Abstract
Spoofing interference is one of the most emerging threats to the Global Navigation Satellite System (GNSS); therefore, the research on anti-spoofing technology is of great significance to improving the security of GNSS. For single spoofing source interference, all the spoofing signals are broadcast from the same antenna. When the receiver is in motion, the pseudo-range of spoofing signals changes nonlinearly, while the difference between any two pseudo-ranges changes linearly. Authentic signals do not have this characteristic. On this basis, an anti-spoofing method is proposed by jointly monitoring the linearity of the pseudo-range difference (PRD) sequence and pseudo-range sum (PRS) sequence, which transforms the spoofing detection problem into the sequence linearity detection problem. In this paper, the model of PRD and PRS is derived, the hypothesis based on the linearity of PRD sequence and PRS sequence is given, and the detection performance of the method is evaluated. This method uses the sum of squares of errors (SSE) of linear fitting of the PRD sequence and PRS sequence to construct detection statistics, and has low computational complexity. Simulation results show that this method can effectively detect spoofing interference and distinguish spoofing signals from authentic signals.
1. Introduction
Global Navigation Satellite System (GNSS) has the unique technical characteristics of all-weather, all-day, and global coverage and has become the most widely used space-based radio positioning system at present [1,2]. While it is widely used, the security of GNSS has been paid more attention [3]. Due to the inherent vulnerability of GNSS, such as weak signal power, publicly known civil signal structure, slow message update, etc., GNSS is vulnerable to external interference, and its security is seriously threatened [4,5]. In its current form, the main types of GNSS interference include suppression interference and spoofing interference. Suppression interference interferes with the target receiver by transmitting high-power signals, which reduces its positioning performance and even makes it impossible to locate [6]. However, the effect of suppressing interference is dominant. It is easy for the attacked receiver to find out that it has been suppressed and take countermeasures accordingly. The more covert spoofing interference induces the receiver to output wrong positioning results by broadcasting false signals with the same structural characteristics and different parameters as GNSS signals [7]. Compared with suppression interference, spoofing interference does not require high power, and its interference effect is more concealed, so its potential harm is higher [8]. The research on anti-spoofing technology is of great significance to improving the security of GNSS, which has gradually been widely valued by academic circles and has become a new research hotspot [9,10].
According to the number of spoofing sources, spoofing interference can be divided into two modes: single spoofing source interference and multiple spoofing sources interference [11]. Single spoofing source interference means that a spoofing source transmits multiple spoofing signals, which is the most common spoofing interference mode at present. In this way, the spoofing signals can be consistent without knowing the target receiver position [12]. Multiple spoofing sources interference means that each spoofing source produces a spoofing signal, and all the spoofing signals are transmitted to the receiver from different directions. This way is closer to the actual scene. Nevertheless, to make the spoofing signals meet the consistency, the receiver position should be known, and the spoofing sources need to synchronize accurately through the communication link, which requires high implementation cost and technical level. Up to now, the interference mode of multiple spoofing sources cooperative spoofing is still in the theoretical research stage, and there is no public report in the literature.
Because of the complexity of spoofing interference, the principles of anti-spoofing methods are quite different. The anti-spoofing method based on C/N0 monitoring assumes that the C/N0 of spoofing signals exceeds the normal range, but if the spoofing signals are broadcast together with noise, this method will be invalidated [13]. The signal quality monitoring method can detect the traction spoofing interference based on the fact that overlapping correlation peaks in the traction process will lead to distortion of the autocorrelation function but is ineffective when correlation peaks are separated [14]. The receiver autonomous integrity monitoring method detects spoofing interference according to the consistency of authentic signals, but it will fail when spoofing signals tend to be consistent [15].
For single spoofing source interference, an important feature is that all spoofing signals are broadcast from the same antenna. Therefore, the incidence angles of all spoofing signals are the same, while those of authentic signals are different. According to this, methods based on multiple antennas or multiple receivers can effectively detect spoofing interference [16,17,18,19,20,21]. However, these methods not only need to synchronize the observations of all antennas or receivers but also need to add extra hardware, which leads to high complexity and cost. In addition, methods based on mobile receivers are also effective [22,23,24]. All spoofing signals have the same propagation path, while the authentic signals from different satellites have different propagation paths. Therefore, when the receiver moves, some observations of the authentic signals and the spoofing signals will show different changes. Previous studies assumed that the channel gains or carrier Doppler shifts of all the spoofing signals are correlated, so spoofing interference can be detected by monitoring the correlation of channel gains or carrier Doppler shifts between different signals. However, the change in channel gain is related to the distance between the spoofing source and the receiver. The farther the distance, the less obvious the channel gain variation caused by the receiver motion [11]. In addition, the change in carrier Doppler shift is related to the velocity change in the receiver. The smaller the velocity change, the less obvious the carrier Doppler shift variation caused by the receiver motion.
