1. Introduction
Traffic accidents cause driving injuries and property damage. According to World Health Organization (WHO) statistics, about 1.35 million people die in road traffic accidents each year [
1], and road traffic accidents are currently estimated to be the eighth leading cause of death in all age groups globally. In addition to the millions of fatalities, the number of traffic accidents in each country is also quite large. In 2020, according to statistics from the National Highway Traffic Safety Administration (NHTSA), US police reported 5,250,837 traffic accidents [
2]. The China Statistical Yearbook published by the National Bureau of Statistics of China reported 244,674 traffic accidents [
3]. The data in the European Commission’s annual statistical report on road safety are estimated at 757,566 traffic accidents [
4]. From the above data, it can be seen that traffic accidents are very dangerous to the global community. Because traffic accidents often require compensation for high medical bills and vehicle repair costs, people will need car insurance to protect themselves and reduce the burden of compensation.
At present, there are still many problems with car insurance. The first is that insurance fraud often occurs between policyholders and insurance companies during the insurance process, such as some policyholders obtaining insurance premiums by forging or falsifying information, and unscrupulous insurance officers forging policies to obtain insurance premiums from policyholders. Car insurance fraud is estimated to cause
$29 billion in losses each year [
5], and these problems lead to distrust between the public and insurance companies. The second is that in the traditional insurance process, the insurance company has to assign an insurance officer to go out and negotiate with the policyholder on the insurance documents, which will result in the insurance company settling the claim at a much slower speed. When applying for insurance, policyholders often need to bring a lot of documents and spend time meeting and engaging in discussions with insurance personnel, which makes them perceive the process of dealing with insurance matters as troublesome and complicated, and thus they are reluctant to apply for insurance. Third, the insurance company has to bring the application documents and the insured’s information to the medical institution to confirm the insured’s identity when accessing the insured’s medical records as well as to the police agency to obtain authorization for the insured’s traffic accident-related information, which makes the process of obtaining the insured’s information cumbersome and reduces the speed of the claim settlement. All of these problems have created problems for both the insurance company and the policyholder, so it is very important to address them.
To address the challenges mentioned above, a multitude of research efforts have been dedicated to combating car insurance fraud. Notable contributions have been made by Vandervorst et al. [
6] and Faheem et al. [
7], who employed sophisticated machine learning techniques for the detection of car insurance fraud. Vandervorst et al. focused on evaluating data misrepresentation risk: the insurance company can improve their decision-making process in the validation of insurance contracts with potentially misrepresented self-reported information. Faheem et al. focused on the Boruta algorithm, enabling insurance companies to achieve more effective fraud detection, identification, and examination. Additionally, Shaikh et al. [
8] delved into the application of telematics, showcasing its potential to not only reduce instances of car insurance fraud but also improve accident investigation procedures.
Compared to traditional paper insurance documents and the need to repeatedly go out to negotiate, in recent years, many insurance companies have started to use online insurance to make insurance claims. The policyholder only needs to register on the insurance company’s website and can directly start the insurance policy. This form makes the insurance process more convenient by reducing the time it takes the policyholder and the insurance company to process the insurance information and by reducing the generation of paper documents [
9].
Although these practices have improved and optimized the car insurance claims process, there are still some unresolved issues. There is still a risk that policy information may be tampered with by the policyholder or the insurance company, and the insurance information may not be traceable. In the existing online insurance claims system, since the insurance information is stored in the insurance company, if the endpoint of the insurance company was to be attacked, the insurance information would likely be stolen or disappear. The policy information and related documents of the online insurance system are also stored in the insurance company, and a large amount of insurance information will cause the insurance company to pay high data storage costs. Additionally, the interaction between insurance companies and medical and police agencies is still weak, and there is no good way to quickly perform functions such as information sharing and transmission for all three parties.
