A Novel Hybrid Convolutional Neural Network- and Gated Recurrent Unit-Based Paradigm for IoT Network Traffic Attack Detection in Smart Cities
Abstract
1. Introduction
- Integration of Convolutional Neural Networks (CNNs) and Gated Recurrent Units (GRUs) to capture both spatial and sequential features in network traffic data, enhancing the model’s ability to identify attacks.
- Achieved an impressive overall accuracy rate of 99% after ten training epochs, demonstrating the effectiveness of the proposed approach.
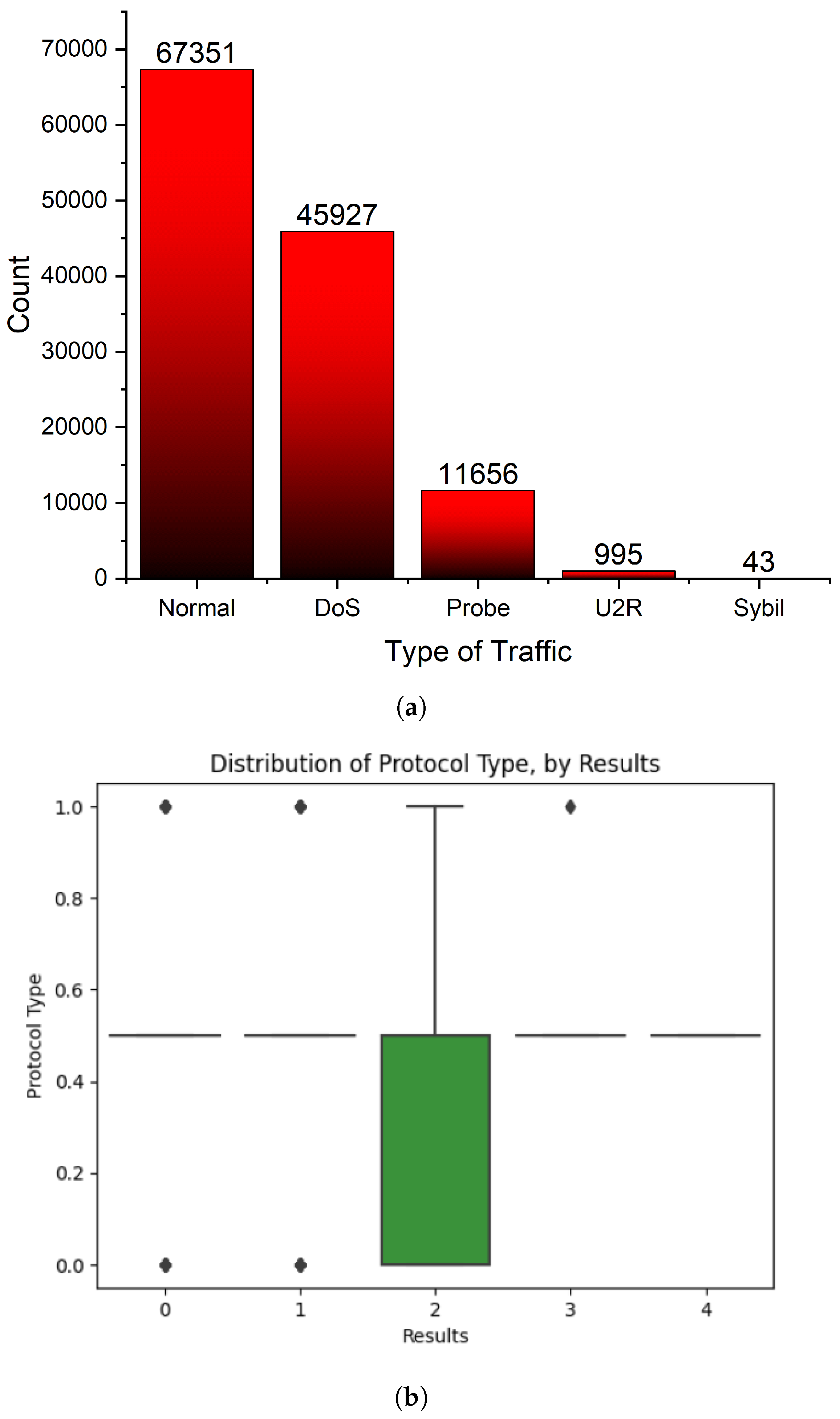
- Proficiency in distinguishing various attack categories, including ‘Normal’, ‘DoS’ (Denial of Service), ‘Probe’, ‘U2R’ (User to Root), and ’Sybil’, as shown in the classification report.
2. Related Work
- Traditional approaches may not be able to keep up with the immense size and ever-changing nature of IoT networks, in which many devices produce vast volumes of data in near real-time [23].
- Traditional solutions are less effective against changing attack tactics since they depend on static rules or signatures to identify threats [24].
- Traditional approaches may produce a high number of false positives, which results in unwanted notifications and extra work for security staff [24].
- Sensor readings, network traffic, and device information are just a few examples of the many types of data that are generated by IoT networks. It is possible that conventional approaches will have difficulty analysing and comprehending such varied data [25].
