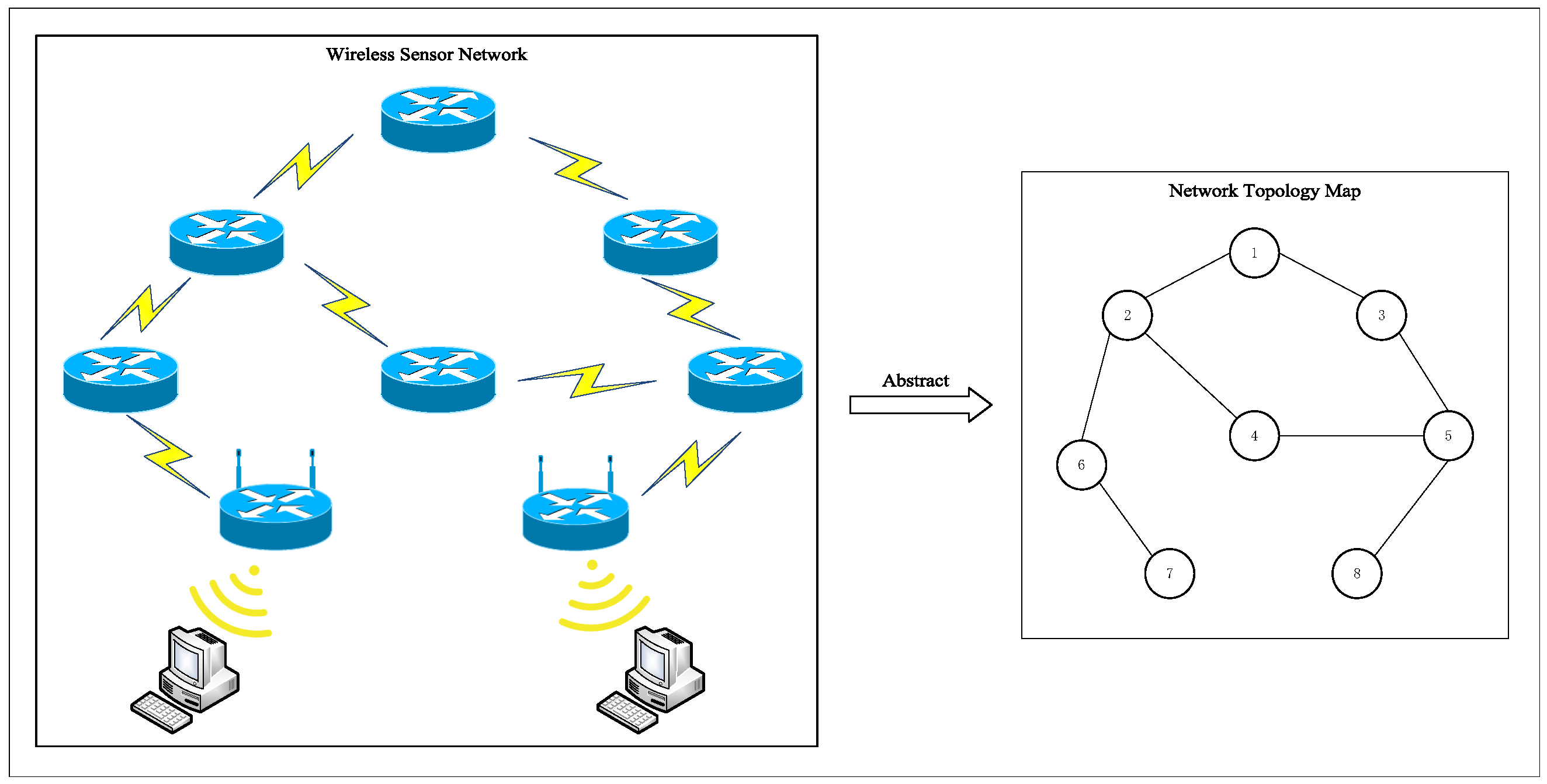
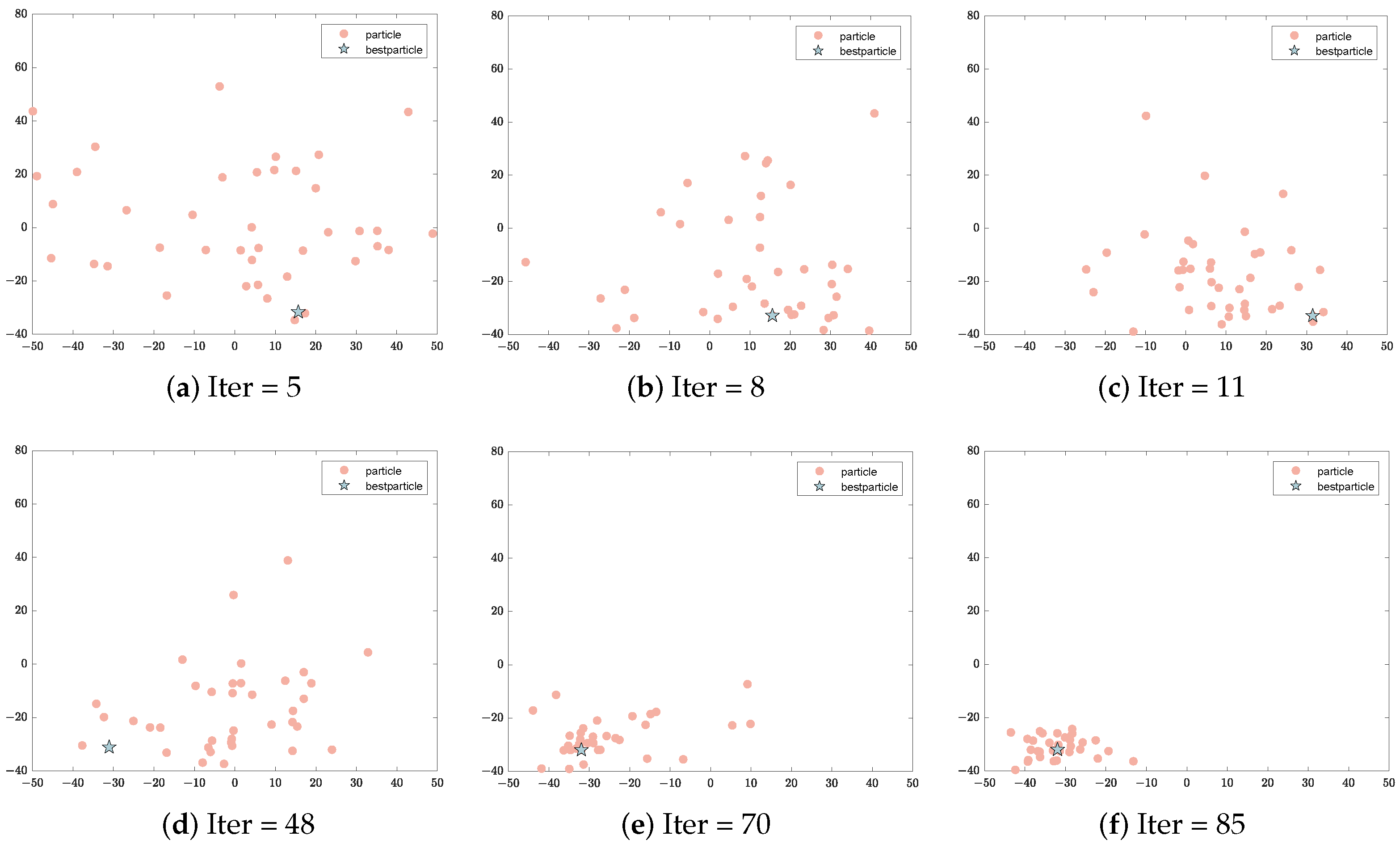