Based on the above considerations, this paper proposes an anti-spoofing method for single spoofing source interference, which jointly monitors the linearity of the pseudo-range difference (PRD) sequence and pseudo-range sum (PRS) sequence. In a short time, the pseudo-range variation caused by the satellite motion is linear. For spoofing signals, although the variations in pseudo-ranges caused by the receiver motion are nonlinear, these variations are the same. Consequently, the pseudo-range of spoofing signals changes nonlinearly, while the difference between any two pseudo-ranges changes linearly. For authentic signals, it does not have this characteristic. Therefore, we can detect spoofing interference by monitoring the linearity of the PRD sequence and PRS sequence and distinguishing between authentic signals and spoofing signals. Compared with the existing research, the proposed method can effectively solve the problem of spoofing detection even when the distance between the spoofing source and the receiver is far away or the velocity of the receiver changes slowly, which shows that the performance of the method is more robust.
Subsequent sections of this paper are arranged as follows. In Section 2, the models of PRD and PRS are derived, and their linear problems are analyzed. In Section 3, hypothesis testing is given, linearity detection statistics are constructed, and false alarm probability and detection probability are analyzed. Section 4 shows the simulation results. Section 5 summarizes the content of this paper.
2. Linearity Analysis
2.1. Pseudo-Range Sequence Linearity Analysis
The pseudo-range measurement value ρ of the authentic signal is as shown in Equation (1):
where represents the geometric distance between satellite and receiver; represents the speed of light; and represent receiver clock error and satellite clock error, respectively; is ionospheric delay; is tropospheric delay; and represents pseudo-range measurement noise, which can be considered as Gaussian white noise.
Define the pseudo-range sequence . denotes the pseudo-range measurement value of the signal i at the -th measurement time. The measurement time interval is , and the sequence length is . In a short time, the changes in ionospheric delay, tropospheric delay, and satellite clock error are very small and can be ignored. In addition, since the distance between the satellite and receiver is far enough, the position change of the satellite and receiver in a short time is very small relative to the distance between them. Therefore, the unit observation vector of the satellite at the receiver can be considered constant. Thus, can be approximately expressed as
In Equation (2), is a constant; and represent the position vectors of the satellite and the receiver from time to time , respectively.
means the radial projection component of the satellite position change. The radial acceleration of the satellite is less than [11]. The radial acceleration is so small that it has little effect on radial velocity. Therefore, in a short time, it can be considered that the radial velocity is constant, which means that varies linearly. The receiver is driven by a stable clock, and its clock drift does not change obviously with time [25]. Therefore, the receiver clock difference can also be considered to vary linearly in a short time. When the receiver velocity is constant, changes linearly with time. When its velocity changes, changes nonlinearly. According to the above analysis, the elements in are linear when the receiver moves at a uniform velocity, and nonlinear when the receiver moves at a variable velocity.
In case of spoofing signal, under the assumption that the position of the spoofing source is unchanged, can be approximately expressed as
where represents the unit observation vector of the satellite at the spoofing source, represents the unit observation vector of the spoofing source at the receiver, and represents the difference between the additional component of the spoofing source at time and time . It should be emphasized that in addition to the assumption that the spoofing source is stationary, we also need to assume that the additional component of the spoofing source to any signal changes linearly, which is the prerequisite for the effectiveness of the proposed method. Thus, can be considered to vary linearly.
Since the distance between the satellite and the spoofing source is far enough, can be considered to be constant in a short time, so that varies linearly with time. While for , due to the distance between the spoofing source and the receiver being relatively close, will change continuously with the movement of the receiver. Therefore, whether the receiver is moving at a uniform velocity or not, is nonlinear with time, and then the elements in are nonlinear.
2.2. PRD Sequence Linearity Analysis
Defining is the sequence of measured pseudo-range differences between the signal and the signal , where can be denoted as
If the two signals are authentic signals, can be derived as
where is a constant. The pseudo-range variation caused by the change in the receiver clock difference is eliminated in the calculation process. In a short time, and change linearly, and can be considered unchanged. Therefore, it is not difficult to conclude that the elements in are linear when the receiver moves at a uniform velocity and nonlinear when the receiver moves at a variable velocity.
