Abstract
Covert communications have arisen as an effective communications security measure that overcomes some of the limitations of cryptography and physical layer security. The main objective is to completely conceal from external devices the very existence of the link for exchanging confidential messages. In this paper, we take a step further and consider a scenario in which a covert communications node disguises itself as another functional entity for even more covertness. To be specific, we study a system where a source node communicates with a seemingly receive-only destination node which, in fact, is full-duplex (FD) and covertly delivers critical messages to another hidden receiver while evading the surveillance. Our aim is to identify the achievable covert rate at the hidden receiver by optimizing the public data rate and the transmit power of the FD destination node subject to the worst-case detection error probability (DEP) of the warden. Closed-form solutions are provided, and we investigate the effects of various system parameters on the covert rate through numerical results, one of which reveals that applying more (less) destination transmit power achieves a higher covert rate when the source transmit power is low (high). Since our work provides a performance guideline from the information-theoretic point of view, we conclude this paper with a discussion on possible future research such as analyses with practical modulations and imperfect channel state information.
1. Introduction
Wireless technology has revolutionized the way people live in various ways [1]. However, behind the proliferation of wireless communications are cyberattacks that leave users open to information leakage [2]. To cope with this, cryptography has widely been adopted, which encrypts and decrypts data using secret keys [3]. Nevertheless, this approach has certain limitations, e.g., high complexity for generating secret keys and vulnerability to eavesdroppers with stronger computational power, which are particularly unfavorable for the Internet of Things (IoT) devices. These downsides have led researchers to examine the possibility of utilizing physical layer security [4]. Its main characteristic is that a wireless link from legitimate entities to eavesdroppers can be effectively obstructed, either by nullifying beamforming with multiple antennas, or by disruption with artificial noise (AN) [5]. Hence, the dependency on secret key agreements and the need of avoiding high-powered adversaries can be greatly alleviated.
Still, some applications require an even more strict level of confidentiality. A reconnaissance troop would require reporting its surroundings to the operation center without being detected by enemies in the middle of a military mission [6], or closed networks in security facilities need to make sure that any classified information over the air is concealed from any external party. An adequate technology for such situations is covert communications or low-probability-of-detection communications that hide the existence of a critical communications link [7].
Covert communications have also been extensively studied for full-duplex (FD) systems. A basic three-node system with a covert transmitter and an FD receiver that simultaneously emits AN was studied in [8]. The authors of [9,10] further treated specific channel properties where only channel distribution information of the transmitter-warden link is available, and where every link is non-coherent with channel distribution information for slow or fast fading, respectively. An antenna selection at the receiver was studied in [11], and a transmission time selection and power control strategy were presented by [12] based on channel state information (CSI). The authors in [13] also verified the effectiveness of a truncated channel inversion power control that ceases covert transmission when the channel of the transmitter–receiver is low. A delay-constrained covert communications with a fixed AN power was investigated in [14], and joint AN power and receiver position optimization problems were discussed in [15,16]. Uncertain locations of a warden node were also taken into consideration in [17]. On top of the AN, a random covert channel selection by the transmitter was studied in [18] to aggravate the confusion of the warden. The maximum detection error probability (DEP) subject to the age of information constraint was identified by [19].
As for more complex FD systems, an FD amplify-and-forward (AF) relay was considered by [20], and the authors in [21] designed an energy harvesting FD decode-and-forward (DF) relay-based covert communications protocol in which the relay forwards and harvests energy simultaneously. Moreover, for integrated satellite–terrestrial communications, an FD relay-aided covert communications from a satellite to a ground node was explored in [22].
For intelligent reflecting surface (IRS)-aided covert communications, a transmit beamforming vector and the reflecting coefficients are jointly optimized when an FD receiver broadcasts random AN to confuse the warden in [23]. An uplink covert communications with the aid of an IRS was also investigated by [24]. Utilizing an active IRS, which is naturally FD, for covert communications between a pair of users was discussed in [25]. The age of information was minimized in [26] when a receiver covertly transmits confidential messages to the transmitter, shielded under public transmissions from the transmitter to the receiver with the aid of an IRS.
For an FD unmanned aerial vehicle (UAV) that collects data from a scheduled user and interferes with unscheduled users with AN, the maximum lowest average covert rate was obtained in [27]. In [28], the location of a covert transmitter UAV was optimized with the help of an FD ground receiver that confuses the warden, and in [29], covert communications with a hovering FD UAV relay assuming Rician air–ground channel was studied. The authors of [30] considered an FD DF UAV relay to aid in covert communications where multiple sensors deliver messages to a remote base station in orthogonal time slots.