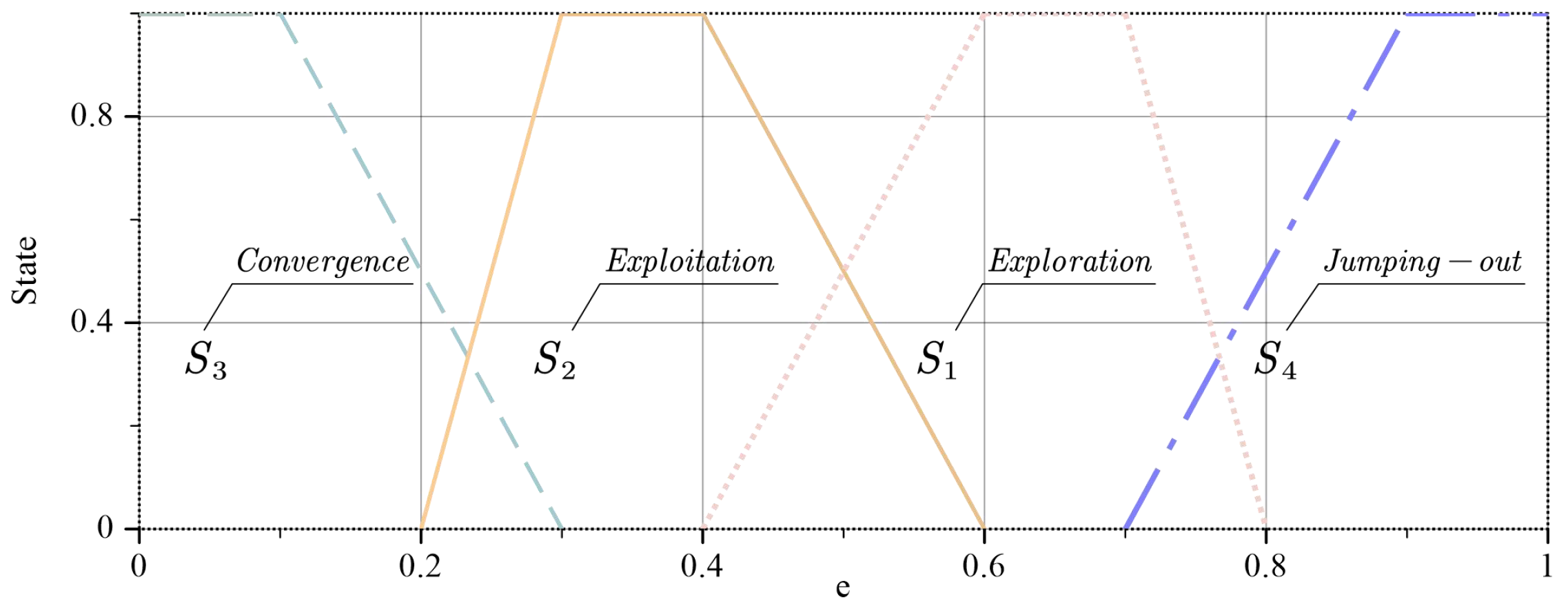
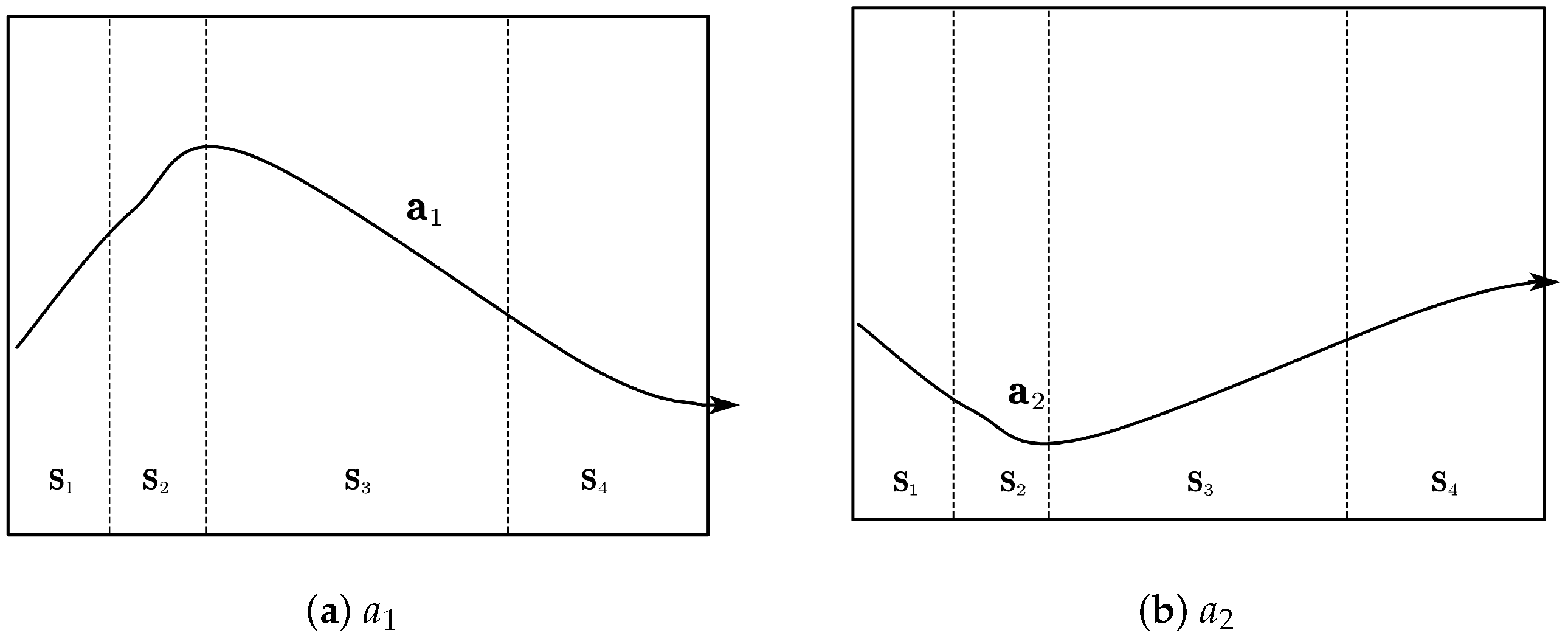
