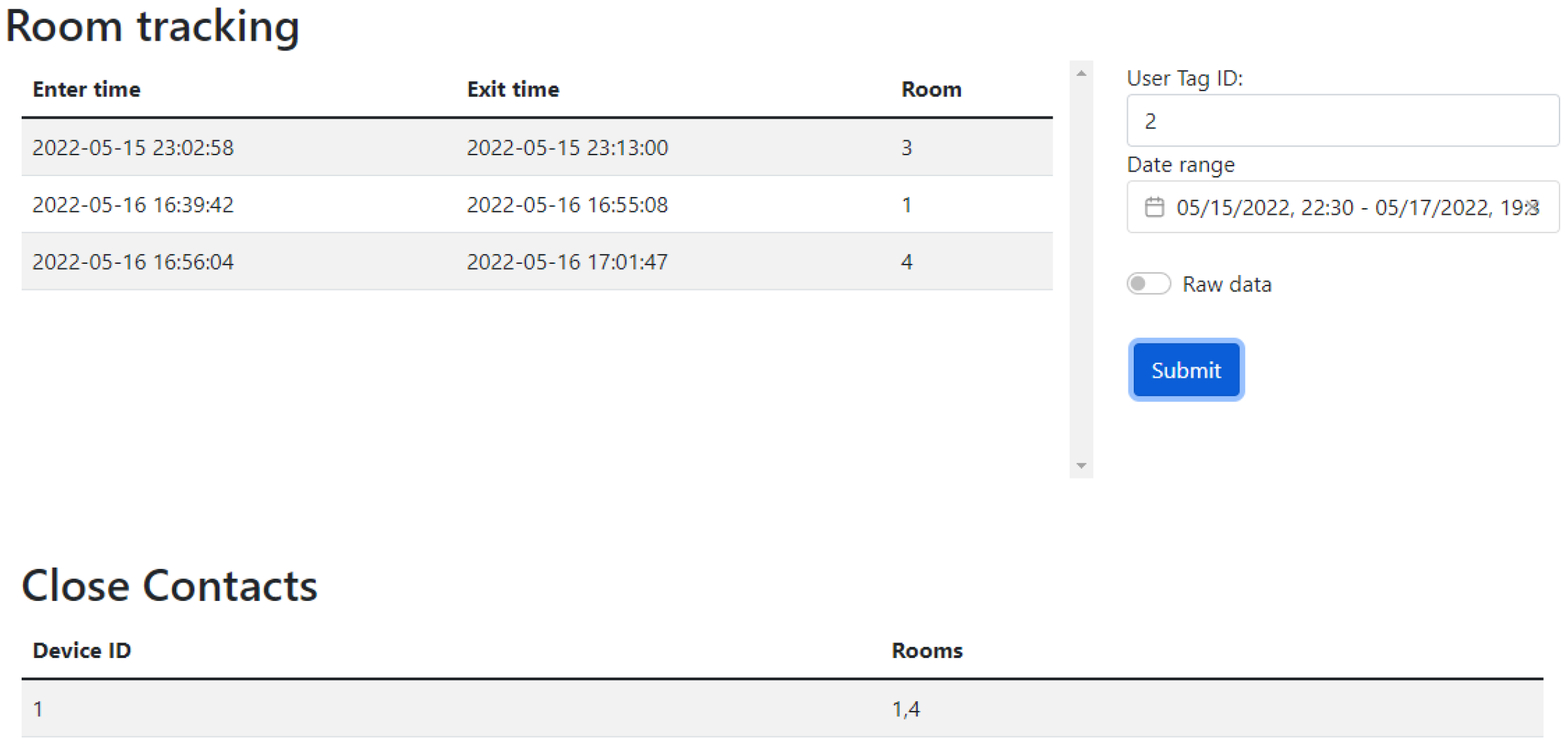
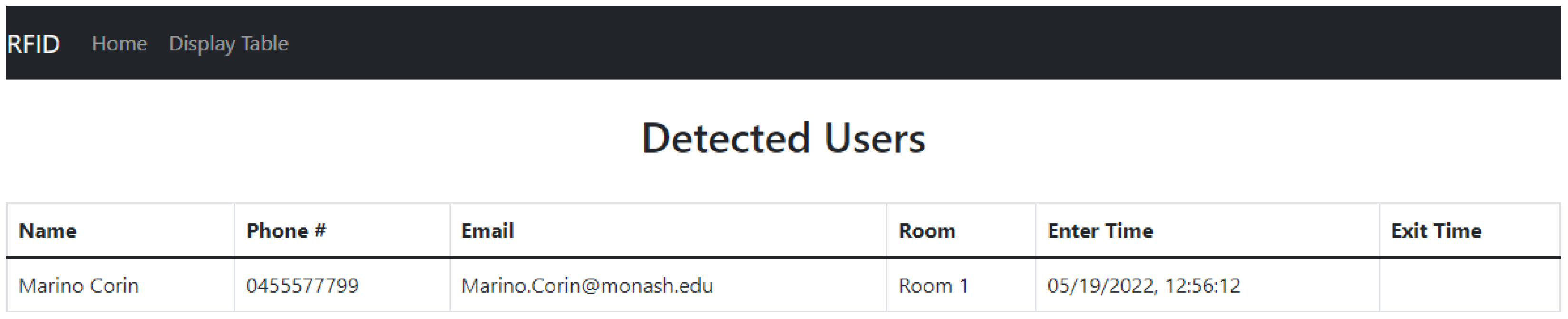
Section 5. In this study, a web interface front-end was developed using the MEAN stack (MongoDB ExpressJS Angular Nodejs) for easy integration with the main database that uses MongoDB and is hosted on the Raspberry Pi. The web interface front-end has two main features. The first is a user interface to allow registration for users’ details with their associated RFID unique ID as aforementioned. The second main feature a display of the
detectedUser database in a more user-friendly table. An example of the display table is shown in
Figure 14.
One potential limitation in this study is the security of the system; data encryption in the database and the addition of server level and database level permissions are among the proposed future system enhancements.
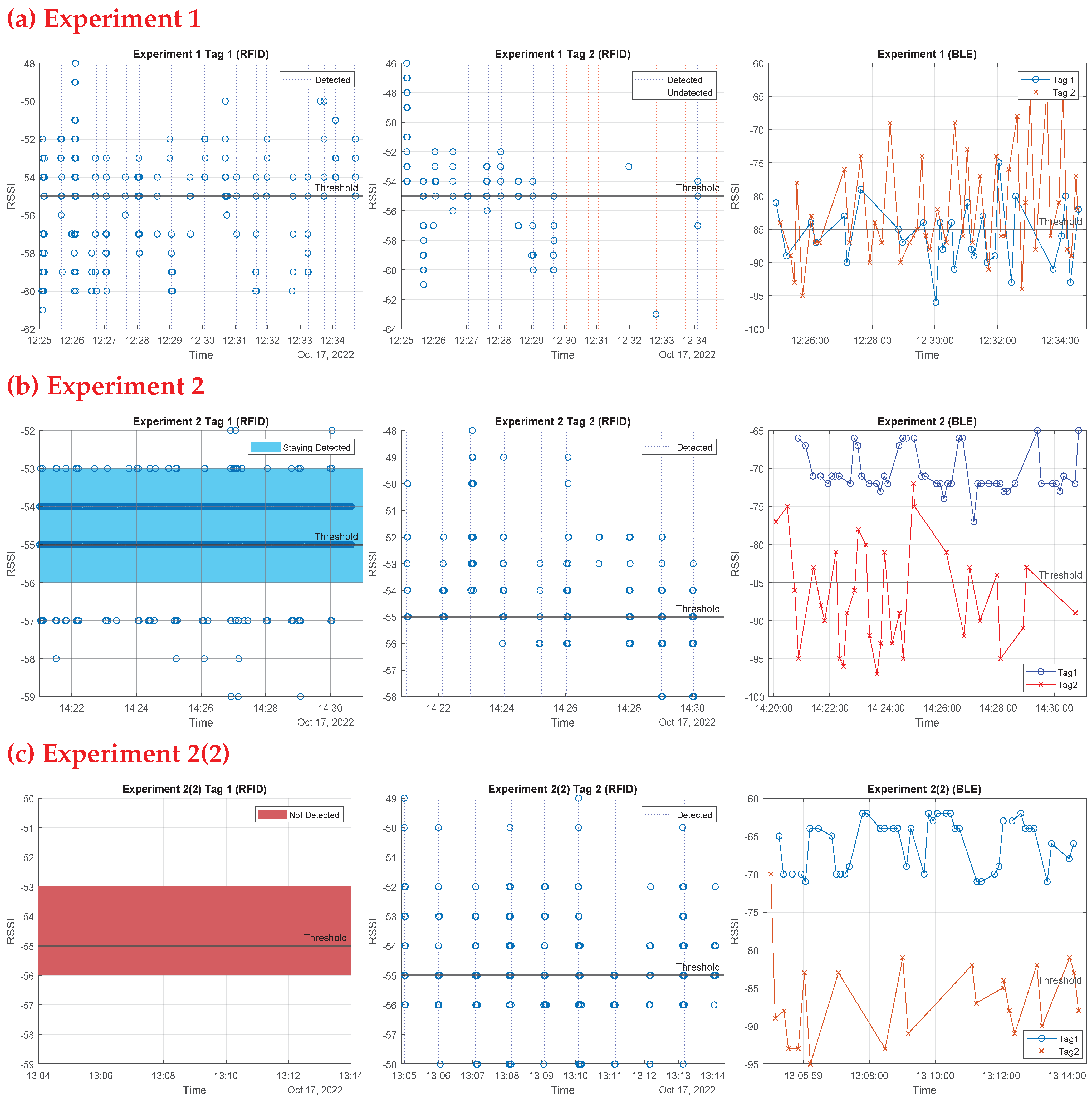
Optimal Reader Placement: One important parameter for the RFID system was the optimal reader placement for enhancing the scanning area, as the system depends on the LoS communication. There were two positions tested: on the side of the entrance and in front of the entrance. Each test scenario was run five times. The results, shown in
Table 4, demonstrate that when the antenna is put in front of the door, the reading region is significantly wider than when it is placed to the side. The green highlighted table cells mean successful attempts, and red highlighted table cells mean unsuccessful attempts. In front of the entrance, the system had a 100% success read rate for both entering and exiting; however, when the antenna was placed on the side of the entrance, it had a 100% entry detection success but only a 40% exit detection success. The beacons placed in front of the entrance will be used throughout the upcoming tests.