Moreover, in a cognitive radio system, covert communications between secondary users in the presence of FD eavesdroppers that interfere with the secondary receiver with AN were examined by [31]. The work in [32] studied covert rate maximization with a half-duplex (HD)/FD mode switching device-to-device (D2D) covert receiver in the presence of an uplink spectrum-sharing cellular network. Both secrecy and covert rates were optimized when an untrusted FD AF relay delivers the covert message to an FD base station that emits AN to the warden in [33].
In the IoT environment, the authors of [34] studied a covert transmitter with an optimized transmission probability, which is wirelessly charged by the AN from an FD receiver. Furthermore, covert uplink transmissions of devices towards FD IoT gateways were optimized based on the mean-field Stackelberg game approach in [35]. With an ambient backscatter system, a radio frequency tag modulates an ambient signal into a covert signal for an FD receiver that concurrently broadcasts AN [36].
Most of past works have assumed that the surveillance nodes have a perfect knowledge of the hardware specifications of covert nodes. However, the covert nodes could disguise themselves as other functional entities for even more covertness. For instance, an original FD node that secretly transmits confidential messages may disguise itself as a receive-only HD node. To the best of the author’s knowledge, there are not enough studies on covert communications that consider such disguised tactics.
In this paper, we study a covert communications system where a source node communicates with a disguised FD destination node. Supposedly receive-only, the destination node covertly delivers critical messages with an invisible extra antenna to another hidden receiver while evading the surveillance of a warden node as much as possible. We identify the optimal public data rate and the transmit power of the FD destination node that maximizes the covert rate at the hidden receiver. Closed-form solutions are provided, and we investigate the effects of various system parameters on the covert rate through numerical results.
Our main contributions are summarized as follows:
- Different from past works which assume that the surveillance party is confident of the hardware specifications of covert nodes, we take a step further and consider a practical scenario in which a covert communications node disguises itself as another functional entity for even more covertness.
- The worst-case DEP is derived in the presence of noise uncertainty at the warden node.
- Noting that covert communications typically suffer from a low data rate due to the stringent DEP requirements, we focus on maximizing the covert rate at the hidden receiver by optimizing the public data rate and the transmit power of the FD destination node subject to the worst-case DEP of the warden.
- We investigate the effects of various system parameters on the covert rate through numerical results, one of which reveals that applying more (less) destination transmit power achieves a higher covert rate when the source transmit power is low (high).
- Since our work provides a performance guideline from the information-theoretic point of view, we suggest analyses with practical modulations and imperfect CSI as valuable future research topics.
2. System Model
2.1. Received Signals
Figure 1 illustrates the considered system model where the source node S sends a public message to the destination node D. In the meantime, the seemingly receive-only destination node executes a covert transmission via an invisible extra antenna to the hidden receiver R in an FD manner when the warden node W keeps monitoring the existence of any such unexpected communications.
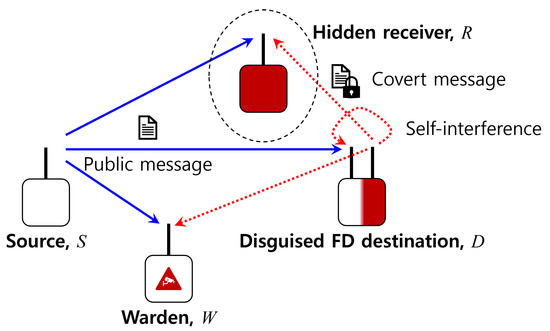
Figure 1.
System model.
First, the received signal at the disguised FD destination node is expressed by
where stands for the channel coefficient between node and for , specifies the residual self-interference channel after self-interference cancellation, and denote the public and covert messages, respectively, and indicate the transmit power at the source node and destination node, respectively, and represents the additive noise at node . Note that the destination node can keep the CSI of the source node since the covert transmission occurs internally under the normal S-D communications. The hidden receiver can also easily estimate the CSI of the source and destination nodes, and , during channel estimation duration if pilot sequences are informed from the destination node in advance. As for the availability of CSI on the warden node, we assume the worst-case covert communications scenario in this work, meaning that the warden has the perfect knowledge of the CSI from the destination and hidden receiver to identify the worst-case achievable covert rate as a performance guideline in practice.