- The low processing capabilities of many IoT devices make it difficult to deploy resource-intensive classical detection techniques [23].
- Delays in identifying and reacting to assaults caused by using traditional approaches might be disastrous in IoT settings, in which prompt action is required [23].
- Traditional approaches may only be able to detect anomalies that fit established attack patterns, making it difficult to identify innovative or complex attacks [26].
3. Proposed Approch
3.1. Loss Function
3.2. Optimiser
| Algorithm 1: Adam algorithm |
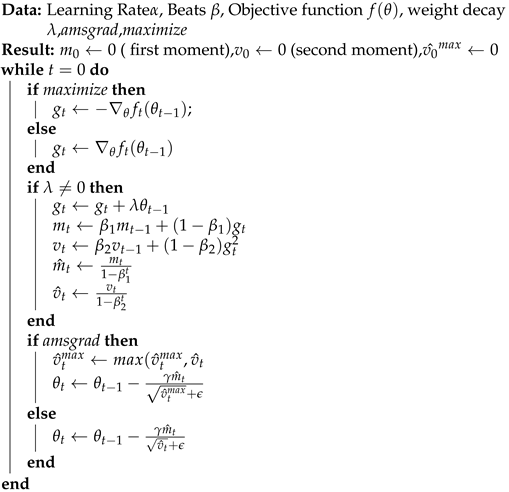 |
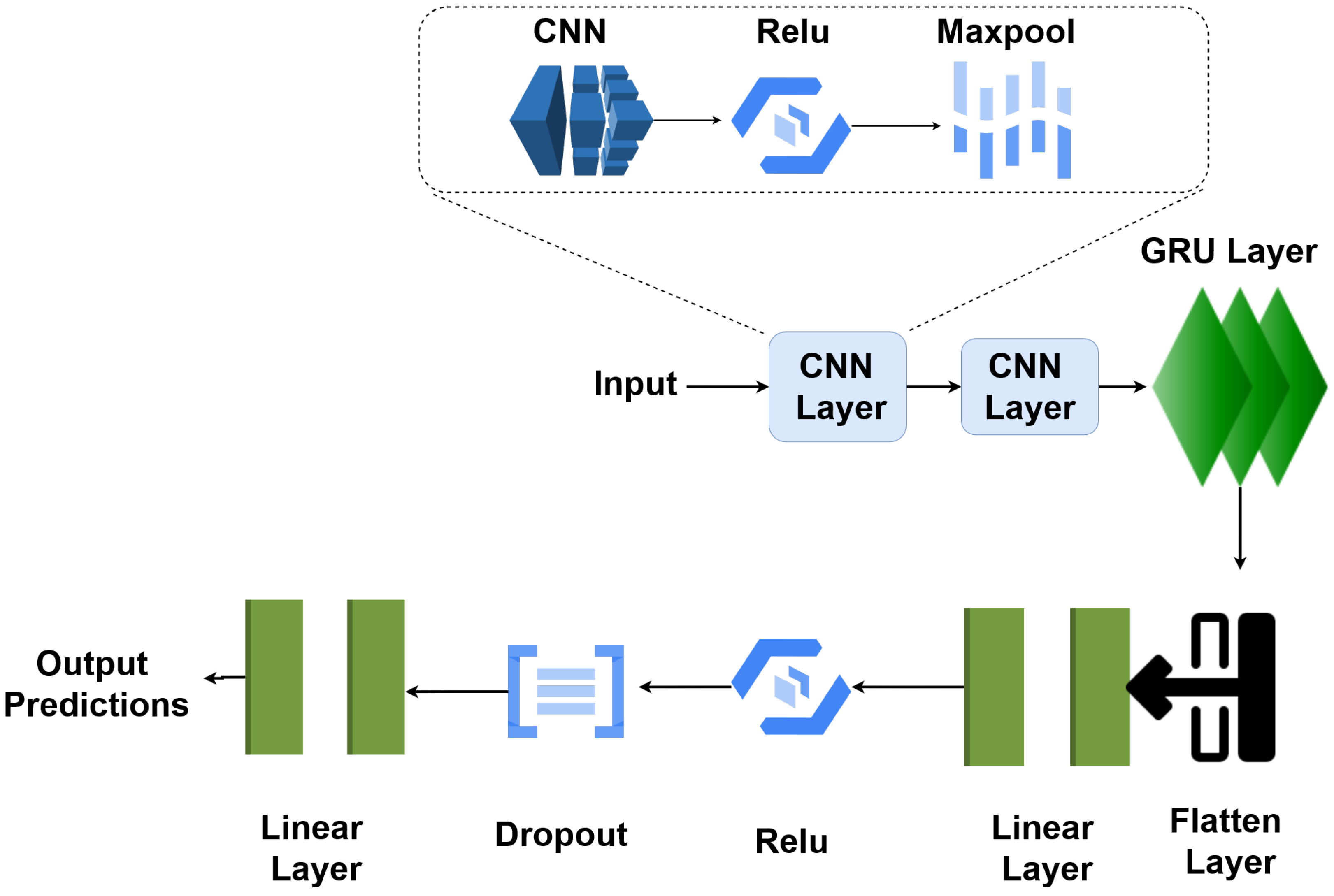
3.3. Model Architecture
- The initial layer, labelled ‘DeepLearning’, represents the overall architecture.
