Performance Comparison of Relay-Based Covert Communications: DF, CF and AF
Abstract
:1. Introduction
- Besides the CF and AF relays explored in [24], we provide in this paper the optimal public and covert rates of DF relay-based covert communications for completeness. We optimize the power distribution between the public and covert messages and obtain a closed-form expression of the achievable covert rate.
- We then examine and make a delay-aware comparison among the asymptotic behaviors of the achievable covert rates with DF, CF and AF relays in different limits of source and relay transmit power for practical usefulness.
- Our analyses reveal that CF or AF tend to outperform DF for high source transmit power or low relay transmit power, while various system parameters such as the processing delay, minimum required quality of service for public messages and DEP threshold lead to different performance relationships among DF, CF and AF for high relay transmit power.
- We conduct various numerical examples, and they are in congruence with our studies on the asymptotic behaviors in various channel models.
- The results of this paper can provide a useful guideline in an environment where multiple relays with different forwarding protocols exist or where a single relay is capable of selecting either DF, CF or AF. We suggest such covert communications scenarios as interesting future works.
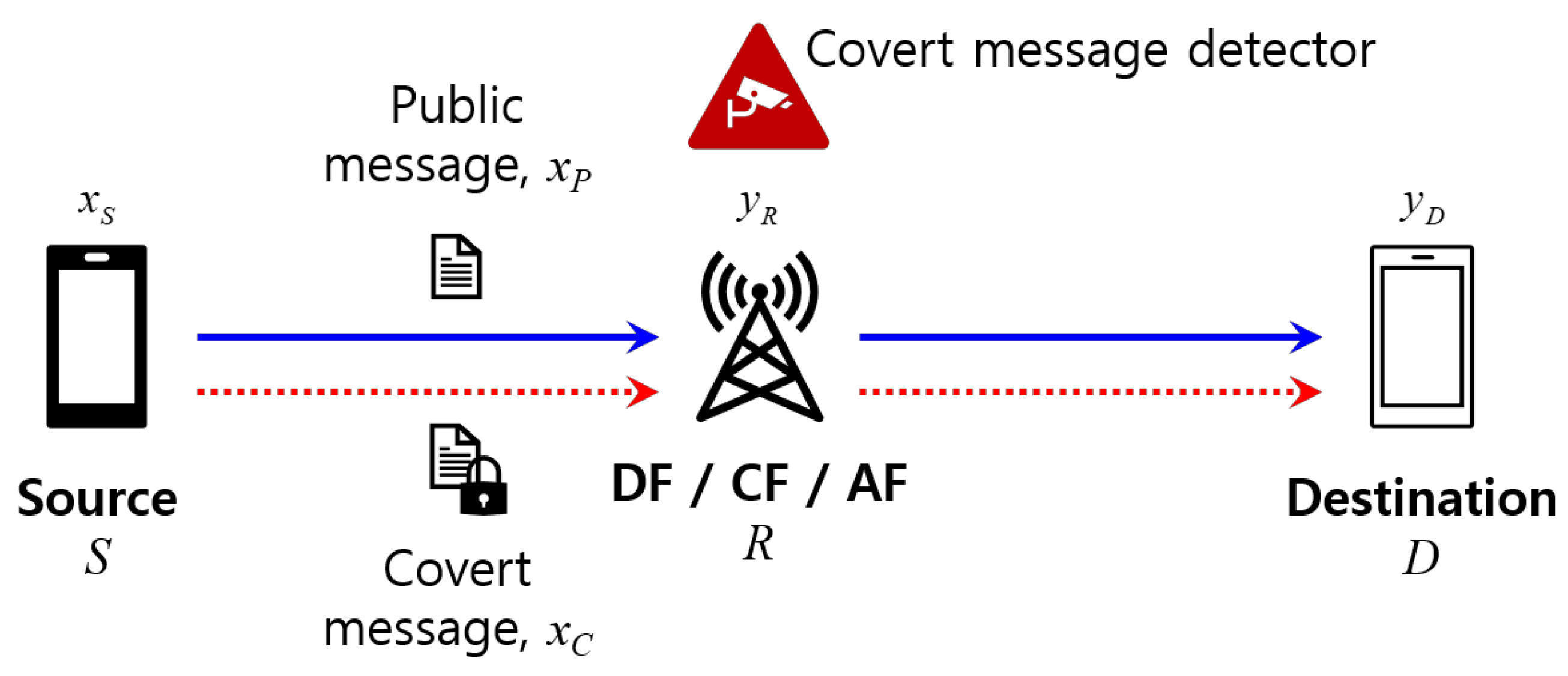
2. System Model
2.1. Received Signals
2.1.1. DF Relay
2.1.2. CF Relay
2.1.3. AF Relay
2.2. Covert Message Detection
3. Problem Formulation
3.1. DF Relay
3.2. CF Relay
3.3. AF Relay
4. Proposed Solutions
4.1. DF Relay
4.2. CF Relay
4.3. AF Relay
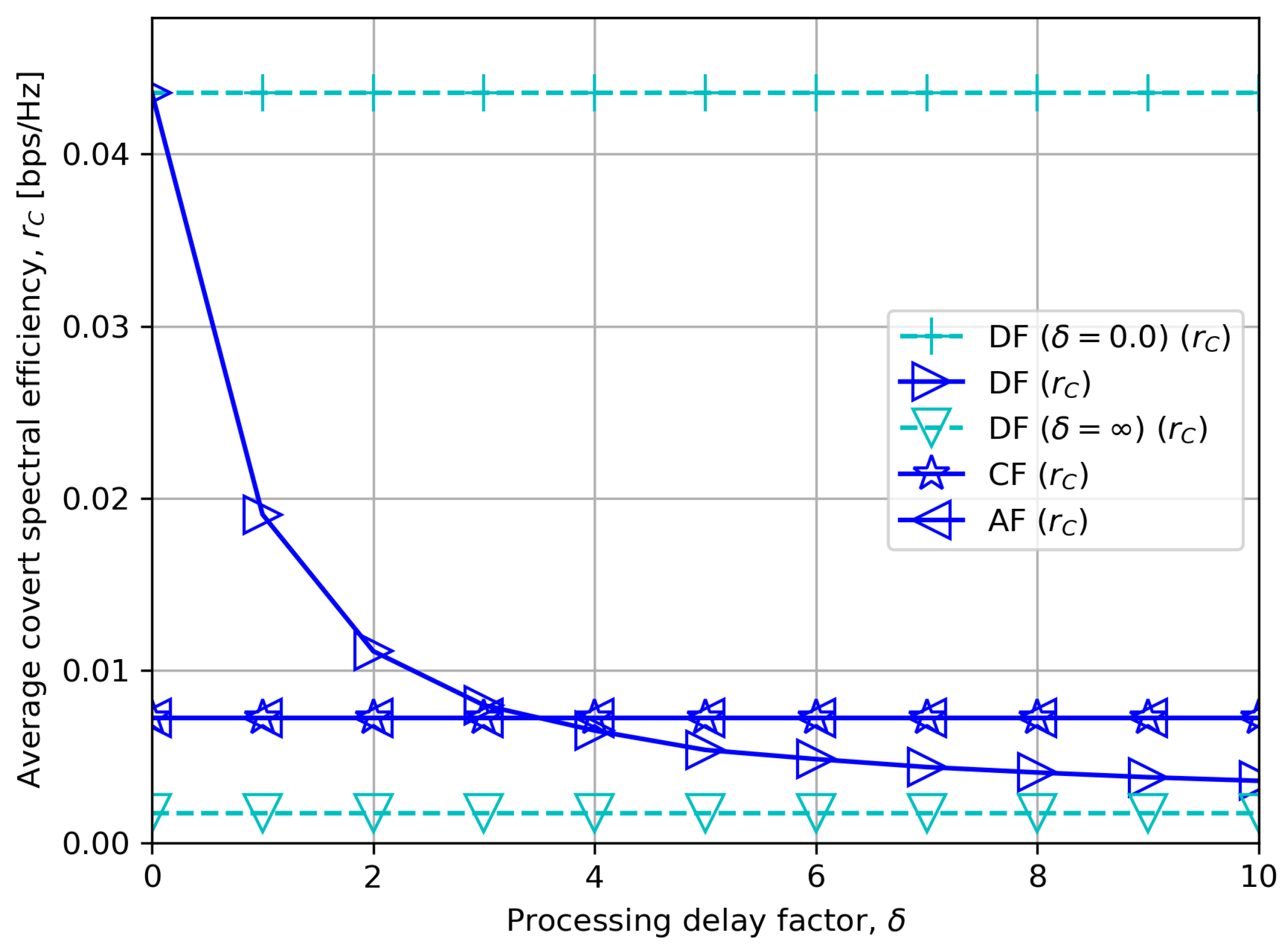
5. Performance Comparison with Relay Processing Delay
5.1. High Source Transmit Power
5.2. High Relay Transmit Power
5.2.1. High Relay Transmit Power with Low Processing Delay
5.2.2. High Relay Transmit Power with High Processing Delay
5.2.3. High Relay Transmit Power with Low DEP Threshold
5.2.4. High Relay Transmit Power with High DEP Threshold
5.3. Low Relay Transmit Power
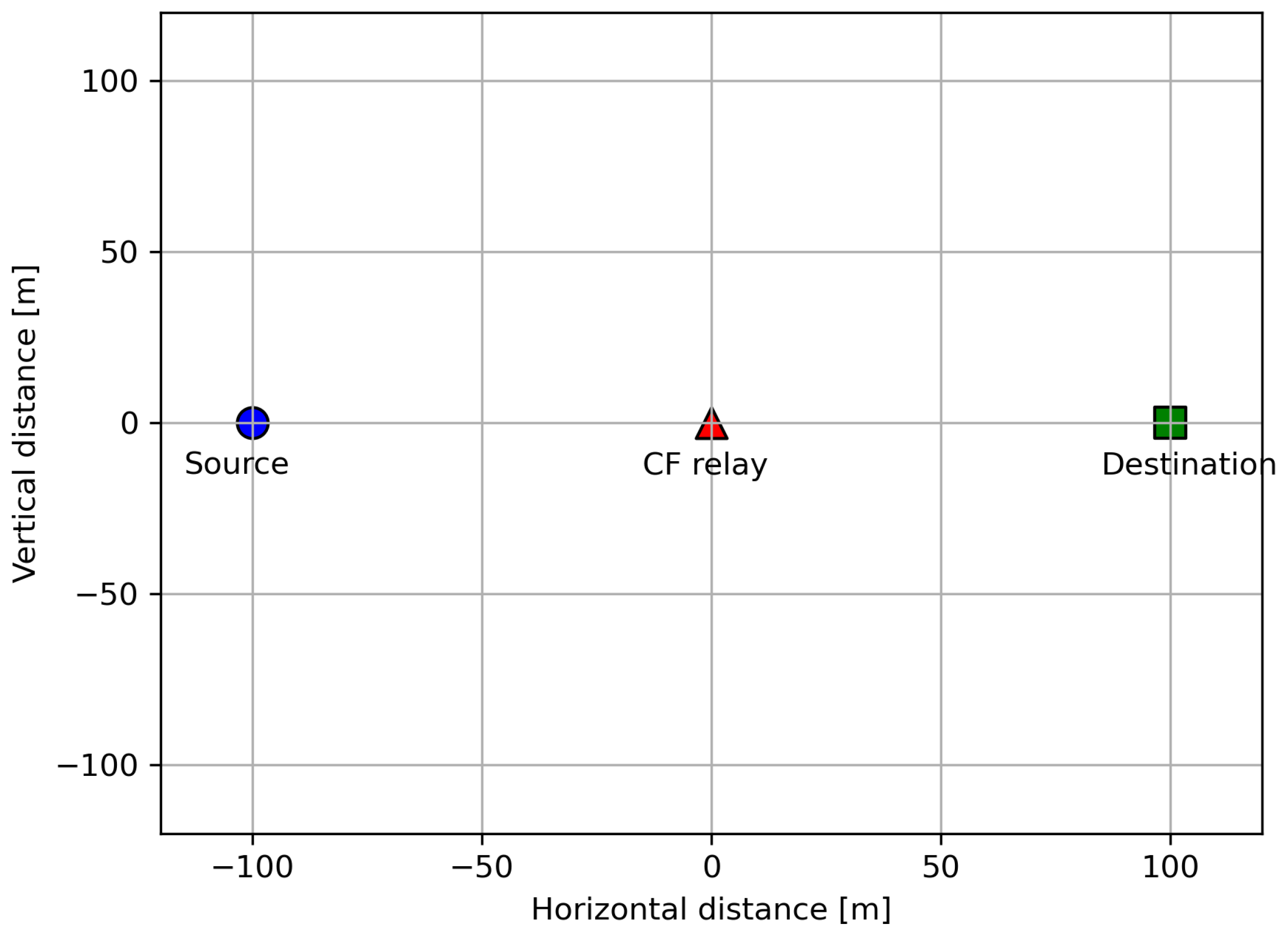
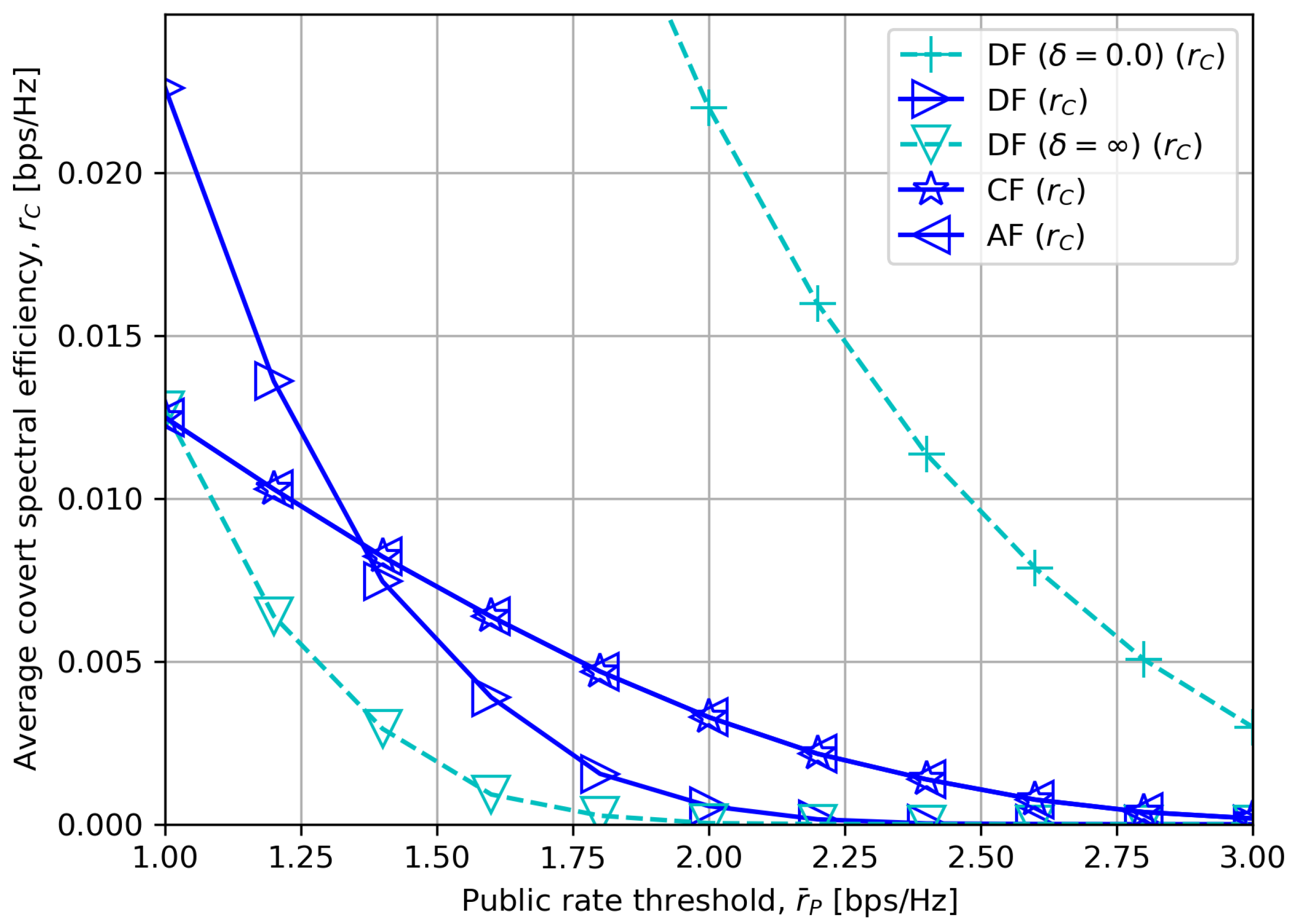
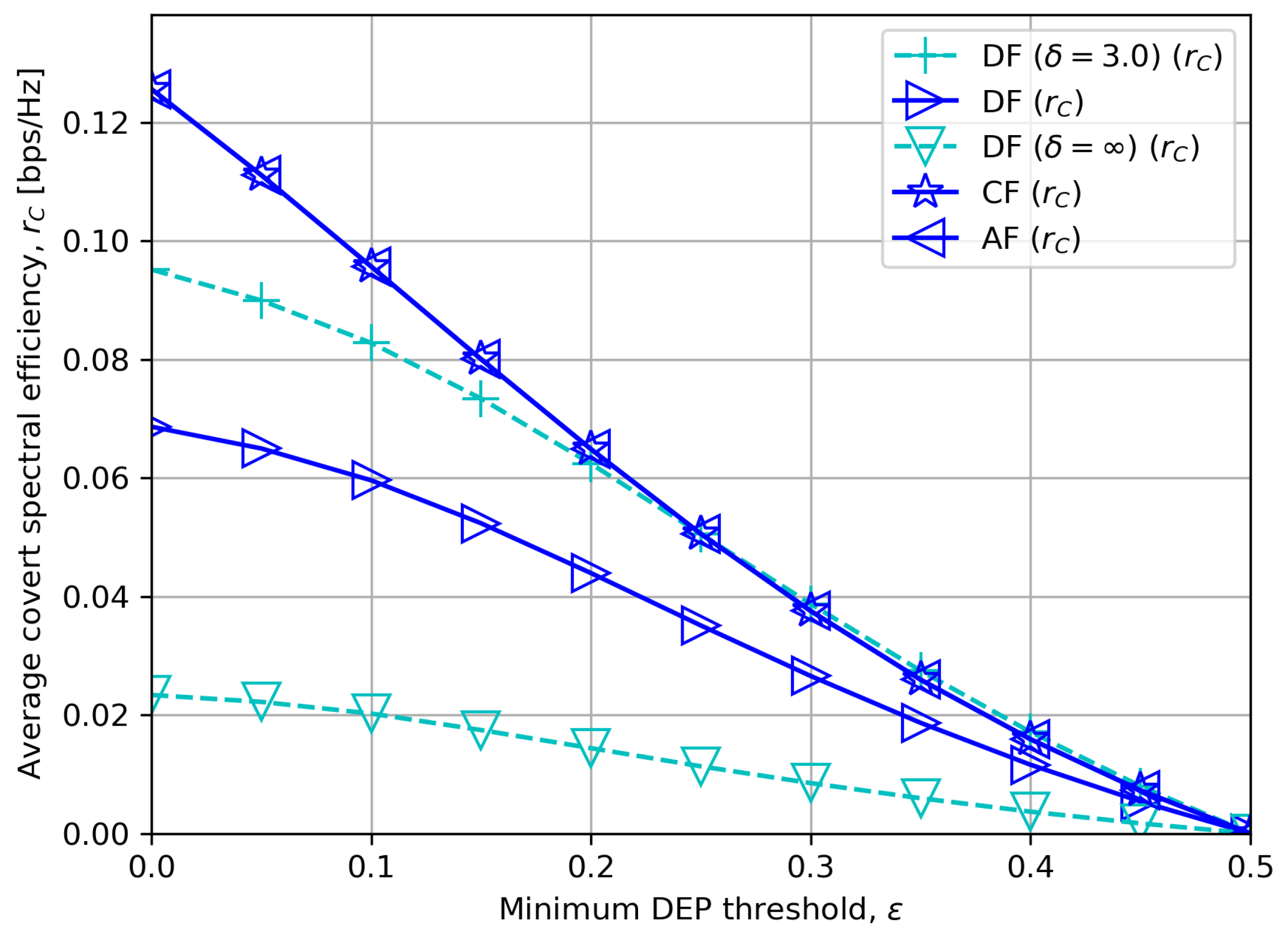
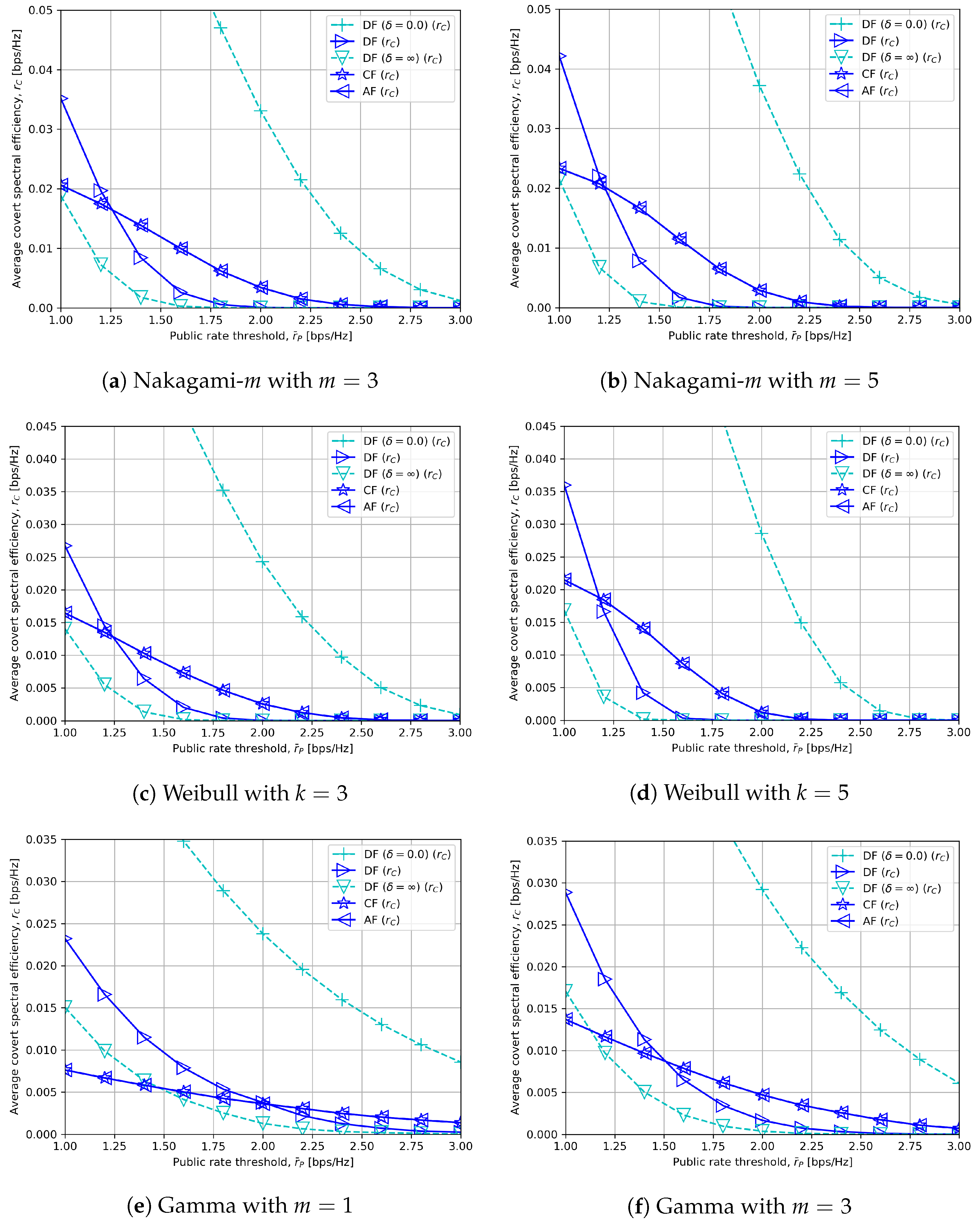
6. Numerical Results
7. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ko, S.-W.; Chae, H.; Han, K.; Lee, S.; Seo, D.-W.; Huang, K. V2X-Based Vehicular Positioning: Opportunities, Challenges, and Future Directions. IEEE Wirel. Commun. 2021, 28, 144–151. [Google Scholar] [CrossRef]
- Qazi, S.; Khawaja, B.A.; Farooq, Q.U. IoT-Equipped and AI-Enabled Next Generation Smart Agriculture: A Critical Review, Current Challenges and Future Trends. IEEE Access 2022, 10, 21219–21235. [Google Scholar] [CrossRef]
- Zhang, J.; Yan, Z.; Fei, S.; Wang, M.; Li, T.; Wang, H. Is Today’s End-to-End Communication Security Enough for 5G and Its Beyond? IEEE Netw. 2022, 36, 105–112. [Google Scholar] [CrossRef]
- Forouzan, B.A. Cryptography and Network Security; McGraw-Hill: New York, NY, USA, 2007. [Google Scholar]
- Wyner, A.D. The Wire-Tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Angueira, P.; Val, I.; Montalbán, J.; Seijo, Ó.; Iradier, E.; Fontaneda, P.S.; Fanari, L.; Arriola, A. A Survey of Physical Layer Techniques for Secure Wireless Communications in Industry. IEEE Commun. Surv. Tutor. 2022, 24, 810–838. [Google Scholar] [CrossRef]