6. Discussion
Upon applying both technologies, some drawbacks appeared in each technology. One drawback to using the BLE is the interference with obstacles/walls, and external factors such as absorption, interference, or diffraction can affect the accuracy of calculation as RSSI tends to fluctuate. The greater the distance between the device and the beacon, the more unpredictable the RSSI becomes. The tag may mistakenly get low RSSI values and compared to the threshold that tag would be seen outside the even though the tag has not left the room. On the other hand, the RFID scanning area of the reader is limited, as it depends on LoS communications. Algorithm 2 for RFID, which depends on altering the tags states upon being detected by the antenna based on past history, showed drawbacks when a tag stayed inside the room. Consequently, Algorithm 3 was implemented that needs two readers inside each room, which can be an expensive solution. As a solution, we tested both technologies together using their RSSI values and the thresholding method. As a result we get a more affordable solution with RSSI values enhancing the performance. The BLE can get over the LoS drawback of the RFID, and, moreover, the RFID can get over the BLE RSSI fluctuation issue.
As proposed future system enhancements, we would like to increase the number of tags to practically evaluate the system’s efficiency and scalability. In addition, the system’s security and data encryption are important topics to be considered for better enhancing the systems capabilities.
7. Conclusions
In this research, we proposed two IoT based sensing devices for contact tracing in hospitals and offices settings, aiming to prevent personnel from cross infections, by measuring their close proximity while placing as little strain on them as possible. These devices have been demonstrated to be IoT-enabled, autonomous, low-cost, long-battery-life systems and built with off-the shelf materials for simplicity. In the first approach, a BLE device is proposed, programmed to be used in any environment, indoor or outdoor, simply by changing the path-loss exponent (n). This method locates tags by comparing their RSSI values to practically pre-determined threshold RSSI values; it can also detect close proximity between tag holders in various rooms. The second proposed method for contact tracing is based on RFID technology, and it investigates the usage of two different frequency ranges: high frequency (HF) and ultra high frequency (UHF) RFID systems (UHF). This method was successful in both indoor tag localization and detecting proximity between tags by comparing their RSSI values. Both systems were thoroughly described in terms of operation, hardware, cost, software, and web interfaces. Both systems were set up in an office/hospital-like environment and tested against various life scenarios in order to evaluate their efficiency. The results demonstrated that they met the required criteria and that they can be used to solve the previously indicated problem. It is worth noting that the approaches claimed benefits without sacrificing other aspects, such as power consumption, cost, and simplicity, which distinguish our proposed approaches from previous work.