The source node follows an adaptive transmission policy by which the public data rate is adjusted based on the feedback from the destination, and the achievable public data rate at the destination can be written as [37]
The hidden receiver then receives both a public message through the direct link from the source node and a covert message from the destination node as
Therefore, the hidden receiver needs to successfully decode and eliminate public messages before retrieving covert messages. This implies that the public data rate is also limited by the achievable public data rate at the hidden receiver as
The resulting achievable covert rate after removing from can also be calculated as
2.2. Covert Message Detection
At the same time, the warden node receives
It first excludes public messages from to obtain the effective residual signal , assuming it perfectly knows and [38]. We then have the following two hypotheses:
where the null hypothesis assumes that there does not exist a covert message, and the alternative hypothesis presumes that the source node did not send a covert message. This work considers a radiometer [39] as a detection means at the warden, and the sufficient test statistic T for (7) after observing number of signals reduces to the average residual power as [40]
The warden node makes a decision that a covert transmission exists when and otherwise when with some threshold .
We consider the uncertainty in the noise variance at the warden node as in [39,41]. Concretely, in decibel scale with and set to the mean and bounded range, respectively. We then derive the DEP that consists of the false alarm and miss probabilities as
in which the warden node conjectures that the covert transmission randomly takes place with [42]. Making use of the cumulative distribution function (CDF) of (Appendix A),
the false alarm and miss probability are specifically written by
respectively. Here, and .
We have two different cases depending on the value of and . If ,
where . In contrast, if ,
with , and .
The warden node may desire a particular that can minimize the DEP. To this end, we first see that (11) and (12) are monotonic from 1 to 0 for and 0 to 1 for , respectively. Moreover, the first derivative of is calculated as
This is always positive for ; therefore, the optimal threshold for the warden node in both (13) and (14) is determined by the boundary between and , or and as
Note that (16) provides the worst-case minimum DEP assuming that the warden node knows the exact value of .
3. Problem Formulation
In this work, we aim to identify the optimal public data rate and transmit power of the FD destination node that maximizes the covert rate at the hidden receiver as
Constraint (17b) guarantees that the hidden receiver successfully decodes and eliminates a public message prior to decoding a covert message, and (17c) indicates the achievable public data rate up to which the destination node can notify the source node to adjust. A minimum quality of service for the public transmission is considered in (17d), and (17e) with (17f) assures the non-zero minimum DEP for . Lastly, (17g) shows the power budget at the disguised FD destination node.
4. Proposed Solutions
We first note that the covert rate in (17a) is an increasing function of while the upper limits of in (17b) and (17c) are decreasing functions of . This means that the covert rate cannot exceed a value at which one of the upper limits becomes , i.e., . Therefore, it is optimal for to be as low as possible for the maximum covert rate as
We now simplify (P1) using the monotonicity of logarithms as
The right-hand side of (19d) is larger than or equal to that of (19e) for , implying that satisfying (19d) automatically fulfills (19e). Therefore, the optimal transmit power can be obtained by taking the minimum of the upper bounds from (19b)–(19d) and (19f) as
Remark 1.
When the D-R link is extremely strong, i.e., , we have since the hidden receiver cannot eliminate a source message in the presence of a dominant covert message, which is a prerequisite. When there exists excessive FD self-interference, i.e., , we also have for the public data rate, which cannot reach the given threshold . Lastly, when the channel gain of the D-W link is exceptionally high, i.e., , we have as well, since the absence and existence of covert transmission will cause a large difference in the received power at the warden, making it easier to detect any covert transmissions.
5. Numerical Results
We evaluate the proposed solutions for covert communications with the disguised FD node through numerical results. The effects of various system parameters such as the source transmit power, disguised FD destination transmit power budget, noise uncertainty bound, and minimum DEP threshold on the achievable covert rate in (5) with the derived optimal destination transmit power in (20) are examined in the upcoming figures. We also focus on verification that fulfills the DEP requirements for any desired threshold in (17e) and compare with baseline schemes to stress the significance of .
The distance-dependent channel model is adopted for [43]. Concretely, we let , where indicates the path loss between and . Here, stands for the path loss at a reference distance m, represents the path loss exponent, and indicates the distance between and . Also, the small-scale channel variable follows . The four nodes are placed with certain distances from the origin in a Cartesian coordinate system such that the coordinates of S, D, R, W are , , , , respectively (Figure 2). The overall system parameters are fixed as follows unless otherwise stated: the bandwidth MHz, m, source transmit power dBm, destination transmit power budget dBm, public message quality of service bps/Hz, mean noise power at the warden node dBm/Hz, noise uncertainty bound dB, noise power at the destination node and hidden receiver dBm/Hz, residual self-interference dB, minimum DEP threshold , and pathloss exponent .