- Jiang, X.; Chen, X.; Tang, J.; Zhao, N.; Zhang, X.Y.; Niyato, D.; Wong, K.-K. Covert Communication in UAV-Assisted Air-Ground Networks. IEEE Wirel. Commun. 2021, 28, 190–197. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D.; Guha, S. Hiding information in noise: Fundamental limits of covert wireless communication. IEEE Commun. Mag. 2015, 53, 26–31. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Zhou, X.; Shu, F.; Li, J.; Wang, J. Covert Communication Achieved by a Greedy Relay in Wireless Networks. IEEE Trans. Wirel. Commun. 2018, 17, 4766–4779. [Google Scholar] [CrossRef]
- Lv, L.; Li, Z.; Ding, H.; Al-Dhahir, N.; Chen, J. Achieving Covert Wireless Communication with a Multi-Antenna Relay. IEEE Trans. Inf. Forensics Secur. 2022, 17, 760–773. [Google Scholar] [CrossRef]
- Hu, J.; Yan, S.; Shu, F.; Wang, J. Covert Transmission with a Self-Sustained Relay. IEEE Trans. Wirel. Commun. 2019, 18, 4089–4102. [Google Scholar] [CrossRef]
- Wang, J.; Tang, W.; Zhu, Q.; Li, X.; Rao, H.; Li, S. Covert Communication with the Help of Relay and Channel Uncertainty. IEEE Wirel. Commun. Lett. 2019, 8, 317–320. [Google Scholar] [CrossRef]
- Sun, R.; Yang, B.; Ma, S.; Shen, Y.; Jiang, X. Covert Rate Maximization in Wireless Full-Duplex Relaying Systems with Power Control. IEEE Trans. Commun. 2021, 69, 6198–6212. [Google Scholar] [CrossRef]