For these reasons, this study uses blockchain technology to solve the above problems. Blockchain is a type of distributed ledger technology: it includes features such as decentralization, anonymity, traceability, and immutability. Decentralization will spread data across many nodes for storage instead of storing them in a single center, thus preventing centralized data control and allowing users on each node to enjoy the same rights. Anonymity is guaranteed since users on the blockchain use a string of English words and numbers as their names, thus protecting their privacy. Traceability is achieved because each block of data on the blockchain contains the hash value of the previous block of data so that the data in the blockchain can be traced back. Immutability means that once the data have been uploaded, they cannot be corrected. Blockchain technology can also be applied to many fields, including financial services [
10], manufacturing [
11], logistics management [
12], agricultural products [
13], and insurance services [
14,
15]. The introduction of blockchain technology can effectively improve the insurance process, improve the security of policy information, increase the efficiency of insurance claims, and reduce the problem of insurance disputes.
This study proposes an anticounterfeit traceable car insurance claims system through blockchain technology with IPFS and Hyperledger Fabric, and aims to achieve the following research objectives:
- (1)
Immutability: For the security of the insurance data, the data are encrypted, using the hashing operation and uploading the data to the blockchain center to ensure that the data are not tampered with.
- (2)
Decentralized data sharing: In this paper, we use a Hyperledger Fabric to form a consortium chain among insurance companies, medical institutions, and police agencies. If they want to exchange policyholder information, they can do so securely and efficiently through a Hyperledger Fabric mechanism.
- (3)
Traceability: Blockchain technology allows insurance data to be uploaded and stored on the blockchain. If the policyholder or insurance company wants to trace insurance data or past medical information, they can go to the blockchain center and IPFS to compare the data and trace the data.
- (4)
Non-repudiation: Due to the use of the elliptic digital signature algorithm, the data cannot be reversed after it has been transferred to the blockchain, thus providing non-repudiation of the data transfer.
- (5)
Resist man-in-the-middle attacks: To prevent data transmission from being tampered with by malicious people and forming man-in-the-middle attacks, this paper uses digital signatures and asymmetric encryption techniques to protect against them [
16,
17].
- (6)
Reduce storage costs: This article uses IPFS to store some of the data and images generated during the insurance process. Since IPFS is a decentralized storage system, it can reduce data storage costs and permanently store insurance data.