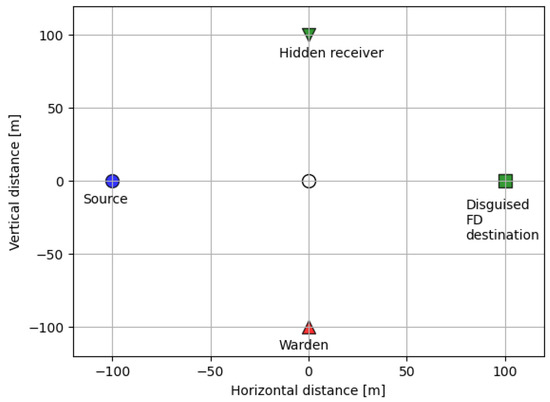
Figure 2.
Node placements.
Figure 3 shows the average covert rate as the source transmit power varies. Motivated by the fact that the destination transmit power should be much lower than for successful covert transmissions, we compare the optimal scheme with “% ” in which is fixed as . We notice that the proposed public data rate in (18) and destination transmit power in (20) result in the highest covert rate for every value, indicating the importance of optimizing and .
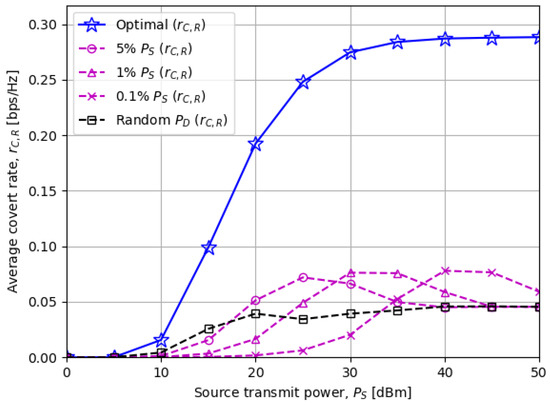
Figure 3.
The average covert rate versus the source node power : Applying more (less) is preferred when is low (high).
We also observe from the “% ” schemes that applying more to a covert transmission induces a higher covert rate when is low, while less is preferred when is high. First, when is low, the public data rate constraints in (17b) and (17c) dominate determining from (20). If , then any “% ” schemes with are likely to be infeasible on average. It can be inferred from Figure 3 that that for our system setup since “5% ” performs the best among the other fixed schemes.
On the other hand, when is high, the DEP constraint in (17e) and the power budget dominate deciding . Hence, only the “% ” schemes with sufficiently low % can meet these requirements and be feasible on average. This explains the reason why “0.1% ” outperforms those with higher % in Figure 3 in the high region.
Figure 4 compares the average covert rate as the destination transmit power budget changes. It can be seen that “5% ” and random schemes perform close to the optimal scheme when is low. The reasons are that is dominated by in this region and that fixed or randomly chosen in the compared schemes is reduced to if . For the rest of the regions, our proposed solutions achieve the highest covert rate which once more highlights the necessity of optimizing the and .
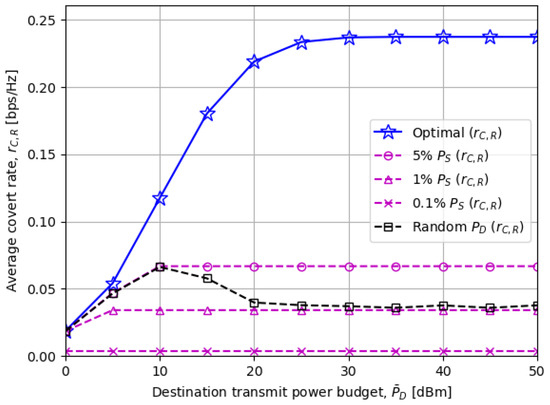
Figure 4.
The average covert rate versus the destination node power budget : Close performance among the presented schemes for low since the optimal is dominantly limited by .
Figure 5 demonstrates the average covert rate for different noise uncertainty bounds at the warden node. Quantitatively, a larger widens the upper bound for in (20) so that the covert rate, which is proportional to , has more chance to be enhanced on average. Also, from the qualitative aspect, the larger there is, the more confusion the warden node undergoes in deciding the existence of covert communications.