- Fu, Z.; Ju, B.; Moon, J.; Hwang, S.; Lee, I. Covert Communications in Two-way Relay Systems with Energy Harvesting. In Proceedings of the 2022 13th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 19–21 October 2022; pp. 985–989. [Google Scholar]
- Deng, D.; Li, X.; Dang, S.; Gursoy, M.C.; Nallanathan, A. Covert Communications in Intelligent Reflecting Surface-Assisted Two-Way Relaying Networks. IEEE Trans. Veh. Technol. 2022, 71, 12380–12385. [Google Scholar] [CrossRef]
- Wang, M.; Xu, Z.; Xia, B.; Guo, Y.; Chen, Z. DF Relay Assisted Covert Communications: Analysis and Optimization. IEEE Trans. Veh. Technol. 2023, 72, 4073–4078. [Google Scholar] [CrossRef]
- Forouzesh, M.; Azmi, P.; Kuhestani, A. Secure Transmission with Covert Requirement in Untrusted Relaying Networks. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018; pp. 670–675. [Google Scholar]
- Forouzesh, M.; Khodadad, F.S.; Azmi, P.; Kuhestani, A.; Ahmadi, H. Simultaneous Secure and Covert Transmissions against Two Attacks under Practical Assumptions. IEEE Internet Things J. 2023, 10, 10160–10171. [Google Scholar] [CrossRef]