- The first layer is a 1D convolutional layer (‘Conv1d’) with a depth of 32 and is designed to extract features from the input data. This layer has 1344 parameters.
- The ‘ReLU’ activation layer follows the convolutional layer, introducing non-linearity to the model.
- Next is a ‘MaxPool1d’ layer, which performs max-pooling to downsample the data and reduce its spatial dimensions.
- This is followed by another convolutional layer (‘Conv1d’) which has a depth of 128, further extracting hierarchical features from the data. This layer has 4224 parameters.
- Again, a ‘ReLU’ activation layer introduces non-linearity.
- Subsequently, a ‘MaxPool1d’ layer performs max-pooling.
- This is followed by the ‘GRU’ (Gated Recurrent Unit) layer, which has 128 units. GRUs are recurrent layers that can capture sequential patterns in the data.
- The ‘Flatten’ layer reshapes the output from the previous layers into a flat vector.
- Two fully connected (‘Linear’) layers follow, one with 64 and other with 5 output units. These layers have 8256 and 325 parameters, respectively.
- ‘ReLU’ activation is applied to the first fully connected layer, introducing non-linearity.
- A ‘Dropout’ layer is included for regularization, which helps prevent overfitting.
- Finally, the last ‘Linear’ layer produces the model’s output with 5 units, corresponding to the different attack categories.
4. Results and Disscussion
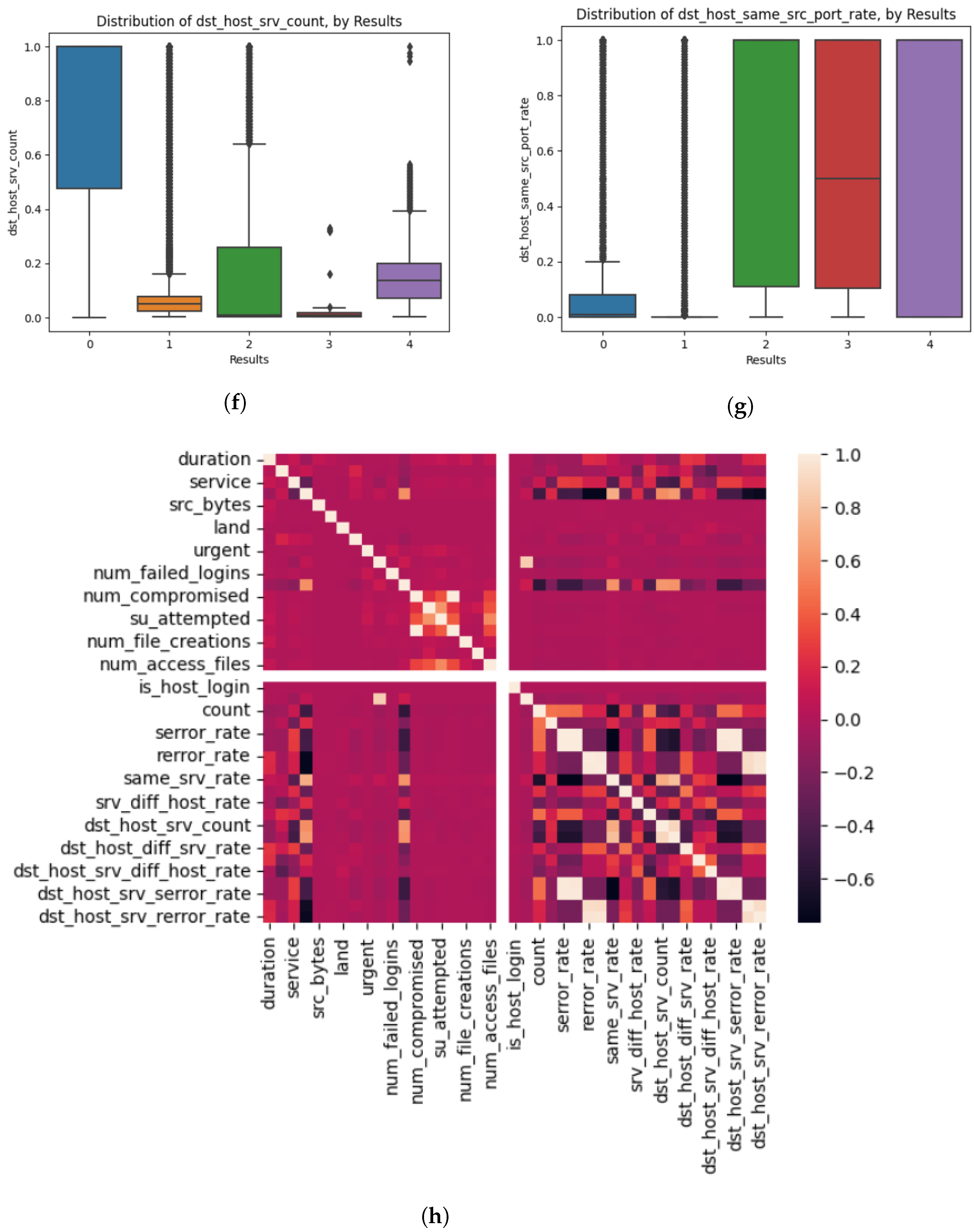
4.1. Data Representation
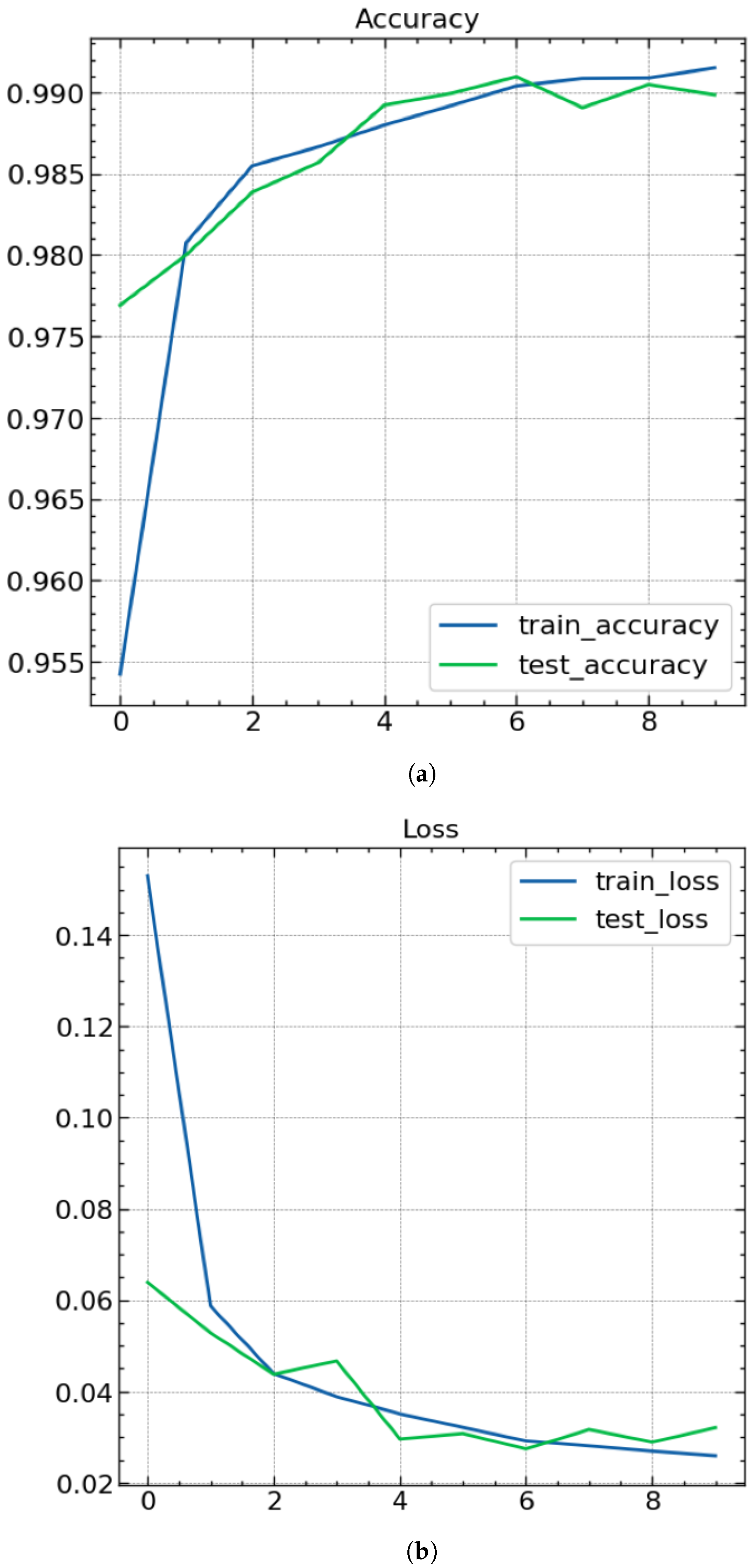
4.2. Accuracy and Loss Curves
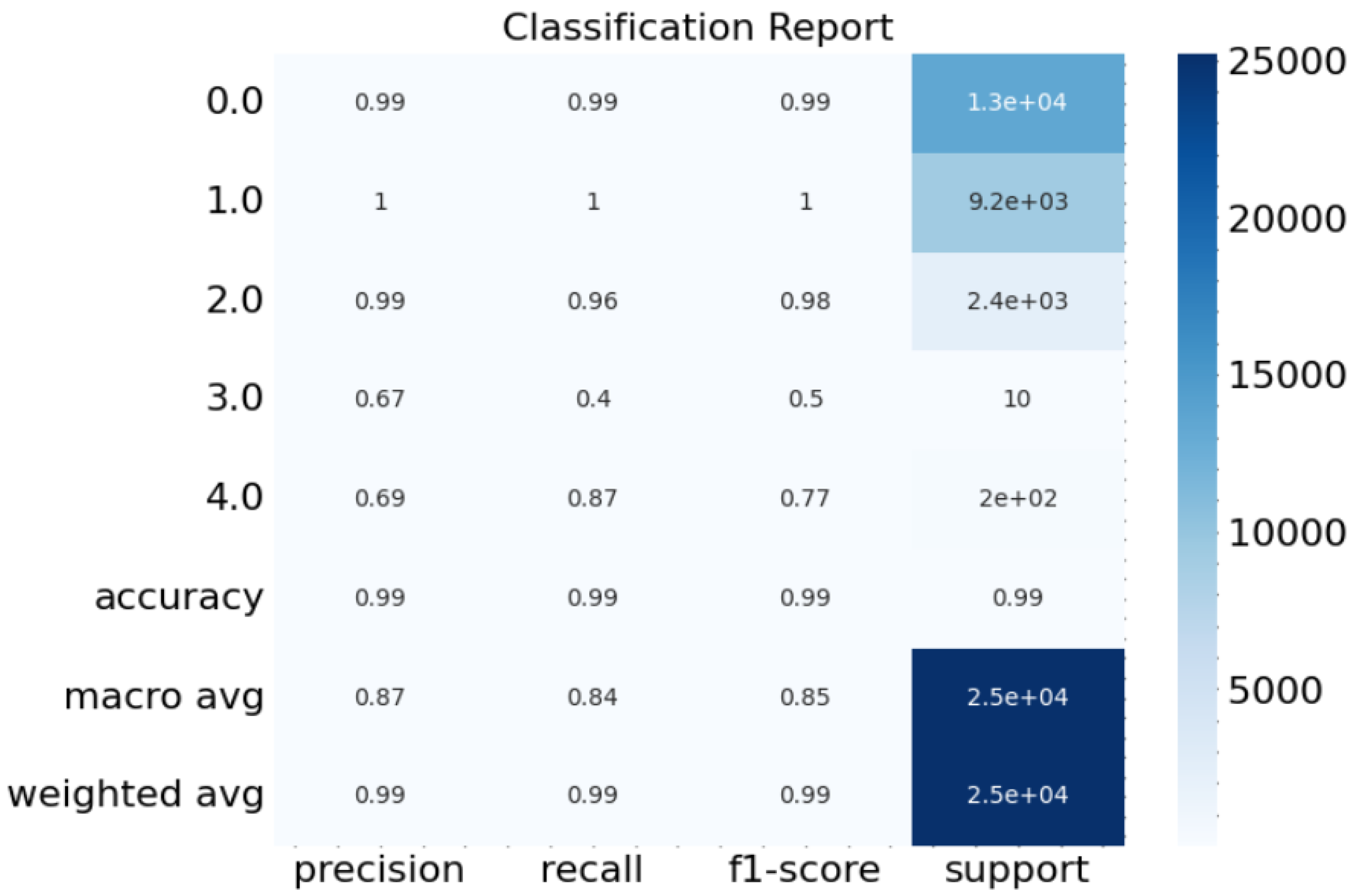
4.3. Classification Report
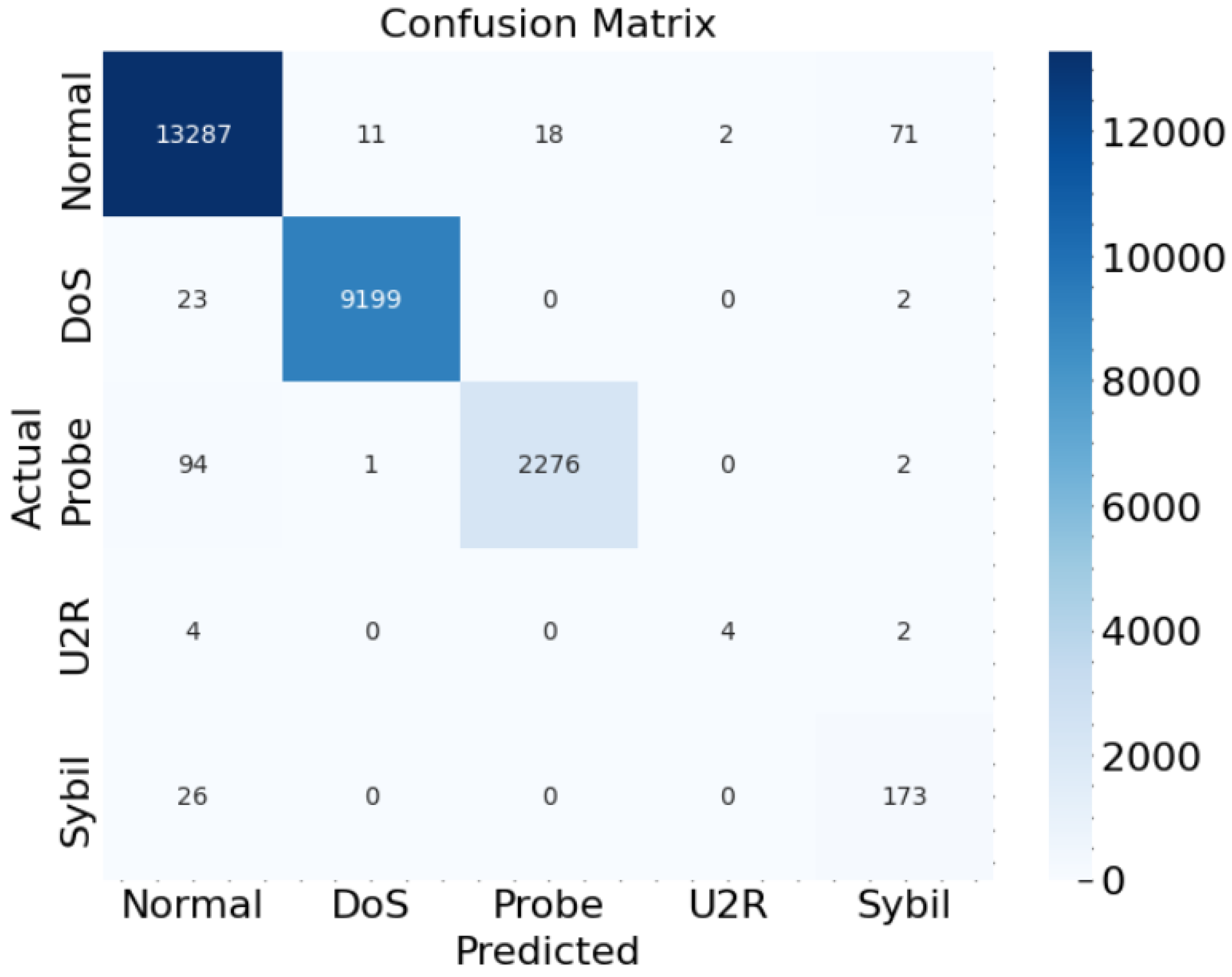
4.4. Confussion Matrix
- For “Normal” attacks, the majority of instances (13,287) are correctly classified as “Normal”, with only a small number of instances (11) mistakenly classified as “DoS” and a few instances (18) misclassified as “Probe”. Additionally, a few “Normal” instances are incorrectly classified as “U2R” and “Sybil”, with 2 and 71 instances, respectively.
- For “DoS” attacks, the model demonstrates excellent performance, correctly classifying 9199 instances as “DoS”. There are very few false negatives (instances mistakenly classified as something other than “DoS”), with only 25 in total.