The organization of the rest of the study is as follows.
Section 2 will introduce the technical knowledge used in this study,
Section 3 will introduce the method and framework used in this study,
Section 4 will analyze the security of the method; and
Section 5 will compare the calculation and communication costs and finally conclude this study.
3. Method
3.1. System Architecture
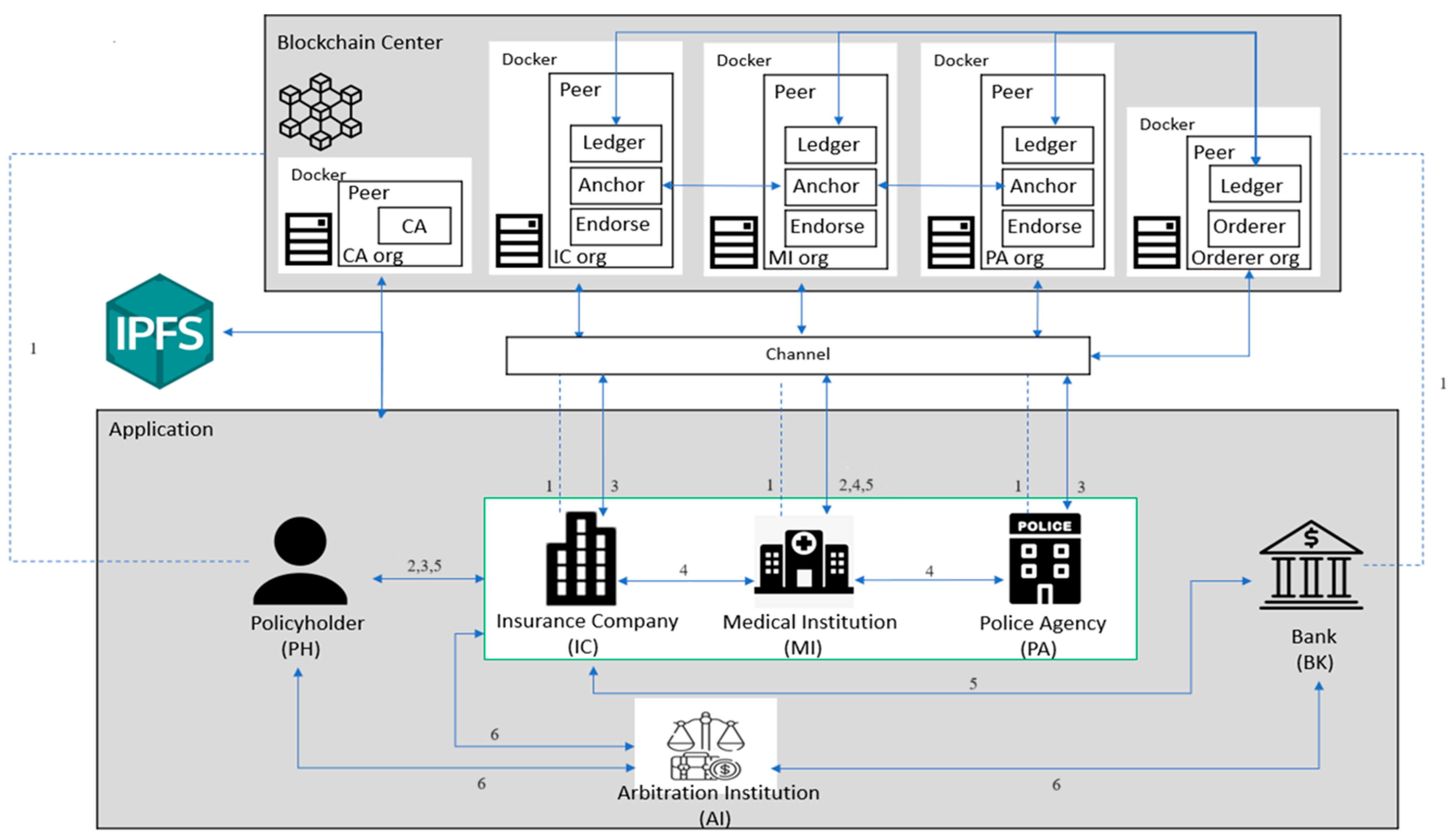
In this paper, we propose a new car accident insurance claims system using blockchain technology. The system architecture consists of nine main actors:
- (1)
The policyholder (PH): People who are insured by an insurance company will receive a claim after a traffic accident.
- (2)
Insurance Company (IC): Insurance companies are responsible for handling insurance claims. After a traffic accident, they will obtain information about the accident from police agencies and medical institutions and notify the bank of the claim.
- (3)
Police Agency (PA): After the traffic accident, the police will go to the accident site to take photos and identify the traffic accident, which will be sent to the insurance company for processing claims.
- (4)
Medical Institution (MI): After the traffic accident, the medical institution will make a medical diagnosis of the insured person, and the diagnostic documents will be submitted to the insurance company after the authorization of the medical institution.
- (5)
Bank (BK): After the accident, the insurance company will use a bank to pay the policyholder’s claim.
- (6)
Blockchain Center (BCC): All actors in the system need to register with the blockchain center. The blockchain center also receives data files for upload and storage.
- (7)
Interplanetary File System (IPFS): Images uploaded to the blockchain, such as photos uploaded by PA, medical receipts, diagnoses uploaded by MI, etc., are transferred to IPFS.
- (8)
Certificate Authorities (CA): Certificate authorities are used to issue personal identity IDs and public and private keys for each character after registration.
- (9)
Arbitration Institution (AI): Any insurance claim dispute between the actors can be appealed to the arbitration institution.
The seamless functioning of the proposed car accident insurance claim system relies on the collaborative efforts of its various actors. The interactions among the PH, IC, PA, MI, BK, BCC, IPFS, CA, and AI form the foundation of a dynamic and interconnected network. As we enter the distinct phases of the system’s operation, a closer look at the registration, insurance purchasing, traffic accident, claims processing, claims payment, and insurance dispute arbitration phases will illuminate the intricate collaboration and information exchange among these key actors. This collaborative ecosystem ensures the integrity and transparency of the insurance claim process, setting the stage for a more detailed exploration in subsequent sections.