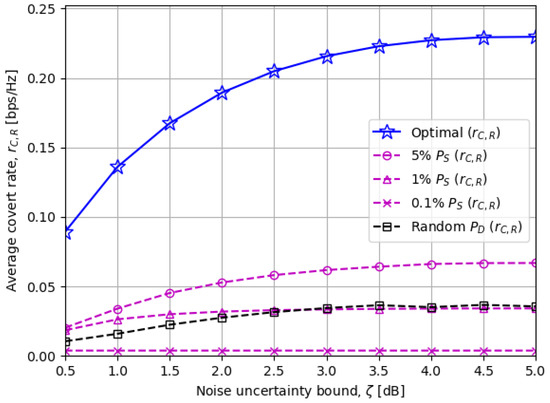
Figure 5.
The average covert rate versus the noise uncertainty bound [dB]: The more unsettled is, the easier it is to perform covert transmissions.
Figure 6 and Figure 7 illustrate the average covert rate and DEP, respectively, when the minimum DEP threshold changes. The covert rates decline in a monotonic manner as increases and eventually become zero when a perfect DEP of 0.5 is imposed on. Figure 7 also verifies that the proposed optimal solutions provide just enough DEP above the threshold in general, while the other baseline schemes achieve unnecessarily high DEP by sacrificing the covert rate.
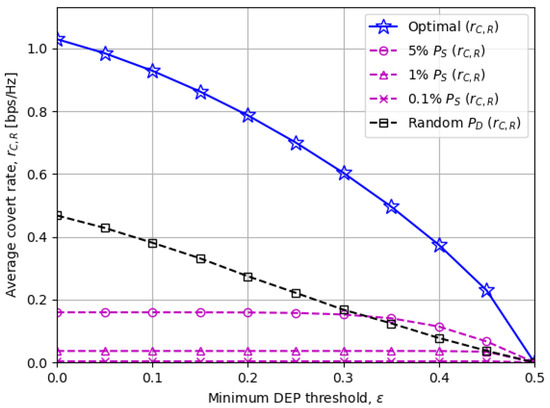
Figure 6.
The average covert rate versus the minimum DEP threshold .
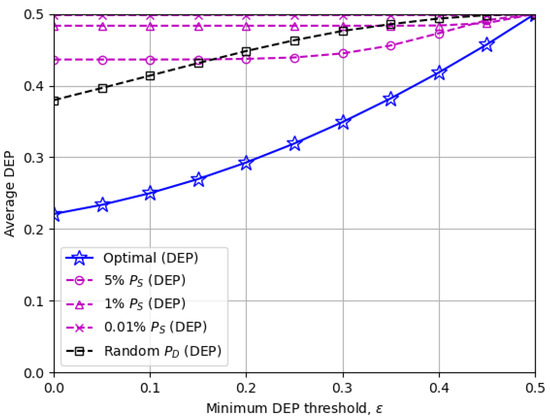
Figure 7.
The average DEP versus the minimum DEP threshold : The optimal scheme benefits from the best trade-off between the covert rate and DEP for a given .
6. Discussion
6.1. Performance
The numerical results from Figure 3, Figure 4, Figure 5, Figure 6 and Figure 7 confirmed that the optimized transmit power at the disguised FD destination node has a significant impact on the covert rate performance. Furthermore, Figure 3 revealed an interesting relationship between the source and destination transmit power, which is that applying more (less) destination transmit power achieves a higher covert rate when the source transmit power is low (high). Figure 7 also showed that the optimal destination transmits power exploits the best trade-off between the covert rate and minimum DEP threshold.
6.2. Applications
The considered system model and obtained solution may be used in various practical networks. In the military, a reconnaissance troop may place on the adversary side a counterfeit FD device that periodically reports situations while disguising itself as a typical half-duplex one. Moreover, the authors in [44] demonstrated the feasibility of FD on a low Earth orbit (LEO) satellite, and the future non-terrestrial military network would utilize the disguise tactic proposed in this paper for either defense or offense purposes. For surveillance, an IoT network administrator may exploit a disguised FD node to covertly monitor any suspicious users that misuse the network for prohibitive activities.