- In the case of ‘Probe’ attacks, the model correctly identifies the majority of instances (2276), with just a couple of instances misclassified as ‘Normal’ and ’U2R’.
- “U2R” attacks, being a relatively rare class with only 10 instances, have some misclassifications. Four instances are correctly classified, while six are incorrectly classified as “Normal”.
- “Sybil” attacks are correctly identified for the most part, with 173 instances correctly classified and only 26 instances mistakenly classified as ‘Normal’.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Tiwari, A.; Garg, R. Adaptive Ontology-Based IoT Resource Provisioning in Computing Systems. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–18. [Google Scholar] [CrossRef]
- Raj, M.G.; Pani, S.K. Chaotic whale crow optimization algorithm for secure routing in the IoT environment. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–25. [Google Scholar] [CrossRef]
- Srivastava, A.M.; Rotte, P.A.; Jain, A.; Prakash, S. Handling data scarcity through data augmentation in training of deep neural networks for 3D data processing. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–16. [Google Scholar] [CrossRef]
- Khanam, S.; Tanweer, S.; Khalid, S.S. Future of Internet of Things: Enhancing Cloud-Based IoT Using Artificial Intelligence. Int. J. Cloud Appl. Comput. 2022, 12, 1–23. [Google Scholar]
- Kiran, M.A.; Pasupuleti, S.K.; Eswari, R. Efficient Pairing-Free Identity-Based Signcryption Scheme for Cloud-Assisted IoT. Int. J. Cloud Appl. Comput. 2022, 12, 1–15. [Google Scholar]
- Rath, M.; Pattanayak, B. Technological improvement in modern health care applications using internet of things (iot) and proposal of novel health care approach. Int. J. Hum. Rights Healthc. 2019, 12, 148–162. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven iot ehealth: Promises and challenges of iot in medicine and healthcare. Future Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.K.; Lobiyal, D.; Chui, K.T.; Santaniello, D.; Rafsanjani, M.K. A Novel Decentralized Group Key Management Scheme for Cloud-Based Vehicular IoT Networks. Int. J. Cloud Appl. Comput. 2022, 12, 1–34. [Google Scholar]