Figure 1 shows the main operational structure of the system. Among this figure, a Ledger is a public database that records all transactions. Anchor typically refers to the process in a transaction in which participants confirm or acknowledge the transaction. Endorse typically refers to the process in a transaction where participants confirm or acknowledge the transaction. The following is a description of each phase.
- (1)
Registration Phase: The relevant actors in the system need to apply for an account with the BCC, and after confirmation, they will upload the account information to the BCC. The CA will issue the corresponding public key and private key. In this case, the MI administrator will organize the members of the MI, the PA, and the IC into a consortium chain to pass information about the insured to each other.
- (2)
Insurance Purchasing Phase: After the PH purchases insurance from the IC, the IC and the PH will sign an insurance policy. The PH must provide the bank account to the IC. After signing the insurance policy, it is uploaded to the BCC, and the policy ID is submitted to the PH.
- (3)
Traffic Accident Phase: When the PH is involved in a traffic accident, the PH should first notify the PA to deal with the accident. After the PA arrives at the scene, the PA will take photos to confirm the traffic accident, make a record of the accident, and finally upload the photos and identity records to the BCC. The medical receipts and diagnoses of the PH will be uploaded from the MI to the blockchain center.
- (4)
Claims Processing Phase: When the PH submits a claim, the IC will request authorization of the PH’s medical receipt information of the PH from the MI where the PH was treated through the PH’s ID. After authorization, the claim will be evaluated in conjunction with the accident identification records provided by the PA.
- (5)
Claims Payment Phase: The IC notifies the BK to pay the PH’s claim and then uploads the claim record to the BCC and notifies the PH.
- (6)
Insurance Dispute Arbitration Phase: When an IC denies a claim or when there is an insurance dispute between the parties involved in the traffic accident, arbitration can be conducted through AI.
3.2. Registration Phase
In the registration phase, all roles must first register with the BCC first.
Step 1: Role first generates an identity, , and sends to the BCC.
The BCC generates an ECDSA private key
and calculates the public key
of role
X:
Step 2: The BCC sends back to role X, and role X stores the .
3.3. Insurance Purchasing Phase
When the PH purchases car insurance from the IC, the IC verifies the identity of the PH and signs a policy. The PH will provide the IC with their bank account and then send the generated CC and CD to the BCC.
Step 1: The IC first gives the PH an insurance policy
. The PH will first confirm the content of the policy. After confirmation, the PH will confirm and complete the basic insurance information in the policy to form
; then, the PH selects a random value
and uses the IC’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the sign function of Algorithm 1 to obtain the signature value . Finally, the PH sends to the IC.
Step 2: The IC will check the validity of the timestamp after receiving the encrypted information from the PH:
Use the IC’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the function of Algorithm 2 to verify whether is correct. If it is correct, the IC will obtain the PH’s information. Generate from . Then, generate a claim certificate and claim detail . Finally, upload the policy identity and to the blockchain.
After uploading the information, to allow the PH to view his insurance information, the IC will select a random value
and use the PH’s public key
to encrypt
:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value , which the IC sends to the PH.
Step 3: The PH will check the validity of the timestamp after receiving the encrypted information from the IC:
Use the PH’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the function of Algorithm 2 to verify whether is correct; if it is correct, the PH will be able to view his insurance information.
| Algorithm 1 Function |
| ; |
| ; |
| ; |
| ; |
| return ; |
| Algorithm 2 Function |
| ; |
| ; |
| ; |
|
|
|
|
| return true/false; |
3.4. Traffic Accident Phase
After a traffic accident, the PH will notify the PA of the accident. The PH will provide the PA with his ID, complete the accident registration form and his public key, and provide his driver’s license and vehicle registration to the PA for verification. The PA will take photos of the accident and make an accident identification record. The photos and identification will then be stored in IPFS, and the stored data will be hashed and uploaded to the blockchain with the PH’s ID.