7. Conclusions
In this paper, we studied a covert communications system where a source node communicates with a disguised FD destination node. Supposedly receive-only, the destination node covertly delivers critical messages to another hidden receiver while evading the surveillance of a warden node as much as possible. We identified the optimal public data rate and the transmit power of the FD destination node that maximizes the covert rate at the hidden receiver.
The obtained closed-form solution exhibited the following: When the destination–receiver link is extremely strong, the optimal destination transmit power approaches zero since the hidden receiver cannot eliminate a source message prior to retrieving a covert message. If the self-interference is not sufficiently suppressed, the optimal destination transmit power approaches zero in this case as well since the public data rate cannot reach the required quality of service. In addition, when the destination–warden channel gain is exceptionally high, the optimal destination transmit power approaches zero since the large difference in the received power at the warden makes it easier to detect the covert link.
The extensive numerical results presented a phenomenon that applying more (less) destination transmit power achieves a higher covert rate when the source transmit power is low (high). It was also verified that the optimal destination transmits power yields the best balance between the covert rate and minimum DEP threshold.
Since our work provides a performance guideline from the information-theoretic point of view, we suggest analyses with practical modulations and imperfect CSI as valuable future research topics.
Funding
This research was partially supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2021R1I1A3050126). This work was partially supported by Korea Research Institute for Defense Technology Planning and Advancement (KRIT) grant funded by the Korean government (DAPA (Defense Acquisition Program Administration)) (21-106-A00-007, Space-Layer Intelligent Communication Network Laboratory, 2022).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The author declares no conflict of interest.
Appendix A
First note that . By the transformation of probability density functions (PDFs) with the Jacobian J defined by [45]
the PDF of becomes
Accordingly, the CDF of is obtained by
which yields (10).
References
- Qazi, S.; Khawaja, B.A.; Farooq, Q.U. IoT-Equipped and AI-Enabled Next Generation Smart Agriculture: A Critical Review, Current Challenges and Future Trends. IEEE Access 2022, 10, 21219–21235. [Google Scholar] [CrossRef]
- Zhang, J.; Yan, Z.; Fei, S.; Wang, M.; Li, T.; Wang, H. Is Today’s End-to-End Communication Security Enough for 5G and Its Beyond? IEEE Netw. 2022, 36, 105–112. [Google Scholar] [CrossRef]
- Forouzan, B.A. Cryptography and Network Security; McGraw-Hill: New York, NY, USA, 2007. [Google Scholar]
- Wyner, A.D. The Wire-Tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Angueira, P.; Val, I.; Montalbán, J.; Seijo, Ó.; Iradier, E.; Fontaneda, P.S.; Fanari, L.; Arriola, A. A Survey of Physical Layer Techniques for Secure Wireless Communications in Industry. IEEE Commun. Surv. Tutor. 2022, 24, 810–838. [Google Scholar] [CrossRef]
- Jiang, X.; Chen, X.; Tang, J.; Zhao, N.; Zhang, X.Y.; Niyato, D.; Wong, K.-K. Covert Communication in UAV-Assisted Air-Ground Networks. IEEE Wirel. Commun. 2021, 28, 190–197. [Google Scholar] [CrossRef]
- Bash, B.A.; Goeckel, D.; Towsley, D.; Guha, S. Hiding information in noise: Fundamental limits of covert wireless communication. IEEE Commun. Mag. 2015, 53, 26–31. [Google Scholar] [CrossRef]
- Shahzad, K.; Zhou, X.; Yan, S.; Hu, J.; Shu, F.; Li, J. Achieving Covert Wireless Communications Using a Full-Duplex Receiver. IEEE Trans. Wirel. Commun. 2018, 17, 8517–8530. [Google Scholar] [CrossRef]