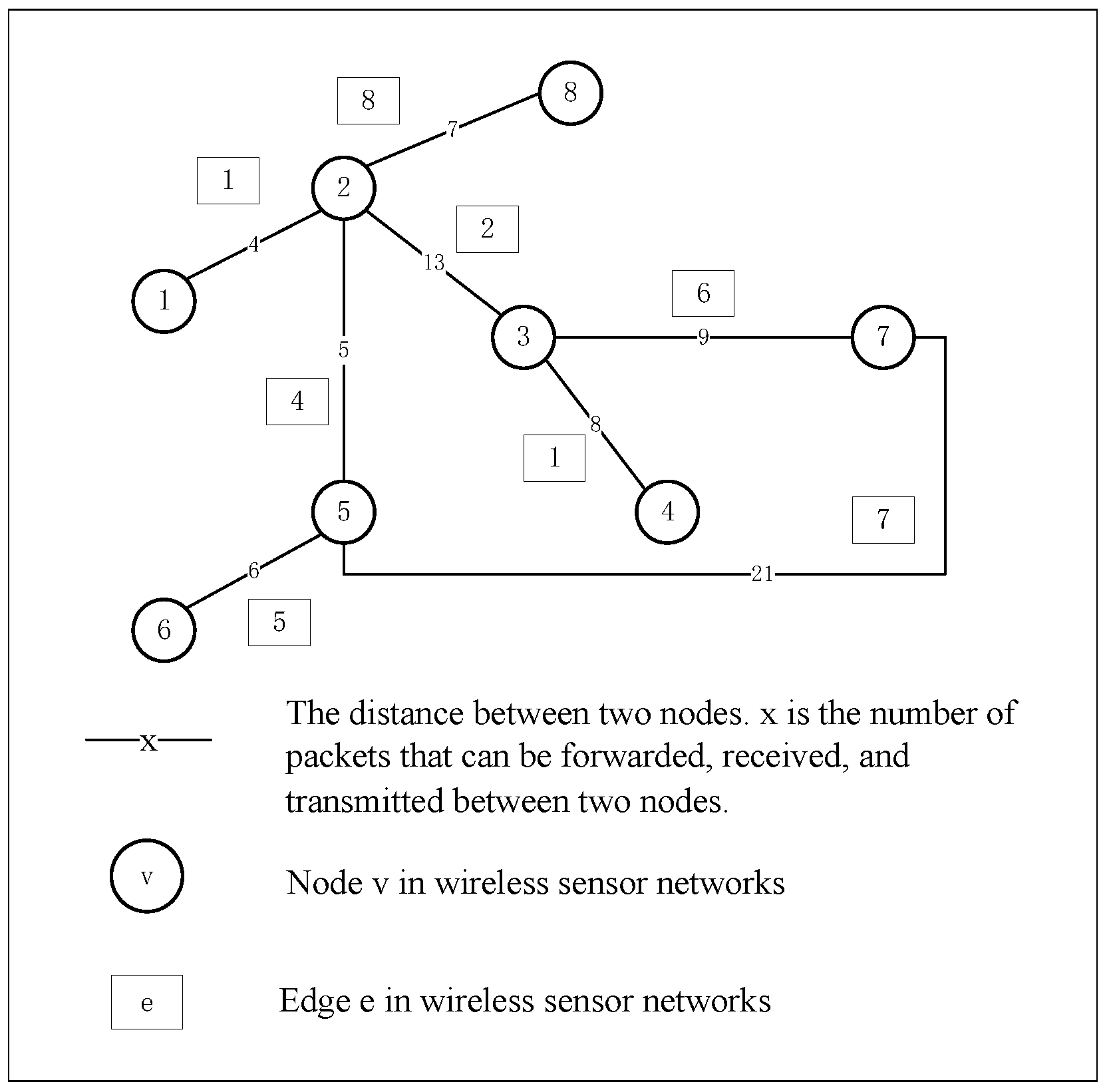
This section introduces the application and development of game theory in network security and the ideas and steps of the EO.