Step 1: The PH first fills out a traffic accident registration form, which is also filled out for the other owner of the vehicle involved in the accident, generating
. Then, the PH selects a random value
and uses the IC’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value , which the PH sends to the PA.
Step 2: The PA will verify the validity of the timestamp after receiving the encrypted information from the PH:
Use the PA’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter
to the Verify function of Algorithm 2 to verify whether
is correct; if it is correct, the PA will obtain the PH’s information and record the traffic accident identity
. After that, the PA saves the photos of the accident
and the traffic accident identification records to IPFS and obtains the hashed photos of the accident
and the accident identification certificate
. Finally, upload
to the blockchain center. After uploading the information, to allow the PH to view his insurance information, the PA will generate the message
with the relevant information, select a random value
, and use the PH’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the PA sends to PH.
Step 3: The PH will verify the validity of the timestamp after receiving the encrypted information from the PA:
Use the PH’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the Verify function of Algorithm 2 to verify whether it is correct. If it is correct, then the PH can view his traffic accident-related information.
3.5. Medical Phase
After filling out the traffic accident information, the PH will go to the MI to seek medical treatment. The PH will need to provide his ID and public key to the MI and fill in basic personal information. Medical receipts and diagnoses will be stored in IPFS by the MI, and the stored data will be washed and uploaded to the blockchain center with the PH’s ID.
Step 1: The PH first fills out basic personal information and generates
; then, the PH selects a random value
and uses the MI’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value , which the PH sends to the MI.
Step 2: The MI will check the validity of the timestamp after receiving the encrypted information from the PH:
The MI’s private key is used to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter
to the Verify function of Algorithm 2 to verify whether
is correct; if it is correct, the MI will obtain the PH’s information and save the PH’s medical diagnosis and medical receipt data to IPFS, and then it will obtain the hashed diagnosis
and receipts
. Finally, the PH uploads the
to the blockchain. After the PH uploads the information, to allow the PH to view his insurance information, the MI will generate the message
with the relevant information, select a random value
, and use the PH’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value , which the MI sends to the PH.
Step 3: The PH will check the validity of the timestamp after receiving the encrypted information from the MI:
Use the PH’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the Verify function of Algorithm 2 to verify whether it is correct; if it is correct, then the PH can view his medical information.
3.6. Claims Processing Phase
When the PH has received the relevant documents from the PH and MI, he can notify the IC to proceed with the claim processing. The PH will authorize the IC to have access to the PH’s information and to process the claim.
3.6.1. Request for Authorization of the Traffic Accident Identification Process
After the PA has processed the PH’s accident identification data, the PH can notify the IC to proceed with claim processing. The IC will submit the relevant policyholder’s claim documents and its ID to the PA to identify itself. After the PA agrees to authorize the information, the IC can obtain the policyholder’s information regarding the identification of the traffic accident.
Step 1: The PH submits his identity and traffic accident identity to the IC for authorization. Once the information is available, the IC will provide the data access to the PA.
Step 2: The IC will send a message
to the PA with the identity of the IC and the policy identity, claim certificate, claim details, ID, and traffic accident identity of the PH. The system encrypts the data content and generates
; then, the IC selects a random value
and uses the PA’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value . Finally, the IC sends to PA:
Step 3: The PA will check the validity of the timestamp after receiving the encrypted information from the IC:
Use the PA’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter
to the Verify function of Algorithm 2 to verify whether
is correct; if it is correct, the PA will obtain the application information from the IC. Finally, upload the
to the blockchain. After uploading the information, to allow the IC to view the PH’s traffic accident identification, the PA will generate the message
with the relevant information, select a random value
, and use the IC’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the PA sends to IC.
Step 4: The IC will verify the validity of the timestamp after receiving the encrypted information from the PA:
Use the IC’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the Verify function of Algorithm 2 to verify whether is correct; if it is correct, then the IC can view the information related to the identification of the PH’s traffic accidents.