If the two signals are spoofing signals, can be derived as
The pseudo-range change caused by the change in receiver position is eliminated in the calculation process. In this case, the elements in are linear regardless of whether the receiver is moving at a uniform velocity or a variable velocity.
If one of the two signals is an authentic signal and the other is a spoofing signal, can be derived as
Since will change during the motion of the receiver, changes nonlinearly with time regardless of whether the receiver moves at a uniform velocity, which means that the elements in are nonlinear.
2.3. PRS Sequence Linearity Analysis
Defining is the sequence of measured pseudo-range sums between the signal and the signal , where can be denoted as
If the two signals are authentic signals, can be derived as
where is a constant. In a short time, and change linearly, and can be considered unchanged. Therefore, it is not difficult to conclude that the elements in are linear when the receiver moves at a uniform velocity and nonlinear when the receiver moves at a variable velocity.
If the two signals are spoofing signals, can be derived as
If one of the two signals is an authentic signal and the other is a spoofing signal, can be derived as
For the two cases, since will change during the motion of the receiver, will change with time regardless of whether the receiver moves at a uniform velocity, which means that the elements in are nonlinear.
2.4. Analysis Summary
Based on all the above analysis, we can draw a conclusion, as shown in Table 1. Case 1 indicates that the two signals are authentic signals. Case 2 indicates that the two signals are spoofing signals. Case 3 indicates that one of the two signals is an authentic signal and the other is a spoofing signal.

Table 1.
Linearity analysis results of PRD sequence and PRS sequence.
3. Anti-Spoofing Method
From the analysis in Section 2, it can be seen that when the two signals are spoofing signals, the PRD sequence is linear, while the PRS sequence is nonlinear. In other cases, this characteristic is not satisfied. Accordingly, the detection result is linear and is nonlinear, indicating that the signal and the signal are spoofing signals from the same spoofing source. Although no definite conclusion can be obtained from other detection results, all authentic signals and spoofing signals can still be distinguished with traversal detection.
The specific detection process includes the following two steps.
- ✧
- Step 1: Randomly select two signals and use the proposed method to detect whether they are both spoofing signals. If yes, proceed to Step 2. If not, we will reselect two signals for detection until two spoofing signals are selected.
- ✧
- Step 2: For the other signals, except the two spoofing signals, one of them is selected in turn to be jointly detected with any one of the spoofing signals.
For Step 2, on the premise that one signal is a spoofing signal, the proposed method can directly determine whether the other signal is an authentic signal or a spoofing signal. As a result, all authentic signals and spoofing signals can be judged.
The above spoofing detection process is represented with a flowchart, as shown in Figure 1. Next, this section will introduce the detection method of the linearities of PRD sequence and PRS sequence involved in the spoofing detection process.
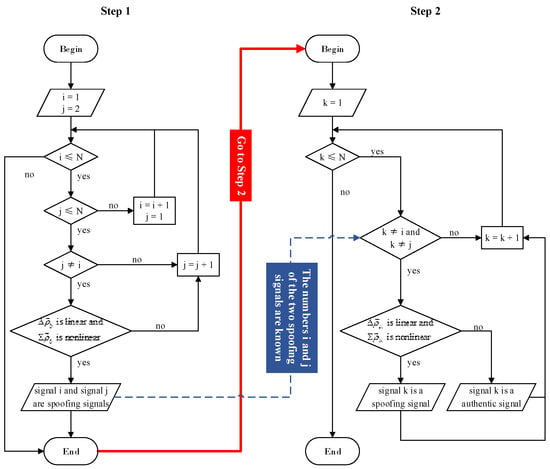
Figure 1.
Flowchart corresponding to spoofing detection process.
3.1. PRD Sequence Linearity Detection
In the linearity detection of the PRD sequence, two hypotheses for PRD sequence are as follows:
For , we can calculate its least square linear regression model:
where and are the estimated model parameters and represents the estimated value of obtained with a linear model.
Under the hypothesis, can be expressed as
where represents a nonlinear equation and is Gaussian white noise. The variance of is :
and denote the pseudo-range measurement noise variance of the signal and the signal , respectively. In this case, the difference between the actual value and the estimated value can be deduced as follows:
Therefore, obeys the Gaussian distribution with mean value and variance .