2.1. Application of Game Theory to Network Security
Game theory describes a multi-player decision-making scenario as a game. Each player chooses the action that gives him or her the best payoff while predicting the rational actions of the other players [
28]. Regarding the time-series nature of behavior, game theory is subdivided into two categories, namely static games and dynamic games. In terms of whether there is cooperation between participants, games can be divided into cooperative games and non-cooperative games. For the problem of cyberspace security, many scholars have used game theory to solve it and have achieved certain results [
29]. Afrand studies the offense and defense game problem in WSN intrusion detection during 2004–2005. He establishes a non-cooperative game model for offenders and defenders and constructs the payoff function and Nash equilibrium in this game. The chance of detecting an intrusion can be significantly improved through the game [
30,
31,
32]. Han applies a non-cooperative static information game model to intrusion modeling in WSNs, which improves prediction accuracy and reduces the energy consumption of IDS [
33]. Shamik applies a non-cooperative imperfect information game to the distributed sensor network power control problem. He obtains the maximum payoff of the model by analyzing the Nash equilibrium [
34]. Liu combines intelligent computing with Stackelberg game to analyze the attack and defense adversarial behavior under a graph structure network [
35]. Yang proposes a WSN offense and defense game model for multiple crimes. The game process of WSN under three modes of external offense, internal offense, and hybrid offense, respectively, gives practical guidance for the design of an intrusion detection system in WSNs [
36]. Deyu proposes a novel routing protocol based on evolutionary game theory to improve energy efficiency and longevity of WSNs [
37]. Yenumula uses a zero-sum game approach to detection to build a framework and detect malicious nodes of nodes in the forward data path to improve the defense of WSNs [
38]. It can be seen that many scholars have applied game theory to WSN security. Game theory is also applied for the offense and defense problem of WSNs in this paper. Intelligent calculation is used to solve and analyze the Nash equilibrium problem in the established game theory model to improve the solution accuracy.
2.2. Equilibrium Optimizer Algorithm
Heuristic algorithms are proposed relative to optimization algorithms. Scholars have proposed heuristic algorithms such as Bat Algorithm (BA) [
39], Differential Evolution algorithm (DE) [
40], Particle Swarm optimization algorithm (PSO) [
41], and Whale Optimization Algorithm (WOA) [
42,
43]. These algorithms have improved the ability to search for optimal solutions. EO is a physics-based heuristic optimization algorithm for dynamic source and sink models proposed by Afshin in 2020, which has the advantages of good optimization and fast convergence [
44]. The heuristic algorithm has also been improved by adding many strategies. Zheng presents a Levy flight black edge regeneration black algorithm (LEBH) to speed up the convergence rate of BH [
45]. Zheng applies the compact strategy to the snake optimization algorithm (SO). The compact snake optimization algorithm (cSO) is proposed, which effectively reduces the use of memory resources [
46]. Wang proposes the adaptive Bat algorithm (ABA), which can dynamically and adaptively adjust the flight speed and direction, significantly improving the global convergence accuracy of the BA [
47]. Zhan applies the adaptive optimization strategy to the PSO (APSO). The problem of slow convergence of PSO and ease of falling into the local optimal land was effectively solved. [
48]. Ahmed and Qin also apply adaptive strategy to WOA (ANWOA) and DE (ADE), respectively, and the convergence speed and optimization accuracy of the original algorithm can be effectively improved [
49,
50]. The adaptive strategy can dynamically adjust the parameters of the algorithm and change the direction and speed of particle motion in the algorithm so that it can easily solve the problem that the algorithm is prone to local optimization and improve the accuracy of the global optimization. Thus, the adaptive strategy is applied to EO to improve the optimization ability and convergence speed of EO.