- Jacobs, N.; Edwards, P.; Markovic, M.; Cottrill, C.; Salt, K. Who trusts in the smart city? transparency, governance, and the internet of things. Data Policy 2020, 2, E11. [Google Scholar] [CrossRef]
- Bibri, S. The iot for smart sustainable cities of the future: An analytical framework for sensor-based big data applications for environmental sustainability. Sustain. Cities Soc. 2018, 38, 230–253. [Google Scholar] [CrossRef]
- Suryotrisongko, H.; Ananto, P. The potential of microservice architecture for internet of things (iot) in smart city, a literature review. J. Ilm. Kursor 2017, 9, 9–14. [Google Scholar] [CrossRef][Green Version]
- Janssen, M.; Luthra, S.; Mangla, S.; Rana, N.; Dwivedi, Y. Challenges for adopting and implementing iot in smart cities. Internet Res. 2019, 29, 1589–1616. [Google Scholar] [CrossRef]
- Avila-Garzon, C.; Balaguera, M.; Tabares-Morales, V. An Agent-Based Social Simulation for Citizenship Competences and Conflict Resolution Styles. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–23. [Google Scholar] [CrossRef]
- Tembhurne, J.V.; Almin, M.M.; Diwan, T. Mc-DNN: Fake news detection using multi-channel deep neural networks. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–20. [Google Scholar] [CrossRef]
- Ling, Z.; Hao, Z.J. Intrusion detection using normalized mutual information feature selection and parallel quantum genetic algorithm. Int. J. Semant. Web Inf. Syst. 2022, 18, 1–24. [Google Scholar] [CrossRef]
- Boulos, M.; Al-Shorbaji, N. On the internet of things, smart cities and the who healthy cities. Int. J. Health Geogr. 2014, 13, 10. [Google Scholar] [CrossRef]
- Alaiz-Moretón, H.; Aveleira-Mata, J.; Ondicol-Garcia, J.; Muñoz-Castañeda, A.; García-Rodríguez, I.; Benavides, C. Multiclass classification procedure for detecting attacks on mqtt-iot protocol. Complexity 2019, 2019, 6516253. [Google Scholar] [CrossRef]
- Madhu, S.; Padunnavalappil, S.; Saajlal, P.P.; Vasudevan, V.A.; Mathew, J. Powering up an IoT-enabled smart home: A solar powered smart inverter for sustainable development. Int. J. Softw. Sci. Comput. Intell. 2022, 14, 1–21. [Google Scholar] [CrossRef]
- Sharma, R.; Sharma, N. Attacks on resource-constrained IoT devices and security solutions. Int. J. Softw. Sci. Comput. Intell. 2022, 14, 1–21. [Google Scholar] [CrossRef]