Under the hypothesis, can be expressed as
where and are model parameters, is Gaussian white noise, and its variance is also . Thus, the difference between the actual value and the estimated value can be deduced as follows:
Compared with , and are very small and can be ignored. Therefore, obeys the Gaussian distribution with zero mean and variance.
is called the fitting error sequence of the PRD sequence. The effect of linear fitting can be evaluated using the sum of squares of errors (SSE) between actual data and estimated data. The smaller the SSE, the better the linear fitting effect. Based on this, we construct the linearity detection statistic corresponding to the PRD sequence:
It can be proved that under the hypothesis of , obeys the non-central chi-square distribution with the degree of freedom and the non-central parameter . And under the hypothesis, obeys the central chi-square distribution with the degree of freedom .
The non-central parameter is as follows:
When the degree of freedom is large enough, the chi-square distribution can be approximately Gaussian distribution [26]. According to this characteristic of chi-square distribution, the distribution of under the hypothesis and the hypothesis can be approximately expressed as
Figure 2 shows the probability density function of the linearity detection statistic under different hypotheses, where the solid lines are the theoretical curves calculated according to the Equation (22), and the star points are the statistical results obtained through 10,000 Monte Carlo random experiments. Figure 2a,b correspond to the hypothesis, where their central parameters are and , respectively, while Figure 2c corresponds to the hypothesis. It can be found that the simulation results are very close to the theoretical results. Under the hypothesis, is closer to zero, and the smaller the noise variance and the longer the sequence length, the more concentrated the distribution of . Under the hypothesis, the mean and variance of increase with the increase in central parameters.
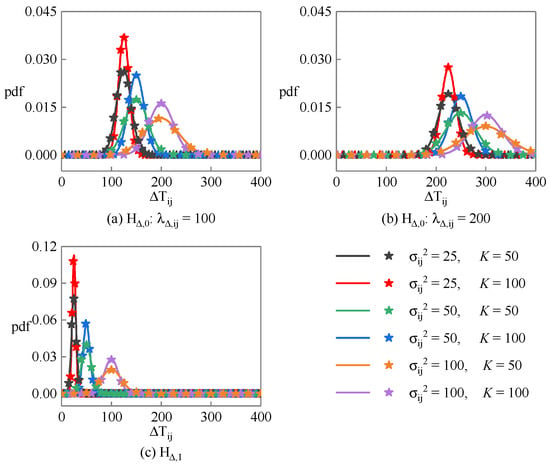
Figure 2.
Probability density function of the linearity detection statistic corresponding to PRD sequence under different hypotheses.
3.2. PRS Sequence Linearity Detection
In the linearity detection of the PRS sequence, two hypotheses for PRS sequence are as follows:
Similarly, the difference between the actual value and the estimated value obtained with linear fitting is represented by . Under the hypothesis, obeys the Gaussian distribution with zero mean and variance. Under the hypothesis, obeys the Gaussian distribution with mean value and variance . is called the fitting error sequence of the PRS sequence. Constructing the linearity detection statistic corresponding to the PRS sequence:
It can be proved that under the hypothesis of , obeys the central chi-square distribution with the degree of freedom . And under the hypothesis, obeys the non-central chi-square distribution with the degree of freedom and the non-central parameter .
The non-central parameter is as follows:
Combined with the previous analysis, when the degree of freedom is large enough, the chi-square distribution can be approximately Gaussian distribution. Therefore, the distribution of under different hypotheses can be derived:
Figure 3 shows the probability density function of the linearity detection statistic under different hypotheses, where the solid lines are the theoretical curves calculated according to the Equation (27), and the star points are the statistical results obtained through 10,000 Monte Carlo random experiments. Figure 3a corresponds to the hypothesis, while Figure 3b,c correspond to the hypothesis, where their central parameters are and , respectively. It can be found that the simulation results are very close to the theoretical results. Under the hypothesis, is closer to zero, and the smaller the noise variance and the longer the sequence length, the more concentrated the distribution of . Under the hypothesis, the mean and variance of increase with the increase in central parameters.
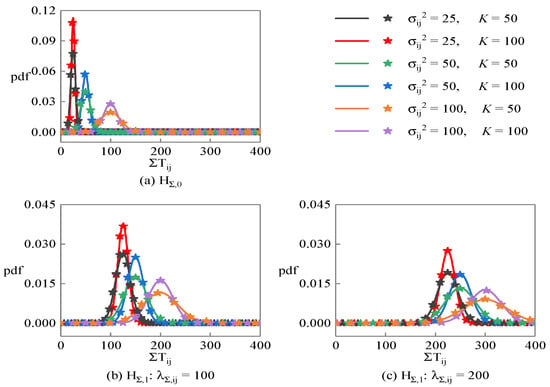
Figure 3.
Probability density function of the linearity detection statistic corresponding to PRS sequence under different hypotheses.