- Bai, J.; He, J.; Chen, Y.; Shen, Y.; Jiang, X. On Covert Communication Performance with Outdated CSI in Wireless Greedy Relay Systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2920–2935. [Google Scholar] [CrossRef]
- Su, Y.; Sun, H.; Zhang, Z.; Lian, Z.; Xie, Z.; Wang, Y. Covert Communication with Relay Selection. IEEE Wirel. Commun. Lett. 2021, 10, 421–425. [Google Scholar] [CrossRef]
- Forouzesh, M.; Azmi, P.; Kuhestani, A.; Yeoh, P.L. Covert Communication and Secure Transmission over Untrusted Relaying Networks in the Presence of Multiple Wardens. IEEE Trans. Commun. 2020, 68, 3737–3749. [Google Scholar] [CrossRef]
- Yu, X.; Yan, S.; Hu, J.; Haskell-Dowl, P.; Han, Y.; Ng, D.W.K. On Relaying Strategies in Multi-Hop Covert Wireless Communications. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 666–672. [Google Scholar]
- Gao, C.; Yang, B.; Jiang, X.; Inamura, H.; Fukushi, M. Covert Communication in Relay-Assisted IoT Systems. IEEE Internet Things J. 2021, 8, 6313–6323. [Google Scholar] [CrossRef]
- Moon, J. Covert Communications in a Compress-and-Forward Relay System. ICT Express, 2023; in press. [Google Scholar] [CrossRef]