- Al-Qerem, A.; Alauthman, M.; Almomani, A.; Gupta, B.B. IoT transaction processing through cooperative concurrency control on fog–cloud computing environment. Soft Comput. 2020, 24, 5695–5711. [Google Scholar] [CrossRef]
- Battula, S.K.; Naha, R.K.; Kc, U.; Hameed, K.; Garg, S.; Amin, M.B. Mobility-Based Resource Allocation and Provisioning in Fog and Edge Computing Paradigms: Review, Challenges, and Future Directions. In Mobile Edge Computing; Springer: Cham, Switzerland, 2021; pp. 251–279. [Google Scholar]
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Hussain, F.; Hussain, R.; Hassan, S.; Hossain, E. Machine learning in iot security: Current solutions and future challenges. IEEE Commun. Surv. Tutorials 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Haji, S.; Ameen, S. Attack and anomaly detection in iot networks using machine learning techniques: A review. Asian J. Res. Comput. Sci. 2021, 9, 30–46. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. Mqttset, a new dataset for machine learning techniques on mqtt. Sensors 2020, 20, 6578. [Google Scholar] [CrossRef] [PubMed]
- Xie, L.; Ni, H.; Yang, H.; Zhang, J. A key business node identification model for internet of things security. Secur. Commun. Netw. 2020, 2020, 6654283. [Google Scholar] [CrossRef]
- Tayyab, M.; Marjani, M.; Jhanjhi, N.; Hashem, I.A.T.; Usmani, R.S.A.; Qamar, F. A Comprehensive Review on Deep Learning Algorithms: Security and Privacy Issues. Comput. Secur. 2023, 131, 103297. [Google Scholar] [CrossRef]
- Deepa, N.; Pham, Q.V.; Nguyen, D.C.; Bhattacharya, S.; Prabadevi, B.; Gadekallu, T.R.; Maddikunta, P.K.R.; Fang, F.; Pathirana, P.N. A survey on blockchain for big data: Approaches, opportunities, and future directions. Future Gener. Comput. Syst. 2022, 131, 209–226. [Google Scholar] [CrossRef]
- Maleh, Y.; Shojafar, M.; Alazab, M.; Romdhani, I. Blockchain for Cybersecurity and Privacy: Architectures, Challenges, and Applications; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar]
- Lian, G. Blockchain-Based Secure and Trusted Distributed International Trade Big Data Management System. Mob. Inf. Syst. 2022, 2022, 7585288. [Google Scholar] [CrossRef]