3.3. Detection Performance Analysis
From the analysis in Section 2, it can be seen that the noise contained with the PRD is , and the noise contained with PRS is . and are not correlated. Therefore, the variance of and is . The correlation coefficient between them can be derived as
When the pseudo-range measurement noise variances and are equal, the correlation coefficient is , which means that the PRD sequence is not correlated with the noise contained in the PRS sequence . When , is correlated with the noise contained in , and the greater the difference between the two noise variances, the higher the correlation. Considering that the spoofing signals broadcast by the same spoofing source have similar power, to simplify the problem, it is assumed that the noises contained in and are not correlated. That is to say, the detection of PRD sequence linearity is independent of the detection of PRS sequence linearity.
For the PRD sequence and PRS sequence linearity detection, since the noise variance is and the detection length is , the same detection threshold can be set. In the linearity detection of the PRD sequence, the hypothesis is considered to be valid when , and the hypothesis is considered to be valid when . Combined with the Equation (22), the false alarm probability and the detection probability can be derived as follows:
where is the right tail probability function. In the linearity detection of the PRS sequence, the hypothesis is considered to be valid when , and the hypothesis is considered to be valid when . Combined with the Equation (27), the false alarm probability and the detection probability can be derived as follows:
For the method proposed in this paper, the false alarm probability and detection probability of joint detection can be expressed as
Since it is assumed that the PRD sequence linearity detection is independent of the PRS sequence linearity detection, and can be further derived:
The false alarm probability and detection probability of joint detection corresponding to the detection threshold in different scenes are shown in Figure 4. Compared with the Figure 4a,b, the increase in noise variance makes higher and lower. Compared with the Figure 4a,c, the reduction in sequence length makes higher and lower. Compared with the Figure 4a,d, the decrease in non-central parameter makes increase, and remains unchanged. Compared with the Figure 4a,e, the decrease in non-central parameter reduces and .
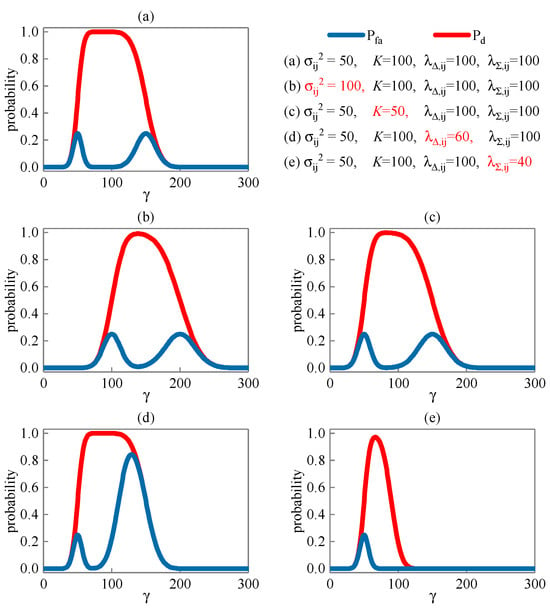
Figure 4.
False alarm probability and detection probability corresponding to detection threshold.
The lower the false alarm probability and the higher the detection probability, the better the detection performance. Furthermore, we count the difference between the detection probability and the false alarm probability corresponding to the detection threshold in different scenes, as shown in Figure 5. It is not difficult to find from the figure that the smaller the noise variance, the longer the sequence length, and the larger the non-central parameters and , the better the detection performance.
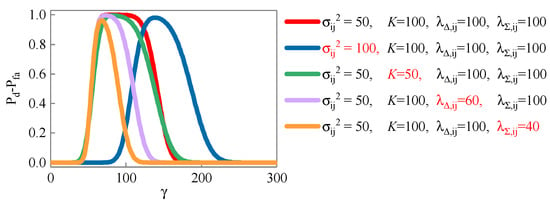
Figure 5.
Difference between detection probability and false alarm probability corresponding to detection threshold.
4. Simulation Results and Analysis
In this section, the feasibility of the method will be verified with simulation tests. Simulation scenes are divided into the uniform motion scene and the circular motion scene, as shown in Figure 6. The authentic signals and spoofing signals in the two scenes are generated with the GNSS signal source simulator, sampled and stored in signal memory, and then processed with the GNSS software receiver.
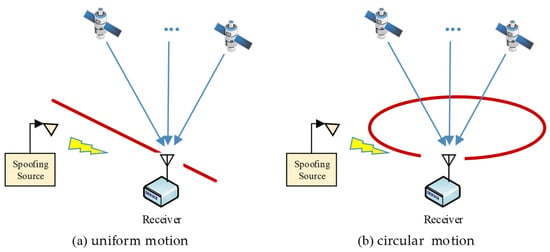
Figure 6.