The main of inspiration for the EO is the simple mixing of well-defined dynamic mass balance phenomena on the control volume. The first-order ordinary differential equation for the mass balance equation is given by Equation (
1) [
44].
is the rate of mass change in the control volume, and
C is the concentration inside the control volume. When
is equal to zero, the solution reaches a steady state.
Q is the volumetric flow rate into and out of the control volume, and
represents the concentration at an equilibrium state.
G is the mass generation rate inside the control volume. By solving for Equation (
1) [
44], through the arrangement and combination of Equation (
1) [
44],
can be converted into a function of
.
is introduced into the formula as the flow rate, and
C can be expressed in the form of another Equation (
2) [
44].
F is the coefficient of the exponential term, which can be calculated by Equation (
3) [
44].
is the mobility rate, and
is the initial concentration of the control volume at the initial time
. The three parts of Equation (
2) [
44] can represent the three update rules in the inspired EO. The first is the equilibrium concentration, and the second is related to the concentration difference and represents the search mechanism. The third represents the part of the optimal solution. Applying Equation (
2) [
44] to the EO,
C represents the solution obtained in the current iteration, and
represents the optimal solution in the current generation. Thus, the EO continuously updates the positions of the particles through iterative search and searches for the optimal solution through a combination of local search and global search. The principle and process of the EO are shown below.
The initial concentration is constructed based on the number and dimensional of the particle swarm. The particle swarm is initialized as in Equation (
4) [
44].
represents the initial concentration of the ith particle, and it also represents the initial position of the ith particle. and denote the minimum and maximum values of the range. n represents the number of particle groups, and is a random number in the range of [0, 1].
In each iteration, each particle randomly selects a particle in the equilibrium state pool with the same probability to update its concentration. The equilibrium state pool is defined by the following Equation (
5) [
44].
, , , and are the best four solutions obtained throughout the current iteration. represents the average position of the four solutions.
To optimize the search ability, two parameters
and
are introduced to improve Equation (
3) [
44] to better balance the local and global search. The improved equation is given in Equation(
6) [
44], where
t is defined as a function of iteration (Iter) and it decreases as the number of iterations increases, as shown in Equation (
7) [
44].
r and
are random variables in the range of [0, 1]. The
in Equation (
6) [
44] represents the control exploration capability. The larger
becomes, the greater the exploration capacity and the weaker the exploitation capacity. The
in Equation (
7) [
44] represents the managed exploration capacity. The larger the
, the greater the exploitation capacity and the weaker the exploration capacity.
affects the direction of exploration and development.
Generation rate (
G) is one of the most important terms in EO, providing precise solutions by improving the development phase. G is described as a first-order exponential decay process, which is used in many engineering applications, as shown in Equation (
8) [
44].
is the initial value and
k is the attenuation constant. To better adapt to the iteration of the algorithm, the exponential term of Equation (
8) [
44] is adopted. The generation speed control parameter
is defined as Equation (
9) [
44].
G is the mass generation rate, defined as Equation (
10) [
44]. Combined with Equation (
8) [
44], G is defined in EO as shown in Equation (
11) [
44], which can provide an exact solution by improving the development phase.
gives an ideal balance of local and global search capabilities.
In summary, the rules for updating the particle positions in the EO are given in Equation (
12) [
44].
Equation (
12) [
44] is divided into three terms, the first term being the equilibrium concentration. The second and third terms indicate the change in concentration. The second term can use the concentration difference to search globally to find the best solution. The third part can make the solution more precise when the solution is found. This provides better global and local search based on the difference of symbols of the second and third terms.
Algorithm 1 is the pseudo-code for the EO.
| Algorithm 1 Equilibrium Optimizer |
Require: ParticleNumber, MaxIter, ,
Ensure: Best Position
- 1:
Initialize the position of the particle swarm using Equation ( 4) - 2:
Construct the fitness function - 3:
Initialization parameters , , - 4:
for iter = 1: MaxIter do - 5:
Find the location and concentration of the top 4 best adapted particles . - 6:
- 7:
- 8:
- 9:
for i = 1: ParticleNumber do - 10:
Randomly select a candidate from - 11:
Generate random vectors and r - 12:
Use Equations ( 6)–( 11) to calculate F, , and G. - 13:
Update - 14:
end for - 15:
iter = iter+1 - 16:
end for - 17:
Best Position =
|