3.6.2. Request for Authorization of the Medical Diagnostic Information Process
The IC will request authorization for the PH’s medical information from the MI after receiving the traffic accident identification records. Once the MI has authorized the information, the IC will obtain the medical diagnosis and receipts and combine them with the identification records to process the claim.
Step 1: The PH submits his identity and the identity of the MI where he was treated at the time of the traffic accident to the IC for authorization; once the information is available, the IC will enable the data access of the MI.
Step 2: The IC will send a message
to the MI with the identity of the IC and the policy identity, claim certificate, claim details, and ID. The system encrypts the data content and generates
; then, the IC selects a random value
and uses the MI’s public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the IC sends to MI.
Step 3: The MI will verify the validity of the timestamp after receiving the encrypted information from the IC:
Use the MI’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter
to the Verify function of Algorithm 2 to verify whether
is correct. If it is correct, the MI will obtain the application information from the IC. Finally, upload the
to the blockchain. After uploading the information, to allow the IC to view the medical diagnosis and medical receipts of the PH, the IC will generate the message
with the relevant information, select a random value
, and use the public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the MI sends to the IC.
Step 4: The IC will check the validity of the timestamp after receiving the encrypted information from the MI:
Use the IC’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter to the Verify function of Algorithm 2 to verify whether is correct; if it is correct, then the IC can view the PH’s medical diagnosis and medical receipts.
3.7. Claims Payment Phase
After the IC confirms the claim, they will notify the BK to pay the claim to the PH. The BK will notify the PH of the successful payment.
Step 1: The IC encrypts the PH’s identification ID, bank account ID, and the insurance policy signed by the PH to generate a message
; then, the IC selects a random value
and uses the public key
for encryption:
Then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the IC sends to BK.
Step 2: The BK will check the validity of the timestamp after receiving the encrypted information from the IC:
Uses the BK’s private key to decrypt the encrypted data and obtain the content:
Then, calculate the ECDSA parameters:
Pass the parameter
to the Verify function of Algorithm 2 to verify whether
is correct; if it is correct, the BK will obtain the data and call the smart contract for payment of compensation. After the payment, the BK will upload
to the blockchain center; then, the BK will send a notification
to the PH, and the BK will select a random value
; then, calculate the ECDSA parameters:
Pass the parameter to the Sign function of Algorithm 1 to obtain the signature value ; then, the BK sends to the PH.
Step 3: The PH will check the validity of the timestamp after receiving the encrypted information from the BK:
Then, calculate the ECDSA parameters:
Pass the parameter to the Verify function of Algorithm 2 to verify whether is correct; if it is correct, the PH receives the BK remittance notification and successfully obtains the claim.
3.8. Insurance Dispute Arbitration Phase
When a dispute arises between the PH, the IC or the BK, the PH can propose an arbitration application to the AI. The PH will provide related information for the AI to confirm the PH’s information and identity.