- Xu, T.; Xu, L.; Liu, X.; Lu, Z. Covert Communication with A Full-Duplex Receiver Based on Channel Distribution Information. In Proceedings of the 2018 12th International Symposium on Antennas, Propagation and EM Theory (ISAPE), Hangzhou, China, 3–6 December 2018; pp. 1–4. [Google Scholar]
- Zheng, M.; Hamilton, A.; Ling, C. Covert Communications with a Full-Duplex Receiver in Non-Coherent Rayleigh Fading. IEEE Trans. Commun. 2021, 69, 1882–1895. [Google Scholar] [CrossRef]
- Yang, L.; Yang, W.; Xu, S.; Tang, L.; He, Z. Achieving Covert Wireless Communications Using a Full-Duplex Multi-Antenna Receiver. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019; pp. 912–916. [Google Scholar]
- Wang, J.; Li, Y.; Tang, W.; Li, X.; Li, S. Channel State Information Based Optimal Strategy for Covert Communication. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 December 2019; pp. 1–6. [Google Scholar]
- Hu, J.; Yan, S.; Zhou, X.; Shu, F.; Li, J. Covert Wireless Communications With Channel Inversion Power Control in Rayleigh Fading. IEEE Trans. Veh. Technol. 2019, 68, 12135–12149. [Google Scholar] [CrossRef]
- Shu, F.; Xu, T.; Hu, J.; Yan, S. Delay-Constrained Covert Communications With a Full-Duplex Receiver. IEEE Wirel. Commun. Lett. 2019, 8, 813–816. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, Z.; Cheng, N.; Wang, D.; Quan, W.; Shen, X. Joint Power and Position Optimization for the Full-Duplex Receiver in Covert Communication. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 July 2020; pp. 1–6. [Google Scholar]
- Xu, R.; Guan, L.; Zhao, Y.; Li, Z.; Wang, D. Robust Power and Position Optimization for the Full-Duplex Receiver in Covert Communication. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Chen, X.; Sun, W.; Xing, C.; Zhao, N.; Chen, Y.; Yu, F.R.; Nallanathan, A. Multi-Antenna Covert Communication via Full-Duplex Jamming Against a Warden With Uncertain Locations. IEEE Trans. Wirel. Commun. 2021, 20, 5467–5480. [Google Scholar] [CrossRef]
- Che, B.; Yang, W.; Lu, X. Covert Communication for Multi-Channel Transmission with A Full-Duplex Receiver. In Proceedings of the 2021 13th International Conference on Wireless Communications and Signal Processing (WCSP), Changsha, China, 20–22 October 2021; pp. 1–5. [Google Scholar]
- Wang, Y.; Yan, S.; Yang, W.; Cai, Y. Covert Communications With Constrained Age of Information. IEEE Wirel. Commun. Lett. 2021, 10, 368–372. [Google Scholar] [CrossRef]
- Sun, R.; Yang, B.; Ma, S.; Shen, Y.; Jiang, X. Covert Rate Maximization in Wireless Full-Duplex Relaying Systems With Power Control. IEEE Trans. Commun. 2021, 69, 6198–6212. [Google Scholar] [CrossRef]
- Li, Y.; Zhao, R.; Deng, Y.; Shu, F.; Nie, Z.; Aghvami, A.H. Harvest-and-Opportunistically-Relay: Analyses on Transmission Outage and Covertness. IEEE Trans. Wirel. Commun. 2020, 19, 7779–7795. [Google Scholar] [CrossRef]
- Wu, Z.; Guo, K.; Zhu, S. Covert Communication for Integrated Satellite–Terrestrial Relay Networks with Cooperative Jamming. Electronics 2023, 12, 999. [Google Scholar] [CrossRef]
- Wang, C.; Li, Z.; Shi, J.; Ng, D.W.K. Intelligent Reflecting Surface-Assisted Multi-Antenna Covert Communications: Joint Active and Passive Beamforming Optimization. IEEE Trans. Commun. 2021, 69, 3984–4000. [Google Scholar] [CrossRef]
- Pejoski, S.; Hadzi-Velkov, Z.; Zlatanov, N. Full-Duplex Covert Communications Assisted by Intelligent Reflective Surfaces. IEEE Commun. Lett. 2022, 26, 2846–2850. [Google Scholar] [CrossRef]
- Wang, M.; Xu, Z.; Xia, B.; Guo, Y. Active Intelligent Reflecting Surface Assisted Covert Communications. IEEE Trans. Veh. Technol. 2023, 72, 5401–5406. [Google Scholar] [CrossRef]