- Tayyab, M.; Marjani, M.; Jhanjhi, N.; Hashim, I.A.T.; Almazroi, A.A.; Almazroi, A.A. Cryptographic based secure model on dataset for deep learning algorithms. CMC Comput. Mater. Contin. 2021, 69, 1183–1200. [Google Scholar] [CrossRef]
- Ahmed, K.; Tahir, M.; Habaebi, M.; Lau, S.; Ahad, A. Machine learning for authentication and authorization in iot: Taxonomy, challenges and future research direction. Sensors 2021, 21, 5122. [Google Scholar] [CrossRef]
- Sharma, B.; Sharma, L.; Lal, C.; Roy, S. Explainable artificial intelligence for intrusion detection in IoT networks: A deep learning based approach. Expert Syst. Appl. 2023, 238, 121751. [Google Scholar] [CrossRef]
- Azimjonov, J.; Kim, T. Stochastic gradient descent classifier-based lightweight intrusion detection systems using the efficient feature subsets of datasets. Expert Syst. Appl. 2024, 237, 121493. [Google Scholar] [CrossRef]
- Feng, X.; Xia, H.; Xu, S.; Xu, L.; Zhang, R. TSGS: Two-stage security game solution based on deep reinforcement learning for Internet of Things. Expert Syst. Appl. 2023, 234, 120965. [Google Scholar] [CrossRef]
- Akshaya, V.; Mandala, V.; Anilkumar, C.; VishnuRaja, P.; Aarthi, R. Security enhancement and attack detection using optimized hybrid deep learning and improved encryption algorithm over Internet of Things. Meas. Sens. 2023, 30, 100917. [Google Scholar]
- Muna, R.K.; Hossain, M.I.; Alam, M.G.R.; Hassan, M.M.; Ianni, M.; Fortino, G. Demystifying machine learning models of massive IoT attack detection with Explainable AI for sustainable and secure future smart cities. Internet Things 2023, 24, 100919. [Google Scholar] [CrossRef]
- Ding, F.; Li, H.; Luo, F.; Hu, H.; Cheng, L.; Xiao, H.; Ge, R. DeepPower: Non-intrusive and deep learning-based detection of IoT malware using power side channels. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security, New York, NY, USA, 5–9 October 2020; pp. 33–46. [Google Scholar]
- Fowdur, H.; Armoogum, S.; Suddul, G.; Armoogum, V. Detecting Malicious IoT Traffic using Supervised Machine Learning Algorithms. In Proceedings of the 2022 IEEE Zooming Innovation in Consumer Technologies Conference (ZINC), Novi Sad, Serbia, 25–26 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 209–213. [Google Scholar]