Two simulation scenes.
The number of test signals is 8, in which the PRNs of authentic signals are 2, 11, 14, and 21, and the PRNs of spoofing signals are 5, 10, 16, and 33. The standard deviation of the pseudo-range measurement error of all signals is set to 3 m. This assumption implies that the noise variance of PRD and PRS for any two signals is 18. The receiver tracks the collected signals and obtains the measured pseudo-range sequence with the sequence length and the time interval . The difference between two measurement pseudo-range sequences is selected to form a PRD sequence, and the sum forms a PRS sequence. Each PRD sequence and PRS sequence is linearly fitted to obtain fitting error sequences, and the detection statistics are obtained by statistics. The detection threshold . For this threshold, the probability that the sequence is linear but the detection result is nonlinear will be less than 0.001%.
4.1. Uniform Motion Scene Test
In the uniform motion scene test, the distance between the spoofing source and the target receiver is 1000 m at 0 time, and the speed of the receiver is 40 m/s. The fitting error sequences and correspond to the PRD sequence and the PRS sequence, and the linearity detection statistics and obtained by statistics are shown in Figure 7. In the case of two authentic signals, as shown in Figure 7a, both and are below the threshold. For the case of one authentic signal and one spoofing signal, as shown in Figure 7c, both and are above the threshold. For the case of two spoofing signals, as shown in Figure 7b, and are satisfied. The simulation results are consistent with the analysis results, which show that the proposed method can detect spoofing signals in uniform motion scenes.
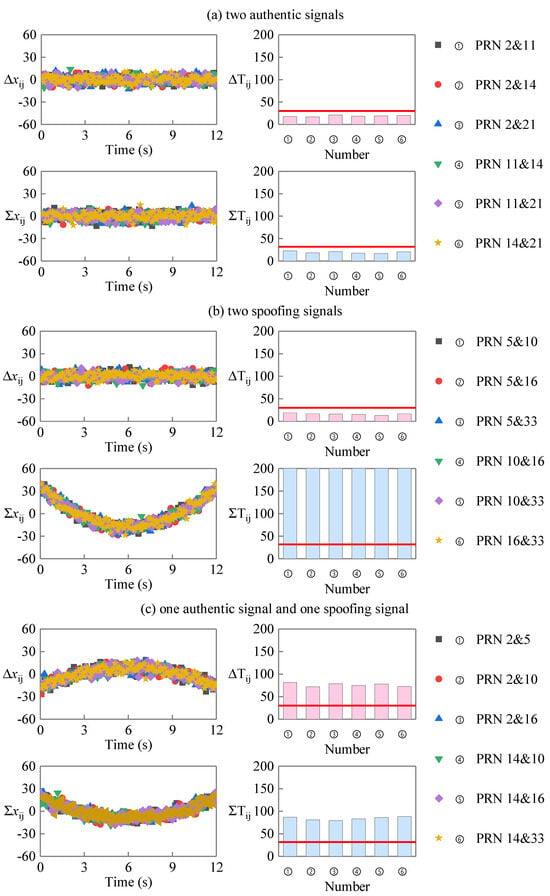
Figure 7.
Fitting error sequences and detection statistics in the uniform motion scene.
4.2. Circular Motion Scene Test
In the circular motion scene test, the distance between the spoofing source and the target receiver is 1000 m at 0 time, the speed of the receiver is 40 m/s, and the circumference radius is 300 m. The fitting error sequences and correspond to the PRD sequence and the PRS sequence, and the linearity detection statistics and obtained with the test are shown in Figure 8. In the case of two authentic signals, as shown in Figure 8a, both and are above the threshold. For the case of one authentic signal and one spoofing signal, as shown in Figure 8c, both and are above the threshold. For the case of two spoofing signals, as shown in Figure 8b, and are satisfied. The simulation results are consistent with the analysis results, which show that the proposed method can detect spoofing signals in variable motion scenes.