- Makki, B.; Alouini, M.-S. End-to-End Performance Analysis of Delay-Sensitive Multi-Relay Networks. IEEE Commun. Lett. 2019, 23, 2159–2163. [Google Scholar] [CrossRef]
- He, B.; Yan, S.; Zhou, X.; Lau, V.K.N. On Covert Communication with Noise Uncertainty. IEEE Commun. Lett. 2017, 21, 941–944. [Google Scholar] [CrossRef]
- Si, J.; Li, Z.; Zhao, Y.; Cheng, J.; Guan, L.; Shi, J.; Al-Dhahir, N. Covert Transmission Assisted by Intelligent Reflecting Surface. IEEE Trans. Commun. 2021, 69, 5394–5408. [Google Scholar] [CrossRef]
- Ta, H.Q.; Ho-Van, K.; da Costa, D.B.; Kim, S.W.; Oh, H. Covert Communications over Non-Orthogonal Multiple Overt Channels. IEEE Access 2022, 10, 122361–122375. [Google Scholar] [CrossRef]
- Park, S.-H.; Simeone, O.; Sahin, O.; Shitz, S.S. Fronthaul Compression for Cloud Radio Access Networks: Signal processing advances inspired by network information theory. IEEE Signal Process. Mag. 2014, 31, 69–79. [Google Scholar] [CrossRef]
- Gamal, A.E.; Kim, Y.H. Network Information Theory; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Kim, S.W.; Ta, H.Q. Covert Communications over Multiple Overt Channels. IEEE Trans. Commun. 2022, 70, 1112–1124. [Google Scholar] [CrossRef]