- CrossEntropyLoss. Available online: https://pytorch.org/docs/stable/generated/torch.nn.CrossEntropyLoss.html (accessed on 3 October 2023).
- Adam. Available online: https://pytorch.org/docs/stable/generated/torch.optim.Adam.html (accessed on 3 October 2023).
- Kingma, D.P.; Ba, J. Adam: A method for stochastic optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]
| Ref. | Dataset | Method | Accuracy | Precision | F1 | Recall |
|---|---|---|---|---|---|---|
| [33] | NSL-KDD | 1D-CNN | 0.99 | 1 | 0.99 | 0.99 |
| 2D-CNN | 0.99 | 1 | 1 | 1 | ||
| UNSW-NB 15 | 1D-CNN | 0.80 | 0.48 | 0.06 | 0.10 | |
| 2D-CNN | 0.81 | 0.57 | 0.04 | 0.07 | ||
| [34] | KDD-CUP-1999 | Stochastic gradient descent classifier (SGDC) | 0.9961 | 0.9724 | 0.9713 | 0.9718 |
| BotIoT-2018 | SGDC | 0.88 | 0.9403 | 0.9285 | 0.9344 | |
| N-BaIoT-2021 | SGDC | 0.9691 | 0.9979 | 0.9513 | 0.9089 | |
| [35] | NA | Game Theory | NA | NA | NA | NA |
| [36] | NSL-KDD | Hybrid-CNN | 0.92 | 0.90 | 0.85 | 0.81 |
| [37] | OTD20 | XG-Boost | 0.86 | 1 | 1 | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gupta , B.B.; Chui, K.T.; Gaurav , A.; Arya , V.; Chaurasia , P. A Novel Hybrid Convolutional Neural Network- and Gated Recurrent Unit-Based Paradigm for IoT Network Traffic Attack Detection in Smart Cities. Sensors 2023, 23, 8686. https://doi.org/10.3390/s23218686
Gupta BB, Chui KT, Gaurav A, Arya V, Chaurasia P. A Novel Hybrid Convolutional Neural Network- and Gated Recurrent Unit-Based Paradigm for IoT Network Traffic Attack Detection in Smart Cities. Sensors. 2023; 23(21):8686. https://doi.org/10.3390/s23218686
Chicago/Turabian StyleGupta , Brij B., Kwok Tai Chui, Akshat Gaurav , Varsha Arya , and Priyanka Chaurasia . 2023. "A Novel Hybrid Convolutional Neural Network- and Gated Recurrent Unit-Based Paradigm for IoT Network Traffic Attack Detection in Smart Cities" Sensors 23, no. 21: 8686. https://doi.org/10.3390/s23218686
APA StyleGupta , B. B., Chui, K. T., Gaurav , A., Arya , V., & Chaurasia , P. (2023). A Novel Hybrid Convolutional Neural Network- and Gated Recurrent Unit-Based Paradigm for IoT Network Traffic Attack Detection in Smart Cities. Sensors, 23(21), 8686. https://doi.org/10.3390/s23218686