- Wang, C.; Li, Z.; Zheng, T.-X.; Ng, D.W.K.; Al-Dhahir, N. Intelligent Reflecting Surface-Aided Full-Duplex Covert Communications: Information Freshness Optimization. IEEE Trans. Wirel. Commun. 2023, 22, 3246–3263. [Google Scholar] [CrossRef]
- Zhou, X.; Yan, S.; Shu, F.; Chen, R.; Li, J. UAV-Enabled Covert Wireless Data Collection. IEEE J. Sel. Areas Commun. 2021, 39, 3348–3362. [Google Scholar] [CrossRef]
- Guo, Z.; Zhao, S.; Wang, J.; Lit, H.; Shen, Y. Optimal Location Design for UAV Covert Communications with a Full-Duplex Receiver. In Proceedings of the 2022 International Conference on Networking and Network Applications (NaNA), Urumqi, China, 3–5 December 2022; pp. 35–40. [Google Scholar]
- Zhang, R.; Chen, X.; Liu, M.; Zhao, N.; Wang, X.; Nallanathan, A. UAV Relay Assisted Cooperative Jamming for Covert Communications Over Rician Fading. IEEE Trans. Veh. Technol. 2022, 71, 7936–7941. [Google Scholar] [CrossRef]
- Li, M.; Tao, X.; Wu, H.; Li, N. Joint Trajectory and Resource Optimization for Covert Communication in UAV-Enabled Relaying Systems. IEEE Trans. Veh. Technol. 2023, 72, 5518–5523. [Google Scholar] [CrossRef]
- Yang, J.; Zhou, H.; Chen, R.; Shi, J.; Li, Z. Covert Communication Against a Full-Duplex Adversary in Cognitive Radio Networks. In Proceedings of the GLOBECOM 2022-2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 3144–3149. [Google Scholar]
- Yang, Y.; Yang, B.; Shen, S.; She, Y.; Taleb, T. Covert Rate Study for Full-Duplex D2D Communications Underlaid Cellular Networks. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Sun, R.; Yang, B.; Shen, Y.; Jiang, X.; Taleb, T. Covertness and Secrecy Study in Untrusted Relay-Assisted D2D Networks. IEEE Internet Things J. 2023, 10, 17–30. [Google Scholar] [CrossRef]
- Wang, Y.; Yan, S.; Yang, W.; Zhong, C.; Ng, D.W.K. Probabilistic Accumulate-Then-Transmit in Wireless-Powered Covert Communications. IEEE Trans. Wirel. Commun. 2022, 21, 10393–10406. [Google Scholar] [CrossRef]
- Feng, S.; Lu, X.; Sun, S.; Niyato, D. Mean-Field Artificial Noise Assistance and Uplink Power Control in Covert IoT Systems. IEEE Trans. Wirel. Commun. 2022, 21, 7358–7373. [Google Scholar] [CrossRef]
- Liu, J.; Yu, J.; Chen, X.; Zhang, R.; Wang, S.; An, J. Covert Communication in Ambient Backscatter Systems With Uncontrollable RF Source. IEEE Trans. Commun. 2022, 70, 1971–1983. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory; John Wiley & Sons, Inc.: New Jersey, NJ, USA, 2005. [Google Scholar]
- Kim, S.W.; Ta, H.Q. Covert Communications Over Multiple Overt Channels. IEEE Trans. Commun. 2022, 70, 1112–1124. [Google Scholar] [CrossRef]
- He, B.; Yan, S.; Zhou, X.; Lau, V.K.N. On Covert Communication With Noise Uncertainty. IEEE Commun. Lett. 2017, 21, 941–944. [Google Scholar] [CrossRef]
- Sobers, T.V.; Bash, B.A.; Guha, S.; Towsley, D.; Goeckel, D. Covert Communication in the Presence of an Uninformed Jammer. IEEE Trans. Wirel. Commun. 2017, 16, 6193–6206. [Google Scholar] [CrossRef]
- Si, J.; Li, Z.; Zhao, Y.; Cheng, J.; Guan, L.; Shi, J.; Al-Dhahir, N. Covert Transmission Assisted by Intelligent Reflecting Surface. IEEE Trans. Commun. 2021, 69, 5394–5408. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, J.; Zeng, Y.; Ma, J. Covert Wireless Communications in IoT Systems: Hiding Information in Interference. IEEE Wirel. Commun. 2018, 25, 46–52. [Google Scholar] [CrossRef]
- Moon, J.; Lee, S.H.; Lee, H.; Lee, I. Proactive Eavesdropping With Jamming and Eavesdropping Mode Selection. IEEE Trans. Wirel. Commun. 2019, 18, 3726–3738. [Google Scholar] [CrossRef]
- Grayver, E.; Keating, R.; Parower, A. Feasibility of full duplex communications for LEO satellite. In Proceedings of the 2015 IEEE Aerospace Conference, Big Sky, MT, USA, 7–14 March 2015; pp. 1–8. [Google Scholar]
- Ross, S. A First Course in Probability, 10th ed.; Pearson: London, UK, 2019. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).