- Moon, J.; Simeone, O.; Park, S.-H.; Lee, I. Online Reinforcement Learning of X-Haul Content Delivery Mode in Fog Radio Access Networks. IEEE Signal Process. Lett. 2019, 26, 1451–1455. [Google Scholar] [CrossRef]
- Yacoub, M.D. The α-η-κ-μ Fading Model. IEEE Trans. Antennas Propag. 2016, 64, 3597–3610. [Google Scholar] [CrossRef]
- Yacoub, M.D. The α-μ Distribution: A Physical Fading Model for the Stacy Distribution. IEEE Trans. Veh. Technol. 2007, 56, 27–34. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Moon, J. Performance Comparison of Relay-Based Covert Communications: DF, CF and AF. Sensors 2023, 23, 8747. https://doi.org/10.3390/s23218747
Moon J. Performance Comparison of Relay-Based Covert Communications: DF, CF and AF. Sensors. 2023; 23(21):8747. https://doi.org/10.3390/s23218747
Chicago/Turabian StyleMoon, Jihwan. 2023. "Performance Comparison of Relay-Based Covert Communications: DF, CF and AF" Sensors 23, no. 21: 8747. https://doi.org/10.3390/s23218747
APA StyleMoon, J. (2023). Performance Comparison of Relay-Based Covert Communications: DF, CF and AF. Sensors, 23(21), 8747. https://doi.org/10.3390/s23218747