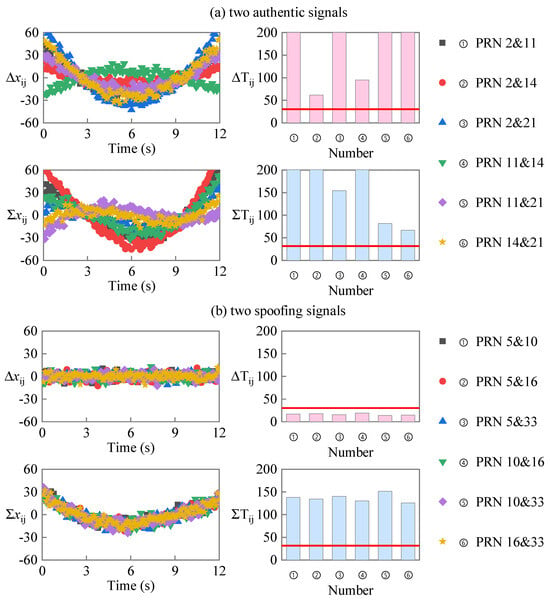
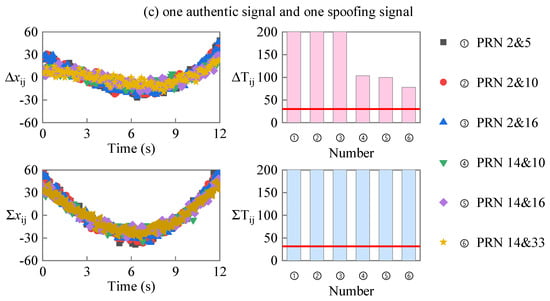
Figure 8.
Fitting error sequences and detection statistics in the circular motion scene.
5. Conclusions
Aiming at single spoofing interference, this paper proposes an anti-spoofing method based on the joint monitoring of the PRD sequence and the PRS sequence linearity, which changes the spoofing detection problem into the sequence linearity detection problem. The detection statistics are constructed based on the SSE of linear fitting of the PRD sequence and PRS sequence. When the sequence length is large enough, the detection statistics approximately obey the Gaussian distribution. The influence of noise variance, sequence length, and non-central parameters on the detection performance of the method is analyzed. It can be concluded that the smaller the noise variance, the longer the sequence length, and the larger the non-central parameters, the better the detection performance. In addition, the feasibility of the method is verified by simulation tests. Simulation results show that this method can detect spoofing interference and distinguish authentic signals from spoofing signals in both uniform motion scenes and variable motion scenes. This is the premise of improving the security and availability of GNSS in the presence of spoofing interference.
The proposed method is low complexity because it only requires pseudo-range information and does not need to modify the baseband processing of the receiver. Nevertheless, the precondition for the effectiveness of the method is that the spoofing source is stationary, and the additional component of the spoofing source to any signal is linearly varying. In addition, this paper lacks an exploration of the influence of receiver motion on non-central parameters, which makes it impossible to establish a direct relationship between receiver motion and detection performance. Our future work will focus on these two aspects to improve.
Author Contributions
Conceptualization, X.Z. and T.L.; methodology, X.Z.; software, T.L., J.W. and C.W.; validation, X.Z.; formal analysis, X.Z.; investigation, X.Z. and M.C.; resources, J.T.; data curation, X.Z.; writing, X.Z.; visualization, M.C.; supervision, J.T.; project administration, T.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the CAEP Foundation under Grant CX20200010.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Bhatti, J.; Humphreys, T.E. Hostile control of ships via false GPS signals: Demonstration and detection. Navigation 2017, 64, 51–66. [Google Scholar] [CrossRef]
- Han, S.; Chen, L.; Meng, W.; Li, C. Improve the Security of GNSS Receivers Through Spoofing Mitigation. IEEE Access 2017, 5, 21057–21069. [Google Scholar] [CrossRef]
- Grant, A.; Williams, P.; Ward, N.; Basker, S. GPS Jamming and the Impact on Maritime Navigation. J. Navig. 2009, 62, 173–187. [Google Scholar] [CrossRef]
- Ioannides, T.; Pany, T.; Gibbons, G. Known Vulnerabilities of Global Navigation Satellite Systems, Status, and Potential Mitigation Techniques. Proc. IEEE 2016, 104, 1174–1194. [Google Scholar] [CrossRef]
- Chen, F.; Nie, J.; Ni, S.; Li, Z.; Wang, F. Combined algorithm for interference suppression and signal acquisition in GNSS receivers. Electron. Lett. 2017, 53, 274–275. [Google Scholar] [CrossRef]
- Warner, J.S.; Johnston, R.G. A Simple Demonstration that the Global Positioning System (GPS) is Vulnerable to Spoofing. J. Secur. Adm. 2002, 25, 19–27. [Google Scholar]
- Shepard, D.P.; Humphreys, T.E.; Fansler, A.A. Evaluation of the Vulnerability of Phasor Measurement Units to GPS Spoofing Attacks. Int. J. Crit. Infrastruct. Prot. 2012, 5, 146–153. [Google Scholar] [CrossRef]