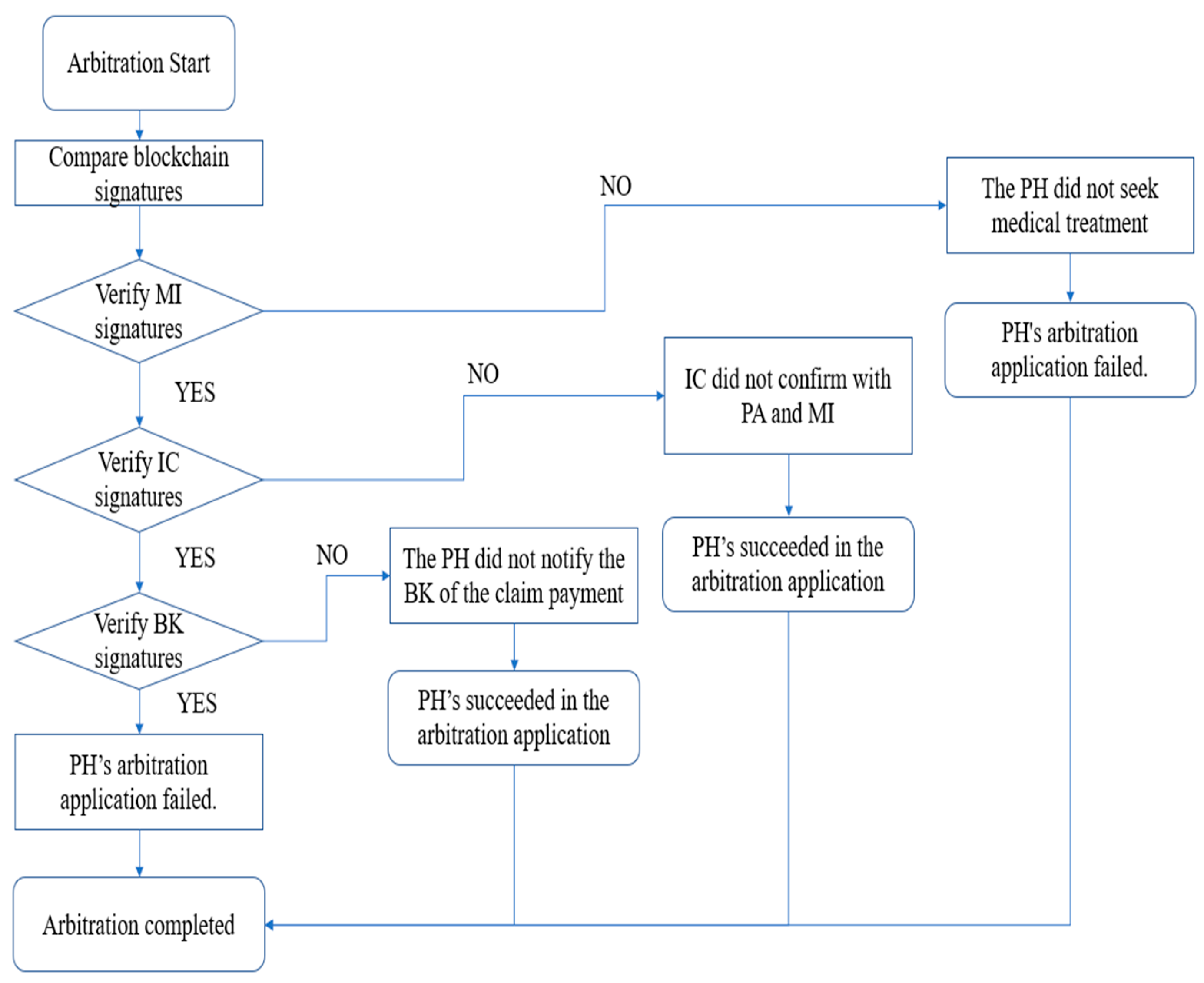
When arbitrating insurance disputes, the AI confirms the accuracy of each phase of operation by comparing the information and signatures on the blockchain.
Figure 2 shows the flow chart during the insurance dispute arbitration phase.
Step 1: To confirm the authenticity of the event, the PH must first submit , , and to the AI. After confirming receipt of the PH’s documents, the AI will verify them. If the verification fails, it means that the PH has provided incorrect information; otherwise, the verification is successful, and it will begin signing verification.
Step 2: The AI will first pass the PH’s and obtain the signature values , , , , , , , and , and then it will verify according to the signature value.
The AI will first verify
and
:
If the verification fails, it means that the PH did not perform the action of medical treatment, and if the verification is successful, the procedure will proceed to the next step.
Step 3: The AI then verifies the signature of the PH and will simultaneously verify
,
,
, and
:
If one of the verifications fails, it means that the IC has not processed the claim with the PA and MI, and if the verification is successful, the procedure will proceed to the next step.
Step 4: The AI will take the signature of the verifying BK and verify
and
:
If the verification fails, it means that the BK did not proceed with the claim payment.
If all of the above steps have been verified successfully, the AI can determine the validity of the insurance claim and terminate the arbitration procedure.