- Schmidt, D.; Radke, K.; Camtepe, S. A Survey and Analysis of the GNSS Spoofing Threat and Countermeasures. ACM Comput. Surv. 2016, 48, 1–31. [Google Scholar] [CrossRef]
- Yang, H.; Jin, R.; Xu, W.; Che, L.; Zhen, W. Satellite Navigation Spoofing Interference Detection and Direction Finding Based on Array Antenna. Sensors 2023, 23, 1604. [Google Scholar] [CrossRef] [PubMed]
- Tu, J.; Zhan, X.; Zhang, X.; Zhang, Z.; Jing, S. Low-complexity GNSS anti-spoofing technique based on Doppler frequency difference monitoring. IET Radar Sonar Navig. 2018, 12, 1058–1065. [Google Scholar] [CrossRef]
- Tao, H.; Wu, H.; Li, H.; Lu, M. GNSS Spoofing Detection Based on Consistency Check of Velocities. Chin. J. Electron. 2019, 28, 218–225. [Google Scholar] [CrossRef]
- Jafarnia-Jahromi, A.; Broumandan, A.; Nielsen, J. GPS spoofer countermeasure effectiveness based on signal strength, noise power, and C/N0 observables. Int. J. Satell. Commun. Netw. 2012, 30, 181–191. [Google Scholar] [CrossRef]
- Ali, P.; Ali, B.; Lachapelle, G. Characterization of Signal Quality Monitoring Techniques for Multipath Detection in GNSS Applications. Sensors 2017, 17, 1579. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Montgomery, P.Y.; Humphreys, T.E.; Ledvina, B.M. Receiver-autonomous spoofing detection: Experimental results of a multi-antenna receiver defense against a portable civil GPS spoofer. In Proceedings of the International Technical Meeting of The Institute of Navigation, Anaheim, CA, USA, 26–28 January 2009; pp. 124–130. [Google Scholar]
- Montgomery, P.Y.; Humphreys, T.E.; Ledvina, B.M. A multi-antenna defense: Receiver autonomous GPS spoofing detection. Inside GNSS 2009, 4, 40–46. [Google Scholar]
- Swaszek, P.F.; Hartne, R.J. Spoof detection using multiple COTS receivers in safety critical applications. In Proceedings of the ION GNSS+, Nashville, TN, USA, 16–20 September 2013; pp. 2921–2930. [Google Scholar]
- Swaszek, P.F.; Richard, J.H. A multiple COTS receiver GNSS spoof detector-extensions. In Proceedings of the International Technical Meeting of The Institute of Navigation, San Diego, CA, USA, 27–29 January 2014; pp. 316–326. [Google Scholar]
- Axell, E.; Larsson, E.G.; Persson, D. GNSS spoofing detection using multiple mobile COTS receivers. In Proceedings of the IEEE International Conference on Acoustics, Speech, and Signal Process (ICASSP), Brisbane, Australia, 19–24 April 2015; pp. 3192–3196. [Google Scholar]
- Radin, S.D.; Swaszek, P.F.; Seals, K.C. GNSS spoof detection based on pseudo-ranges from multiple receivers. In Proceedings of the International Technical Meeting of The Institute of Navigation, Dana Point, CA, USA, 26–28 January 2015; pp. 657–671. [Google Scholar]
- Nielsen, J.; Broumandan, A.; Lachapelle, G. GNSS spoofing detection for single antenna handheld receivers. Navigation 2011, 58, 335–344. [Google Scholar] [CrossRef]
- Broumandan, A.; Jafarnia, A.; Dehghanian, V. GNSS spoofing detection in handheld receivers based on signal spatial correlation. In Proceedings of the IEEE/ION Position Location and Navigation Symposium (PLANS), Myrtle Beach, SC, USA, 24–26 April 2012; pp. 479–487. [Google Scholar]
- Broumandan, A.; Jafarnia-Jahromi, A.; Lachapelle, G. Spoofing detection, classification and cancelation (SDCC) receiver architecture for a moving GNSS receiver. GPS Solut. 2014, 19, 475–487. [Google Scholar] [CrossRef]
- Hesselbarth, A.; Wanninger, L. Short-term stability of GNSS satellite clocks and its effects on precise point positioning. In Proceedings of the ION GNSS, Savannah, GA, USA, 16–19 September 2008; pp. 1855–1863. [Google Scholar]
- Szilárd, A.; Árpád, B. Properties of the probability density function of the non-central chi-squared distribution. J. Math. Anal. Appl. 2008, 346, 395–402. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).